PKI for the Mystified A Nontechnical Introduction to



























- Slides: 45

PKI for the Mystified A Non-technical Introduction to Public Key Infrastructure and Cryptography Mark Norman DCOCE Oxford University Computing Services 23 February 2004 1

DCOCE Der-kot-chee (…bless you!) Digital Certificate Operation in a Complex Environment 23 February 2004 2

The DCOCE project • DCOCE is about authentication with digital certificates • Digital certificates use Public Key Infrastructure (PKI) – PKI is very secure – but can be difficult to administer – and a lot of people don't understand it too well 23 February 2004 3

Aim of this talk • Improve the understanding of the fundamentals of encryption and public key encryption – So that people can then go on and be confident with: • • • PKI PGP SSL (e. g. using a credit card on-line) Encrypting documents (and email) Signing documents (and email) Deciding whether a signature is good or not • I won’t use any maths! 23 February 2004 4

Parts of this talk • Define a few terms • Symmetric keys – (A demonstration) – Breaking (or cracking) encrypted information • Asymmetric keys • Signing things with keys • Trusting keys 23 February 2004 5

A few terms: Authentication • The act of verifying that an electronic identity (username, login name etc. ) is being employed by the person to whom it was issued – Strictly it should mean "establishing the validity of something, such as an identity". – (The procedure as indicated by the definition above can be very difficult indeed, but PKI attempts to do this. ) 23 February 2004 6

A few terms: Authentication 23 February 2004 7

A few terms: Authorisation • Associating rights or capabilities with a subject • Authorisation usually comes after authentication – i. e. once the service knows who it is (Authenticated), it then proceeds to decide what that person/subject can do (Authorisation) 23 February 2004 8

What is Public Key Infrastructure? • A key is like a code sheet • A public key is an odd concept – why would you reveal your secret code in public? • We need to understand symmetric keys and asymmetric keys 23 February 2004 9

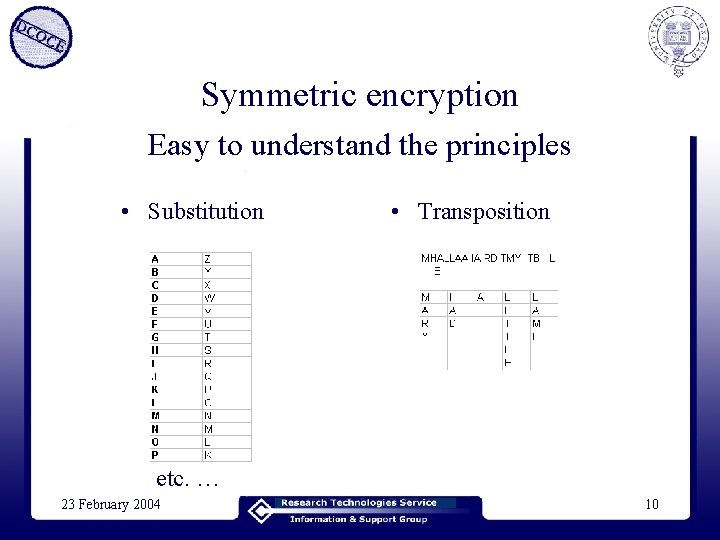
Symmetric encryption Easy to understand the principles • Substitution • Transposition etc. … 23 February 2004 10

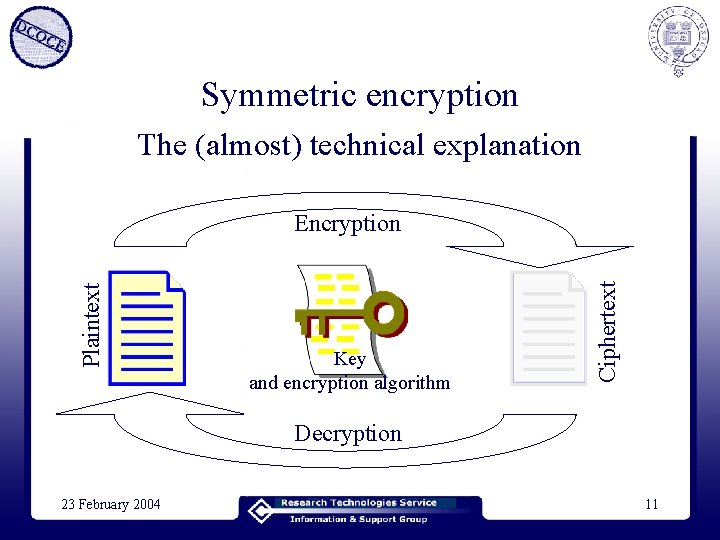
Symmetric encryption The (almost) technical explanation Key and encryption algorithm Ciphertext Plaintext Encryption Decryption 23 February 2004 11

Demonstration 23 February 2004 12

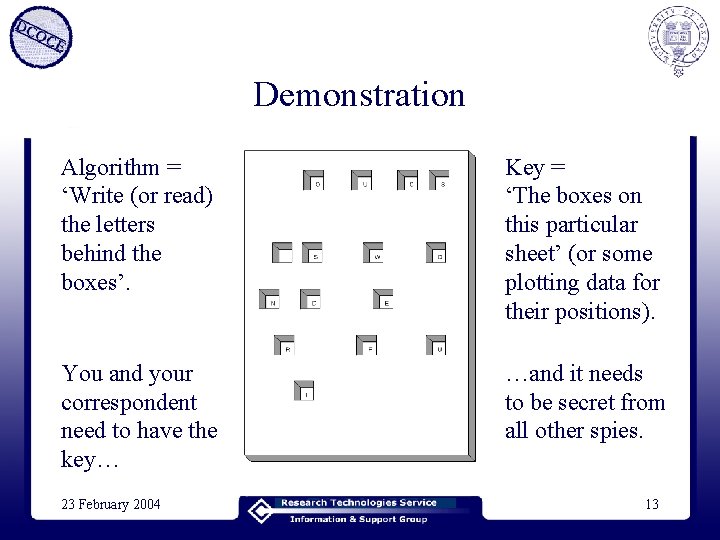
Demonstration Algorithm = ‘Write (or read) the letters behind the boxes’. Key = ‘The boxes on this particular sheet’ (or some plotting data for their positions). You and your correspondent need to have the key… …and it needs to be secret from all other spies. 23 February 2004 13

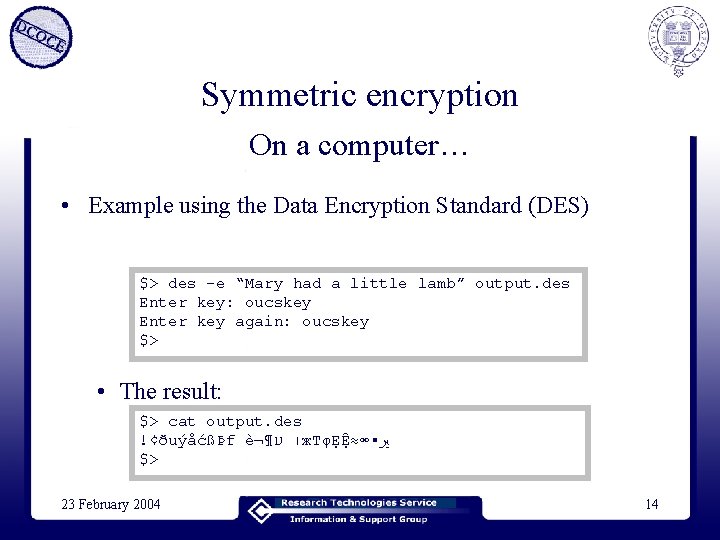
Symmetric encryption On a computer… • Example using the Data Encryption Standard (DES) $> des -e “Mary had a little lamb” output. des Enter key: oucskey Enter key again: oucskey $> • The result: $> cat output. des !¢ðuýåćßÞf 謶 ׀ ע ж. ТφẸỆ≈∞▪ ﲑ $> 23 February 2004 14

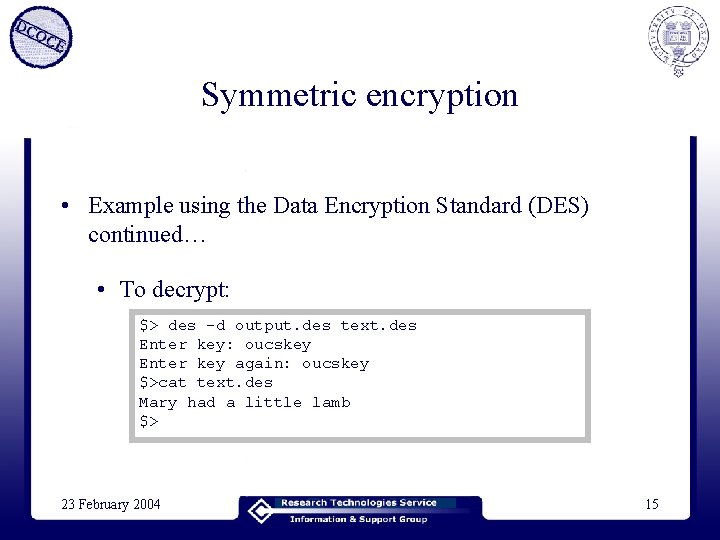
Symmetric encryption • Example using the Data Encryption Standard (DES) continued… • To decrypt: $> des -d output. des text. des Enter key: oucskey Enter key again: oucskey $>cat text. des Mary had a little lamb $> 23 February 2004 15

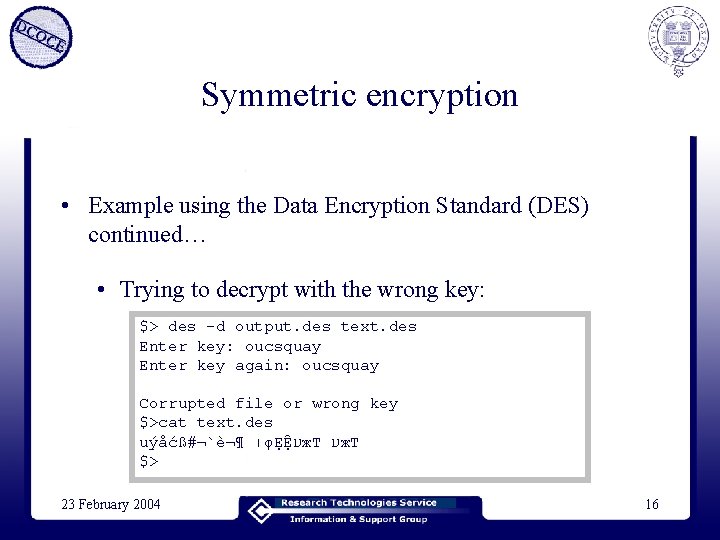
Symmetric encryption • Example using the Data Encryption Standard (DES) continued… • Trying to decrypt with the wrong key: $> des -d output. des text. des Enter key: oucsquay Enter key again: oucsquay Corrupted file or wrong key $>cat text. des uýåćß#¬`謶 ׀ φẸỆ ע ж. Т $> 23 February 2004 16

Symmetric encryption Attacking a cipher • How safe are encryption algorithms anyway? • Example using (DES) continued… • What about a ‘brute force’ attack? i. e. ‘guessing’ at the key “oucskey” • DES algorithm has a 56 -bit key. Therefore, there are 256 = 72, 057, 594, 037, 900, 000 different keys • 834 days at a billion keys per second • But for a typed key, effectively 968 (83 days) 23 February 2004 17

Symmetric encryption Attacking a cipher • How safe are encryption algorithms anyway? – Established algorithms should remain sound – Safety is dependent on key length 23 February 2004 18

Symmetric encryption Demonstration 23 February 2004 19

Symmetric encryption Some issues • So you have to have the same key as your correspondent – is that a problem? – How do you send the key safely? – Do I try to exchange keys before I communicate? • How many keys will I need to communicate with everyone? – You need a key for everyone! 23 February 2004 20

Symmetric encryption • What makes it symmetric? 23 February 2004 21

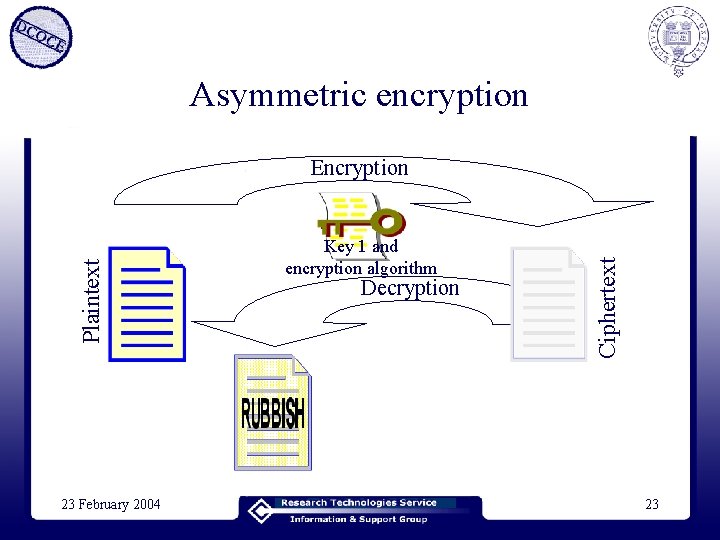
Asymmetric encryption • Then there was asymmetric encryption – Whitfield Diffie and Martin Hellman (1975) – (Ellis and Cox, 1973) – A key pair is constructed using some complicated maths (the keys are not the same) – Each party has two keys (public and private) – Anything encrypted with key 1 can only be decrypted with key 2 – Asymmetric! 23 February 2004 22

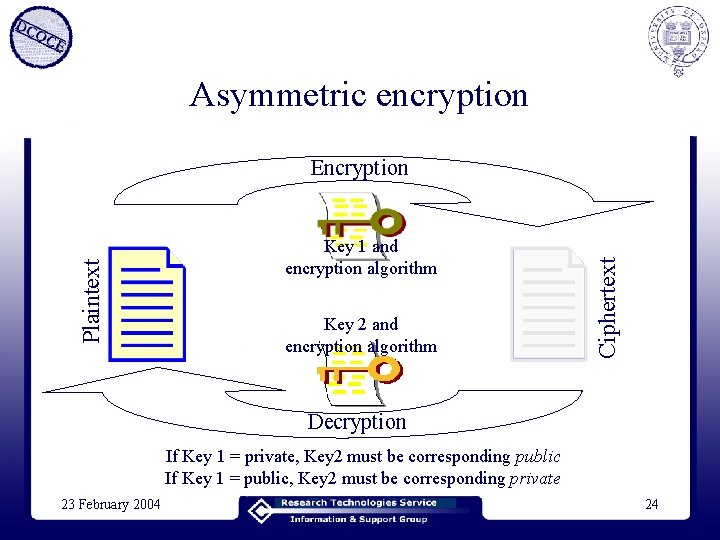
Asymmetric encryption 23 February 2004 Key 1 and encryption algorithm Decryption Ciphertext Plaintext Encryption 23

Asymmetric encryption Key 1 and encryption algorithm Key 2 and encryption algorithm Ciphertext Plaintext Encryption Decryption If Key 1 = private, Key 2 must be corresponding public If Key 1 = public, Key 2 must be corresponding private 23 February 2004 24

Public and private keys • Keys exist in pairs – Keep one private (very secret) and 'publish' one – Public keys can exist on certificates • Encryption can be done by either key – If it is your key pair, you can use the private key – Anyone else can use the public key to encrypt something 23 February 2004 25

Asymmetric encryption Demonstration Public key Complex maths! Private key 23 February 2004 26

Asymmetric encryption Demonstration 23 February 2004 27

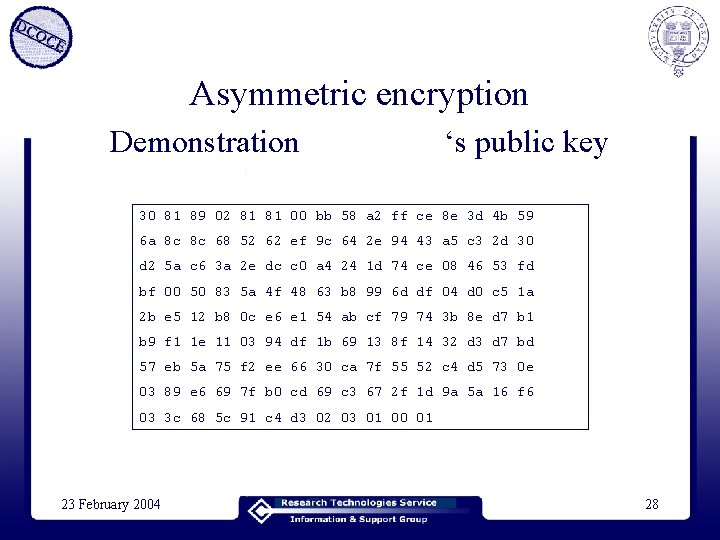
Asymmetric encryption Demonstration ‘s public key 30 81 89 02 81 81 00 bb 58 a 2 ff ce 8 e 3 d 4 b 59 6 a 8 c 8 c 68 52 62 ef 9 c 64 2 e 94 43 a 5 c 3 2 d 30 d 2 5 a c 6 3 a 2 e dc c 0 a 4 24 1 d 74 ce 08 46 53 fd bf 00 50 83 5 a 4 f 48 63 b 8 99 6 d df 04 d 0 c 5 1 a 2 b e 5 12 b 8 0 c e 6 e 1 54 ab cf 79 74 3 b 8 e d 7 b 1 b 9 f 1 1 e 11 03 94 df 1 b 69 13 8 f 14 32 d 3 d 7 bd 57 eb 5 a 75 f 2 ee 66 30 ca 7 f 55 52 c 4 d 5 73 0 e 03 89 e 6 69 7 f b 0 cd 69 c 3 67 2 f 1 d 9 a 5 a 16 f 6 03 3 c 68 5 c 91 c 4 d 3 02 03 01 00 01 23 February 2004 28

Private keys • Extremely secret! • If you send something encrypted by a private key, it can be read by everyone, but they know it came from you. – Authentication 23 February 2004 29

Public keys • Not at all secret! – Widely available, but must be trusted – May be supplied as part of a certificate • If you send something using a public key, it can only be read by the entity to which it is addressed. – Secure communications • e. g. SSL 23 February 2004 30

How can I trust a public key? • Someone can use a public key to prove their identity to me – but only if I trust that public key – there's public keys out there that say they belong to George Bush etc. • So if someone I trusted endorsed (signed) that public key – hold that thought for a moment - we’ll come back to this. . . 23 February 2004 31

Signing things with keys • Asymmetric keys can be used to sign things – encrypt a bit of text with your private key (can be attached 'securely' to the 'document') – people can de-crypt it with the public key and know that it was signed by you • What? … 23 February 2004 32

Signing things with keys • You need to know something about hashes… – Message digests or one way hash functions distil the information contained in a file (very small or very large) into a single large number (usually between 128 and 256 bits in length) • So, you can actually add the hash value to the file somehow and then sign (or encrypt) that hash value with your private key. 23 February 2004 33

Signing things with keys Very important document. Blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, Alg. <975764138552> 23 February 2004 34

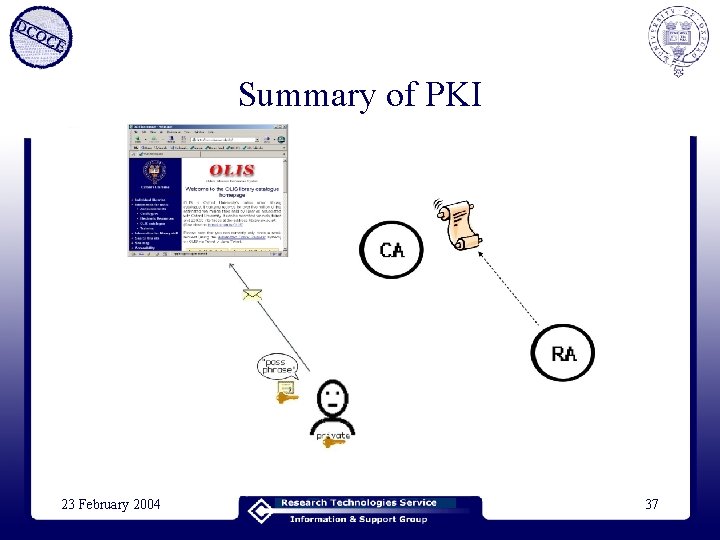
How can I trust a public key? • Put that public key on a certificate • (There are other ways, but this is PKI) • Get someone you trust to sign the certificate – If the certificate is tampered with, the signature is broken • Organisations who sign public keys/certificates are called Certification Authorities (CA) 23 February 2004 35

Public Key Infrastructure • • You create a key pair Put one key of the pair on a certificate Send the certificate (request) to the CA Present yourself or identify yourself to the Registration Authority (RA) • The RA tells the CA that you are OK • The CA sends you the signed certificate 23 February 2004 36

Summary of PKI 23 February 2004 37

Public Key Infrastructure • Now you have a signed certificate, people and services can trust that you are who you say you are • Present your certificate to a service • Tell them something encrypted by your private key • They like your certificate and know it is you 23 February 2004 38

Public Key Infrastructure • You keep your private key very secret – Obey the rules for this! • Your public key is on the certificate • Services must trust the CA • Your certificate will have an expiry date – after which you may have to re-visit the RA • Your certificate can be revoked at any time 23 February 2004 39

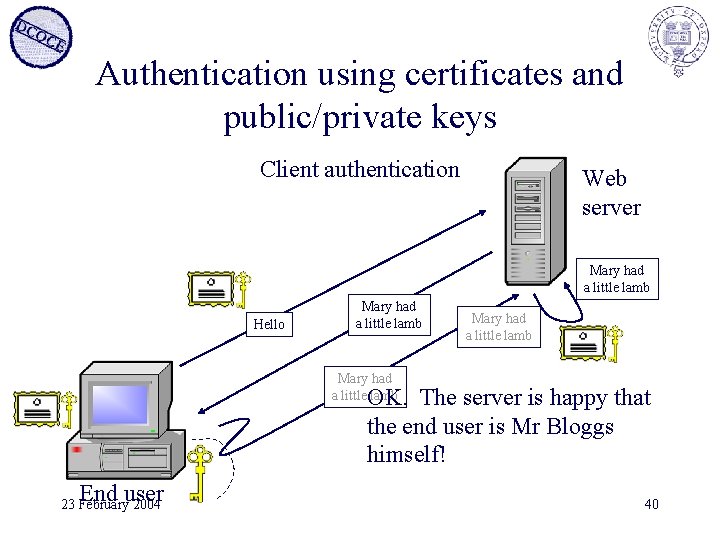
Authentication using certificates and public/private keys Client authentication Web server Mary had a little lamb Hello Mary had a little lamb OK. The server is happy that the end user is Mr Bloggs himself! End user 23 February 2004 40

Public Key Infrastructure • Asymmetric encryption = public/private keys • Symmetric encryption is faster – but how do you deliver the keys • Asymmetric encryption is used in SSL – Secure Sockets Layer, very common • Also used in client authentication (less common, at the moment) 23 February 2004 41

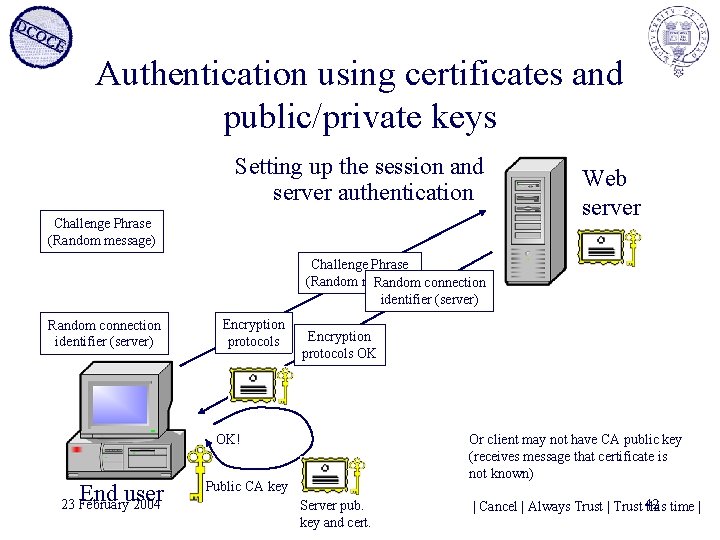
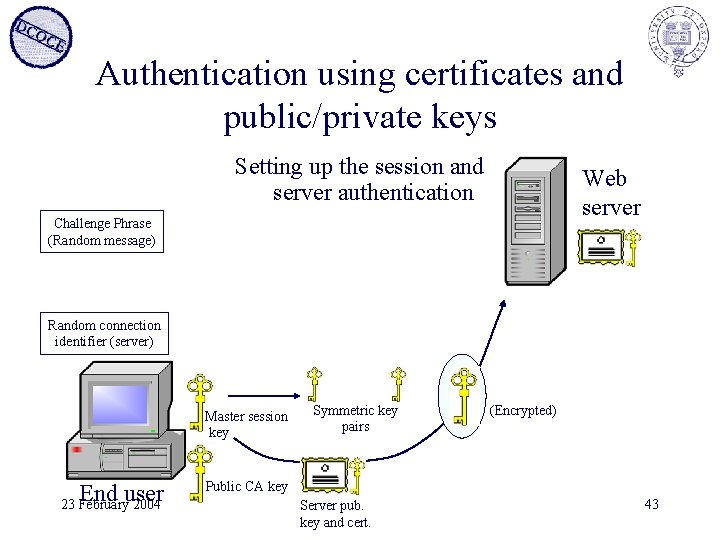
Authentication using certificates and public/private keys Setting up the session and server authentication Challenge Phrase (Random message) Web server Challenge Phrase (Random message) Random connection identifier (server) Encryption protocols OK OK! End user 23 February 2004 Or client may not have CA public key (receives message that certificate is not known) Public CA key Server pub. key and cert. | Cancel | Always Trust | Trust 42 this time |

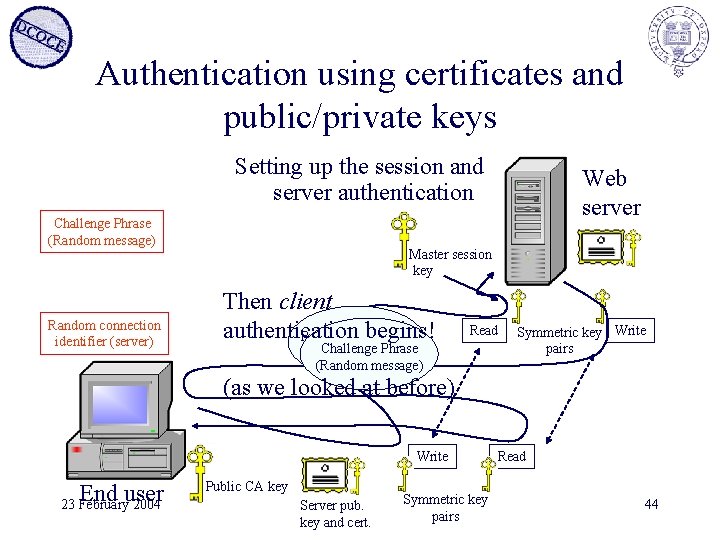
Authentication using certificates and public/private keys Setting up the session and server authentication Web server Challenge Phrase (Random message) Random connection identifier (server) Master session key End user 23 February 2004 Symmetric key pairs (Encrypted) Public CA key Server pub. key and cert. 43

Authentication using certificates and public/private keys Setting up the session and server authentication Challenge Phrase (Random message) Random connection identifier (server) Web server Master session key Then client authentication begins! Random connection Read Challenge Phrase identifier (server) (Random message) Symmetric key Write pairs (as we looked at before) Write End user 23 February 2004 Public CA key Server pub. key and cert. Symmetric key pairs Read 44

PKI for the Mystified A Non-technical Introduction to Public Key Infrastructure and Cryptography Please tell me you’re not still mystified! Mark Norman DCOCE Oxford University Computing Services 23 February 2004 45