i CORE Networking Research Carey Williamson i CORE









![Sequential Progress Example k E[j] = ------M - k + 1 21 Sequential Progress Example k E[j] = ------M - k + 1 21](https://slidetodoc.com/presentation_image/88947eb30b5cb25be1876541f4762137/image-21.jpg)



- Slides: 28

i. CORE Networking Research Carey Williamson i. CORE Chair Broadband Wireless Networks, Protocols, Applications, and Performance Department of Computer Science University of Calgary 1

Talk Outline n n n i. CORE Overview (15 min) Questions (5 min) Networks Research Group (30 min) n n n Network Traffic Measurement Cellular Data Network Provisioning Peer-to-Peer (P 2 P) Video Streaming New Initiatives (5 min) Questions (5 min) 2

Networks Research Group n Research area? n n Wireless networks, Internet protocols, computer systems performance evaluation Mission: “Make the Internet go faster” Approach? n Experimental, simulation, analytical Key challenges? n n Citius, Altius, Fortius! Performance, scalability, robustness 3

Research Personnel n n n Team Leader: Carey Williamson Faculty: Majid Ghaderi, Zongpeng Li, Mea Wang Research Staff: Martin Arlitt, Niklas Carlsson, Nisan Lev-Tov, Maxim Podlesny, Hanan Shpungin n Support Staff: Jennifer Harper, Terence Robinson Ph. D. Students: Marian Doerk, Ajay Gopinathan, n M. Sc. Students: n Emir Halepovic, Islam Hegazy, Andreas Hirt, Aniket Mahanti, Mohsen Molla, Nadim Parvez Ali Abedi, Ali Dabirmoghaddam, Mostafa Dehghan, Ibrahim Ismail, Shreya Maheshwar, Saikat Sarkar, Shambavi Srinivasa, M. Tauhiduzzaman, Tuan Vu, Song Zhang, Tongjie Zhang 4

Experimental Facilities n Experimental Laboratory for Internet Systems and Applications (Uof. C/Uof. S, CFI) n n Geographically distributed Internet testbed between Calgary and Saskatoon Clients, servers, notebooks, routers, switches, Web proxies, network analyzers, 802. 11 a/b Fully operational since Spring 2004 Wireless Internet Performance Lab (Uof. C) n n n IEEE 802. 11 b wireless LAN Sniffer. Pro, Airopeek wireless network analyzers PCs, laptops, PDAs, wireless NICs, Web proxy 5

Research Highlights n Network Traffic Measurements n Wireless/Cellular Networks n Peer-to-Peer (P 2 P) Streaming 6

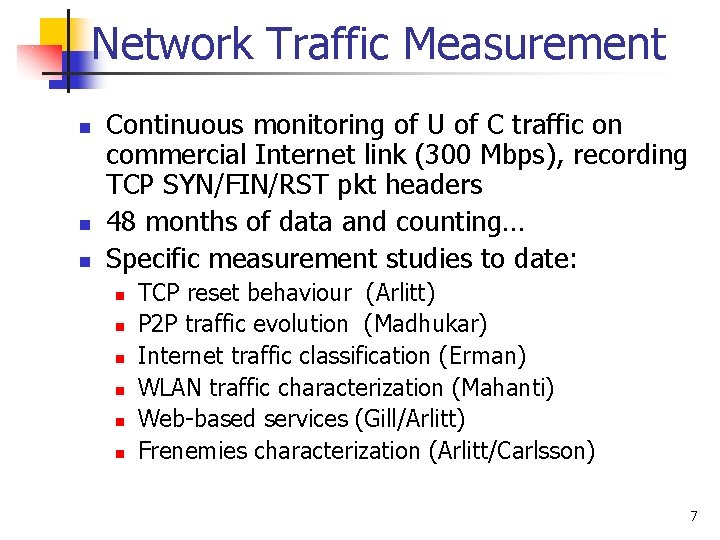
Network Traffic Measurement n n n Continuous monitoring of U of C traffic on commercial Internet link (300 Mbps), recording TCP SYN/FIN/RST pkt headers 48 months of data and counting… Specific measurement studies to date: n n n TCP reset behaviour (Arlitt) P 2 P traffic evolution (Madhukar) Internet traffic classification (Erman) WLAN traffic characterization (Mahanti) Web-based services (Gill/Arlitt) Frenemies characterization (Arlitt/Carlsson) 7

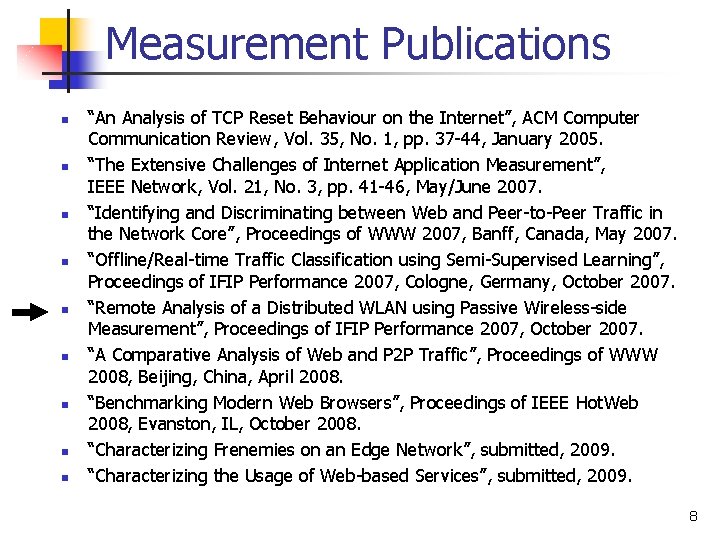
Measurement Publications n n n n n “An Analysis of TCP Reset Behaviour on the Internet”, ACM Computer Communication Review, Vol. 35, No. 1, pp. 37 -44, January 2005. “The Extensive Challenges of Internet Application Measurement”, IEEE Network, Vol. 21, No. 3, pp. 41 -46, May/June 2007. “Identifying and Discriminating between Web and Peer-to-Peer Traffic in the Network Core”, Proceedings of WWW 2007, Banff, Canada, May 2007. “Offline/Real-time Traffic Classification using Semi-Supervised Learning”, Proceedings of IFIP Performance 2007, Cologne, Germany, October 2007. “Remote Analysis of a Distributed WLAN using Passive Wireless-side Measurement”, Proceedings of IFIP Performance 2007, October 2007. “A Comparative Analysis of Web and P 2 P Traffic”, Proceedings of WWW 2008, Beijing, China, April 2008. “Benchmarking Modern Web Browsers”, Proceedings of IEEE Hot. Web 2008, Evanston, IL, October 2008. “Characterizing Frenemies on an Edge Network”, submitted, 2009. “Characterizing the Usage of Web-based Services”, submitted, 2009. 8

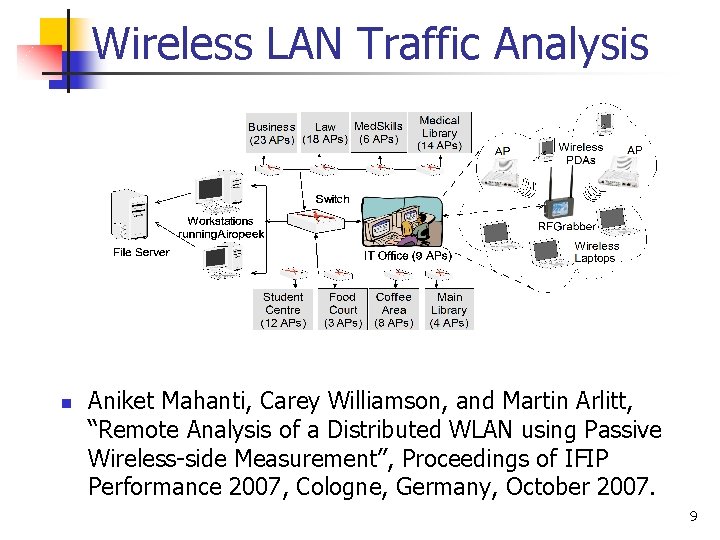
Wireless LAN Traffic Analysis n Aniket Mahanti, Carey Williamson, and Martin Arlitt, “Remote Analysis of a Distributed WLAN using Passive Wireless-side Measurement”, Proceedings of IFIP Performance 2007, Cologne, Germany, October 2007. 9

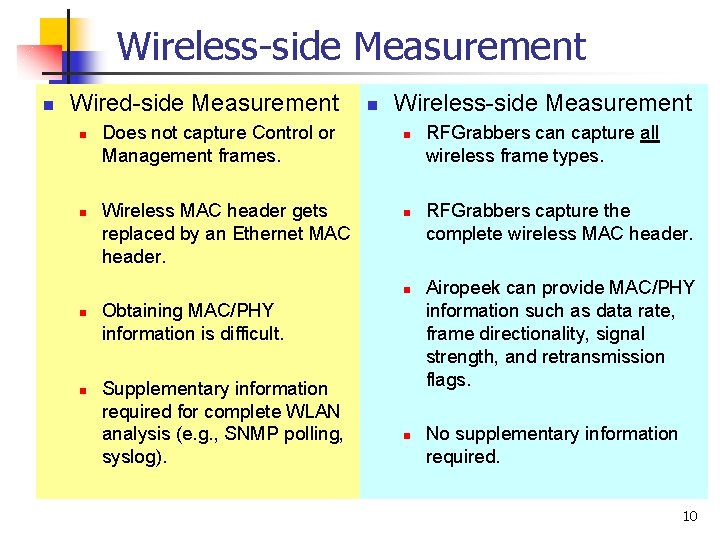
Wireless-side Measurement n Wired-side Measurement n n Does not capture Control or Management frames. Wireless MAC header gets replaced by an Ethernet MAC header. n Wireless-side Measurement n n n Obtaining MAC/PHY information is difficult. Supplementary information required for complete WLAN analysis (e. g. , SNMP polling, syslog). n RFGrabbers can capture all wireless frame types. RFGrabbers capture the complete wireless MAC header. Airopeek can provide MAC/PHY information such as data rate, frame directionality, signal strength, and retransmission flags. No supplementary information required. 10

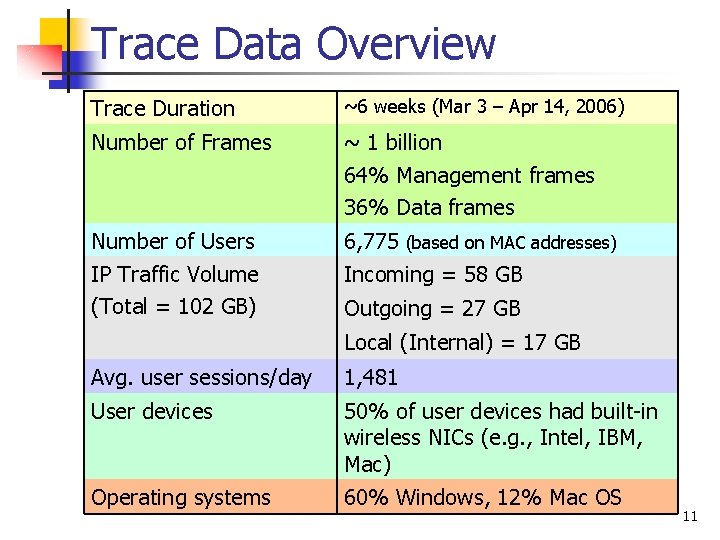
Trace Data Overview Trace Duration ~6 weeks (Mar 3 – Apr 14, 2006) Number of Frames ~ 1 billion 64% Management frames 36% Data frames Number of Users 6, 775 (based on MAC addresses) IP Traffic Volume (Total = 102 GB) Incoming = 58 GB Outgoing = 27 GB Local (Internal) = 17 GB Avg. user sessions/day 1, 481 User devices 50% of user devices had built-in wireless NICs (e. g. , Intel, IBM, Mac) Operating systems 60% Windows, 12% Mac OS 11

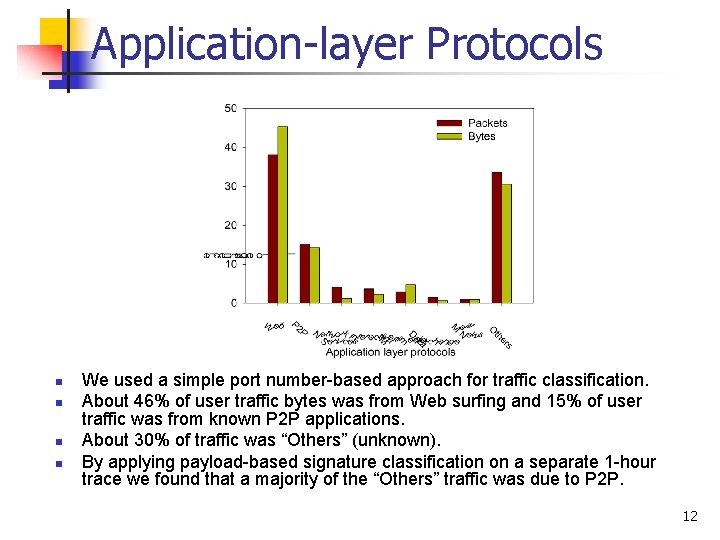
Application-layer Protocols n n We used a simple port number-based approach for traffic classification. About 46% of user traffic bytes was from Web surfing and 15% of user traffic was from known P 2 P applications. About 30% of traffic was “Others” (unknown). By applying payload-based signature classification on a separate 1 -hour trace we found that a majority of the “Others” traffic was due to P 2 P. 12

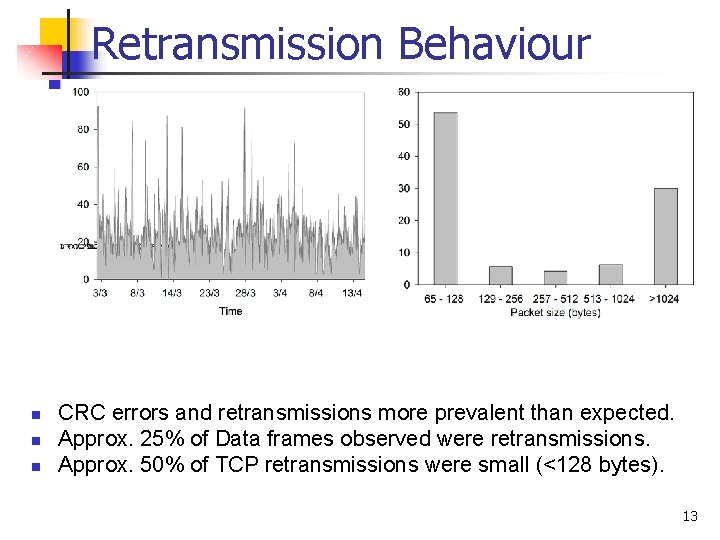
Retransmission Behaviour n n n CRC errors and retransmissions more prevalent than expected. Approx. 25% of Data frames observed were retransmissions. Approx. 50% of TCP retransmissions were small (<128 bytes). 13

Key Results and Observations n n n Our study demonstrated the feasibility and effectiveness of remote non-intrusive wireless-side measurement in a geographically-distributed campus WLAN environment. Analysis of our traces identified several trends consistent with prior campus WLAN measurement studies, including diurnal usage patterns, diverse network application usage, and limited user mobility, while offering new observations on session activity, mobility patterns, and wireless channel usage in our campus WLAN. Our analysis identified several emerging trends in application usage, user mobility behaviour, and WLAN deployment, as well as some performance-related issues at the wireless layer. 14

Wireless/Cellular Publications n n n n “On Processor Sharing and Its Application to Cellular Data Network Provisioning”, Proceedings of IFIP Performance 2007, October 2007. “TCP Fairness Issues in IEEE 802. 11 Wireless LANs”, Elsevier Computer Communications, Vol. 31, No. 10, pp. 2150 -2161, June 2008. “TCP over Wi. MAX: A Measurement Study”, Proceedings of IEEE/ACM MASCOTS 2008, Baltimore, MD, September 2008. “Multimedia Application Performance on a Wi. MAX Network”, Proceedings of MMCN 2009, San Jose, CA, January 2009. “Wireless Data Traffic: A Decade of Change”, IEEE Network, Vol. 23, No. 2, pp. 20 -26, March 2009. “Scheduling Issues in Multi-Channel Wireless Networks”, Proceedings of IEEE/ACM MASCOTS 2009, London, UK, September 2009. “Service Differentiation in Multi-Rate HSDPA Systems”, Proceedings of IEEE/ACM MASCOTS 2009, London, UK, September 2009. “Media Caching Support for Mobile Transit Users”, Proceedings of IEEE Wi. Mob 2009, Marrakech, Morocco, October 2009. 15

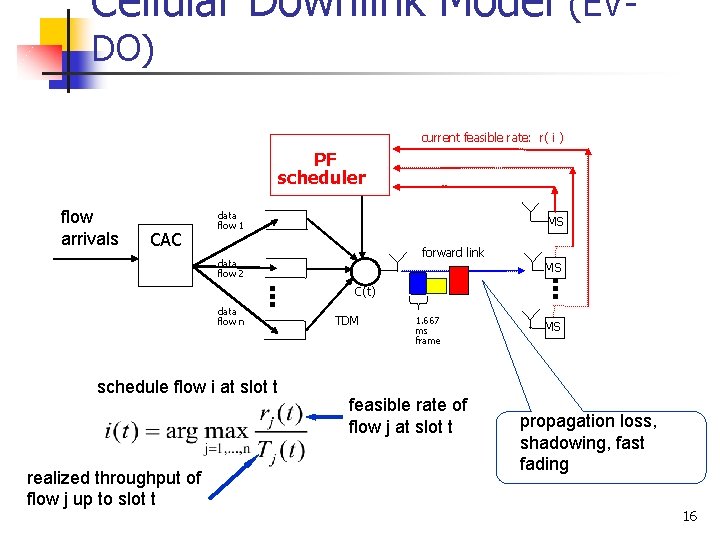
Cellular Downlink Model (EVDO) current feasible rate: r( i ) PF scheduler CAC data flow 1 MS forward link data flow 2 . . . data flow n MS schedule flow i at slot t realized throughput of flow j up to slot t . . . flow arrivals C(t) TDM 1. 667 ms frame feasible rate of flow j at slot t MS propagation loss, shadowing, fast fading 16

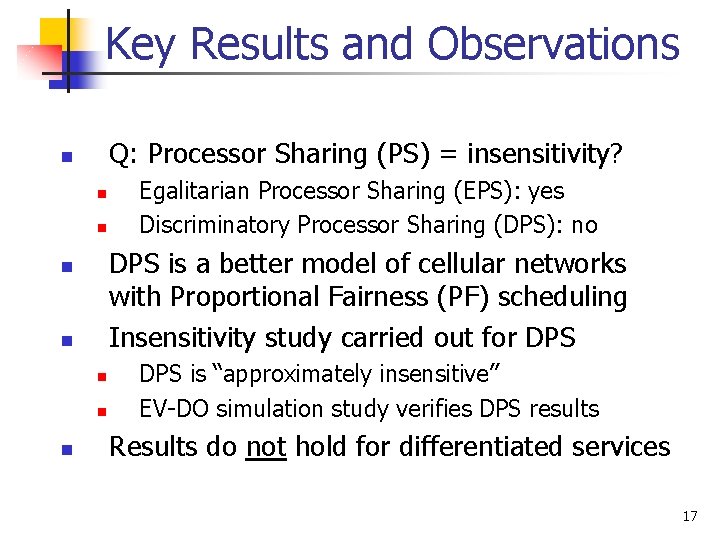
Key Results and Observations Q: Processor Sharing (PS) = insensitivity? n n n DPS is a better model of cellular networks with Proportional Fairness (PF) scheduling Insensitivity study carried out for DPS n n n Egalitarian Processor Sharing (EPS): yes Discriminatory Processor Sharing (DPS): no DPS is “approximately insensitive” EV-DO simulation study verifies DPS results Results do not hold for differentiated services 17

Modeling/Analysis Publications n n n n “Analysis of Bit. Torrent-like Protocols for On-Demand Stored Media Streaming”, Proceedings of ACM SIGMETRICS 2008, June 2008. “Performance Implications of Fluctuating Server Capacity”, Computer Communications, Vol. 31, No. 16, pp. 3760 -3770, October 2008. “Enforcing Minimum-Cost Multicast Routing Against Selfish Information Flows”, IEEE Transactions on Parallel and Distributed Systems, Vol. 20, No. 9, pp. 1299 -1308, September 2009. “Optimal Multicast in Multi-Radio Multi-Channel Wireless Networks”, Proceedings of IEEE/ACM MASCOTS 2009, London, UK, September 2009. “Simulation Modeling of Secure Wireless Sensor Networks”, Proceedings of Value. Tools 2009, Pisa, Italy, October 2009. “An Analytic Throughput Model for TCP New. Reno”, to appear, IEEE/ACM Transactions on Networking, 2010. “Performance Modeling of Anonymity Protocols”, submitted, 2009. 18

Research Questions n n n Can Bit. Torrent-like protocols provide scalable on-demand streaming? How sensitive is the performance to the application configuration parameters? n Piece selection policy n Upload/download bandwidth What is the user-perceived performance? n Startup delay n Probability of disrupted playback Nadim Parvez, Carey Williamson, Anirban Mahanti, and Niklas Carlsson, “Analysis of Bit. Torrent-like Protocols for On-Demand Stored Media Streaming”, Proceedings of ACM SIGMETRICS 2008, Annapolis, MD, June 2008. 19

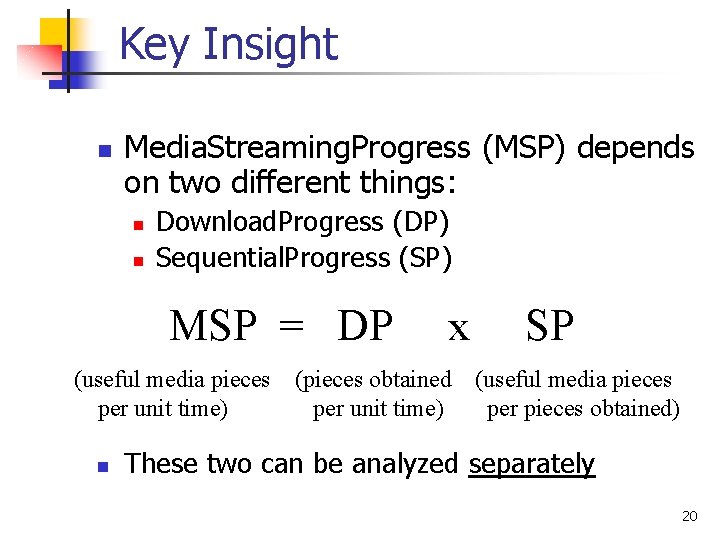
Key Insight n Media. Streaming. Progress (MSP) depends on two different things: n n Download. Progress (DP) Sequential. Progress (SP) MSP = DP (useful media pieces per unit time) n x SP (pieces obtained (useful media pieces per unit time) per pieces obtained) These two can be analyzed separately 20
![Sequential Progress Example k Ej M k 1 21 Sequential Progress Example k E[j] = ------M - k + 1 21](https://slidetodoc.com/presentation_image/88947eb30b5cb25be1876541f4762137/image-21.jpg)
Sequential Progress Example k E[j] = ------M - k + 1 21

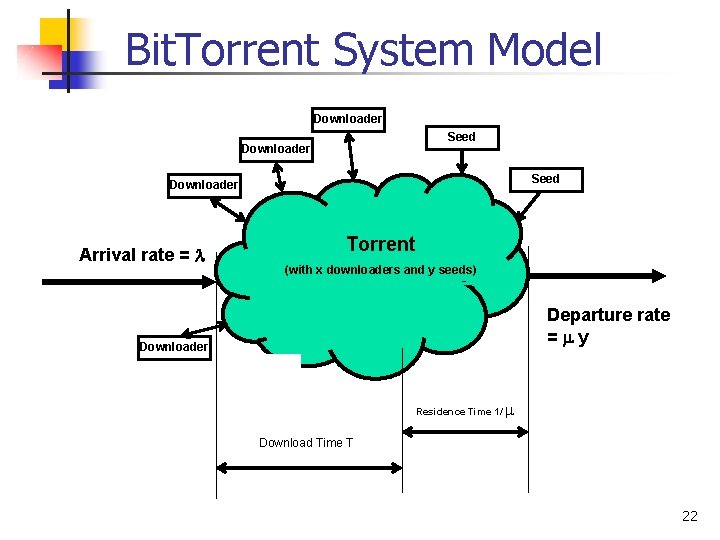
Bit. Torrent System Model Downloader Seed Downloader Arrival rate = Torrent (with x downloaders and y seeds) Departure rate = y Downloader Residence Time 1/ Download Time T 22

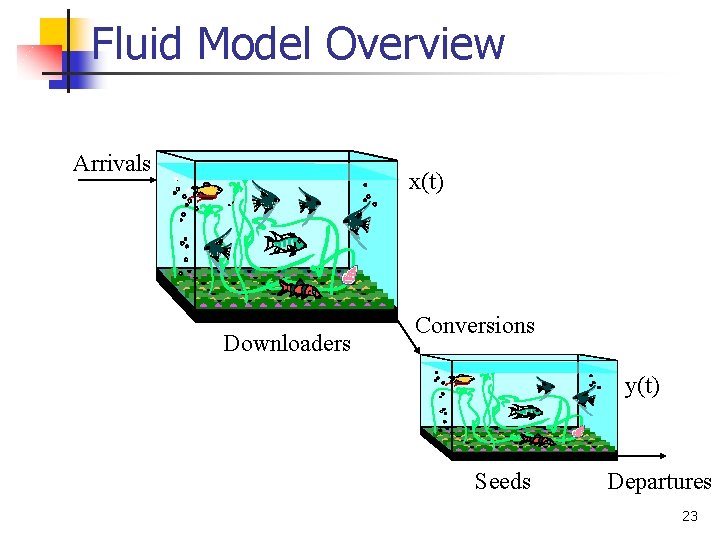
Fluid Model Overview Arrivals x(t) Downloaders Conversions y(t) Seeds Departures 23

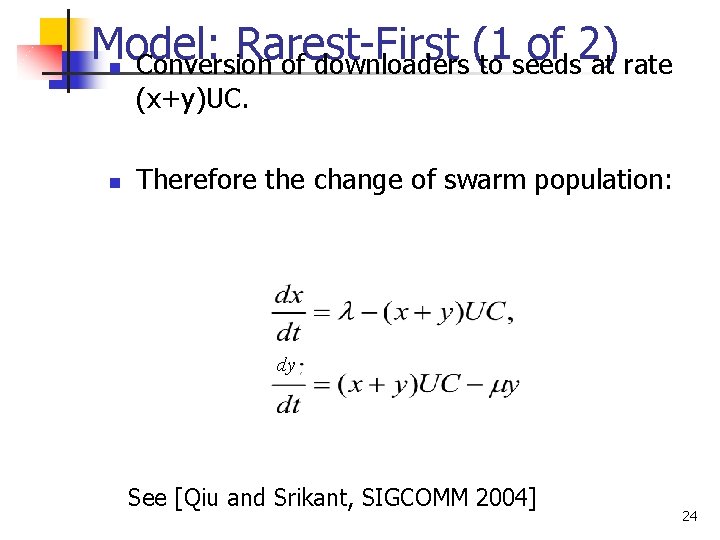
Model: Rarest-First (1 of 2) Conversion of downloaders to seeds at rate n (x+y)UC. n Therefore the change of swarm population: dy See [Qiu and Srikant, SIGCOMM 2004] 24

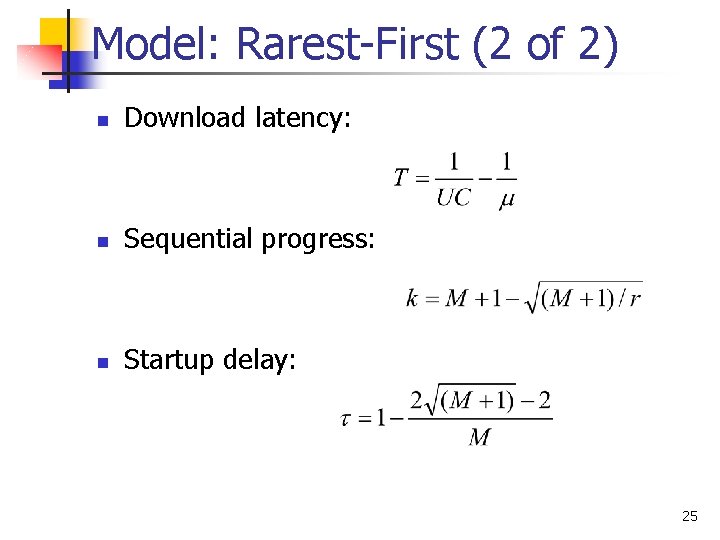
Model: Rarest-First (2 of 2) n Download latency: n Sequential progress: n Startup delay: 25

Key Results and Observations n n n Bit. Torrent-like protocols can support scalable and efficient on-demand streaming Rarest-First has poor sequential progress In-Order (naïve) provides very sluggish system performance In-Order (clever) achieves best performance for media playback while attaining the same download latency of Rarest-First Analytical models validated via simulation 26

New Initiatives n Internetworked Systems Security Network n n “Protecting Canada’s Internet” (www. issnet. ca) NSERC Strategic Network (2008 -2013) Collaborative initiative, led by Paul van Oorschot at Carleton University (+12 others) Pervasive Infrastructure, Services, and Applications (PISA) n n Proposed NSERC NCE, led by Alberto Leon-Garcia at the University of Toronto (+36 others) ICT-enabled “Smart Infrastructure” for cloud computing, power grid, transportation, and more 27

i. CORE Networking Research Carey Williamson i. CORE Chair Broadband Wireless Networks, Protocols, Applications, and Performance Department of Computer Science University of Calgary Email: carey@cpsc. ucalgary. ca http: //www. cpsc. ucalgary. ca/~carey 28