Motivation Hash Functions collision preimages SHA1 Hash Functions








- Slides: 17

- Motivation - Hash Functions: collision, pre-images - SHA-1 Hash Functions CSCI 284 Spring 2009 GWU CS 284/Spring 09/GWU/Vora/Hash Functions

The problems crypto addresses • Confidentiality/secrecy/privacy – How to keep a message secret so it can be read only by a chosen person – Use encryption • Integrity – How to determine a string of symbols has not been changed since it was created – ? 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 2

Integrity • Alice sends message x to Bob. She fears Oscar will manipulate it along the way, and Bob will get an incorrect message. • She could encrypt it using a key Oscar did not have, but is that overkill when she does not need to prevent Oscar from reading it? • But maybe she could tell Bob something else about the message so he would know if something was terribly wrong: parity, last bit, a particular bit, etc. 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 3

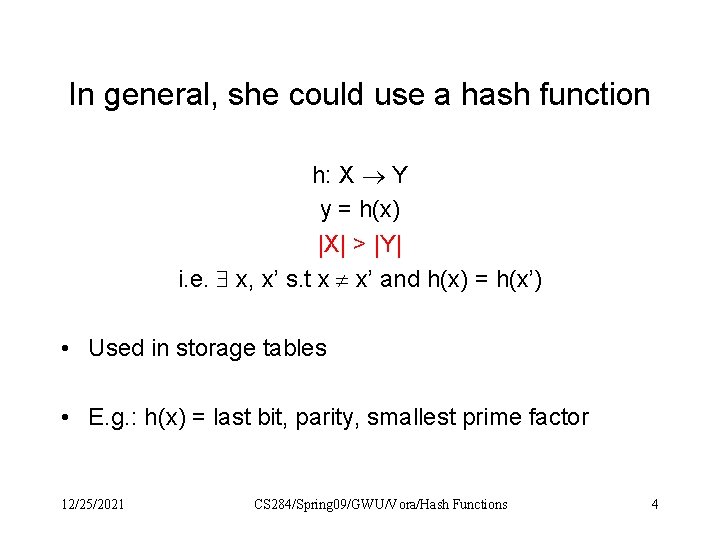
In general, she could use a hash function h: X Y y = h(x) |X| > |Y| i. e. x, x’ s. t x x’ and h(x) = h(x’) • Used in storage tables • E. g. : h(x) = last bit, parity, smallest prime factor 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 4

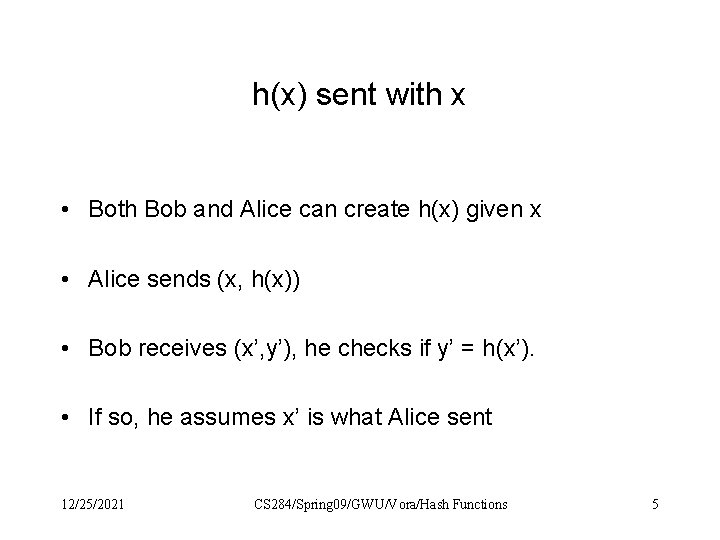
h(x) sent with x • Both Bob and Alice can create h(x) given x • Alice sends (x, h(x)) • Bob receives (x’, y’), he checks if y’ = h(x’). • If so, he assumes x’ is what Alice sent 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 5

In either case, what can the attacker do? • If he can compute h(x), he can: – try to find x’ s. t. h(x) = h(x’). • If he knows h, and can influence Alice, he can – try to get her to send an x that she likes such that h(x) = h(x’) for an x’ he likes. • If he doesn’t, he hopes for the best. 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 6

Hence require an h “secure” in the following ways: • Secure wrt second image requires that the following problem is “difficult”: – Given an x X, find x’ X s. t x’ x but h(x’) = h(x) • Secure wrt collision requires that the following problem is “difficult”: – Find x, x’ X s. t x’ x but h(x’) = h(x) • The above should be true even if h(x 1), h(x 2). . h(xn) are known 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 7

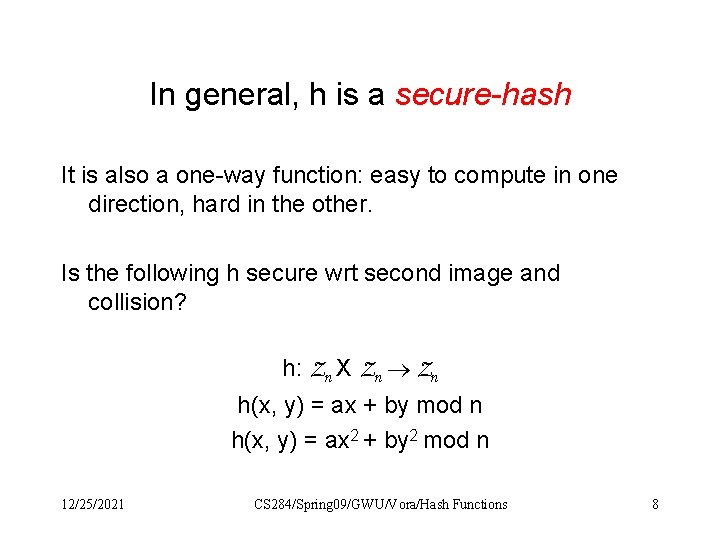
In general, h is a secure-hash It is also a one-way function: easy to compute in one direction, hard in the other. Is the following h secure wrt second image and collision? h: Zn X Zn h(x, y) = ax + by mod n h(x, y) = ax 2 + by 2 mod n 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 8

Easy? • How does one define easy/difficult to compute? • Using computational complexity theory • By requiring a large time for the computation on any computer given a particular computational model • For example, the probabilistic polynomial-time model 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 9

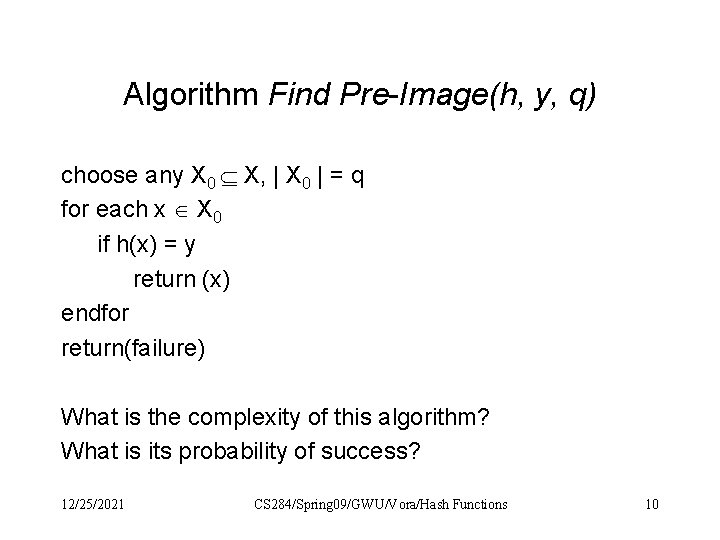
Algorithm Find Pre-Image(h, y, q) choose any X 0 X, | X 0 | = q for each x X 0 if h(x) = y return (x) endfor return(failure) What is the complexity of this algorithm? What is its probability of success? 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 10

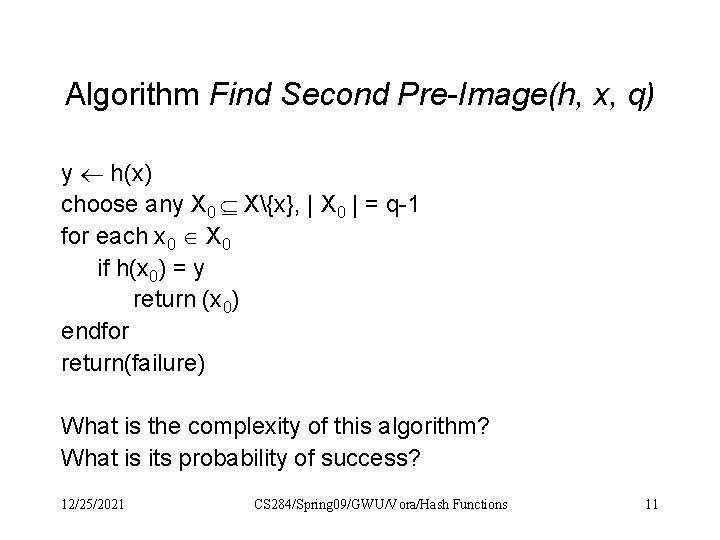
Algorithm Find Second Pre-Image(h, x, q) y h(x) choose any X 0 X{x}, | X 0 | = q-1 for each x 0 X 0 if h(x 0) = y return (x 0) endfor return(failure) What is the complexity of this algorithm? What is its probability of success? 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 11

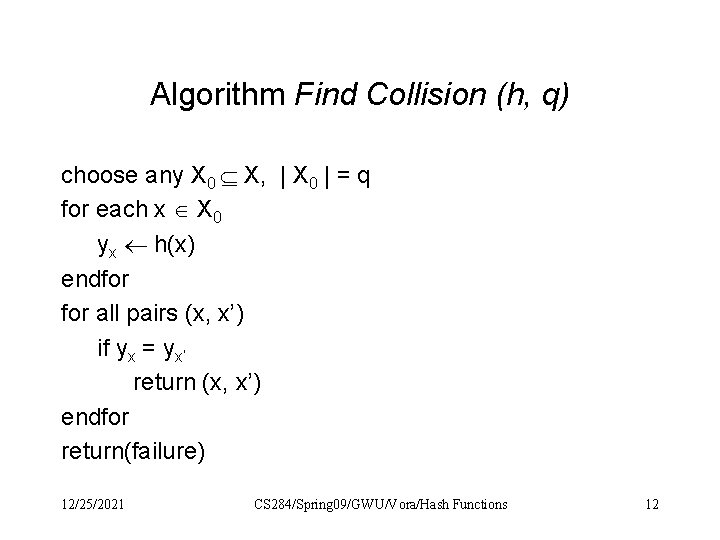
Algorithm Find Collision (h, q) choose any X 0 X, | X 0 | = q for each x X 0 yx h(x) endfor all pairs (x, x’) if yx = yx’ return (x, x’) endfor return(failure) 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 12

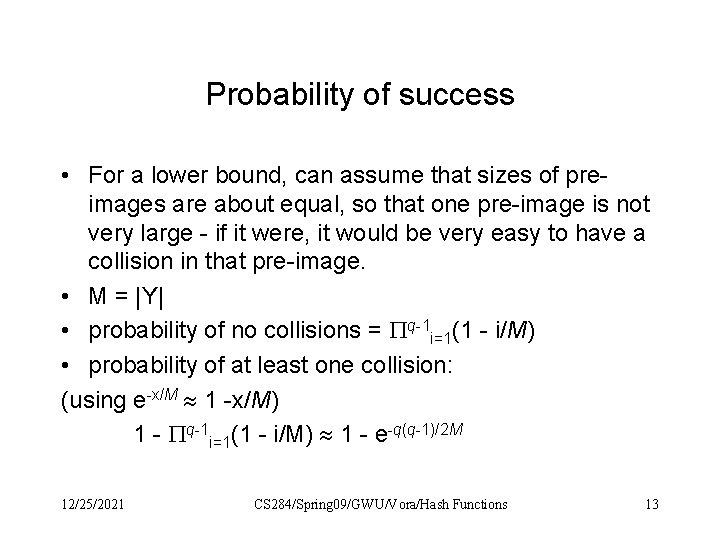
Probability of success • For a lower bound, can assume that sizes of preimages are about equal, so that one pre-image is not very large - if it were, it would be very easy to have a collision in that pre-image. • M = |Y| • probability of no collisions = q-1 i=1(1 - i/M) • probability of at least one collision: (using e-x/M 1 -x/M) 1 - q-1 i=1(1 - i/M) 1 - e-q(q-1)/2 M 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 13

Allowed n, q For a given acceptable collision probability p, what is q in terms of M and p? p = 1 - q-1 i=1(1 - i/M) 1 - e-q(q-1)/2 M q (2 M ln(1/1 -p)) For p = 0. 5, q 1. 17 M if M = 365, q 23 and the probability of 2 people having the same birthday in a group of 23 people is more than 0. 5 – Birthday attack/paradox 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 14

Complexities/Probability of success • Find Pre-Image – Success Probability: 1 -(1 -1/M)q q/M – Complexity: (q) • Find Second Pre-Image – Success Probability: 1 -(1 -1/M)q-1 q/M – Complexity: (q) • Find Collision – Success Probability: 1 - q-1 i=1(1 - i/M) 1 - e-q(q-1)/2 M – Complexity: (q 2) 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 15

SHA-1 • Pad given string x so that it is of length a multiple of 512 bits. Call this string y = M 1||M 2||…||Mn • Iteratively calculate the hash of y using a hash function (known as the compression function) for 512 bits (hash is of length 160 bits) • What is complexity of a birthday attack? 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 16

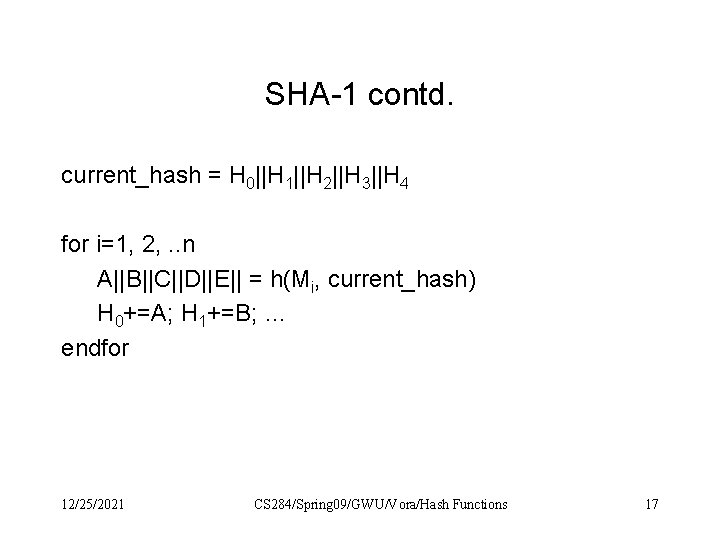
SHA-1 contd. current_hash = H 0||H 1||H 2||H 3||H 4 for i=1, 2, . . n A||B||C||D||E|| = h(Mi, current_hash) H 0+=A; H 1+=B; … endfor 12/25/2021 CS 284/Spring 09/GWU/Vora/Hash Functions 17