Wireless Update Chris Gohlke CPA I Joko Dewanto









































































- Slides: 107

Wireless Update Chris Gohlke, CPA & I. Joko Dewanto Lead Senior Auditor Florida Auditor General IT Audits Division chrisgohlke@aud. state. fl. us

Outline ¡ Main Topics l l l ¡ Wi-Fi (802. 11) Bluetooth RFID Bonus Topics (If Time Permits) l l Media Cleansing Auditor Security Collection The purpose of this class is to serve as a high-level overview. I’ve included a lot of extra information in these slides that won’t be covered in class. If you want even more information on these topics, check out the presentations at http: //www. nasact. org/onlineresources/downloads/2005_IT_Conf erence_Workshop/2005_IT. htm

What is Wi-Fi? Per Wikipedia – • Wi-Fi (sometimes written Wi-fi, Wi. Fi, Wifi, wifi) is a trademark for sets of product compatibility standards for wireless local area networks (WLANs). Wi-Fi, short for "Wireless Fidelity", was intended to allow mobile devices, such as laptop computers and personal digital assistants (PDAs) to connect to local area networks, but is now often used for Internet access and wireless Vo. IP phones. Desktop computers can use Wi-Fi too, allowing offices and homes to be networked without expensive wiring. Many computers are sold today with Wi-Fi built-in, others require adding a Wi-Fi network card. Other devices, such as digital cameras, are sometimes equipped with Wi-Fi. • Short Version – Wi-Fi gets rid of the Network Cable

What Pushes our Entities to Deploy? • Governments are deploying wireless LANs for cost and operational benefits such as allowing for a more mobile workforce. • Educational entities are deploying wireless LANs for cost, operational, and marketing benefits. Short Version – It is CHEAP, EASY, and …

EVERYWHERE - The explosion of devices which is creating a demand expectation of wireless.

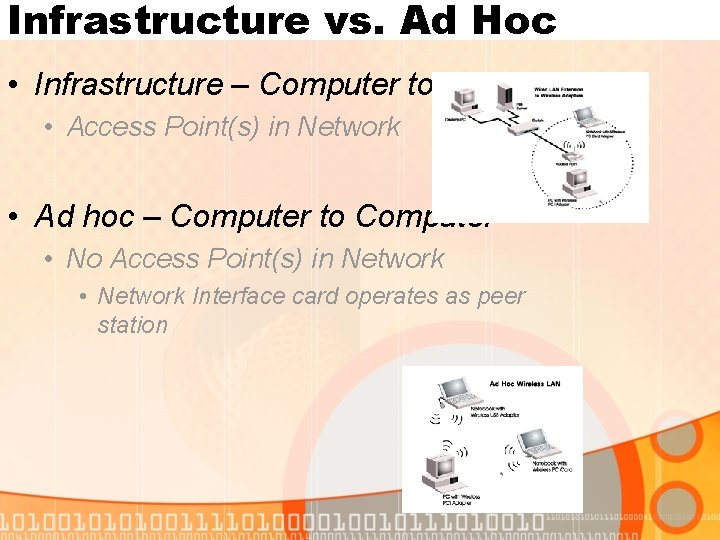
Infrastructure vs. Ad Hoc • Infrastructure – Computer to Network • Access Point(s) in Network • Ad hoc – Computer to Computer • No Access Point(s) in Network • Network Interface card operates as peer station

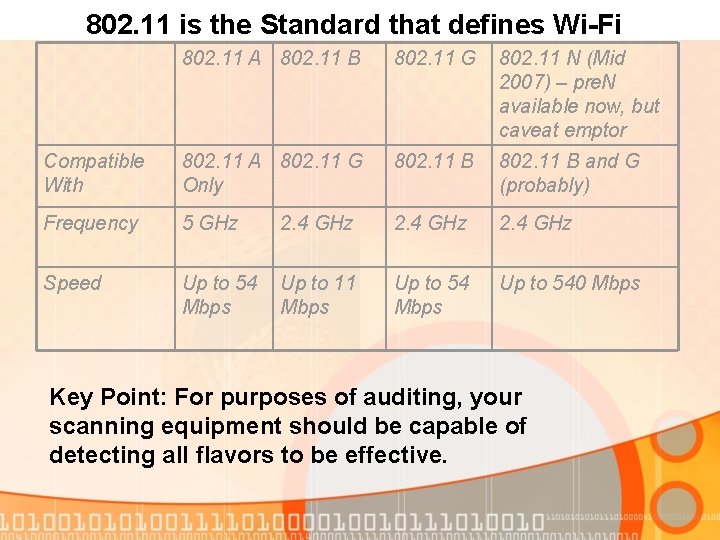
802. 11 is the Standard that defines Wi-Fi 802. 11 A 802. 11 B 802. 11 G 802. 11 N (Mid 2007) – pre. N available now, but caveat emptor Compatible With 802. 11 A 802. 11 G Only 802. 11 B and G (probably) Frequency 5 GHz 2. 4 GHz Speed Up to 54 Up to 11 Mbps Up to 540 Mbps 2. 4 GHz Key Point: For purposes of auditing, your scanning equipment should be capable of detecting all flavors to be effective.

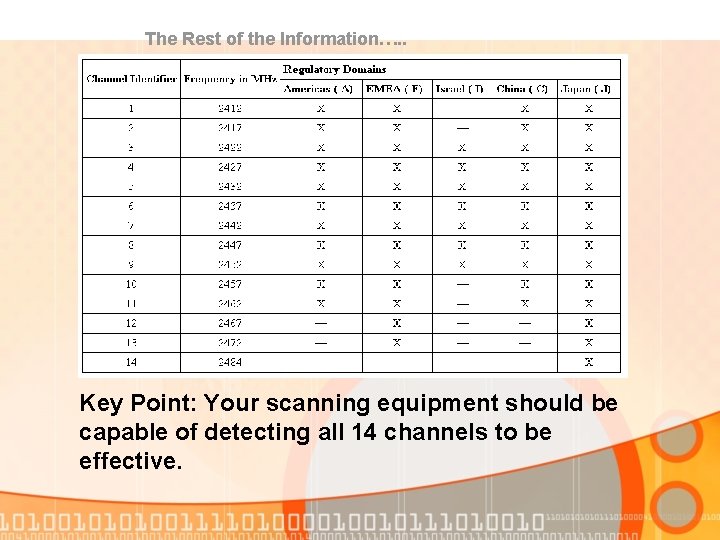
The Rest of the Information…. . Key Point: Your scanning equipment should be capable of detecting all 14 channels to be effective.

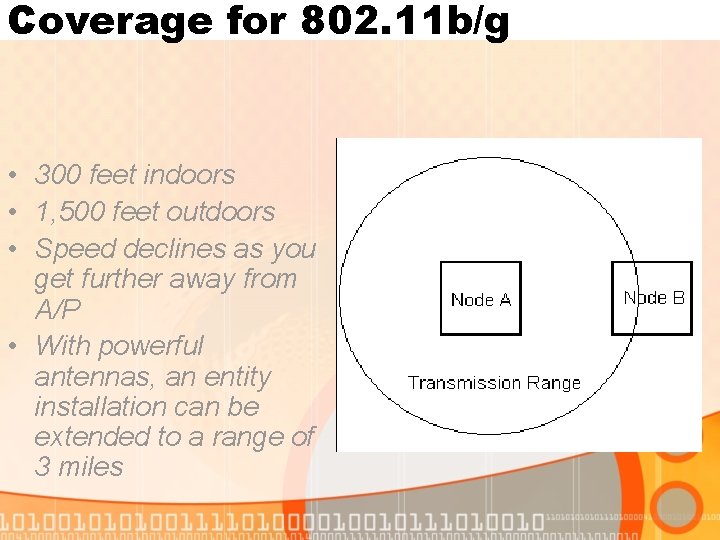
Coverage for 802. 11 b/g • 300 feet indoors • 1, 500 feet outdoors • Speed declines as you get further away from A/P • With powerful antennas, an entity installation can be extended to a range of 3 miles

Definition - MAC Address (Like SSN) • A media access control address (MAC address) is a unique identifier attached to most forms of networking equipment. The addresses are designed to be globally unique. The MAC address allows each host to be uniquely identified and allows frames to be marked for specific hosts. (Note, Hackers can spoof the MAC address. )

Definition – SSID (Like a Name) • A service set identifier (SSID) is a code attached to all packets on a wireless network to identify each packet as part of that network. Think of it as similar to having the company name on the side of a building. The code consists of a maximum of 32 alphanumeric characters. All wireless devices attempting to communicate with each other must share the same SSID. The SSID can be set to whatever the network owner likes.

Authentication • 802. 11 networks use two authentication methods: open-system authentication (no authentication) and shared-key authentication. In both schemes, each mobile client (called a station or supplicant) must authenticate to the access point. • Open-system authentication might better be called "no authentication", because no actual authentication takes place: the station says "please authenticate me", and the AP does so, with no credential exchange. • Shared-key authentication is somewhat more robust (except that it depends on WEP). The station requests authentication, and the access point (AP) responds with a WEP-encrypted challenge. The station can decrypt the challenge and respond only if it has the correct WEP password. In both of these methods, the station must also know the service set identifier (SSID) of the AP. However, because the AP might broadcast its SSID, and because stations talking to that SSID always broadcast it, this behavior isn't much of an obstacle to learning the SSID.

WEP • The 802. 11 b standard includes a provision for encryption called WEP (Wired Equivalent Privacy). Depending on the manufacturer and the model of the NIC card and access point, there are two levels of WEP commonly available - one based on a 40 -bit encryption key and 24 -bit Initialization Vector (also called 64 -bit encryption and generally considered insecure) and a 104 -bit key plus the 24 -bit IV (so called 128 bit encryption. ) Each device on the network must have the same key and that key must be manually entered into the wireless receiving device to match the key on the access point. Some proprietary solutions from vendors like Cisco have automated the passing of keys. Newer 802. 11 encryption standards have automated key functions under the Wi-Fi Protected Access (WPA 2 ) specification.

More WEP • WECA (Wireless Ethernet Compatibility Alliance)has only certified the 64 bit WEP encryption. Thus, access points and cards supporting 128 bit and 256 bit WEP encryption may not work for all vendor wireless cards even if they provide these encryption schemes due to possible variances in the wireless chipsets used by vendors in their products. Therefore, most sites will use the 64 bit encryption to allow wireless cards from different vendors to work on their network. Some vendors like Cisco also have proprietary encryption solutions like LEAP that only work on Cisco wireless cards. For audits, the main concern is that sites using 64 bit WEP encryption are using a weak encryption standard for the security of wireless data communications. Of course, this is better than the majority of access points that are being deployed without WEP even being enabled. • WEP is easily cracked and widely used. This is the lowhanging fruit you should go for in your audits.

WPA (Wi-Fi Protected Access) • WPA is a subset of the 802. 11 i security standard for wireless networks. WPA improves on the authentication and encryption features of WEP. In fact, WPA was developed by the networking industry in response to the shortcomings of WEP. • One of the key technologies behind WPA is the Temporal Key Integrity Protocol (TKIP). TKIP addresses the encryption weaknesses of WEP. Another key component of WPA is built-in authentication that WEP does not offer. With this feature, WPA provides roughly comparable security to VPN tunneling with WEP, with the benefit of easier administration and use. • One variation of WPA is called WPA Pre Shared Key or WPA-PSK for short. WPA-PSK is a simplified but still powerful form of WPA most suitable for home Wi-Fi networking. To use WPA-PSK, a person sets a static key or "passphrase" as with WEP. But, using TKIP, WPA -PSK automatically changes the keys at a preset time interval, making it much more difficult for hackers to find and exploit them.

WPA 2 ü Maintains all components specified in the 802. 11 i standard. ü Supports 802. 1 x port security. ü The primary difference between WPA and WPA 2 is the type of encryption used – the stronger Advanced Encryption Standard (AES) vs. TKIP in WPA. ü WPA 2 provides government grade security by implementing the National Institute of Standards and Technology (NIST) FIPS 140 -2 compliant AES encryption algorithm. http: //www. wi-fi. org/Open. Section/protected_access. asp

Audit Concerns • Rogue access points • Authorized access points that are inadequately secured • Increased vulnerability to the network by extending entity network “beyond the walls” • Confidential data may be sent in the clear • Violation of entity policies/procedures for installation of wireless devices • Errors by Administrators setting up APs

Looking for Rogues

Basic Tools • • • PC Cards/Wi. Fi Antennas Wi-Fi Finders Built in XP Tools Netstumbler Kismet Aircrack

The Laptop Internal or PC Card has Limits • A laptop using a PC card's tiny integrated "bulge" antenna is not a very powerful receiver. Some external cards have a tiny coaxial jack into which you can plug a coaxial connector leading to an external antenna. Experiments using Netstumbler and a PC card's integrated antenna alone showed that 50%-60% as many stations can be discovered using a higher powered external antenna. • BUT, more is not necessarily better. For a normal audit, you don’t really want the “noise” of picking up every access point within a mile if you are just focusing on a particular building. Big antennas are good for demonstrating that you can access a particular site from a distance.

The Basics of Direction • Antennas come in various shapes and sizes. They have different performance patterns and gain. • Directional antennas focus the signal in a specific direction with more power. • Omni directional antennas work great to cover uniformly in all directions.

Backfire Directional Ø The backfire is a small directional antenna with excellent gain (15 d. Bi). They look similar to a parabolic dish, but the gain isn't as high. Work well for point to point or point to multipoint systems because of the excellent gain and the good noise figures.

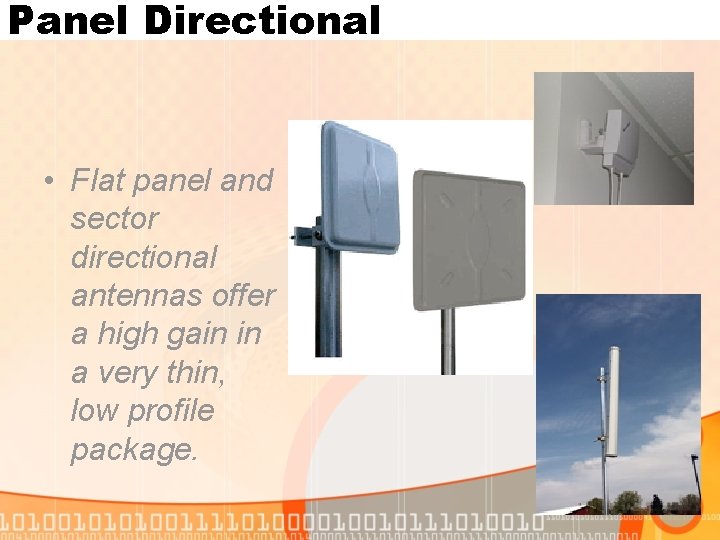
Panel Directional • Flat panel and sector directional antennas offer a high gain in a very thin, low profile package.

Dish Directional • One of the most powerful wireless antennas for distance. Parabolic dish antennas put out tremendous gain but are a little hard to point and make a connection with. As the gain of an antenna increases, the antenna’s radiation pattern decreases until you have a very little window to point or aim your dish correctly. Dish antennas are almost always used for a point to point system for long haul systems. The Parabolic Dish antennas work by focusing the power to a central point and beaming the radio’s signal to a specific area, kind of like the adjustable reflector on a flashlight. These antennas are highly focused and are an excellent tool to send signals a very long distance.

Yagi Directional • Yagi antennas were the design of two Japanese people, Hidetsugu Yagi and Shintaro Uda, and are sometimes referred to as Yagi-Uda antennas. These antennas are typically very directional and are used for point to point, or to extend the range of a point to multipoint system. They have excellent signal strength and in the right circumstances can communicate for miles!

Oh My……. . Sniper Antennas

124. 9 mile 802. 11 link is possible, with the right antenna. Security is important because the attacker could be anywhere.

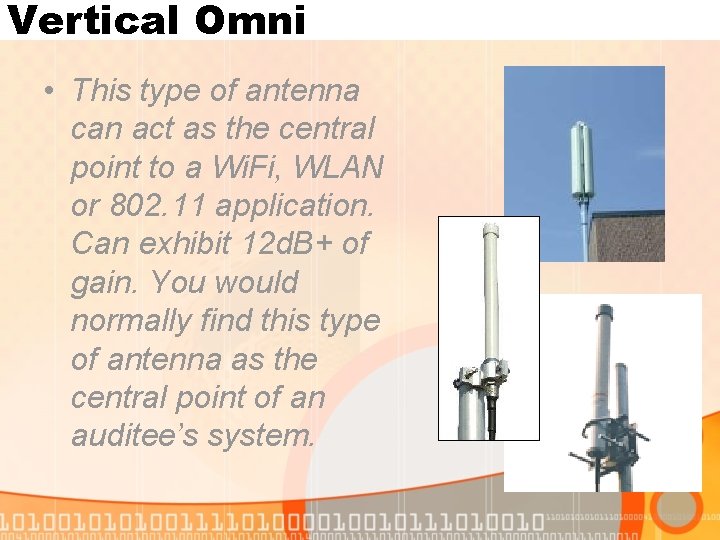
Vertical Omni • This type of antenna can act as the central point to a Wi. Fi, WLAN or 802. 11 application. Can exhibit 12 d. B+ of gain. You would normally find this type of antenna as the central point of an auditee’s system.

Ceiling Dome • Auditees may mount one ceiling dome antenna above every computer or workstation for a complete wireless network.

Rubber Duck Omni • This antenna gives you approximately 2 times the range over your existing wireless AP "Stock" antenna.

Small Desktop • Supplements the rubber duck antennas provided for some APs

Mobile Vertical Omni • Provides a vast improvement over a PC Card wireless card when used for wardriving.

Deployment at the Audit Site

Wi-Fi Finders • Come in a variety of forms. • Some just show whether or not there is available Wi-Fi. • Others test to see if you can get on-line via the connection. • Others actually display the SSID and other information about the network.

Wi-Fi Finders/Detectors • These are great tools to help you find an access point for use, but are not sufficient for audit purposes.

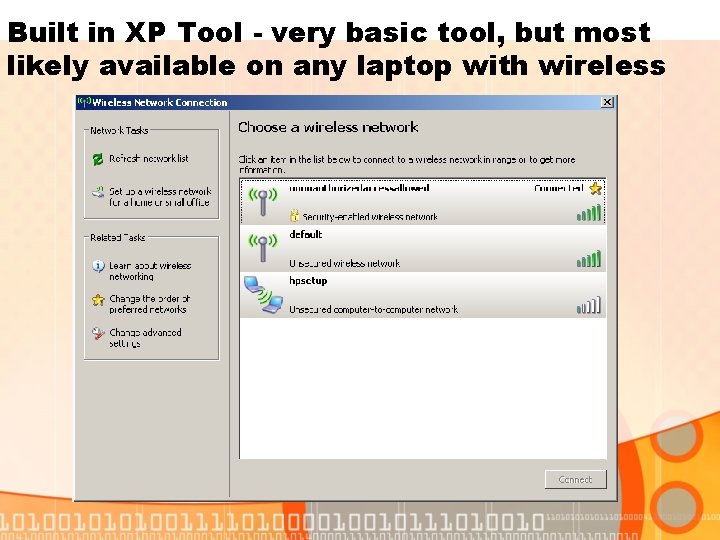
Built in XP Tool - very basic tool, but most likely available on any laptop with wireless

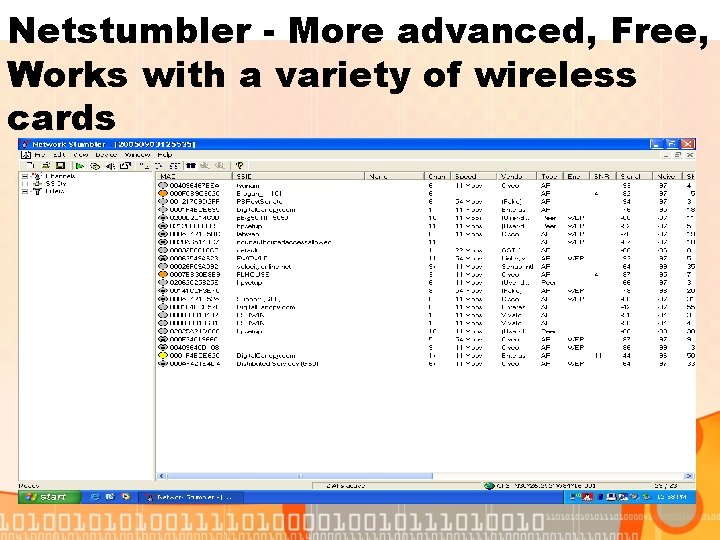
Netstumbler - More advanced, Free, Works with a variety of wireless cards

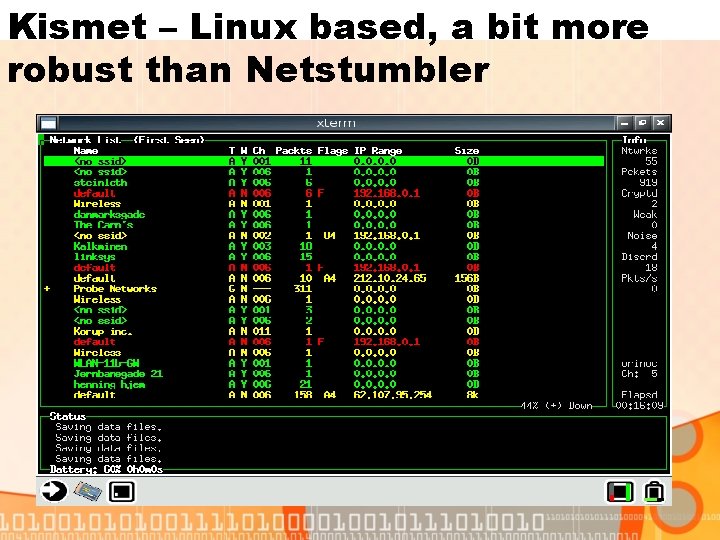
Kismet – Linux based, a bit more robust than Netstumbler

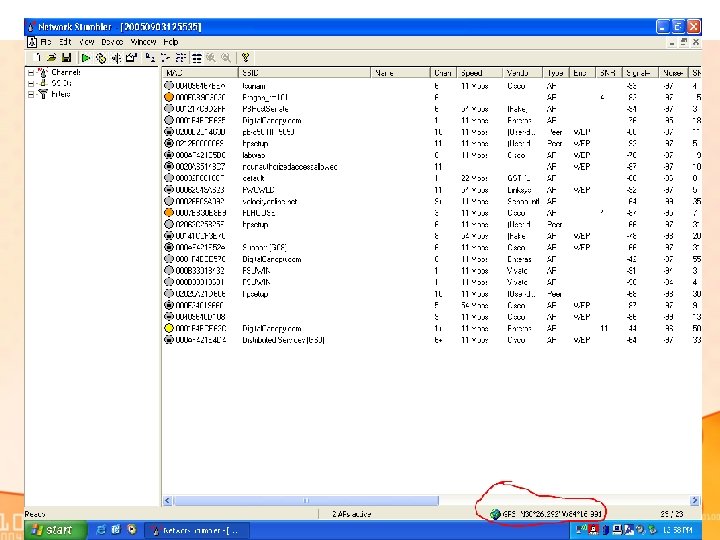
Mapping with a GPS to Find Rogues • By itself, Netstumber just gives you a list of AP’s detected, you really want to know where they are. • GPS helps to filter signals that are not physically coming from the location you are auditing. • GPS helps to localize the signals that are coming from the location you are auditing.


Using Netstumbler, a GPS, and Google Maps, you can create this…

And you can zoom in on the building you are interested in

If you don’t, someone else will (and probably already has)

Process for doing a scan with GPS • First walk the inside of the building without the GPS (GPS only works outside). Then walk around the outside of the building with the GPS and finally drive around the surrounding block or two with the GPS. • The Lat/Long indicated are not exactly where the point is, but where you received the strongest signal. So, • 0’s for the Latitude and Longitude indicate that you only received the signal inside the building you were scanning (you definitely want to investigate these) • The rest of the data should show on the map. You may have also detected these from inside the building, but you need to determine if they are from the inside bleeding out or from the outside bleeding in. So, • If they show up directly surrounding the building on the map, they are probably inside the building as you received the strongest signal nearest to the building. • If they show up further from the building on the map, then they are probably coming from somewhere else.

Hacking with Aircrack • Aircrack is a set of tools for hacking (but also useful for auditing) wireless networks including: • • Airodump: 802. 11 packet capture program Aireplay: 802. 11 packet injection program Aircrack: static Wep and WPA-PSK key cracker Airdecap: Decrypts WEP/WPA capture files www. cr 0. net: 8040/code/network/aircrack

The tools I have shown so far are free. But, if you insist on buying something…

Commercial Products - Air. Magnet ANALYZER • Immediately identify Rogue Devices using multiple methods. • Physically locate and remove Rogues using the Find Tool. Insure every device in the network conforms to your security policy with support for WPA, 802. 11 i, 802. 1 x, VPNs, LEAP, PEAP, TKIP, MIC, FAST, WEP or others. • Proactively identify dozens of wireless attacks and hacks including Do. S attacks, Dictionary Attacks, Wireless Intrusions, and the latest Queensland attack. • Detect a total of 54 security vulnerabilities and events. • Construct and manage detailed security policies through an intuitive policy management interface. • Keep your network protected while you troubleshoot with built-in authentication support for WPA, WEP, LEAP, FAST, PEAP, TLS, FAST and more. $2995 $3495

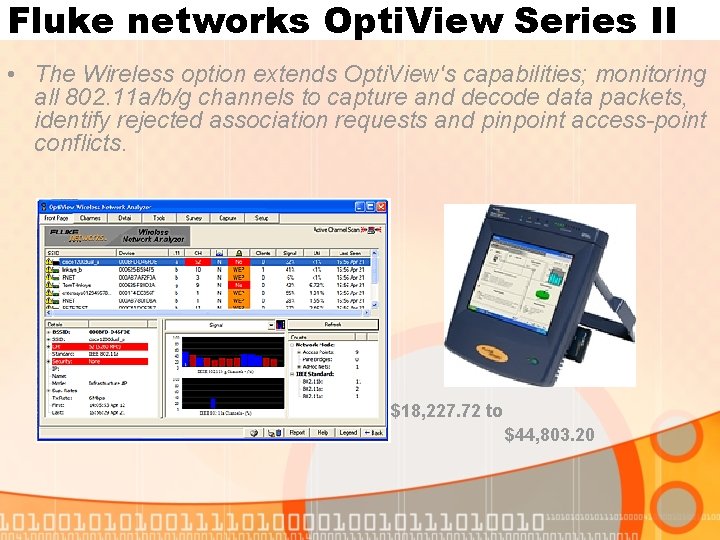
Fluke networks Opti. View Series II • The Wireless option extends Opti. View's capabilities; monitoring all 802. 11 a/b/g channels to capture and decode data packets, identify rejected association requests and pinpoint access-point conflicts. $18, 227. 72 to $44, 803. 20

Procedures - Managing the APs How does the auditee connect to the boxes? Certain vendors, such as Cisco, provide support for Secure Socket Layer (SSL) connections allowing these devices to be managed with optimized security through a Web browser. Is change management of the wireless architecture guided by procedures? Patches, access, and monitoring. Is any of this in writing?

Sample Wireless Procedures • • Department heads shall register any deployment of wireless access points with ACNS. This registration shall provide information requested by the wireless overseeing committee. Registration and information of wireless activity will be available at: http: //www. acns. fsu. edu/Network/wireless_survey. shtml. Installation of Access Points will be the responsibility of the individual department, but must comply with rules and regulations of the University as implemented by the overseeing committee and enforced by ACNS. i. e. , all installations must not interfere with existing installations and cooperation must be awarded to insure baseline levels of connection service quality. Installation of antennas must comply with all federal and state regulations for antennas. The installation of access points and bridging devices must be consistent with health, building, and fire codes. Security: General access to the network infrastructure, including wireless infrastructure, will be limited to individuals authorized to use campus and Internet resources. Users of campus and Internet resources shall be authenticated. • • • Physical Security of wireless access points will be maintained to protect the access point from theft or access to the data port. Password and data protection is the responsibility of the application. The wireless infrastructure will not provide specialized encryption or authentication that should be relied on by applications. In particular, no application should rely on IP address based security or reusable clear text passwords. It is expected instead that service machines will expect/require their own general or applications authentication, authorization and encryption mechanisms to be used by clients entering from any unprotected network. Access points or the first switch after the access point shall provide user authentication and/or authorization to the network before access shall be given.

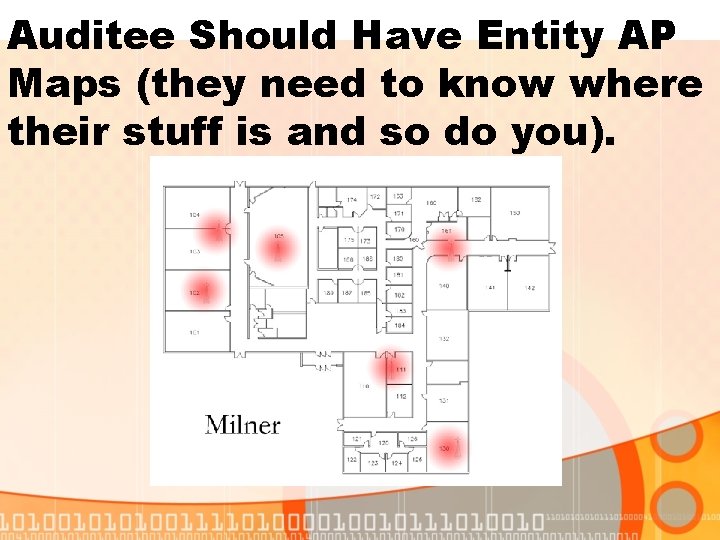
Auditee Should Have Entity AP Maps (they need to know where their stuff is and so do you).

What can be done to secure wireless? No security is perfect so keep in mind the concept of security in layers. • Activate WEP at the very least. WEP is not very secure, but it is still better than nothing. Because 802. 11 does not support the dynamic exchange of WEP keys, leaving the same key in use for weeks, months, and years. This is the same as never changing your password. But the key can be changed manually. There should be procedures to periodically change the WEP Key. But, if site is transmitting confidential information, this is not enough security. Example: A site that must meet HIPAA requirements would probably need a stronger encryption system to meet the spirit of the legislation.

What can be done to secure wireless? • If available, Utilize dynamic key exchange mechanisms. Use 802. 11 i or vendor-specific technologies for enhanced encryption and dynamic key exchange. • Ensure NIC and access point firmware is up-todate. Vendors often implement patches to firmware that fix security issues. Start by upgrading the firmware in the access point soon after pulling it out of the box. On an ongoing basis, make it a habit to check that all devices have the most recent firmware releases to cover up all known security holes. As an audit procedure, you can see what version of the firmware they have and compare it to the most up-to-date version.

What can be done to secure wireless? • Ensure only authorized people can reset the access points. Some access points will revert back to factory default settings (i. e. , no security at all) when someone pushes the reset button on the access point. This makes the access point a fragile entry point for a hacker to extend their reach into the network. As a result, provide adequate physical security for the access point hardware. For example, don't place an access point within easy reach on a table in the office. Instead, mount them out of view above ceiling tiles. Some access points don't have reset buttons, but they allow you to reset via an RS-232 cable through a console connection. To prevent this, be sure to disable the console port. • Assign "strong" passwords to access points. Don't use default passwords for access points. They are also well known, making it easy for someone to change configuration parameters on the access point to their advantage. Be sure to alter these passwords periodically.

What can be done to secure wireless? • Don't broadcast SSIDs (this is not an absolute rule). If this feature is available, you can avoid having user devices automatically sniff the SSID in use by the access point. Windows. XP and other monitoring tools (e. g. , Air. Magnet, Net. Stumbler, Air. Peek, and Win. C) will automatically sniff 802. 11 traffic to obtain the SSID. With SSID broadcasting turned off, the access point will not include the SSID in the beacon frame, making most sniffing tools useless. This isn't foolproof, however, because someone can still monitor 802. 11 association frames (which always carry the SSID, even if SSID broadcasting is turned off). At least shutting off the broadcast mechanism will limit access.

What can be done to secure wireless? • Don't use default SSID names. As a default setting, most access point vendors use their vendor name as the SSID. Others are also commonly known -- such as "Any. " As a result, set the SSID to something different ---- as odd an word or phrase as possible -- to avoid people from guessing. Better yet, make it something like “Do Not Enter” or “No Trespassing” to put a hacker on notice that this is not a public network. Think of the SSID as being a weak password that will stop a casual snooper. A hacker, though, can easily find the SSID in association frames when a user first boots their wireless device. • Implement personal firewalls. If a hacker is able to associate with an access point, which is extremely probable if WEP is turned off, the hacker can easily access (via the Windows operating system) files on other users' devices that are associated with an access point on the same WLAN. As a result, it's crucial that all users disable file sharing for all folders and utilize personal firewalls.

What can be done to secure wireless? • Monitor for rogue access points. Create a wireless baseline by creating an inventory of wireless access points including SSIDs, MAC addresses, and communication channels used. Continually monitor the network and check for access points that don't conform to the baseline or configuration policies. An access point that doesn't match specific security settings has likely been reset or is actually a rogue access point installed by a hacker or an employee not wanting to coordinate with IT personnel. You can also deploy intrusion detection sensors to identify the presence of hackers based on invalid MAC addresses. The main idea is to provide alerts if suspicious behavior is occurring. Ideally, the auditee should have this baseline for you to use although most will not.

Summary for Securing the Wireless Environment 1) Create Wireless policies and procedures after analyzing risks. 2) Authenticate users (LDAP; RADIUS). 3) Run WAPs outside of firewall and provide adequate physical security for WAPs; interdepartmental firewalls segregate wireless areas from trusted network assets. 4) Run antivirus and firewall software on wirelessenabled client devices. 5) Use a VPN, the new WPA encryption or, use WEP or LEAP if other encryption methods not available.

Securing the Wireless Environment 6) Turnoff SSID broadcast or change to name that does not identify entity; 7) Employ intrusion detection systems on wireless network segments to monitor for unusual activity on the network and scan for rouge wireless access points, and 8) Keep abreast of security vulnerabilities with the wireless infrastructure and take corrective action quickly. 9) Attach WAPs to switches and ensure switches are not set to broadcast mode 10) Inventory SSIDs, MAC addresses of WAPs, and channels as baseline for use in wireless audits.

What our audits have found • • • Rogue Access Points Poor Security over Authorized Access Points No internal scans Lack of Policies and Procedures Lack of Documentation Firmware not up-to-date on wireless hardware

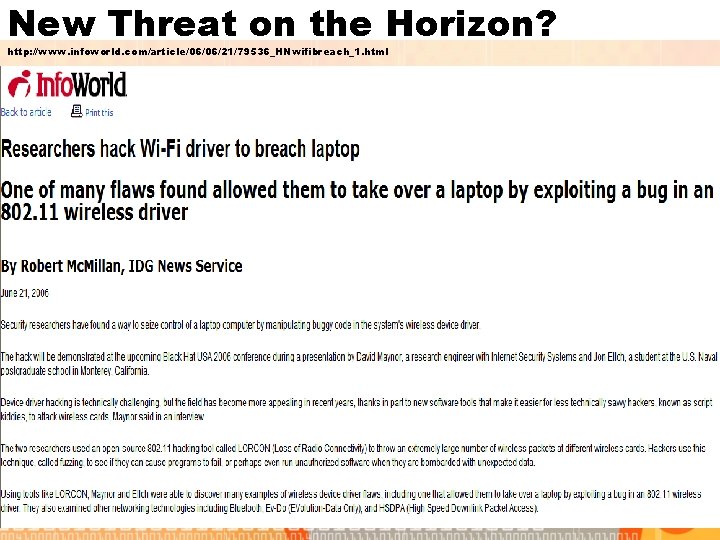
New Threat on the Horizon? http: //www. infoworld. com/article/06/06/21/79536_HNwifibreach_1. html

Bluetooth

What is Bluetooth? n n n Short range communications Personal Area Networks Low Power Communications Between Devices Get rid of the wires for peripherals The name Bluetooth is from the a 10 th century king of Denmark, Harald Bluetooth. According to the inventors of the Bluetooth technology, Harald engaged in diplomacy which led warring parties to negotiate with each other, making Bluetooth a fitting name for their technology, which allows different devices to talk to each other. The name of the king in Danish was Harald Blåtand the Bluetooth logo is based on the H and B runes.

Bluetooth-Enabled Devices n n n Printers Cell Phones Audio Speakers / Headsets PDA’s Keyboards / Mice / Joysticks Cameras MP 3 Players Networking Cars Remote Controls GPS

Paris Hilton Contrary to most reports, Paris Hilton’s cell phone was not hacked via Bluetooth. Rather the data from Tmobile phones are stored on a T-mobile website which was hacked via social engineering. In fact, it was reported that her phone did not even have Bluetooth.

Bluetooth Classes Class 3 (1 m. W) is the rarest and allows transmission of 10 centimeters (3. 9 inches), with a maximum of 1 meter (3. 2 feet) n Class 2 (2. 5 m. W) is most common and allows a quoted transmission distance of 10 meters (32 ft) n Class 1 (100 m. W) has the longest range at up to 100 meters. This class of product is readily available. n

Bluetooth Security n Encryption n Profiles n Security Modes n Security Levels n PIN

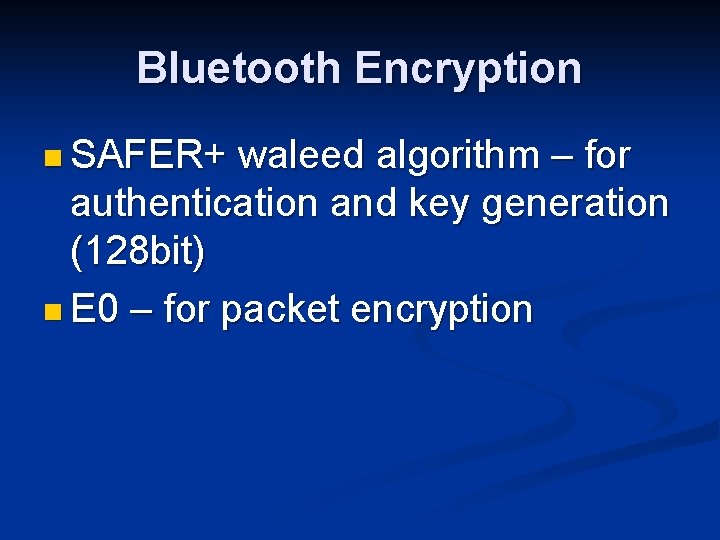
Bluetooth Encryption n SAFER+ waleed algorithm – for authentication and key generation (128 bit) n E 0 – for packet encryption

What are Profiles? n n Short Version – They are like drivers for peripherals Profiles have been developed in order to describe how implementations of user models are to be accomplished n n n Describes a number of user scenarios where Bluetooth performs the radio transmission A profile can be described as a vertical slice through the protocol stack Defines options in each protocol that are mandatory for the profile Defines parameter ranges for each protocol. Concept is used to decrease the risk of interoperability problems between different manufacturers' products

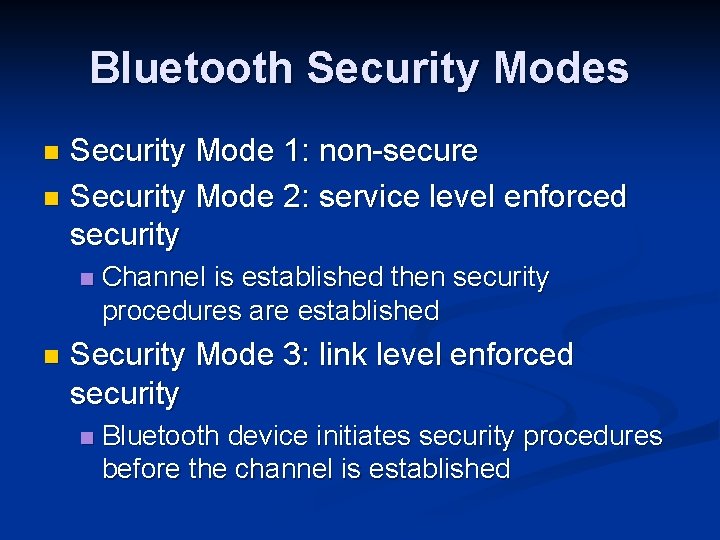
Bluetooth Security Modes Security Mode 1: non-secure n Security Mode 2: service level enforced security n n n Channel is established then security procedures are established Security Mode 3: link level enforced security n Bluetooth device initiates security procedures before the channel is established

Bluetooth Security Levels n Devices, there are 2 levels: n “trusted device" and "untrusted device". The trusted device obviously has unrestricted access to all services. n Services, 3 security levels are defined: n services that require authorization and authentication n services that require authentication only n services that are open to all devices.

Bluetooth PIN 1 -16 Digits n Basic Attack: Pairing and Authentication Process n Repairing Attack: Exploits the connection establishment protocol and force to repeat the pairing n Sniffing to cracking times (3 GHZ CPU): n 4 Digits: 0. 063 seconds n 5 Digits: 0. 75 seconds n 6 Digits 7. 609 seconds n 7 Digits: 76. 127 seconds n

Bluetooth Hacking / Cracking

Bluetooth Hardware/Software Linksys USBBT 100 ($40) n Hyper. Gain RE 05 U 2. 4 GHz antenna ($15) n btscanner v 1 n btscanner v 2 n BT Audit n Bluez n

Long Distance Snarfing n Unamplified at over 1 mile

Hacking Tools Blue Bug - Security loophole to allow for downloading of data from bluetooth -enabled cell phones, non-intrusive – the owner is not prompted. Blooover - Tool to check if other phones are vulnerable to Blue. Bug, runs on J 2 ME-enabled devices (cell phones) Blue. Smack - Knocks out Bluetoothenabled devices immediately, Do. S attack, easy as l 2 ping –s 600 <bt-hexaddress>

Effects n Privacy concerns n n Use of services n n Theft of data and personal information (Imagine being able to pick up everything someone types on a Bluetooth keyboard from a mile away. ) Theft of digital resources Do. S, Viruses, Worms

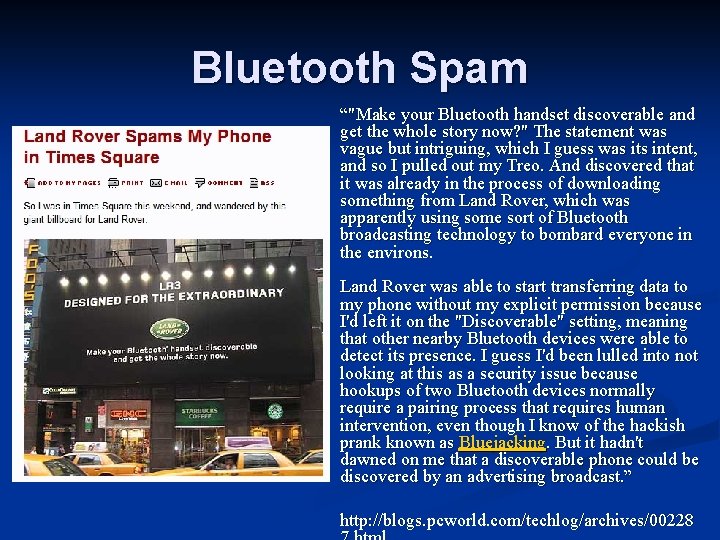
Bluetooth Spam “"Make your Bluetooth handset discoverable and get the whole story now? " The statement was vague but intriguing, which I guess was its intent, and so I pulled out my Treo. And discovered that it was already in the process of downloading something from Land Rover, which was apparently using some sort of Bluetooth broadcasting technology to bombard everyone in the environs. Land Rover was able to start transferring data to my phone without my explicit permission because I'd left it on the "Discoverable" setting, meaning that other nearby Bluetooth devices were able to detect its presence. I guess I'd been lulled into not looking at this as a security issue because hookups of two Bluetooth devices normally require a pairing process that requires human intervention, even though I know of the hackish prank known as Bluejacking. But it hadn't dawned on me that a discoverable phone could be discovered by an advertising broadcast. ” http: //blogs. pcworld. com/techlog/archives/00228

Points of Interests / Reference Bluetooth Security White Paper v 1. 0 (www. bluetooth. com/upload/24 Security_P aper. PDF) n Cracking the Bluetooth PIN: (http: //www. eng. tau. ac. il/~yash/shakedwool-mobisys 05/) n

Radio Frequency Identification (RFID)

About RFID Radio Frequency Identification (RFID) is an automatic identification method, relying on storing and remotely retrieving data using devices called RFID tags or transponders n RFID tag: a small object can be attached or incorporated into a product (retail merchandise, shipping containers, tires, etc. ) animals or people n RFID tags contain antennas to enable them to receive and respond to radio-frequency queries from an RFID transceiver n – Passive tags require no internal power source, whereas active tags require a power source. n Think of it as an invisible bar code then ask yourself the question, what kind of security does a barcode provide?

RFID’s

Early RFID n The use of RFID in tracking and access applications first appeared during the 1980 s. n Take the example of books in a library. Security gates can detect whether or not a book has been properly checked out of the library. When users return items, the security bit is re-set and the item’s computer record is automatically updated.

Current RFID Uses n n n n Talking Prescriptions - 13. 56 MHz tags are being placed on prescriptions for Visually Impaired Veterans. The Department of Veterans Affairs Outpatient pharmacies are now supplying the tags with label information stored inside that can be read by a battery powered, talking prescription reader. This reader speaks information such as: Drug Name; Instruction; Warnings; etc. Low-frequency RFID tags are commonly used for animal identification. Pets can be implanted with small chips so that they may be returned to their owners if lost. Beer kegs are also tracked with LF RFID. Casino Chips are being embedded with RFID both to help deter counterfeiters and to provide better tracking of betting. High-frequency RFID tags are used in library book or bookstore tracking, pallet tracking, building access control, airline baggage tracking, and apparel item tracking. High-frequency tags are widely used in identification badges, replacing magnetic stripe cards. These badges need only be held within a certain distance of the reader to authenticate the holder. The American Express Blue credit card now includes a high-frequency RFID tag, a feature American Express calls Express. Pay.

More Current RFID Uses n n n RFID tags are used for electronic toll collection at toll booths. The system helps to speed traffic through toll plazas as it records the date, time, and billing data for the RFID vehicle tag. Some smart cards embedded with RFID chips are used as electronic cash, to pay fares in mass transit systems. Starting with the 2004 model year, a Smart Key/Smart Start option became available to the Toyota Prius. The key uses an active RFID circuit which allows the car to acknowledge the key's presence within approximately 3 feet of the sensor. The driver can open the doors and start the car while the key remains in a purse or pocket. Ohio Department of Rehabilitation and Correction is evaluating personnel tracking technology from Alanco Technologies. Inmates will wear wristwatch-sized transmitters that can detect if prisoners have been trying to remove them and send an alert to prison computers. Facilities in Michigan, California and Illinois already employ the technology. Wal-Mart has required its top 100 suppliers to apply RFID labels to all shipments.

RFID Implications n Privacy concerns – Stealing Tag number – Clean Dumpster Diving – Casing a home or business n Duplication of tags (spoofing) n Changes how inventory is done

RFID’s and Passports New U. S. passports will soon be read remotely at borders around the world, thanks to embedded chips that will broadcast on command an individual's name, address and digital photo to a computerized reader.

RFID Passport Implications n Researchers demonstrated that passports equipped with radio frequency identification (RFID) tags can be cloned with a laptop equipped with a $200 RFID reader and a similarly inexpensive smart card writer. In addition, they suggested that RFID tags embedded in travel documents could identify U. S. passports from a distance, possibly letting terrorists use them as a trigger for explosives. n If security does not physically check the passport, a terrorist whose name is in a watchlist could use a passport with his own name and date of birth but a different RFID without being identified.

CLEARLY, RFID has or will have critical functions which require it to be secure. RFID may already be in use at entities you audit.

RFID Frequencies n 13. 56 mhz n 125 khz (original) & 134. 2 khz n UHF n Microwave n Range: 10 meters

Tools (Or Toys Depending on your Perspective)

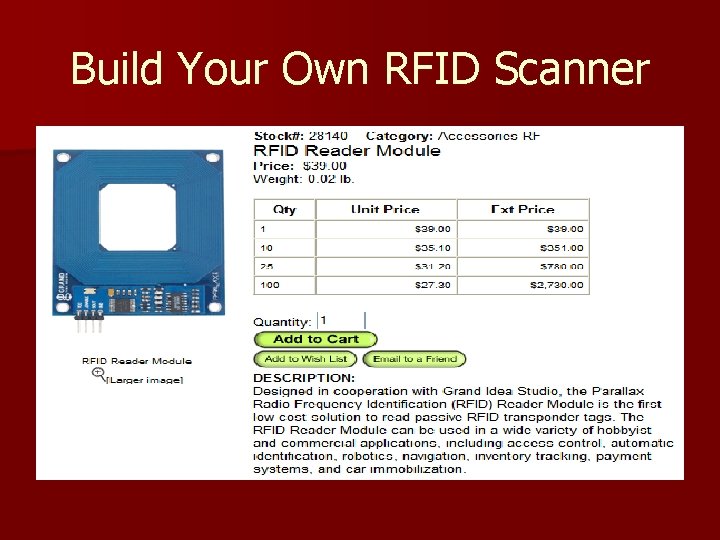
Build Your Own RFID Scanner

Or Buy One for $199

Or ideally buy this one…

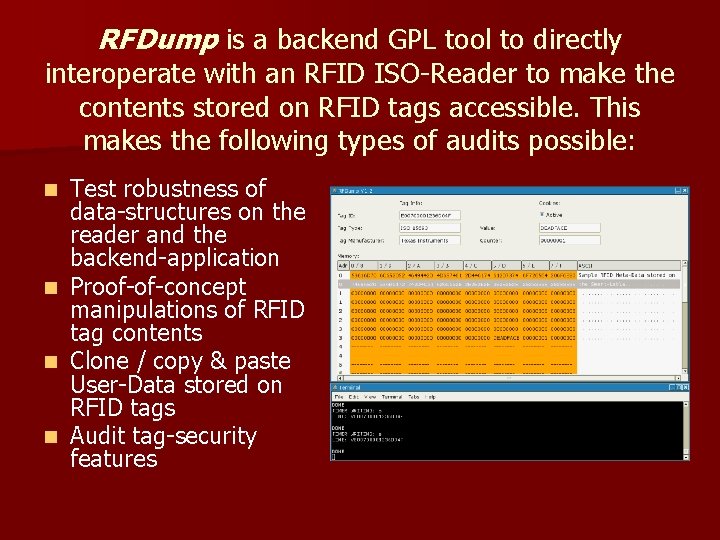
RFDump is a backend GPL tool to directly interoperate with an RFID ISO-Reader to make the contents stored on RFID tags accessible. This makes the following types of audits possible: Test robustness of data-structures on the reader and the backend-application n Proof-of-concept manipulations of RFID tag contents n Clone / copy & paste User-Data stored on RFID tags n Audit tag-security features n

Auditor Security Collection § The Auditor security collection is a Live-System based on KNOPPIX. With no installation whatsoever, the analysis platform is started directly from the CD-Rom and is fully accessible within minutes. § Independent of the hardware in use, the Auditor security collection offers a standardized working environment, so that the build-up of know-how and remote support is made easier. Professional open-source programs offer you a complete toolset to analyze your safety, byte for byte. § In order to become quickly proficient within the Auditor security collection, the menu structure is supported by recognized phases of a security check. (Foot-printing, analysis, scanning, wireless, brute-forcing, cracking). By this means, you instinctively find the right tool for the appropriate task.

Auditor Security Collection § In addition to the approx. 300 tools, the Auditor security collection contains further background information regarding the standard configuration and passwords, as well as word lists from many different areas and languages with approx. 64 million entries. § Current productivity tools such as web browser, editors and graphic tools allow you to create or edit texts and pictures for reports, directly within the Auditor security platform. § Many tools were adapted, newly developed or converted from other system platforms, in order to make as many current auditing tools available as possible on one CDROM. Tools like Wellenreiter and Kismet were equipped with an automatic hardware identification, thus avoiding irritating and annoying configuration of the wireless cards. § http: //new. remote-exploit. org/index. php/auditor_main

Media Sanitization n We have been taught to think that when "deleting" files and then emptying the Recycle Bin that the selected files are now gone. This is not true. What happens is that the Windows disk manager only "deletes" its known reference to the name and where a file is being stored on the hard drive. The files are actually still there and can be very easily recovered with simple software tools.

n n Many people think that formatting a hard drive will permanently erase all the data on the drive. This also is not true. Formatting is only a very low level hard drive cleaning function. Formatting a hard drive does not completely erase all data as one may think. It only erases the file structure information. This means that your deleted data can be recovered by anyone possessing the right tools, until it is over written.

n Imagine the hard drive of a computer is like a book. Instead of words, the hard drive is made up of binary data (0’s and 1’s). Like a book, the hard drive has a table of contents that catalogs where on the drive the 0’s and 1’s are that make up data files. Deleting and formatting drives is equivalent to removing the table of contents from the book. All of the data is still there. Software tools basically allow the computer to read the book and recreate the table of contents and thereby making all the data accessible.

n n The only way to erase your hard drive is to overwrite it. When you delete a file on your computer, it is eventually overwritten when the computer puts a new piece of data in the same place. This could happen quickly or could never happen depending on the usage of the computer. To truly erase a disk, you want to systematically overwrite every bit on the disk. We use a piece of free software called Killdisk. What this software does is systematically write 0’s into every bit on the disk.

n However, you should know that after doing this, a disk is still theoretically readable because even after the computer writes over everything with a 0, there may still be a magnetic signature left over from the old data. We won’t go into the physics behind magnetic media, so think of it this way. Imagine the surface of the drive is full of little circles. Imagine the write head on the drive puts a drop of ink in each circle to write data (white ink for a 0 or black ink for a 1). When one drop overwrites the previous drop, if you look real close at the edge, you might just be able to see what the previous drop was. So, by using very specialized pieces of hardware, you could physically examine the hard drive even after it has been overwritten.

n This equipment is prohibitively expensive and is probably only really cost effective for spies trying to access top secret government/corporate information. To be effective against this type of scan, Department of Defense uses a system of 7 consecutive passes alternating 0’s and 1’s. Or to be truly effective, you can physically destroy the drive and platters.

Tableau Device n Tableau device is a forensic tool to maintain the status of the drive being tested. The device is one way, meaning, you can read the drive, but it is impossible to change anything on the drive when it is hooked up in this manner. If a device like this is not used for testing, your results would be suspect if they had to be used in a legal proceeding. (Auditees do not need to have a device like this to be wiping their drives – in fact, you could not wipe a drive that was attached in this manner. )

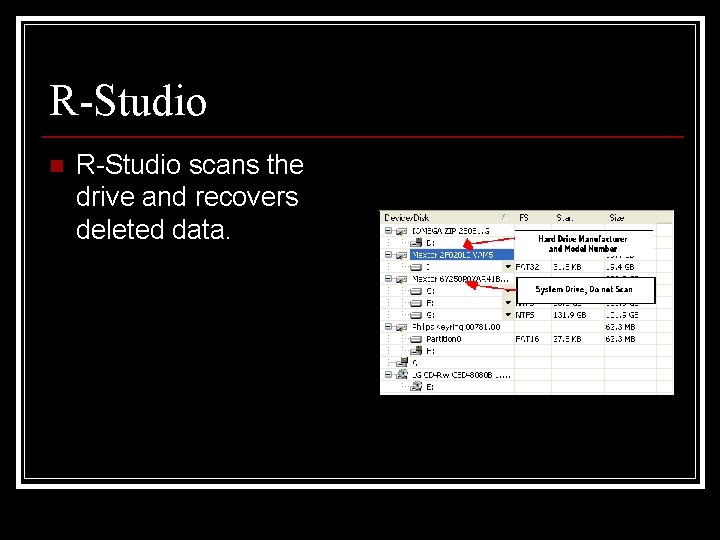
R-Studio n R-Studio scans the drive and recovers deleted data.

Audit Guidelines n n n The types of files you try and recover will depend on your scope. If you are looking for confidential information, you probably want documents (. doc, . xls, and. txt) and databases (. mdb). If you are looking for inappropriate use, you may be looking for pornography and want. jpg and. bmp. If the auditee has a process for wiping drives, you want to see documentation. Most cleaning software should create a log. You should ask for a copy of any that have been sent out to prove that they were cleaned first. If the drives or computers don’t physically work, they can’t run cleaning software, but drives can be repaired and still be read. They should have procedures like Degaussing or physically destroying the drives. Also you may want to consider what they are doing with the surplus computers. If they are being given away to charities, are they reloading an operating system onto the computers? If so, there may be licensing issues. If they are being trashed, there are environmental concerns for which most States have regulations in place. You should have a relationship with law enforcement. For example, if you find what you suspect to be child pornography during your testing, you have a legal obligation to report it. You want to make sure you have had a documented and secure chain of custody so that the drive is admissible as evidence. Since you don’t know what will be on the drive beforehand, you need to do this before you begin testing.

For More Information… n See NIST Special Publication 800 -88 (Public Draft, February 2006) – Guidelines for Media Sanitization.