Hash Functions 1 Cryptographic Hash Function q Crypto






![Public Key Notation q Sign message M with Alice’s private key: [M]Alice q Encrypt Public Key Notation q Sign message M with Alice’s private key: [M]Alice q Encrypt](https://slidetodoc.com/presentation_image_h/2747ac99fc8d60308c93e51b8494255b/image-7.jpg)




![Hashing and Signatures Alice signs h(M), sends M and S = [h(M)]Alice to Bob Hashing and Signatures Alice signs h(M), sends M and S = [h(M)]Alice to Bob](https://slidetodoc.com/presentation_image_h/2747ac99fc8d60308c93e51b8494255b/image-13.jpg)












![Signature Birthday Attack q Alice signs innocent message Ij q Then Trudy has [h(Ij)]Alice Signature Birthday Attack q Alice signs innocent message Ij q Then Trudy has [h(Ij)]Alice](https://slidetodoc.com/presentation_image_h/2747ac99fc8d60308c93e51b8494255b/image-28.jpg)












- Slides: 42

Hash Functions 1

Cryptographic Hash Function q Crypto hash function h(x) must provide o Compression output length is small o Efficiency h(x) easy to compute for any x o One-way given a value y it is infeasible to find an x such that h(x) = y o Weak collision resistance given x and h(x), infeasible to find y x such that h(y) = h(x) o Strong collision resistance infeasible to find any x and y, with x y such that h(x) = h(y) q Many collisions exist, but cannot find any Hash Functions 2

Non-crypto Hash (1) Data X = (X 0, X 1, X 2, …, Xn-1), each Xi is a byte q Spse hash(X) = X 0+X 1+X 2+…+Xn-1 q Is this secure? q Example: X = (1010, 00001111) q Hash is 10111001 q But so is hash of Y = (00001111, 1010) q Easy to find collisions, so not secure… q Hash Functions 3

Non-crypto Hash (2) Data X = (X 0, X 1, X 2, …, Xn-1) q Suppose hash is q o h(X) = n. X 0+(n-1)X 1+(n-2)X 2+…+1 Xn-1 Is this hash secure? At least h(1010, 00001111) h(00001111, 1010) q But hash of (00000001, 00001111) is same as hash of (0000, 0001) q Not secure, but it is used in the (non-crypto) application rsync q Hash Functions 4

Non-crypto Hash (3) q Cyclic Redundancy Check (CRC) q Essentially, CRC is the remainder in a long division calculation q Good for detecting burst errors q Easy for Trudy to construct collisions q CRC sometimes mistakenly used in crypto applications (WEP) Hash Functions 5

Popular Crypto Hashes q MD 5 invented by Rivest o 128 bit output o Note: MD 5 collision recently found q SHA-1 A US government standard (similar to MD 5) o 160 bit output Many others hashes, but MD 5 and SHA-1 most widely used q Messages are hashed in blocks q Hash Functions 6
![Public Key Notation q Sign message M with Alices private key MAlice q Encrypt Public Key Notation q Sign message M with Alice’s private key: [M]Alice q Encrypt](https://slidetodoc.com/presentation_image_h/2747ac99fc8d60308c93e51b8494255b/image-7.jpg)
Public Key Notation q Sign message M with Alice’s private key: [M]Alice q Encrypt message M with Alice’s public key: {M}Alice q Then {[M]Alice}Alice = M [{M}Alice]Alice = M Hash Functions 7

Crypto Hash Motivation: Digital Signatures q Suppose Alice signs M o Alice sends M and S = [M]Alice to Bob verifies that M = {S}Alice If M is big, [M]Alice is costly to compute q Suppose instead, Alice signs h(M), where h(M) is much smaller than M q o Alice sends M and S = [h(M)]Alice to Bob verifies that h(M) = {S}Alice Hash Functions 8

Digital Signatures q Digital signatures provide integrity o Like MAC and HMAC Why? q Alice sends M and S = [h(M)]Alice to Bob q If M changed to M or S changed to S (accident or intentional) Bob detects it: h(M ) {S}Alice, h(M) {S }Alice, h(M ) {S }Alice q Hash Functions 9

Non-repudiation q Digital signature also provides for non -repudiation q Alice sends M and S = [h(M)]Alice to Bob q Alice cannot “repudiate” signature o Alice cannot claim she did not sign M q Why does this work? q Is the same true of MAC? Hash Functions 10

Non-non-repudiation Alice orders 100 shares of stock from Bob q Alice computes MAC using symmetric key q Stock drops, Alice claims she did not order q Can Bob prove that Alice placed the order? q No! Since Bob also knows symmetric key, he could have forged message q Problem: Bob knows Alice placed the order, but he cannot prove it q Hash Functions 11

Non-repudiation Alice orders 100 shares of stock from Bob q Alice signs order with her private key q Stock drops, Alice claims she did not order q Can Bob prove that Alice placed the order? q Yes! Only someone with Alice’s private key could have signed the order q This assumes Alice’s private key is not stolen (revocation problem) q Hash Functions 12
![Hashing and Signatures Alice signs hM sends M and S hMAlice to Bob Hashing and Signatures Alice signs h(M), sends M and S = [h(M)]Alice to Bob](https://slidetodoc.com/presentation_image_h/2747ac99fc8d60308c93e51b8494255b/image-13.jpg)
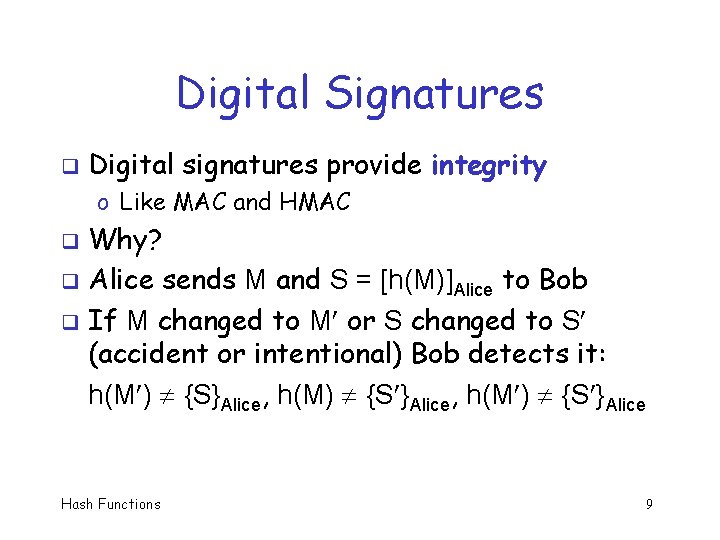
Hashing and Signatures Alice signs h(M), sends M and S = [h(M)]Alice to Bob and Bob verifies h(M) = {S}Alice q Security depends on public key system and hash function q Suppose Trudy can find collision: M M with h(M ) = h(M) q Then Trudy can replace M with M and signature scheme is broken q Hash Functions 13

Crypto Hash Function Design q Desired property: avalanche effect o Any change to input affects lots of output bits q Crypto hash functions consist of some number of rounds o Analogous to block cipher in CBC mode q Want security and speed o Avalanche effect after few rounds o But simple rounds Hash Functions 14

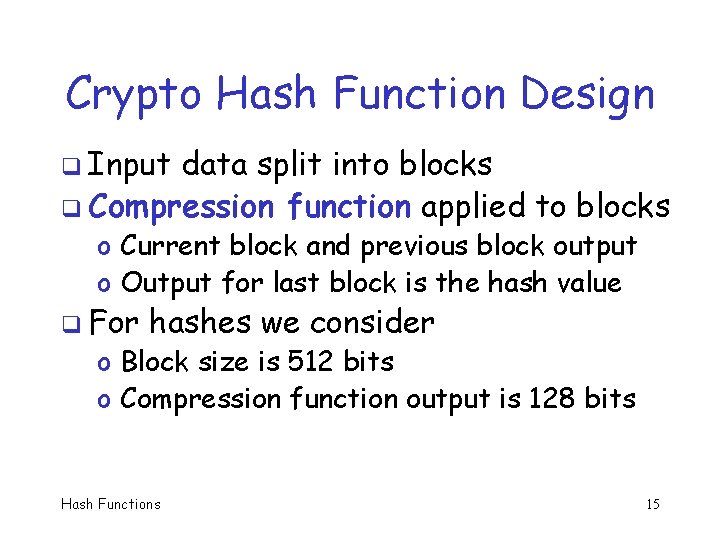
Crypto Hash Function Design q Input data split into blocks q Compression function applied to blocks o Current block and previous block output o Output for last block is the hash value q For hashes we consider o Block size is 512 bits o Compression function output is 128 bits Hash Functions 15

Hash Function q Input or “message” blocks M 0, M 1, …, MN 1 q Addition is mod 232 per 32 -bit word q This is known as Merkle-Damgard construction Hash Functions 16

Crypto Hash: Fun Facts If msg is one 512 -bit block: h(M) = f(IV, M) where f and IV known to Trudy q For 2 blocks: h(M) = f(f(IV, M 0), M 1) = f(h(M 0), M 1) q In general h(M) = f(h(M 0, M 1, …, Mn 2), Mn 1) o If h(M) = h(M ) then h(M, X) = h(M , X) for any X q o Implications for design of “hashed MAC”… Hash Functions 17

HMAC q MAC: block cipher for integrity q Can we use a hash function instead? q A “hashed MAC”, HMAC, of M with key K o Why is a key necessary? q How to compute HMAC? q Two obvious choices: h(K, M) and h(M, K) q Which (if either) is better? Hash Functions 18

How to Compute HMAC? q Should we compute HMAC as h(K, M) ? q Hashes computed in blocks q Recall h(M 0, M 1) = f(h(M 0), M 1) q Let M = (M, X) o Then h(K, M ) = f(h(K, M), X) o Trudy can compute HMAC of M without K o Defeats the purpose of HMAC Hash Functions 19

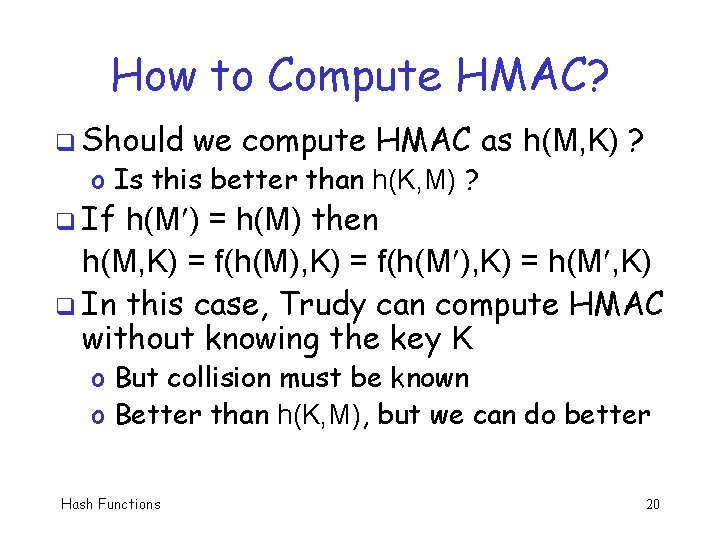
How to Compute HMAC? q Should we compute HMAC as h(M, K) ? o Is this better than h(K, M) ? q If h(M ) = h(M) then h(M, K) = f(h(M), K) = f(h(M ), K) = h(M , K) q In this case, Trudy can compute HMAC without knowing the key K o But collision must be known o Better than h(K, M), but we can do better Hash Functions 20

The Right Way to HMAC Described in RFC 2104 q Let B be the block length of hash, in bytes q For popular hash functions, B = 64 q o SHA-1, MD 5, Tiger, etc. Define ipad = 0 x 36 repeated B times opad = 0 x 5 C repeated B times q Then HMAC(M, K) = h(K opad, h(K ipad, M)) q Hash Functions 21

Hashing and Birthdays The “birthday problem” arises in many crypto contexts q We discuss it in hashing context q o And “birthday attack” on digital signature q Then Nostradamus attack o Learn how to predict the future! o Works against any hash that uses Merkle. Damgard construction Hash Functions 22

Pre-Birthday Problem q Suppose N people in a room q How large must N be before the probability someone has same birthday as me is at least 1/2 o Solve: 1/2 = 1 (364/365)N for N o Find N = 253 Hash Functions 23

Birthday Problem q How many people must be in a room before probability is at least 1/2 that any two or more have same birthday? o 1 365/365 364/365 (365 N+1)/365 o Set equal to 1/2 and solve: N = 23 q Surprising? A paradox? q No, it “should be” about sqrt(365) since compare pairs x and y Hash Functions 24

Of Hashes and Birthdays If h(x) is N bits, 2 N hash values q Note that sqrt(2 N) = 2 N/2 q So, hash 2 N/2 inputs and find a collision q o “Birthday attack” — an exhaustive search An N-bit symmetric cipher key requires at most 2 N 1 work to “break” q An N-bit hash: at most 2 N/2 work to “break” q Hash Functions 25

Signature Birthday Attack q Suppose hash output is n bits q Trudy selects evil message E o Wants to get Alice’s signature on E q Trudy creates innocent message I o Alice willing to sign message I q How Hash Functions can Trudy use birthday problem? 26

Signature Birthday Attack q Trudy creates 2 n/2 variants of I o All have same meaning as I o Trudy hashes each: h(I 0), h(I 1), … q Trudy creates 2 n/2 variants of E o All have same meaning as E o Trudy hashes each: h(E 0), h(E 1), … q By birthday problem, h(Ij)= h(Ek), some j, k Hash Functions 27
![Signature Birthday Attack q Alice signs innocent message Ij q Then Trudy has hIjAlice Signature Birthday Attack q Alice signs innocent message Ij q Then Trudy has [h(Ij)]Alice](https://slidetodoc.com/presentation_image_h/2747ac99fc8d60308c93e51b8494255b/image-28.jpg)
Signature Birthday Attack q Alice signs innocent message Ij q Then Trudy has [h(Ij)]Alice q But [h(Ij)]Alice = [h(Ek)]Alice q Alice unwittingly “signed” evil msg Ek q Attack relies only on birthday problem Hash Functions 28

Online Bid Example Suppose Alice, Bob, Charlie are bidders q Alice plans to bid A, Bob B and Charlie C q o They do not trust that bids will be secret o Nobody willing to submit their bid q Solution? o Alice, Bob, Charlie submit hashes h(A), h(B), h(C) o All hashes received and posted online o Then bids A, B and C revealed Hashes do not reveal bids (one way) q Cannot change bid after hash sent (collision) q Hash Functions 29

Online Bid q This protocol is not secure! q A forward search attack is possible o Bob computes h(A) for likely bids A q How to prevent this? q Alice computes h(A, R), R is random o Then Alice must reveal A and R o Trudy cannot try all A and R Hash Functions 30

Online Bid q Spse B = $1000 and Bob submits h(B, R) q When revealed, A = $1 and C = $2 q Bob wants to change his bid: B = $3 q Bob computes h(B , R ) for different R until he finds h(B , R ) = h(B, R) o How much work? o Apparently, about 2 n hashes required Hash Functions 31

Weak Collision Attack q Hash often used to commit to something o For example, online bid example Attack on weak collision resistance requires work of about 2 n hashes q Collision attack is only about 2 n/2 q Nostradamus attack solves weak collision problem with only about 2 n/2 hashes q o For some cases, such as online bid example o Applicable to any Merkle-Damgard hash Hash Functions 32

Trudy Predicts Future? Trudy claims she can predict future q Jan 1, 2008, she publishes y, claiming y = h(x) q o Where x includes final S&P 500 index for 2008 and other predictions for 2009 and beyond q Jan 1, 2009, Trudy reveals x, with y = h(x) o And x has S&P 500 index for Dec. 31, 2008 along with other rambling predictions for 2009 q Does this prove Trudy can predict future? Hash Functions 33

Trudy Predicts Future? q Trudy specifies y in advance q Let P be S&P 500 for Dec 31, 2008 q Assuming Trudy cannot predict future, she must find S so that y = h(P, S) q Trudy can hash 2 n different S o But, we assume this is too much work q Is there any shortcut? Hash Functions 34

Nostradamus Attack q Nostradamus (1503 -1566) was a prophet o Some claim he predicted recent events o His predictive powers work best in retrospect q Nostradamus attack o Trudy can “predict” the future o Convert 2 n pre-image problem into about 2 n/2 collision attack (essentially) o Applies to any Merkle-Damgard hash function Hash Functions 35

Nostradamus Attack q Computing collisions: each 2 2 n/2 work o Comparing one set to another set q Pre-compute collisions in clever way q This determines y, the hash value q When we specify prefix P, we can “herd” collisions into hash value y o Suffix S determined in this process Hash Functions 36

Diamond Structure q Choose M 0 randomly q Compute d 00 = f(IV, M 0) q And M 1, …, M 7 q Then find M 00, M 01 that give collision: d 10 = f(d 00, M 00) = f(d 01, M 01) q Continue: y = d 30 is “predicted” hash Hash Functions 37

Nostradamus Attack q Pre-computation o Compute diamond structure of “height” 2 k o Choose y = dk 0 as hash of prediction q When “prediction” is known, Trudy will o Let P be “prediction” o Select S at random, where (P, S ) one block o Until she finds f(IV, P, S ) = d 0 j for some j Hash Functions 38

Nostradamus Attack q Once such S is found, Trudy has result o Follow directed path from d 0 j to dk 0 In previous diamond structure example, suppose Trudy finds f(IV, P, S ) = d 02 q Then h(P, S , M 02, M 11, M 20) = d 30 = y q o Recall that y is hash of Trudy’s “prediction” Let x = (P, S , M 02, M 11, M 20) q And x is Trudy’s “prediction”: P is S&P 500 index, S , M 02, M 11, M 20 are future predictions q Hash Functions 39

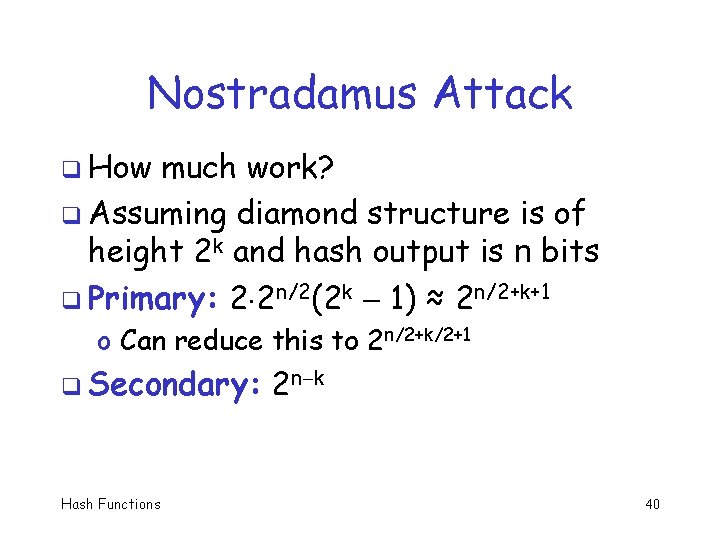
Nostradamus Attack q How much work? q Assuming diamond structure is of height 2 k and hash output is n bits q Primary: 2 2 n/2(2 k 1) ≈ 2 n/2+k+1 o Can reduce this to 2 n/2+k/2+1 q Secondary: Hash Functions 2 n k 40

Nostradamus Attack q To minimize work, set primary work equal to secondary work, solve for k q We have n/ 2 + k/ 2 + 1 = n k which implies k = (n 4) / 3 q For MD 4 or MD 5, n = 128, so k = 41 q Diamond structure of height 241 q Total work is about 287 Hash Functions 41

Nostradamus: Bottom Line q Generic attack on any hash that uses Merkle-Damgard construction q Not practical for 128 -bit hash o Almost practical with small success prob q Using hash to commit to something is not quite as strong as it seems q Next, MD 4 and MD 5 o Must look at inner workings of these… Hash Functions 42