The Model of Digital Signature Signers secret key



































- Slides: 39


















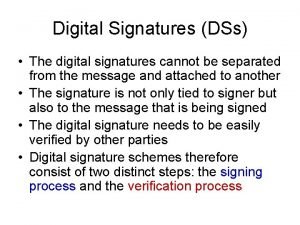
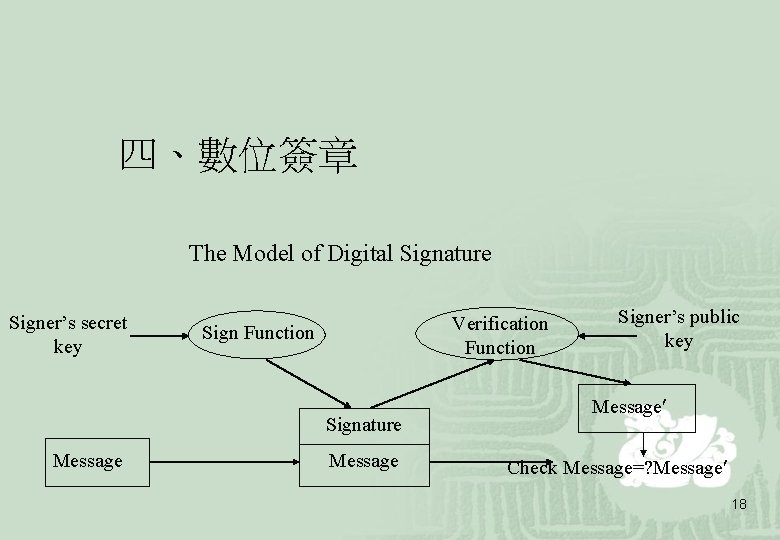
四、數位簽章 The Model of Digital Signature Signer’s secret key Verification Function Signature Message Signer’s public key Message Check Message=? Message 18

RSA Public Key Cryptosystem and Digital Signature Scheme q RSA Digital Signature Scheme v Sign Function: Signature S=Md mod N. v Verification Function: M=Se mod N. q Example 1. P=11, Q=13, N=143, and (143)=120. 2. e=103, then d=7 (for 103× 7 mod 120=1 ). 3. Sign for M=3: S=37 mod 143=42. 4. Verification: M= Se mod N = 42103 mod 143=3. 19

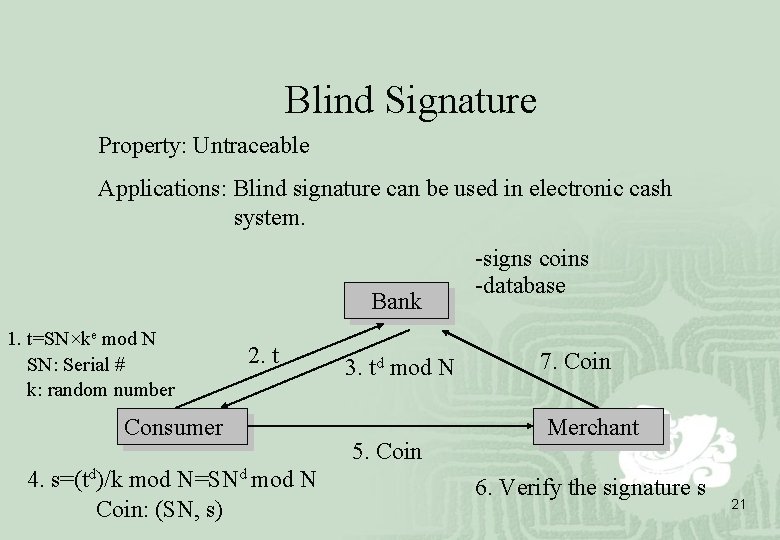
Blind Signature q D. Chaum proposed in 1983 q D. Chaum’s Blind Signature Scheme ◆ It uses the RSA algorithm. Security Basis: Factorization Problem ◆ Construction: Bob has a public key, e, a private key, d, and a public modulus, N. Alice wants Bob to sign message M blindly. 1. Alice chooses a random integer k between 1 and N. Then she blinds M by computing t = Mke mod N. 2. Bob signs t, td=(Mke)d mod N. 3. Alice unblinds td by computing s=td/k mod N = Md mod N. s is the signature of message M. 20

Blind Signature Property: Untraceable Applications: Blind signature can be used in electronic cash system. Bank 1. t=SN×ke mod N SN: Serial # k: random number 2. t Consumer 4. s=(td)/k mod N=SNd mod N Coin: (SN, s) 3. td mod N 5. Coin -signs coins -database 7. Coin Merchant 6. Verify the signature s 21




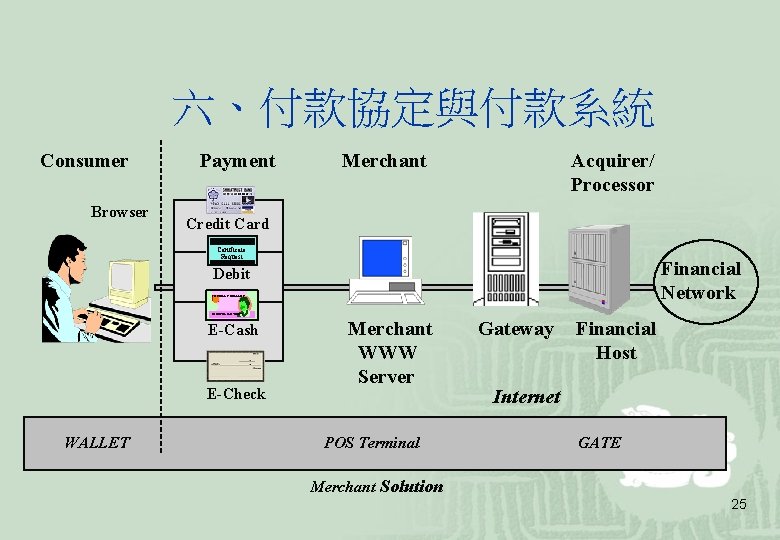
六、付款協定與付款系統 Consumer Browser Payment Merchant Acquirer/ Processor Credit Card Certificate Request Financial Network Debit 1 OF BILL’S DOLLARS IN EXCEL WE TRUST E-Cash E-Check WALLET Merchant WWW Server POS Terminal Gateway Financial Host Internet GATE Merchant Solution 25








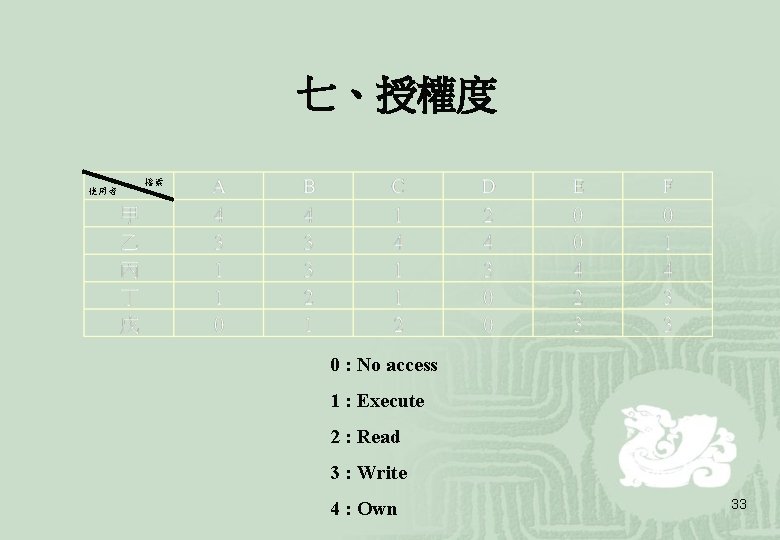
七、授權度 使用者 檔案 0 : No access 1 : Execute 2 : Read 3 : Write 4 : Own 33




九、結論 ¡ 10 Commandments of Commercial Security Today Don’t aim for perfect security. So, be realistic, and do the best you can within your limits. Roughly, you should double security expenditure to halve risk. Don’t solve the wrong problem. For example, note that US banks lose 10 billion dollars a year in check fraud but only 5 million in online 37

九、結論 Don’t sell security bottom-up ( in terms of the personnel hierarchy). Don’t use cryptographic overkill. Even bad crypto is usually the strong part of the system. Don’t make it complicated. This yields more places to attack the system, and it encourages users to find ways to bypass security. Don’t make it expensive. 38

九、結論 Don’t use a single line of defense. Have several layers so security can be maintained without expensive replacement of the primary line. Don’t forget the “mystery attack”. Be able to regenerate security even when you have no idea what’s going wrong. For example, smart cards are attackable but are great for quick cheap recovery. Don’t trust systems. Don’t trust people. 39
 No talking signs
No talking signs A digital signature needs a private key system
A digital signature needs a private key system Dsa
Dsa Java for pfms
Java for pfms Approaches to message authentication
Approaches to message authentication Diffie hellman signature
Diffie hellman signature Properties of digital signature
Properties of digital signature Rsa digital signature
Rsa digital signature Digital signature
Digital signature Digital signature authentication protocol
Digital signature authentication protocol Dsa in network security
Dsa in network security Digital signature authentication protocol
Digital signature authentication protocol Digital signature forgery
Digital signature forgery Dss digital signature
Dss digital signature Digital certificate example
Digital certificate example Digital signature algorithm
Digital signature algorithm Digital signature crossword
Digital signature crossword Irreusable
Irreusable Digital signature authentication protocol
Digital signature authentication protocol Simple secret key distribution
Simple secret key distribution Key management issues
Key management issues Simple secret key distribution
Simple secret key distribution Cryptography
Cryptography Determining key signature
Determining key signature Rsa public-key encryption and signature lab
Rsa public-key encryption and signature lab 15 key signatures
15 key signatures Key evolving signature
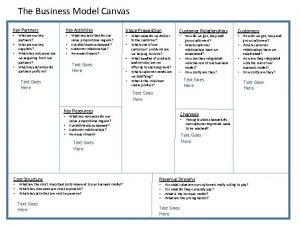
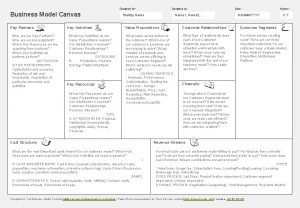
Key evolving signature Example of business model canvas
Example of business model canvas Key partners key activities key resources
Key partners key activities key resources Hát kết hợp bộ gõ cơ thể
Hát kết hợp bộ gõ cơ thể Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Gấu đi như thế nào
Gấu đi như thế nào Tư thế worms-breton
Tư thế worms-breton Chúa sống lại
Chúa sống lại Các môn thể thao bắt đầu bằng tiếng bóng
Các môn thể thao bắt đầu bằng tiếng bóng Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Cong thức tính động năng
Cong thức tính động năng