Pass the Hash Detection with DDNA Phil Wallisch



![Locate Attack Remnants (cont. ) • Pattern Used: • "b[a-f. A-F 0 -9]{32}: [a-f. Locate Attack Remnants (cont. ) • Pattern Used: • "b[a-f. A-F 0 -9]{32}: [a-f.](https://slidetodoc.com/presentation_image_h/05fa7cd47888e4a36e7875189f744fb3/image-10.jpg)
- Slides: 16

“Pass the Hash” Detection with DDNA Phil Wallisch phil@hbgary. com

The Need • It is possible for “admin” users to dump LSA hashes on modern Windows platforms • An attacker can impersonate any user by leveraging a captured hash • No persistent malware is required to perform the attack. We must detect exited tools. • Detect hash dumping/injecting capability in running processes

The Approach • Locate attack remnants in unallocated memory • Identify active processes that exhibit hash grabbing characteristics

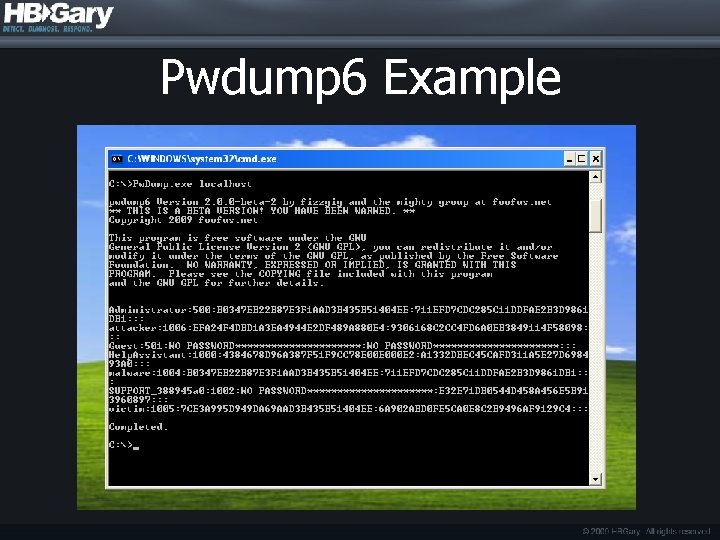
Attack Tools Examined • Pass-The-Hash (PTH) Toolkit • http: //oss. coresecurity. com/projects/pshtoolkit. html • Gsecdump • http: //www. truesec. com/Public. Store/catalog/Downloads, 223. aspx • Pwdump 6 • http: //www. foofus. net/fizzgig/pwdump/

Attack Procedure • Platform: Windows XP SP 2 32 bit running in VMWare Workstation 6. 5. • Two users added to the “administrator” group: ‘attacker’ and ‘victim’ • Victim logs in via a standard interactive session • The “switch user” functionality is executed • Attacker logs in via a standard interactive session • Attacker executes the hash dump functionality of the tool

PTH Toolkit Example

Gsecdump Example

Pwdump 6 Example

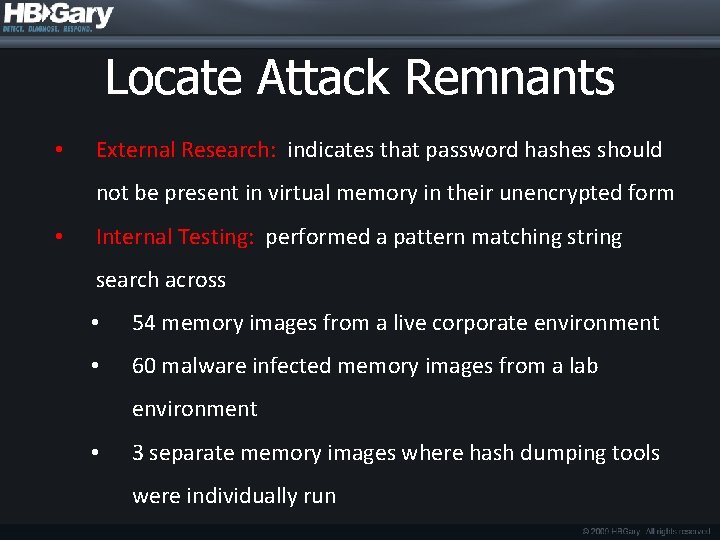
Locate Attack Remnants • External Research: indicates that password hashes should not be present in virtual memory in their unencrypted form • Internal Testing: performed a pattern matching string search across • 54 memory images from a live corporate environment • 60 malware infected memory images from a lab environment • 3 separate memory images where hash dumping tools were individually run
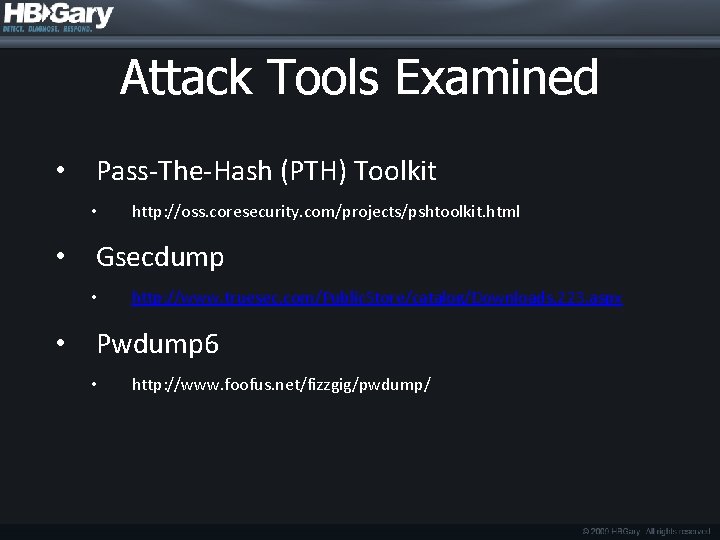
![Locate Attack Remnants cont Pattern Used baf AF 0 932 af Locate Attack Remnants (cont. ) • Pattern Used: • "b[a-f. A-F 0 -9]{32}: [a-f.](https://slidetodoc.com/presentation_image_h/05fa7cd47888e4a36e7875189f744fb3/image-10.jpg)
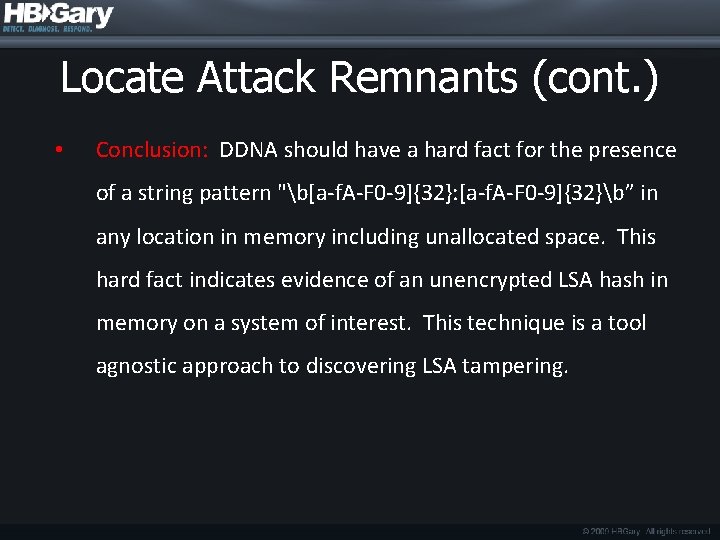
Locate Attack Remnants (cont. ) • Pattern Used: • "b[a-f. A-F 0 -9]{32}: [a-f. A-F 0 -9]{32}b“ • Word bounded search for two 32 hexadecimal character patterns separated by a colon • Results: • Live corporate images = 0 matches • Malware infected images = 0 matches • Hash dump memory images = 60 matches

Locate Attack Remnants (cont. ) • Conclusion: DDNA should have a hard fact for the presence of a string pattern "b[a-f. A-F 0 -9]{32}: [a-f. A-F 0 -9]{32}b” in any location in memory including unallocated space. This hard fact indicates evidence of an unencrypted LSA hash in memory on a system of interest. This technique is a tool agnostic approach to discovering LSA tampering.

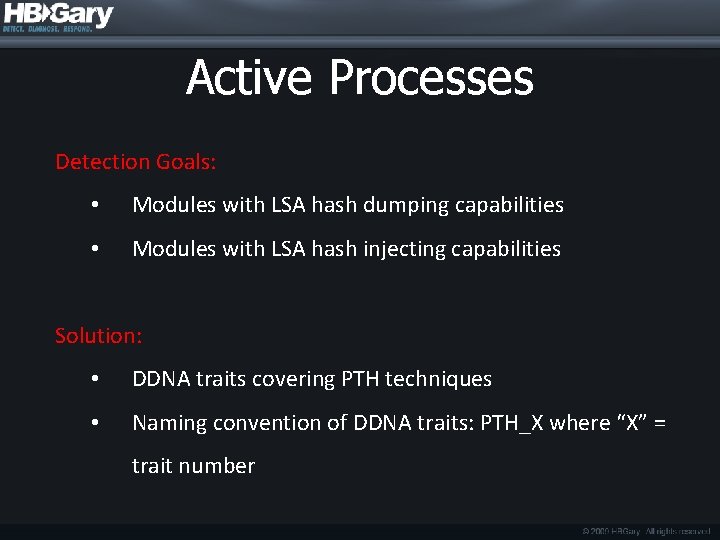
Active Processes Detection Goals: • Modules with LSA hash dumping capabilities • Modules with LSA hash injecting capabilities Solution: • DDNA traits covering PTH techniques • Naming convention of DDNA traits: PTH_X where “X” = trait number

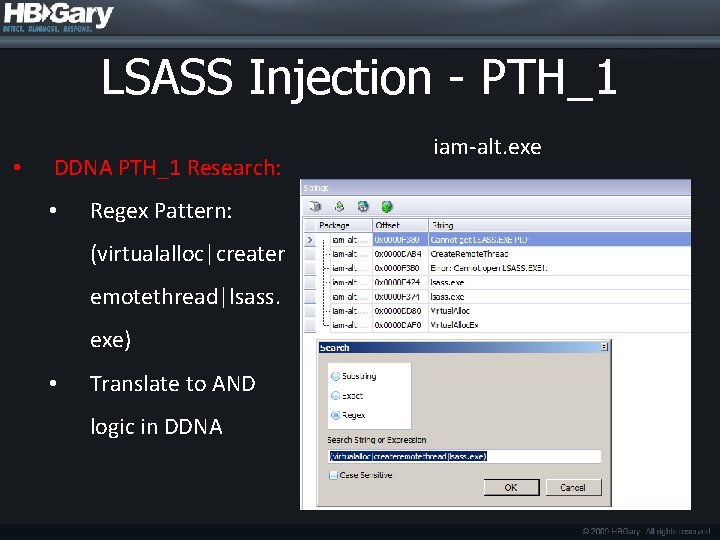
LSASS Injection - PTH_1 • DDNA PTH_1 Research: • Regex Pattern: (virtualalloc|creater emotethread|lsass. exe) • Translate to AND logic in DDNA iam-alt. exe

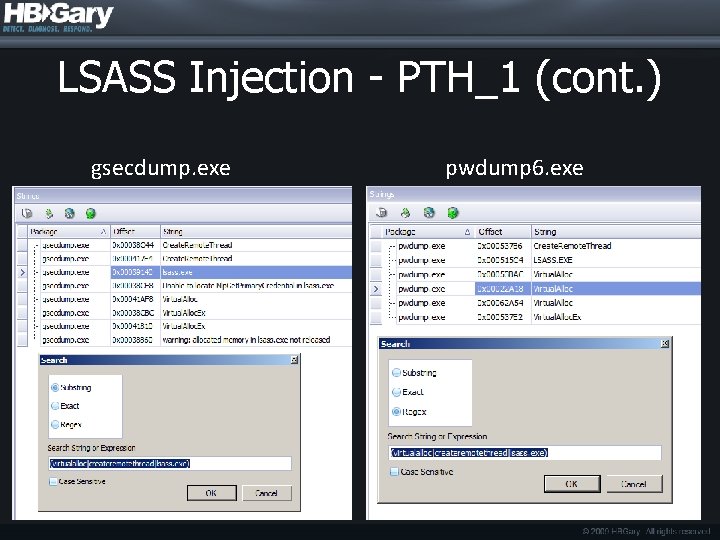
LSASS Injection - PTH_1 (cont. ) gsecdump. exe pwdump 6. exe

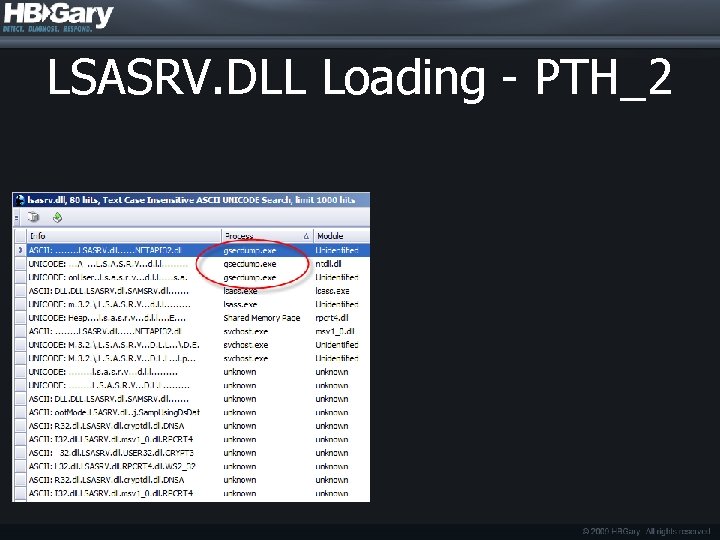
LSASRV. DLL Loading - PTH_2

Active Processes Conclusion DDNA Traits Required: • PTH_1: Hash Injection : Identify LSASS DLL injection : I“Virtual. Alloc"ku AND I“Create. Remote. Thread”ku AND I”lsass. exe”ku • PTH_2: Hash Dumping : Identify LSASRV. DLL access : I”lsasrv. dll”ku NOT N”svchost. exe” NOT N”lsass. exe”