Network Authentication with PKI EDUCAUSEDartmouth PKI Summit July








- Slides: 22

Network Authentication with PKI EDUCAUSE/Dartmouth PKI Summit July 27, 2005 Jim Jokl University of Virginia 1

Background: UVa Wireless LAN Project p Deploy campus-wide Wireless LAN (WLAN) n n p Support multiple applications n n p Initial focus on student areas Later emphasis on faculty/staff areas Focus on standard applications: Email, Web, login, file transfer, etc Don’t focus on applications such as video Provide security n Wireless really is different in this regard 2

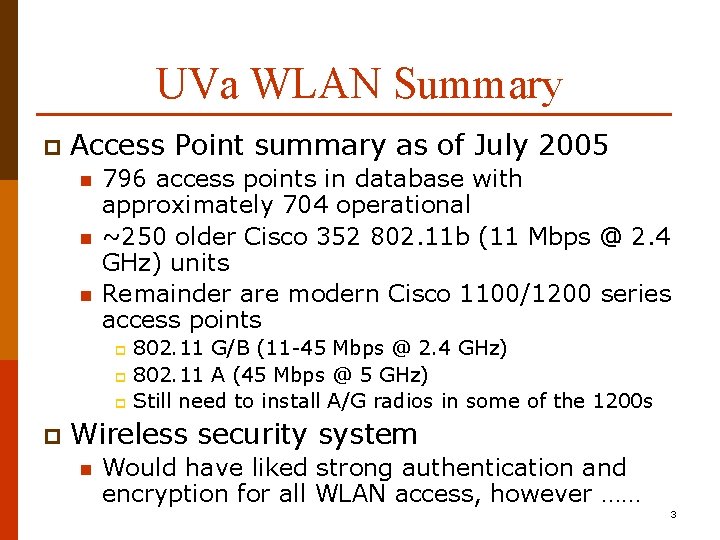
UVa WLAN Summary p Access Point summary as of July 2005 n n n 796 access points in database with approximately 704 operational ~250 older Cisco 352 802. 11 b (11 Mbps @ 2. 4 GHz) units Remainder are modern Cisco 1100/1200 series access points 802. 11 G/B (11 -45 Mbps @ 2. 4 GHz) p 802. 11 A (45 Mbps @ 5 GHz) p Still need to install A/G radios in some of the 1200 s p p Wireless security system n Would have liked strong authentication and encryption for all WLAN access, however …… 3

Wireless Security Have to support “other” devices 4

Initial Wireless Security System p MAC address validation n p Users register the hardware address of their wireless adapter Provisions for anyone affiliated with the university to register cards for guests Supports “random” devices Secured wireless via Cisco LEAP n n n Password-based authentication Dynamic symmetric cipher keys Had expected this technology to be widely implemented by vendors 5

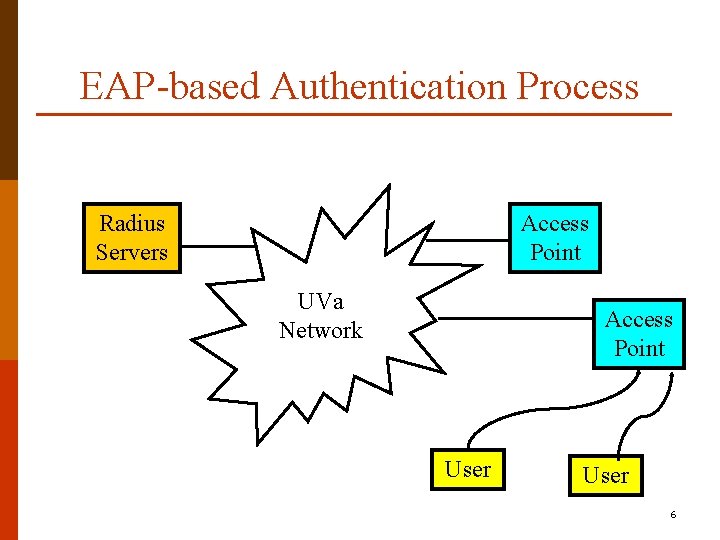
EAP-based Authentication Process Radius Servers Access Point UVa Network Access Point User 6

Authentication Transition Combination of LEAP and MAC registration was OK for a couple of years p However p n n n LEAP never became mainstream and generally required a Cisco wireless card and software installation We had anticipated native LEAP support with Windows XP Final straw was a reported security vulnerability with the LEAP protocol 7

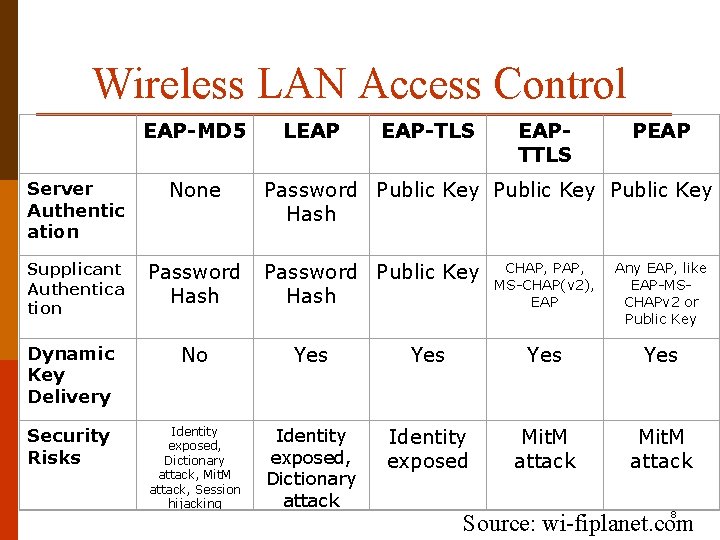
Wireless LAN Access Control EAP-MD 5 Server Authentic ation None Supplicant Authentica tion Password Hash LEAP EAP-TLS EAPTTLS PEAP Password Public Key Hash Password Public Key Hash CHAP, PAP, MS-CHAP(v 2), EAP Any EAP, like EAP-MSCHAPv 2 or Public Key Dynamic Key Delivery No Yes Yes Security Risks Identity exposed, Dictionary attack, Mit. M attack, Session hijacking Identity exposed, Dictionary attack Identity exposed Mit. M attack 8 Source: wi-fiplanet. com

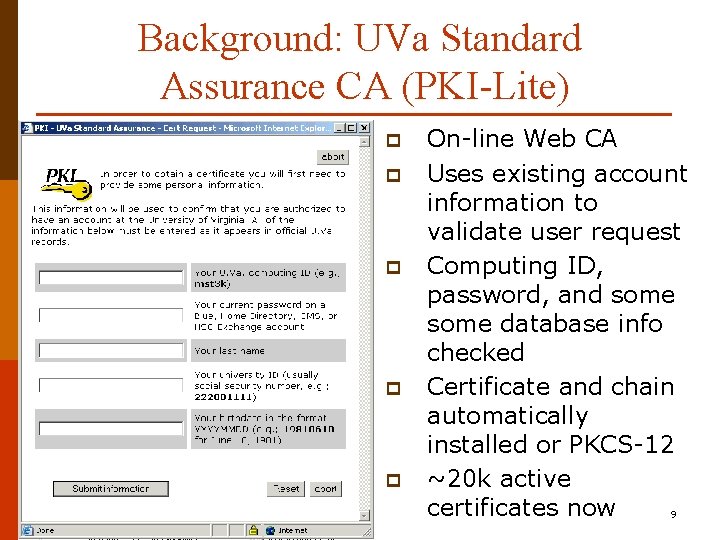
Background: UVa Standard Assurance CA (PKI-Lite) p p p On-line Web CA Uses existing account information to validate user request Computing ID, password, and some database info checked Certificate and chain automatically installed or PKCS-12 ~20 k active certificates now 9

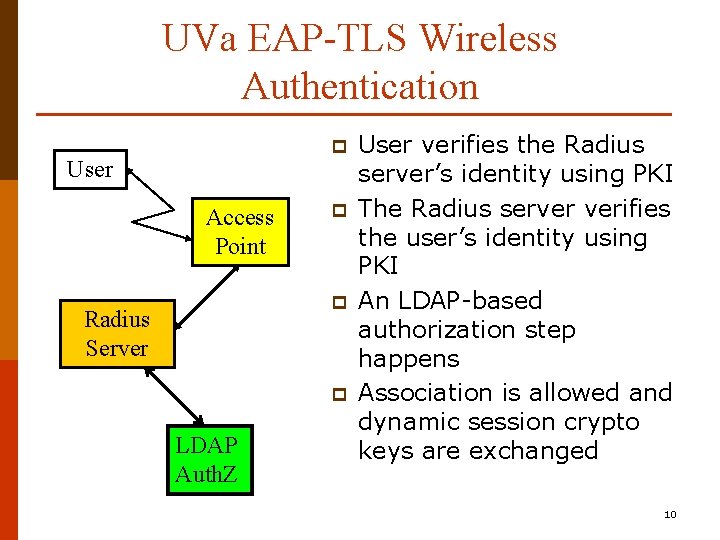
UVa EAP-TLS Wireless Authentication p User Access Point p p Radius Server p LDAP Auth. Z User verifies the Radius server’s identity using PKI The Radius server verifies the user’s identity using PKI An LDAP-based authorization step happens Association is allowed and dynamic session crypto keys are exchanged 10

OS Support for EAP-TLS p Operating System Support n n n p Windows XP, Windows 2000 SP-4* Mac. OS (10. 3. 3) 3 rd party software available Very easy to use n n n No account management, passwords, etc Login to your workstation and secure wireless just works Auth. Z step will make it easier to keep hacked machines off of the WLAN 11

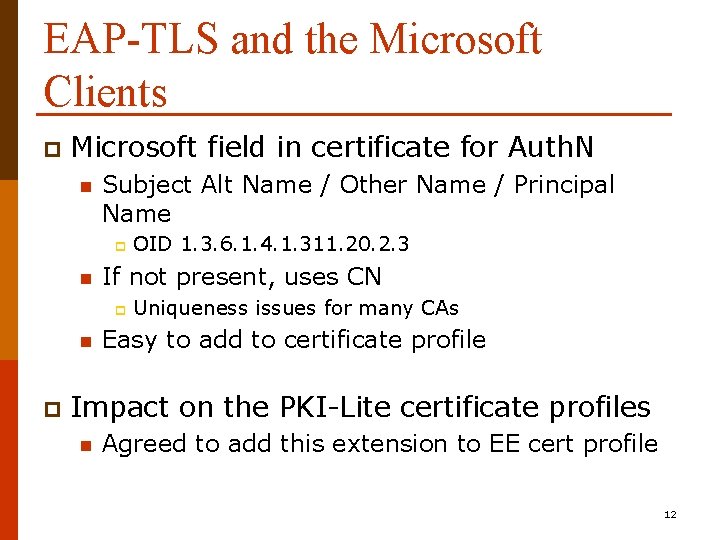
EAP-TLS and the Microsoft Clients p Microsoft field in certificate for Auth. N n Subject Alt Name / Other Name / Principal Name p n If not present, uses CN p n p OID 1. 3. 6. 1. 4. 1. 311. 20. 2. 3 Uniqueness issues for many CAs Easy to add to certificate profile Impact on the PKI-Lite certificate profiles n Agreed to add this extension to EE cert profile 12

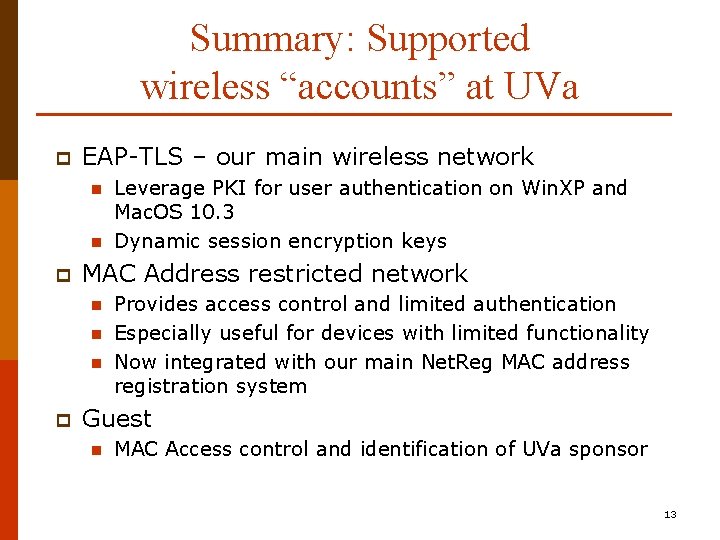
Summary: Supported wireless “accounts” at UVa p EAP-TLS – our main wireless network n n p MAC Address restricted network n n n p Leverage PKI for user authentication on Win. XP and Mac. OS 10. 3 Dynamic session encryption keys Provides access control and limited authentication Especially useful for devices with limited functionality Now integrated with our main Net. Reg MAC address registration system Guest n MAC Access control and identification of UVa sponsor 13

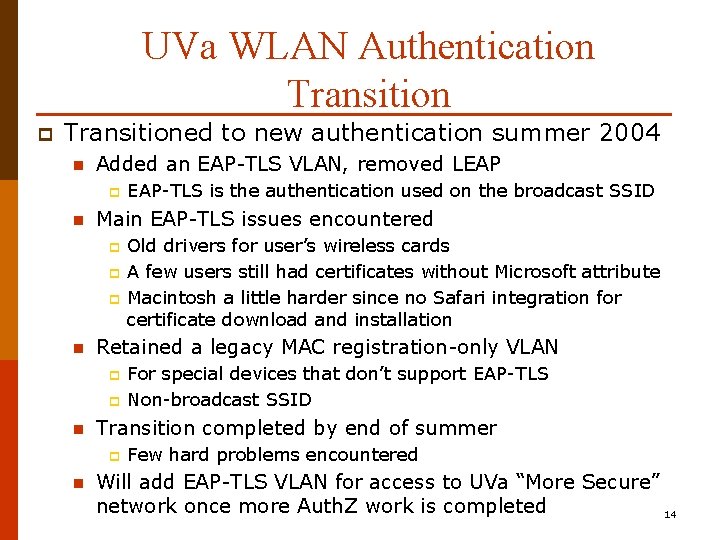
UVa WLAN Authentication Transition p Transitioned to new authentication summer 2004 n Added an EAP-TLS VLAN, removed LEAP p n Main EAP-TLS issues encountered p p p n p For special devices that don’t support EAP-TLS Non-broadcast SSID Transition completed by end of summer p n Old drivers for user’s wireless cards A few users still had certificates without Microsoft attribute Macintosh a little harder since no Safari integration for certificate download and installation Retained a legacy MAC registration-only VLAN p n EAP-TLS is the authentication used on the broadcast SSID Few hard problems encountered Will add EAP-TLS VLAN for access to UVa “More Secure” network once more Auth. Z work is completed 14

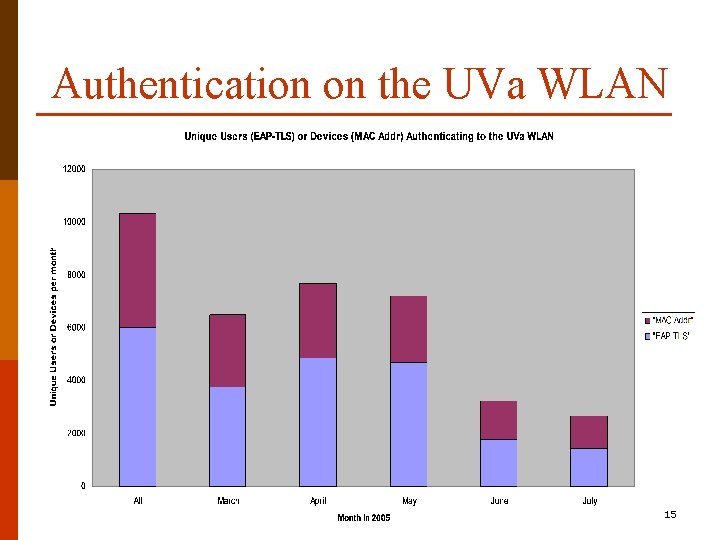
Authentication on the UVa WLAN 15

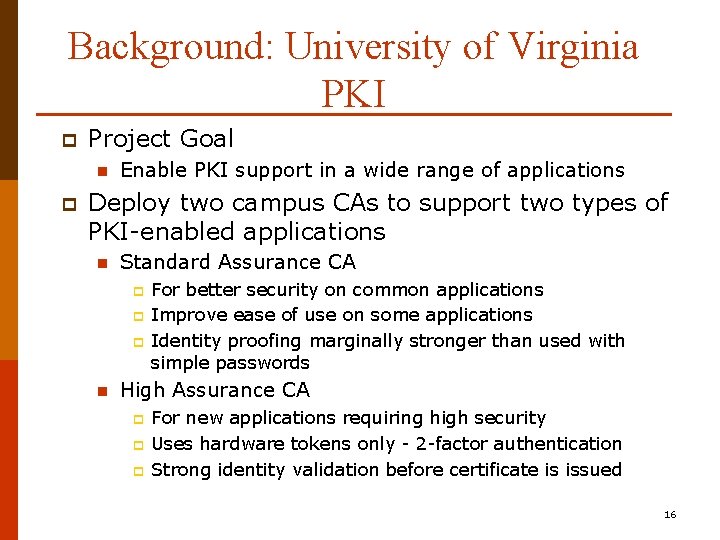
Background: University of Virginia PKI p Project Goal n p Enable PKI support in a wide range of applications Deploy two campus CAs to support two types of PKI-enabled applications n Standard Assurance CA p p p n For better security on common applications Improve ease of use on some applications Identity proofing marginally stronger than used with simple passwords High Assurance CA p p p For new applications requiring high security Uses hardware tokens only - 2 -factor authentication Strong identity validation before certificate is issued 16

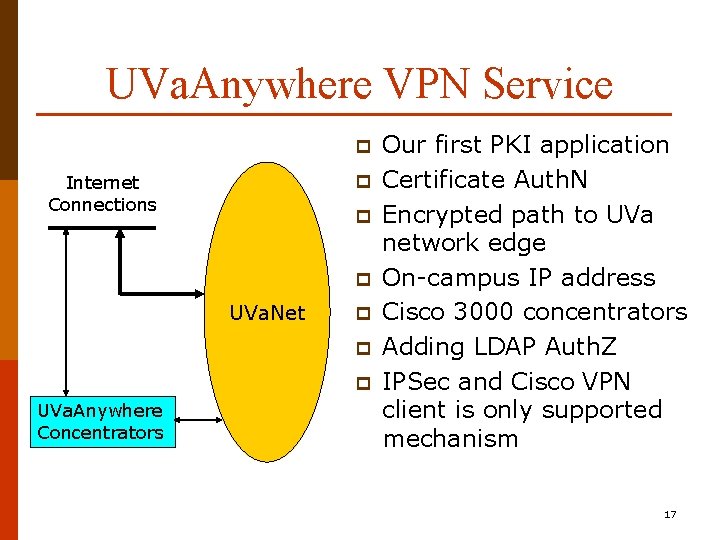
UVa. Anywhere VPN Service p p Internet Connections p p UVa. Net p p p UVa. Anywhere Concentrators Our first PKI application Certificate Auth. N Encrypted path to UVa network edge On-campus IP address Cisco 3000 concentrators Adding LDAP Auth. Z IPSec and Cisco VPN client is only supported mechanism 17

UVa. Anywhere-Lite p Just added new SSL VPN service n n n For web applications only Uses existing Cisco 3000 concentrators PKI for authentication Uses LDAP for authorization Web VPN provides convenient pop-up box for navigation p Customized with library and department pages that point to their web resources 18

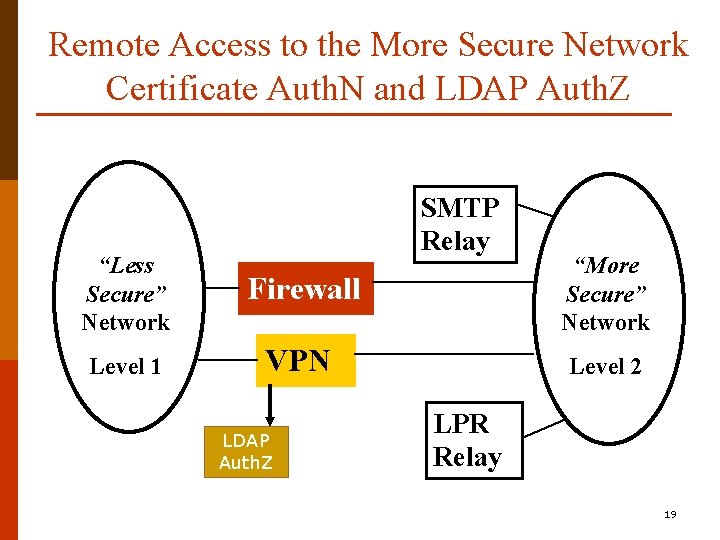
Remote Access to the More Secure Network Certificate Auth. N and LDAP Auth. Z SMTP Relay “Less Secure” Network Firewall “More Secure” Network Level 1 VPN Level 2 LDAP Auth. Z LPR Relay 19

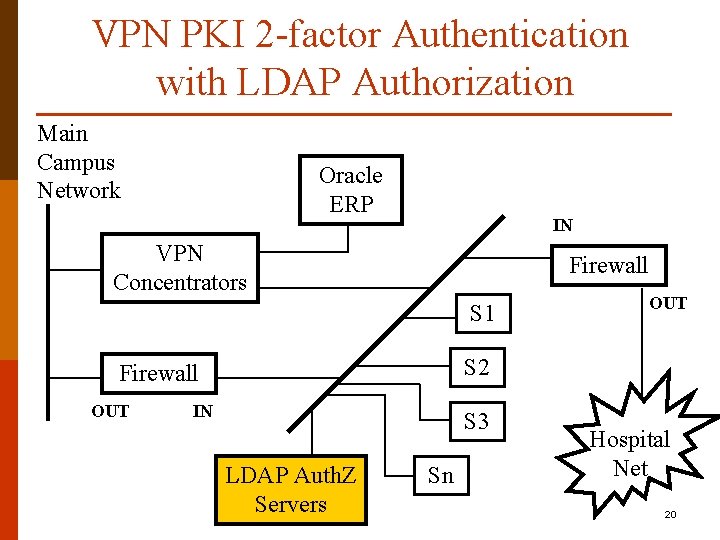
VPN PKI 2 -factor Authentication with LDAP Authorization Main Campus Network Oracle ERP IN VPN Concentrators Firewall S 1 S 2 Firewall OUT IN S 3 LDAP Auth. Z Servers Sn Hospital Net 20

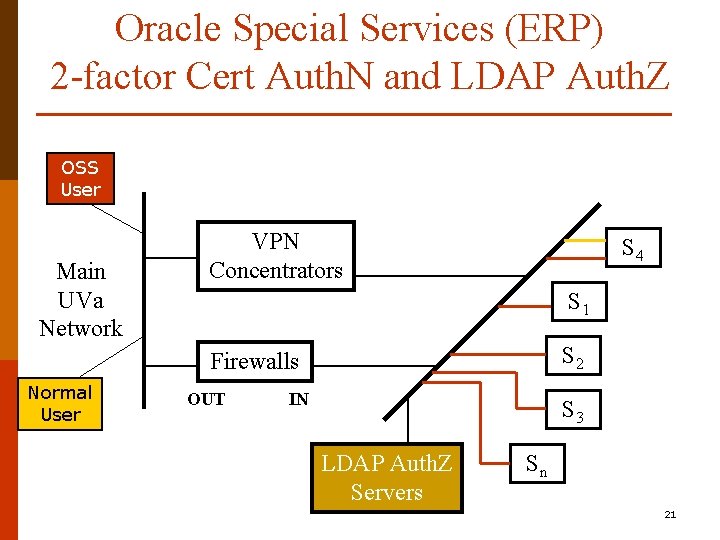
Oracle Special Services (ERP) 2 -factor Cert Auth. N and LDAP Auth. Z OSS User Main UVa Network VPN Concentrators S 4 S 1 S 2 Firewalls Normal User OUT IN S 3 LDAP Auth. Z Servers Sn 21

Some References p UVa Wireless LAN site n p UVa PKI Site n p http: //www. itc. virginia. edu/desktop/pki/ UVa VPN Sites n n p http: //www. itc. virginia. edu/wireless/ http: //www. itc. virginia. edu/desktop/vpn http: //www. itc. virginia. edu/vpn/webvpn HEPKI-TAG PKI-Lite n http: //middleware. internet 2. edu/hepki-tag/ 22
 Message authentication and entity authentication
Message authentication and entity authentication Peer entity authentication
Peer entity authentication Code c
Code c Authentication in cryptography and network security
Authentication in cryptography and network security July 12 1776
July 12 1776 Criciúma ec
Criciúma ec June july august
June july august Slidetodoc.com
Slidetodoc.com Sources nso frenchhowell neill mit technology...
Sources nso frenchhowell neill mit technology... July 26 1953
July 26 1953 Harris burdick pictures uninvited guest
Harris burdick pictures uninvited guest June too soon july stand by
June too soon july stand by July 10 1856
July 10 1856 Sensory language definition
Sensory language definition 2001 july 15
2001 july 15 July 14 1789
July 14 1789 Monday 13th july
Monday 13th july What is the significance of july 4 1776 brainpop
What is the significance of july 4 1776 brainpop July 16 1776
July 16 1776 July 1-4 1863
July 1-4 1863 July 2 1937 amelia earhart
July 2 1937 amelia earhart Ctdssmap payment schedule july 2021
Ctdssmap payment schedule july 2021 Catawba indian nation bingo
Catawba indian nation bingo