On Homomorphic Encryption and Secure Computation challenge response

![Privacy Homomorphisms [RAD 78] Plaintext space P x 1 x 2 ci Enc(xi) Ciphertext Privacy Homomorphisms [RAD 78] Plaintext space P x 1 x 2 ci Enc(xi) Ciphertext](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-7.jpg)
![More Privacy Homomorphisms o Mult-mod-p [El. Gamal’ 84] o Add-mod-N [Pallier’ 98] o NC More Privacy Homomorphisms o Mult-mod-p [El. Gamal’ 84] o Add-mod-N [Pallier’ 98] o NC](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-8.jpg)
![(x, +)-Homomorphic Encryption, the Gentry Way [G’ 09] Evaluate any function in four “easy” (x, +)-Homomorphic Encryption, the Gentry Way [G’ 09] Evaluate any function in four “easy”](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-12.jpg)

![An Example: Integers mod p (similar to [Regev’ 03]) p N o Code determined An Example: Integers mod p (similar to [Regev’ 03]) p N o Code determined](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-15.jpg)
![Integers Rings [v. DGHV’ 10] o Recall mod-p scheme: ci = qip + 2 Integers Rings [v. DGHV’ 10] o Recall mod-p scheme: ci = qip + 2](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-19.jpg)
![Integers Rings [v. DGHV’ 10] Thm: “Approximate GCD” is hard Enc(0), Enc(1) are indistinguishable Integers Rings [v. DGHV’ 10] Thm: “Approximate GCD” is hard Enc(0), Enc(1) are indistinguishable](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-20.jpg)
![Polynomial Rings [G’ 09] o R = polynomial ring modulo some f(x) ØE. g. Polynomial Rings [G’ 09] o R = polynomial ring modulo some f(x) ØE. g.](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-21.jpg)
![Polynomial Rings [G’ 09] Thm: Bounded-Distance Decoding in ideal lattices is hard Enc(0), Enc(1) Polynomial Rings [G’ 09] Thm: Bounded-Distance Decoding in ideal lattices is hard Enc(0), Enc(1)](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-22.jpg)
![*Doesn’t quite fit the mold Matrix Rings* [GHV’ 10] o R = ring of *Doesn’t quite fit the mold Matrix Rings* [GHV’ 10] o R = ring of](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-23.jpg)
![*Doesn’t quite fit the mold Matrix Rings* [GHV’ 10] Thm: Learning with Errors hard *Doesn’t quite fit the mold Matrix Rings* [GHV’ 10] Thm: Learning with Errors hard](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-24.jpg)
![Step 3: Bootstrapping [G’ 09] o So far, can evaluate low-degree polynomials x 1 Step 3: Bootstrapping [G’ 09] o So far, can evaluate low-degree polynomials x 1](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-25.jpg)
![Step 3: Bootstrapping [G’ 09] o So far, can evaluate low-degree polynomials x 1 Step 3: Bootstrapping [G’ 09] o So far, can evaluate low-degree polynomials x 1](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-26.jpg)
![Step 3: Bootstrapping [G’ 09] o So far, can evaluate low-degree polynomials x 1 Step 3: Bootstrapping [G’ 09] o So far, can evaluate low-degree polynomials x 1](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-27.jpg)
![Step 3: Bootstrapping [G’ 09] o Include in the public key also Encpk(sk) x Step 3: Bootstrapping [G’ 09] o Include in the public key also Encpk(sk) x](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-28.jpg)
![Step 3: Bootstrapping [G’ 09] o Include in the public key also Encpk(sk) x Step 3: Bootstrapping [G’ 09] o Include in the public key also Encpk(sk) x](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-29.jpg)
![Step 4: Everything Else o Cryptosystems from [G’ 09, v. DGHV’ 10] cannot handle Step 4: Everything Else o Cryptosystems from [G’ 09, v. DGHV’ 10] cannot handle](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-30.jpg)
![Two-Message SFE [Yao’ 82, …] Alice(x) (c, s) SFE 1(x) y SFE 3(s, r) Two-Message SFE [Yao’ 82, …] Alice(x) (c, s) SFE 1(x) y SFE 3(s, r)](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-33.jpg)

![A More Complex Setting: i-Hop HE [GHV 10 b] Alice(x) c 0 Enc(x) Bob(f) A More Complex Setting: i-Hop HE [GHV 10 b] Alice(x) c 0 Enc(x) Bob(f)](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-40.jpg)

- Slides: 46

On Homomorphic Encryption and Secure Computation challenge response Shai Halevi IBM|NYU|Columbia Theory Day, May 7, 2010 IBM|NYU|Columbia Theory Day

Computing on Encrypted Data Wouldn’t it be nice to be able to… o Encrypt my data in the cloud o While still allowing the cloud to search/sort/edit/… this data on my behalf o Keeping the data in the cloud in encrypted form Ø Without needing to ship it back and forth to be decrypted May 7, 2010 IBM|NYU|Columbia Theory Day 2

Computing on Encrypted Data Wouldn’t it be nice to be able to… o Encrypt my queries to the cloud o While still allowing the cloud to process them o Cloud returns encrypted answers Ø that I can decrypt May 7, 2010 IBM|NYU|Columbia Theory Day 3

Computing on Encrypted Data Directions • From: 19 Skyline Drive, Hawothorne, NY 10532, USA • To: Columbia University May 7, 2010 $skj#h. S 28 ksyt. A@ … IBM|NYU|Columbia Theory Day 4

Computing on Encrypted Data typo May 7, 2010 IBM|NYU|Columbia Theory Day $kjh 9*mslt@na 0 &ma. Xxjq 02 bflx m^00 a 2 nm 5, A 4. p. E. abxp 3 m 58 bsa (3 sa. M%w, snanba nq~m. D=3 akm 2, A Z, ltnhde 83|3 mz{n dewiunb 4]gnb. Ta* kjew^bw. J^mdns 0 5

Part I: Constructing Homomorphic Encryption May 7, 2010 IBM|NYU|Columbia Theory Day
![Privacy Homomorphisms RAD 78 Plaintext space P x 1 x 2 ci Encxi Ciphertext Privacy Homomorphisms [RAD 78] Plaintext space P x 1 x 2 ci Enc(xi) Ciphertext](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-7.jpg)
Privacy Homomorphisms [RAD 78] Plaintext space P x 1 x 2 ci Enc(xi) Ciphertext space C c 1 * c 2 # y Dec(d) y d Some examples: o “Raw RSA”: c xe mod N (x cd mod N) Ø x 1 e x x 2 e = (x 1 x x 2)e mod N o GM 84: Enc(0) R QR, Enc(1) R QNR (in ZN*) Ø Enc(x 1) x Enc(x 2) = Enc(x 1 x 2) mod N May 7, 2010 IBM|NYU|Columbia Theory Day 7
![More Privacy Homomorphisms o Multmodp El Gamal 84 o AddmodN Pallier 98 o NC More Privacy Homomorphisms o Mult-mod-p [El. Gamal’ 84] o Add-mod-N [Pallier’ 98] o NC](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-8.jpg)
More Privacy Homomorphisms o Mult-mod-p [El. Gamal’ 84] o Add-mod-N [Pallier’ 98] o NC 1 circuits [SYY’ 00] o Quadratic-polys mod p [BGN’ 06] o Poly-size branching programs [IP’ 07] o See Part II for a “different type of solution” for any poly-size circuit [Yao’ 82, …] May 7, 2010 IBM|NYU|Columbia Theory Day 8

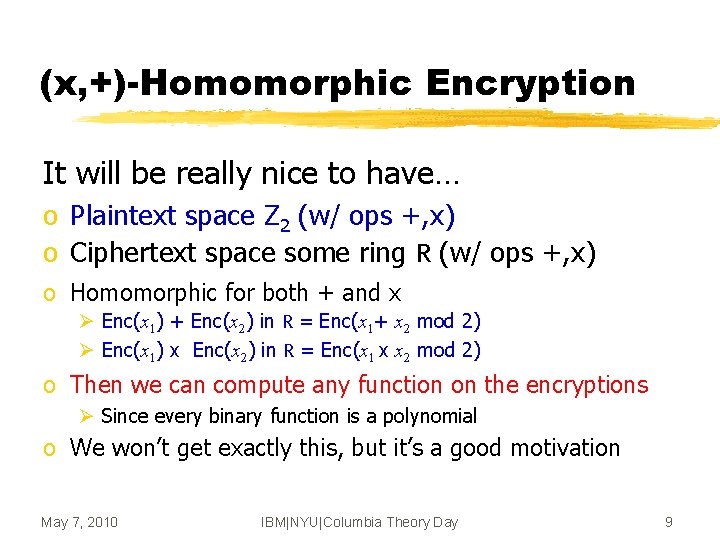
(x, +)-Homomorphic Encryption It will be really nice to have… o Plaintext space Z 2 (w/ ops +, x) o Ciphertext space some ring R (w/ ops +, x) o Homomorphic for both + and x Ø Enc(x 1) + Enc(x 2) in R = Enc(x 1+ x 2 mod 2) Ø Enc(x 1) x Enc(x 2) in R = Enc(x 1 x x 2 mod 2) o Then we can compute any function on the encryptions Ø Since every binary function is a polynomial o We won’t get exactly this, but it’s a good motivation May 7, 2010 IBM|NYU|Columbia Theory Day 9

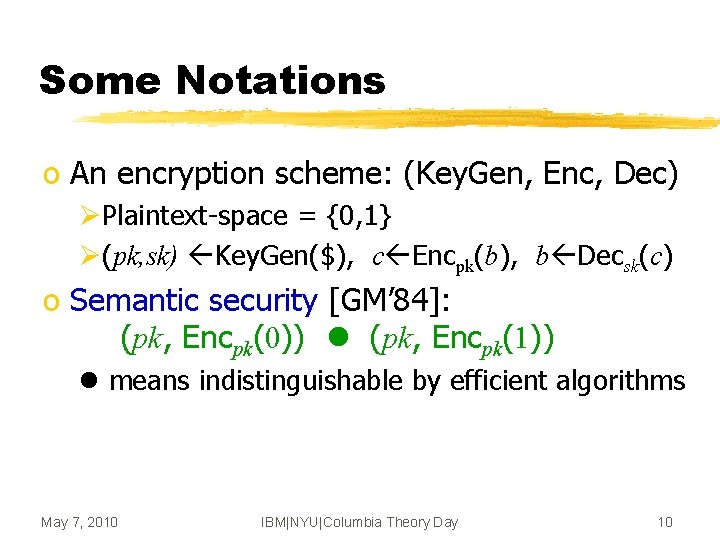
Some Notations o An encryption scheme: (Key. Gen, Enc, Dec) ØPlaintext-space = {0, 1} Ø(pk, sk) Key. Gen($), c Encpk(b), b Decsk(c) o Semantic security [GM’ 84]: (pk, Encpk(0)) (pk, Encpk(1)) means indistinguishable by efficient algorithms May 7, 2010 IBM|NYU|Columbia Theory Day 10

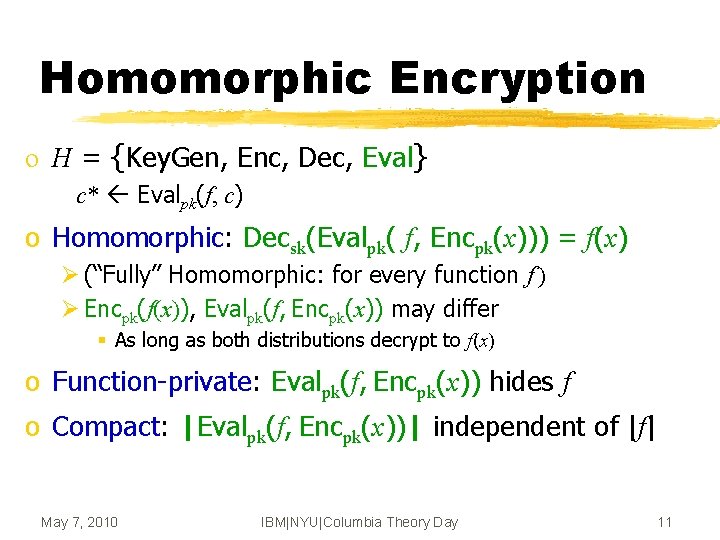
Homomorphic Encryption o H = {Key. Gen, Enc, Dec, Eval} c* Evalpk(f, c) o Homomorphic: Decsk(Evalpk( f, Encpk(x))) = f(x) Ø (“Fully” Homomorphic: for every function f ) Ø Encpk(f(x)), Evalpk(f, Encpk(x)) may differ § As long as both distributions decrypt to f(x) o Function-private: Evalpk(f, Encpk(x)) hides f o Compact: |Evalpk(f, Encpk(x))| independent of |f| May 7, 2010 IBM|NYU|Columbia Theory Day 11
![x Homomorphic Encryption the Gentry Way G 09 Evaluate any function in four easy (x, +)-Homomorphic Encryption, the Gentry Way [G’ 09] Evaluate any function in four “easy”](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-12.jpg)
(x, +)-Homomorphic Encryption, the Gentry Way [G’ 09] Evaluate any function in four “easy” steps o Step 1: Encryption from linear ECCs Ø Additive homomorphism o Step 2: ECC lives inside a ring Ø Also multiplicative homomorphism Ø But only for a few operations (i. e. , low-degree poly’s) o Step 3: Bootstrapping Ø Few ops (but not too few) any number of ops o Step 4: Everything else May 7, 2010 IBM|NYU|Columbia Theory Day 12

Step One: Encryption from Linear ECCs o For “random looking” codes, hard to distinguish close/far from code o Many cryptosystems built on this hardness ØE. g. , [Mc. Eliece’ 78, AD’ 97, GGH’ 97, R’ 03, …] May 7, 2010 IBM|NYU|Columbia Theory Day 13

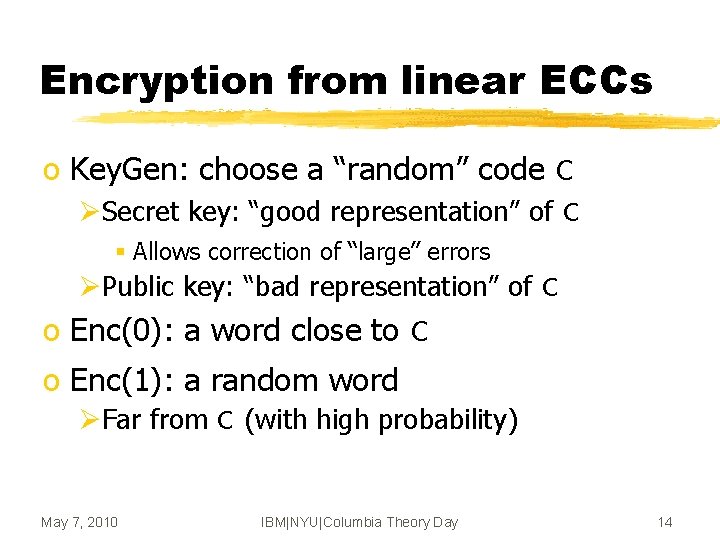
Encryption from linear ECCs o Key. Gen: choose a “random” code C ØSecret key: “good representation” of C § Allows correction of “large” errors ØPublic key: “bad representation” of C o Enc(0): a word close to C o Enc(1): a random word ØFar from C (with high probability) May 7, 2010 IBM|NYU|Columbia Theory Day 14
![An Example Integers mod p similar to Regev 03 p N o Code determined An Example: Integers mod p (similar to [Regev’ 03]) p N o Code determined](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-15.jpg)
An Example: Integers mod p (similar to [Regev’ 03]) p N o Code determined by an integer p ØCodewords: multiples of p o Good representation: p itself o Bad representation: ri p ØN = pq, and also many xi = pqi + ri o Enc(0): subset-sum(xi’s)+r mod N o Enc(1): random integer mod N May 7, 2010 IBM|NYU|Columbia Theory Day 15

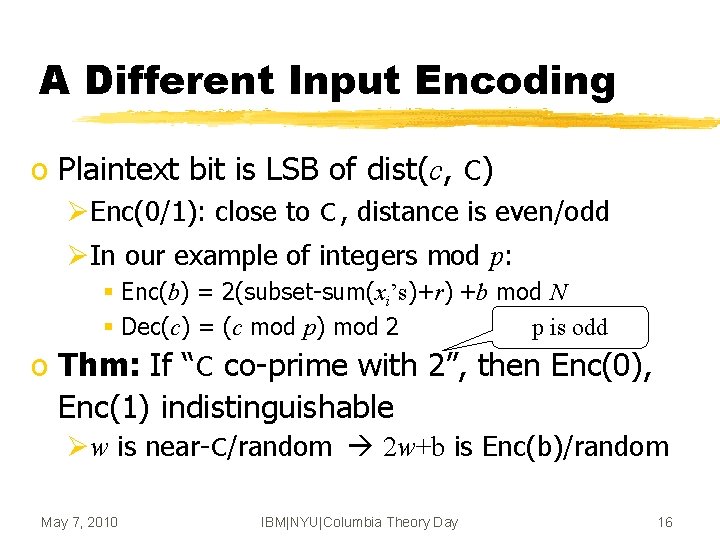
A Different Input Encoding o Plaintext bit is LSB of dist(c, C) ØEnc(0/1): close to C , distance is even/odd ØIn our example of integers mod p: § Enc(b) = 2(subset-sum(xi’s)+r) +b mod N § Dec(c) = (c mod p) mod 2 p is odd o Thm: If “C co-prime with 2”, then Enc(0), Enc(1) indistinguishable Øw is near-C/random 2 w+b is Enc(b)/random May 7, 2010 IBM|NYU|Columbia Theory Day 16

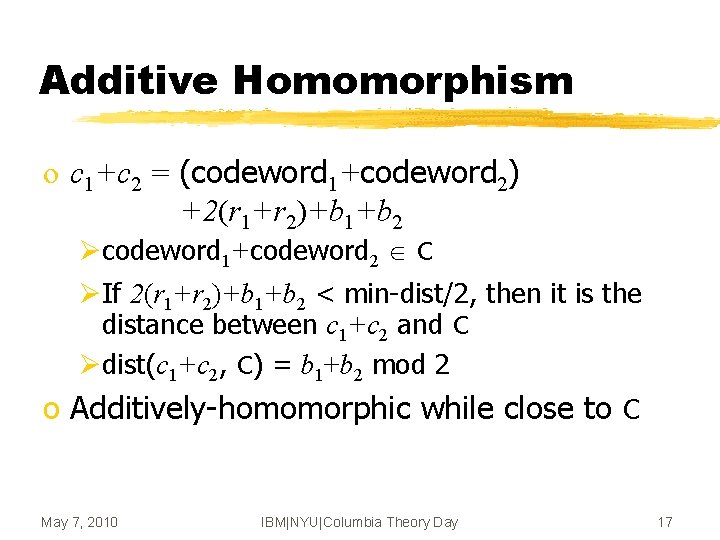
Additive Homomorphism o c 1+c 2 = (codeword 1+codeword 2) +2(r 1+r 2)+b 1+b 2 Øcodeword 1+codeword 2 C ØIf 2(r 1+r 2)+b 1+b 2 < min-dist/2, then it is the distance between c 1+c 2 and C Ødist(c 1+c 2, C) = b 1+b 2 mod 2 o Additively-homomorphic while close to C May 7, 2010 IBM|NYU|Columbia Theory Day 17

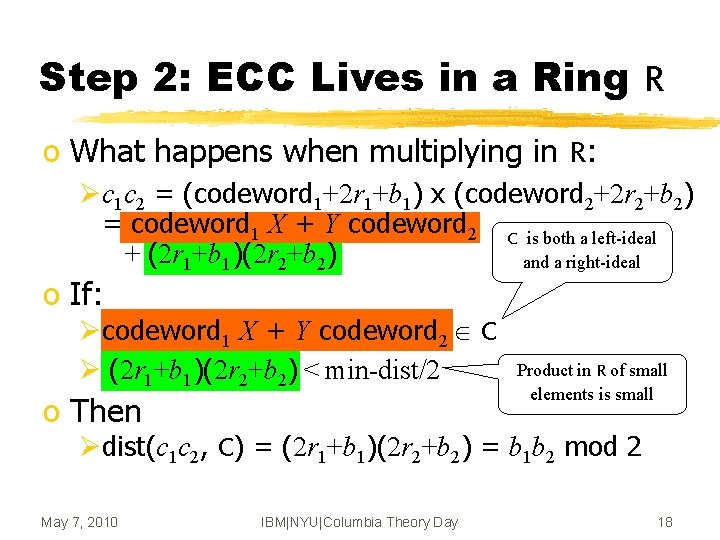
Step 2: ECC Lives in a Ring R o What happens when multiplying in R: Øc 1 c 2 = (codeword 1+2 r 1+b 1) x (codeword 2+2 r 2+b 2) = codeword 1 X + Y codeword 2 C is both a left-ideal + (2 r 1+b 1)(2 r 2+b 2) and a right-ideal o If: Øcodeword 1 X + Y codeword 2 C Ø (2 r 1+b 1)(2 r 2+b 2) < min-dist/2 o Then Product in R of small elements is small Ødist(c 1 c 2, C) = (2 r 1+b 1)(2 r 2+b 2) = b 1 b 2 mod 2 May 7, 2010 IBM|NYU|Columbia Theory Day 18
![Integers Rings v DGHV 10 o Recall modp scheme ci qip 2 Integers Rings [v. DGHV’ 10] o Recall mod-p scheme: ci = qip + 2](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-19.jpg)
Integers Rings [v. DGHV’ 10] o Recall mod-p scheme: ci = qip + 2 ri+bi (mod N=qp) Ø Parameters: |ri|=n, |p|=n 2, |q|=|qi|=n 5 o c 1+c 2 mod N = (q 1+q 2 -kq)p + 2(r 1+r 2)+(b 1+b 2) sum mod p = 2(r 1+r 2) + (b 1+b 2) o c 1 x c 2 mod N = (c 1 q 2+q 1 c 2 -q 1 q 2 -kq)p + 2(2 r 1 r 2+r 1 m 2+m 1 r 2) + b 1 b 2 product mod p = 2(2 r 1 r 2+…) + b 1 b 2 o Can evaluate polynomials of degree ~ n before the distance from C exceeds p/2 May 7, 2010 IBM|NYU|Columbia Theory Day 19
![Integers Rings v DGHV 10 Thm Approximate GCD is hard Enc0 Enc1 are indistinguishable Integers Rings [v. DGHV’ 10] Thm: “Approximate GCD” is hard Enc(0), Enc(1) are indistinguishable](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-20.jpg)
Integers Rings [v. DGHV’ 10] Thm: “Approximate GCD” is hard Enc(0), Enc(1) are indistinguishable o Apprixmate-GCD: Given N=qp and many xi = pqi + ri, hard to recover p May 7, 2010 IBM|NYU|Columbia Theory Day 20
![Polynomial Rings G 09 o R polynomial ring modulo some fx ØE g Polynomial Rings [G’ 09] o R = polynomial ring modulo some f(x) ØE. g.](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-21.jpg)
Polynomial Rings [G’ 09] o R = polynomial ring modulo some f(x) ØE. g. , f(x) = xn +1 o C is an ideal in R ØE. g. , random g(x), Cg = { gxh mod f : h R } § C is also a lattice ØGood representation: g itself ØBad representation: Hermite-Normal-Form o If g has t-bit coefficients, can evaluate polynomials of degree O(t/log n) May 7, 2010 IBM|NYU|Columbia Theory Day 21
![Polynomial Rings G 09 Thm BoundedDistance Decoding in ideal lattices is hard Enc0 Enc1 Polynomial Rings [G’ 09] Thm: Bounded-Distance Decoding in ideal lattices is hard Enc(0), Enc(1)](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-22.jpg)
Polynomial Rings [G’ 09] Thm: Bounded-Distance Decoding in ideal lattices is hard Enc(0), Enc(1) are indistinguishable o Bounded-Distance-Decoding: Given x close to the lattice, find dist(x, lattice) May 7, 2010 IBM|NYU|Columbia Theory Day 22
![Doesnt quite fit the mold Matrix Rings GHV 10 o R ring of *Doesn’t quite fit the mold Matrix Rings* [GHV’ 10] o R = ring of](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-23.jpg)
*Doesn’t quite fit the mold Matrix Rings* [GHV’ 10] o R = ring of mxm matrices over Zq Ø o q = poly(n), m > n log q (n security-parameter) C has low-rank matrices mod q (rank=n) ØA is a random nxm matrix, CA = { AX : X R } ØBad representation: A itself ØGood representation: full rank Tmxm (over Z), small entries, TA = 0 mod q • Problem: CA is left-ideal, but not right-ideal • Can still evaluate quadratic formulas, no more May 7, 2010 IBM|NYU|Columbia Theory Day 23
![Doesnt quite fit the mold Matrix Rings GHV 10 Thm Learning with Errors hard *Doesn’t quite fit the mold Matrix Rings* [GHV’ 10] Thm: Learning with Errors hard](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-24.jpg)
*Doesn’t quite fit the mold Matrix Rings* [GHV’ 10] Thm: Learning with Errors hard Enc(0), Enc(1) are indistinguishable o Learning with Errors: Given A, Ax+e (random A, x, small error e), find x May 7, 2010 IBM|NYU|Columbia Theory Day 24
![Step 3 Bootstrapping G 09 o So far can evaluate lowdegree polynomials x 1 Step 3: Bootstrapping [G’ 09] o So far, can evaluate low-degree polynomials x 1](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-25.jpg)
Step 3: Bootstrapping [G’ 09] o So far, can evaluate low-degree polynomials x 1 x 2 … P P(x 1, x 2 , …, xt) xt May 7, 2010 IBM|NYU|Columbia Theory Day 25
![Step 3 Bootstrapping G 09 o So far can evaluate lowdegree polynomials x 1 Step 3: Bootstrapping [G’ 09] o So far, can evaluate low-degree polynomials x 1](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-26.jpg)
Step 3: Bootstrapping [G’ 09] o So far, can evaluate low-degree polynomials x 1 x 2 … P P(x 1, x 2 , …, xt) xt o Can eval y=P(x 1, x 2…, xn) when xi’s are “fresh” o But y is an “evaluated ciphertext” ØCan still be decrypted ØBut eval Q(y) will increase noise too much May 7, 2010 IBM|NYU|Columbia Theory Day 26
![Step 3 Bootstrapping G 09 o So far can evaluate lowdegree polynomials x 1 Step 3: Bootstrapping [G’ 09] o So far, can evaluate low-degree polynomials x 1](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-27.jpg)
Step 3: Bootstrapping [G’ 09] o So far, can evaluate low-degree polynomials x 1 x 2 … P P(x 1, x 2 , …, xt) xt o Bootstrapping to handle higher degrees: o For ciphertext c, consider Dc(sk) = Decsk(c) ØHope: Dc(*) is a low-degree polynomial in sk ØThen so are Ac 1, c 2(sk) = Decsk(c 1) + Decsk(c 2) and Mc 1, c 2(sk) = Decsk(c 1) x Decsk(c 2) May 7, 2010 IBM|NYU|Columbia Theory Day 27
![Step 3 Bootstrapping G 09 o Include in the public key also Encpksk x Step 3: Bootstrapping [G’ 09] o Include in the public key also Encpk(sk) x](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-28.jpg)
Step 3: Bootstrapping [G’ 09] o Include in the public key also Encpk(sk) x 1 c 1 sk 2 … skn May 7, 2010 x 2 c 2 Requires “circular security” Mc 1, c 2 c Mc 1, c 2(sk) = Decsk(c 1) x Decsk(c 2) = x 1 x x 2 IBM|NYU|Columbia Theory Day 28
![Step 3 Bootstrapping G 09 o Include in the public key also Encpksk x Step 3: Bootstrapping [G’ 09] o Include in the public key also Encpk(sk) x](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-29.jpg)
Step 3: Bootstrapping [G’ 09] o Include in the public key also Encpk(sk) x 1 c 1 sk 2 … skn x 2 c 2 Requires “circular security” Mc 1, c 2 c Mc 1, c 2(sk) = Decsk(c 1) x Decsk(c 2) = x 1 x x 2 o Homomorphic computation applied only to the “fresh” encryption of sk May 7, 2010 IBM|NYU|Columbia Theory Day 29
![Step 4 Everything Else o Cryptosystems from G 09 v DGHV 10 cannot handle Step 4: Everything Else o Cryptosystems from [G’ 09, v. DGHV’ 10] cannot handle](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-30.jpg)
Step 4: Everything Else o Cryptosystems from [G’ 09, v. DGHV’ 10] cannot handle their own decryption as-is o Apply some tricks to “squash” the decryption procedure May 7, 2010 IBM|NYU|Columbia Theory Day 30

Part II: Homomorphic Encryption vs. Secure Computation May 7, 2010 IBM|NYU|Columbia Theory Day

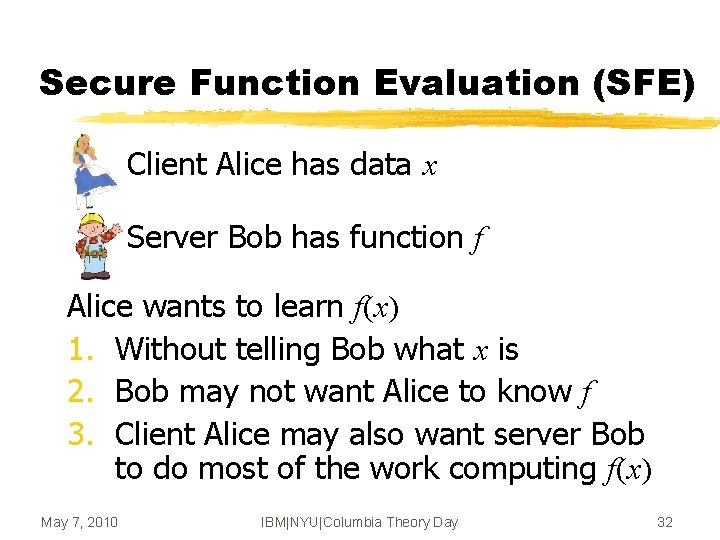
Secure Function Evaluation (SFE) Client Alice has data x Server Bob has function f Alice wants to learn f(x) 1. Without telling Bob what x is 2. Bob may not want Alice to know f 3. Client Alice may also want server Bob to do most of the work computing f(x) May 7, 2010 IBM|NYU|Columbia Theory Day 32
![TwoMessage SFE Yao 82 Alicex c s SFE 1x y SFE 3s r Two-Message SFE [Yao’ 82, …] Alice(x) (c, s) SFE 1(x) y SFE 3(s, r)](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-33.jpg)
Two-Message SFE [Yao’ 82, …] Alice(x) (c, s) SFE 1(x) y SFE 3(s, r) Bob(f) c r r SFE 2(f, c) o Many different instantiations are available Ø Based on hardness of factoring/DL/lattices/… o Alice’s x and Bob’s f are kept private o But Alice does as much work as Bob Ø Bob’s reply of size poly(n) x (|f|+|x|) May 7, 2010 IBM|NYU|Columbia Theory Day 33

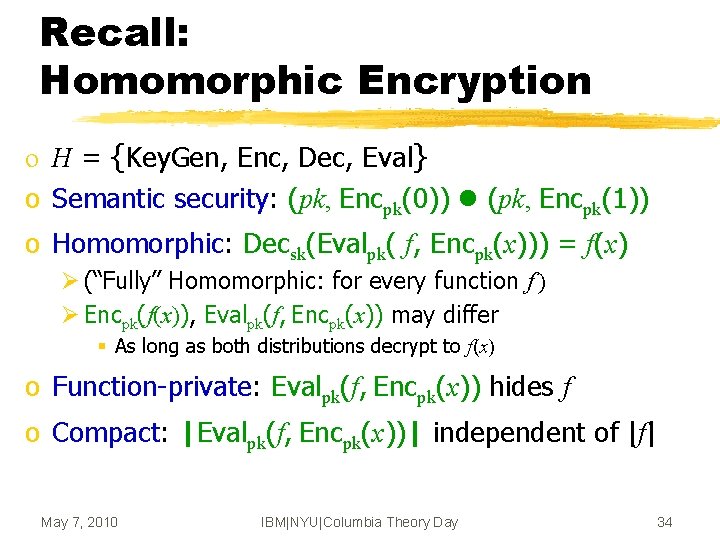
Recall: Homomorphic Encryption o H = {Key. Gen, Enc, Dec, Eval} o Semantic security: (pk, Encpk(0)) (pk, Encpk(1)) o Homomorphic: Decsk(Evalpk( f, Encpk(x))) = f(x) Ø (“Fully” Homomorphic: for every function f ) Ø Encpk(f(x)), Evalpk(f, Encpk(x)) may differ § As long as both distributions decrypt to f(x) o Function-private: Evalpk(f, Encpk(x)) hides f o Compact: |Evalpk(f, Encpk(x))| independent of |f| May 7, 2010 IBM|NYU|Columbia Theory Day 34

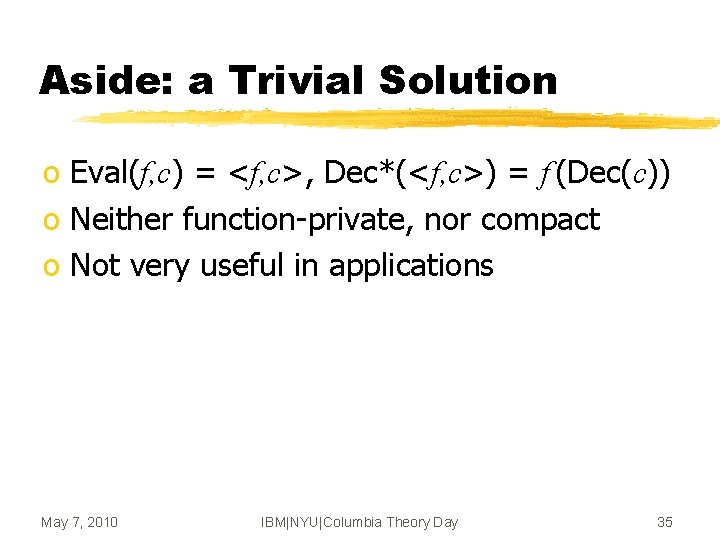
Aside: a Trivial Solution o Eval(f, c) = <f, c>, Dec*(<f, c>) = f (Dec(c)) o Neither function-private, nor compact o Not very useful in applications May 7, 2010 IBM|NYU|Columbia Theory Day 35

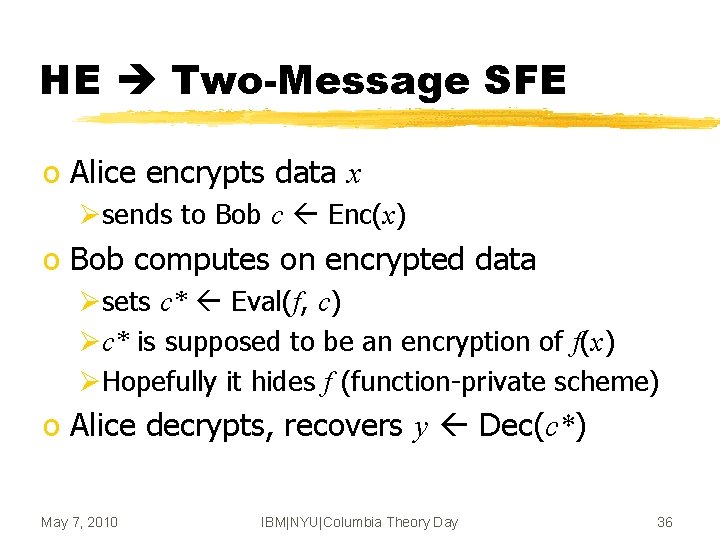
HE Two-Message SFE o Alice encrypts data x Øsends to Bob c Enc(x) o Bob computes on encrypted data Øsets c* Eval(f, c) Øc* is supposed to be an encryption of f(x) ØHopefully it hides f (function-private scheme) o Alice decrypts, recovers y Dec(c*) May 7, 2010 IBM|NYU|Columbia Theory Day 36

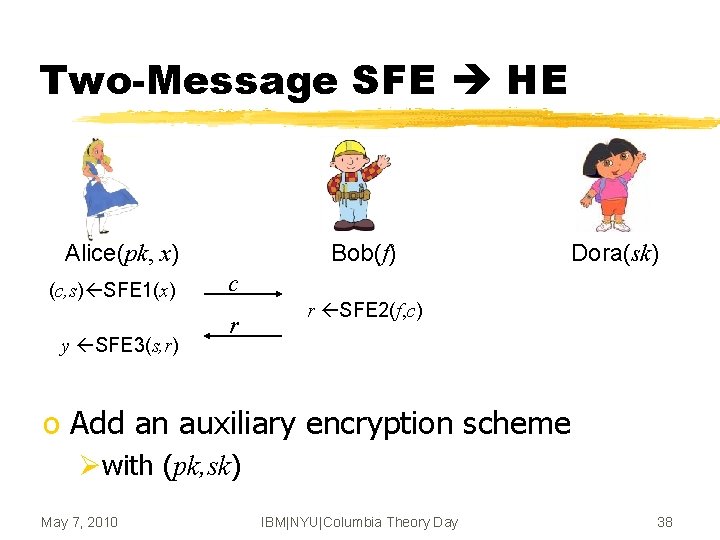
Two-Message SFE HE o Roughly: ØAlice’s message c SFE 1(x) is Enc(x) ØBob’s reply r SFE 2(f, c) is Eval(f, c) o Not quite public-key encryption yet ØWhere are (pk, sk)? ØCan be fixed with an auxiliary PKE scheme May 7, 2010 IBM|NYU|Columbia Theory Day 37

Two-Message SFE HE Alice(pk, Alice(x)x) (c, s) SFE 1(x) y SFE 3(s, r) Bob(f) Dora(sk) c r r SFE 2(f, c) o Add an auxiliary encryption scheme Øwith (pk, sk) May 7, 2010 IBM|NYU|Columbia Theory Day 38

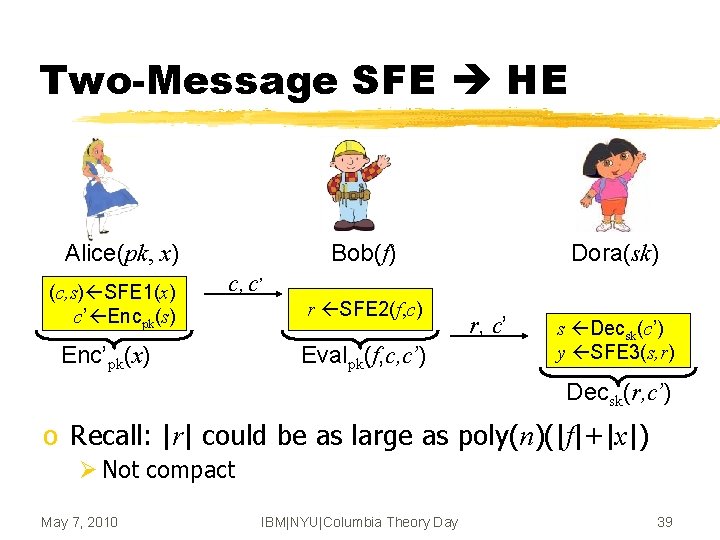
Two-Message SFE HE Alice(pk, x) (c, s) SFE 1(x) c’ Encpk(s) Bob(f) Dora(sk) c, c’ Enc’pk(x) r SFE 2(f, c) Evalpk(f, c, c’) r, c’ s Decsk(c’) y SFE 3(s, r) Decsk(r, c’) o Recall: |r| could be as large as poly(n)(|f|+|x|) Ø Not compact May 7, 2010 IBM|NYU|Columbia Theory Day 39
![A More Complex Setting iHop HE GHV 10 b Alicex c 0 Encx Bobf A More Complex Setting: i-Hop HE [GHV 10 b] Alice(x) c 0 Enc(x) Bob(f)](https://slidetodoc.com/presentation_image_h2/1361b004795f2e603a8c1fd0344c73ca/image-40.jpg)
A More Complex Setting: i-Hop HE [GHV 10 b] Alice(x) c 0 Enc(x) Bob(f) c 0 Charlie(g) c 1 Eval(f, c 0) c 1 c 2 Eval(g, c 1) Dora(sk) c 2 y Dec(c 2) 2 -Hop Homomorphic Encryption o c 1 is not a fresh ciphertext Ø May look completely different o Can Charlie process it at all? Ø What about security? May 7, 2010 IBM|NYU|Columbia Theory Day 40

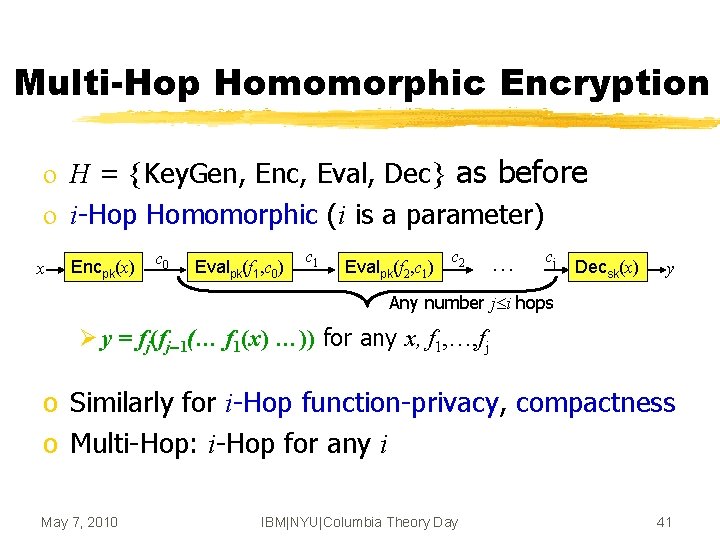
Multi-Hop Homomorphic Encryption o H = {Key. Gen, Enc, Eval, Dec} as before o i-Hop Homomorphic (i is a parameter) x Encpk(x) c 0 Evalpk(f 1, c 0) c 1 Evalpk(f 2, c 1) c 2 … cj Decsk(x) y Any number j i hops Ø y = fj(fj-1(… f 1(x) …)) for any x, f 1, …, fj o Similarly for i-Hop function-privacy, compactness o Multi-Hop: i-Hop for any i May 7, 2010 IBM|NYU|Columbia Theory Day 41

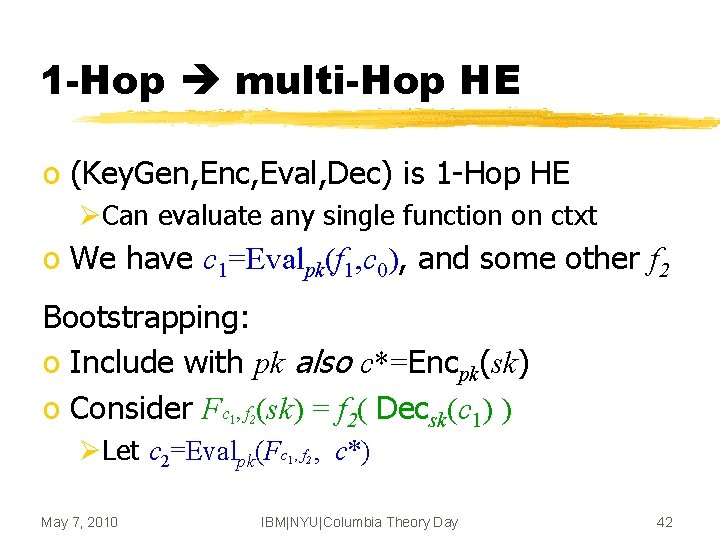
1 -Hop multi-Hop HE o (Key. Gen, Enc, Eval, Dec) is 1 -Hop HE ØCan evaluate any single function on ctxt o We have c 1=Evalpk(f 1, c 0), and some other f 2 Bootstrapping: o Include with pk also c*=Encpk(sk) o Consider Fc , f (sk) = f 2( Decsk(c 1) ) 1 2 ØLet c 2=Evalpk(Fc , f , c*) 1 May 7, 2010 2 IBM|NYU|Columbia Theory Day 42

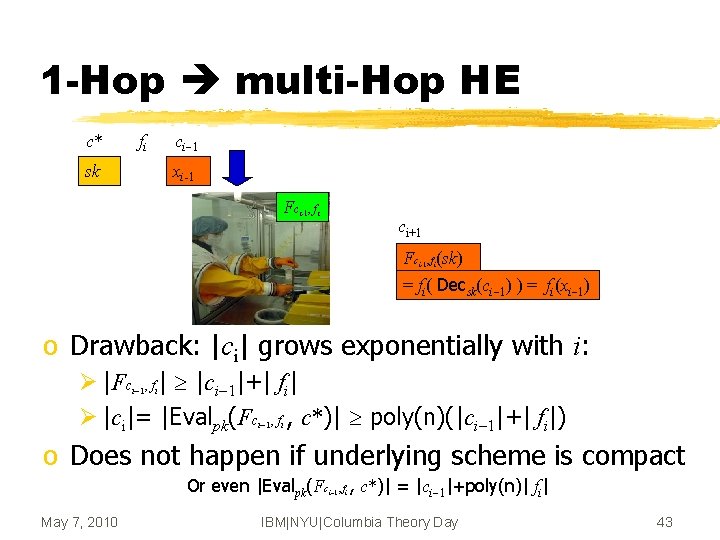
1 -Hop multi-Hop HE c* fi ci-1 sk xi-1 Fci-1, fi ci+1 Fc , f (sk) = fi( Decsk(ci-1) ) = fi(xi-1) i-1 i o Drawback: |ci| grows exponentially with i: Ø |Fc , f | |ci-1|+| fi| Ø |ci|= |Evalpk(Fc , f , c*)| poly(n)(|ci-1|+| fi|) i-1 i o Does not happen if underlying scheme is compact Or even |Evalpk(Fc May 7, 2010 i-1, fi , c*)| = |ci-1|+poly(n)| fi| IBM|NYU|Columbia Theory Day 43

Other Constructions o Private 1 -hop HE + Compact 1 -hop HE Compact, Private multi-hop HE o A direct construction of multi-hop HE from Yao’s protocol May 7, 2010 IBM|NYU|Columbia Theory Day 44

Summary o Homomorphic Encryption is useful ØEspecially multi-hop HE o A method for constructing HE schemes from linear ECCs in rings ØTwo (+e) known instances so far o Connection to two-message protocols for secure computation May 7, 2010 IBM|NYU|Columbia Theory Day 45

Thank You May 7, 2010 IBM|NYU|Columbia Theory Day