Windows 10 Security Journey Creators Update New Features


















- Slides: 40



Windows 10 Security Journey Creators Update New Features Calls to Action

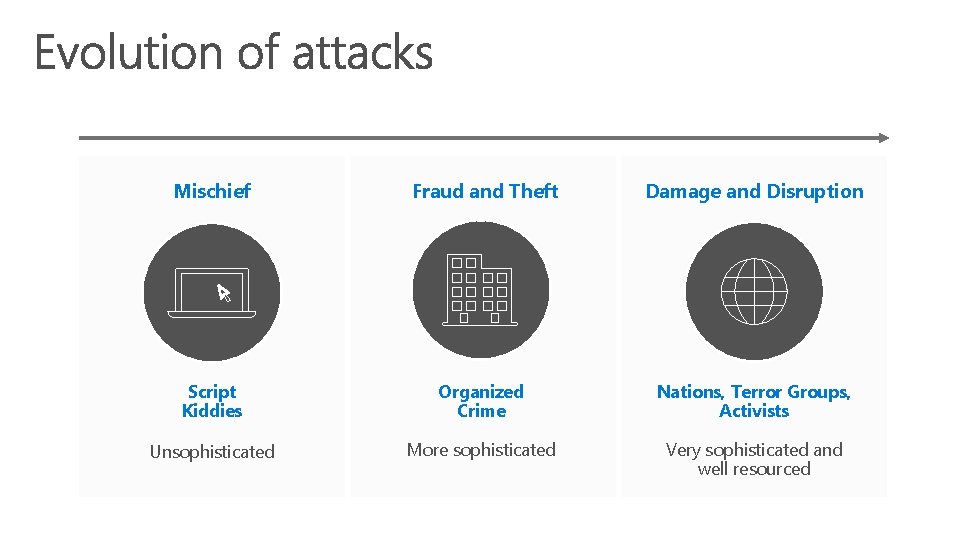
Mischief Fraud and Theft Damage and Disruption Script Kiddies Organized Crime Nations, Terror Groups, Activists Unsophisticated More sophisticated Very sophisticated and well resourced

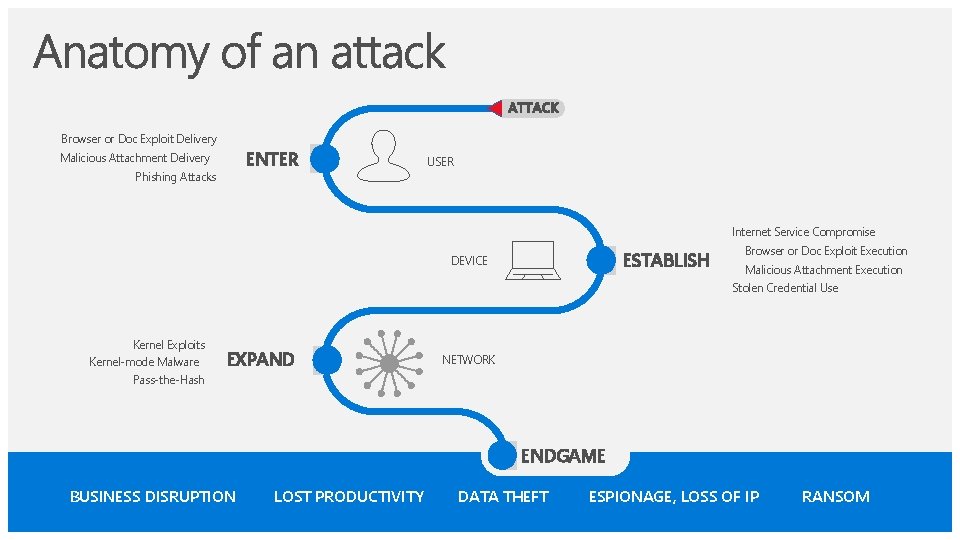
Browser or Doc Exploit Delivery ENTER Malicious Attachment Delivery Phishing Attacks USER Internet Service Compromise ESTABLISH DEVICE Browser or Doc Exploit Execution Malicious Attachment Execution Stolen Credential Use Kernel Exploits Kernel-mode Malware EXPAND NETWORK Pass-the-Hash ENDGAME BUSINESS DISRUPTION LOST PRODUCTIVITY DATA THEFT ESPIONAGE, LOSS OF IP RANSOM

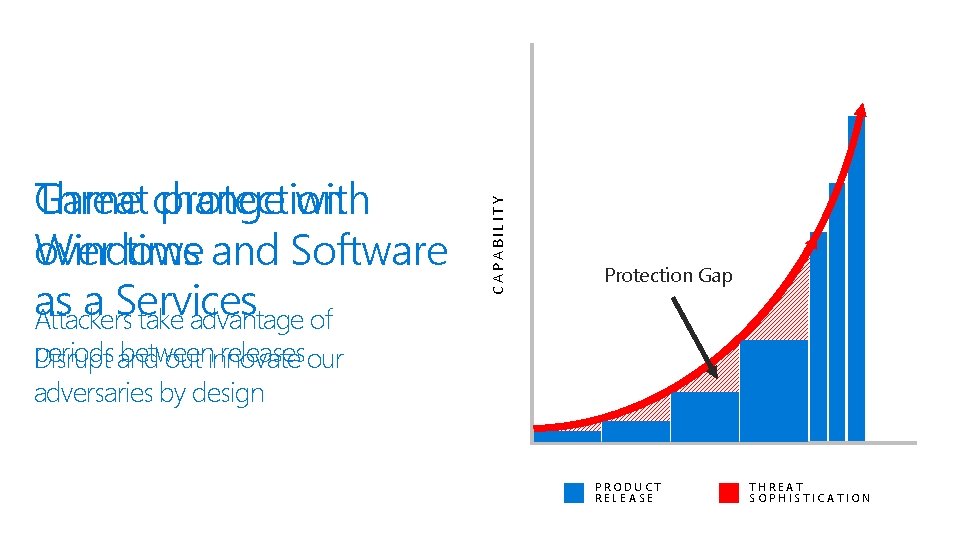
CAPABILITY Threat protection Game change with over time and Software Windows as a Services Attackers take advantage of Protection Gap periods and between releasesour Disrupt out innovate adversaries by design TIME PRODUCT RELEASE THREAT SOPHISTICATION


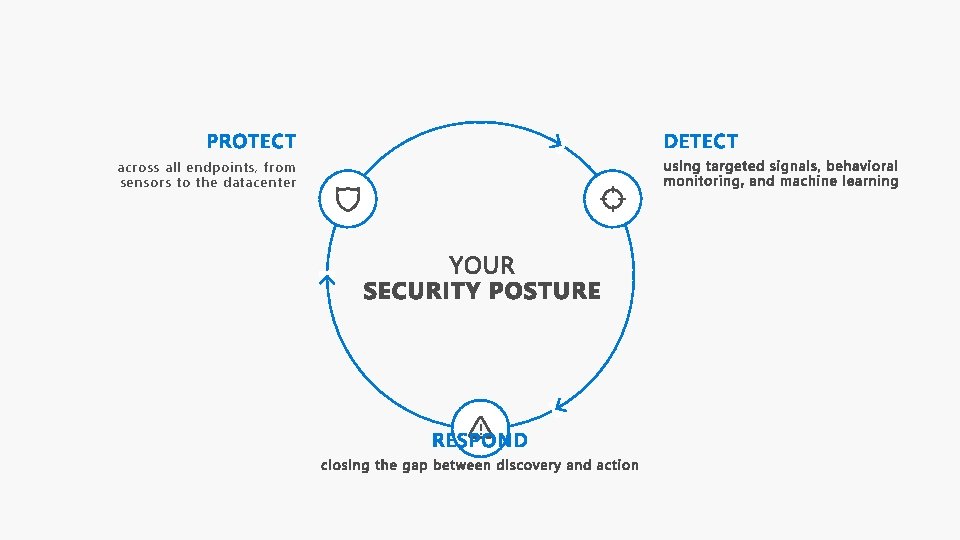
across all endpoints, from sensors to the datacenter !




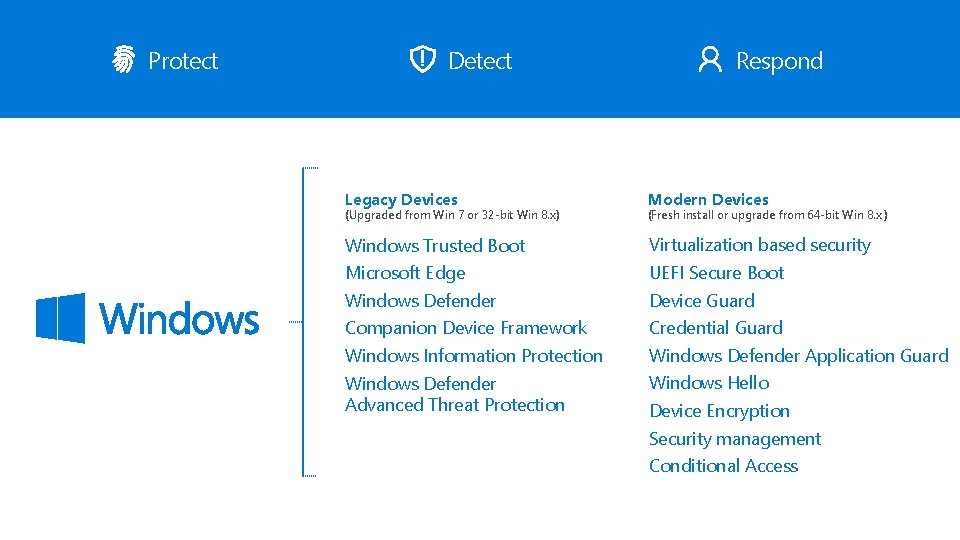
Protect Detect Respond Legacy Devices Modern Devices Windows Trusted Boot Virtualization based security Microsoft Edge UEFI Secure Boot Windows Defender Device Guard Companion Device Framework Credential Guard Windows Information Protection Windows Defender Application Guard Windows Defender Advanced Threat Protection Windows Hello (Upgraded from Win 7 or 32 -bit Win 8. x) (Fresh install or upgrade from 64 -bit Win 8. x ) Device Encryption Security management Conditional Access


“I don’t pay any attention to those things anymore…People get weary from being bombarded by watch out messages. ” “Years ago, you had 1 password to keep up with at work, ” she said. “Now people are being asked to remember 25 or 30. We haven’t really thought about cybersecurity expanding and what it has done to end users. ”

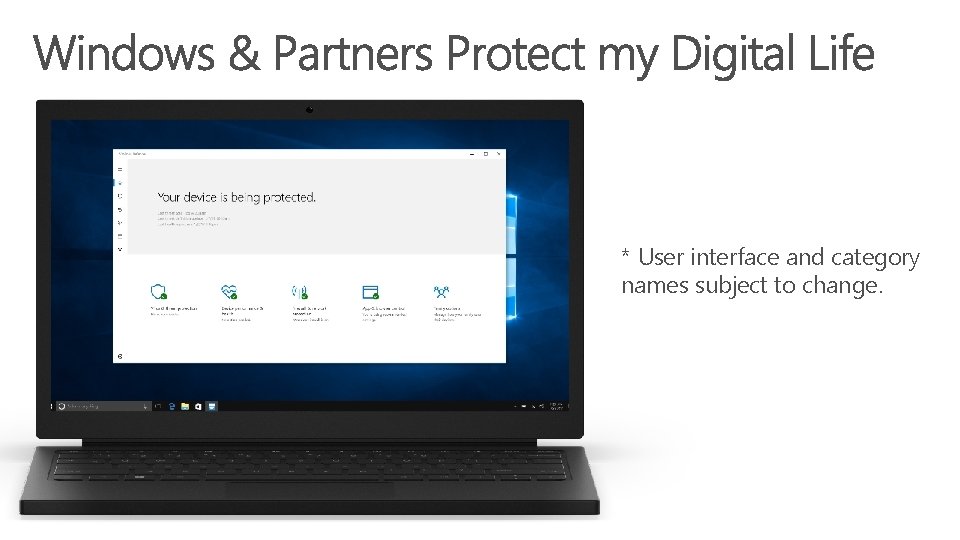
TPM 2. 0 on every device – helping protect your credentials and other key data Windows Hello , fingerprint or face authentication – helping solve the ever confusing world of passwords Device encryption – helping protect your local data if it is accessed or if your device is stolen Smart Screen filter in Edge – helping protect you against malicious web sites

You can see & control your security and device health features in one unified experience

* User interface and category names subject to change.

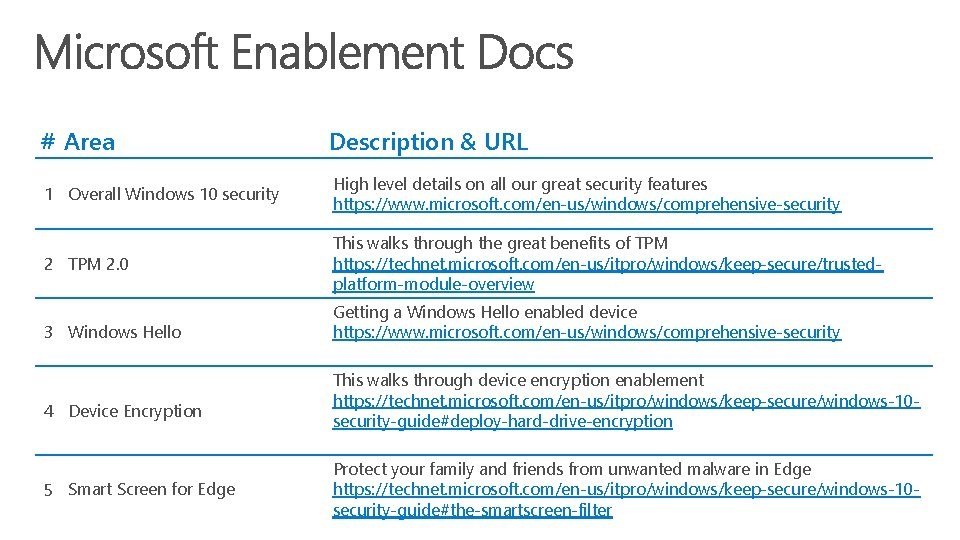
# Area Description & URL 1 Overall Windows 10 security High level details on all our great security features https: //www. microsoft. com/en-us/windows/comprehensive-security 2 TPM 2. 0 This walks through the great benefits of TPM https: //technet. microsoft. com/en-us/itpro/windows/keep-secure/trustedplatform-module-overview 3 Windows Hello 4 Device Encryption 5 Smart Screen for Edge Getting a Windows Hello enabled device https: //www. microsoft. com/en-us/windows/comprehensive-security This walks through device encryption enablement https: //technet. microsoft. com/en-us/itpro/windows/keep-secure/windows-10 security-guide#deploy-hard-drive-encryption Protect your family and friends from unwanted malware in Edge https: //technet. microsoft. com/en-us/itpro/windows/keep-secure/windows-10 security-guide#the-smartscreen-filter


Apps Windows Platform Services Kernel Device Hardware

Windows Platform Services Kernel Windows Defender Application Guard Trustlet #3 Apps Credential Guard Microsoft Edge Device Guard Protected by Windows Defender Application Guard Kernel Windows Operating System Hyper-V Device Hardware Hypervisor System Container

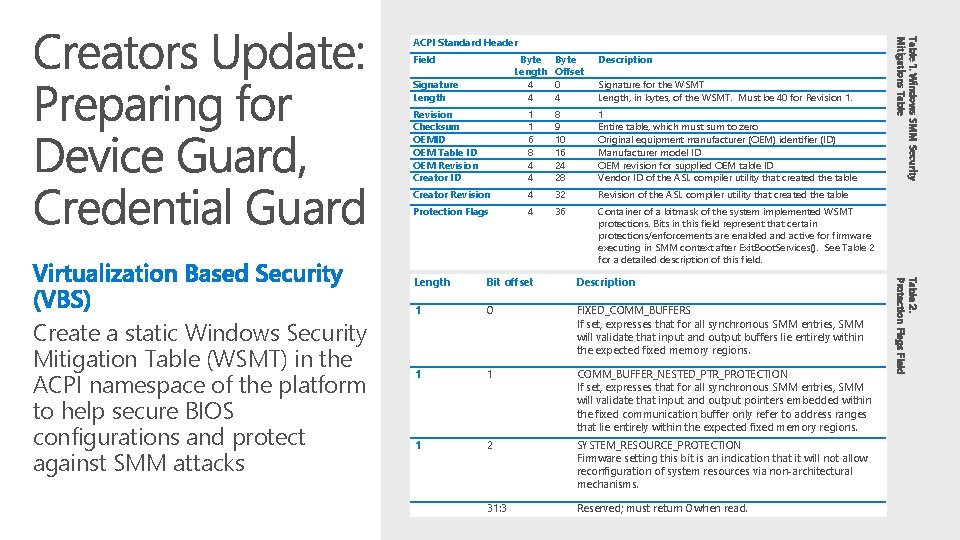
Field Byte Length 4 4 Signature Length Description Signature for the WSMT Length, in bytes, of the WSMT. Must be 40 for Revision 1. Revision Checksum OEMID OEM Table ID OEM Revision Creator ID 1 1 6 8 4 4 8 9 10 16 24 28 1 Entire table, which must sum to zero Original equipment manufacturer (OEM) identifier (ID) Manufacturer model ID OEM revision for supplied OEM table ID Vendor ID of the ASL compiler utility that created the table Creator Revision 4 32 Revision of the ASL compiler utility that created the table Protection Flags 4 36 Container of a bitmask of the system implemented WSMT protections. Bits in this field represent that certain protections/enforcements are enabled and active for firmware executing in SMM context after Exit. Boot. Services(). See Table 2 for a detailed description of this field. Length Bit offset Description 1 0 FIXED_COMM_BUFFERS If set, expresses that for all synchronous SMM entries, SMM will validate that input and output buffers lie entirely within the expected fixed memory regions. 1 1 COMM_BUFFER_NESTED_PTR_PROTECTION If set, expresses that for all synchronous SMM entries, SMM will validate that input and output pointers embedded within the fixed communication buffer only refer to address ranges that lie entirely within the expected fixed memory regions. 1 2 SYSTEM_RESOURCE_PROTECTION Firmware setting this bit is an indication that it will not allow reconfiguration of system resources via non-architectural mechanisms. 31: 3 Reserved; must return 0 when read. Table 2. Protection Flags Field Create a static Windows Security Mitigation Table (WSMT) in the ACPI namespace of the platform to help secure BIOS configurations and protect against SMM attacks Byte Offset 0 4 Table 1. Windows SMM Security Mitigations Table ACPI Standard Header

Virtualization Based Security (VBS) To help mitigate vulnerabilities that happen at UEFI runtime such as updating the capsule or setting variables, we are requiring the following: Implement key UEFI 2. 6 EFI_MEMORY_ATTRIBUTES_TABLE for EFI_MEMORY_RO and EFI_MEMORY_XP No entries may be left with neither of the above attributes, indicating memory that is both executable and writable. Memory must be either readable and executable or writeable and non-executable www. uefi. org/sites/default/files/resources/UEFI%20 Spec%202_6. pdf

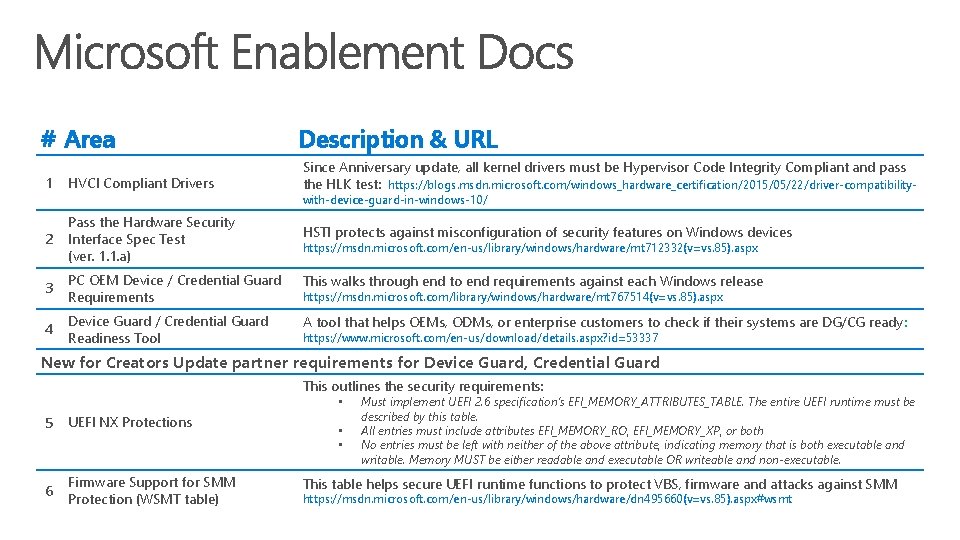
# Area Description & URL 1 HVCI Compliant Drivers Since Anniversary update, all kernel drivers must be Hypervisor Code Integrity Compliant and pass the HLK test: https: //blogs. msdn. microsoft. com/windows_hardware_certification/2015/05/22/driver-compatibility- 2 Pass the Hardware Security Interface Spec Test (ver. 1. 1. a) 3 PC OEM Device / Credential Guard Requirements This walks through end to end requirements against each Windows release 4 Device Guard / Credential Guard Readiness Tool A tool that helps OEMs, ODMs, or enterprise customers to check if their systems are DG/CG ready: with-device-guard-in-windows-10/ HSTI protects against misconfiguration of security features on Windows devices https: //msdn. microsoft. com/en-us/library/windows/hardware/mt 712332(v=vs. 85). aspx https: //msdn. microsoft. com/library/windows/hardware/mt 767514(v=vs. 85). aspx https: //www. microsoft. com/en-us/download/details. aspx? id=53337 New for Creators Update partner requirements for Device Guard, Credential Guard This outlines the security requirements: • 5 UEFI NX Protections 6 Firmware Support for SMM Protection (WSMT table) • • Must implement UEFI 2. 6 specification’s EFI_MEMORY_ATTRIBUTES_TABLE. The entire UEFI runtime must be described by this table. All entries must include attributes EFI_MEMORY_RO, EFI_MEMORY_XP, or both No entries must be left with neither of the above attribute, indicating memory that is both executable and writable. Memory MUST be either readable and executable OR writeable and non-executable. This table helps secure UEFI runtime functions to protect VBS, firmware and attacks against SMM https: //msdn. microsoft. com/en-us/library/windows/hardware/dn 495660(v=vs. 85). aspx#wsmt


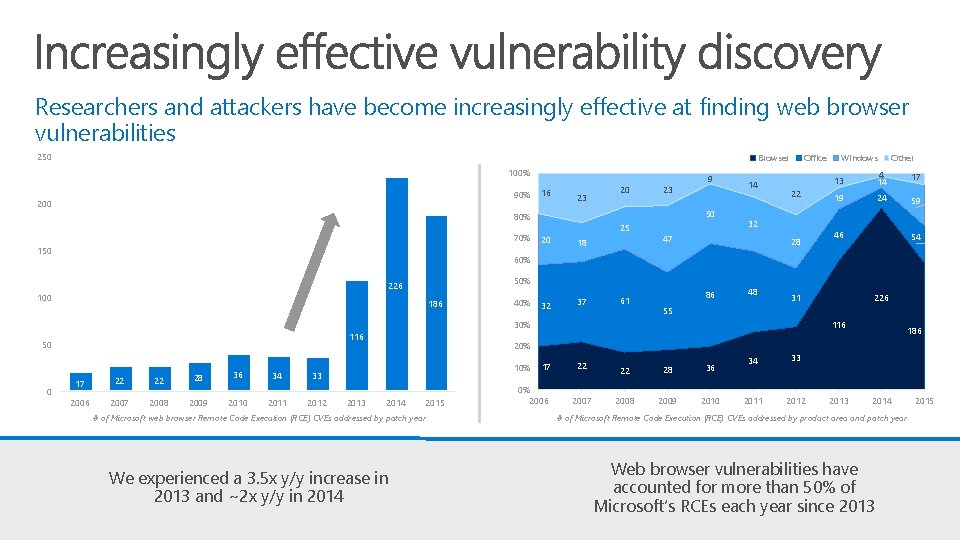
Researchers and attackers have become increasingly effective at finding web browser vulnerabilities 250 Browser 100% 90% 200 16 23 150 23 50 80% 70% 20 9 25 20 18 32 37 14 Office 22 32 47 28 Other 13 4 14 17 19 24 59 46 54 60% 50% 226 100 186 40% 61 86 48 31 116 50 17 22 22 28 36 34 33 2006 2007 2008 2009 2010 2011 2012 2013 116 20% 10% 2014 2015 # of Microsoft web browser Remote Code Execution (RCE) CVEs addressed by patch year We experienced a 3. 5 x y/y increase in 2013 and ~2 x y/y in 2014 226 55 30% 0 Windows 17 0% 2006 22 2007 22 28 36 2008 2009 2010 34 33 2011 2012 2013 186 2014 # of Microsoft Remote Code Execution (RCE) CVEs addressed by product area and patch year Web browser vulnerabilities have accounted for more than 50% of Microsoft’s RCEs each year since 2013 2015

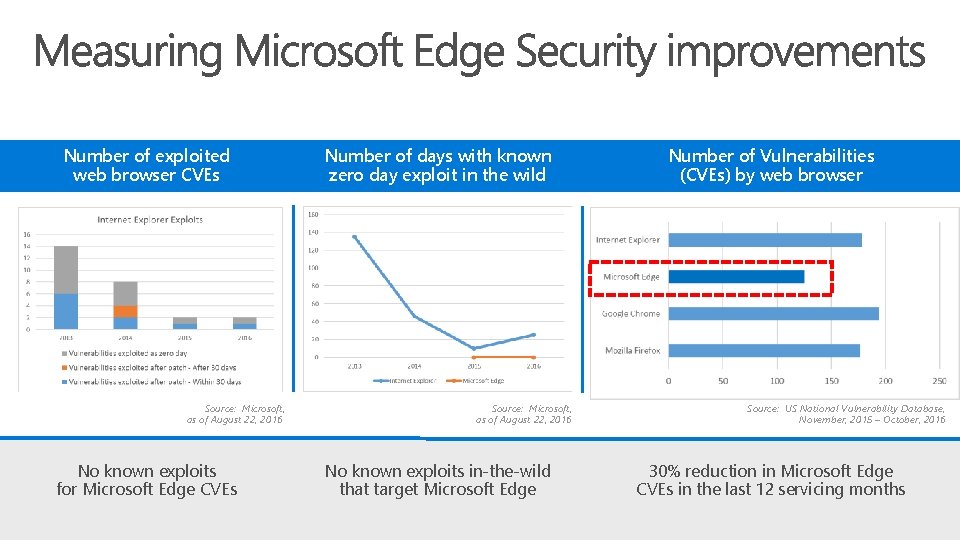
Number of exploited web browser CVEs Source: Microsoft, as of August 22, 2016 No known exploits for Microsoft Edge CVEs Number of days with known zero day exploit in the wild Source: Microsoft, as of August 22, 2016 No known exploits in-the-wild that target Microsoft Edge Number of Vulnerabilities (CVEs) by web browser Source: US National Vulnerability Database, November, 2015 – October, 2016 30% reduction in Microsoft Edge CVEs in the last 12 servicing months

Our goal: Match the industry, and balance customer experience and adjust as warranted by changes in technology. Today February 14, 2017 http: //aka. ms/sha 1


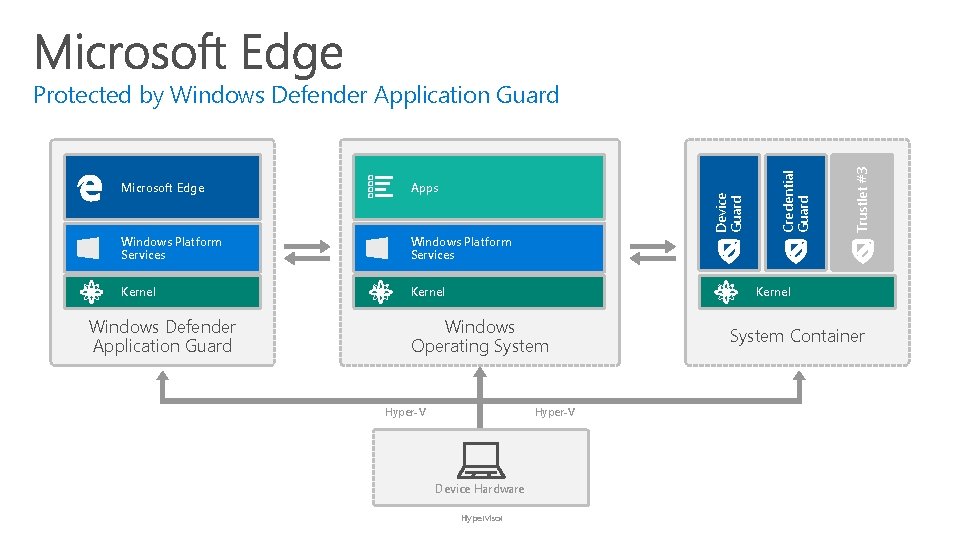
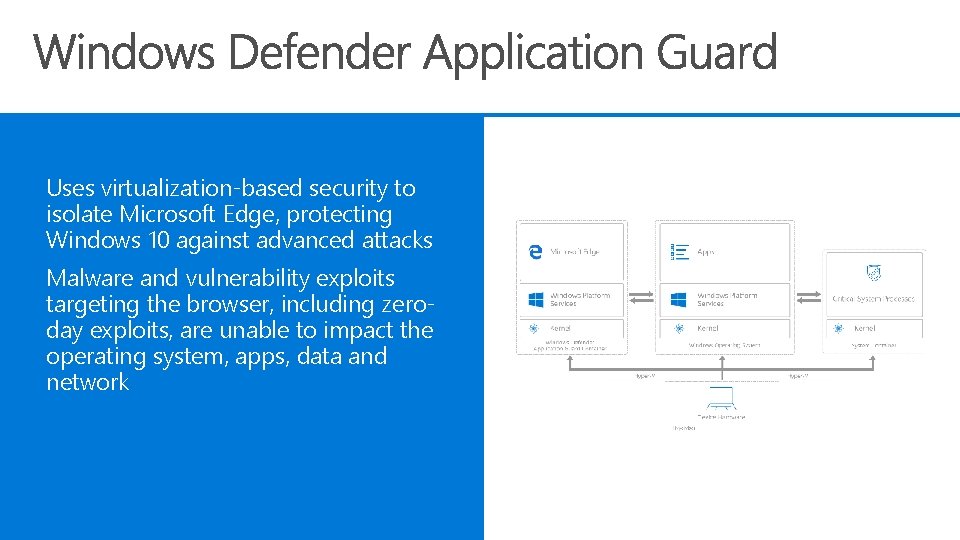
Uses virtualization-based security to isolate Microsoft Edge, protecting Windows 10 against advanced attacks Malware and vulnerability exploits targeting the browser, including zeroday exploits, are unable to impact the operating system, apps, data and network


As a partner for Microsoft, are you running Windows 10 today? If not, join the club now!

3 K 2 K 600 Top apps being tested with every release across consumers, gamers and information worker categories Number of devices and peripherals tested Engagement with hardware and software partners to detect and resolve compat issues 99% Millions 20 K %age of millions of apps inferred as compatible from Windows telemetry Windows Insiders validating early Windows builds Number of user feedback processed for detecting compat issues

Windows upgrade analytics Opt-in feedback from Windows 7 and 8. 1 Track upgrade readiness Identify app and driver issues Remediate Drive deployment Sign up via http: //www. microsoft. com/enus/Windows. For. Business/upgrade-analytics

Ready for Windows makes it easy for ISVs to list their software solutions that support Windows 10 and generate market visibility. It also give access to the Windows as a Service compatible logo program. The Microsoft Ready for Windows program helps IT decision makers search and source business applications that are compatible and supported on Windows 10.

Global reach and exposure App data from commercial Windows 10 installs ISV support declaration for Waa. S Windows 10 compatible logo for Windows as a Service App Status Guidance Adopted This application has been installed on at least 10, 000 commercial Windows 10 devices. Highly adopted This application has been installed on at least 100, 000 commercial Windows 10 devices. Supported version available The ISV has declared support for a version of this application on Windows 10. Contact software provider There may be compatibility issues with this solution, and thus Microsoft recommends contacting the software provider to learn more.

What can you do? https: //www. microsoft. com/enus/Windows. For. Business/upgrade-analytics https: //technet. microsoft. com/itpro/windows/deploy/mana ge-windows-upgrades-with-upgrade-analytics https: //developer. microsoft. com/en-us/windows/ready-forwindows#/



�� Please follow Win. HEC @ Win. HEC. com