Intrusion Detection snort Snort Get snort Installation Configure














- Slides: 34

Intrusion Detection snort

Snort ● Get snort ● Installation ● Configure ● Setup logs ● Rules ● Start

Get snort source ● http: //www. snort. org/ ● tar. gz ● Source – ● Rpm's – Redhat Package Manager ● ● http: //www. snort. org/dl/current/snort-2. 8. 2. 3. tar. gz yum install snort Apt-get – Debian package manager ● apt-get install snort

Install Make from source ● Source based installation ● ● Move the tar. gz file to ● /usr/local/src/ or ● /usr/src/redhat/SOURCES tar -zxvf snort-2. 4. 3. tar. gz ● ● Unpacks the source in snort-2. 4. 3 Build the app ● cd snort-2. 4. 3 ● . /configure ● make install

Documentation ● Included documentation in the distribution AUTHORS BUGS CREDITS faq. pdf faq. tex INSTALL Makefile. am Makefile. in NEWS PROBLEMS README. alert_order README. asn 1 README. csv README. database README. event_queue README. FLEXRESP README. flowbits README. flow-portscan README. frag 3 README. http_inspect README. INLINE README. PLUGINS README. sfportscan README. thresholding README. UNSOCK README. WIN 32 README. wireless RULES. todo snort_manual. pdf snort_manual. tex snort_schema_v 106. pdf TODO USAGE WISHLIST ● man snort ● More documentation on the snort website

Configure ● Create directory mkdir /etc/snort, cd /etc/snort ● Get snort rules ● ● ttp: //www. snort. org/pub-bin/downloads. cgi/Download/vrt_pr/snortrules-pr-2. 4. tar. gz Unpack the rule set ● tar -zxvf snortrules-pr-2. 4. tar. gz ● Edit /etc/snort/rules/snort. conf ● mkdir /var/log/snort ● Snort has to know where everything is

snort. conf var HOME_NET any var HOME_NET 192. 168. 50. 0/24 var EXTERNAL_NET any var EXTERNAL_NET !$HOME_NET var SMTP $HOME_NET var HTTP_SERVICES $HOME_NET var SQL_SERVERS $HOME_NET var DNS_SERVERS $HOME_NET var RULE_PATH /etc/snort/rules

Modes of operation ● Sniffer mode ● ● ● On screen packet sniffer Packet logger mode ● Logs in text format or tcpdump format ● Direct the logging to a remote host ● Logs every packet NIDS mode ● Uses snort. conf ● Logs only the packets that satisfies a rule

Sniffer mode ● snort -v -i eth 0 Shows only the headers on the screen 02/16 -12: 59: 45. 856485 127. 0. 0. 1 -> 127. 0. 0. 1 ICMP TTL: 64 TOS: 0 x 0 ID: 0 Ip. Len: 20 Dgm. Len: 84 DF Type: 8 Code: 0 ID: 13104 Seq: 256 ECHO =+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+ 02/16 -12: 59: 45. 856519 127. 0. 0. 1 -> 127. 0. 0. 1 ICMP TTL: 64 TOS: 0 x 0 ID: 50341 Ip. Len: 20 Dgm. Len: 84 Type: 0 Code: 0 ID: 13104 Seq: 256 ECHO REPLY =+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+

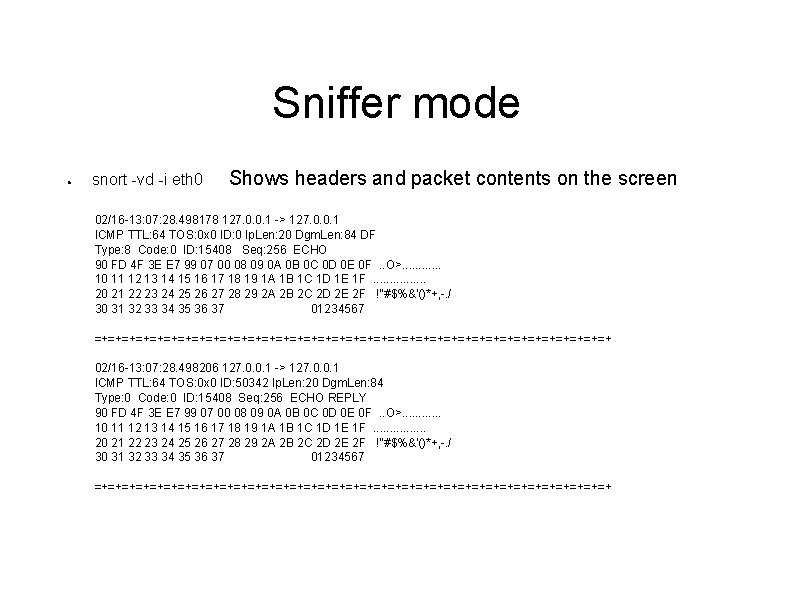
Sniffer mode ● snort -vd -i eth 0 Shows headers and packet contents on the screen 02/16 -13: 07: 28. 498178 127. 0. 0. 1 -> 127. 0. 0. 1 ICMP TTL: 64 TOS: 0 x 0 ID: 0 Ip. Len: 20 Dgm. Len: 84 DF Type: 8 Code: 0 ID: 15408 Seq: 256 ECHO 90 FD 4 F 3 E E 7 99 07 00 08 09 0 A 0 B 0 C 0 D 0 E 0 F. . O>. . . 10 11 12 13 14 15 16 17 18 19 1 A 1 B 1 C 1 D 1 E 1 F. . . . 20 21 22 23 24 25 26 27 28 29 2 A 2 B 2 C 2 D 2 E 2 F !"#$%&'()*+, -. / 30 31 32 33 34 35 36 37 01234567 =+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+ 02/16 -13: 07: 28. 498206 127. 0. 0. 1 -> 127. 0. 0. 1 ICMP TTL: 64 TOS: 0 x 0 ID: 50342 Ip. Len: 20 Dgm. Len: 84 Type: 0 Code: 0 ID: 15408 Seq: 256 ECHO REPLY 90 FD 4 F 3 E E 7 99 07 00 08 09 0 A 0 B 0 C 0 D 0 E 0 F. . O>. . . 10 11 12 13 14 15 16 17 18 19 1 A 1 B 1 C 1 D 1 E 1 F. . . . 20 21 22 23 24 25 26 27 28 29 2 A 2 B 2 C 2 D 2 E 2 F !"#$%&'()*+, -. / 30 31 32 33 34 35 36 37 01234567 =+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+

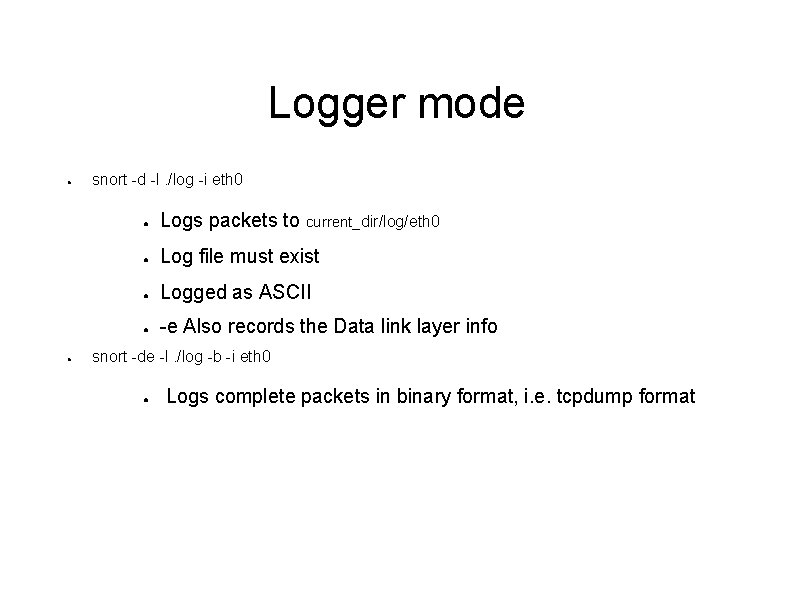
Logger mode ● ● snort -d -l. /log -i eth 0 ● Logs packets to current_dir/log/eth 0 ● Log file must exist ● Logged as ASCII ● -e Also records the Data link layer info snort -de -l. /log -b -i eth 0 ● Logs complete packets in binary format, i. e. tcpdump format

NIDS Mode ● ● Runs snort as an intrusion detector ● Every packet is not recorded ● Only those packets matching a rule snort -de -l -i eth 0 -c snort. conf ● Uses rules in snort. conf ● tcpdump format ● Sends log files to /var/log/snort

Rules ● The basis for logging or not logging a packet ● Can be more that one line long – now ● Each line to be continued must be terminated with a ' ‘ ● ● That is “space ” Generic syntax rule_header (rule_options) ● Rule header ● ● Action, addresses, ports, masks Rule options ● Messages, what to look for, where to look

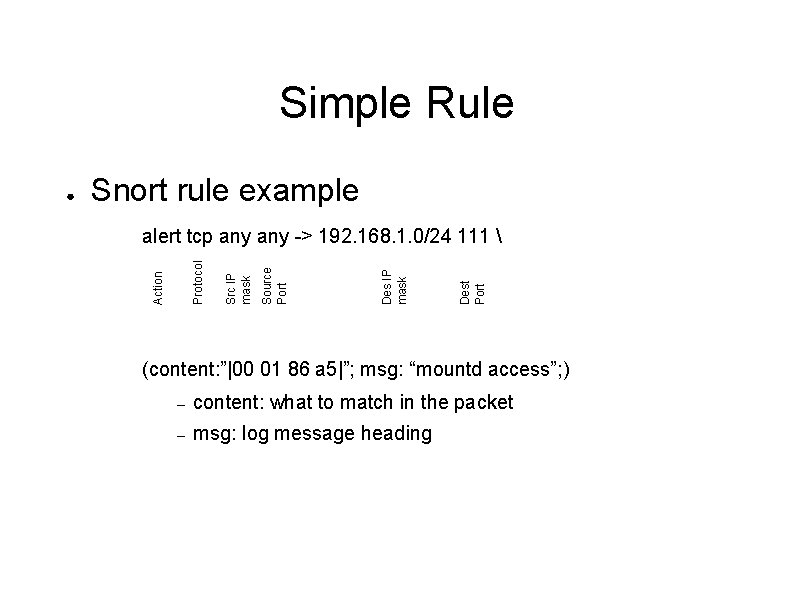
Simple Rule Snort rule example Dest Port Des IP mask Source Port Src IP mask Protocol alert tcp any -> 192. 168. 1. 0/24 111 Action ● (content: ”|00 01 86 a 5|”; msg: “mountd access”; ) – content: what to match in the packet – msg: log message heading

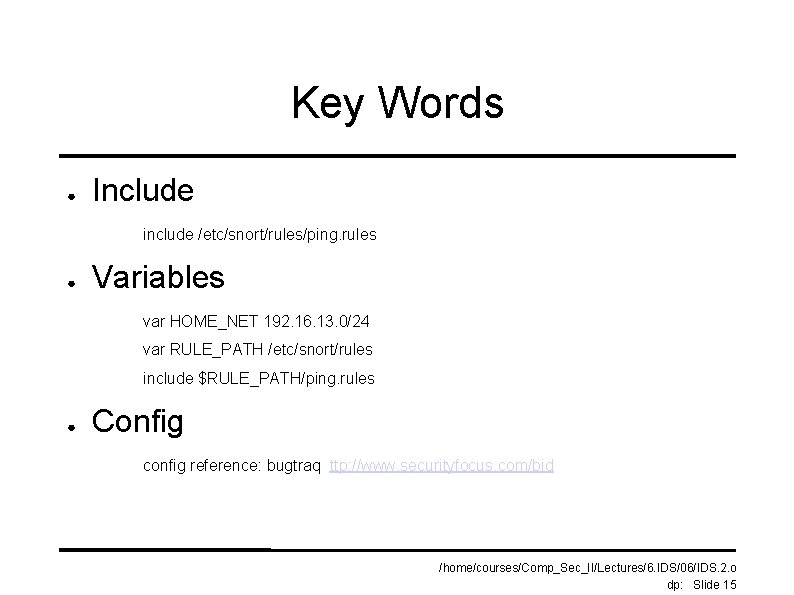
Key Words ● Include include /etc/snort/rules/ping. rules ● Variables var HOME_NET 192. 16. 13. 0/24 var RULE_PATH /etc/snort/rules include $RULE_PATH/ping. rules ● Config config reference: bugtraq ttp: //www. securityfocus. com/bid /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 15

Rule Actions/Types Field 1 ● ● ● Alert, log, pass ● Alert – generates an alert message and then logs the packet ● Log – logs the packet ● Pass – ignores the packet Activate, dynamic ● Activate – sends an alert and then turns on a dynamic rule ● Dynamic – idle until activated and then acts as a log rule User defined rule types /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 16

Protocols Field 2 ● tcp, udp, icmp, ip ● ● Todate arp, igrp, gre, ospf, rip, etc. ● The distant future /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 17

Addresses Fields 3 & 5 ● Usual dotted decimal notation with mask indicated ● ● 192. 16. 13. 0/24 Dereferenced variable ● $HOME_NET ● Keyword any ● List [192. 16. 13. 0/24, 10. 1. 1. 0/24] ● Negation !192. 16. 13. 1 /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 18

Ports Fields 4 & 6 ● ● Numerical, “any” ● 80, 21, 23, etc. ● 100: 1024 - ports 100 through 1024 ● : 600 - ports 0 through 600 ● 500: - ports greater than or equal to 500 Typical address/port fields !192. 16. 13. 0/24 any -> 192. 16. 13. 0/24 111 /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 19

Rule Options Key words: - msg - ttl - tos - id - fragbits - dsize - flags - seq - ack - itype - sid - rev - ip_proto - reference prints a message in the log test the ip header's ttl value test the tos field test the ip header's id field test the fragmentation bits test the packet's payload size test tcp flags test the sequence number for a specific value test the ack bit for set or clear test icmp type snort rule for id rule revision number ip header's protocol number external attack /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 20

Options Examples ● msg – Puts a message in the log record to identify the snort rule msg: “SYN packet malformed”; ● ttl – Tests for a specific ttl value ttl: “ 127”; ● dsize – Tests for a specific size of the packet, >, <, <> dsize: “ 400<>500”; /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 21

Options Examples cont'd ● fragbits – Tests for configuration of the IP dgram frag bits RB, MF, DF (reserved bit, more frags bit, do not frag bit) modifiers: + all have to match * any have to match ! match if bits are not set fragbits: R+; /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 22

Options Examples cont'd ● content – Tests for specific content within the payload packet Binary data enclosed by “|. . . |” ASCII data enclosed by “. . . “ ! tests that the content does not contain the string content: “|90 CB C 0 FF FFF|/bin/sh”; content: !”GET”; /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 23

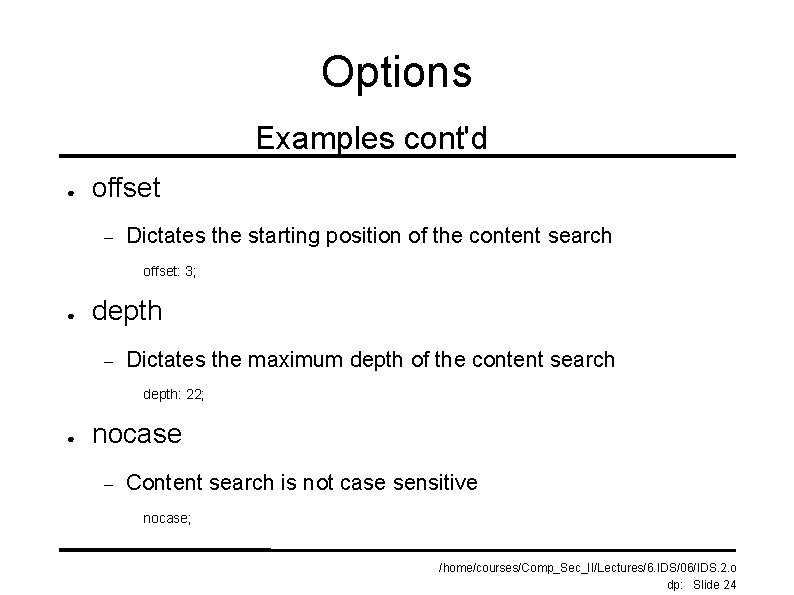
Options Examples cont'd ● offset – Dictates the starting position of the content search offset: 3; ● depth – Dictates the maximum depth of the content search depth: 22; ● nocase – Content search is not case sensitive nocase; /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 24

Options Examples cont'd ● flags – Tests for TCP flags for a match F, S, R, P, A, U, 2, 1, 0 1 & 2 are the reserved bits in the flag octet 0 no flag is set ! tests that the content does not contain the string modifiers: + all have to match * any have to match ! match if bits are not set flags: SF; /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 25

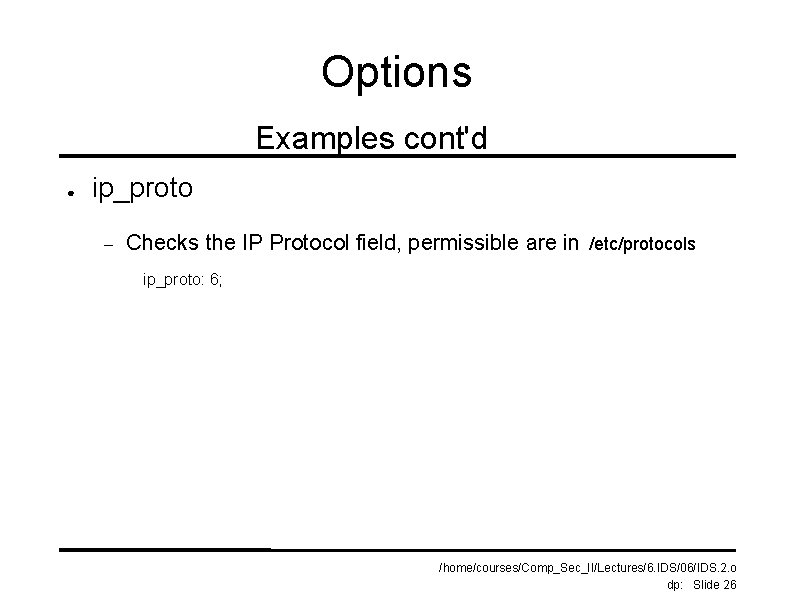
Options Examples cont'd ● ip_proto – Checks the IP Protocol field, permissible are in /etc/protocols ip_proto: 6; /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 26

# # # # # /etc/protocols: $Id: protocols, v 1. 3 2001/07/07 07: 15 nalin Exp $ Internet (IP) protocols from: @(#)protocols 5. 1 (Berkeley) 4/17/89 Updated for Net. BSD based on RFC 1340, Assigned Numbers (July 1992). See also http: //www. iana. org/assignments/protocol-numbers ip 0 #hopopt icmp 1 igmp 2 ggp 3 ipencap st 5 tcp 6 cbt 7 egp 8 igp 9 bbn-rcc nvp 11 pup 12 argus emcon xnet 15 chaos udp 17 mux 18 dcn 19 hmp 20 prm 21 IP 0 HOPOPT ICMP IGMP GGP 4 IP-ENCAP ST TCP CBT EGP IGP 10 BBN-RCC-MON NVP-II PUP 13 ARGUS 14 EMCON XNET 16 CHAOS UDP MUX DCN-MEAS HMP PRM # internet protocol, pseudo protocol number # hop-by-hop options for ipv 6 # internet control message protocol # internet group management protocol # gateway-gateway protocol # IP encapsulated in IP (officially ``IP'') # ST datagram mode # transmission control protocol # CBT, Tony Ballardie <A. Ballardie@cs. ucl. ac. uk> # exterior gateway protocol # any private interior gateway (Cisco: for IGRP) # BBN RCC Monitoring # Network Voice Protocol # PARC universal packet protocol # ARGUS # EMCON # Cross Net Debugger # Chaos # user datagram protocol # Multiplexing protocol # DCN Measurement Subsystems # host monitoring protocol # packet radio measurement protocol

Options Examples cont'd ● classtype – Categorizes snort detects into attack classes classtype: <class name>; Listed in classification: config classtype: misc-attack; /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 28

Options Examples cont'd ● itype – Checks the value of the ICMP type field itype: 0; ● icode – Checks the value of the ICMP code field icode: 8; /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 29

Options Examples cont'd ● reference – References to external attack identification systems Bugtrack, CVE, Arachnids Mc. Afee, url reference: <id-system>, <id> reference: arach. NIDS, IDS 287; reference: bugtraq, 1387; /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 30

Options Examples cont'd ● flow – Used with TCP stream reassembly, applies to certain directions – Applies to either client or server to_client - triggers on server responses to_server – triggers on client requests from_client – triggers on client requests from_server – triggers on server responses established – triggers only on established TCP connections flow: from_server; /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 31

Rule Example Alert TCP any -> any 7070 (msg: “IDS 411/dos-realaudio”; flags: AP; content: “|fff 4 fffd 06|”; reference: arach. NIDS, IDS 411; ) /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 32

Rule Example alert udp any -> any 1434 (msg: “MS-SQL Worm propagation attempt”; content: “|04|”; depth: 1; content: ”|81 f 1 03 01 04 9 b 81 f 1 01|” content: ”sock”; content: ”send”; reference: bugtraq, 5310; reference: bugtraq, 5311; reference: url, il. nai. com/vil/content/v_99992. htm; classtype: misc-attack; sid: 2003; rev: 2; ) /home/courses/Comp_Sec_II/Lectures/6. IDS/06/IDS. 2. o dp: Slide 33

Final Lab Setup and configure snort. Select a rule set. Be sure to include scanning rules Start snort in NIDS mode. With your firewall up and down: Scan your system using ping scan, xmas tree scan, OS scan Check your syslog and snort logs and nmap e. g. Icmp ping scan, map returns 1. With shields up what got through and what did snort think was happening. 2. With shields down what got through and what did snort think was happening. 3. What did nmap think it saw in each case. Hand in: 1. Firewall policies 2. Firewall script with comments, especially how each policy is enforced 3. snort. conf 4. Discussion from the experiments above.