Digital Watermarking Principles and Practices Dr Latha Parameswaran
























- Slides: 48

Digital Watermarking: Principles and Practices Dr. Latha Parameswaran AMRITA University India Digital Watermarking

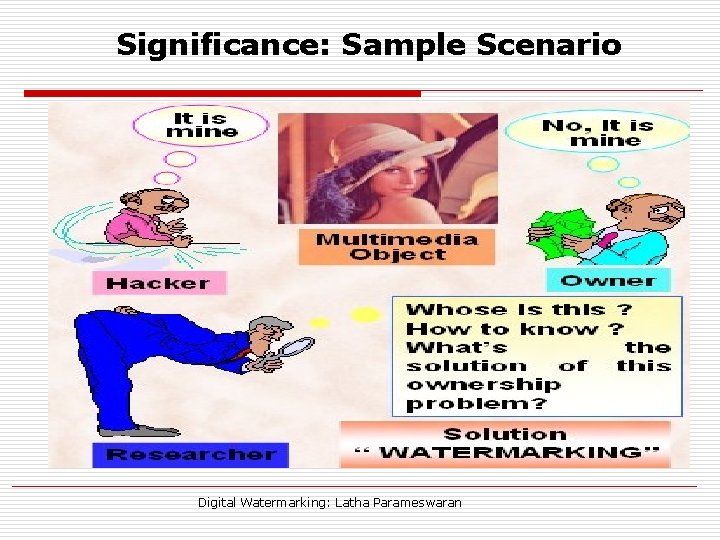
Significance n Vast multimedia content in Internet n Availability of economical and simple tools - easy to pirate and alter contents n Secure Intellectual Property Rights (IPR) n Digital Rights Management (DRM Achieved using INFORMATION HIDING Digital Watermarking: Latha Parameswaran

Motivation Ø The distribution of digital media is becoming faster, easier and requiring less effort to make exact copies Ø How to protect the intellectual property? property Conventional approaches Ø In analog world: signature, steel seal, embossed portrait, copyright label. . . Ø In digital world: Cryptology, Watermarking Digital Watermarking: Latha Parameswaran

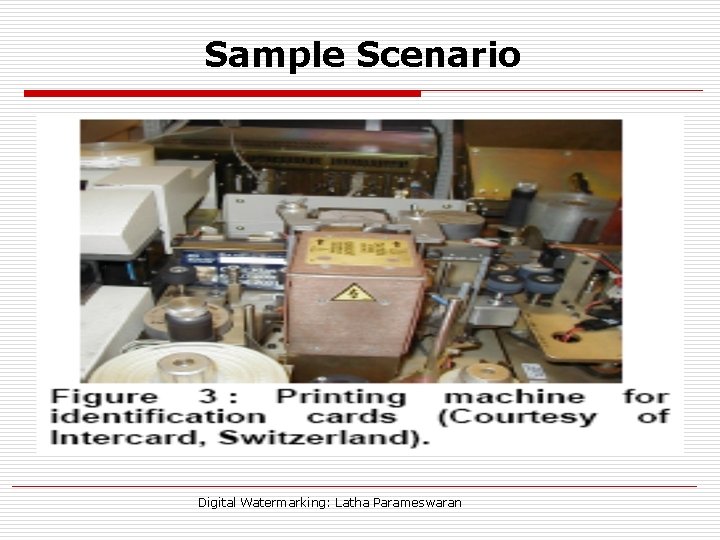
Significance: Sample Scenario Digital Watermarking: Latha Parameswaran

Information Hiding § Information Hiding is a general term encompassing many sub disciplines § Two important sub disciplines are: Steganography and watermarking Digital Watermarking: Latha Parameswaran

Solutions Available n Steganography - the art of concealed communication n Watermarking - the practice of hiding a message in a media n Cryptography - the practice of keeping messages secret Digital Watermarking: Latha Parameswaran

What is a Watermark ? A distinguishing mark or device impressed in the substance of a sheet of paper during manufacture, usually barely noticeable except when the sheet is held against strong light Ø to make forgery more difficult Ø to record the manufacturer’s trademark Digital Watermarking: Latha Parameswaran

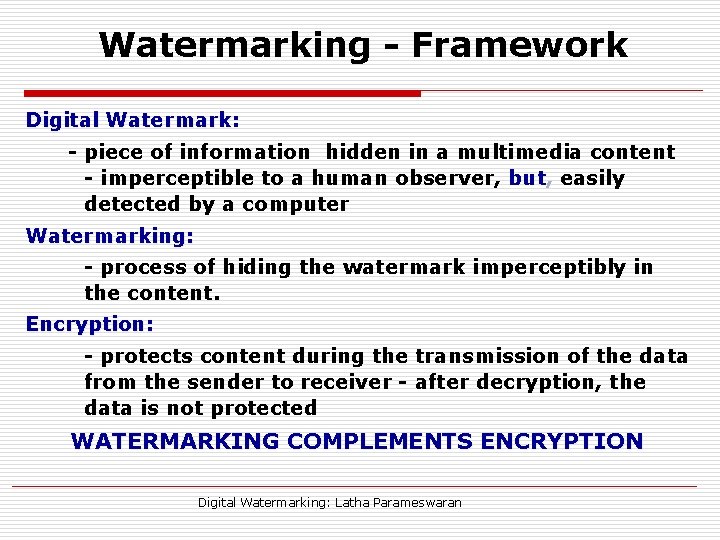
Watermarking - Framework Digital Watermark: Watermark - piece of information hidden in a multimedia content - imperceptible to a human observer, but, easily detected by a computer Watermarking: - process of hiding the watermark imperceptibly in the content. Encryption: - protects content during the transmission of the data from the sender to receiver - after decryption, the data is not protected WATERMARKING COMPLEMENTS ENCRYPTION Digital Watermarking: Latha Parameswaran

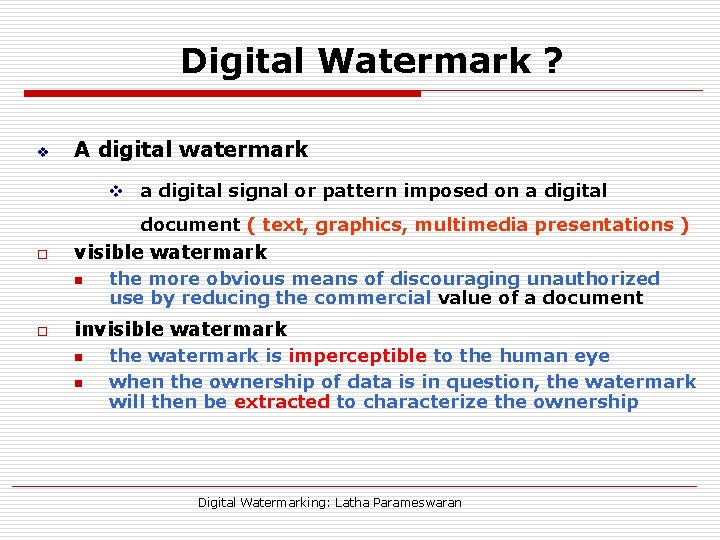
Digital Watermark ? v A digital watermark v a digital signal or pattern imposed on a digital document ( text, graphics, multimedia presentations ) o visible watermark n o the more obvious means of discouraging unauthorized use by reducing the commercial value of a document invisible watermark n n the watermark is imperceptible to the human eye when the ownership of data is in question, the watermark will then be extracted to characterize the ownership Digital Watermarking: Latha Parameswaran

Watermarking History Ø Ø Ø More than 700 years ago - Italy - indicate the paper brand the mill that produced it 18 th century - used as anti counterfeiting measures on money and other documents Term “Watermark” - introduced - end of the 18 th century. First example – similar technology - patent filed in 1954 by Emil Hembrooke - identifying music works In 1988, Komatsu and Tominaga appear to be the first to use the term “Digital Watermarking” Since 1995, WATERMARKING ERA …. Digital Watermarking: Latha Parameswaran

Watermarking Definition Ø Ø A practice of imperceptibly altering a cover to embed a message about that cover Often used whenever the cover is available to parties who know the existence of the hidden data and may have an interest in removing it – additional notion of resilience against attempts to remove the hidden data Digital Watermarking: Latha Parameswaran

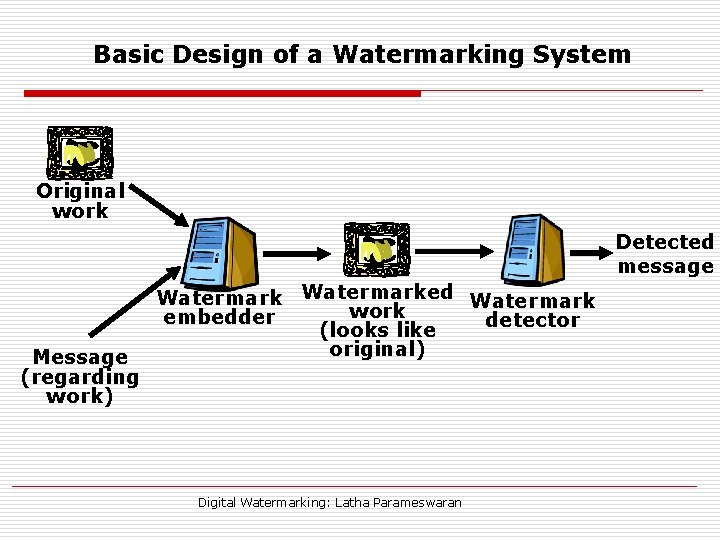
Basic Design of a Watermarking System Original work Detected message Message (regarding work) Watermarked Watermark work embedder detector (looks like original) Digital Watermarking: Latha Parameswaran

Watermarking Applications 1. Copyright protection Ø Most prominent application Ø Embed information about the owner to prevent others from claiming copyright Ø Require very high level of robustness 2. Copy protection Ø Embed watermark to disallow unauthorized copying of the cover Ø For example, a compliant DVD player will not playback or copy data that carry a “copy never” watermark 3. Content Authentication Ø Embed a watermark to detect modifications to the cover Ø The watermark in this case has low robustness, “fragile” Digital Watermarking: Latha Parameswaran

Watermarking Applications … 4. Transaction Tracking Ø Embed a watermark to convey information about the legal recipient of the cover Ø This is useful to monitor or trace back illegally produced copies of the cover Ø This is usually referred to as “fingerprinting” 5. Broadcast Monitoring Ø Embed a watermark in the cover and use automatic monitoring to verify whether cover was broadcasted as agreed Digital Watermarking: Latha Parameswaran

Watermarking Characteristics Imperceptibility Ø The modifications caused by watermark embedding should be below the perceptible threshold Robustness Ø The ability of the watermark to resist distortion introduced by standard or malicious data processing Security Ø A watermark is secure if knowing the algorithms for embedding and extracting does not help unauthorized party to detect or remove the watermark Digital Watermarking: Latha Parameswaran

Watermarking Characteristics Payload Ø The amount of information that can be stored in a watermark Informed (non oblivious, or private) Ø The original un watermarked cover is required to perform the extraction process Blind (oblivious, or public) Ø The original un watermarked cover is NOT required to perform the extraction process Digital Watermarking: Latha Parameswaran

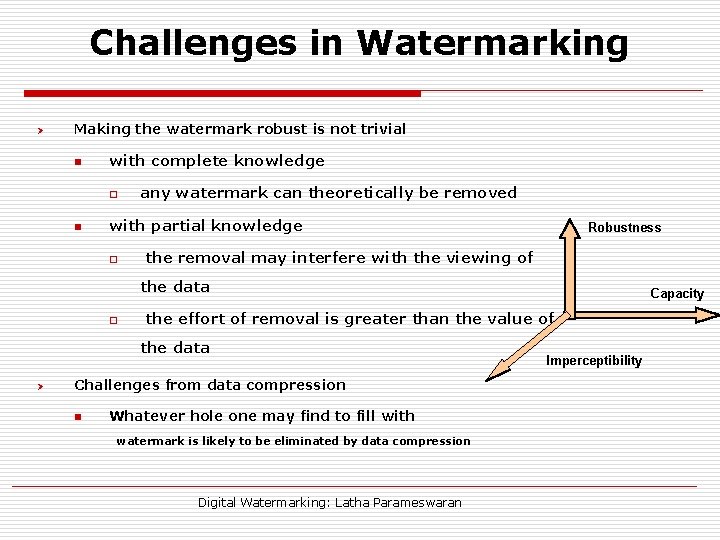
Challenges in Watermarking Ø Making the watermark robust is not trivial n with complete knowledge o n any watermark can theoretically be removed with partial knowledge o Robustness the removal may interfere with the viewing of the data o the effort of removal is greater than the value of the data Ø Challenges from data compression n Capacity Whatever hole one may find to fill with watermark is likely to be eliminated by data compression Digital Watermarking: Latha Parameswaran Imperceptibility

Attacks Q Signal enhancement (sharpening, contrast enhancement, etc. ) Q Additive and multiplicative noise (gaussian, uniform, etc. ) Q Filtering (High pass, low pass, linear, nonlinear, etc. ) Q Lossy compression (JPEG, MPEG-x, etc. ) Q Geometric transforms (RST) Q Data reduction (cropping, clipping, etc. ) Q D/A and A/D conversion (print-scan, etc. ) Q Multiple watermarking, Collusion attack, Mosaic attack Digital Watermarking: Latha Parameswaran

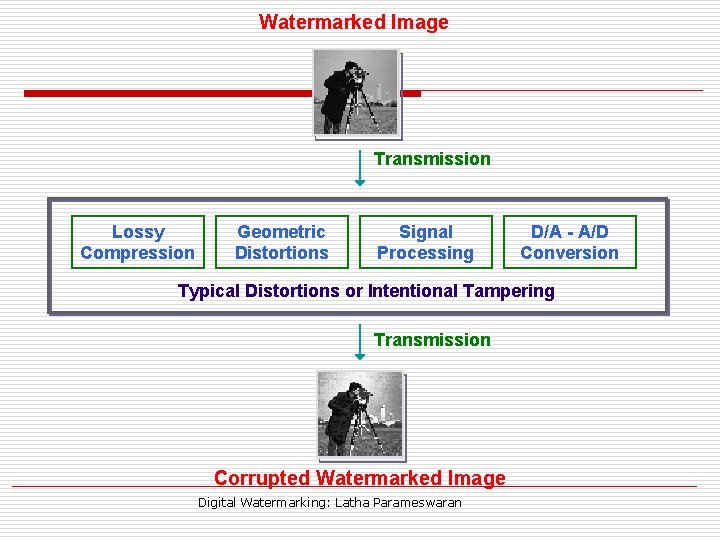
Watermarked Image Transmission Lossy Compression Geometric Distortions Signal Processing D/A - A/D Conversion Typical Distortions or Intentional Tampering Transmission Corrupted Watermarked Image Digital Watermarking: Latha Parameswaran

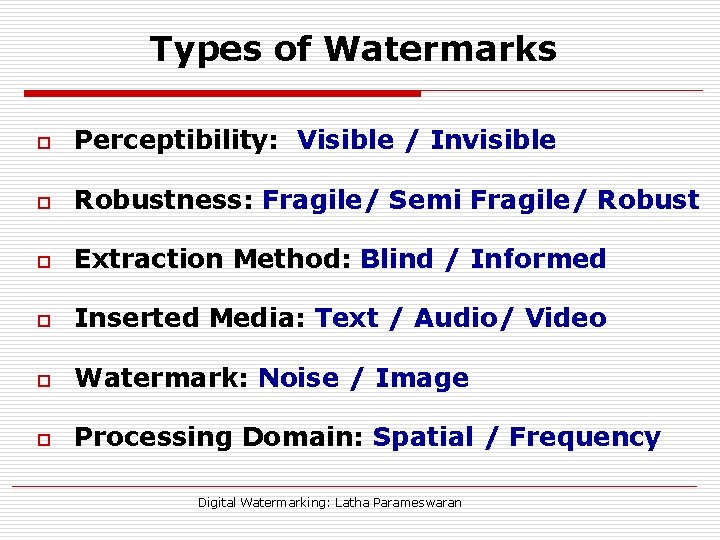
Types of Watermarks o Perceptibility: Visible / Invisible o Robustness: Fragile/ Semi Fragile/ Robust o Extraction Method: Blind / Informed o Inserted Media: Text / Audio/ Video o Watermark: Noise / Image o Processing Domain: Spatial / Frequency Digital Watermarking: Latha Parameswaran

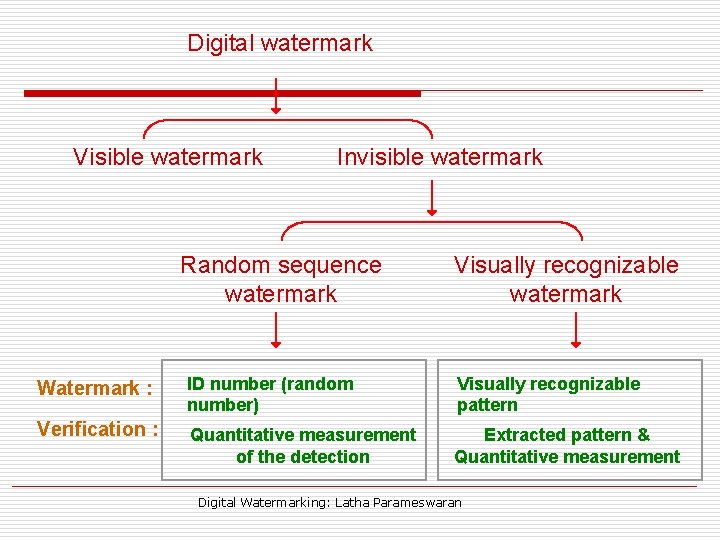
Digital watermark Visible watermark Invisible watermark Random sequence watermark Visually recognizable watermark Watermark : ID number (random number) Visually recognizable pattern Verification : Quantitative measurement of the detection Extracted pattern & Quantitative measurement Digital Watermarking: Latha Parameswaran

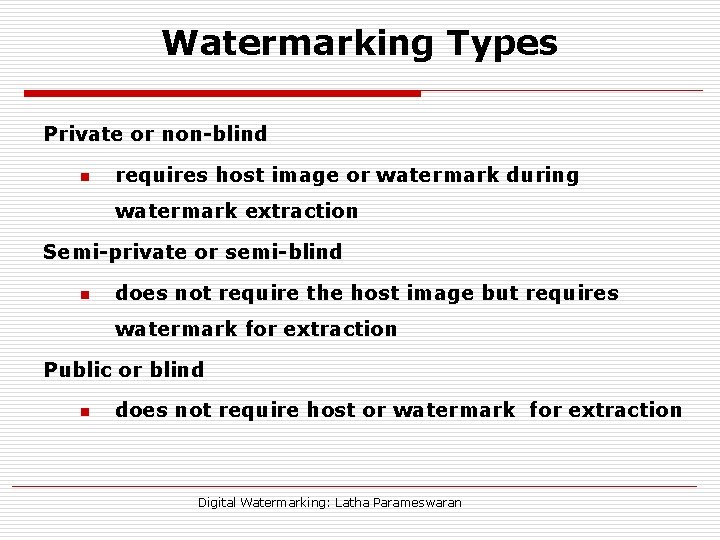
Watermarking Types Private or non-blind n requires host image or watermark during watermark extraction Semi-private or semi-blind n does not require the host image but requires watermark for extraction Public or blind n does not require host or watermark for extraction Digital Watermarking: Latha Parameswaran

Another classification Robust watermarking n resist legitimate, content-preserving, unintentional modifications n Applications: copyright protection and content tracking Fragile watermarking n are sensitive, to the slightest modification of the watermarked image n Applications: Content Authentication in sensitive documents like medical images Semi-fragile watermarking n tolerates some degree of legitimate modifications n identify regions of suspected alterations n Applications: Content Authentication Digital Watermarking: Latha Parameswaran

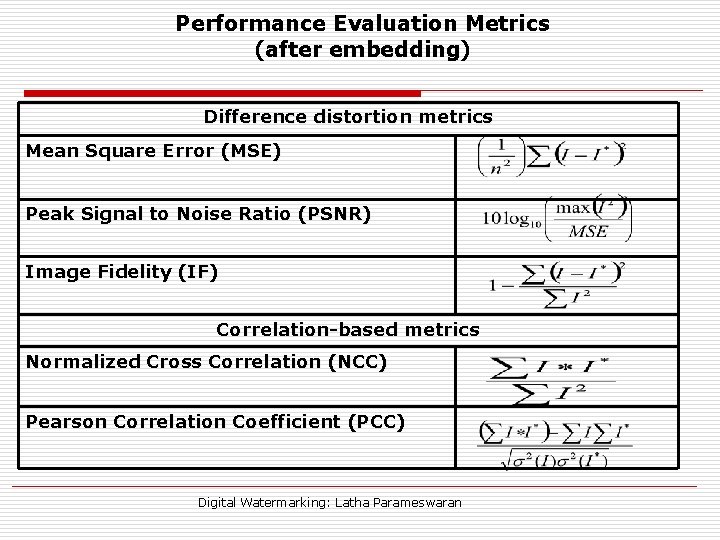
Performance Evaluation Metrics (after embedding) Difference distortion metrics Mean Square Error (MSE) Peak Signal to Noise Ratio (PSNR) Image Fidelity (IF) Correlation-based metrics Normalized Cross Correlation (NCC) Pearson Correlation Coefficient (PCC) Digital Watermarking: Latha Parameswaran

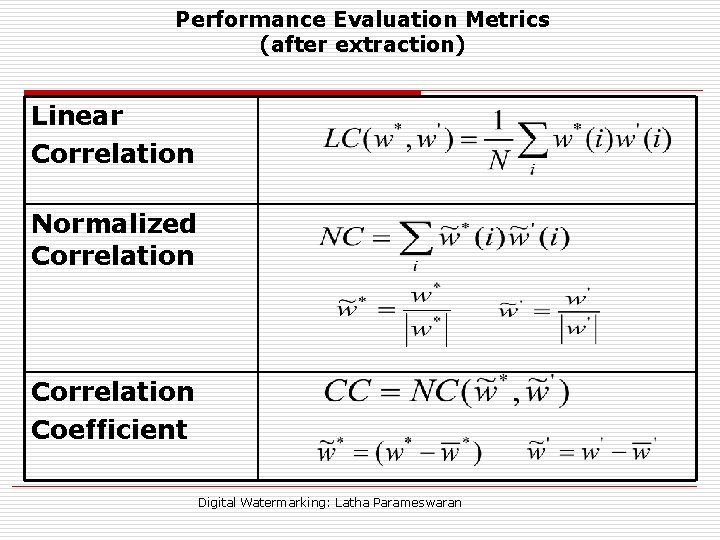
Performance Evaluation Metrics (after extraction) Linear Correlation Normalized Correlation Coefficient Digital Watermarking: Latha Parameswaran

Watermarking Phases 1. Watermark Embedding n Embed watermark in watermark carriers (DCT, DWT, …) of the host data o May be corrupted by noise, compressed, etc. during transmission 2. Watermark Extraction n Extract the embedded watermark from the carriers o Extracted watermark may vary from embedded n Compute the watermark from the received data n Measure closeness by metrics like correlation Digital Watermarking: Latha Parameswaran

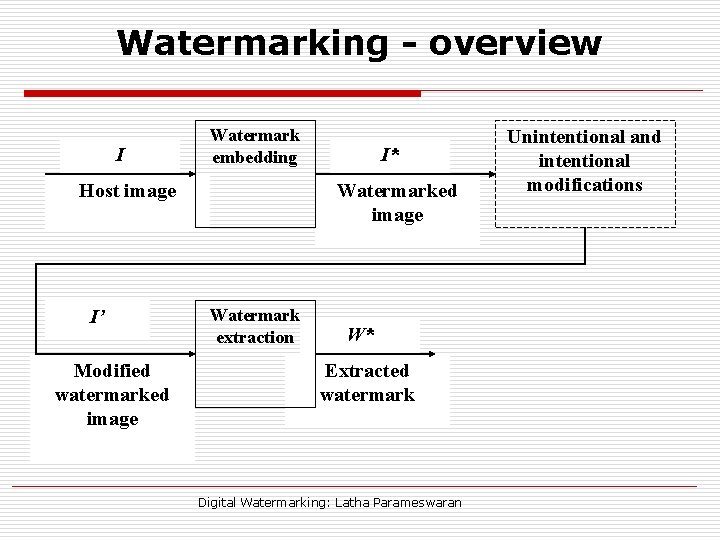
Watermarking - overview I Watermark embedding Host image I’ Modified watermarked image I* Watermarked image Watermark extraction W* Extracted watermark Digital Watermarking: Latha Parameswaran Unintentional and intentional modifications

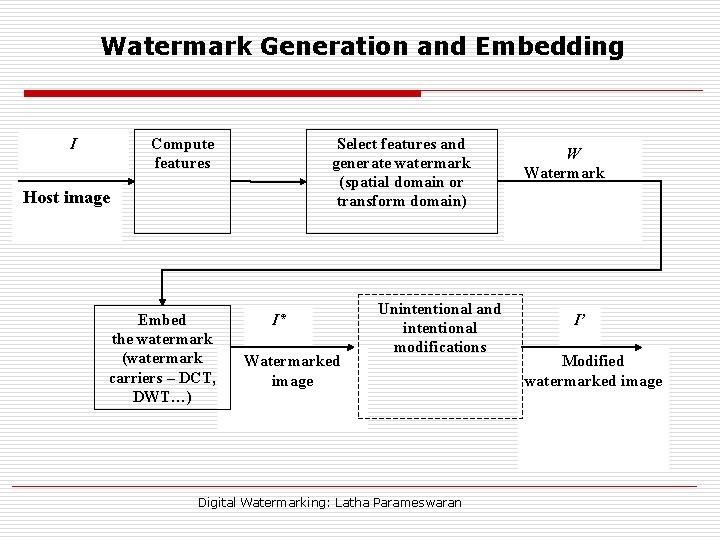
Watermark Generation and Embedding I Select features and generate watermark (spatial domain or transform domain) Compute features Host image Embed the watermark (watermark carriers – DCT, DWT…) I* Watermarked image Unintentional and intentional modifications Digital Watermarking: Latha Parameswaran W Watermark I’ Modified watermarked image

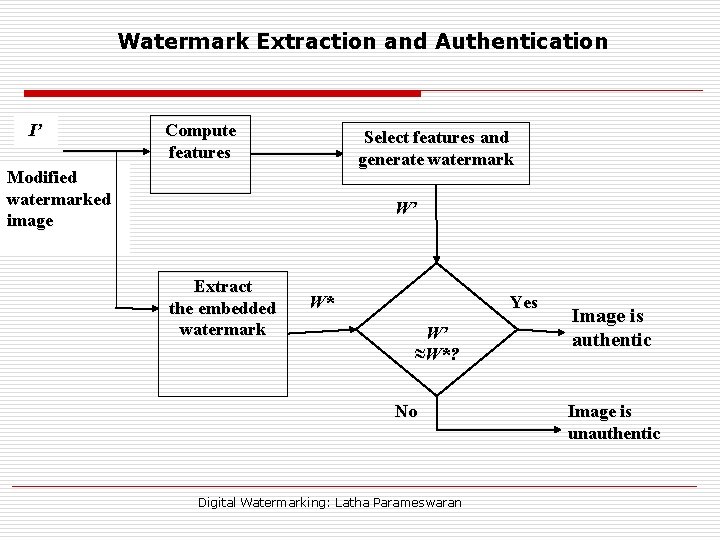
Watermark Extraction and Authentication I’ Compute features Select features and generate watermark Modified watermarked image W’ Extract the embedded watermark W* Yes W’ ≈W*? No Digital Watermarking: Latha Parameswaran Image is authentic Image is unauthentic

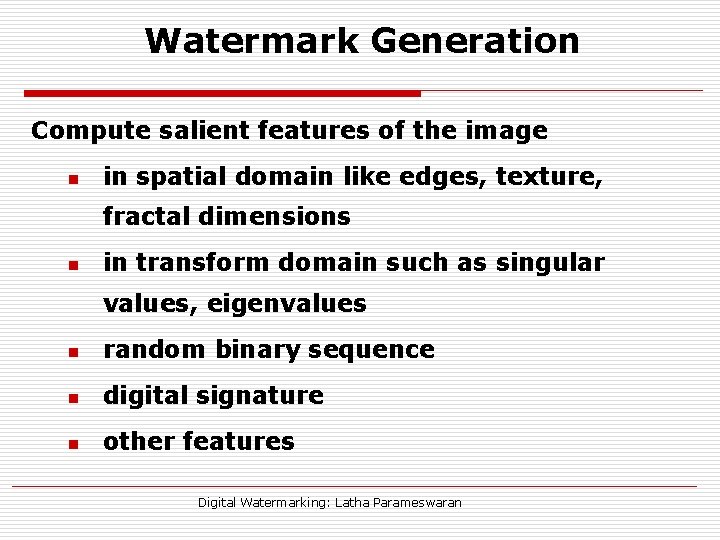
Watermark Generation Compute salient features of the image n in spatial domain like edges, texture, fractal dimensions n in transform domain such as singular values, eigenvalues n random binary sequence n digital signature n other features Digital Watermarking: Latha Parameswaran

Watermark Carriers Embed watermark in watermark carriers: n Discrete Fourier Transform (DFT) n Discrete Walsh-Hadamard Transform (DWHT), n Discrete Cosine Transform (DCT) and Discrete Wavelet Transform (DWT) Digital Watermarking: Latha Parameswaran

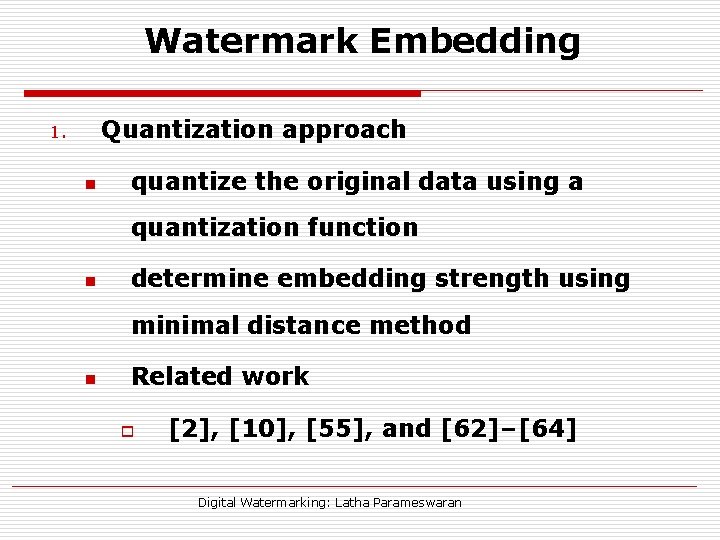
Watermark Embedding Quantization approach 1. n quantize the original data using a quantization function n determine embedding strength using minimal distance method n Related work o [2], [10], [55], and [62]–[64] Digital Watermarking: Latha Parameswaran

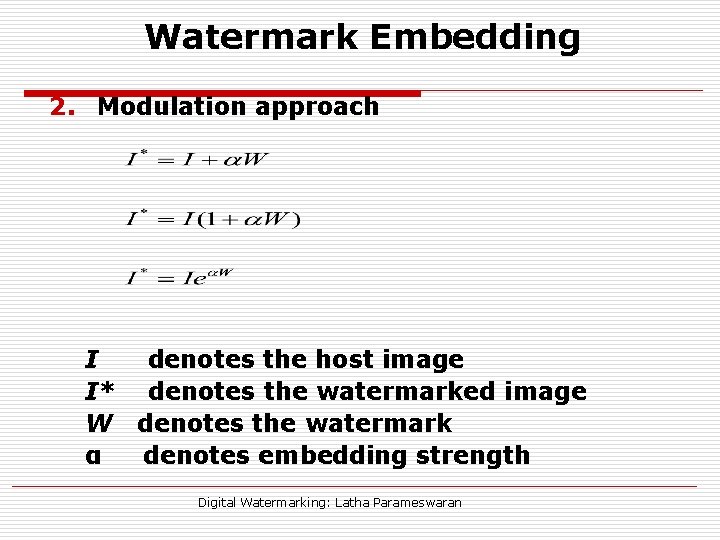
Watermark Embedding 2. Modulation approach I denotes the host image I* denotes the watermarked image W denotes the watermark α denotes embedding strength Digital Watermarking: Latha Parameswaran

Watermark Extraction and Verification Three step process: 1. 2. 3. Extract the embedded watermark from the received image Compute watermark from the received image using the same watermark generation procedure Compare extracted watermark with the computed watermark using the correlation metric - Verification Non- blind, Semi-blind, Blind Digital Watermarking: Latha Parameswaran

Digital Watermarking: Latha Parameswaran

Sample Scenarios Digital Watermarking: Latha Parameswaran

Sample Scenarios Digital Watermarking: Latha Parameswaran

Sample Scenario Digital Watermarking: Latha Parameswaran

Sample Scenario Digital Watermarking: Latha Parameswaran

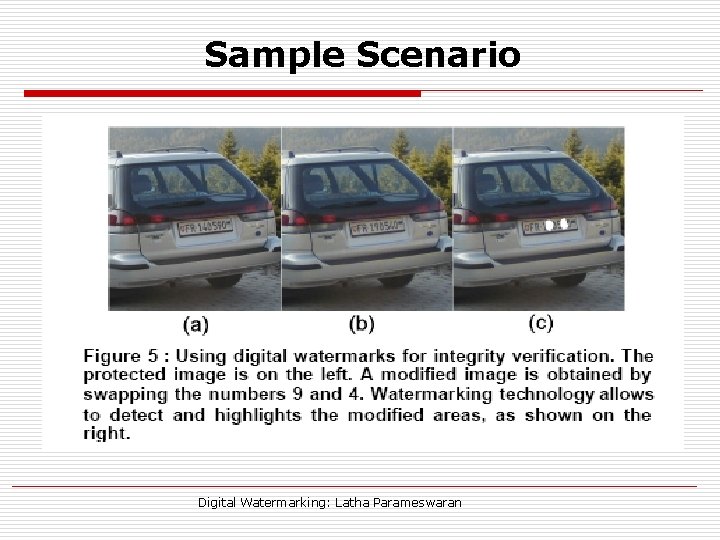
Sample Scenario Digital Watermarking: Latha Parameswaran

Sample Scenario Digital Watermarking: Latha Parameswaran

What next ? o Is the interest warranted? o What are the existing and potential commercial applications of this technology? o What scientific progress has been made in the past 10 years? o What are the most exciting areas for research? o Where might the next 10 years take us? Digital Watermarking: Latha Parameswaran

Current Standards o The CPTWG (Copy Protection Technical Working Group) tested watermarking systems for protection of video on DVD disks. o The SDMI (Secure Digital Music Initiative) made watermarking a core component in their system for music protection. o Two projects sponsored by the European Union, VIVA and Talisman, tested watermarking for broadcast monitoring. o The ISO (International Organization for Standardization) took an interest in the context of designing advanced MPEG standards. (MPEG-21) Digital Watermarking: Latha Parameswaran

Problems Faced o Initial expectations of watermarking are too high n Security against intentional efforts to remove a watermark from content o Request for proposal met specifications o Slow adoption of watermarking techniques n o Mainly due to the diverge business interests of the three industry groups o Content owner o Manufacturers of consumer electronics o Manufactures of computers Is the current business and academic interest in watermarking warranted? Digital Watermarking: Latha Parameswaran

Business Perpective o Can watermarking provide economic solutions to real problems? o Current business interests n Security o Current watermark solutions are of weak sucurity, but suitable for many business models n Device control o No security threat or requirements o Linking traditional media to the Web is receiving increased attention. Digital Watermarking: Latha Parameswaran

What is in research? o Some advances are in their infancy, and much work remains to be done. o Some results are imminent, making an area exciting. While in other cases, no breakthroughs are found on the horizon. o Possible research topics n Informed embedding n Geometric/temporal distortions in a blind detector n Optimally embedding with fidelity and robustness constraints n Whether a watermarking system can be designed that permits public detection while preventing an adversary form removing the watermark. (The authors are divided in this problem) Digital Watermarking: Latha Parameswaran

Conclusion o o o No standards have been derived An exhaustive list of open problems A significant area of research Wide applications Industry – Academia relation builder Digital Watermarking: Latha Parameswaran

Digital Watermarking: Latha Parameswaran