Encryption What is Encryption Types of Encryption 1











- Slides: 18

Encryption • What is Encryption • Types of Encryption 1

E-Commerce Risks for Businesses n n Need for a robust, reliable web site Fraudulent transactions Customer reluctance to purchase online Increased competition 2

E-Commerce Risks for Consumers n n Possible Security Issues Possible Privacy Issues Purchasing from photos & descriptions Possible difficulty with returns 3

E-Commerce Issues n n n Intellectual Property Security Fraud Taxation International Commerce 4

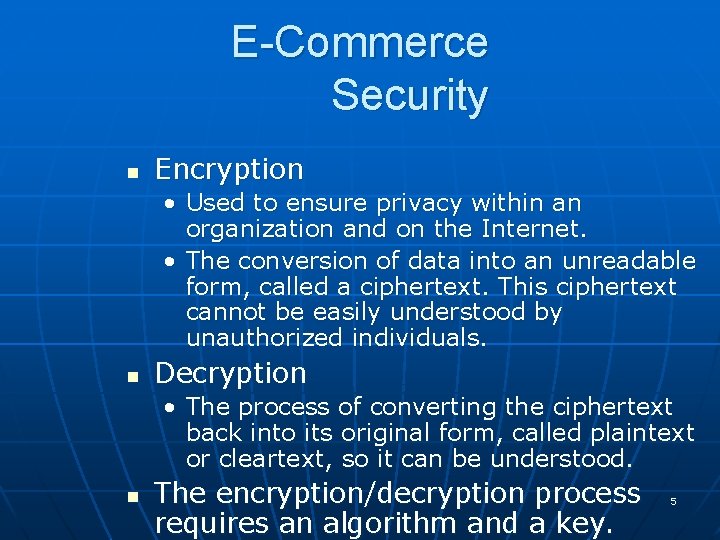
E-Commerce Security n Encryption • Used to ensure privacy within an organization and on the Internet. • The conversion of data into an unreadable form, called a ciphertext. This ciphertext cannot be easily understood by unauthorized individuals. n Decryption • The process of converting the ciphertext back into its original form, called plaintext or cleartext, so it can be understood. n The encryption/decryption process requires an algorithm and a key. 5

E-Commerce Security Encryption Types Secure E-Commerce transactions make use of the encryption technologies below: n Symmetric-key Encryption n Asymmetric-key Encryption n Hash Encryption These technologies are used as part of SSL (Secure Sockets Layer) – the technology that helps to make commerce on the Internet secure. 6

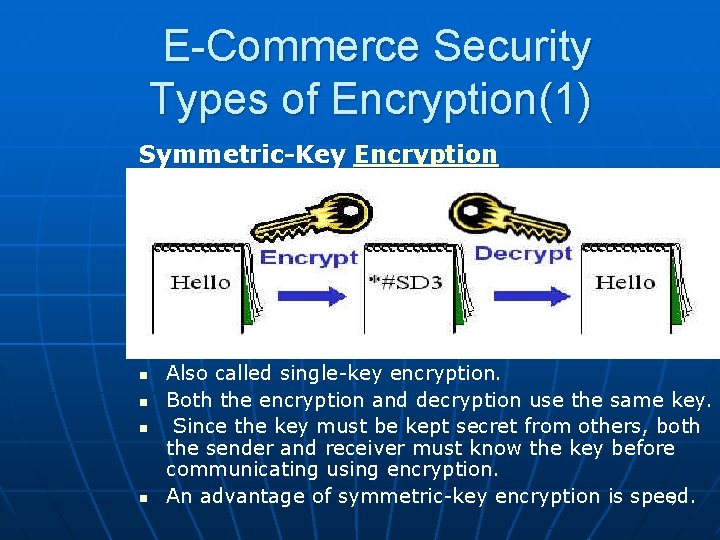
E-Commerce Security Types of Encryption(1) Symmetric-Key Encryption n n Also called single-key encryption. Both the encryption and decryption use the same key. Since the key must be kept secret from others, both the sender and receiver must know the key before communicating using encryption. An advantage of symmetric-key encryption is speed. 7

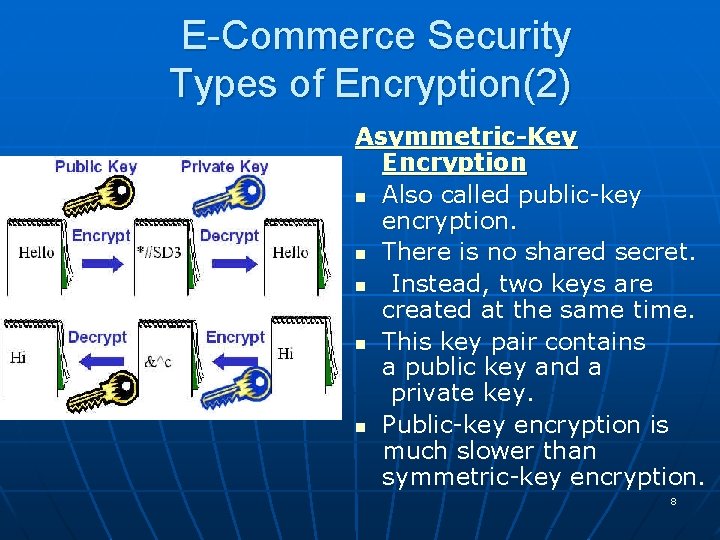
E-Commerce Security Types of Encryption(2) Asymmetric-Key Encryption n Also called public-key encryption. n There is no shared secret. n Instead, two keys are created at the same time. n This key pair contains a public key and a private key. n Public-key encryption is much slower than symmetric-key encryption. 8

E-Commerce Security Types of Encryption(3) Hash Encryption n A hash algorithm transforms a string of characters into a usually shorter fixed-length value or key that represents the original string, called a digest. n Hash encryption is one-way encryption. n Hash encryption is used for information that will not be read or decrypted. n The function of hash encryption is to verify the integrity of information. 9

Secure Sockets Layer (SSL) n n n SSL is a protocol that allows data to be privately exchanged over public networks. SSL was developed by Netscape and is used to encrypt data sent between a client (usually a web browser) and a web server. SSL utilizes both symmetric and asymmetric keys. SSL uses the “https” protocol instead of the “http” protocol Most browsers display a “lock” icon when SSL is 10 being used.

Secure Sockets Layer (SSL) n SSL provides secure communication between a client and server by using: • Server and (optionally) client digital certificates for authentication • Symmetric-key cryptography using a "session key" for bulk encryption • Public-key cryptography for transfer of the session key • Message Digests (hash encryption) to verify the integrity of the transmission 11

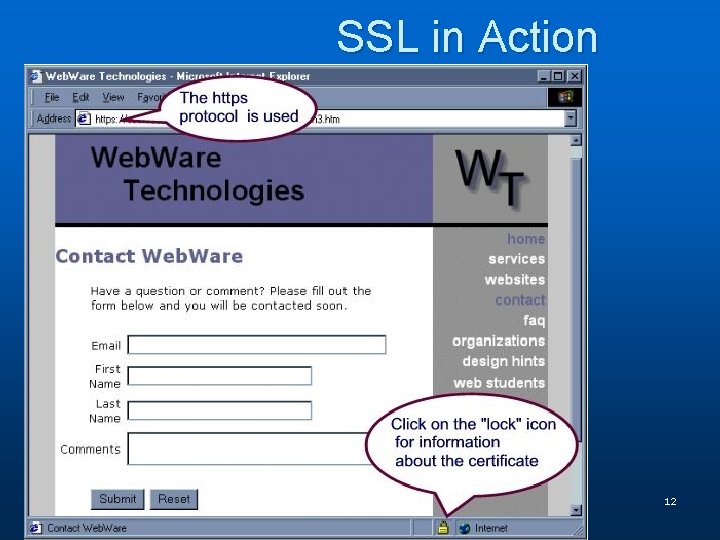
SSL in Action 12

SSL & Digital Certificate n n SSL enables two computers to securely communicate by using a digital certificate for authentication. A digital certificate is a form of an asymmetric key that also contains information about the certificate, the holder of the certificate, and the issuer of the certificate. 13

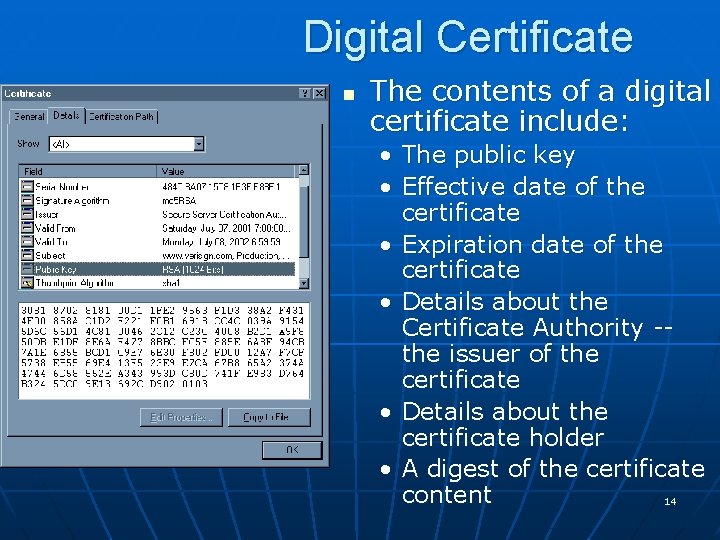
Digital Certificate n The contents of a digital certificate include: • The public key • Effective date of the certificate • Expiration date of the certificate • Details about the Certificate Authority -the issuer of the certificate • Details about the certificate holder • A digest of the certificate content 14

Certificate Authority n n A Certificate Authority is a trusted third-party organization or company that issued digital certificates. Well-known Certificate Authorities: • Verisign n http: //www. verisign. com • Thawte n http: //www. thawte. com 15

Obtaining a Digital Certificate n n Request a certificate from a Certificate Authority and pay the application fee. The Certificate Authority: • • • n n verifies your identity, issues your Certificate, and supplies you with a public/private key pair. Store the certificate in your software - such as a web server, web browser, or e-mail application. The Certificate Authority makes your certificate publicly known. 16

SSL & Digital Certificates n When you visit an e-commerce site that uses SSL, a number of steps are involved in the authentication process. • The web browser and web server go through initial handshaking steps using the server certificate and keys. • Once trust is established, the web browser encrypts the single secret key (symmetric key) that will be used for the rest of the communication. • From this point on, all data is encrypted using the secret key. 17

Questions 1. Define SSL. Describe how an online shopper can tell that an ecommerce site is using SSL. 18