PKI CA CSH 6 Chapter 37 PKI Certificate

























- Slides: 45

PKI & CA CSH 6 Chapter 37 “PKI & Certificate Authorities” Santosh Chokhani, Padgett Peterson, & Steven Lovaas 1 Copyright © 2020 M. E. Kabay. All rights reserved.

Topics Ø Introduction Ø Need for PKI Ø Public Key Certificate Ø Enterprise Public Key Infrastructure Ø Certificate Policy Ø Global PKI Ø Forms of Revocation Ø Rekey Ø Key Recovery Ø Privilege Management Ø Trusted Archival Services & Trusted Time Stamps Ø Cost of PKI 2 Copyright © 2020 M. E. Kabay. All rights reserved.

Introduction ØOverview ØSymmetric Key Cryptography ØPublic Key Cryptosystem ØAdvantages of PKC over SKC ØCombination of the Two 3 Copyright © 2020 M. E. Kabay. All rights reserved.

Overview Ø Early days of encryption across Internet q. Individuals q. Pretty Good Privacy (PGP) q. Web of trust Ø Today’s encryption much more complex q. Formalized q. Organizational q. Fundamentally concerned with trust relationships Ø Key applications include q. Data in flight (networking) q. Data at rest (storage) See CSH 6 Chapters 7: Encryption 32: VPNs & Secure Remote Access 4 Copyright © 2020 M. E. Kabay. All rights reserved.

Symmetric Key Cryptography 5 Copyright © 2020 M. E. Kabay. All rights reserved.

Public Key Cryptosystem 6 Copyright © 2020 M. E. Kabay. All rights reserved.

Advantages of PKC over SKC Ø PKC requires fewer keys to manage q. Total keys 2 n (Cf SKC with ½n(n-1) ≈ ½n 2) Ø Can focus on authenticating only public keys Ø No secret keys transmitted over networks q. Not susceptible to compromise even if public keys must be changed Ø Public keys can be used to encrypt temporary session keys for one-time use Ø Session keys allow PKC to encrypt message for multiple recipients easily 7 Copyright © 2020 M. E. Kabay. All rights reserved.

Combination of the Two Ø Usual implementation of PKC uses symmetric algorithm for session key q. Computationally less onerous q. Encrypt session key with asymmetric key Ø Digital signing uses similar method q. Encrypt secure hash of document q. Decrypt encrypted hash to verify data integrity and authenticity of text 8 Copyright © 2020 M. E. Kabay. All rights reserved.

Need for PKI Ø Everything in PKC depends on trustworthiness (authenticity) of the public key (certificate) q. If someone posts a public key in victim’s name, can üIntercept encrypted content intended for spoofed victim üIssue fraudulent content in victim’s name Ø Similar problems with Secure Sockets Layer (SSL) v 2 Ø Develop chain of trust for certificates (value signed by public keys) 9 Copyright © 2020 M. E. Kabay. All rights reserved.

Public Key Certificate (1) Ø Certification authority (CA) issues signatures for public keys Ø Standard is ANSI X. 509 (IETF RFC 5280) q. Described in Abstract Syntax Notation (ANS. 1) q. Often encoded in MIME (Multipurpose Internet Mail Extensions) to use only ASCII characters Ø Trust the root & you can trust the issued keys 10 Copyright © 2020 M. E. Kabay. All rights reserved.

Public Key Certificate (2) Every CA’s certificate has list of key info: Ø Version # Ø Certificate serial # Ø Algorithm Ø CA name Ø Validity period for certificate Ø Subscriber name Ø Subscriber public key, PK algorithm, parameters Ø CA unique ID (optional) Ø Extensions (optional) Ø CA’s digital signature 11 Copyright © 2020 M. E. Kabay. All rights reserved.

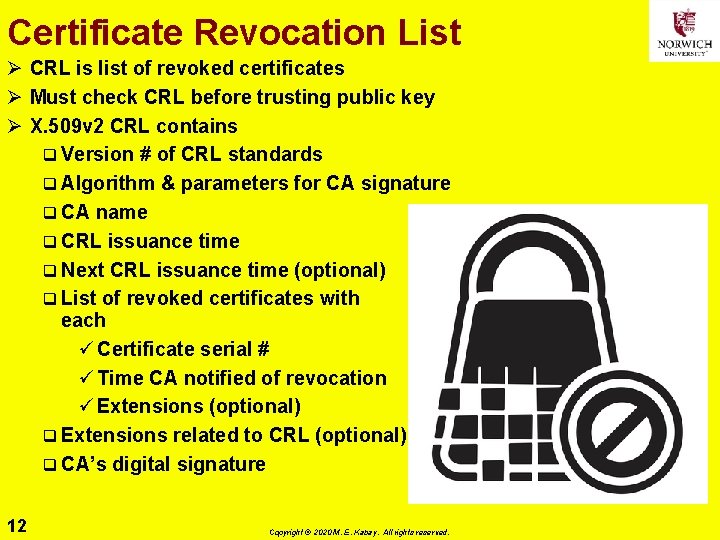
Certificate Revocation List Ø CRL is list of revoked certificates Ø Must check CRL before trusting public key Ø X. 509 v 2 CRL contains q Version # of CRL standards q Algorithm & parameters for CA signature q CA name q CRL issuance time q Next CRL issuance time (optional) q List of revoked certificates with each ü Certificate serial # ü Time CA notified of revocation ü Extensions (optional) q Extensions related to CRL (optional) q CA’s digital signature 12 Copyright © 2020 M. E. Kabay. All rights reserved.

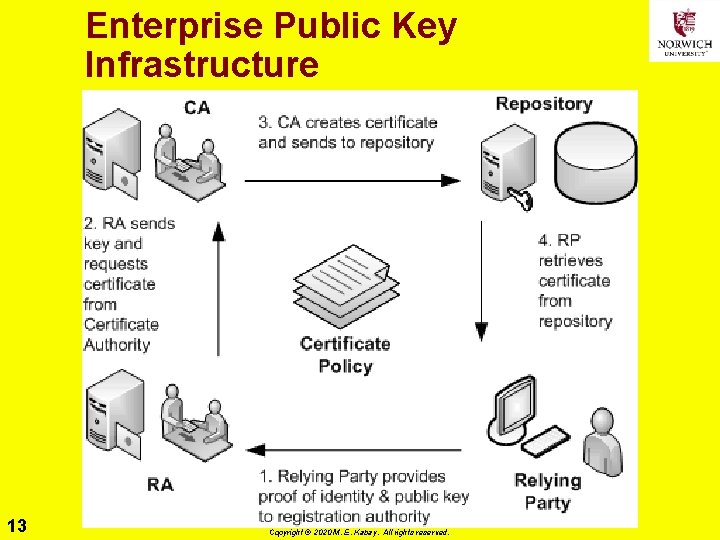
Enterprise Public Key Infrastructure 13 Copyright © 2020 M. E. Kabay. All rights reserved.

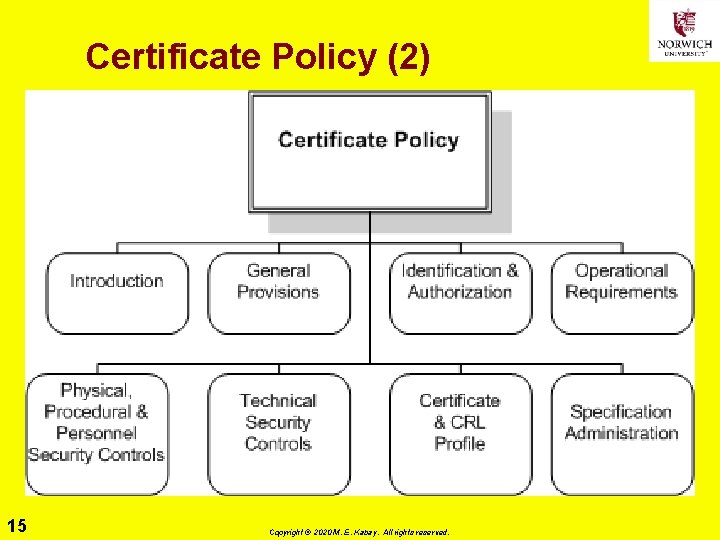
Certificate Policy (1) Ø Private keys must be q. Kept confidential q. Used only by owners of keys Ø Trust anchors’ public key integrity must be assured Ø Initial authentication of subscriber q. Must be strong q. Must prevent identity theft at time of certificate creation Ø CA & RA (Registration Authority) computer systems must be protected against tampering Ø Requirements for level of trust must be defined 14 Copyright © 2020 M. E. Kabay. All rights reserved.

Certificate Policy (2) 15 Copyright © 2020 M. E. Kabay. All rights reserved.

Global PKI ØLevels of Trust ØProofing ØTrusted Paths ØChoosing a PKI Architecture ØCross-Certification ØPKI Interoperability 16 Copyright © 2020 M. E. Kabay. All rights reserved.

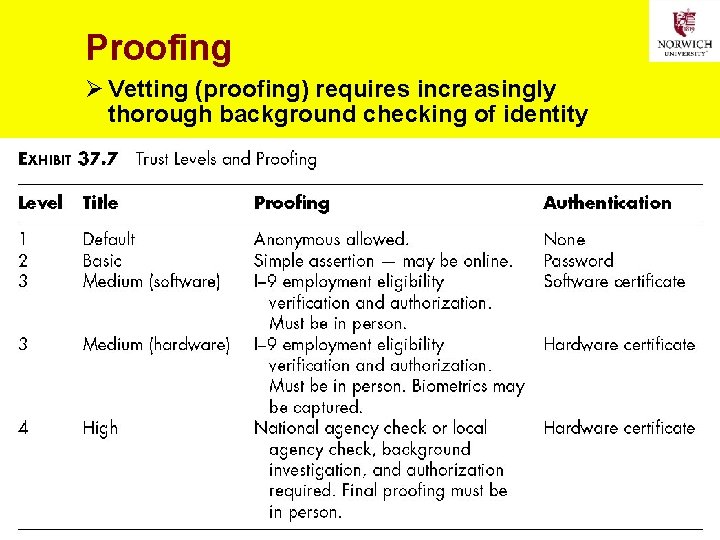
Levels of Trust Ø OMB M 04 -04 § 2. 1 basic levels of trust: q. Level 1: Little or no confidence in asserted identity’s validity q. Level 2: Some confidence q. Level 3: High confidence q. Level 4: Very high confidence 17 Copyright © 2020 M. E. Kabay. All rights reserved.

Proofing Ø Vetting (proofing) requires increasingly thorough background checking of identity 18 Copyright © 2020 M. E. Kabay. All rights reserved.

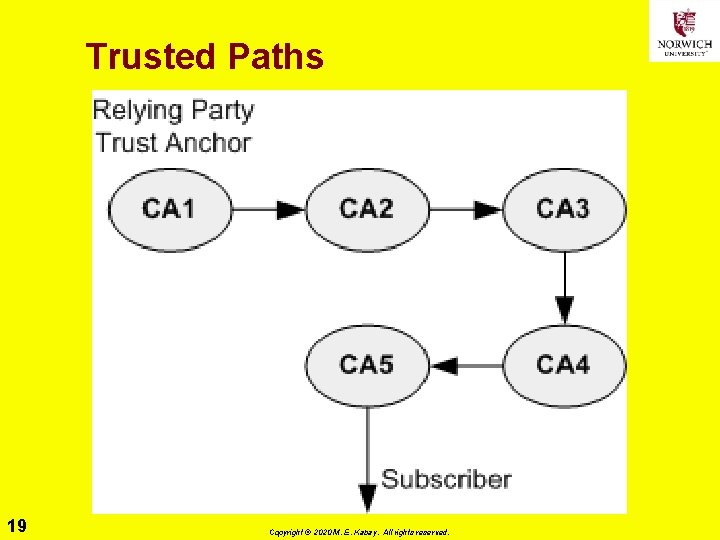
Trusted Paths 19 Copyright © 2020 M. E. Kabay. All rights reserved.

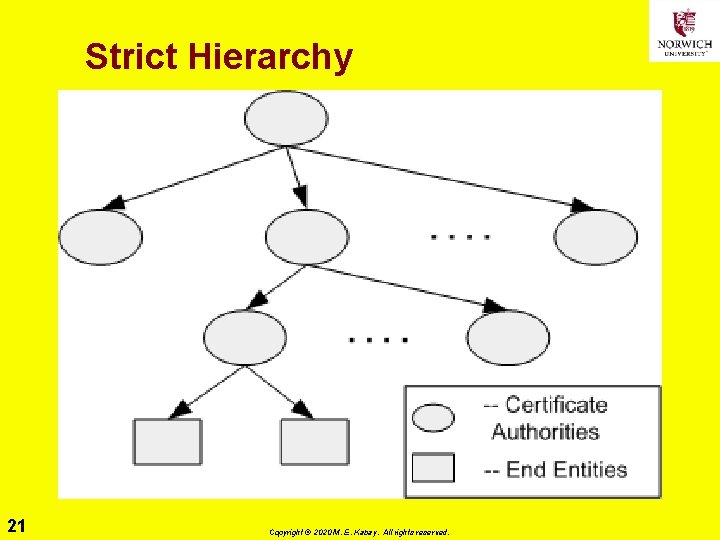
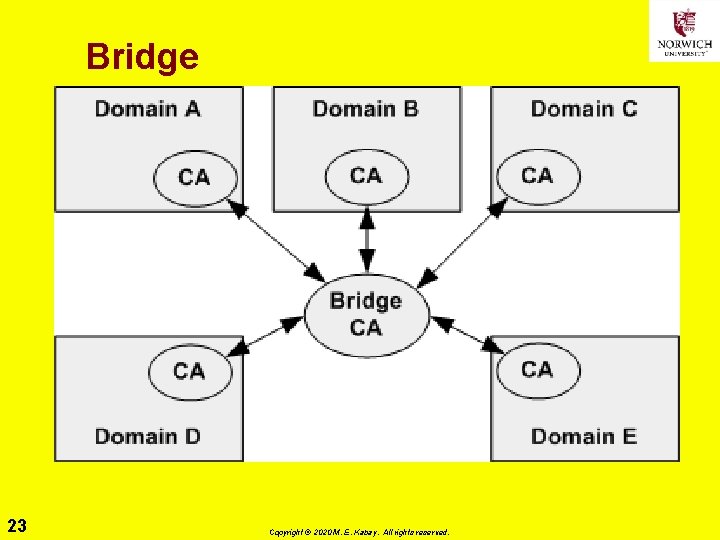
Choosing a PKI Architecture ØStrict Hierarchy ØBridge ØMultiple Trust Anchors ØMesh (Anarchy, Web) ØMaking a Choice 20 Copyright © 2020 M. E. Kabay. All rights reserved.

Strict Hierarchy 21 Copyright © 2020 M. E. Kabay. All rights reserved.

Hierarchy Ø Strict hierarchy requires public key of common ancestor as trust anchor q. Thus single root is trust anchor Ø Nonstrict hierarchy allows any CA to be trust anchor q. Usually local CA becomes trust anchor q. Local CA is CA that issued certificate to a relying party 22 Copyright © 2020 M. E. Kabay. All rights reserved.

Bridge 23 Copyright © 2020 M. E. Kabay. All rights reserved.

Multiple Trust Anchors Ø Relying party obtains public keys of many CAs q. Must use secure method q. Each key becomes a trust anchor Ø Helpful for situations where CAs cannot cross -certify each other 24 Copyright © 2020 M. E. Kabay. All rights reserved.

Mesh (Anarchy, Web) ØWeb of trust ØAny CA can trust any other ØOriginal concept underlying PGP ØNot scalable (WHY NOT? ) 25 Copyright © 2020 M. E. Kabay. All rights reserved.

Making a Choice Ø Factors q. Management culture q. Organizational politics q. Certification path size q. Subscriber population distribution q. Revocation information Ø Often end up with multiple CAs 26 Copyright © 2020 M. E. Kabay. All rights reserved.

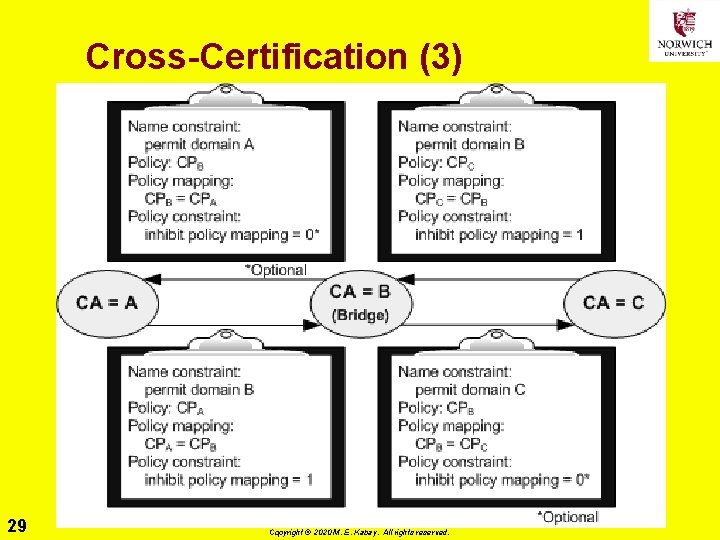
Cross-Certification (1) Ø Simplest case: q. Two CAs grant the other a certificate Ø Problems q. Incompatible PKI products q. Incompatible certification policies üMust review policies üNeed equivalent, not identical policies q. Use name constraints extension in X. 509 v 3 certificates üTrust each others’ domain names 27 Copyright © 2020 M. E. Kabay. All rights reserved.

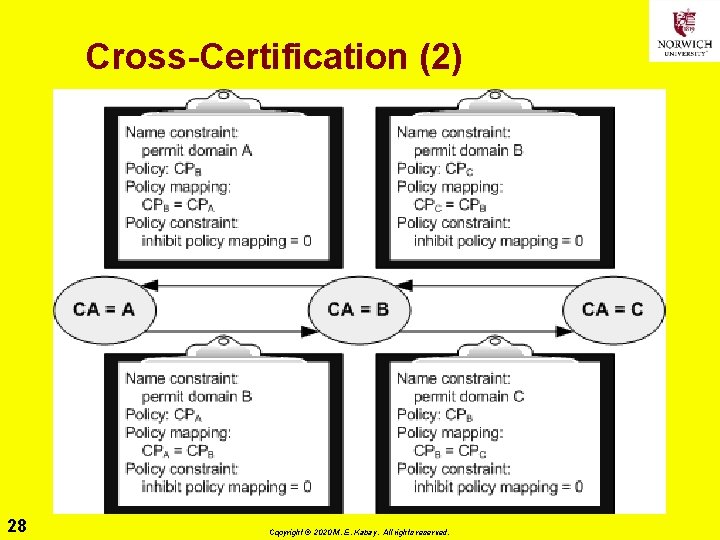
Cross-Certification (2) 28 Copyright © 2020 M. E. Kabay. All rights reserved.

Cross-Certification (3) 29 Copyright © 2020 M. E. Kabay. All rights reserved.

PKI Interoperability Factors Ø Trust Path Ø Cryptographic Algorithms Ø Certificate & CRL Formats Ø Certificate & CRL Dissemination Ø Certificate Policies Ø Names 30 Copyright © 2020 M. E. Kabay. All rights reserved.

Forms of Revocation Ø Types of Revocation-Notification Mechanisms Ø Certificate Revocation Lists & Variants Ø Server-Based Revocation Protocols Ø Summary of Recommendations 31 Copyright © 2020 M. E. Kabay. All rights reserved.

Types of Revocation-Notification Mechanisms Ø Concerns about CRLs have led to variations for checking validity of certificates Ø Online Certificate Status Protocol (OCSP) q. RFC 2560 Ø Directory-based verification & revocation Ø B-tree revocation lists 32 Copyright © 2020 M. E. Kabay. All rights reserved.

Certificate Revocation Lists & Variants Ø Most versatile, effective & recommended Ø Variations q. Full & complete CRL (rare) üAll certificates, revoked and valid üMost CRLs have only recent revocations q. Authority revocation list (ARL) – usually short üRevocations only for CAs üDon’t use X. 509 v 1 ARL – only X. 509 v 2, which distinguishes between CRL & ARL q. Distribution-point CRL: allows partitions for shorter lists q. Delta CRL: changes only since last CRL 33 Copyright © 2020 M. E. Kabay. All rights reserved.

Server-Based Revocation Protocols Ø Servers provide revocation info; e. g. , q On-Line Certificate Status Protocol (OCSP) q Simple Certificate Validation Protocol (SCVP) Ø Flaws q Need to secure channel to server q Computationally intensive digital signature generation makes system difficult to scale q Need trusted servers Ø Useful when need to q Have thinnest possible PKI clients q Generate revenue for CA services q Check changing credentials q Update changing credentials 34 Copyright © 2020 M. E. Kabay. All rights reserved.

Summary of Recommendations for CRLs Ø Use combination of Ø CRLs Ø Replication of CA directory entry for fast access Ø ARLs & their consolidation Ø Consolidation of reason-codes of key compromise in a domain q Use Distribution Point extension q Issue CRL frequently Ø Partition routine revocation info using Distribution Point CRLs if CRLs become too large Ø Store plaintext CRLs for fast searching Ø Eliminate private information to eliminate need for authentication when searching CRLs 35 Copyright © 2020 M. E. Kabay. All rights reserved.

Recommendations 36 Copyright © 2020 M. E. Kabay. All rights reserved.

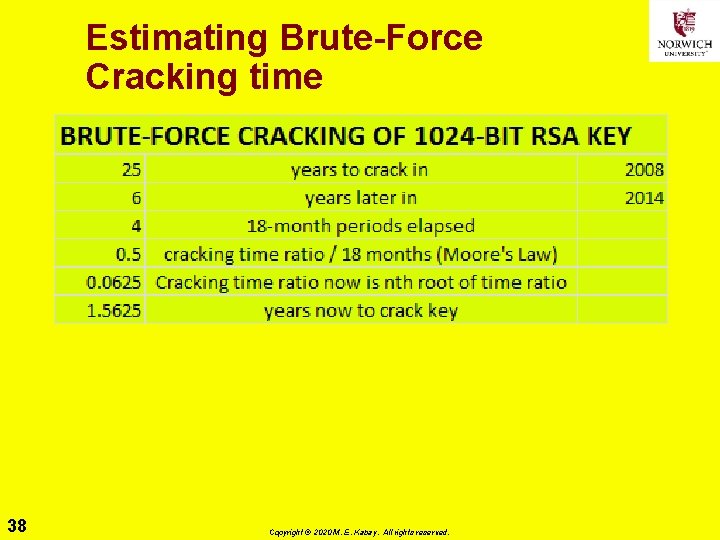
Rekey Ø Public key certificates eventually expire q. Thus need new PK certificates Ø Don’t use PKs longer than estimated time for brute-force cryptanalysis q. Cryptanalysis threat period q. Shortens all the time as computational power increases Ø Current estimates q 1024 bit RSA key → 25 years in 2009 & 1. 5 now Why? q. Therefore worthwhile recertifying keys üReduce number of keys necessary to access or validate older files/messages 37 Copyright © 2020 M. E. Kabay. All rights reserved.

Estimating Brute-Force Cracking time 38 Copyright © 2020 M. E. Kabay. All rights reserved.

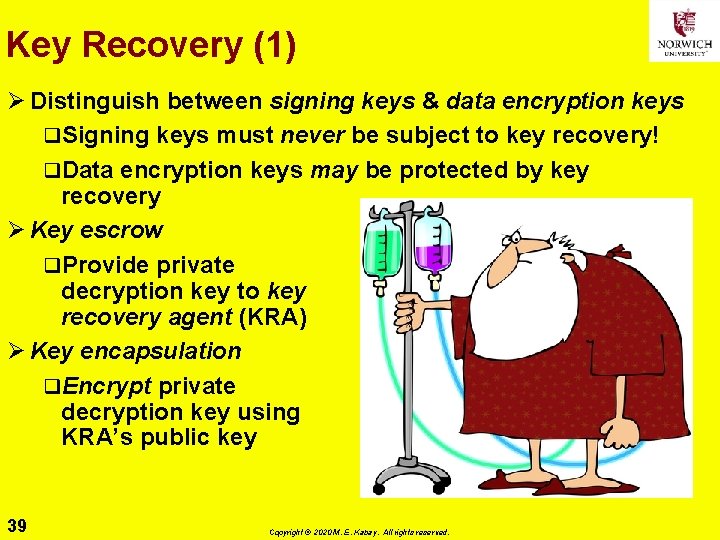
Key Recovery (1) Ø Distinguish between signing keys & data encryption keys q. Signing keys must never be subject to key recovery! q. Data encryption keys may be protected by key recovery Ø Key escrow q. Provide private decryption key to key recovery agent (KRA) Ø Key encapsulation q. Encrypt private decryption key using KRA’s public key 39 Copyright © 2020 M. E. Kabay. All rights reserved.

Key Recovery (2) Ø Avoiding giving KRA control Ø May not want KRA to have unfettered access to decryption key Ø So can q. Superencrypt üEncrypt using 2 keys üRequires collaboration to get key q. Split the key: Shamir’s n out of m rule üSend parts of key to m recipients üRequire at least n recipients to collaborate in restoring key 40 Copyright © 2020 M. E. Kabay. All rights reserved.

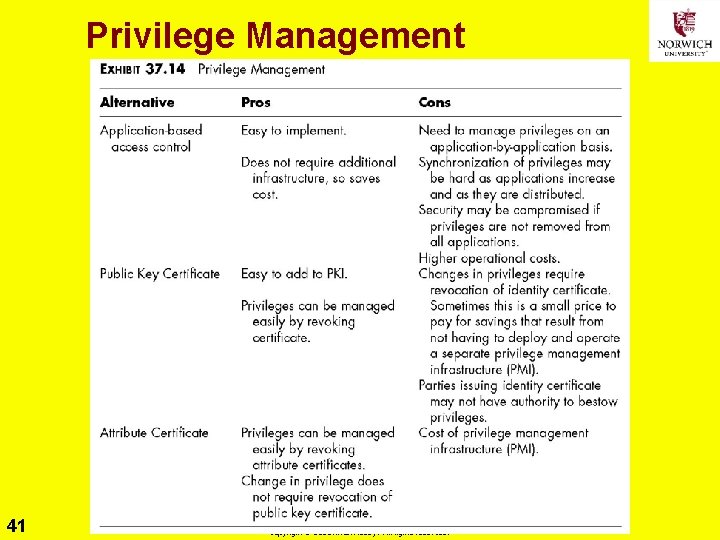
Privilege Management 41 Copyright © 2020 M. E. Kabay. All rights reserved.

Trusted Archival Services & Trusted Time Stamps Ø PKI does not prevent alteration or spoofing q. Merely detects them Ø Could also challenge digital signature after expiry of cryptanalysis threat period Ø But can use trusted archival services q. Need to provide storage of signed materials q. Trustworthy assurance of error-free transcription from medium to medium over time as media degrade & technologies change q. Can add functions of trusted time stamps 42 Copyright © 2020 M. E. Kabay. All rights reserved.

Cost of PKI Ø Compare costs of PKI with costs of not having PKI! q. Scalability is key factor: n vs n 2 keys Ø Consider consequences of untrusted digital communications q. Continued dependence on trust M. E. Kabay’s question sent in 2001 to Norwich University authorities who resisted digital signatures on documents sent by e-mail: How is depending on pigment smeared through a hole in the end of a stick onto compressed fibers from dead plants supposed to engender more trust in the authenticity and integrity of a document than cryptographically sound digital signatures? 43 Copyright © 2020 M. E. Kabay. All rights reserved.

Prof Kabay’s Notes on HR v IT for CA Ø IT q. Can support software for issuing and revoking certificates q. But have no information about new hires, changes of position, authorization as CAs, deauthorization or firing Ø HR q. Equipped to handle all employee-related issues q. Issuing/revoking certificates run by software q. Therefore appropriate CAs 44 Copyright © 2020 M. E. Kabay. All rights reserved.

Now go and study 45 Copyright © 2020 M. E. Kabay. All rights reserved.