CCM 4300 Lecture 7 Computer Networks Wireless and
























![Symmetric key crypto: DES: Data Encryption Standard n. US encryption standard [NIST 1993] n Symmetric key crypto: DES: Data Encryption Standard n. US encryption standard [NIST 1993] n](https://slidetodoc.com/presentation_image/46923ec13b48b52fbf43110d501d242d/image-35.jpg)












- Slides: 88

CCM 4300 Lecture 7 Computer Networks, Wireless and Mobile Communications Dr E. Ever School of Computing Science ccm 4300 1

Lesson objectives - Understand principles of network security: m. Cryptography and its many uses beyond “confidentiality”. m. Authentication. m. Message integrity and non-repudiation. m. Availability and access control. m. Key distribution. -Security in practice: m. Firewalls and IDS m. Security and protocols in application, transport, network, and link layers. ccm 4300 2

Session Content §What is network security? §Principles of cryptography §Authentication §Integrity §Key Distribution and certification §Access control: firewalls §Attacks and counter measures §Security in many layers ccm 4300 3

What is Network Security? n n Confidentiality: only sender, intended receiver should “understand” message contents sender encrypts message receiver decrypts message Authentication: sender, receiver want to confirm identity of each other Message Integrity and Non-Repudiation: sender, receiver want to ensure message not altered (in transit, or afterwards) without detection, and want to be able to prove that the sender did, in fact, send the message Access and Availability: services must be accessible and available to properly authorised users ccm 4300 4

Why is Network Security Difficult? n n n n Open and interoperable protocols, while desirable, tend to work against security. Security is often sacrificed in return for gains in performance and scalability. Providing good security is expensive, so it an be difficult to get resources to support it. People tend to see security as a barrier to getting useful work done, and resist it. Information on circumventing security is widely available, as are software tools. (view it as a puzzle) Some people see circumventing security as a challenge and enjoy doing it. (fun) Most systems and networks were not designed with any security concerns in mind. (not involved in the initial stage) ccm 4300 5

Security Planning, Policies, and Mechanisms n A secure network does not come naturally. First, a security plan must be developed. Based on this plan, security policies must be developed. n. To enforce these policies, the appropriate security mechanisms must be put in place. n n This is not a one time effort either. Security plans must be reviewed and revised. n. Security policies must be assessed and updated. n. Security mechanisms must be patched, updated, or replaced as newer technologies become available. ccm 4300 6 n

Security Planning, Policies, and Mechanisms n Security planning must do the following: n Determine what your security needs are. n Determine what your security threats and risks are. n Identify who can be trusted to do what. Security policies are developed from this information, so be as specific as possible. n ccm 4300 7

Security Planning, Policies, and Mechanisms Security policies that are developed must ensure appropriate levels of security for the activities performed in the network by: n. Making it clear what is protected and why. n. Clearly stating responsibility for providing that protection. n. Making it clear what users are allowed to do, and what they must or must not do. n. Providing grounds on how to interpret and resolve conflicts in policies later on. ccm 4300 8

Security Planning, Policies, and Mechanisms n. Security mechanisms are employed to ensure that security policies are being adequately enforced. n. Mechanisms can be based on people, software, hardware, or other physical means (for example, cameras, locks, cabling, and so on). n. Choosing the right mechanisms can be difficult. n. Can these mechanisms be trusted? n. Determining if the mechanisms fully implement the desired security policies is even harder. n. You can try a formal proof, but those are complex and very time consuming. n. Addressing the problem of characterising and proving security properties has led to an immensely promising research programme in computer security using CSP (Communication Sequential Process) and its modelchecker, FDR (Failure Divergence Refinement Checker). The result is a well-developed and intellectually-satisfying theory of security in CSP, where formal proof is replaced by automatic checking. ccm 4300 9

Security Mechanisms n. These Mechanisms exist to provide and support security services and can be divided into two classes: Specific security mechanisms, used to provide specific security services, and n. Pervasive security mechanisms, not specific to particular services. n ccm 4300 10

Specific Security Mechanisms n Eight types: encipherment, ndigital signature, naccess control mechanisms, ndata integrity mechanisms, nauthentication exchanges, ntraffic padding, nrouting control, nnotarisation. n ccm 4300 11

Specific Mechanisms n n n Encipherment mechanisms = encryption algorithms. n Can provide data and traffic flow confidentiality. Digital signature mechanisms n signing procedure (private), n verification procedure (public). n Can provide non-repudiation, origin authentication and data integrity services. Both can be basis of some authentication exchange mechanisms. ccm 4300 12

Specific Mechanisms … cont. . n n n Access Control mechanisms n A server using client information to decide whether to grant access to resources n E. g. access control lists, capabilities, security labels. Data integrity mechanisms n Protection against modification of data. n Provide data integrity and origin authentication services. Also basis of some authentication exchange mechanisms. Authentication exchange mechanisms n Provide entity authentication service. ccm 4300 13

Specific Mechanisms … cont. . n Traffic padding mechanisms n n n Routing control mechanisms n n n The addition of ‘pretend’ data to conceal real volumes of data traffic. Provides traffic flow confidentiality. Used to prevent sensitive data using insecure channels. E. g. route might be chosen to use only physically secure network components. Notarisation mechanisms n Integrity, origin and/or destination of data can be guaranteed by using a third party trusted notary. n Notary typically applies a cryptographic transformation to the data. ccm 4300 14

Security Threats Q: What could an INTRUDER do? A: Unfortunately, a lot more than you think! ninterruption: somehow disrupt the service being provided by the network to communicating parties ninterception: eavesdrop on communication meant to be private or confidential nmodification: tamper with information or network resources nfabrication: counterfeit information or network resources or services are inserted into the network ccm 4300 15

Security Threats: Interruption In an interruption attack, a network service is made degraded or unavailable for legitimate use. n. Interruption attacks are attacks against the availability of the network. n. These attacks can take the form of: {DOS} n Overloading a server host so that it cannot respond. n. Blocking access to a service by overloading an intermediate network or network device. n. Redirecting requests to invalid destinations. n. Vandalizing software or hardware involved. n. Theft of software or hardware involved. n ccm 4300 16

Security Threats: Interception In an interception attack, an unauthorized individual gains access to confidential or private information. n. Interception attacks are attacks against network confidentiality. n. These attacks can take the form of: n. Eavesdropping on communication. n. Wiretapping telecommunications networks. n. Illicit copying of files or programs. n. Obtaining copies of messages for later replay. n ccm 4300 17

Security Threats: Modification In a modification attack, an unauthorised individual not only gains access to, but tampers with information, resources, or services. n. Modification attacks are attacks against the integrity of the network. n. These attacks can take the form of: n Modifying the contents of messages in the network. n. Changing information stored in data files. n. Altering programs so they perform differently. n. Reconfiguring system hardware or network topologies. n n Also called “man in the middle” attacks. ccm 4300 18

Security Threats: Fabrication n In a fabrication attack, an individual inserts counterfeit information, resources, or services into the network. Fabrication attacks are attacks against the authentication, access control, and authorisation capabilities of the network. These attacks can take the form of: n n n Inserting messages into the network using the identity of another individual. Replaying previously intercepted messages. Spoofing a web site or other network service. Taking the address of another host or service, essentially becoming that host or service. Also called “masquerading” attacks. ccm 4300 19

Security Threats: Methods of Execution Attacks on security can be carried out using software or hardware tools, or by some other physical means. n. Common software examples include: n. Tools and toolkits: programs that automatically probe for security weaknesses or attack systems. n. Back doors and trap doors: openings (in code, firewalls, and so on) intentionally left open to grant access to individuals without going through normal methods of authentication and authorization. n. Logic bombs: code embedded in software that lies dormant until some event triggers them to carry out ccm 4300 20 an attack. n

Security Threats: Methods of Execution n n Additional common software examples: n Viruses: executable code inserted into other code or data that is executed when the other code or data is used, and launches an attack. n Worms: relatively independent programs that travel from machine to machine across network connections to carry out attacks. n Trojan horses: programs that appear to have one function but actually perform a hidden function that attacks the system. n Bacteria or rabbit programs: programs that do no damage other than replicate themselves exponentially to overwhelm network resources. ccm 4300 21 Sometimes, these can work together too.

Security Services and Mechanisms Recall: A security threat is a possible means by which a security policy may be breached (e. g. loss of integrity or confidentiality). n. Recall: A security mechanism is a means to provide a service (e. g. encryption, digital signature). n. A security service is a measure which can be put in place to address a threat (e. g. provision of confidentiality). n ccm 4300 22

Security Service Classification n Security services in ISO 7498 -2 are a special class of safeguard applying to a communications environment. Five main categories of security service: n Authentication (including entity authentication and origin authentication), n Access control, n Data confidentiality, n Data integrity, n Non-repudiation. Sixth category: “other” – includes physical security, personnel security, life-cycle controls, … ccm 4300 23

Authentication n Entity authentication provides checking of a claimed identity at a point in time. n. Typically used at start of a connection. n. Addresses masquerade and replay threats. n. Origin authentication provides verification of source of data. ccm 4300 24

Access Control Provides protection against unauthorised use of resource, including: nuse of a communications resource, nreading, writing or deletion of an information resource, nexecution of a processing resource. n n Example: file permissions in Unix/NT file systems. ccm 4300 25

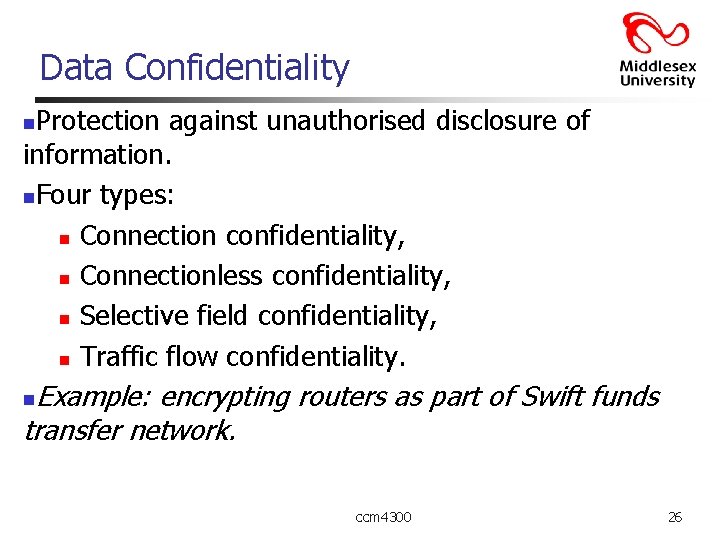
Data Confidentiality Protection against unauthorised disclosure of information. n. Four types: n Connection confidentiality, n Connectionless confidentiality, n Selective field confidentiality, n Traffic flow confidentiality. n Example: encrypting routers as part of Swift funds transfer network. n ccm 4300 26

Data Integrity Provides protection against active threats to the validity of data. n. Five types: n. Connection integrity with recovery, n. Connection integrity without recovery, n. Selective field connection integrity, n. Connectionless integrity, Selective field connectionless integrity. n Example: MD 5 hashes on software at http: //www. apache. org/dist/httpd/binaries/linux/ Example: AH protocol in IPSec ccm 4300 27

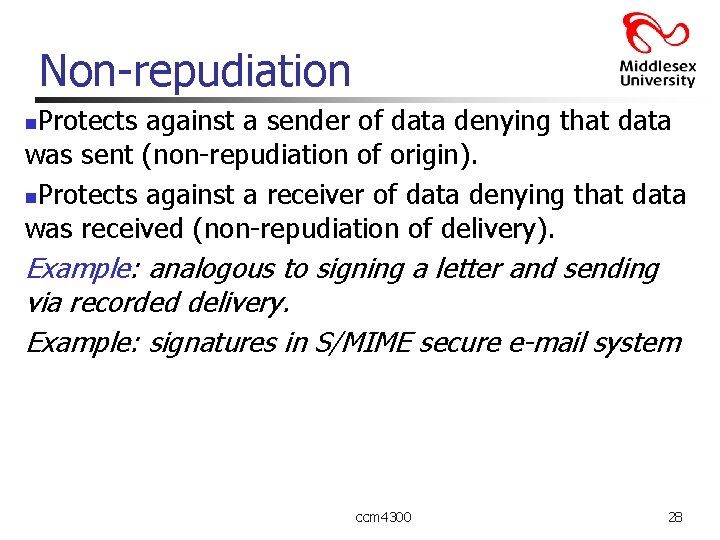
Non-repudiation Protects against a sender of data denying that data was sent (non-repudiation of origin). n. Protects against a receiver of data denying that data was received (non-repudiation of delivery). n Example: analogous to signing a letter and sending via recorded delivery. Example: signatures in S/MIME secure e-mail system ccm 4300 28

Security Provisioning n n n How can we protect ourselves from these attacks? Interruption attacks: n Firewalls, replication, backups, hardware appliances Interception attacks: n Encryption, traffic padding Modification attacks: n Encryption, traffic padding, backups, messaging techniques (checksums, sequence numbers, digests, authentication codes) Fabrication attacks: n Authentication and authorisation, firewalls, digital signatures ccm 4300 29

Security Principles To Follow n n n n n There is no a 100% secure environment. Expect the unexpected. The more you know the better you can defend your system. The more someone knows about you, the better they can exploit you. Do unto yourself before someone does unto you. Never assume that all security risks are from the outside, and not the inside. Never assume that your users know what they are doing. Security is only as good as the least secure link in the chain. Security is a process, not an end product. Do not forget about the simple aspects of physical security ccm 4300 30

Security Principles To Follow m The following are rules/principles you may or may not follow: m Policy first, access second. m Deny first, permit only when required. m Mistrust everyone. ccm 4300 31

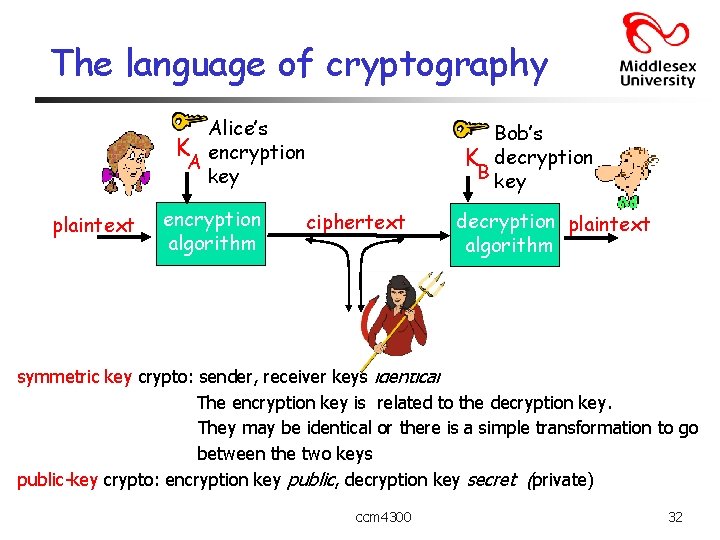
The language of cryptography Alice’s K encryption A key plaintext encryption algorithm Bob’s K decryption B key ciphertext decryption plaintext algorithm symmetric key crypto: sender, receiver keys identical The encryption key is related to the decryption key. They may be identical or there is a simple transformation to go between the two keys public-key crypto: encryption key public, decryption key secret (private) ccm 4300 32

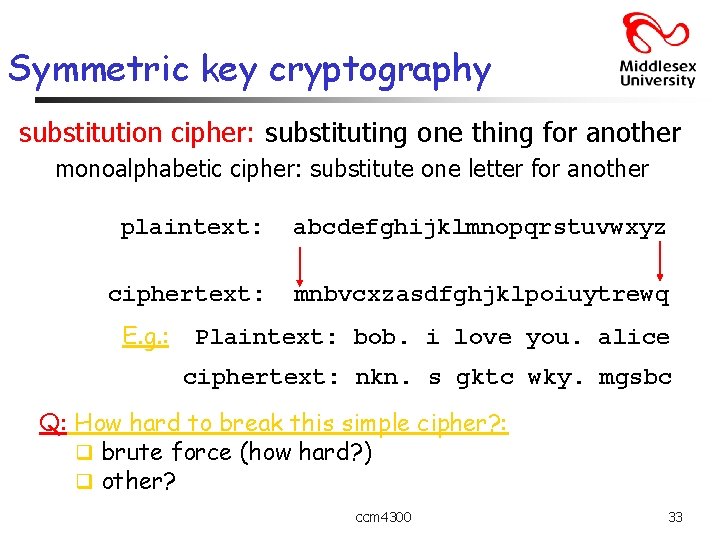
Symmetric key cryptography substitution cipher: substituting one thing for another monoalphabetic cipher: substitute one letter for another plaintext: abcdefghijklmnopqrstuvwxyz ciphertext: mnbvcxzasdfghjklpoiuytrewq E. g. : Plaintext: bob. i love you. alice ciphertext: nkn. s gktc wky. mgsbc Q: How hard to break this simple cipher? : q brute force (how hard? ) q other? ccm 4300 33

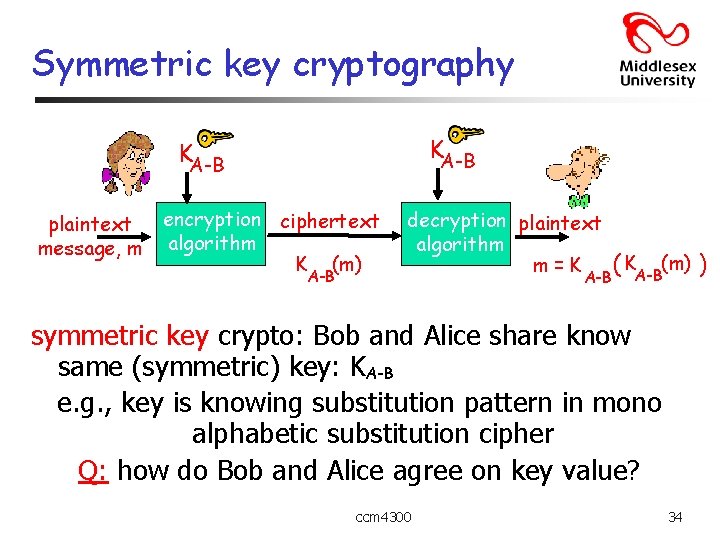
Symmetric key cryptography KA-B plaintext message, m encryption ciphertext algorithm K (m) A-B decryption plaintext algorithm m=K A-B ( KA-B(m) ) symmetric key crypto: Bob and Alice share know same (symmetric) key: KA-B e. g. , key is knowing substitution pattern in mono alphabetic substitution cipher Q: how do Bob and Alice agree on key value? ccm 4300 34
![Symmetric key crypto DES Data Encryption Standard n US encryption standard NIST 1993 n Symmetric key crypto: DES: Data Encryption Standard n. US encryption standard [NIST 1993] n](https://slidetodoc.com/presentation_image/46923ec13b48b52fbf43110d501d242d/image-35.jpg)
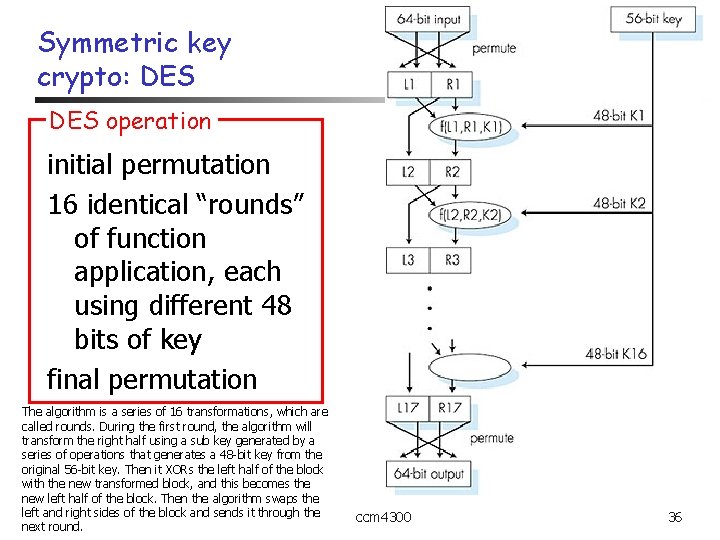
Symmetric key crypto: DES: Data Encryption Standard n. US encryption standard [NIST 1993] n 56 -bit symmetric key, 64 -bit plaintext input n. How secure is DES? n. DES Challenge: 56 -bit-key-encrypted phrase (“Strong cryptography makes the world a safer place”) decrypted (brute force) in 4 months nno known “backdoor” decryption approach nmaking DES more secure: nuse three keys sequentially (3 -DES) on each datum nuse cipher-block chaining n ccm 4300 35

Symmetric key crypto: DES operation initial permutation 16 identical “rounds” of function application, each using different 48 bits of key final permutation The algorithm is a series of 16 transformations, which are called rounds. During the first round, the algorithm will transform the right half using a sub key generated by a series of operations that generates a 48 -bit key from the original 56 -bit key. Then it XORs the left half of the block with the new transformed block, and this becomes the new left half of the block. Then the algorithm swaps the left and right sides of the block and sends it through the next round. ccm 4300 36

AES: Advanced Encryption Standard new (Nov. 2001) symmetric-key NIST standard, replacing DES nprocesses data in 128 bit blocks n 128, 192, or 256 bit keys nbrute force decryption (try each key) taking 1 sec on DES, takes 149 trillion years for AES n ccm 4300 37

Public Key Cryptography symmetric key crypto n n requires sender, receiver know shared secret key Q: how to agree on key in first place (particularly if never “met”)? public key cryptography radically different approach [Diffie. Hellman 76, RSA 78] sender, receiver do not share secret key public encryption key known to all private decryption key known only to receiver ccm 4300 38

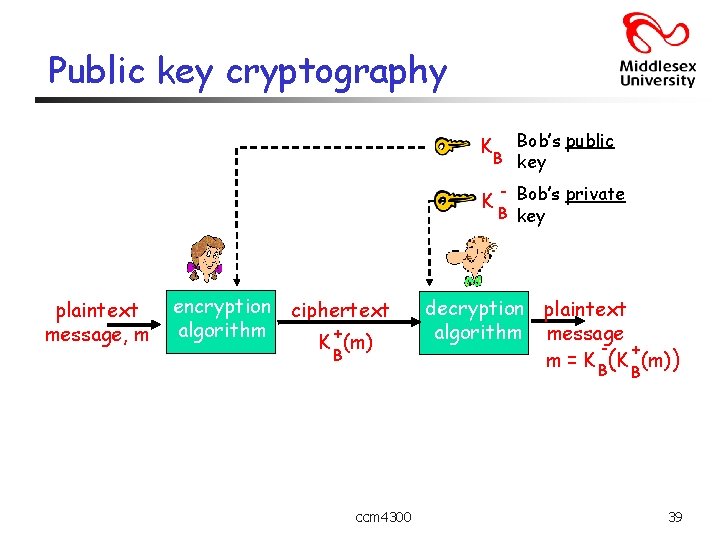
Public key cryptography Bob’s public B key K K plaintext message, m encryption ciphertext algorithm + K (m) B - Bob’s private B key decryption plaintext algorithm message + m = K B(K (m)) B ccm 4300 39

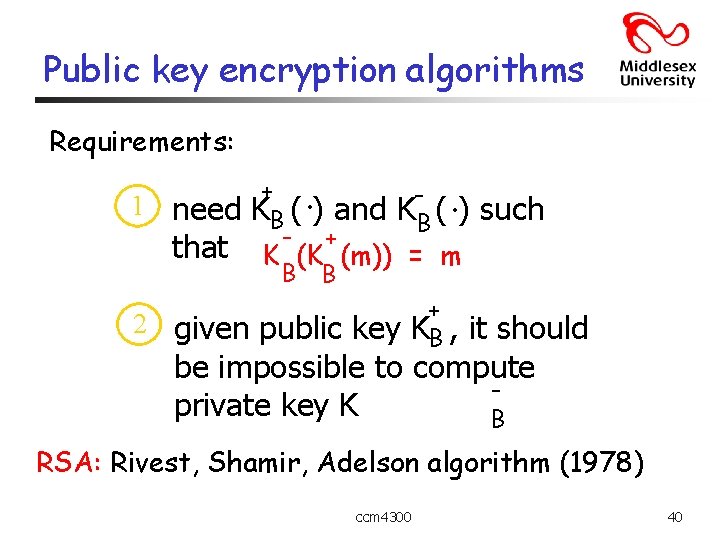
Public key encryption algorithms Requirements: 1 need that + KB ( - . ) and K-B (. ) such + K (K (m)) = m B B 2 given public key + KB , it should be impossible to compute private key K B RSA: Rivest, Shamir, Adelson algorithm (1978) ccm 4300 40

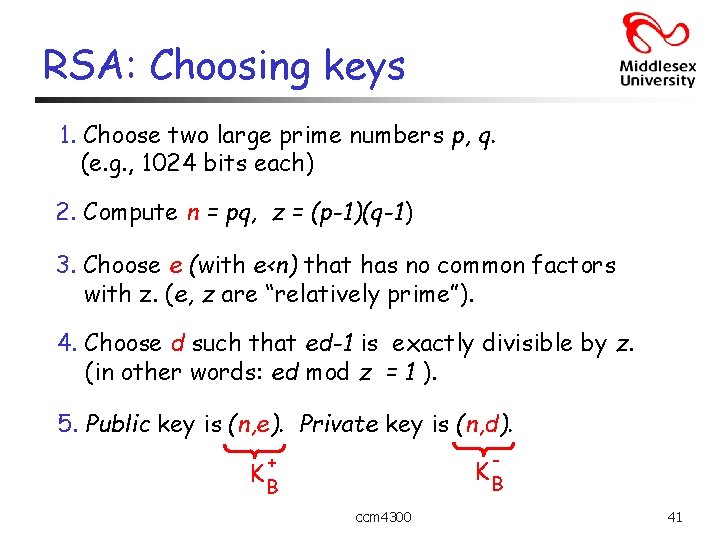
RSA: Choosing keys 1. Choose two large prime numbers p, q. (e. g. , 1024 bits each) 2. Compute n = pq, z = (p-1)(q-1) 3. Choose e (with e<n) that has no common factors with z. (e, z are “relatively prime”). 4. Choose d such that ed-1 is exactly divisible by z. (in other words: ed mod z = 1 ). 5. Public key is (n, e). Private key is (n, d). - + KB KB ccm 4300 41

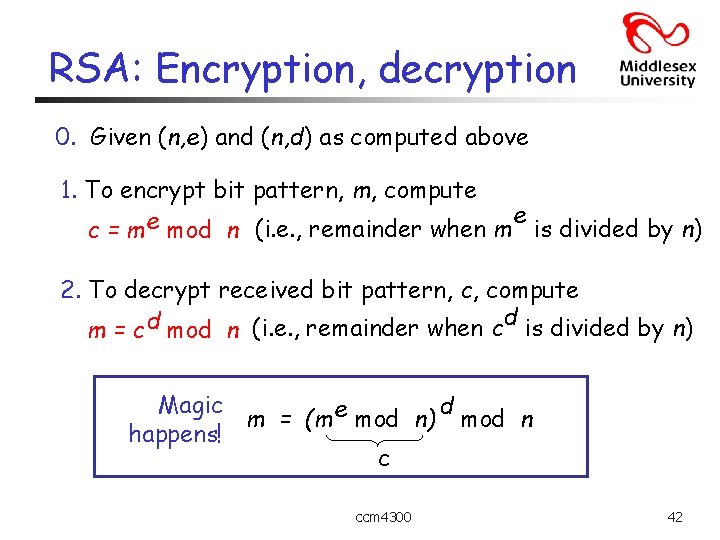
RSA: Encryption, decryption 0. Given (n, e) and (n, d) as computed above 1. To encrypt bit pattern, m, compute e e c = m mod n (i. e. , remainder when m is divided by n) 2. To decrypt received bit pattern, c, compute d m = c d mod n (i. e. , remainder when c is divided by n) Magic d m = (m e mod n) mod n happens! c ccm 4300 42

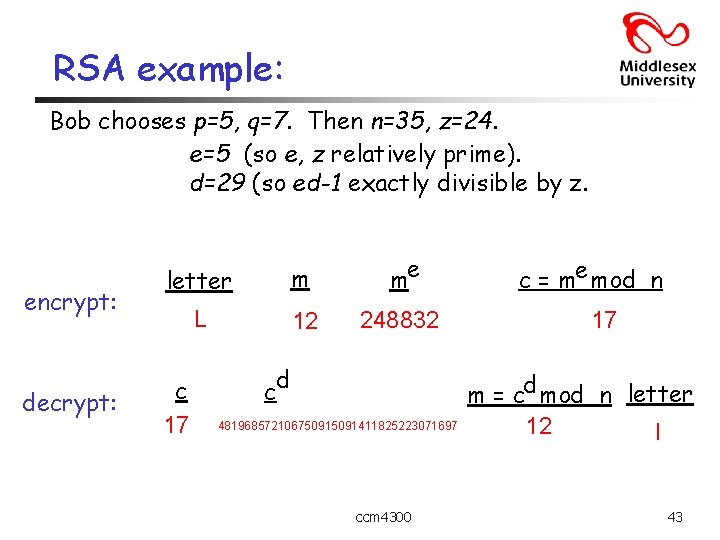
RSA example: Bob chooses p=5, q=7. Then n=35, z=24. e=5 (so e, z relatively prime). d=29 (so ed-1 exactly divisible by z. encrypt: decrypt: letter m me L 12 248832 c 17 d c 48196857210675091411825223071697 ccm 4300 c = me mod n 17 m = cd mod n letter 12 l 43

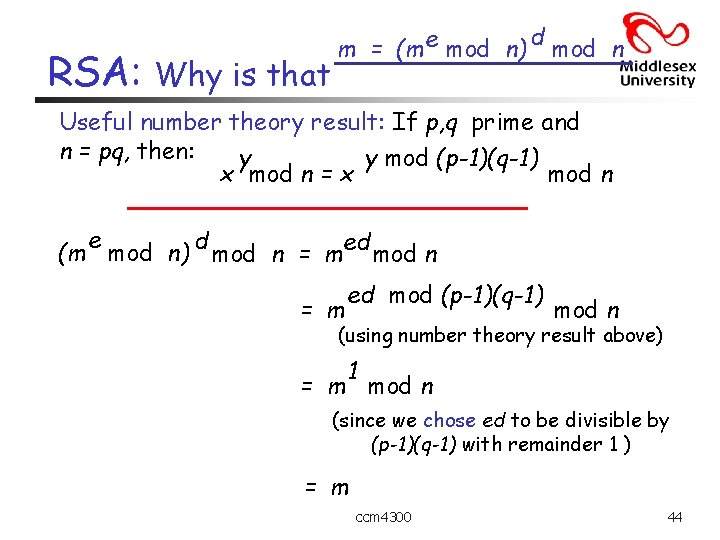
RSA: Why is that m = (m e mod n) d mod n Useful number theory result: If p, q prime and n = pq, then: y y mod (p-1)(q-1) x mod n = x mod n e (m mod n) d mod n = med mod n = m ed mod (p-1)(q-1) mod n (using number theory result above) 1 = m mod n (since we chose ed to be divisible by (p-1)(q-1) with remainder 1 ) = m ccm 4300 44

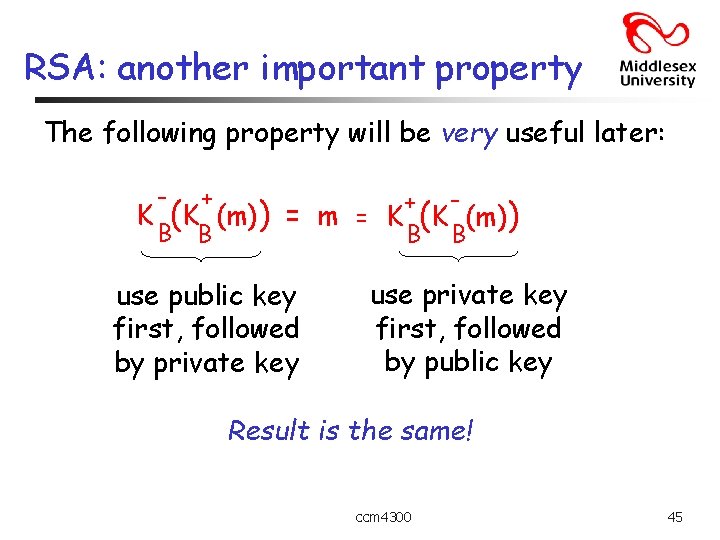
RSA: another important property The following property will be very useful later: - + B B K (K (m)) + = m = K (K (m)) B B use public key first, followed by private key use private key first, followed by public key Result is the same! ccm 4300 45

Where are we? n n n n What is network security? Principles of cryptography Authentication Integrity Key Distribution and certification Access control: firewalls Attacks and counter measures Security in many layers ccm 4300 46

Authentication Goal: Bob wants Alice to “prove” her identity to him Protocol ap 1. 0: Alice says “I am Alice” Failure scenario? ? ccm 4300 47

Authentication Goal: Bob wants Alice to “prove” her identity to him Protocol ap 1. 0: Alice says “I am Alice” in a network, Bob can not “see” Alice, so Trudy simply declares herself to be Alice ccm 4300 48

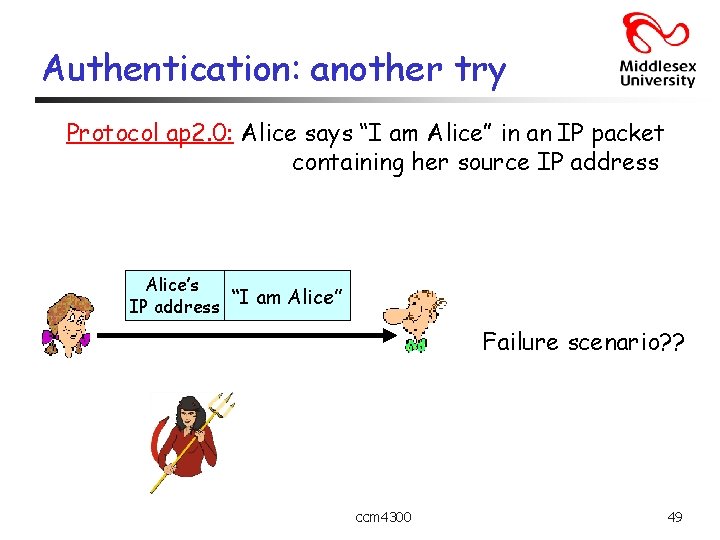
Authentication: another try Protocol ap 2. 0: Alice says “I am Alice” in an IP packet containing her source IP address Alice’s “I am Alice” IP address Failure scenario? ? ccm 4300 49

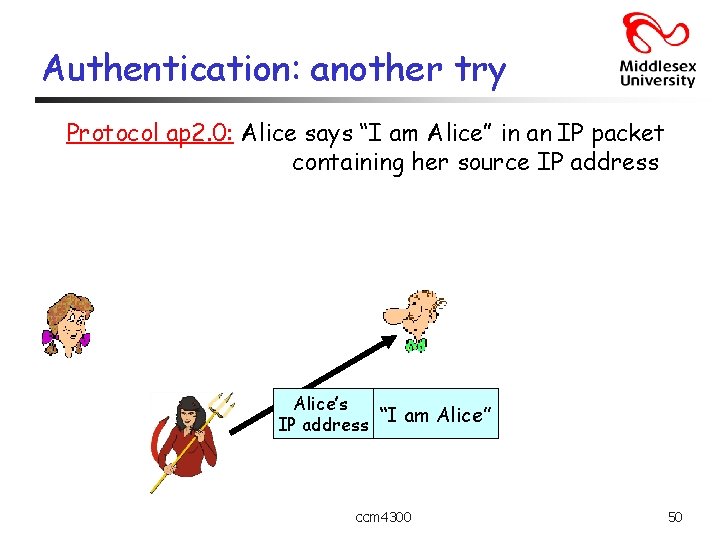
Authentication: another try Protocol ap 2. 0: Alice says “I am Alice” in an IP packet containing her source IP address Alice’s “I am Alice” IP address ccm 4300 50

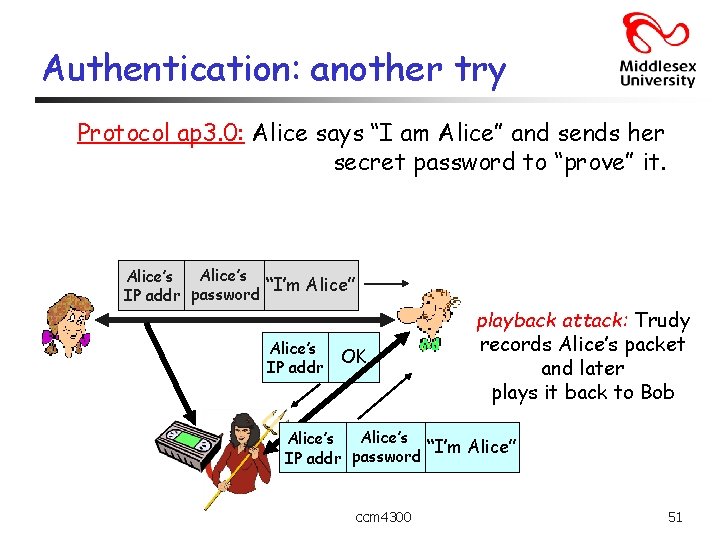
Authentication: another try Protocol ap 3. 0: Alice says “I am Alice” and sends her secret password to “prove” it. Alice’s “I’m Alice” IP addr password Alice’s IP addr OK playback attack: Trudy records Alice’s packet and later plays it back to Bob Alice’s “I’m Alice” IP addr password ccm 4300 51

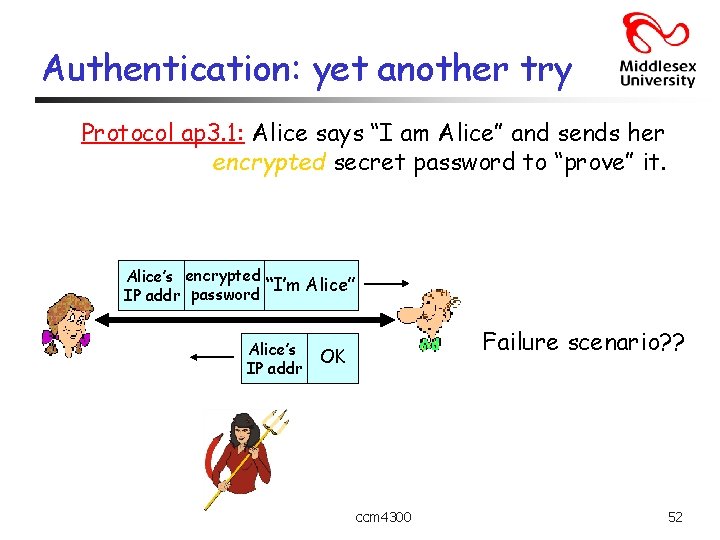
Authentication: yet another try Protocol ap 3. 1: Alice says “I am Alice” and sends her encrypted secret password to “prove” it. Alice’s encrypted “I’m Alice” IP addr password Alice’s IP addr Failure scenario? ? OK ccm 4300 52

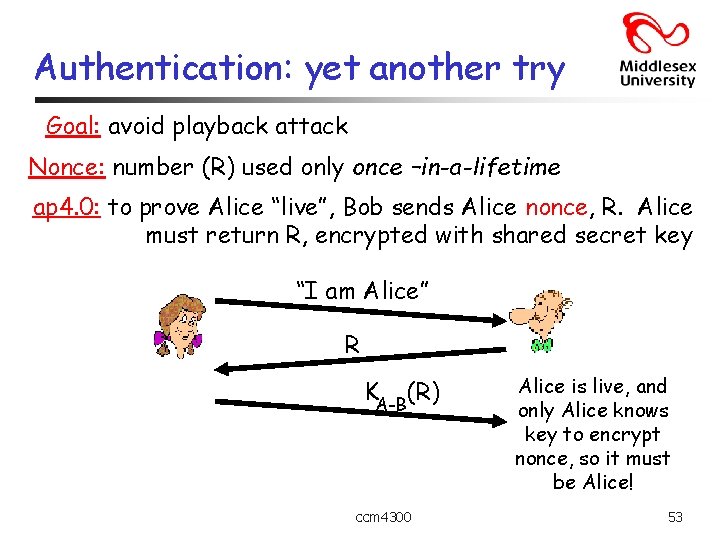
Authentication: yet another try Goal: avoid playback attack Nonce: number (R) used only once –in-a-lifetime ap 4. 0: to prove Alice “live”, Bob sends Alice nonce, R. Alice must return R, encrypted with shared secret key “I am Alice” R KA-B(R) ccm 4300 Alice is live, and only Alice knows key to encrypt nonce, so it must be Alice! 53

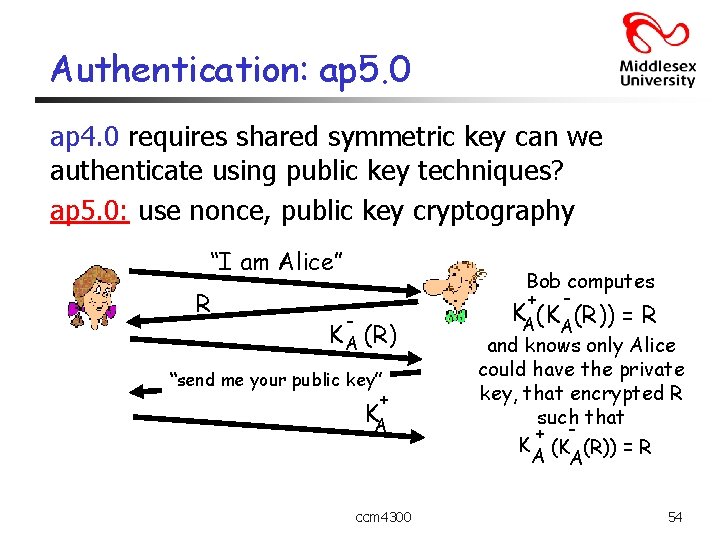
Authentication: ap 5. 0 ap 4. 0 requires shared symmetric key can we authenticate using public key techniques? ap 5. 0: use nonce, public key cryptography “I am Alice” R Bob computes + - - K A (R) “send me your public key” + KA ccm 4300 KA(KA (R)) = R and knows only Alice could have the private key, that encrypted R such that + K (K (R)) = R A A 54

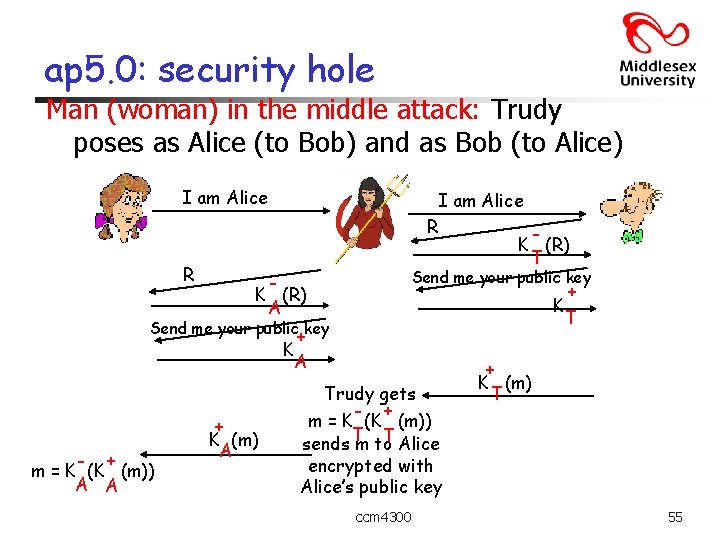
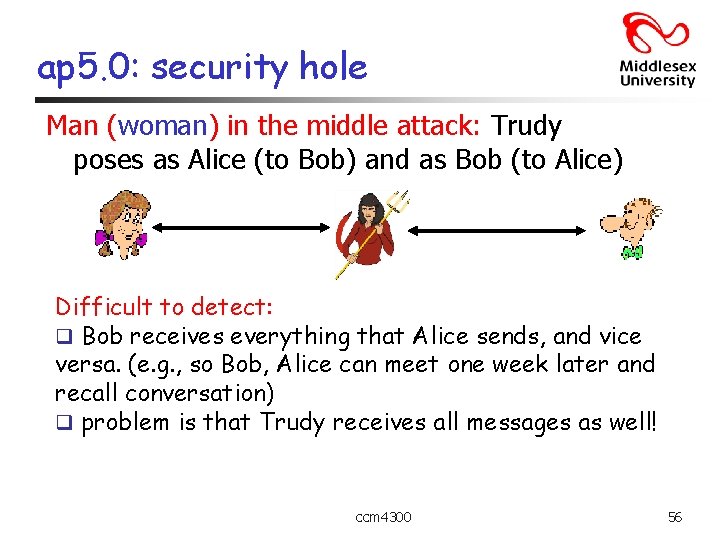
ap 5. 0: security hole Man (woman) in the middle attack: Trudy poses as Alice (to Bob) and as Bob (to Alice) I am Alice R K (R) T Send me your public key K (R) A + K T Send me your public key + K A - + m = K (K (m)) A A + K (m) A Trudy gets - + m = K (K (m)) T Alice sends T m to + K (m) T encrypted with Alice’s public key ccm 4300 55

ap 5. 0: security hole Man (woman) in the middle attack: Trudy poses as Alice (to Bob) and as Bob (to Alice) Difficult to detect: q Bob receives everything that Alice sends, and vice versa. (e. g. , so Bob, Alice can meet one week later and recall conversation) q problem is that Trudy receives all messages as well! ccm 4300 56

Where are we? What is network security? n. Principles of cryptography n. Authentication n. Message integrity n. Key Distribution and certification n. Access control: firewalls n. Attacks and counter measures n. Security in many layers n ccm 4300 57

Digital Signatures Cryptographic technique analogous to hand-written signatures. n n sender (Bob) digitally signs document, establishing he is document owner/creator. verifiable, nonforgeable: recipient (Alice) can prove to someone that Bob, and no one else (including Alice), must have signed document ccm 4300 58

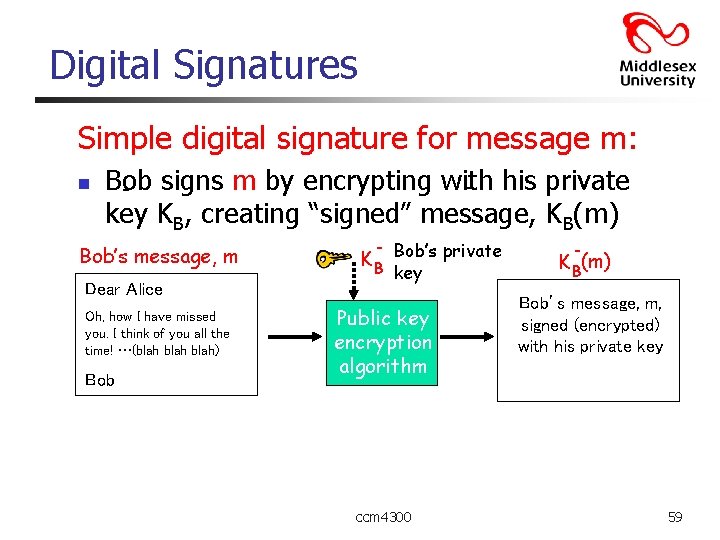
Digital Signatures Simple digital signature for message m: n Bob signs m by encrypting with - his private key KB, creating “signed” message, KB(m) Bob’s message, m Dear Alice Oh, how I have missed you. I think of you all the time! …(blah) Bob K B Bob’s private key Public key encryption algorithm ccm 4300 K B(m) Bob’s message, m, signed (encrypted) with his private key 59

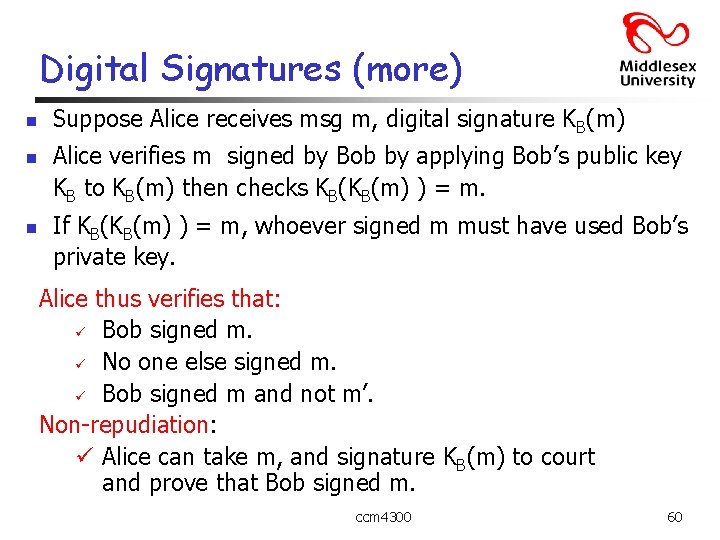
Digital Signatures (more) n n n Suppose Alice receives msg m, digital signature KB(m) Alice verifies m signed by Bob by applying Bob’s public key KB to KB(m) then checks KB(KB(m) ) = m. If KB(KB(m) ) = m, whoever signed m must have used Bob’s private key. Alice thus verifies that: ü Bob signed m. ü No one else signed m. ü Bob signed m and not m’. Non-repudiation: ü Alice can take m, and signature KB(m) to court and prove that Bob signed m. ccm 4300 60

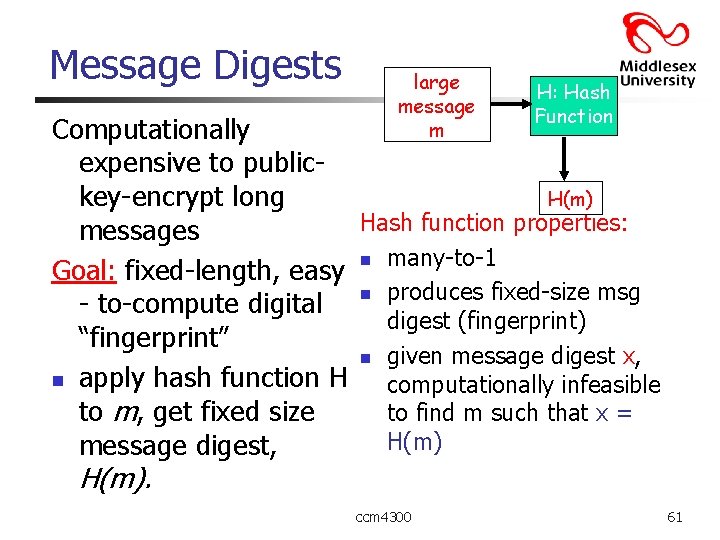
Message Digests large message m H: Hash Function Computationally expensive to publickey-encrypt long H(m) Hash function properties: messages n many-to-1 Goal: fixed-length, easy - to-compute digital n produces fixed-size msg digest (fingerprint) “fingerprint” n given message digest x, n apply hash function H computationally infeasible to m, get fixed size to find m such that x = H(m) message digest, H(m). ccm 4300 61

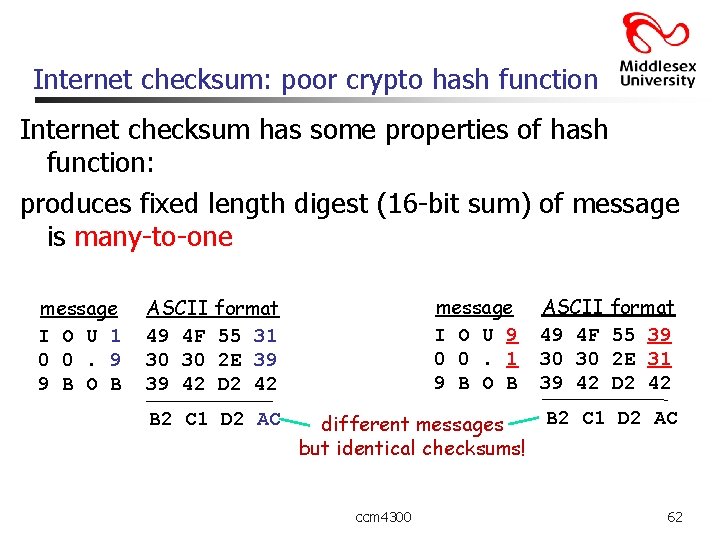
Internet checksum: poor crypto hash function Internet checksum has some properties of hash function: produces fixed length digest (16 -bit sum) of message is many-to-one message I O U 1 0 0. 9 9 B O B message I O U 9 0 0. 1 9 B O B ASCII format 49 4 F 55 31 30 30 2 E 39 39 42 D 2 42 B 2 C 1 D 2 AC different messages but identical checksums! ccm 4300 ASCII format 49 4 F 55 39 30 30 2 E 31 39 42 D 2 42 B 2 C 1 D 2 AC 62

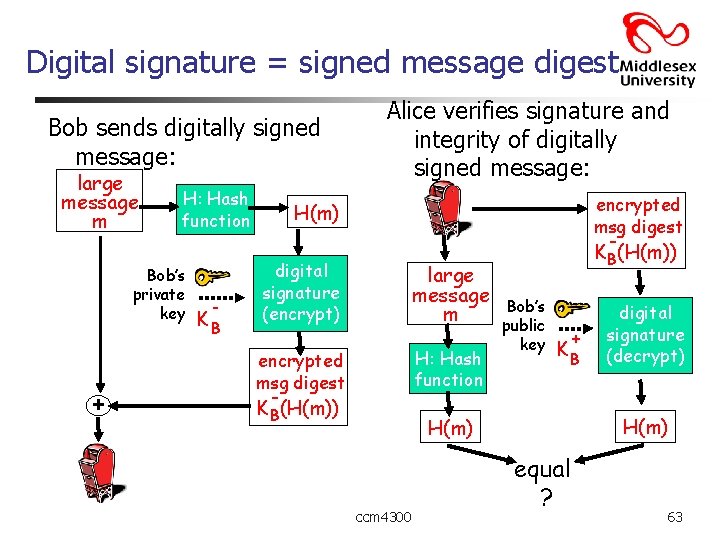
Digital signature = signed message digest Bob sends digitally signed message: large message m H: Hash function Bob’s private key + KB Alice verifies signature and integrity of digitally signed message: encrypted msg digest H(m) digital signature (encrypt) large message m H: Hash function encrypted msg digest KB(H(m)) Bob’s public key + KB H(m) ccm 4300 digital signature (decrypt) equal ? 63

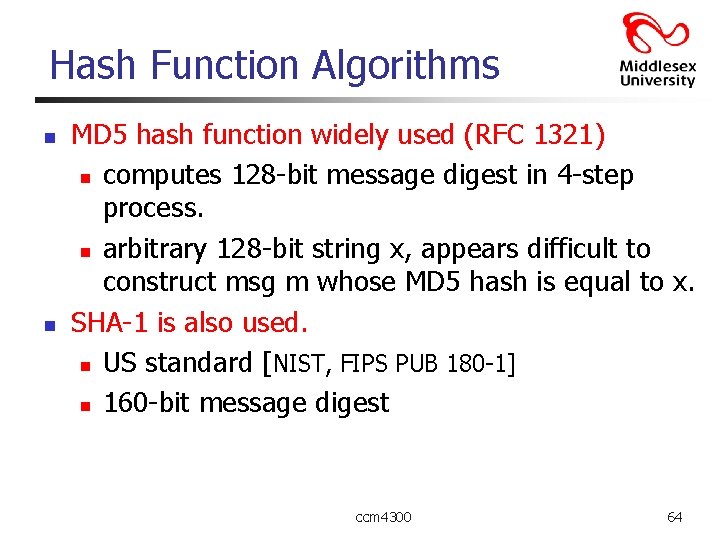
Hash Function Algorithms n n MD 5 hash function widely used (RFC 1321) n computes 128 -bit message digest in 4 -step process. n arbitrary 128 -bit string x, appears difficult to construct msg m whose MD 5 hash is equal to x. SHA-1 is also used. n US standard [NIST, FIPS PUB 180 -1] n 160 -bit message digest ccm 4300 64

Where are we? n n n n What is network security? Principles of cryptography Authentication Integrity Key distribution and certification Access control: firewalls Attacks and counter measures Security in many layers ccm 4300 65

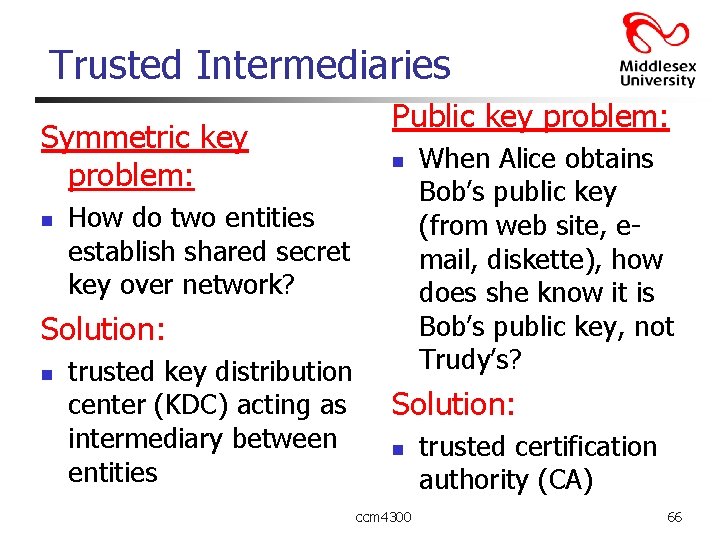
Trusted Intermediaries Symmetric key problem: n Public key problem: n How do two entities establish shared secret key over network? Solution: n trusted key distribution center (KDC) acting as intermediary between entities When Alice obtains Bob’s public key (from web site, email, diskette), how does she know it is Bob’s public key, not Trudy’s? Solution: n ccm 4300 trusted certification authority (CA) 66

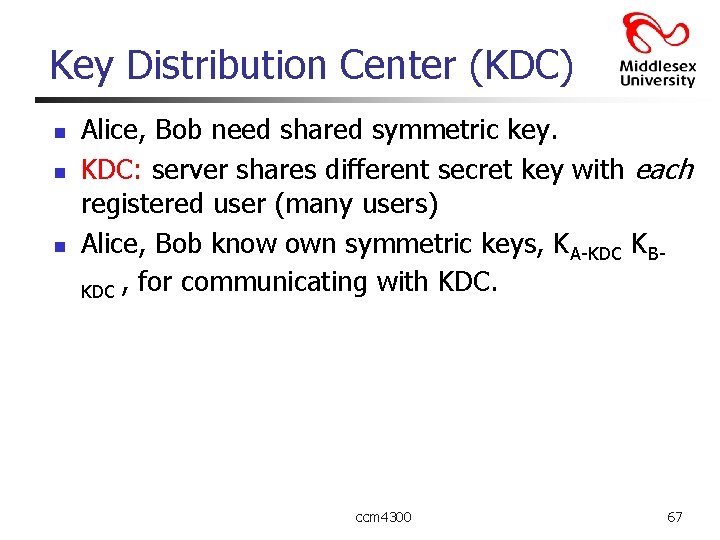
Key Distribution Center (KDC) n n n Alice, Bob need shared symmetric key. KDC: server shares different secret key with each registered user (many users) Alice, Bob know own symmetric keys, KA-KDC KBKDC , for communicating with KDC. ccm 4300 67

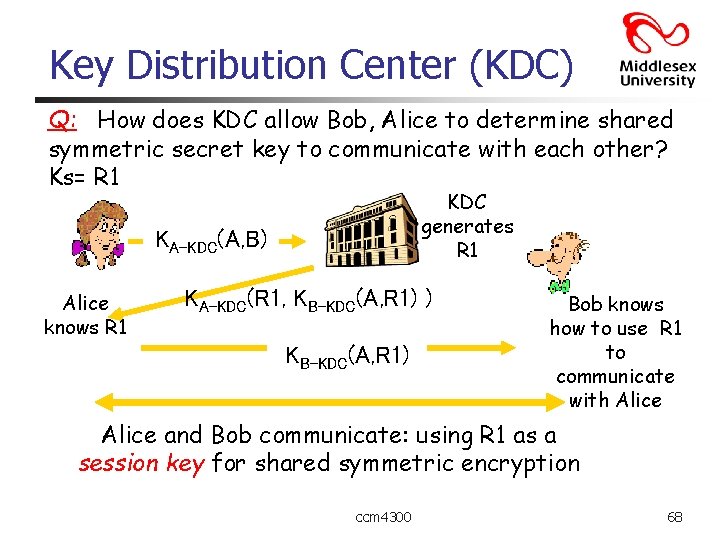
Key Distribution Center (KDC) Q: How does KDC allow Bob, Alice to determine shared symmetric secret key to communicate with each other? Ks= R 1 KDC generates R 1 KA-KDC(A, B) Alice knows R 1 KA-KDC(R 1, KB-KDC(A, R 1) ) KB-KDC(A, R 1) Bob knows how to use R 1 to communicate with Alice and Bob communicate: using R 1 as a session key for shared symmetric encryption ccm 4300 68

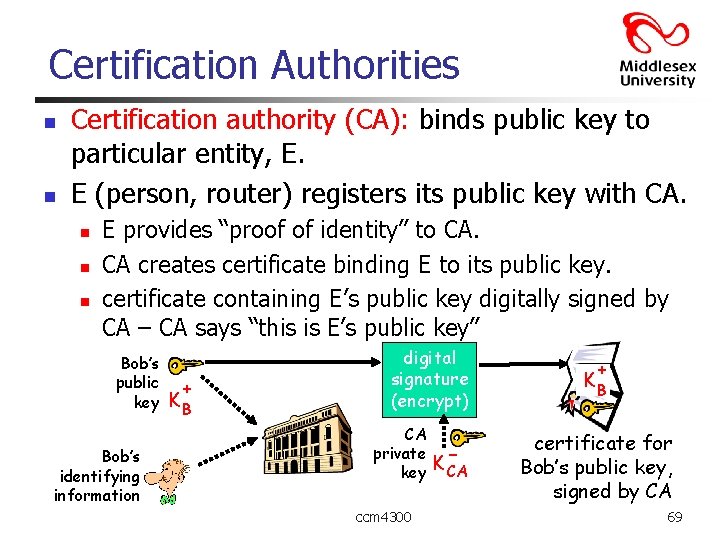
Certification Authorities n n Certification authority (CA): binds public key to particular entity, E. E (person, router) registers its public key with CA. n n n E provides “proof of identity” to CA. CA creates certificate binding E to its public key. certificate containing E’s public key digitally signed by CA – CA says “this is E’s public key” Bob’s public key Bob’s identifying information + KB digital signature (encrypt) CA private key ccm 4300 K- CA + KB certificate for Bob’s public key, signed by CA 69

Certification Authorities n When Alice wants Bob’s public key: n gets Bob’s certificate (Bob or elsewhere). n apply CA’s public key to Bob’s certificate, get Bob’s public key + KB digital signature (decrypt) CA public key Bob’s public + key KB + K CA ccm 4300 70

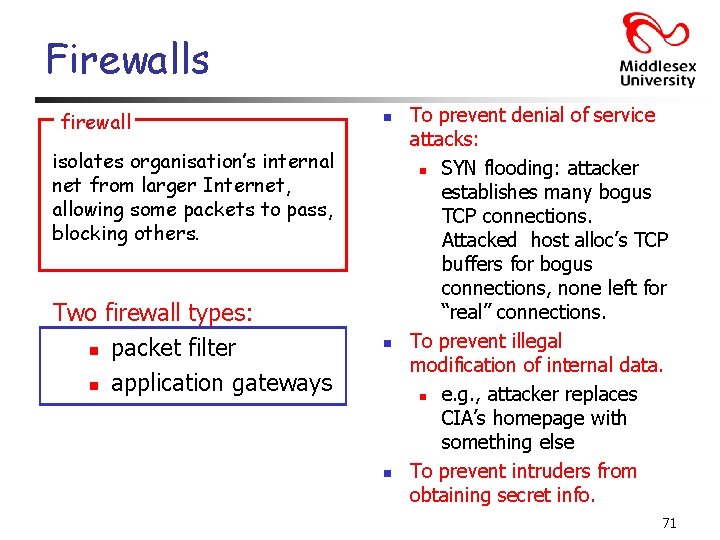
Firewalls firewall n isolates organisation’s internal net from larger Internet, allowing some packets to pass, blocking others. Two firewall types: n packet filter n application gateways n n To prevent denial of service attacks: n SYN flooding: attacker establishes many bogus TCP connections. Attacked host alloc’s TCP buffers for bogus connections, none left for “real” connections. To prevent illegal modification of internal data. n e. g. , attacker replaces CIA’s homepage with something else To prevent intruders from obtaining secret info. 71

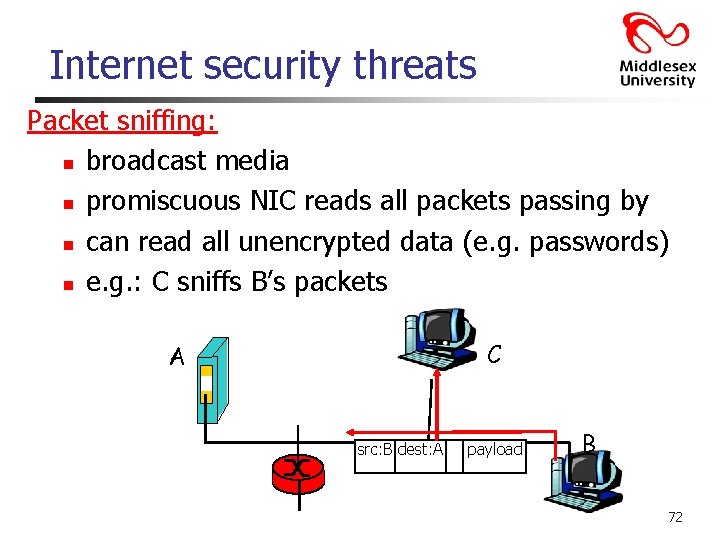
Internet security threats Packet sniffing: n broadcast media n promiscuous NIC reads all packets passing by n can read all unencrypted data (e. g. passwords) n e. g. : C sniffs B’s packets C A src: B dest: A payload B 72

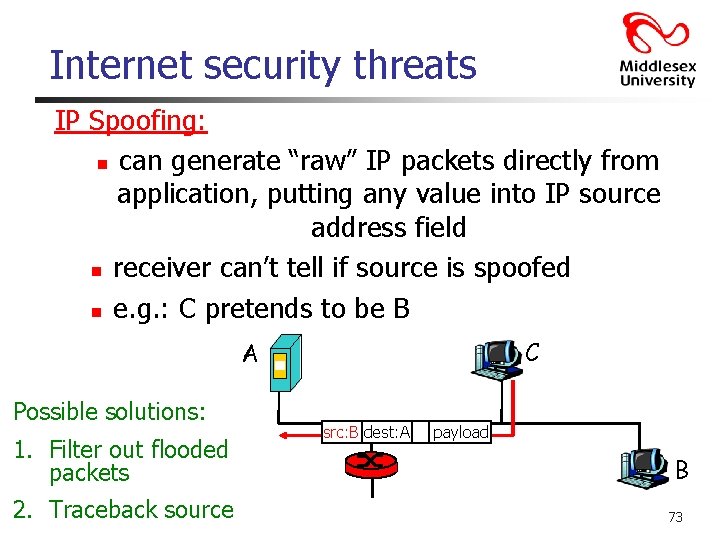
Internet security threats IP Spoofing: n can generate “raw” IP packets directly from application, putting any value into IP source address field n receiver can’t tell if source is spoofed n e. g. : C pretends to be B C A Possible solutions: 1. Filter out flooded packets 2. Traceback source src: B dest: A payload B 73

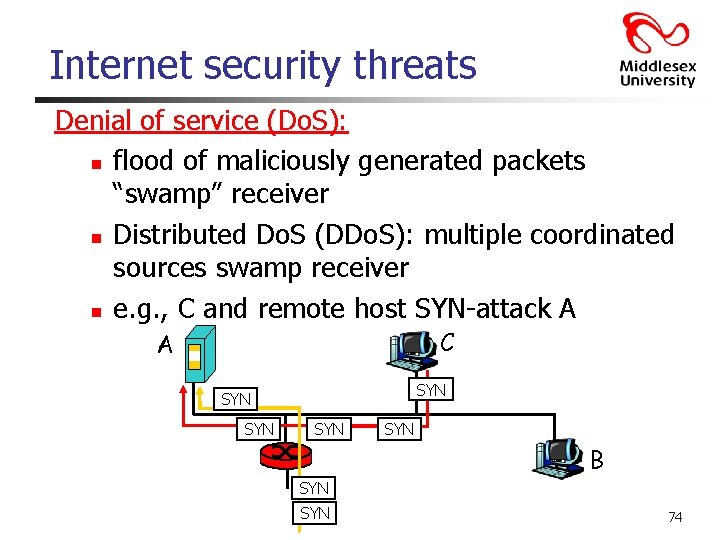
Internet security threats Denial of service (Do. S): n flood of maliciously generated packets “swamp” receiver n Distributed Do. S (DDo. S): multiple coordinated sources swamp receiver n e. g. , C and remote host SYN-attack A C A SYN SYN SYN B SYN 74

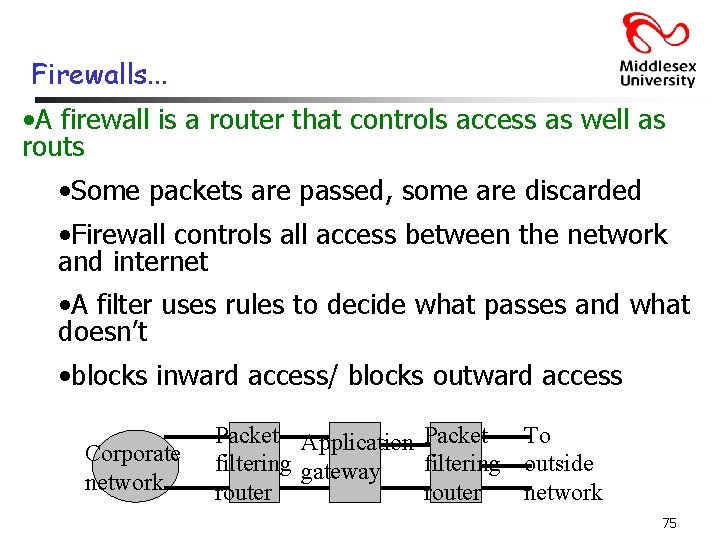
Firewalls. . . • A firewall is a router that controls access as well as routs • Some packets are passed, some are discarded • Firewall controls all access between the network and internet • A filter uses rules to decide what passes and what doesn’t • blocks inward access/ blocks outward access Corporate network Packet Application Packet To filtering gateway filtering outside router network 75

Firewalls: continues…. . • Network level security • IP address filtering • not possible with, e. g. , ftp • Proxy applications • Have to be installed in order to enable the internal users to use services like telnet or ftp • Application level filters • watch for viruses or Java applets (slow!) • No end-to-end security 76

Packet Filtering: examples n n Internal network is connected to Internet through a router. Router manufacturer provides options for filtering packets, based on: n source IP address n destination IP address n TCP/UDP source and destination port numbers n ICMP message type n TCP SYN and ACK bits n n Example 1: block incoming and outgoing datagrams with IP protocol field = 17 and with either source or dest port = 23. n All incoming and outgoing UDP flows and telnet connections are blocked. Example 2: Block inbound TCP segments with ACK=0. n Prevents external clients from making TCP connections with internal clients, but allows internal clients to connect to outside. 77

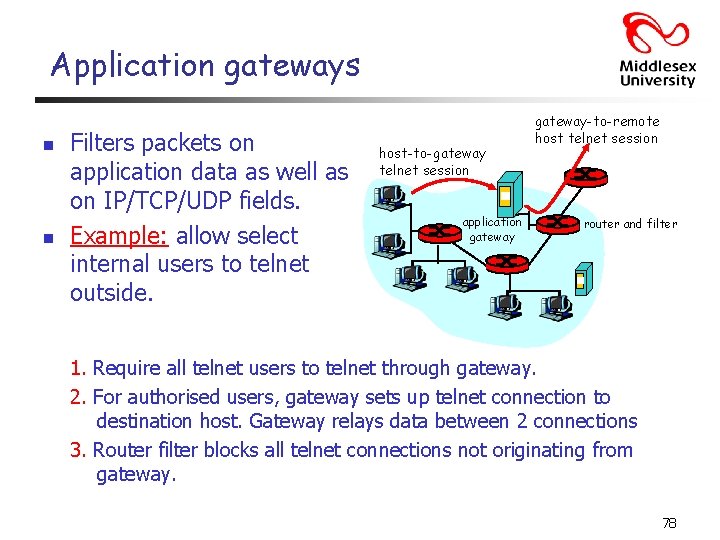
Application gateways n n Filters packets on application data as well as on IP/TCP/UDP fields. Example: allow select internal users to telnet outside. host-to-gateway telnet session application gateway-to-remote host telnet session router and filter 1. Require all telnet users to telnet through gateway. 2. For authorised users, gateway sets up telnet connection to destination host. Gateway relays data between 2 connections 3. Router filter blocks all telnet connections not originating from gateway. 78

Limitations of firewalls and gateways n n n IP spoofing: router can’t know if data “really” comes from the claimed source If multiple app’s. need special treatment, each has own app. gateway. Client software must know how to contact gateway. n e. g. , must set IP address of proxy in Web browser n n n Filters often use all or nothing policy for UDP. Tradeoff: degree of communication with outside world, level of security Many highly protected sites still suffer from attacks. 79

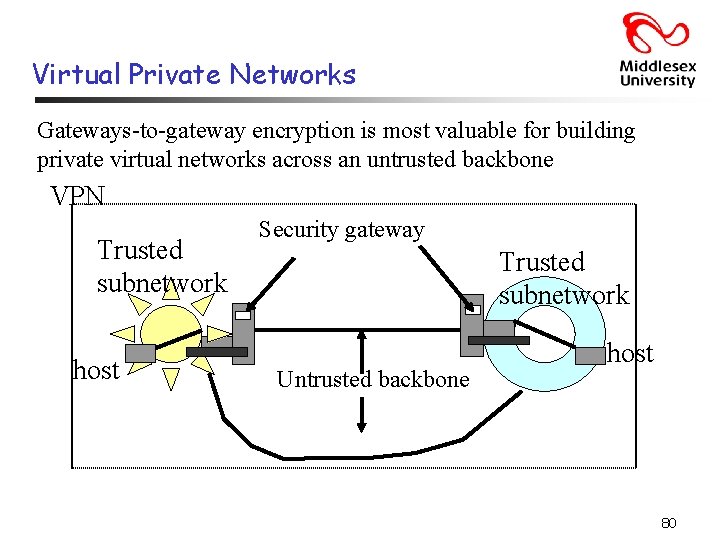
Virtual Private Networks Gateways-to-gateway encryption is most valuable for building private virtual networks across an untrusted backbone VPN Trusted subnetwork host Security gateway Trusted subnetwork Untrusted backbone host 80

Intrusion Detection System - IDS • What is IDS: An Intrusion Detection Systems are either software or hardware products • To detect attacks, preferably, in real-time • To monitor the events occurring in a computer system or network • To analyse the events for signs of intrusions, • To protect the confidentiality, integrity, availability of the system 81

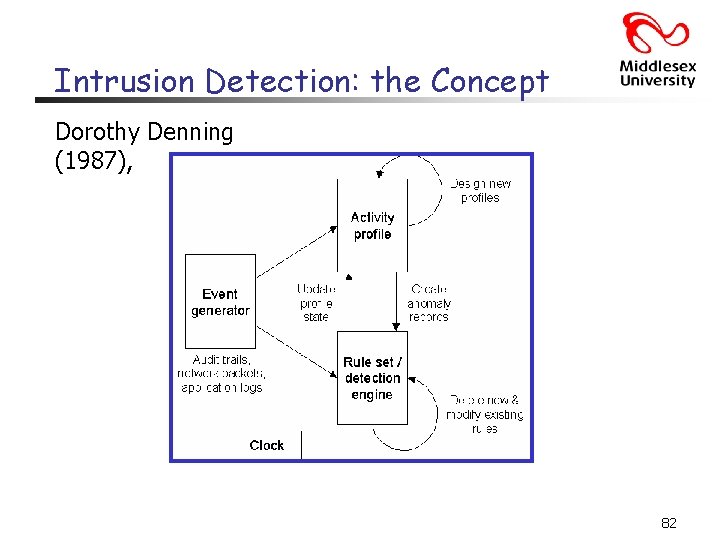
Intrusion Detection: the Concept Dorothy Denning (1987), 82

Detection Models There are two types of detection models: 1. Misuse detection: accurately and efficiently detect known attacks 2. Anomaly detection based on the assumption that misuse or intrusive behaviour deviates from historical norms. 83

Frequency of detection • Real time analysis: useful option from the perspective of detecting attacks as they occur. • But consume resources (high cost) • Interval based analysis: overcomes the problem of resources, but increases the RISK 84

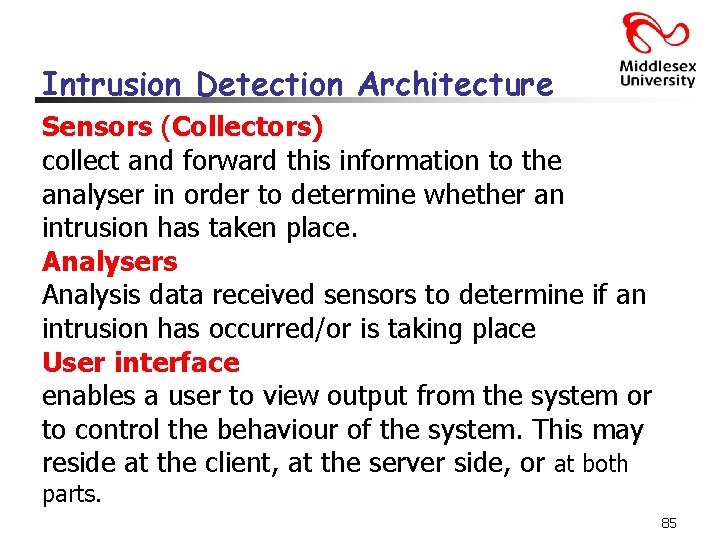
Intrusion Detection Architecture Sensors (Collectors) collect and forward this information to the analyser in order to determine whether an intrusion has taken place. Analysers Analysis data received sensors to determine if an intrusion has occurred/or is taking place User interface enables a user to view output from the system or to control the behaviour of the system. This may reside at the client, at the server side, or at both parts. 85

Pefrormability Evaluation Security Mechanisms • The proposed approach involves temporary interruption to link/server access. • Due to the Kerberos’ delay decryption properties and being a timed authentication protocol, it is proven that in terms of attack prevention this protocol is successful despite of strong intruder connection attempts. • This has implications in terms of performance degradation. • An analytical method is used to evaluate the cost in terms of the degradation of system performance. 86

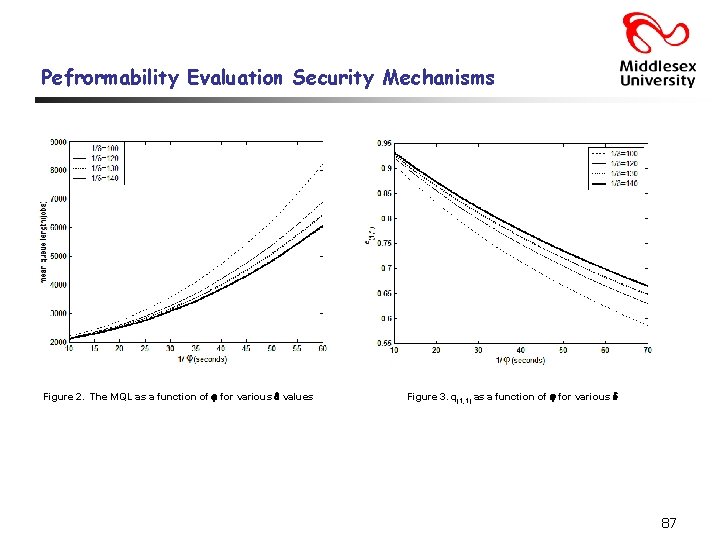
Pefrormability Evaluation Security Mechanisms Figure 2. The MQL as a function of for various values Figure 3. q(1, 1) as a function of for various 87

Summary • Firewalls protect systems from external attacks • To prevent denial of service attacks • To prevent illegal modification of internal data. • IDSs protect systems from internal attacks • IDSs can be viewed as a second line of defence • IDS offer the opportunity to detect and halt attacks in real time 88