Follow the Digital Trail DRAFT All Information Confidential















- Slides: 38

Follow the Digital Trail DRAFT All Information Confidential Chinese State Sponsored Threat (CSST) Greg Hoglund HBGary, Inc Insert presenter logo here on slide master. See hidden slide 2 for directions

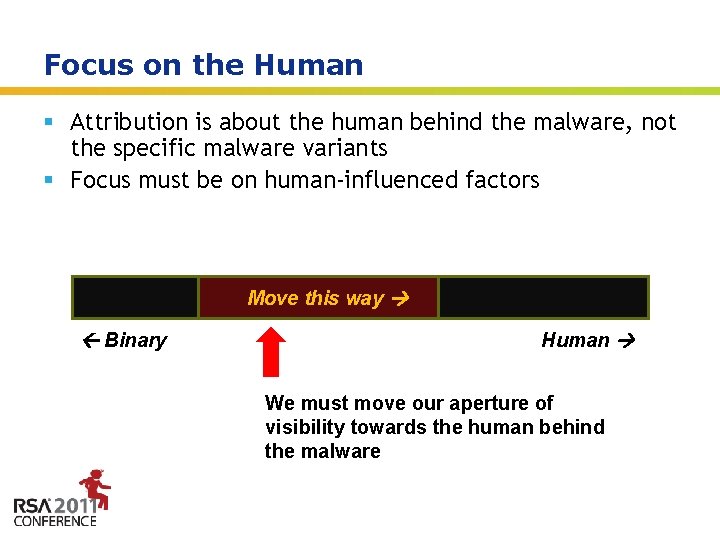
Focus on the Human § Attribution is about the human behind the malware, not the specific malware variants § Focus must be on human-influenced factors Move this way Binary Human We must move our aperture of visibility towards the human behind the malware Insert presenter logo here on slide master. See hidden slide 2 for directions

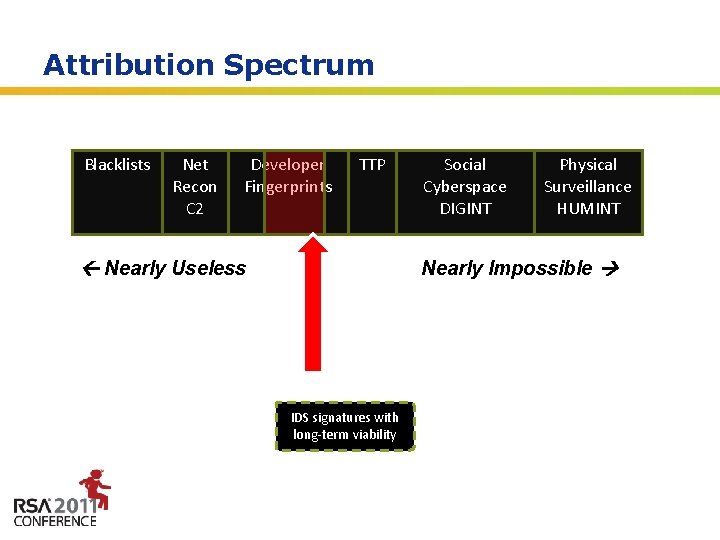
Attribution Spectrum Blacklists Net Recon C 2 Developer Fingerprints TTP Nearly Useless MD 5 Checksum of a single malware sample Social Cyberspace DIGINT Physical Surveillance HUMINT Nearly Impossible Sweet Spot IDS signatures with long-term viability SSN & Missile Coordinates of the Attacker Insert presenter logo here on slide master. See hidden slide 2 for directions

Take Ownership § You need to own the threat intelligence for your own network § Cannot rely solely on an outside vendor to supply a “magical blacklist” Outside vendors do not have this information! Insert presenter logo here on slide master. See hidden slide 2 for directions

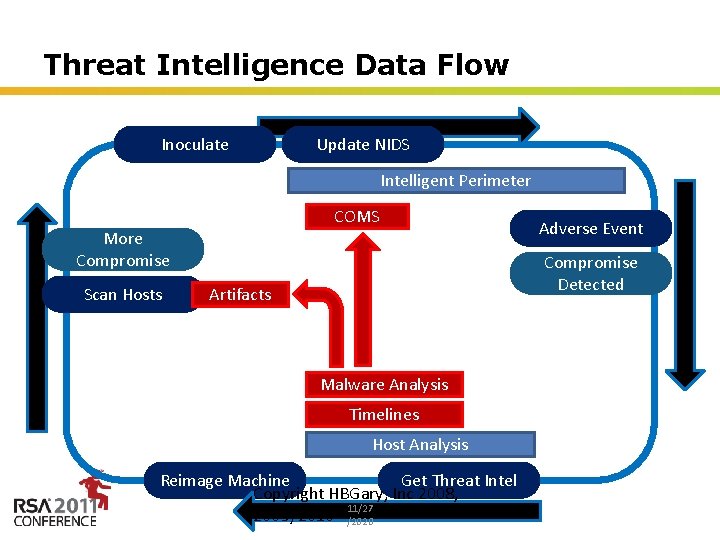
Threat Intelligence Data Flow Inoculate Update NIDS Intelligent Perimeter COMS More Compromise Scan Hosts Adverse Event Compromise Detected Artifacts Malware Analysis Timelines Host Analysis Reimage Machine Get Threat Intel Copyright HBGary, Inc 2008, 11/27 2009, 2010 /2020 Insert presenter logo here on slide master. See hidden slide 2 for directions

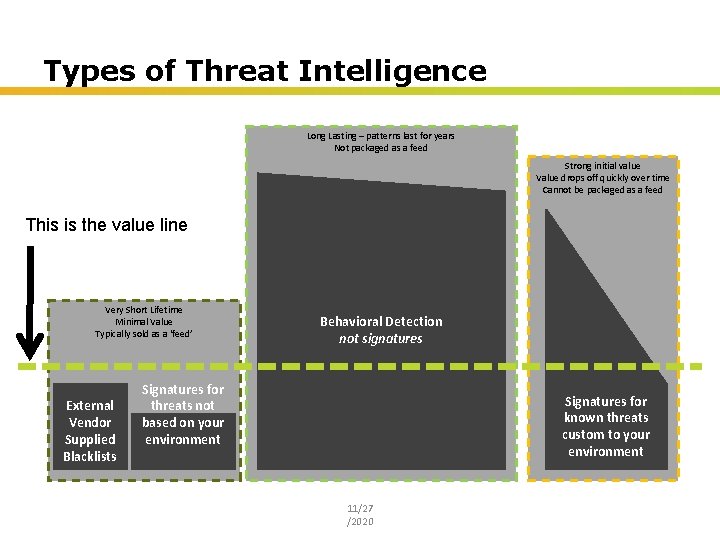
Types of Threat Intelligence Long Lasting – patterns last for years Not packaged as a feed Strong initial value Value drops off quickly over time Cannot be packaged as a feed This is the value line Very Short Lifetime Minimal Value Typically sold as a ‘feed’ External Vendor Supplied Blacklists Behavioral Detection not signatures Signatures for threats not based on your environment Signatures for known threats custom to your environment 11/27 /2020 Insert presenter logo here on slide master. See hidden slide 2 for directions

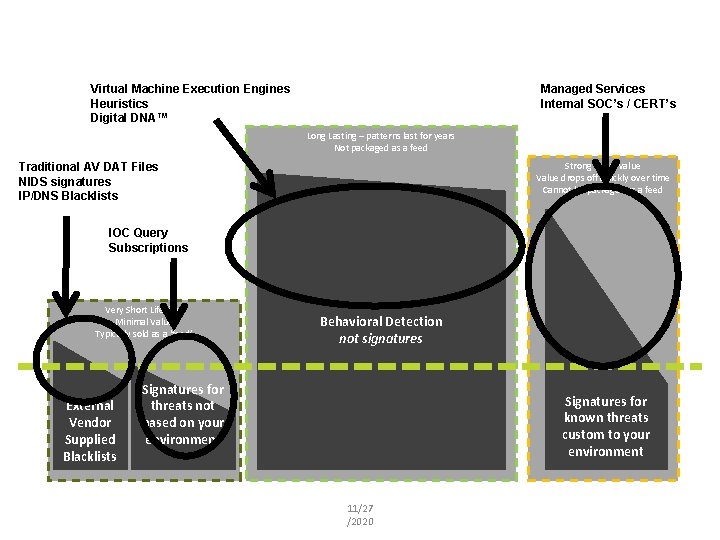
Managed Services Internal SOC’s / CERT’s Virtual Machine Execution Engines Heuristics Digital DNA™ Long Lasting – patterns last for years Not packaged as a feed Strong initial value Value drops off quickly over time Cannot be packaged as a feed Traditional AV DAT Files NIDS signatures IP/DNS Blacklists IOC Query Subscriptions Very Short Lifetime Minimal Value Typically sold as a ‘feed’ External Vendor Supplied Blacklists Behavioral Detection not signatures Signatures for threats not based on your environment Signatures for known threats custom to your environment 11/27 /2020 Insert presenter logo here on slide master. See hidden slide 2 for directions

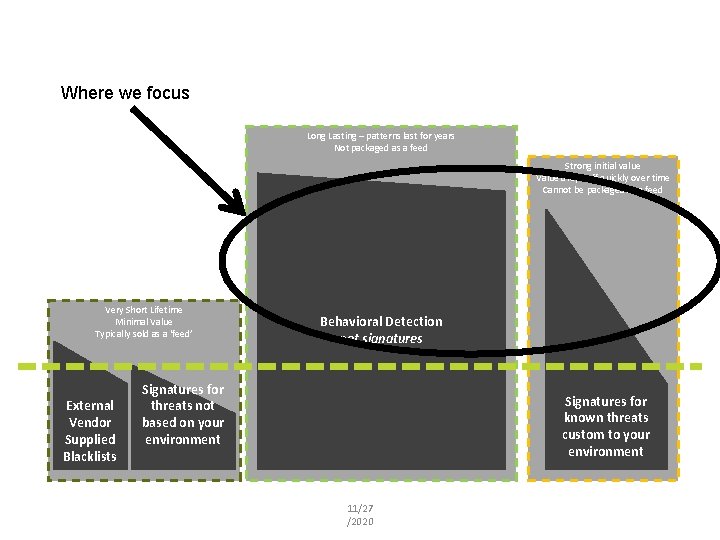
Where we focus Long Lasting – patterns last for years Not packaged as a feed Strong initial value Value drops off quickly over time Cannot be packaged as a feed Very Short Lifetime Minimal Value Typically sold as a ‘feed’ External Vendor Supplied Blacklists Behavioral Detection not signatures Signatures for threats not based on your environment Signatures for known threats custom to your environment 11/27 /2020 Insert presenter logo here on slide master. See hidden slide 2 for directions

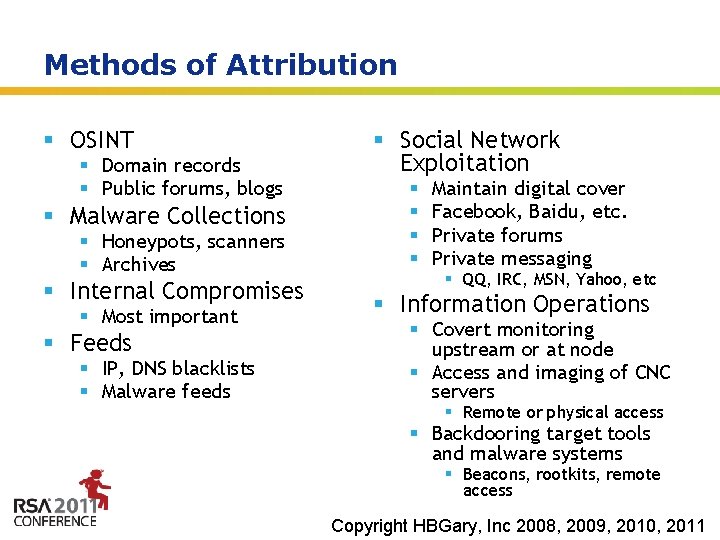
Methods of Attribution § OSINT § Domain records § Public forums, blogs § Malware Collections § Honeypots, scanners § Archives § Internal Compromises § Most important § Feeds § IP, DNS blacklists § Malware feeds § Social Network Exploitation § § Maintain digital cover Facebook, Baidu, etc. Private forums Private messaging § QQ, IRC, MSN, Yahoo, etc § Information Operations § Covert monitoring upstream or at node § Access and imaging of CNC servers § Remote or physical access § Backdooring target tools and malware systems § Beacons, rootkits, Insert remote presenter logo access here on slide master. See hidden slide 2 for directions Copyright HBGary, Inc 2008, 2009, 2010, 2011

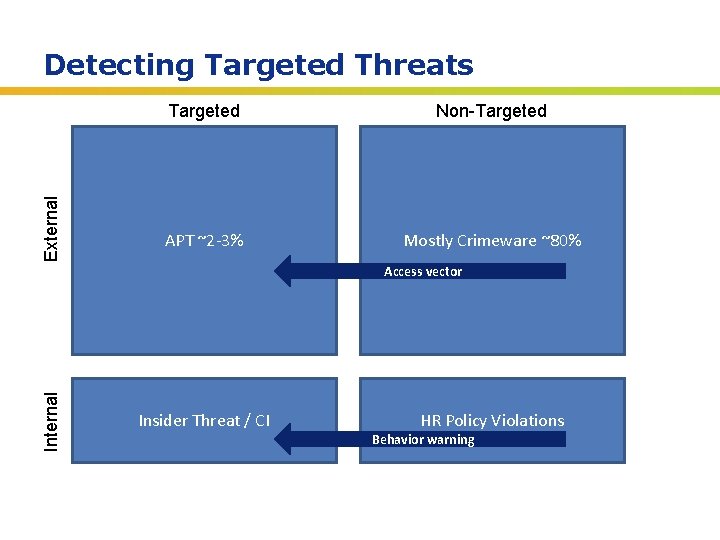
External Detecting Targeted Threats Targeted Non-Targeted APT ~2 -3% Mostly Crimeware ~80% Internal Access vector Insider Threat / CI HR Policy Violations Behavior warning Insert presenter logo here on slide master. See hidden slide 2 for directions

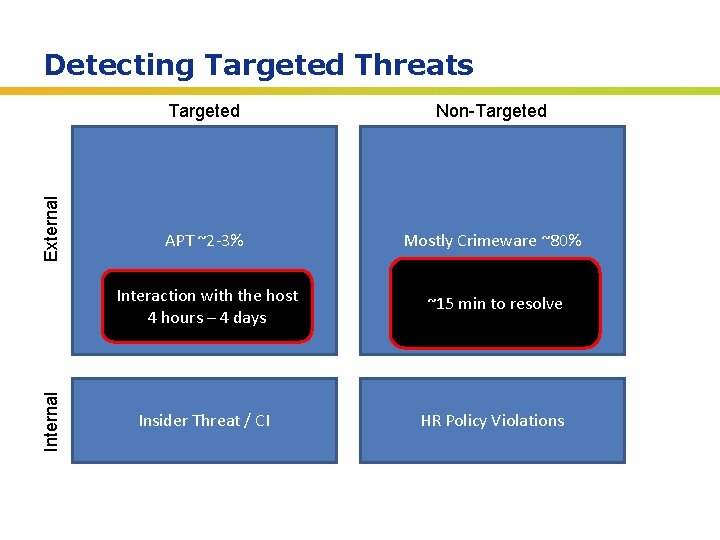
Internal External Detecting Targeted Threats Targeted Non-Targeted APT ~2 -3% Mostly Crimeware ~80% Interaction with the host 4 hours – 4 days ~15 min to resolve Insider Threat / CI HR Policy Violations Insert presenter logo here on slide master. See hidden slide 2 for directions

Formerly known as APT CHINESE STATE SPONSORED THREAT Insert presenter logo here on slide master. See hidden slide 2 for directions Copyright HBGary, Inc 2008, 2009, 2010, 2011

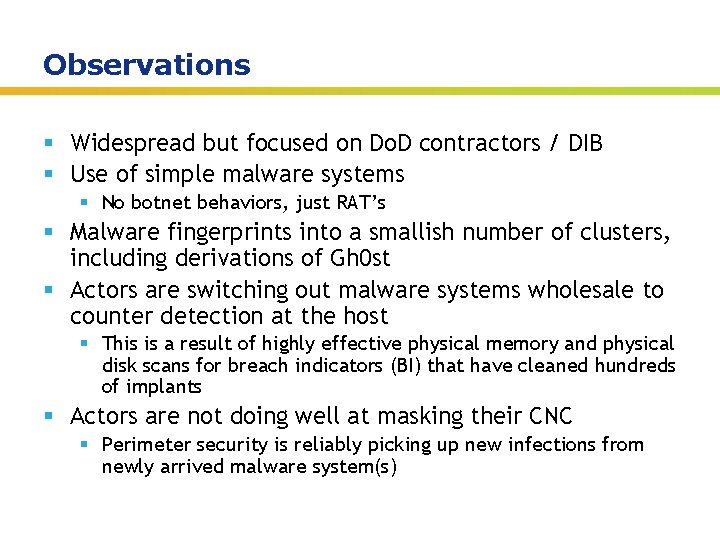
Observations § Widespread but focused on Do. D contractors / DIB § Use of simple malware systems § No botnet behaviors, just RAT’s § Malware fingerprints into a smallish number of clusters, including derivations of Gh 0 st § Actors are switching out malware systems wholesale to counter detection at the host § This is a result of highly effective physical memory and physical disk scans for breach indicators (BI) that have cleaned hundreds of implants § Actors are not doing well at masking their CNC § Perimeter security is reliably picking up new infections from newly arrived malware system(s) Insert presenter logo here on slide master. See hidden slide 2 for directions

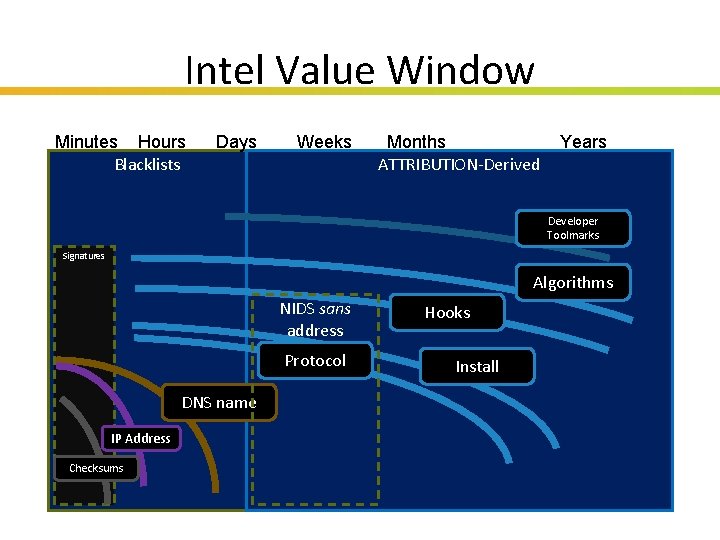
Intel Value Window Lifetime Minutes Hours Blacklists Days Weeks Months ATTRIBUTION-Derived Years Developer Toolmarks Signatures Algorithms NIDS sans address Protocol Hooks Install DNS name IP Address Checksums Insert presenter logo here on slide master. See hidden slide 2 for directions

Case Study OPERATION TOJO Insert presenter logo here on slide master. See hidden slide 2 for directions Copyright HBGary, Inc 2008, 2009, 2010, 2011

Observed § Operating since 2007, possibly as early as 2004 § TTP’s are straight out of ‘Hacking Exposed’ § Some malware uses code-snippits from “Inside Windows 2000” published in 2000 § Some malware is derived from gh 0 st § Some CNC is directly tied to Tibetan attacks § Some CNC is known to have attacked Do. D contractors as early as 2007 § Some malware strains detected as early as 2004 Insert presenter logo here on slide master. See hidden slide 2 for directions

Beliefs § More than one actor involved § Actors are involved in hacker underground even though they also appear to be IO § TTP’s are relatively consistent § CNC scheme and COVCOM have poor OPSEC § Several key servers identified that are believed to contain a wealth of forensic evidence § They are aware of Title 18 § Somewhere between 20 -40 defense contractors currently compromised by threat actor Insert presenter logo here on slide master. See hidden slide 2 for directions

TTP’s § Extensive use of hash cracking, rainbow tables § PTH toolkit and friends § Entrenchment strategy § Multiple backup plans, backup CNC protocol & servers both § Avoidance of packing, rootkits, etc. § Staging data for exfil § Watch out for 3 -day weekends Insert presenter logo here on slide master. See hidden slide 2 for directions

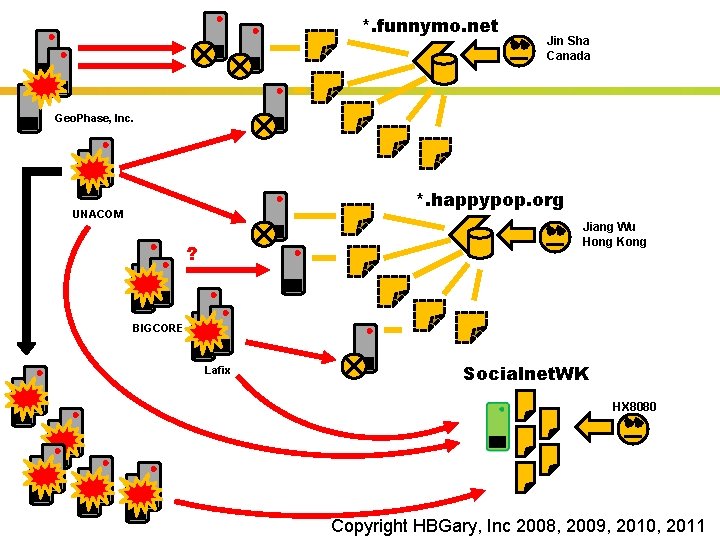
*. funnymo. net Jin Sha Canada Geo. Phase, Inc. *. happypop. org UNACOM Jiang Wu Hong Kong ? BIGCORE Lafix Socialnet. WK HX 8080 Insert presenter logo here on slide master. See hidden slide 2 for directions Copyright HBGary, Inc 2008, 2009, 2010, 2011

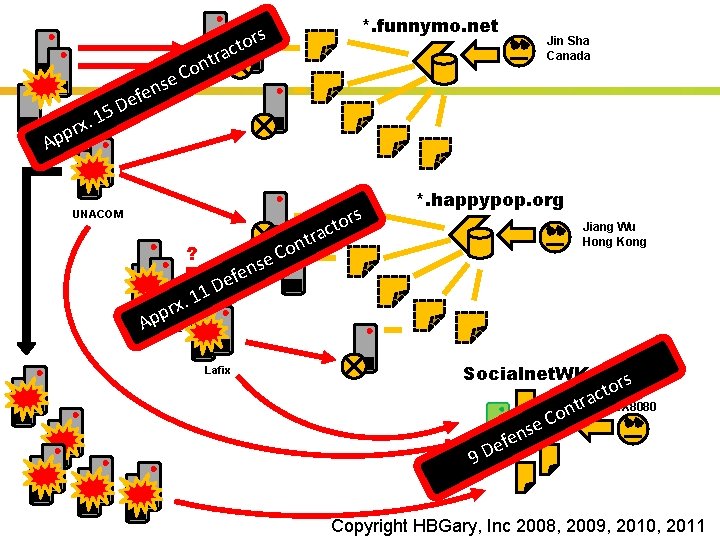
*. funnymo. net s tor c tra on C e 5 1. x ppr Jin Sha Canada ns e f e D Geo. Phase, Inc. A UNACOM ? e 1 1. x pr p A BIGCORE ns e f e rs t n o C to rac *. happypop. org Jiang Wu Hong Kong D Lafix Socialnet. WK se n e ef r t n o C s or t c a HX 8080 9 D Insert presenter logo here on slide master. See hidden slide 2 for directions Copyright HBGary, Inc 2008, 2009, 2010, 2011

OSINT § The names used to register domains may be false § In one case, the registered email does appear in use with QQ and other social networking sites in CN, but this could have been a compromised account § One account is being used on a chinese haching forum § Many of the accounts are hidden behind name registrar privacy and/or using dynamic DNS § GODADDY, etc Insert presenter logo here on slide master. See hidden slide 2 for directions

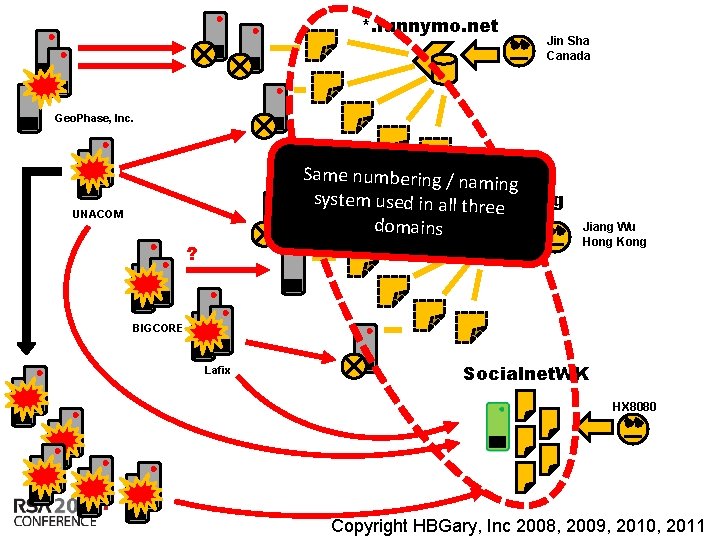
*. funnymo. net Jin Sha Canada Geo. Phase, Inc. Same numbering / namin g system used *. happypop. org in all three domains UNACOM ? Jiang Wu Hong Kong BIGCORE Lafix Socialnet. WK HX 8080 Insert presenter logo here on slide master. See hidden slide 2 for directions Copyright HBGary, Inc 2008, 2009, 2010, 2011

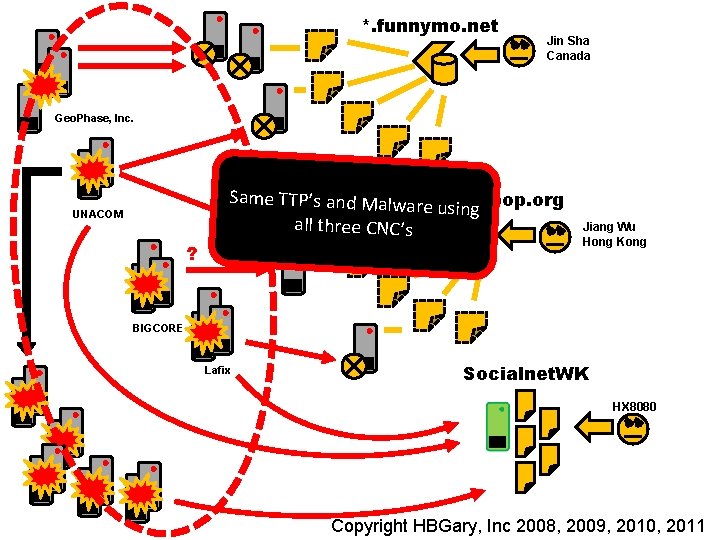
*. funnymo. net Jin Sha Canada Geo. Phase, Inc. UNACOM ? Same TTP’s and Malwa*. happypop. org re using all three CNC’s Jiang Wu Hong Kong BIGCORE Lafix Socialnet. WK HX 8080 Insert presenter logo here on slide master. See hidden slide 2 for directions Copyright HBGary, Inc 2008, 2009, 2010, 2011

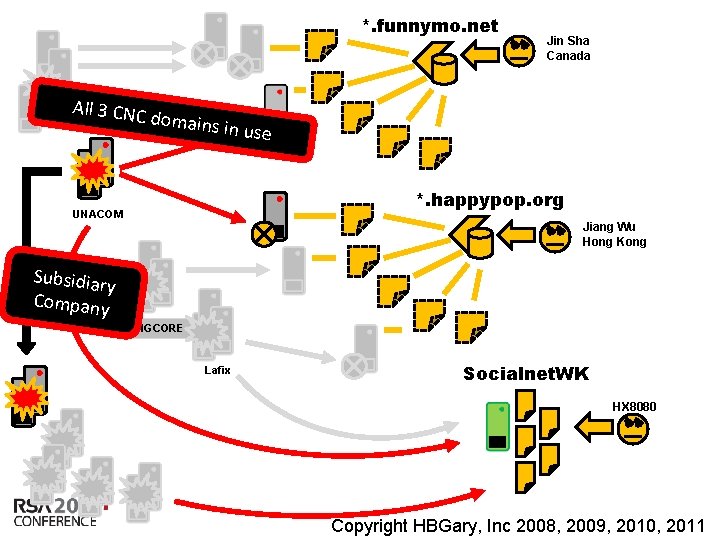
*. funnymo. net All 3 CNC d Geo. Phase, Inc. omains in Jin Sha Canada use *. happypop. org UNACOM Jiang Wu Hong Kong Subsidiar y Company BIGCORE Lafix Socialnet. WK HX 8080 Insert presenter logo here on slide master. See hidden slide 2 for directions Copyright HBGary, Inc 2008, 2009, 2010, 2011

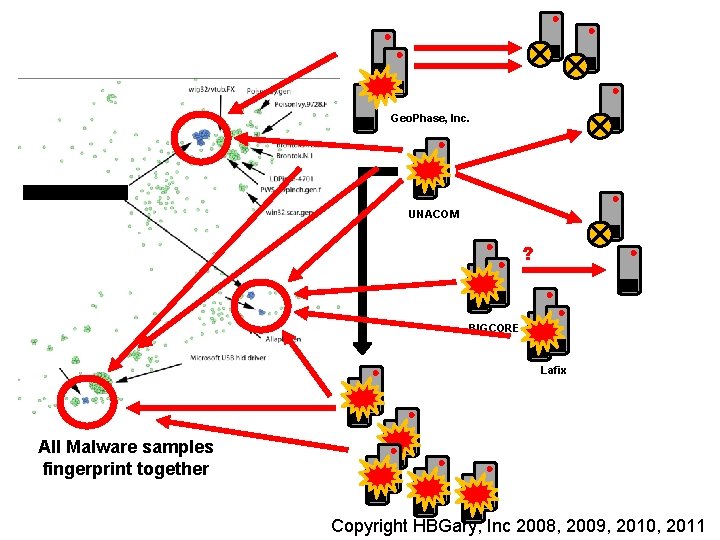
Geo. Phase, Inc. UNACOM ? BIGCORE Lafix All Malware samples fingerprint together Insert presenter logo here on slide master. See hidden slide 2 for directions Copyright HBGary, Inc 2008, 2009, 2010, 2011

Beliefs § Developers are custom building agent payloads § Developers are using a smallish set of source bases for their custom malware § BO 2 k, Gh 0 st, etc § Operators are also using commercial packages § Poison. Ivy, VMProtect, PTH toolkit, etc. Insert presenter logo here on slide master. See hidden slide 2 for directions

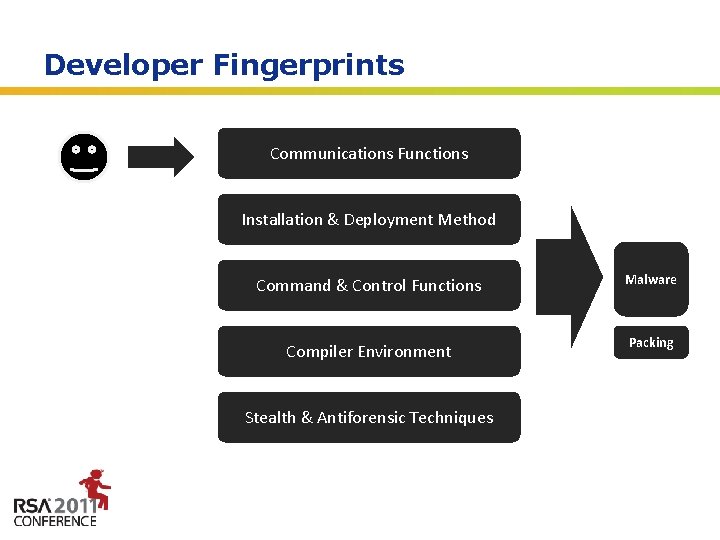
Developer Fingerprints Communications Functions Developer Installation & Deployment Method Sample Command & Control Functions Malware Compiler Environment Packing Stealth & Antiforensic Techniques Insert presenter logo here on slide master. See hidden slide 2 for directions

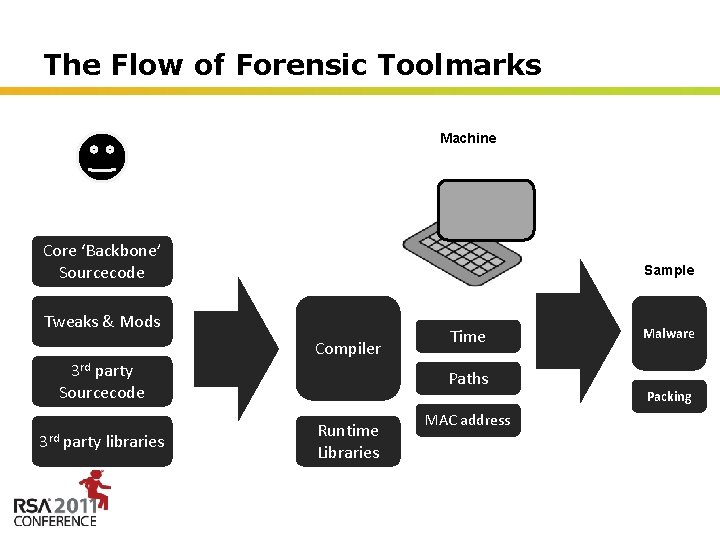
The Flow of Forensic Toolmarks Machine Developer Core ‘Backbone’ Sourcecode Sample Tweaks & Mods Compiler 3 rd party Sourcecode 3 rd party libraries Time Paths Runtime Libraries Malware Packing MAC address Insert presenter logo here on slide master. See hidden slide 2 for directions

Rule #1 § The human is lazy § The use kits and systems to change checksums, hide from A/V, and get around IDS § They DON’T rewrite their code every morning Insert presenter logo here on slide master. See hidden slide 2 for directions

Rule #2 § Most attackers are focused on rapid reaction to network -level filtering and black-holes § Multiple Dyn. DNS C 2 servers, multiple C 2 protocols, obfuscation of network traffic § They are not-so-focused on host level stealth § Most malware is simple in nature, and works great § Enterprises rely on A/V for host, and A/V doesn’t work, and the attackers know this Insert presenter logo here on slide master. See hidden slide 2 for directions

Rule #3 § Physical memory is King § Once executing in memory, code has to be revealed, data has to be decrypted Insert presenter logo here on slide master. See hidden slide 2 for directions

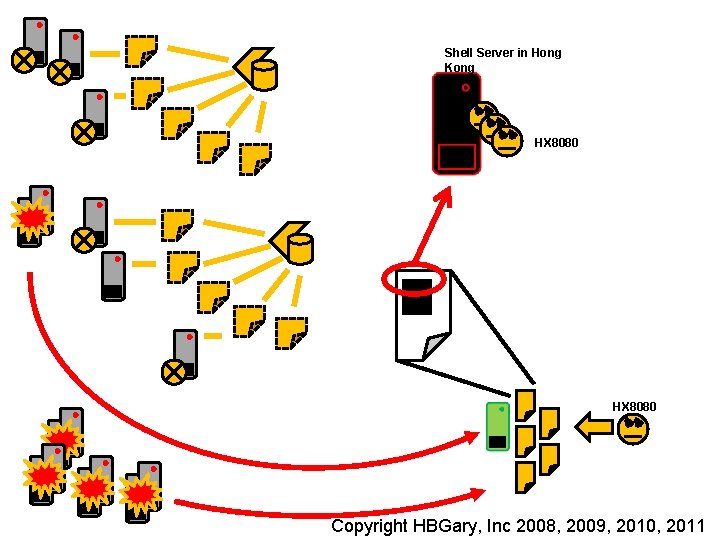
Shell Server in Hong Kong HX 8080 Insert presenter logo here on slide master. See hidden slide 2 for directions Copyright HBGary, Inc 2008, 2009, 2010, 2011

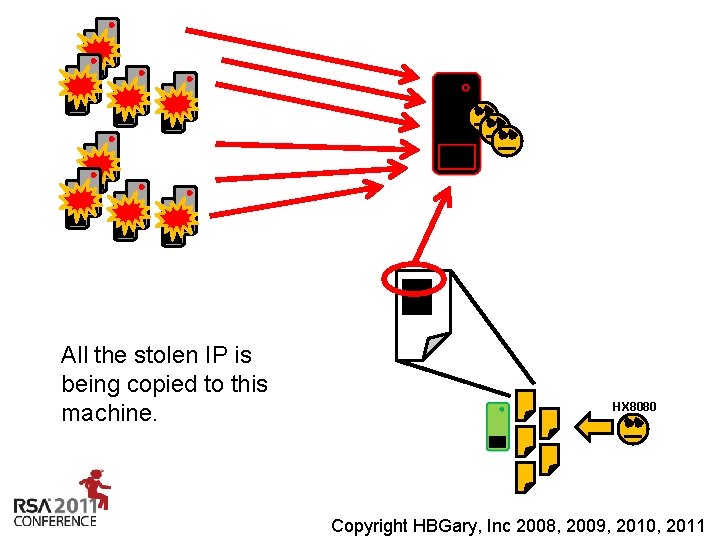
All the stolen IP is being copied to this machine. HX 8080 Insert presenter logo here on slide master. See hidden slide 2 for directions Copyright HBGary, Inc 2008, 2009, 2010, 2011

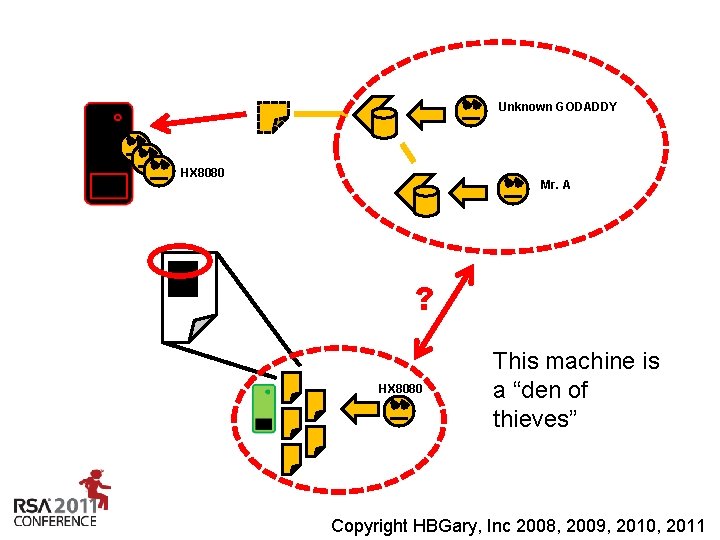
Unknown GODADDY HX 8080 Mr. A ? HX 8080 This machine is a “den of thieves” Insert presenter logo here on slide master. See hidden slide 2 for directions Copyright HBGary, Inc 2008, 2009, 2010, 2011

Tojo on Lock § There about 50 BI’s that detect almost all of Tojo’s malware or tools § There a handful of signatures, DNS names, and IP’s that detect almost all of Tojo’s CNC § We have three physical human targets that can be monitored § We have over a dozen physical CNC servers § We have one physical server in Hong Kong that appears at the center of it all Insert presenter logo here on slide master. See hidden slide 2 for directions

Conclusion § By focusing on attribution we have significantly increased our ability to detect Tojo § This, when combined with the proper technology, enables near-realtime incident response 36 Insert presenter logo here on slide master. See hidden slide 2 for directions

Predictions § Perimeterless network, wireless, opaque cloudbox § The end-node is more important than ever § Social networking for CNC § Twitter, Facebook, forums on well known magazine sites, etc. § Convergence of botnets and APT § Marketplace for information and access evolves § Re-emergence of the rootkit § Security companies are moving towards behavioral detection because signatures don’t work. This means malware will have to be stealthy again. § Continued focus on rich media exploitation 37 Insert presenter logo here on slide master. See hidden slide 2 for directions

Thank You HBGary, Inc. www. hbgary. com Greg Hoglund Insert presenter logo here on slide master. See hidden slide 2 for directions