PassTheHash Gaining Root Access to Your Network June










![Was Pass-The-Hash used on your system? • Grep : [0 -9, A-F, a-f]{32, 32} Was Pass-The-Hash used on your system? • Grep : [0 -9, A-F, a-f]{32, 32}](https://slidetodoc.com/presentation_image_h/dc6d460994f2eafae9d9f4e65bcfe711/image-36.jpg)









- Slides: 54

Pass-The-Hash: Gaining Root Access to Your Network June 24, 2014 Tim Slaybaugh Cyber Incident Analyst Northrop Grumman Information Systems

What is Pass-The-Hash? “Attackers using Pt. H completely compromise just about every network they hit. Pretty much every APT attack team uses them. ” – Roger Grimes, Info. World

What is Pass-The-Hash? • First published in 1997 by Paul Ashton • Allows the use of LM and NTLM hashes to authenticate to a remote host • Passwords do not need to be cracked • Hashes can be harvested from the physical disk or memory

How does Pass-The-Hash work? • Requires admin privileges, therefore an exploit has to be run to gain access • Injects into the Local Security Authority Subsystem Service (LSASS) process to access hashes in memory • Grabs locally stored hashes from SAM registry hive. • Smartcard credentials and Kerberos tickets can be harvested also!

Pass-The-Hash and Smartcards • Smart card credentials are cached in an identical manner as passwords. • Systems that allow both Smartcard or password logons store smartcard credentials for a very long time • Systems that require smartcard only logon will periodically change the hash.

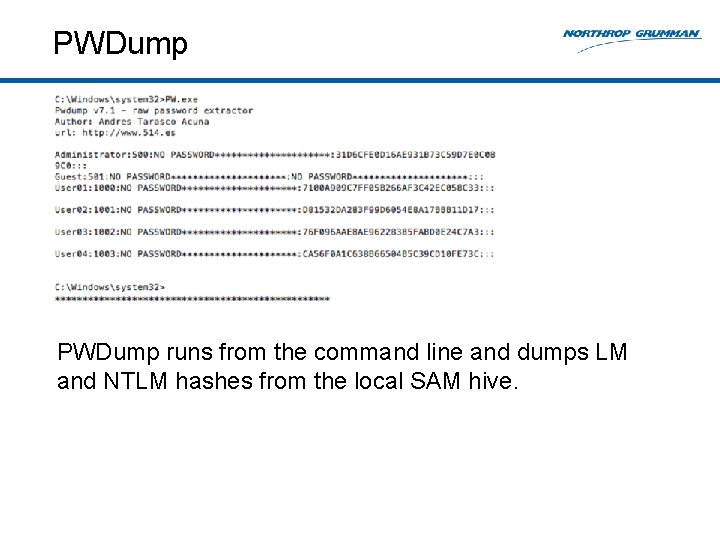
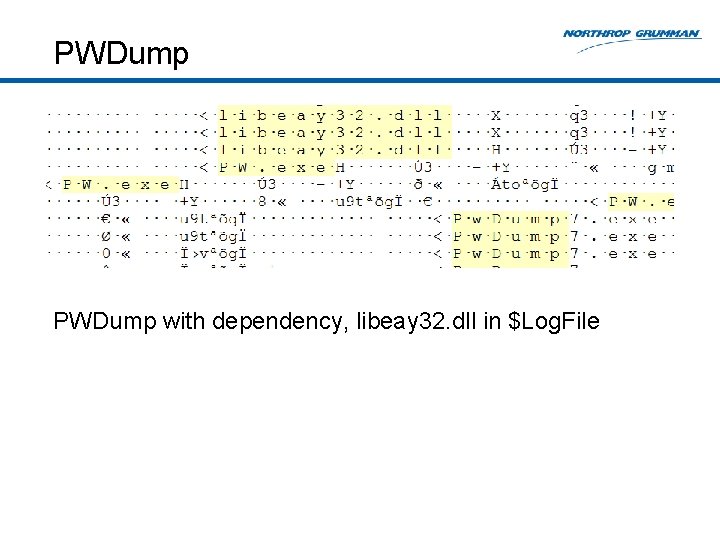
Pass-The-Hash Tools: PWDump • Latest version is PWDump 7. 1 • Author: Andres Tarasco Acuna • Dumps the local SAM hive • Uses syskey from SYSTEM hive to dump LM and NTLM hashes • Statically links the Open. SSL library, libeay 32. dll • PWDump 6 links lsremora. dll

PWDump runs from the command line and dumps LM and NTLM hashes from the local SAM hive.

PWDump with dependency, libeay 32. dll in $Log. File

PWDump in AV signature database

PWDump Keywords used to identify PWDump activity: • Error reading hive root key • Andres Tarasco Acuna • savedump. dat • Error opening sam hive • raw password extractor

Pass-The-Hash Tools: Mimikatz • Author: Benjamin Delpy • Support for both x 86 and 64 bit systems • Requires sekur. LSA. dll to run • Extracts hashes and cleartext passwords

Mimikatz Unlike most PTH tools, Mimikatz will run from the root of Windows.

Mimikatz hooks the System Service Descriptor Table (SSDT) similar to rootkit activity.

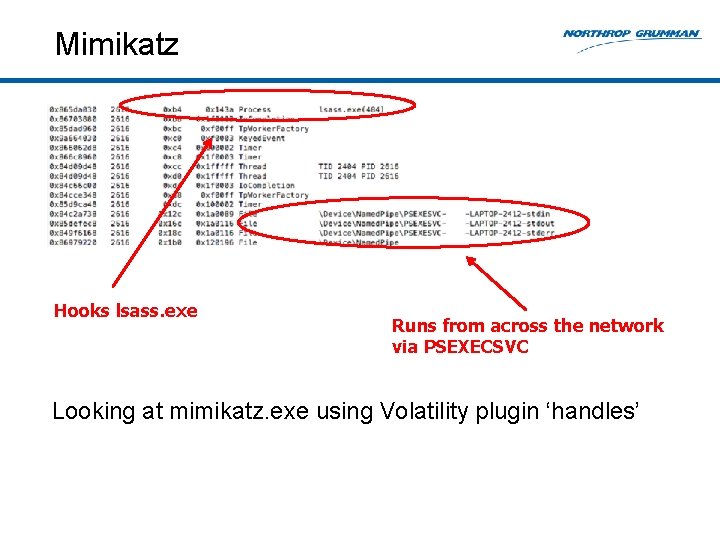
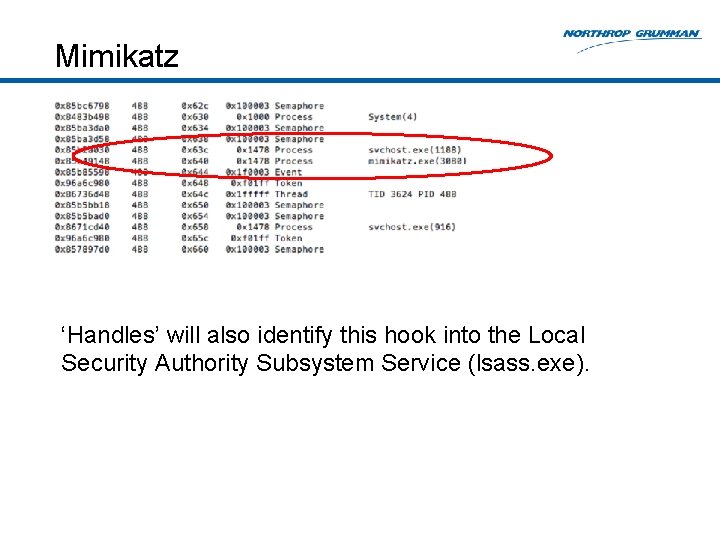
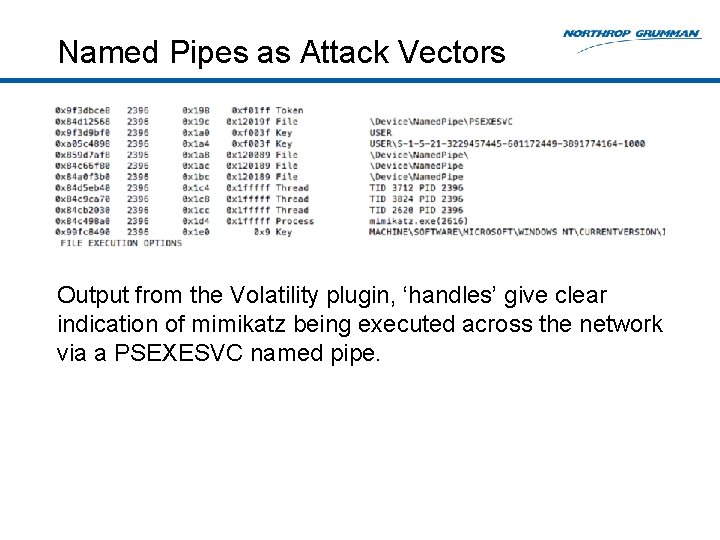
Mimikatz Hooks lsass. exe Runs from across the network via PSEXECSVC Looking at mimikatz. exe using Volatility plugin ‘handles’

Mimikatz ‘Handles’ will also identify this hook into the Local Security Authority Subsystem Service (lsass. exe).

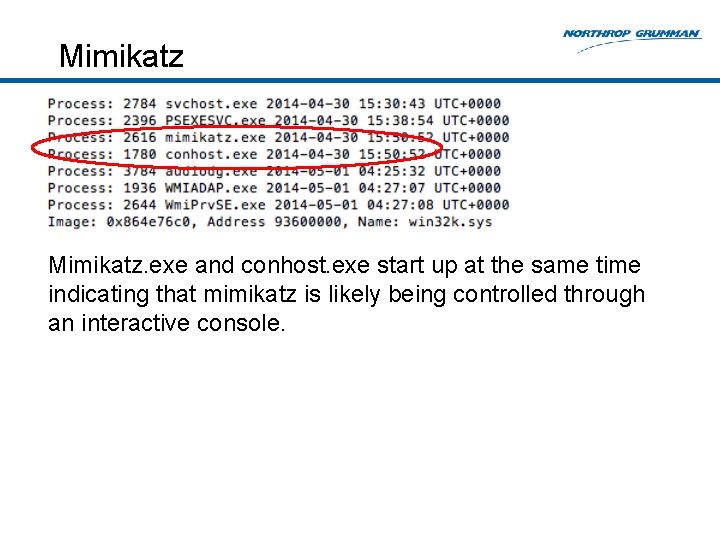
Mimikatz. exe and conhost. exe start up at the same time indicating that mimikatz is likely being controlled through an interactive console.

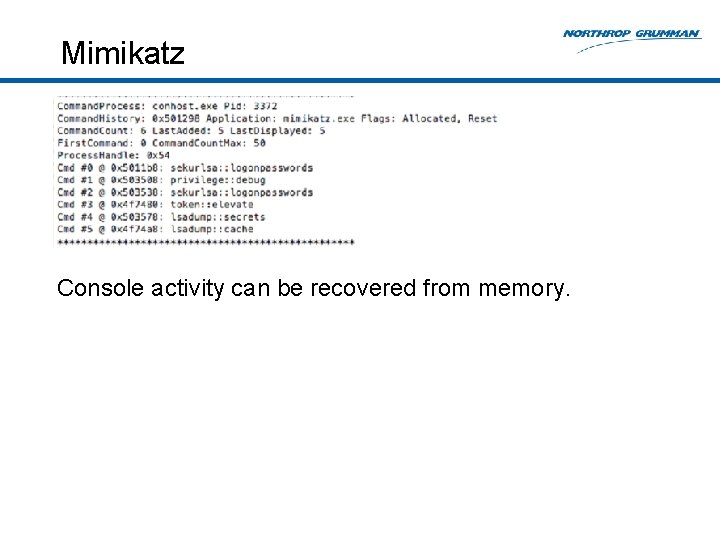
Mimikatz Console activity can be recovered from memory.

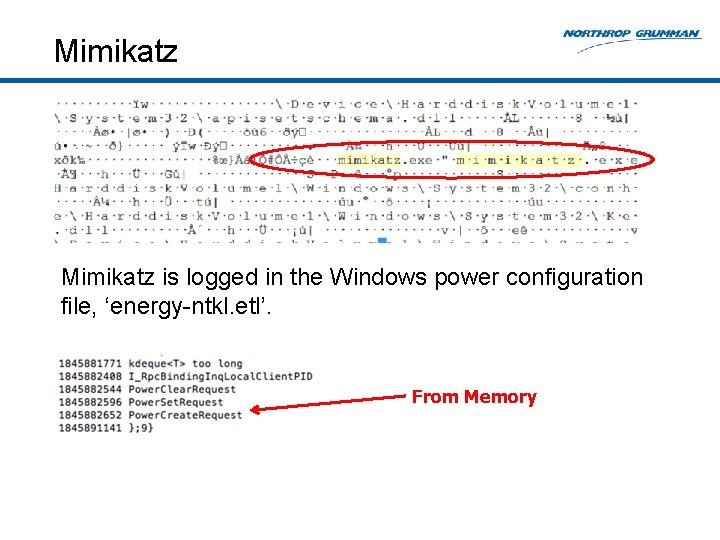
Mimikatz is logged in the Windows power configuration file, ‘energy-ntkl. etl’. From Memory

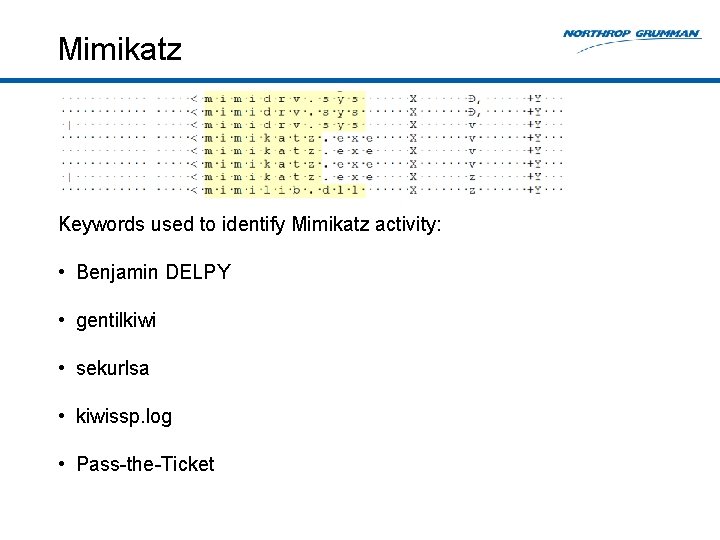
Mimikatz Keywords used to identify Mimikatz activity: • Benjamin DELPY • gentilkiwi • sekurlsa • kiwissp. log • Pass-the-Ticket

Pass-The-Hash Tools: gsecdump • Johannes Gumbel, Truesec • Freeware • Latest version is 2. 0 b 5 • Extracts hashes from SAM, Active Directory and active logon sessions • Works with both x 86 and 64 bit systems

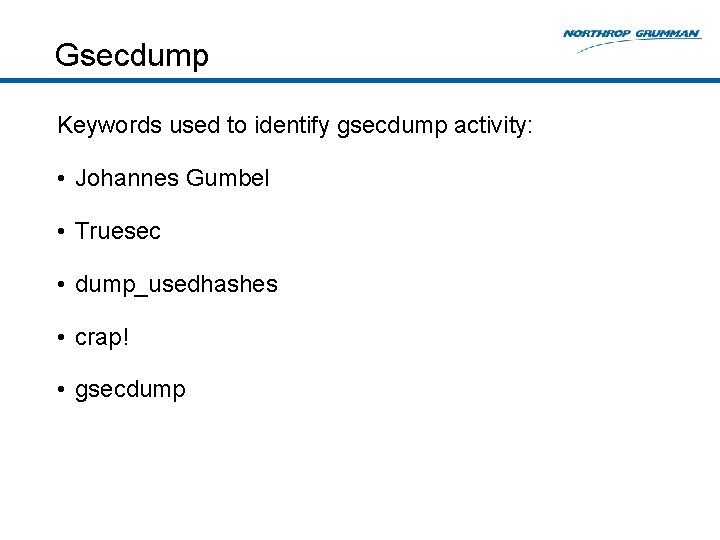
Gsecdump Keywords used to identify gsecdump activity: • Johannes Gumbel • Truesec • dump_usedhashes • crap! • gsecdump

Pass-The-Hash Tools: PSHToolkit • Author: Hernan Ochoa, Core Labs • Latest version, 1. 4 • Toolkit contains three tools: iam. exe, whosthere. exe and genhash. exe • Iam. exe is used to change/modify NTLM credentials in memory • Whosthere. exe is used to list logon sessions that are using NTLM credentials • Genhash. exe used to test iam. exe

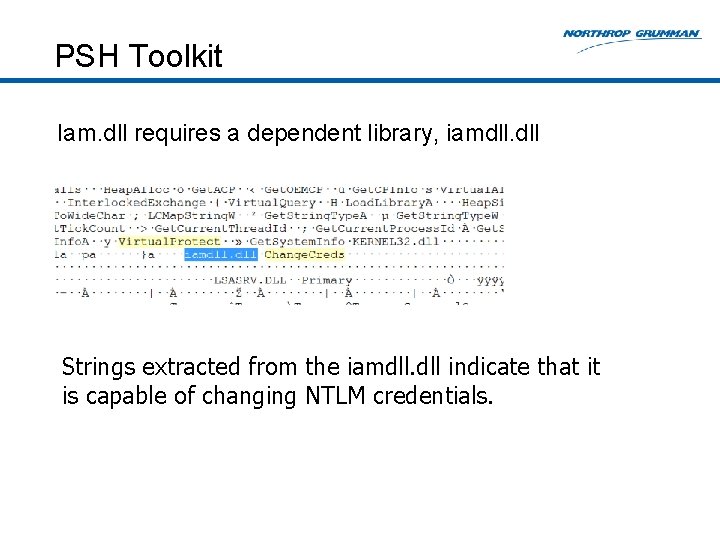
PSH Toolkit Iam. dll requires a dependent library, iamdll. dll Strings extracted from the iamdll. dll indicate that it is capable of changing NTLM credentials.

PSH Toolkit Indicators of the PSH Toolkit can be found in several Windows metadata files like $Log. File seen above.

PSH Toolkit Keywords used to identify PSH Toolkit activity: • Hernan Ochoa • Change. Creds • Gen. Hash • iamdll. dll • pth. dll

Pass-The-Hash Tools: Windows Credential Editor • Author: Hernan Ochoa, Amplia Security • Latest release is 1. 42 beta • Support for both x 86 and 64 bit systems • Extracts NTLM credentials from memory as well as Kerberos tickets and cleartext passwords

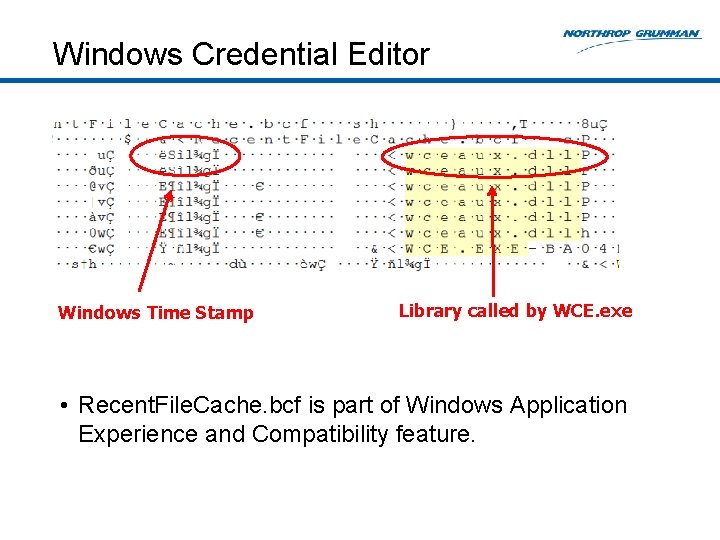
Windows Credential Editor Windows Time Stamp Library called by WCE. exe • Recent. File. Cache. bcf is part of Windows Application Experience and Compatibility feature.

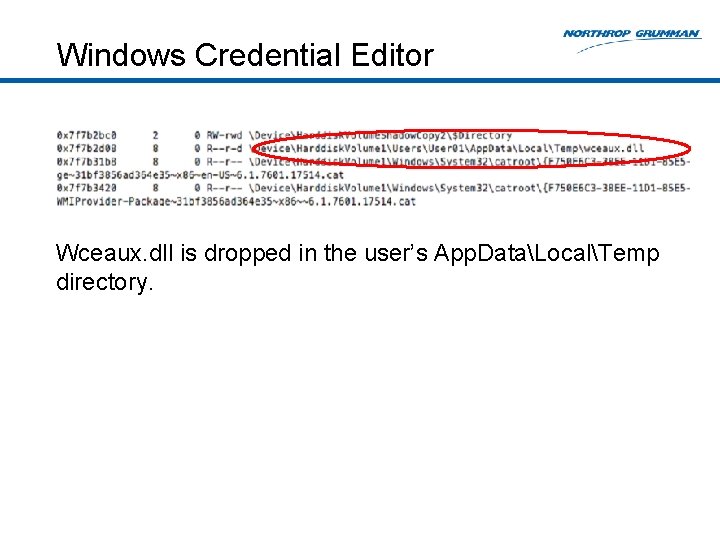
Windows Credential Editor Wceaux. dll is dropped in the user’s App. DataLocalTemp directory.

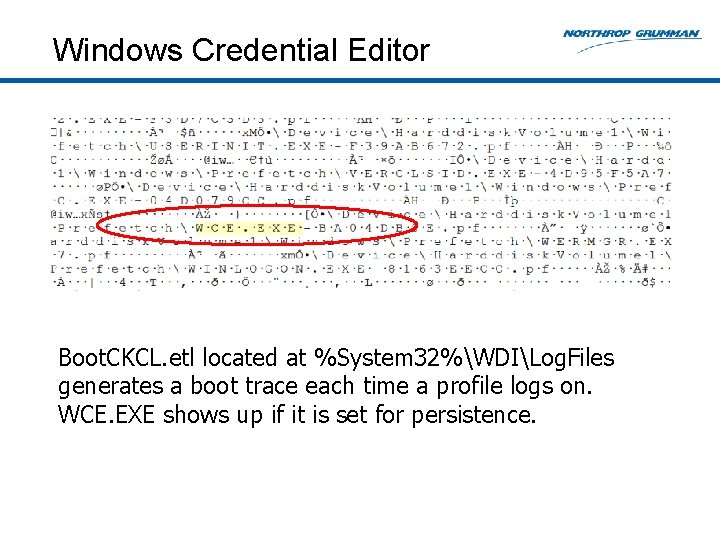
Windows Credential Editor Boot. CKCL. etl located at %System 32%WDILog. Files generates a boot trace each time a profile logs on. WCE. EXE shows up if it is set for persistence.

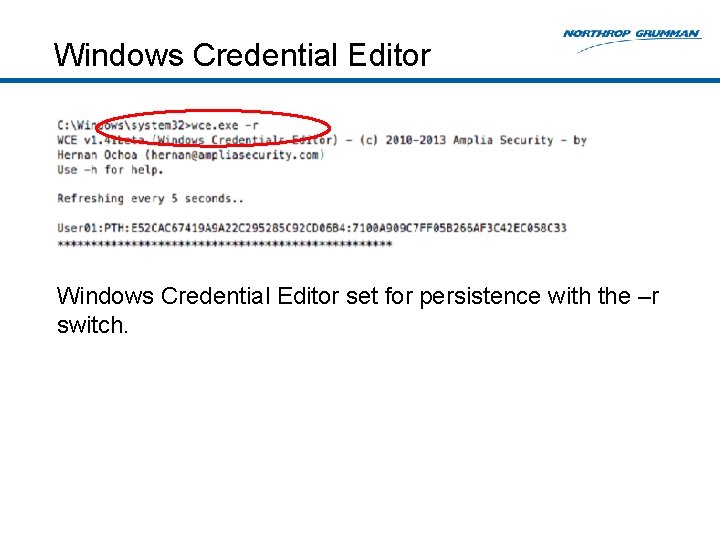
Windows Credential Editor set for persistence with the –r switch.

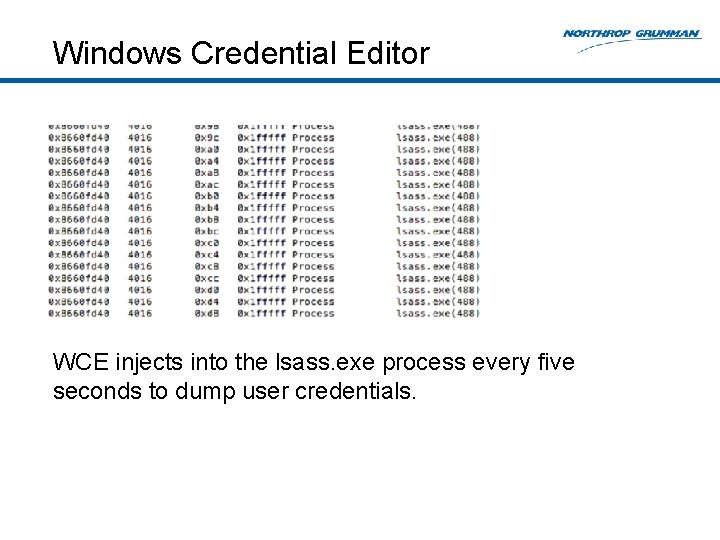
Windows Credential Editor WCE injects into the lsass. exe process every five seconds to dump user credentials.

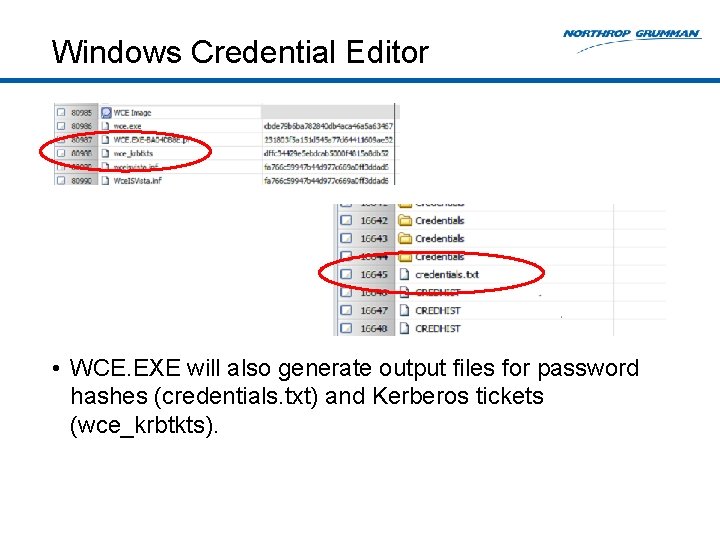
Windows Credential Editor • WCE. EXE will also generate output files for password hashes (credentials. txt) and Kerberos tickets (wce_krbtkts).

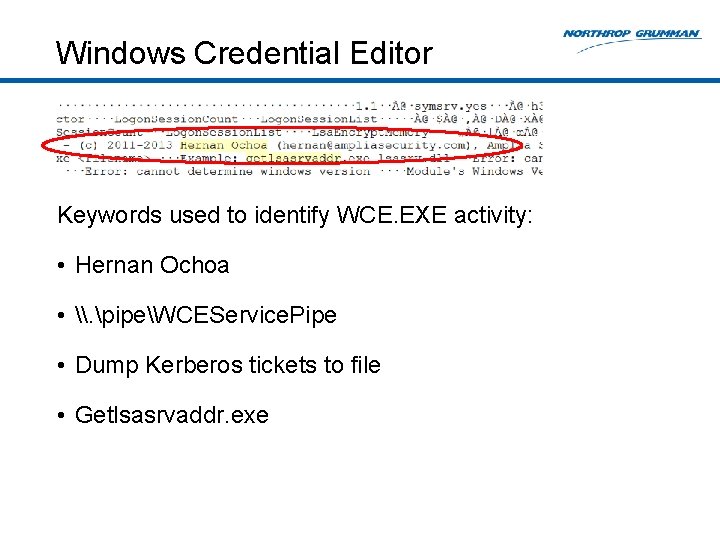
Windows Credential Editor Keywords used to identify WCE. EXE activity: • Hernan Ochoa • \. pipeWCEService. Pipe • Dump Kerberos tickets to file • Getlsasrvaddr. exe

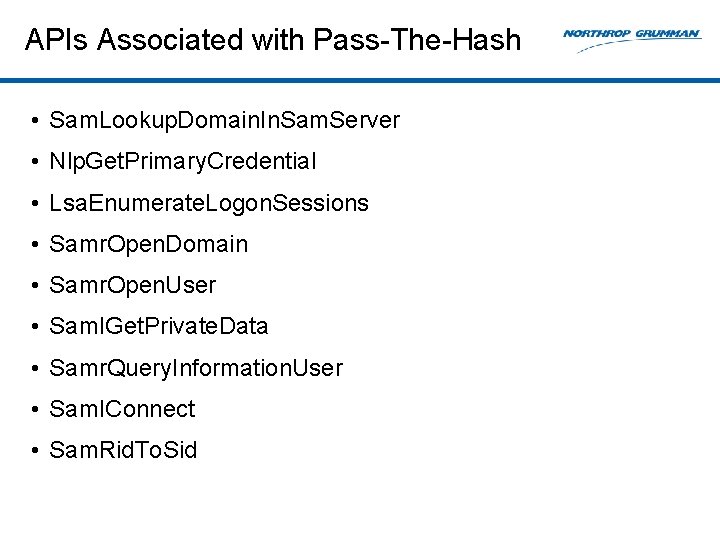
APIs Associated with Pass-The-Hash • Sam. Lookup. Domain. In. Sam. Server • Nlp. Get. Primary. Credential • Lsa. Enumerate. Logon. Sessions • Samr. Open. Domain • Samr. Open. User • Sam. IGet. Private. Data • Samr. Query. Information. User • Sam. IConnect • Sam. Rid. To. Sid

They have my hash. Where do they go from here? Scenarios for Pass-The-Hash: • Dump all hashes on local system looking for admin privileges. • Remote Admin support • Local Admin • Help Desk support • Patches and updates • Database logons
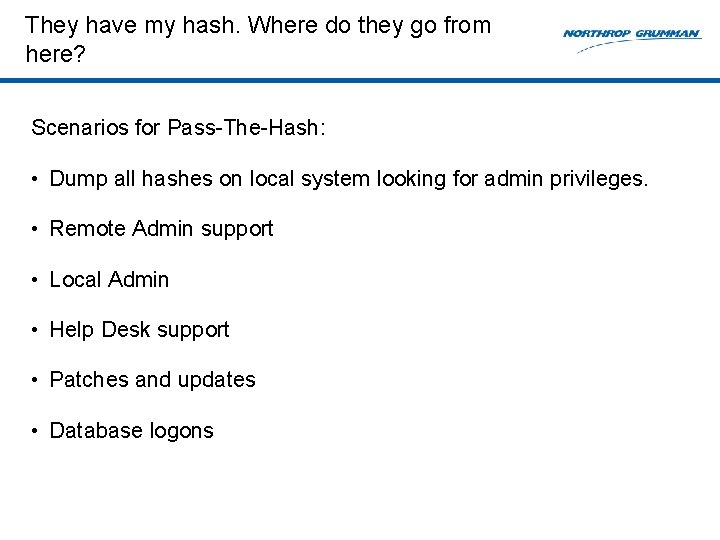
![Was PassTheHash used on your system Grep 0 9 AF af32 32 Was Pass-The-Hash used on your system? • Grep : [0 -9, A-F, a-f]{32, 32}](https://slidetodoc.com/presentation_image_h/dc6d460994f2eafae9d9f4e65bcfe711/image-36.jpg)
Was Pass-The-Hash used on your system? • Grep : [0 -9, A-F, a-f]{32, 32} • Grep : [0 -9, A-W, a-f, *, x 00]{32, 32}: [0 -9, A-F, a-f]{32, 32}

Was Pass-The-Hash used on your system? Grep for hashes in memory also!

Was Pass-The-Hash used on your network? • SMB connections over ports 139/445 to a writeable share (e. g. C$, admin$) • Client then accesses svcctl named pipe through SMB • Malware files are transferred, usually an EXE and a DLL • Connection to Windows Service Control Manager (SCM) remote protocol • SCM will run under services. exe

Network Activity Call stack of a server side RPC call. This connection was initiated from a remote system. Data was recovered from ‘pagefile. sys’.

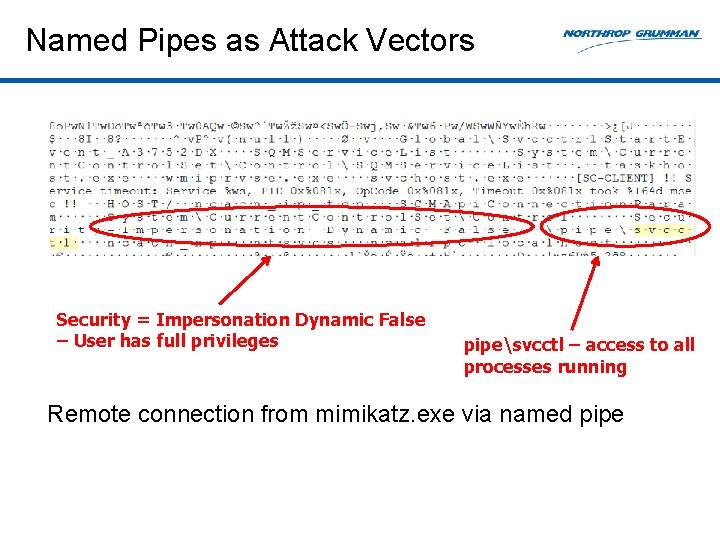
Named Pipes as Attack Vectors Security = Impersonation Dynamic False – User has full privileges pipesvcctl – access to all processes running Remote connection from mimikatz. exe via named pipe

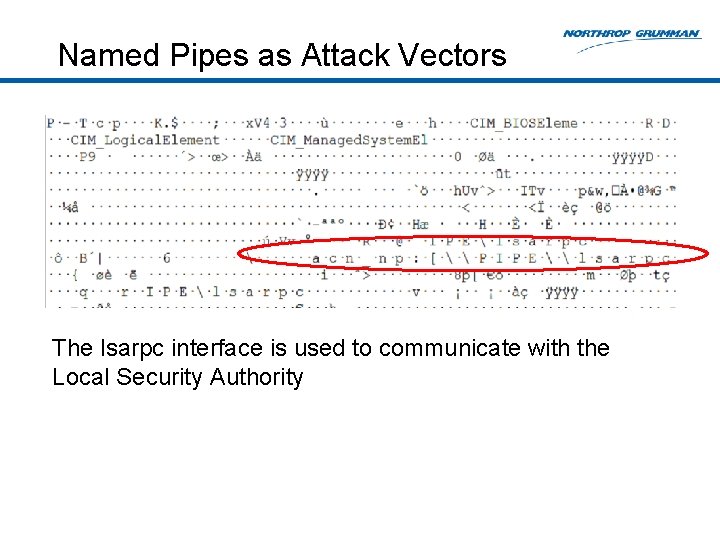
Named Pipes as Attack Vectors The lsarpc interface is used to communicate with the Local Security Authority

Named Pipes as Attack Vectors Output from the Volatility plugin, ‘handles’ give clear indication of mimikatz being executed across the network via a PSEXESVC named pipe.

Named Pipes as Attack Vectors Require SMB Security Signatures HKLM_Local_MachineSYSTEMCurrent. Control. SetServices Lan. Man. ServerParametersRequire. Security. Signature "0"

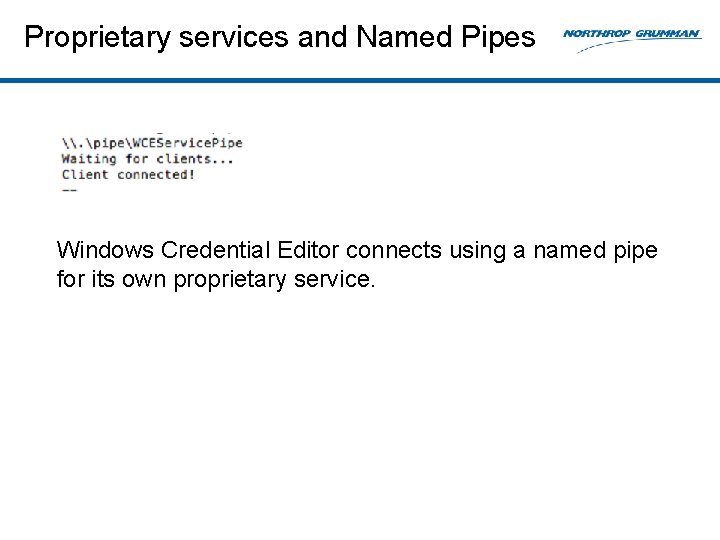
Proprietary services and Named Pipes Windows Credential Editor connects using a named pipe for its own proprietary service.

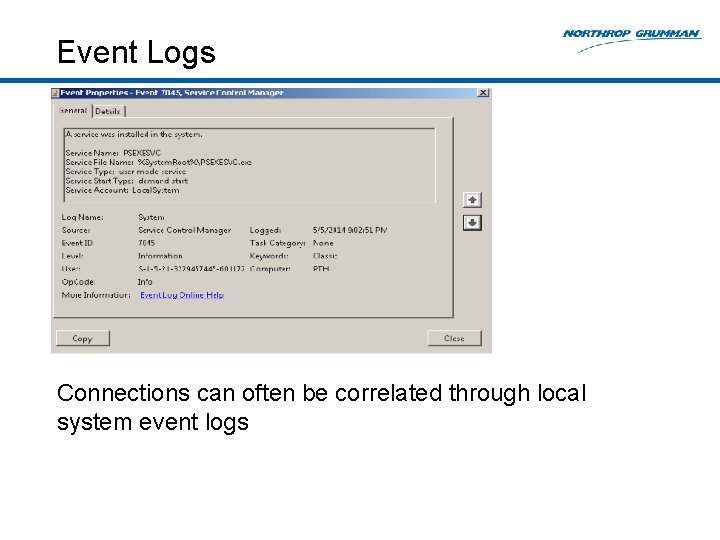
Event Logs Connections can often be correlated through local system event logs

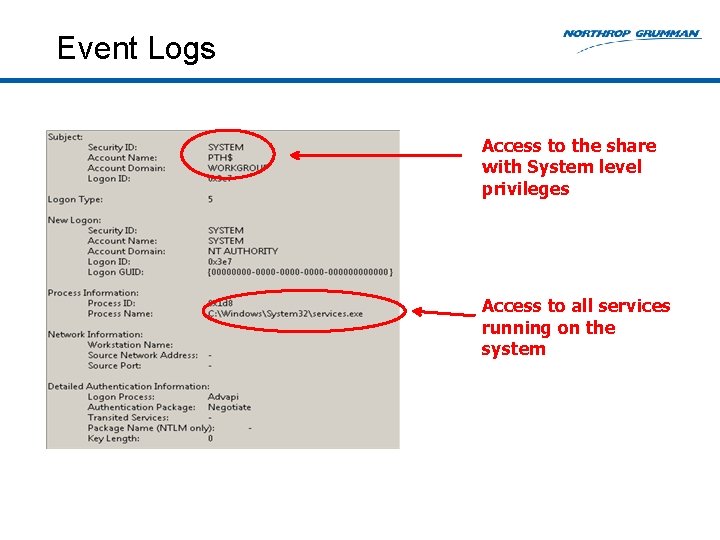
Event Logs Access to the share with System level privileges Access to all services running on the system

Pass-The-Hash and Windows 8. 1 • Domain Accounts do not store plaintext passwords in Memory • Restricted Admin RDP uses only network authentication – No credentials left on the remote box • Protected users using Kerberos authentication cannot be delegated • Authentication silos introduced

Pass-The-Hash and Windows 8. 1 • LSASS runs as a protected process • LM Hashes are not stored in memory • New SIDs for the “Local Account”

Mitigation • Use Kerberos authentication package • Enforce a password policy of a 14 character minimum • Remove or limit access to Windows shares • Disable the remote registry service • Limit the possibility of DLL injection by removing users and groups from the ‘Debug Programs’ policy setting (Se. Debug. Privilege)

Mitigation • Use NTLMv 2 over NTLM if you cannot use Kerberos • Use console tools like Tivoli for remote administration • Use two factor authentication • Protected Users Group – NTLM is not used. Kerberos or third party SSP is required – Kerberos tickets have a shorter life span – Windows Digest is not cached

References • Delfy, B. (2012). Blog de Gentil Kiwi/Mimikatz. Retrieved from URL. • Ewaida, B. (2010). Pass-the-hash attacks: Tools and Mitigation. SANS Institute. • Gumbel, J. (2010). Gsecdump v 2. 0 b 5. Retrieved from URL. • Hummel, C. (2009). Why Crack When You Can Pass The Hash? SANS Institute. • Microsoft Corp, (2014) Microsoft Developer Network, msdn. microsoft. com • National Security Agency/Central Security Service (2013). Reducing the Effectiveness of Pass-The-Hash. • Ochoa, H. (2011). Windows Credential Editor. Amplia Security. Retrieved from URL.

References • Sanders, C. (2010). Dissecting the Pass The Hash attack. Retrieved from URL. • Tarasco Acuna, A. (2010). Password Dumper pwdump 7 (v 7. 1). Retrieved from URL. • Vipzen (2014). Sorry, Microsoft: Pass The Hash on Windows 8. 1 still works. Retrieved from URL.

Thank You! Timothy. slaybaugh@ngc. com
