Computer and Information Security Chapter 5 Hash Functions

![Chapter 5: Hash Functions++ “I'm sure [my memory] only works one way. ” Alice Chapter 5: Hash Functions++ “I'm sure [my memory] only works one way. ” Alice](https://slidetodoc.com/presentation_image/0e6bc82f7bc8e005272f41d1106ed9f6/image-2.jpg)



















































- Slides: 97

Computer and Information Security Chapter 5 Hash Functions 1
![Chapter 5 Hash Functions Im sure my memory only works one way Alice Chapter 5: Hash Functions++ “I'm sure [my memory] only works one way. ” Alice](https://slidetodoc.com/presentation_image/0e6bc82f7bc8e005272f41d1106ed9f6/image-2.jpg)
Chapter 5: Hash Functions++ “I'm sure [my memory] only works one way. ” Alice remarked. “I can't remember things before they happen. ” “It's a poor sort of memory that only works backwards, ” the Queen remarked. “What sort of things do you remember best? " Alice ventured to ask. “Oh, things that happened the week after next, " the Queen replied in a careless tone. Lewis Carroll, Through the Looking Glass Part 1 Cryptography 2

Chapter 5: Hash Functions++ A boat, beneath a sunny sky Lingering onward dreamily In an evening of July Children three that nestle near, Eager eye and willing ear, . . . Lewis Carroll, Through the Looking Glass Part 1 Cryptography 3

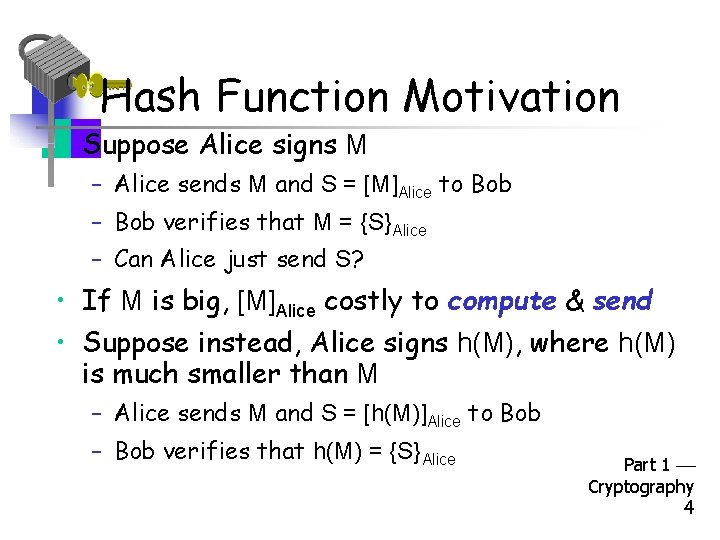
Hash Function Motivation • Suppose Alice signs M – Alice sends M and S = [M]Alice to Bob – Bob verifies that M = {S}Alice – Can Alice just send S? • If M is big, [M]Alice costly to compute & send • Suppose instead, Alice signs h(M), where h(M) is much smaller than M – Alice sends M and S = [h(M)]Alice to Bob – Bob verifies that h(M) = {S}Alice Part 1 Cryptography 4

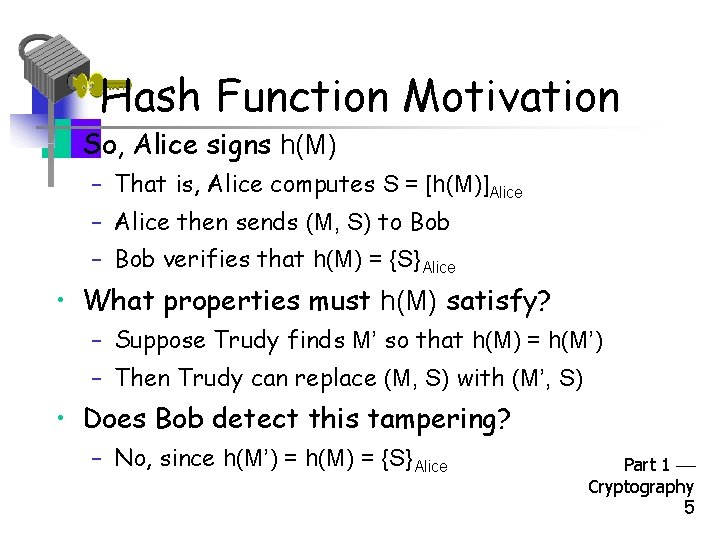
Hash Function Motivation • So, Alice signs h(M) – That is, Alice computes S = [h(M)]Alice – Alice then sends (M, S) to Bob – Bob verifies that h(M) = {S}Alice • What properties must h(M) satisfy? – Suppose Trudy finds M’ so that h(M) = h(M’) – Then Trudy can replace (M, S) with (M’, S) • Does Bob detect this tampering? – No, since h(M’) = h(M) = {S}Alice Part 1 Cryptography 5

Crypto Hash Function • Crypto hash function h(x) must provide – Compression output length is small – Efficiency h(x) easy to compute for any x – One-way given a value y it is infeasible to find an x such that h(x) = y – Weak collision resistance given x and h(x), infeasible to find y x such that h(y) = h(x) – Strong collision resistance infeasible to find any x and y, with x y such that h(x) = h(y) • Lots of collisions exist, but hard to find any Part 1 Cryptography 6

Pre-Birthday Problem • Suppose N people in a room • How large must N be before the probability someone has same birthday as me is 1/2 ? – Solve: 1/2 = 1 (364/365)N for N – We find N = 253 Part 1 Cryptography 7

Birthday Problem • How many people must be in a room before probability is 1/2 that any two (or more) have same birthday? – 1 365/365 364/365 (365 N+1)/365 – Set equal to 1/2 and solve: N = 23 • Surprising? A paradox? • Maybe not: “Should be” about sqrt(365) since we compare all pairs x and y – And there are 365 possible birthdays Part 1 Cryptography 8

Of Hashes and Birthdays • If h(x) is N bits, 2 N different hash values are possible • So, if you hash about 2 N/2 random values then you expect to find a collision – Since sqrt(2 N) = 2 N/2 • Implication: secure N bit symmetric key requires 2 N 1 work to “break” while secure N bit hash requires 2 N/2 work to “break” – Exhaustive search attacks, that is Part 1 Cryptography 9

Non-crypto Hash (1) • Data X = (X 0, X 1, X 2, …, Xn-1), each Xi is a byte • Define h(X) = X 0+X 1+X 2+…+Xn-1 • Is this a secure cryptographic hash? • Example: X = (1010, 00001111) • Hash is h(X) = 10111001 • If Y = (00001111, 1010) then h(X) = h(Y) • Easy to find collisions, so not secure… Part 1 Cryptography 10

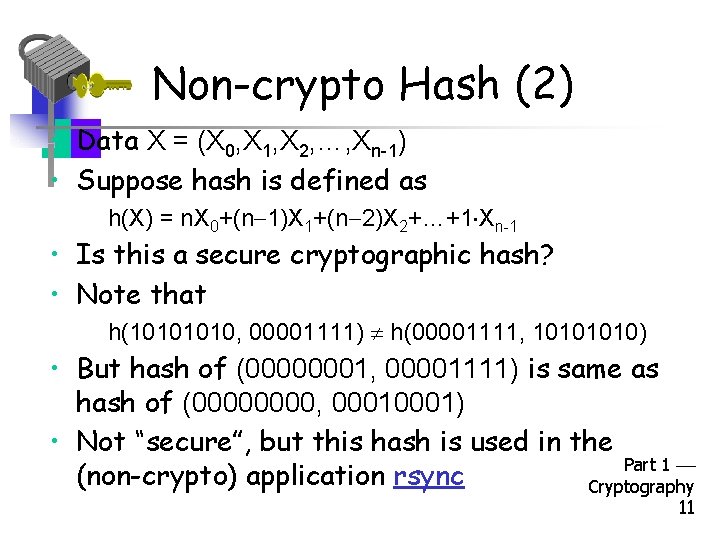
Non-crypto Hash (2) • Data X = (X 0, X 1, X 2, …, Xn-1) • Suppose hash is defined as h(X) = n. X 0+(n 1)X 1+(n 2)X 2+…+1 Xn-1 • Is this a secure cryptographic hash? • Note that h(1010, 00001111) h(00001111, 1010) • But hash of (00000001, 00001111) is same as hash of (0000, 0001) • Not “secure”, but this hash is used in the Part 1 (non-crypto) application rsync Cryptography 11

Non-crypto Hash (3) • Cyclic Redundancy Check (CRC) • Essentially, CRC is the remainder in a long division calculation • Good for detecting burst errors – Random errors unlikely to yield a collision • But easy to construct collisions • CRC has been mistakenly used where crypto integrity check is required (e. g. , WEP) Part 1 Cryptography 12

Popular Crypto Hashes • MD 5 invented by Rivest – 128 bit output – Note: MD 5 collisions easy to find • SHA-1 A U. S. government standard, inner workings similar to MD 5 – 160 bit output • Many other hashes, but MD 5 and SHA-1 are the most widely used • Hashes work by hashing message in blocks Part 1 Cryptography 13

Crypto Hash Design • Desired property: avalanche effect – Change to 1 bit of input should affect about half of output bits • Crypto hash functions consist of some number of rounds • Want security and speed – Avalanche effect after few rounds – But simple rounds • Analogous to design of block ciphers Part 1 Cryptography 14

Tiger Hash • “Fast and strong” • Designed by Ross Anderson and Eli Biham leading cryptographers • Design criteria – Secure – Optimized for 64 -bit processors – Easy replacement for MD 5 or SHA-1 Part 1 Cryptography 15

Tiger Hash • Like MD 5/SHA-1, input divided into 512 bit blocks (padded) • Unlike MD 5/SHA-1, output is 192 bits (three 64 -bit words) – Truncate output if replacing MD 5 or SHA-1 • Intermediate rounds are all 192 bits • 4 S-boxes, each maps 8 bits to 64 bits • A “key schedule” is used Part 1 Cryptography 16

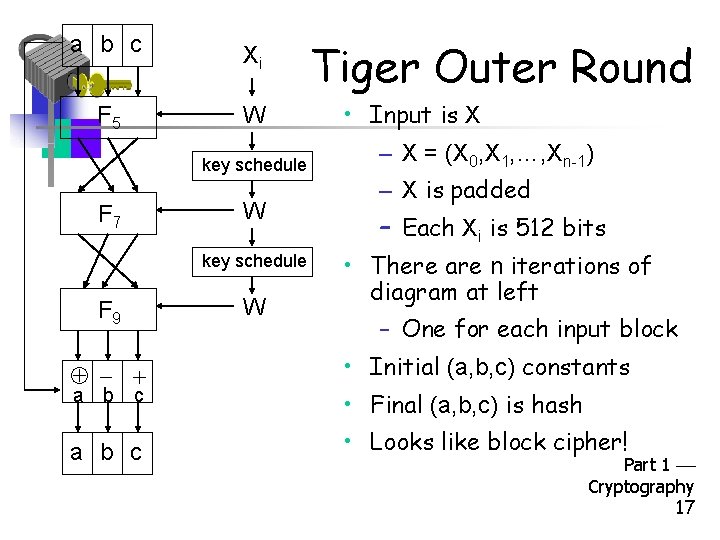
a b c Xi F 5 W key schedule F 7 W key schedule F 9 W Tiger Outer Round • Input is X – X = (X 0, X 1, …, Xn-1) – X is padded – Each Xi is 512 bits • There are n iterations of diagram at left – One for each input block • Initial (a, b, c) constants a b c • Looks like block cipher! a b c • Final (a, b, c) is hash Part 1 Cryptography 17

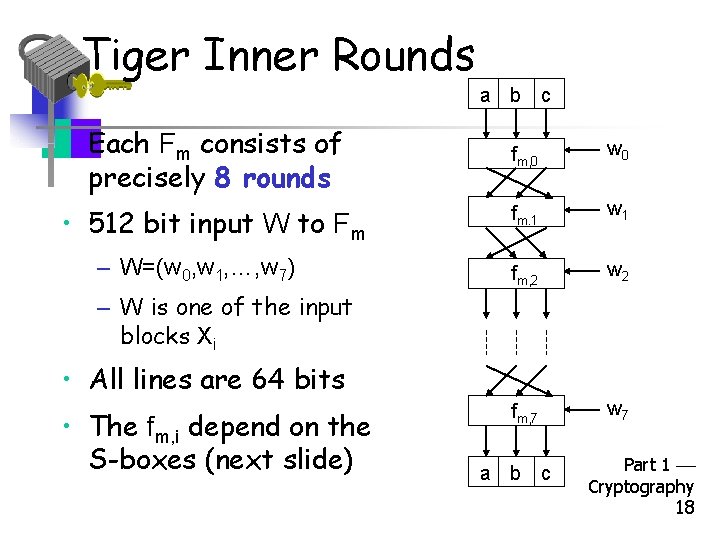
Tiger Inner Rounds a b c • Each Fm consists of precisely 8 rounds fm, 0 w 0 • 512 bit input W to Fm fm. 1 w 1 fm, 2 w 2 fm, 7 w 7 – W=(w 0, w 1, …, w 7) – W is one of the input blocks Xi • All lines are 64 bits • The fm, i depend on the S-boxes (next slide) a b c Part 1 Cryptography 18

Tiger Hash: One Round • Each fm, i is a function of a, b, c, wi and m – Input values of a, b, c from previous round – And wi is 64 -bit block of 512 bit W – Subscript m is multiplier – And c = (c 0, c 1, …, c 7) • Output of fm, i is – c = c wi – a = a (S 0[c 0] S 1[c 2] S 2[c 4] S 3[c 6]) – b = b + (S 3[c 1] S 2[c 3] S 1[c 5] S 0[c 7]) – b=b m • Each Si is S-box: 8 bits mapped to 64 bits Part 1 Cryptography 19

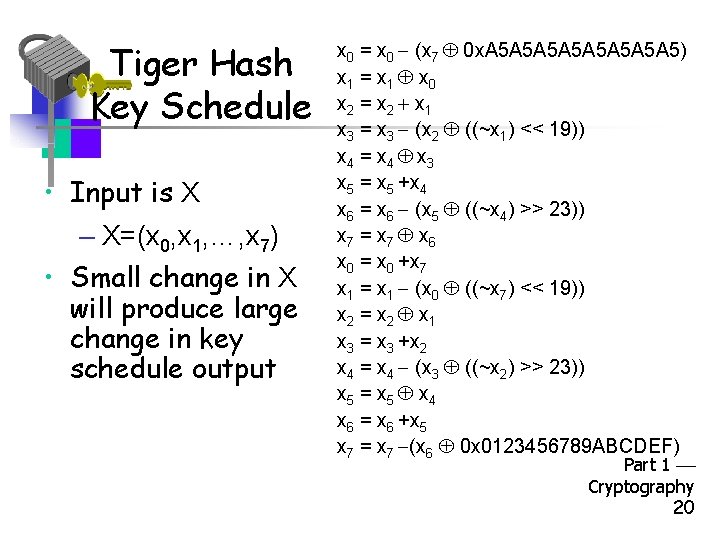
Tiger Hash Key Schedule • Input is X – X=(x 0, x 1, …, x 7) • Small change in X will produce large change in key schedule output x 0 = x 0 (x 7 0 x. A 5 A 5 A 5 A 5) x 1 = x 1 x 0 x 2 = x 2 x 1 x 3 = x 3 (x 2 ((~x 1) << 19)) x 4 = x 4 x 3 x 5 = x 5 +x 4 x 6 = x 6 (x 5 ((~x 4) >> 23)) x 7 = x 7 x 6 x 0 = x 0 +x 7 x 1 = x 1 (x 0 ((~x 7) << 19)) x 2 = x 2 x 1 x 3 = x 3 +x 2 x 4 = x 4 (x 3 ((~x 2) >> 23)) x 5 = x 5 x 4 x 6 = x 6 +x 5 x 7 = x 7 (x 6 0 x 0123456789 ABCDEF) Part 1 Cryptography 20

Tiger Hash Summary (1) • Hash and intermediate values are 192 bits • 24 (inner) rounds – S-boxes: Claimed that each input bit affects a, b and c after 3 rounds – Key schedule: Small change in message affects many bits of intermediate hash values – Multiply: Designed to ensure that input to S-box in one round mixed into many S-boxes in next • S-boxes, key schedule and multiply together designed to ensure strong avalanche effect Part 1 Cryptography 21

Tiger Hash Summary (2) • Uses lots of ideas from block ciphers – S-boxes – Multiple rounds – Mixed mode arithmetic • At a higher level, Tiger employs – Confusion – Diffusion Part 1 Cryptography 22

Authentication • In addition to confidentiality, message authentication is an important security function • “A message, file, document or data is said to be authentic when it is genuine and came from its alleged source. ” • Encryption prevents against passive attacks (eavesdropping) • Message Authentication prevents against active attacks or falsification.

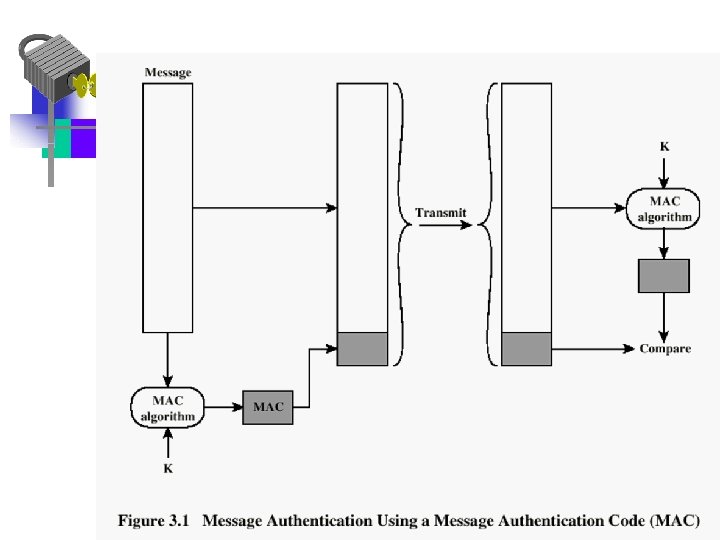
Message Authentication • Message authentication is concerned with: – protecting the integrity of a message – validating identity of originator – non-repudiation of origin (dispute resolution) • The three alternative functions used: – hash function – message encryption – message authentication code (MAC)

Message Authentication • Requirements - must be able to verify that: 1. Message came from apparent source or author 2. Contents have not been altered 3. Timeliness – that it was sent at a certain time or sequence. • Protection against active attack (falsification of data and transactions)

Approaches to Message Authentication • Authentication Using Conventional Encryption – Only the sender and receiver should share a key • Message Authentication without Message Encryption – An authentication tag is generated and appended to each message • Message Authentication Code – Calculate the MAC as a function of the message and the key. MAC = F(K, M)

Message Authentication • Using Encryption – Assume only sender and receiver share a key – Then a correctly encrypted message should be from the sender • Usually also contains error-detection code, sequence number and time stamp • Encryption alone is not suitable for authentication. Blocks could have been reordered, changing meaning


Message Authentication • Without Encryption No confidentiality is preferred when: 1. Same message is broadcast to many destinations 2. Heavy load and cannot decrypt all messages – some chosen at random 3. No danger in sending plaintext Append authentication tag to each message

Message Authentication • Message Authentication Code (MAC) – Small block of data that is appended to the message – MAC is generated by using a secret key – Assumes both parties A, B share common secret key KAB – Code is function of message and key MACM= F(KAB, M) – Message plus code are transmitted

Message Authentication Code • Recipient uses key to compute new code • If received code matches calculated code then – Receiver is sure message has not been altered – Message is from sender, since only sender shares the key – If the message includes correct sequence number, that number could not have been altered by hacker


Message Authentication Code • Different from encryption – MAC does not have to be reversible as the cipher text does in encryption – Because of mathematical properties, it is less vulnerable to being broken than encryption • 16 to 32 bit code is typical

One-way HASH function • Alternative to Message Authentication Code • Accepts a variable size message M as input and produces a fixed-size message digest H (M) as output • Unlike the MAC, a hash function does not take a secret key as input • Message digest also provides data integrity, since if bits are accidentally altered in transit, the message digest will also be in error.

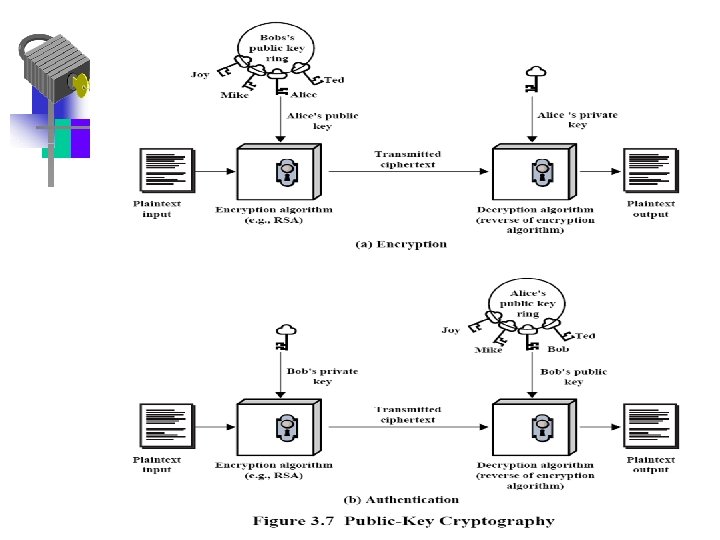
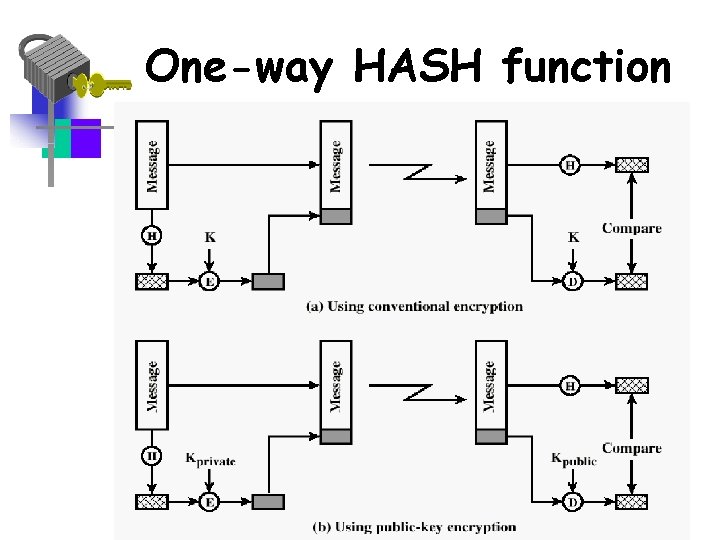
One-Way Hash Function • The message can be authenticated: • Using encryption using a shared secret key • Using public-key encryption – Also provides a digital signature – Does not require key distribution • Using a secret value

One-way HASH function

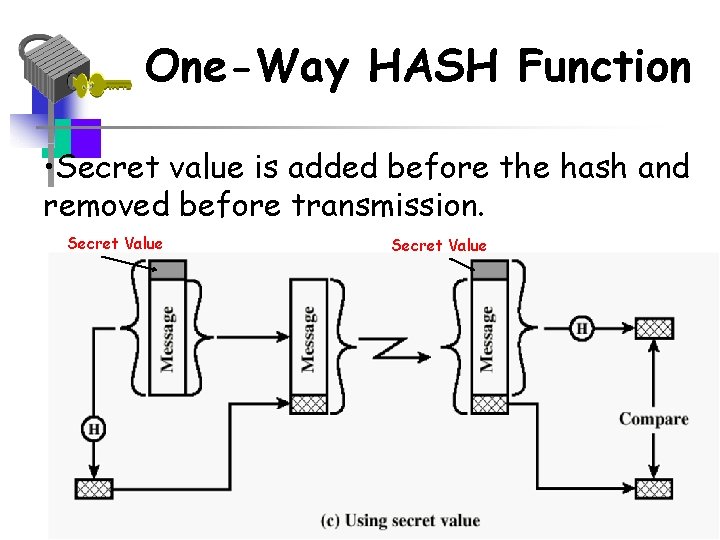
One-Way HASH Function • Secret value is added before the hash and removed before transmission. Secret Value

One-way HASH Function Advantages • Using a hash function instead of encryption has advantages: • Encryption is slow • Encryption hardware can be expensive • Encryption hardware is optimized for large data sets • An encryption algorithm may be protected by a patent

Hash Function • Condenses arbitrary message to fixed size h = H(M) • Usually assume hash function is public • Hash used to detect changes to message • Want a cryptographic hash function • computationally infeasible to find data mapping to specific hash (one-way property) • computationally infeasible to find two data to same hash (collision-free property)

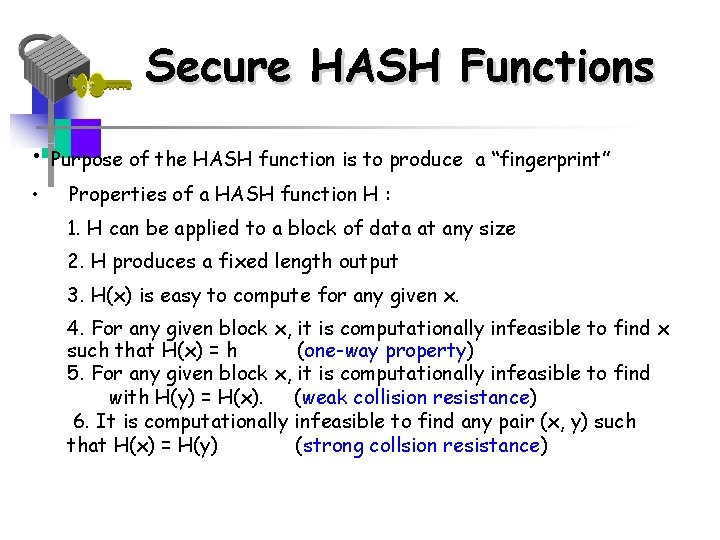
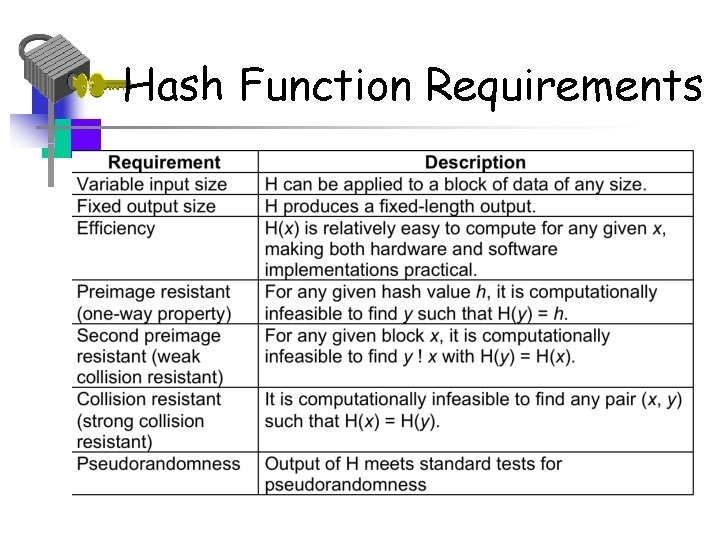
Secure HASH Functions • Purpose of the HASH function is to produce • a “fingerprint” Properties of a HASH function H : 1. H can be applied to a block of data at any size 2. H produces a fixed length output 3. H(x) is easy to compute for any given x. 4. For any given block x, it is computationally infeasible to find x such that H(x) = h (one-way property) 5. For any given block x, it is computationally infeasible to find with H(y) = H(x). (weak collision resistance) 6. It is computationally infeasible to find any pair (x, y) such that H(x) = H(y) (strong collsion resistance)

Simple Hash Function • A weak hash function satisfies the first 5 properties. • A strong hash function also satisfies the 6 th property (strong collision resistance) – Effective against the birthday attack • Message Digest provides both authentication and integrity

Simple Hash Function • A weak hash function satisfies the first 5 properties. • A strong hash function also satisfies the 6 th property (strong collision resistance) – Effective against the birthday attack • Message Digest provides both authentication and integrity

Hash Function Requirements

Security of Hash Functions • Attacking a secure hash function can be done by using cryptanalysis or brute force. • Strength of function depends on the length of the hash code produced by the algorithm. • For example: – A search machine can find a collision for 128 bit code length in 24 days – considered inadequate – With 160 bits, finding a collision might take 4000 years ( or less with today’s speeds)

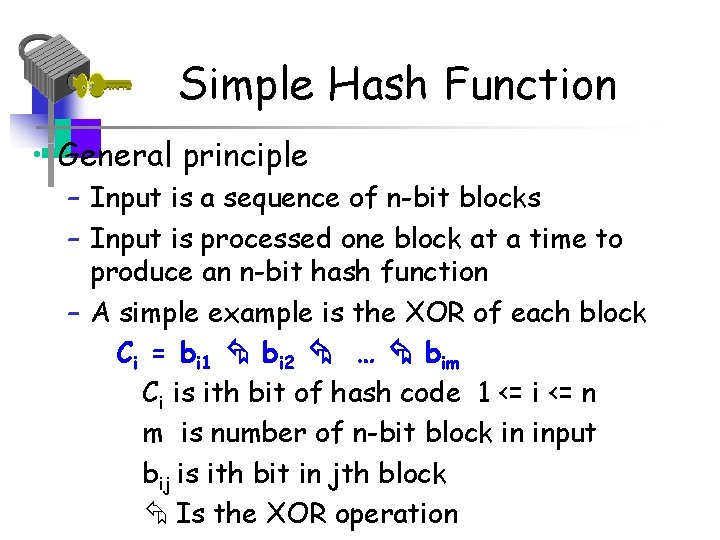
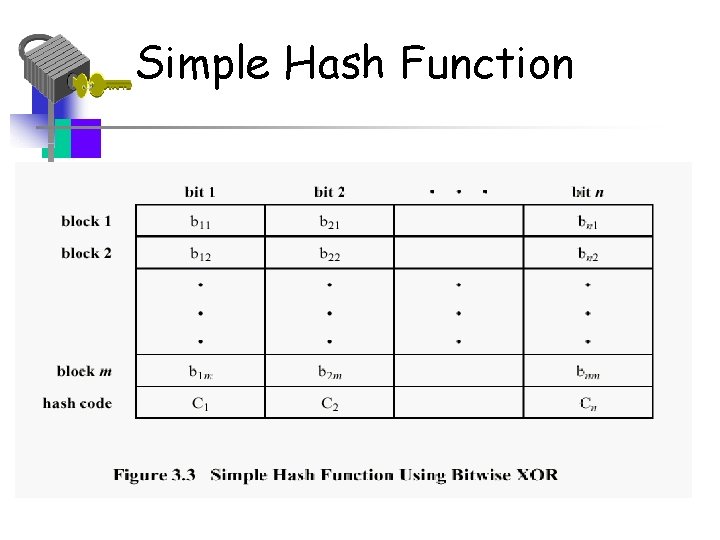
Simple Hash Function • General principle – Input is a sequence of n-bit blocks – Input is processed one block at a time to produce an n-bit hash function – A simple example is the XOR of each block Ci = bi 1 bi 2 … bim Ci is ith bit of hash code 1 <= i <= n m is number of n-bit block in input bij is ith bit in jth block Is the XOR operation

Simple Hash Function

Simple Hash Function Improved • To improve- perform a one-bit circular shift on the hash value after each block is processed – Initially set the n-bit hash value to zero – Process each successive n-bit block of data by: • Rotating current hash value to the left by 1 bit • XOR the block into the hash value – This has the effect of “randomizing” the input

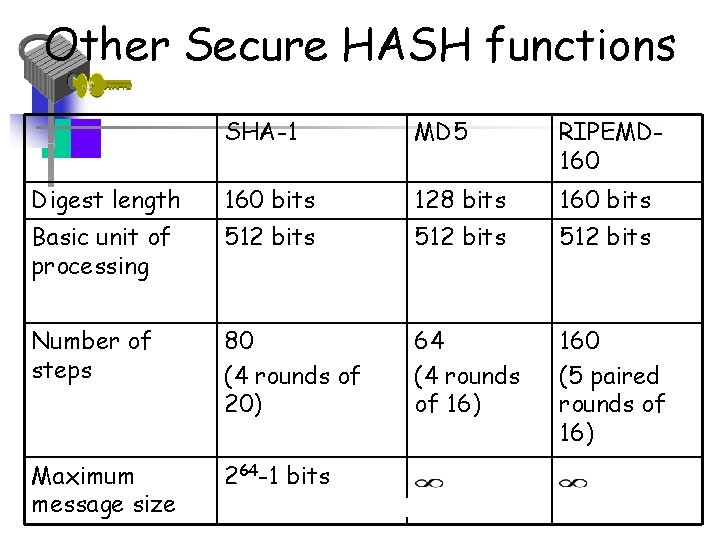
Other Secure HASH functions SHA-1 MD 5 RIPEMD 160 Digest length 160 bits 128 bits 160 bits Basic unit of processing 512 bits Number of steps 80 (4 rounds of 20) 64 (4 rounds of 16) 160 (5 paired rounds of 16) Maximum message size 264 -1 bits

HMAC • Use a MAC derived from a cryptographic hash code, such as SHA-1. • Motivations: – Cryptographic hash functions execute faster in software than encryption algorithms such as DES – Library code for cryptographic hash functions is widely available – No export restrictions from the US

HMAC Design Objectives Ø Use, without modifications, hash functions Ø Allow for easy replaceability of embedded hash function Ø Preserve original performance of hash function without significant degradation Ø Use and handle keys in a simple way. Ø Have well understood cryptographic analysis of authentication mechanism strength

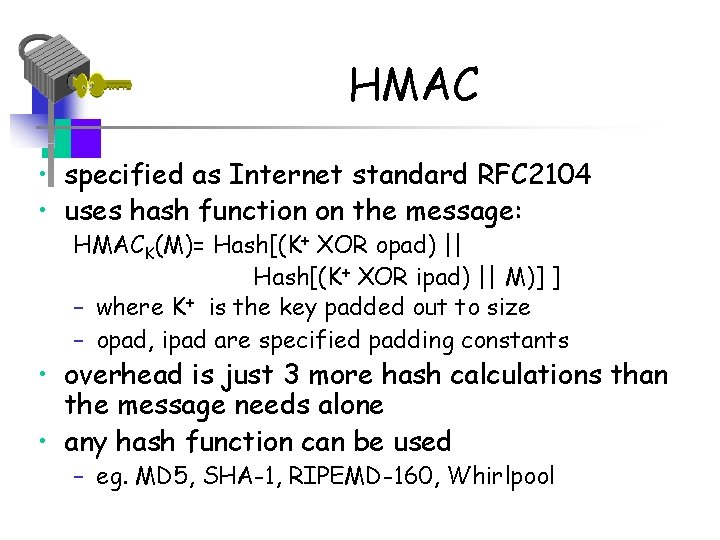
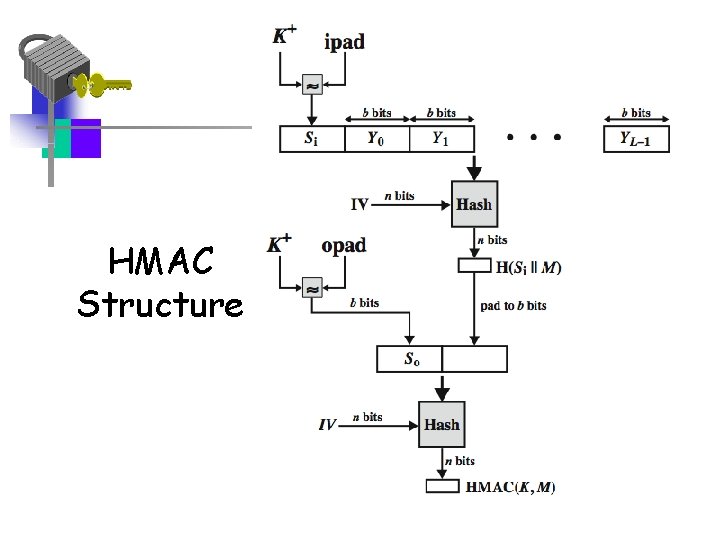
HMAC • specified as Internet standard RFC 2104 • uses hash function on the message: HMACK(M)= Hash[(K+ XOR opad) || Hash[(K+ XOR ipad) || M)] ] – where K+ is the key padded out to size – opad, ipad are specified padding constants • overhead is just 3 more hash calculations than the message needs alone • any hash function can be used – eg. MD 5, SHA-1, RIPEMD-160, Whirlpool

HMAC Structure

HMAC Security • Proved security of HMAC relates to that of the underlying hash algorithm • Attacking HMAC requires either: – brute force attack on key used – birthday attack (but since keyed would need to observe a very large number of messages) • Choose hash function used based on speed verses security constraints

Cipher. Based MAC (CMAC) • Based on use of block cipher • Widely used in government and industry • Has message size limitation (nb, where b= 128 for AES, b=64 for 3 DES) • Can overcome using 2 keys & padding • Thus forming the Cipher-based Message Authentication Code (CMAC) • Adopted by NIST SP 800 -38 B

HMAC • Can compute a MAC of the message M with key K using a “hashed MAC” or HMAC • HMAC is a keyed hash – Why would we need a key? • How to compute HMAC? • Two obvious choices: h(K, M) and h(M, K) • Which is better? Part 1 Cryptography 55

HMAC • Should we compute HMAC as h(K, M) ? • Hashes computed in blocks – h(B 1, B 2) = F(F(A, B 1), B 2) for some F and constant A – Then h(B 1, B 2) = F(h(B 1), B 2) • Let M’ = (M, X) – Then h(K, M’) = F(h(K, M), X) – Attacker can compute HMAC of M’ without K • Is h(M, K) better? – Yes, but… if h(M’) = h(M) then we might have h(M, K)=F(h(M), K)=F(h(M’), K)=h(M’, K) Part 1 Cryptography 56

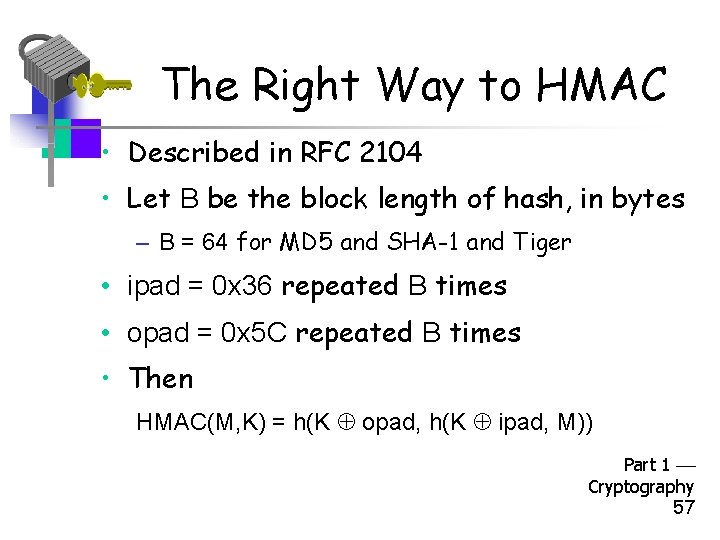
The Right Way to HMAC • Described in RFC 2104 • Let B be the block length of hash, in bytes – B = 64 for MD 5 and SHA-1 and Tiger • ipad = 0 x 36 repeated B times • opad = 0 x 5 C repeated B times • Then HMAC(M, K) = h(K opad, h(K ipad, M)) Part 1 Cryptography 57

Hash Uses • Authentication (HMAC) • Message integrity (HMAC) • Message fingerprint • Data corruption detection • Digital signature efficiency • Anything you can do with symmetric crypto • Also, many clever/surprising uses… Part 1 Cryptography 58

Online Bids • • Suppose Alice, Bob and Charlie are bidders Alice plans to bid A, Bob B and Charlie C They don’t trust that bids will stay secret A possible solution? – Alice, Bob, Charlie submit hashes h(A), h(B), h(C) – All hashes received and posted online – Then bids A, B, and C submitted and revealed • Hashes don’t reveal bids (one way) • Can’t change bid after hash sent (collision) • But there is a flaw here… Part 1 Cryptography 59

Spam Reduction • Spam reduction • Before accept email, want proof that sender spent effort to create email – Here, effort == CPU cycles • Goal is to limit the amount of email that can be sent – This approach will not eliminate spam – Instead, make spam more costly to send Part 1 Cryptography 60

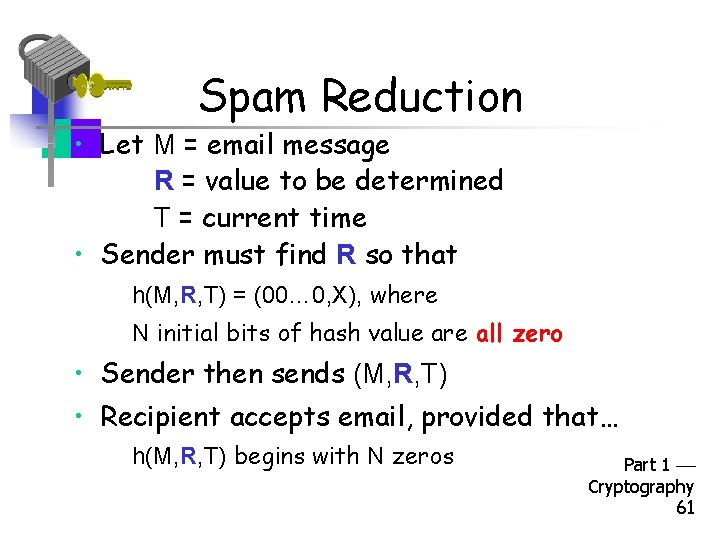
Spam Reduction • Let M = email message R = value to be determined T = current time • Sender must find R so that h(M, R, T) = (00… 0, X), where N initial bits of hash value are all zero • Sender then sends (M, R, T) • Recipient accepts email, provided that… h(M, R, T) begins with N zeros Part 1 Cryptography 61

Spam Reduction • Sender: h(M, R, T) begins with N zeros • Recipient: verify that h(M, R, T) begins with N zeros • Work for sender: about 2 N hashes • Work for recipient: always 1 hash • Sender’s work increases exponentially in N • Small work for recipient regardless of N • Choose N so that… – Work acceptable for normal email users – Work is too high for spammers Part 1 Cryptography 62

Secret Sharing Part 1 Cryptography 63

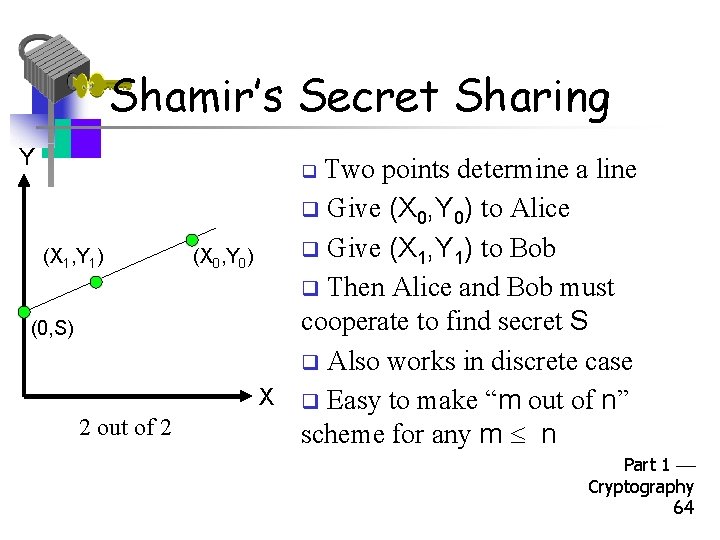
Shamir’s Secret Sharing Y Two points determine a line q Give (X 0, Y 0) to Alice q Give (X 1, Y 1) to Bob (X 1, Y 1) (X 0, Y 0) q Then Alice and Bob must cooperate to find secret S (0, S) q Also works in discrete case X q Easy to make “m out of n” 2 out of 2 scheme for any m n q Part 1 Cryptography 64

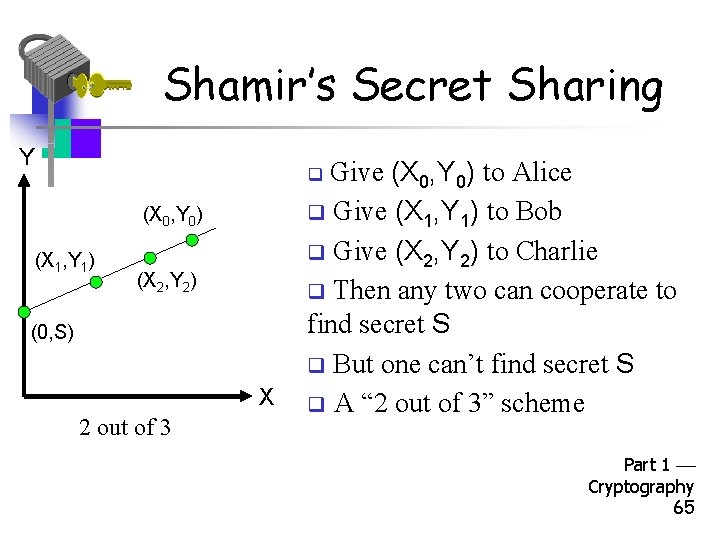
Shamir’s Secret Sharing Y Give (X 0, Y 0) to Alice q Give (X 1, Y 1) to Bob q Give (X 2, Y 2) to Charlie q Then any two can cooperate to find secret S q But one can’t find secret S q A “ 2 out of 3” scheme q (X 0, Y 0) (X 1, Y 1) (X 2, Y 2) (0, S) X 2 out of 3 Part 1 Cryptography 65

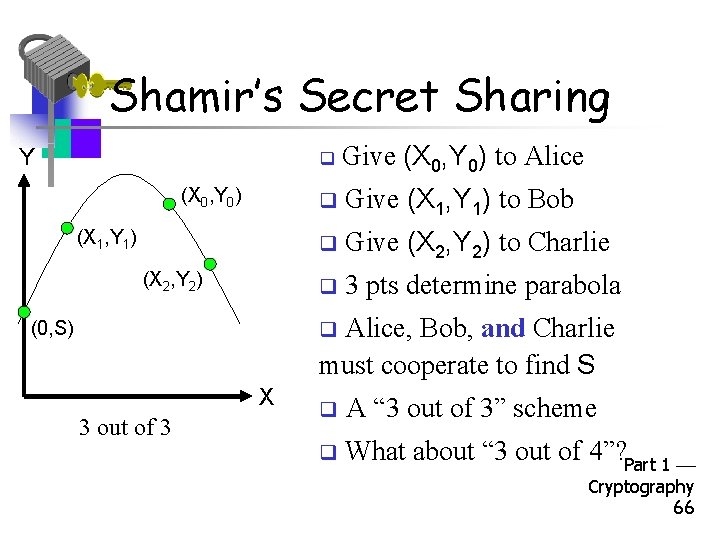
Shamir’s Secret Sharing Y (X 0, Y 0) (X 1, Y 1) (X 2, Y 2) q Give (X 0, Y 0) to Alice q Give (X 1, Y 1) to Bob q Give (X 2, Y 2) to Charlie q 3 pts determine parabola Alice, Bob, and Charlie must cooperate to find S (0, S) q X 3 out of 3 q A “ 3 out of 3” scheme q What about “ 3 out of 4”? Part 1 Cryptography 66

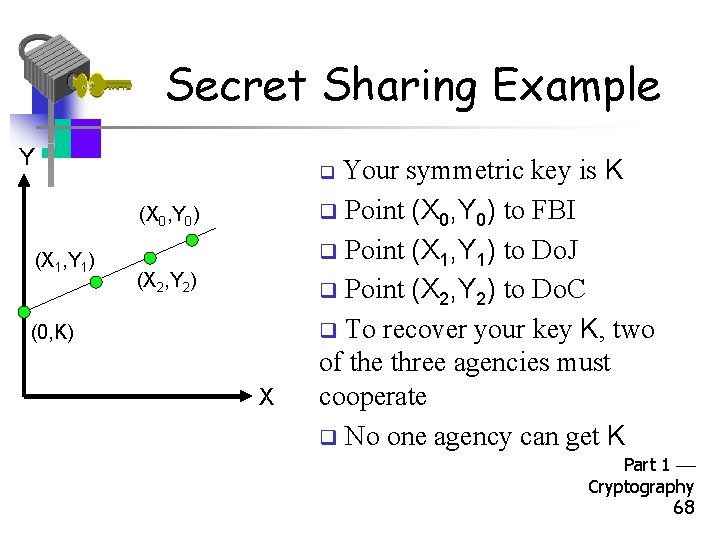
Secret Sharing Example • Key escrow suppose it’s required that your key be stored somewhere • Key can be “recovered” with court order • But you don’t trust FBI to store your keys • We can use secret sharing – Say, three different government agencies – Two must cooperate to recover the key Part 1 Cryptography 67

Secret Sharing Example Y Your symmetric key is K q Point (X 0, Y 0) to FBI q Point (X 1, Y 1) to Do. J q Point (X 2, Y 2) to Do. C q To recover your key K, two of the three agencies must cooperate q No one agency can get K q (X 0, Y 0) (X 1, Y 1) (X 2, Y 2) (0, K) X Part 1 Cryptography 68

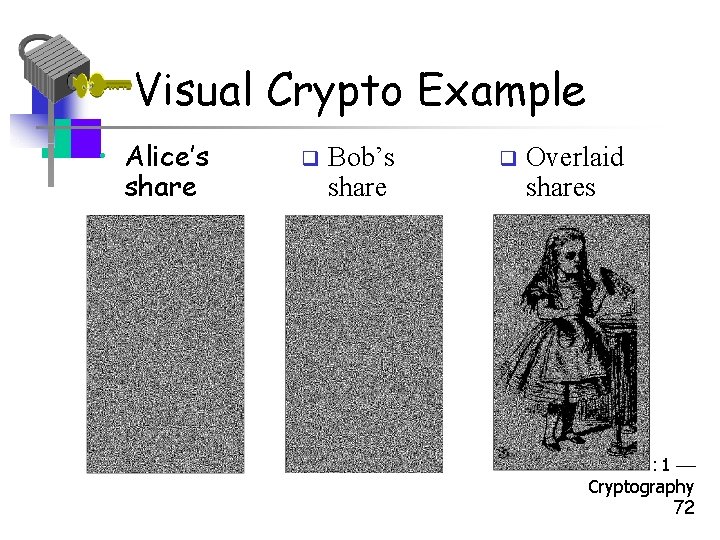
Visual Cryptography • Another form of secret sharing… • Alice and Bob “share” an image • Both must cooperate to reveal the image • Nobody can learn anything about image from Alice’s share or Bob’s share – That is, both shares are required • Is this possible? Part 1 Cryptography 69

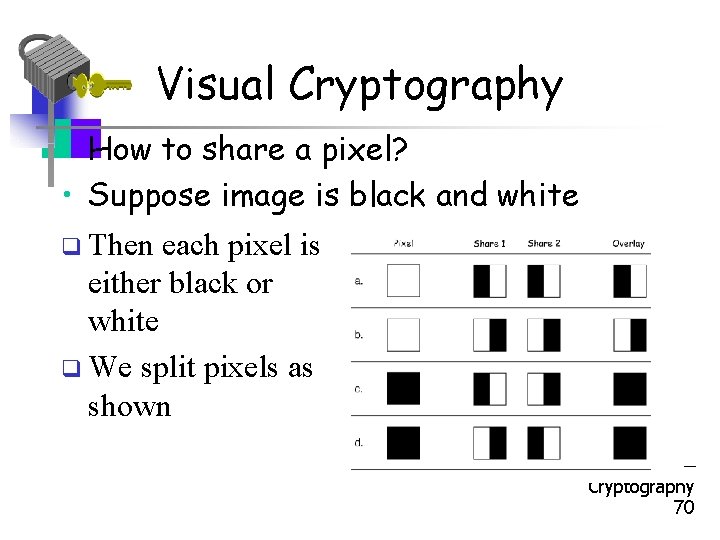
Visual Cryptography • How to share a pixel? • Suppose image is black and white q Then each pixel is either black or white q We split pixels as shown Part 1 Cryptography 70

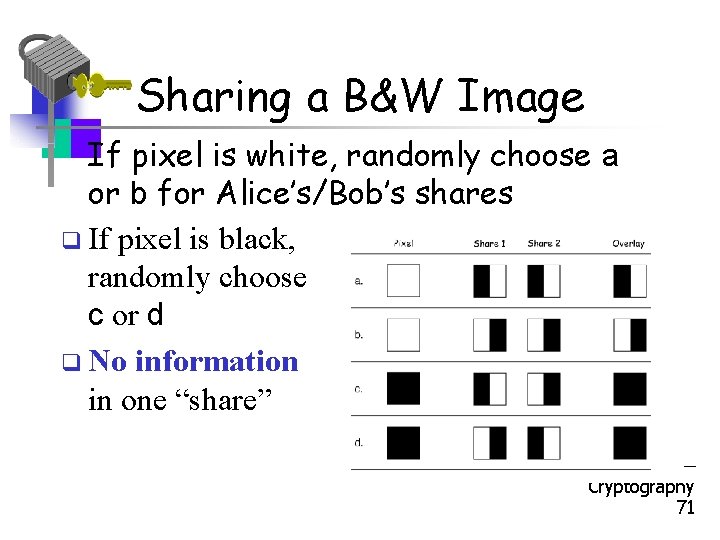
Sharing a B&W Image • If pixel is white, randomly choose a or b for Alice’s/Bob’s shares q If pixel is black, randomly choose c or d q No information in one “share” Part 1 Cryptography 71

Visual Crypto Example • Alice’s share q Bob’s share q Overlaid shares Part 1 Cryptography 72

Visual Crypto • How does visual “crypto” compare to regular crypto? • In visual crypto, no key… – Or, maybe both images are the key? • With encryption, exhaustive search – Except for a one-time pad • Exhaustive search on visual crypto? – No exhaustive search is possible! Part 1 Cryptography 73

Visual Crypto • Visual crypto no exhaustive search… • How does visual crypto compare to crypto? – Visual crypto is “information theoretically” secure true of other secret sharing schemes – With regular encryption, goal is to make cryptanalysis computationally infeasible • Visual crypto an example of secret sharing – Not really a form of crypto, in the usual sense Part 1 Cryptography 74

Random Numbers in Cryptography Part 1 Cryptography 75

Random Numbers • Random numbers used to generate keys – Symmetric keys – RSA: Prime numbers – Diffie Hellman: secret values • Random numbers used for nonces – Sometimes a sequence is OK – But sometimes nonces must be random • Random numbers also used in simulations, statistics, etc. – Such numbers need to be “statistically” random Part 1 Cryptography 76

Random Numbers • Cryptographic random numbers must be statistically random and unpredictable • Suppose server generates symmetric keys… – – Alice: KA Bob: KB Charlie: KC Dave: KD • But, Alice, Bob, and Charlie don’t like Dave • Alice, Bob, and Charlie working together Part 1 must not be able to determine KD Cryptography 77

Non-random Random Numbers q Online version of Texas Hold ‘em Poker o ASF Software, Inc. • Random numbers used to shuffle the deck • Program did not produce a random shuffle • A serious problem or not? Part 1 Cryptography 78

Card Shuffle • There are 52! > 2225 possible shuffles • The poker program used “random” 32 -bit integer to determine the shuffle – So, only 232 distinct shuffles could occur • Code used Pascal pseudo-random number generator (PRNG): Randomize() • Seed value for PRNG was function of number of milliseconds since midnight • Less than 227 milliseconds in a day – So, less than 227 possible shuffles Part 1 Cryptography 79

Card Shuffle • Seed based on milliseconds since midnight • PRNG re-seeded with each shuffle • By synchronizing clock with server, number of shuffles that need to be tested 218 • Could then test all 218 in real time – Test each possible shuffle against “up” cards • Attacker knows every card after the first of five rounds of betting! Part 1 Cryptography 80

Poker Example • Poker program is an extreme example – But common PRNGs are predictable – Only a question of how many outputs must be observed before determining the sequence • Crypto random sequences not predictable – For example, keystream from RC 4 cipher – But “seed” (or key) selection is still an issue! • How to generate initial random values? – Keys (and, in some cases, seed values) Part 1 Cryptography 81

What is Random? • True “randomness” hard to define • Entropy is a measure of randomness • Good sources of “true” randomness – Radioactive decay radioactive computers are not too popular – Hardware devices many good ones on the market – Lava lamp relies on chaotic behavior Part 1 Cryptography 82

Randomness • Sources of randomness via software – Software is (hopefully) deterministic – So must rely on external “random” events – Mouse movements, keyboard dynamics, network activity, etc. • Can get quality random bits by such methods • But quantity of bits is very limited • Bottom line: “The use of pseudo-random processes to generate secret quantities can Part 1 result in pseudo-security” Cryptography 83

Information Hiding Part 1 Cryptography 84

Information Hiding • Digital Watermarks – Example: Add “invisible” identifier to data – Defense against music or software piracy • Steganography – “Secret” communication channel – Similar to a covert channel (more on this later) – Example: Hide data in image or music file Part 1 Cryptography 85

Watermark • Add a “mark” to data • Visibility of watermarks – Invisible Watermark is not obvious – Visible Such as TOP SECRET • Robustness of watermarks – Robust Readable even if attacked – Fragile Damaged if attacked Part 1 Cryptography 86

Watermark Examples • Add robust invisible mark to digital music – If pirated music appears on Internet, can trace it back to original source of the leak • Add fragile invisible mark to audio file – If watermark is unreadable, recipient knows that audio has been tampered (integrity) • Combinations of several types are sometimes used – E. g. , visible plus robust invisible watermarks Part 1 Cryptography 87

Watermark Example (1) • Non-digital watermark: U. S. currency q Image embedded in paper on rhs o Hold bill to light to see embedded info Part 1 Cryptography 88

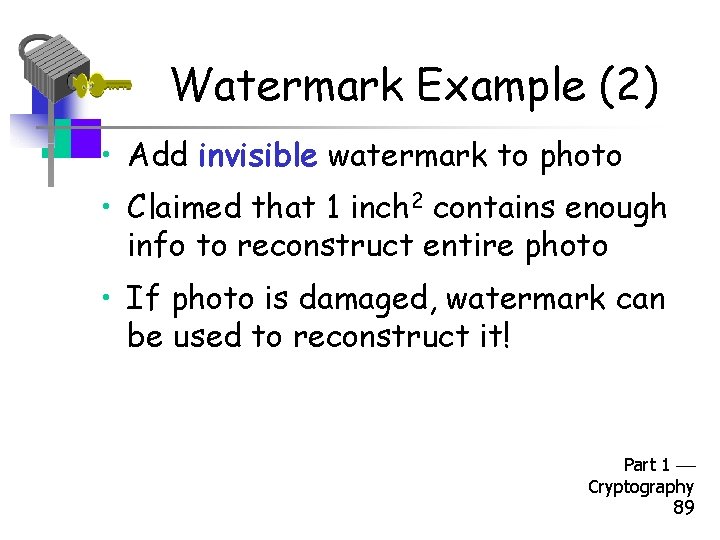
Watermark Example (2) • Add invisible watermark to photo • Claimed that 1 inch 2 contains enough info to reconstruct entire photo • If photo is damaged, watermark can be used to reconstruct it! Part 1 Cryptography 89

Steganography • According to Herodotus (Greece 440 BC) – Shaved slave’s head – Wrote message on head – Let hair grow back – Send slave to deliver message – Shave slave’s head to expose message warning of Persian invasion • Historically, steganography used more often than cryptography Part 1 Cryptography 90

Images and Steganography • Images use 24 bits for color: RGB – 8 bits for red, 8 for green, 8 for blue • For example – 0 x 7 E 0 x 52 0 x 90 is this color – 0 x. FE 0 x 52 0 x 90 is this color • While – 0 x. AB 0 x 33 0 x. F 0 is this color – 0 x. AB 0 x 33 0 x. F 1 is this color • Low-order bits don’t matter… Part 1 Cryptography 91

Images and Stego • Given an uncompressed image file… – For example, BMP format • …we can insert information into low-order RGB bits • Since low-order RGB bits don’t matter, result will be “invisible” to human eye – But, computer program can “see” the bits Part 1 Cryptography 92

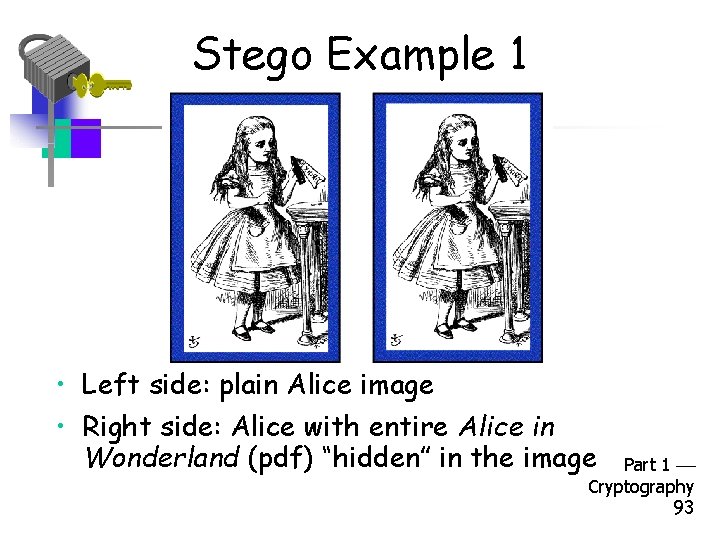
Stego Example 1 • Left side: plain Alice image • Right side: Alice with entire Alice in Wonderland (pdf) “hidden” in the image Part 1 Cryptography 93

Non-Stego Example q Walrus. html in web browser • “View source” reveals: <font color=#000000>"The time has come, " the Walrus said, </font> <font color=#000000>"To talk of many things: </font> <font color=#000000>Of shoes and ships and sealing wax </font> <font color=#000000>Of cabbages and kings </font> <font color=#000000>And why the sea is boiling hot </font> <font color=#000000>And whether pigs have wings. " </font> Part 1 Cryptography 94

Stego Example 2 q stego. Walrus. html in web browser • “View source” reveals: <font color=#000101>"The time has come, " the Walrus said, </font> <font color=#000100>"To talk of many things: </font> <font color=#010000>Of shoes and ships and sealing wax </font> <font color=#010000>Of cabbages and kings </font> <font color=#000000>And why the sea is boiling hot </font> <font color=#010001>And whether pigs have wings. " </font> q “Hidden” message: 011 010 100 000 101 Part 1 Cryptography 95

Steganography • Some formats (e. g. , image files) are more difficult than html for humans to read – But easy for computer programs to read… • Easy to hide info in unimportant bits • Easy to destroy info in unimportant bits • To be robust, must use important bits – But stored info must not damage data – Collusion attacks are another concern • Robust steganography is tricky! Part 1 Cryptography 96

Information Hiding: The Bottom Line • Not-so-easy to hide digital information – “Obvious” approach is not robust – Stirmark: tool to make most watermarks in images unreadable without damaging the image – Stego/watermarking active research topics • If information hiding is suspected – Attacker may be able to make information/watermark unreadable – Attacker may be able to read the information, given the original document (image, audio, etc. )Part 1 Cryptography 97