PKI Symmetric Key Encryption System PKI Forum Dec













- Slides: 19

PKI & Symmetric Key Encryption System PKI Forum Dec. 5 th. , 2000

Agenda n n n E-Sign legislation effective Oct. 1, 2000 Implication of the legislation and what organization (Wells Fargo) needs to protect (and How) in order to mitigate risks and liabilities System we have implemented (since 1997) to mitigate risks & deployment status System we are undertaking today to further reduce risks & deployment status Future Plans Q&A

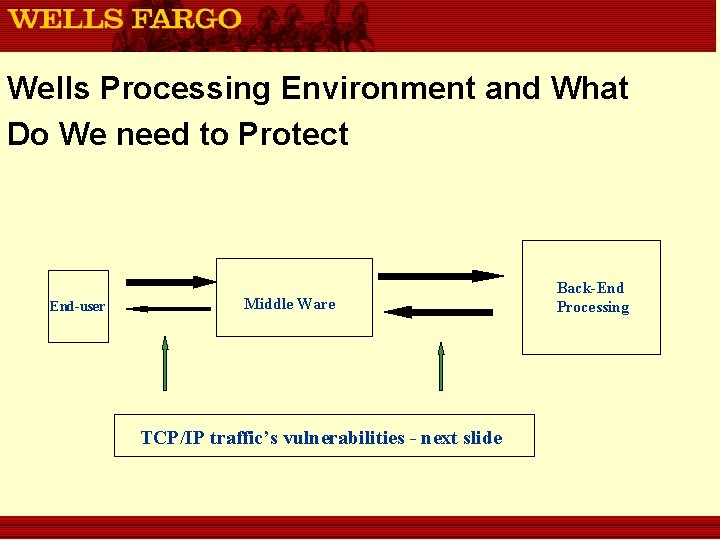
Wells Processing Environment and What Do We need to Protect End-user Middle Ware TCP/IP traffic’s vulnerabilities - next slide Back-End Processing

TCP/IP vulnerabilities n n n Lack of Authentication Lack of Confidentiality Lack of Integrity Check Subject to Re-Play Attack Lack of Non-Repudiation

How does Wells Fargo mitigate risks

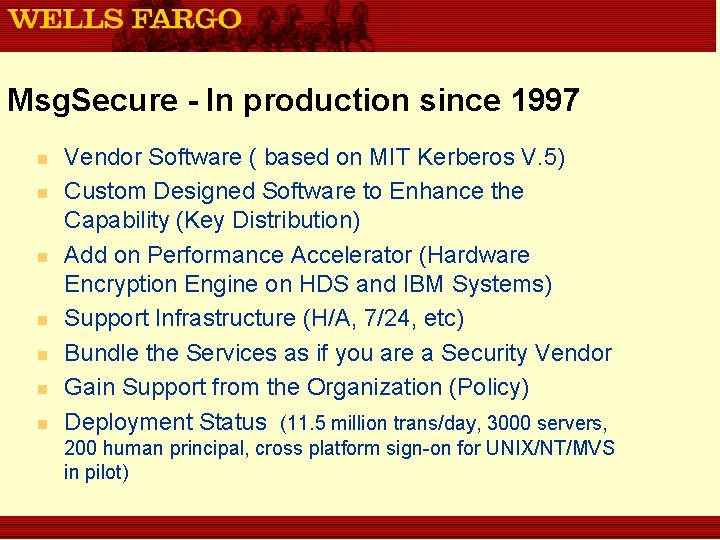
Msg. Secure - In production since 1997 n n n n Vendor Software ( based on MIT Kerberos V. 5) Custom Designed Software to Enhance the Capability (Key Distribution) Add on Performance Accelerator (Hardware Encryption Engine on HDS and IBM Systems) Support Infrastructure (H/A, 7/24, etc) Bundle the Services as if you are a Security Vendor Gain Support from the Organization (Policy) Deployment Status (11. 5 million trans/day, 3000 servers, 200 human principal, cross platform sign-on for UNIX/NT/MVS in pilot)

System we are undertaking today. Public Key Infrastructure (PKI) n n n n Organizational Commitment Define Trust Model Project Organization and Responsibilities Physical Environment Certificate Practice Statement/Policies Root Key Creation Deployment Strategy & Status Future Opportunities within Wells Fargo

Organizational Commitment n n A project truly requires the support of all levels within the organization Business need vs technology Industry analysis shows 20% of effort relies on technology and 80% on buy-in and support from others Requires active participation from legal, enterprise architecture, HR, Audit, Network Engineering, Business Proponent, Security Administration, Security Consulting, Physical Security, Corporate Property and other support organizations.

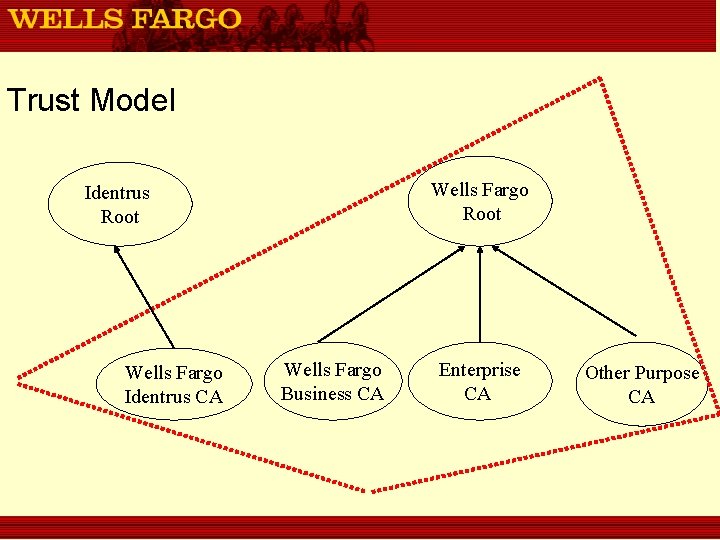
Trust Model Wells Fargo Root Identrus Root Wells Fargo Identrus CA Wells Fargo Business CA Enterprise CA Other Purpose CA

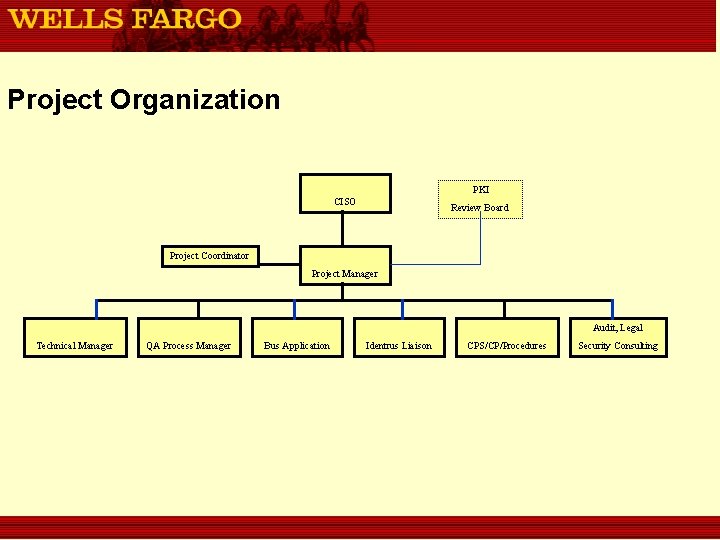
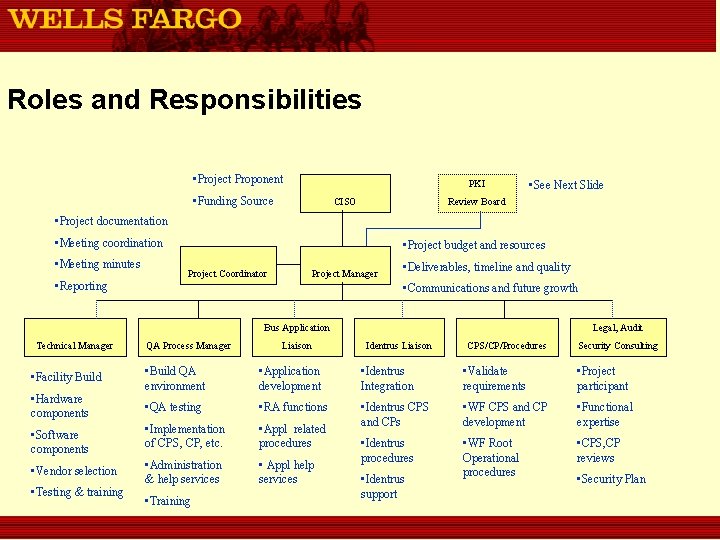
Project Organization PKI CISO Review Board Project Coordinator Project Manager Audit, Legal Technical Manager QA Process Manager Bus Application Identrus Liaison CPS/CP/Procedures Security Consulting

Roles and Responsibilities • Project Proponent PKI • Funding Source CISO • See Next Slide Review Board • Project documentation • Meeting coordination • Meeting minutes • Reporting • Project budget and resources Project Coordinator Project Manager • Deliverables, timeline and quality • Communications and future growth Bus Application Technical Manager QA Process Manager Liaison Legal, Audit Identrus Liaison CPS/CP/Procedures Security Consulting • Build QA environment • Application development • Identrus Integration • Validate requirements • Project participant • QA testing • RA functions • Software components • Implementation of CPS, CP, etc. • Appl related procedures • Identrus CPS and CPs • WF CPS and CP development • Functional expertise • Vendor selection • Administration & help services • Appl help services • Identrus procedures • WF Root Operational procedures • CPS, CP reviews • Facility Build • Hardware components • Testing & training • Training • Identrus support • Security Plan

PKI Review Board Objective A 9 member board to provide the oversight of Wells Fargo PKI practice. Responsibilities n n n Review and approve Certificate Practice Statement and Policies Review and approve on-going changes to CPS and CPs Review and approve Registration Authority and level of Authentication Board Members CISO PKI Manager Network Engineering 2 Business Unit Representatives Corporate legal Corporate HR Internal Audit CTO - Application Development

Physical Environment n n n Site Selection Environment For Housing the Root Key and Master CA/RA Level of Security Requirements including the utilization of Token and multiple Biometrics devices Dual Access Control Camera, Alarm, Automated logging devices

Certificate Practice Statement (CPS) and Policies (CP) n n n A set of agreed upon rules to guide the usage of Digital Certificates CPS covers the life-cycle of the certificates and the associated process/procedures CP address the applicability, usability and the community boundary specific to that certificate True cooperative effort in the development process, involves all stakeholders in early stage An item that could impact production schedule

Root Key Generation n n n Multi-day efforts Plan step by step script Internal, external and specialized personnel Conduct multiple dry runs Expert staff on-site Record and log all tasks and deviations Secure storage of key parts and all records

Deployment Strategy n n n n Pilot with low volume, low risk application Choose simple RA method Gain quick Successes and users confidence Support infrastructure need to be in place to handle the growth Back Up Facility and fail-over is fully functional Market the product - capabilities and benefits Educate the users at large

Deployment Status n n n n Secured physical environment completed in Oct. 2000 Performed Root key Generation in Oct. 2000 Performed Business Sub-Master Generation Nov. , 2000 Enabling first B-to-B application Dec. , 2000 Perform Identrus Sub-Master Generation Feb. , 2001 Enabling first Identrus application Feb. , 2001 Perform Enterprise Sub-Master Generation Mar. , 2001 Enabling enterprise application Mar. , 2001

Future Opportunities n n n Enterprise CA supporting end user authentication and secured email Integrate to support Msg. Secure Other e-business related initiatives Support Wireless and Appliance related applications Public Use of Digital-Certificates Others

Questions? ? n Thanks for your time