DDS PKI and storage of PGP and X
























- Slides: 30

DDS PKI and storage of PGP and X. 509 certificates in LDAP Deployment Bo. F Amsterdam 12. 5. 2000 Peter Gietz Peter. gietz@directory. dfn. de PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS Agenda • • • Why distribute public keys on Server? The classic: X. 509 IETF PKIX LDAP work on X. 509 PGP Keyserver A CA based Infrastructure for NRNs PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS Why distribute public keys on Server? • • Basics of any PKI Encrypt data for somebody without prior contact You don’t have to store all keys yourself Easier distribution of new keys and updates PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS Methods of key publication • Without a third party: • own web page • via FTP file • via finger • With a third party • dedicated key server • Directory PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS PKI and Directory The Burton Group: Network Strategy Report, PKI Architecture, July 1997: (Quoted after: S. Zeber, X. 500 Directory Services and PKI issues, http: //nra. nacosa. nato. int/pki/hdocs/pkiahwg 30/index. htm) “. . . Customers should always consider PKI a directoryenabled set of services and infrastructure. Without directory services, PKI will be exponentially harder to implement and manage. Consequently, customers should’t deploy PKI widely without an accompanying directory plan” PKI and Certs in LDAP Peter Gietz, DFN Directory services

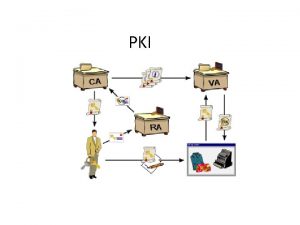
DDS Directory as Key Server • • • Publishing medium for public keys and certificates Gets public keys from user Gets certificates from CA Documents revocation of keys/certificates (CRL) Documents status of a certificate at a specific time PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS X. 509: The classic (1988) • “The Directory: Authentication Framework” • Part of the OSI-Directory standard X. 500 • Defines Data model, e. g. : • user. Certificate; c. ACertificate • cross. Certificate. Pair • certificate. Revocation. List • Defines mechanisms for authentification • Certificate includes DN of the user • Certificate includes DN of the signing CA PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS X. 509 v 3 (1997) • New extension mechanism • Predefined extensions: • • Information about key: identifier, usage, . . . Policy information: certificate policy, . . . User and CA extensions: alternative name, . . . Certification path constraints • Lots of people see X. 509 v 3 as independent from X. 500 • Problem: hypothetical DNs • No proof of uniqueness PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS X. 509 v 4 (2000) • Draft version ready (May 11, 2000) • ftp: //ftp. bull. com/pub/OSIdirectory/ 4 th. Edition. Texts/X. 509_4 th. Edition. Draft. V 2. pdf • Press release: http: //www. itu. int/ITU-T/itu-t_news/ sg 7_x 509_press. htm • Includes verification of certificate chains with CAs from different domains and hierarchies • Enhancements in the area of certificate revocation • New features in attribute certificates (AC) • Defines usage of ACs for access control and authorization PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS Applications of X. 509 certificates • Certificate based security on different levels: • Network Layer: • IPSec (Internet Protocol Security) • Transport Layer: • SSL (Secure Socket Layer) = • TLS (Transport Layer Security) • Application Level: • S/MIME (Secure Multipurpose Internet Mail Extensions) v 3: patent free algorithms, mailing list support • PGP (Pretty Good Privacy), since version 6 PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS IETF WG PKIX • Defines an Internet PKI on basis of X. 509 certificates • Supports the following IETF security protocols: • S/MIME • TLS (=SSL) • IPSec • Status: • 9 RFCs • 21 Internet Drafts • Overview: Arsenault, A. (DOD), Turner, S. (IECA), Internet X. 509 Public Key Infrastructure PKIX Roadmap, <draft-ietfpkix-roadmap-05. txt>, March 2000 PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS PKIX and Certificate profiles • RFC 2459: Housley, R. (Spyrus), Ford, W. (Verisign) et. al. , Internet X. 509 Public Key Infrastructure Certificate and CRL Profile, January 1999 redrafted: <draft-ietf-pkix-new-part 1 -01. txt>, March 2000 defines: • Certificate (X. 509 v 3 standard fields and standard extensions plus one private extension for authority information access, for e. g. validation service) • CRL (X. 509 v 2 standard fields, and standard extensions) • Certificate path validation process, basic and extending PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS PKIX and Attribute Certificate profile • Farrel, S. (Baltimore), Housley, R. (Spyrus), An Internet Attribute Certificate Profile for Authorization, <draft-ietf-pkix-acx 509 prof-03. txt>, May 2000 defines: • Attribute certificate profile for standard fields and extensions • Additional attribute types • Attribute certificate validation • Revocation • Usage for authorization PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS PKIX and Qualified Certificate profile • Santesson, S (Accurata), Polk, W. (NIST), Barzin, P. (Secude), Nystrom, M. (RSA Lab. ), Internet X. 509 Public Key Infrastructure Qualified Certificates p. Profile, <draft-ietf-pkix-qc-03. txt>, February 2000 defines: • • • Qualified Certificate as prescribed by some governmental laws owner is natural person unmistakable identity only non-repudiation as key usage. . . PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS PKIX LDAPv 2 schema • RFC 2587: Boyen, S. (Entrust), Howes, T. (Netscape), Richard, P. (Xcert), Internet X. 509 Public Key Infrastructure LDAPv 2 Schema, June 1999 defines: • Objectclass pki. User with attribute user. Certificate • Objectclass pki. CA with attributes c. ACertificate, certificate. Revocation. List, authority. Revocation. List, cross. Certificate. Pair • Objectclass c. RLDistribution. Point with attributes cn, certificate. Revocation. List, authority. Revocation. List, delta. Revocation. List • Objectclass delta. CRL with attribute delta. Revocation. List PKI and Certs in LDAP Peter Gietz, DFN Directory services

PKIX operational protocols LDAP DDS • LDAPv 2: • RFC 2559: Boyen, S. (Entrust), Howes, T. (Netscape), Richard, P. (Xcert), Internet X. 509 Public Key Infrastructure Operational Protocols - LDAPv 2, April 1999. Defines: • LDAP repository read • LDAP repository search • LDAPv 3: • Chadwick, D. (Univ. Of Salford), Internet X. 509 Public Key Infrastructure Operational Protocols - LDAPv 3 <draft-ietfpkix-ldap-v 3 -01. txt>. [outdated!] Defines: • Which v 3 features are needed in PKIX • attribute. Certificate • certificate matching rules PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS PKIX operational protocols FTP/HTTP • RFC 2585: Housley, R. (Spyrus), Hoffman, P. (IMC), Internet X. 509 Public Key Infrastructure Operational Protocols: FTP and HTTP, May 1999 • defines how to FTP and HTTP to obtain certificates from a repository PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS PKIX and certificate validation SCVP • Malpani, A. (Vali. Cert), Hoffman, P. (VPN Consortium), Simple Certification Verification Protocol (SCVP), <draft-ietf-pkix-scvp-02. txt>, March 2000 • Client can offload certificate validation to a dedicated (trusted) server (validity of certificate and certification path) PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS PKIX and certificate validation OSCP • RFC 2560: Myers, M. (Veri. Sign), Ankney, R. (Cert. Co), et. Al. , X. 509 Internet Public Key Infrastructure Online Certificate Status Protocol - OCSP, June 1999 • determination of current status of a certificate without the use of CRLs • question contains cert id and time • answer contains: “revoked”, “not. Revoked” or “unknown” • Mallam-Baker, P. (Veri. Sign), OCSP Extension, <draftietf-pkix-ocspx-00. txt>, September 1999 • allows client to delegate processing of certificate acceptance functions to a trusted server PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS LDAP work on X. 509: Data model • Greenblatt, B. , LDAP Object Class for Holding Certificate Information, <draft-greenblatt-ldap-certinfoschema-02. txt>, February 2000 • Introduces Objectclass certificate. Type • enables client to retrieve only those certificates that it really wants • contains attributes: type. Name, serial. Number, issuer, validity. Not. Before, validity. Not. After, subject. Public. Key. Info, certificate. Extension, other. Info PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS LDAP work on X. 509: TLS Extensions • Hodges, J. (Oblix), Morgan, RL (Univ. Of Washington), Wahl, M. (Innosoft), LDAP (v 3) Extension for Transport Layer Security, <draft-ietf-ldapext-ldapv 3 -tls-06. txt>, February 2000 • Extended request/response for Start TLS operation PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS LDAP work on X. 509: TLS Usage • Wahl, M. (Innosoft), Alvestrand, H. (Ma. Xware), Hodges, J. , Morgan, RL. (Stanford Univ. ), Authentication Methods for LDAP, <draft-ietf-ldapext-authmeth-04. txt>, June 1999 • Includes (as SHOULD) certificate-based authentication with TLS • Client uses Start TLS operation • Server requests client certificate • Client sends certificate and performs a private key based encryption • Client and server negotiate ciphersuite with encryption algorithm • Server checks validity of certificate and its CA • Client binds with SASL “EXTERNAL” mechanism PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS PGP key server • First only replication of pubring via email • Marc Horrowitz Keyserver (PKSD) • • Started 1995 Own database backend Email and HTTP interface Operational model (add, revoke, etc. ) Net of server Every server has all keys Server synchronisation via email PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS PKSD Statistics • • • 20 synchronising server Almost 1 million keys 1, 05 GB pubring Much more DSS/SH keys than RSA keys Most keys only selfsigned (=islands of trust) PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS PKSD Problems • No distributed system • Permanent server synchronisation causes high bandwith usage • Chaos when one server is down (bouncing emails) • No guarantee that a key is replicated on all server • Not scalable PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS New concepts for PGP key server • PKSD with enhanced backend (Open Keyserver from Highware) • Keyserver based on DNSSec (www. ietf. org/htmlcharter/dnssec-charter. html) • Synchronisation via multicast (G. Baumer, Distributed Server for PGP Keys synchronised by multicast, www. vis. ethz. ch/~baumi/sa/thesis. html) • Keyserver based on LDAP (PGP Certificate Server from NAI) PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS LDAP PGP-Keyserver requirements • Standardizes solution • data model • operational model • Keys searchable by different criteria • Certification path followable • Key status retrievable PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS Process of standardization • 1994 Draft from Roland Hedberg • 1994 proprietary solution in Tübingen • Both models fail to include more than one certificate in a person’s entry • 1998 new initiative by DANTE • DDS and University of Stuttgart take part in the discussion and announce an Internet Draft • Roadmap: Draft in Summer 2000 PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS Status of LDAP PGP key server • • • PGP test server based on LDAP Policy for a service Definition of a data model for PGP Definition of a format for CAs to send certificates Software for storing and retrieving certificates A user can store his key into the server via WWW formular • Model should be enhanced to be sort of PKIX compliant PKI and Certs in LDAP Peter Gietz, DFN Directory services

DDS Discussion • • • A CA based PKI for European NRNs Certificate validation Certificate path validation Where will PCA be? Eurocert Project ICE-CAR Project PKI and Certs in LDAP Peter Gietz, DFN Directory services
 Pgp vs pki
Pgp vs pki Pgp vs x509
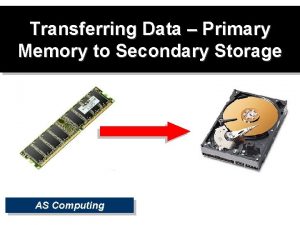
Pgp vs x509 Primary storage vs secondary storage
Primary storage vs secondary storage Primary storage and secondary storage
Primary storage and secondary storage Stream data model
Stream data model Dds utok
Dds utok Dds 9850
Dds 9850 Simulink
Simulink Soabean
Soabean Luis calixto dds
Luis calixto dds Mark costes
Mark costes Dds data distribution service
Dds data distribution service Dds digital display systems
Dds digital display systems Adisimdds
Adisimdds Dds
Dds Dds
Dds Robert grover dds
Robert grover dds Dds 5900
Dds 5900 Sang park dds
Sang park dds James melville dds
James melville dds Rick campbell dds
Rick campbell dds Spelman college
Spelman college Ncidm
Ncidm Dds arduino
Dds arduino Pgp packet structure
Pgp packet structure Pgp message generation and reception
Pgp message generation and reception Pgp in cryptography and network security
Pgp in cryptography and network security Privacy-enhanced mail
Privacy-enhanced mail Uses rigid metallic platters
Uses rigid metallic platters Unified storage vs traditional storage
Unified storage vs traditional storage Pki advantages and disadvantages
Pki advantages and disadvantages