Digital Signature Cryptography Digital signature Digital signature means
































- Slides: 44

Digital Signature Cryptography

Digital signature • ‘Digital signature’ means authentication of any electronic record by means of an electronic method or procedure in accordance with the provisions of Section 3 • Electronic record means data, record or data generated, image or sound, received or sent in an electronic form or microfilm or computer generated fiche • Digital Signature Certificate to be issued by Certifying Authority • Asymmetric Crypto System and hash functions details - as prescribed

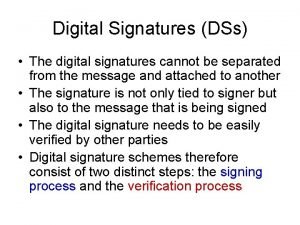
Digital Signature Basically a digital signature is a two way process, involving two parties: • The signer (creator of the digital signature) and • The recipient (verifier of the digital signature). A digital signature is complete, if and only if, the recipient successfully verifies it.

Need for Digital Signature It has been realized that Internet being a public network would never be secure enough and there would always be a fear of interception, transmission errors, delays, deletion, authenticity or verification of an electronic message using Internet as a medium. Hence the goal was to protect the message, not the medium.

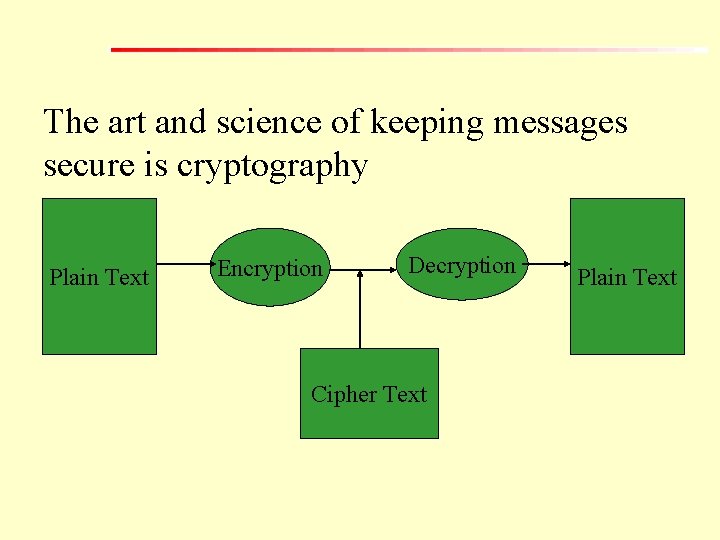
The art and science of keeping messages secure is cryptography Plain Text Encryption Decryption Cipher Text Plain Text

• Symmetric Cryptography • Asymmetric Cryptography

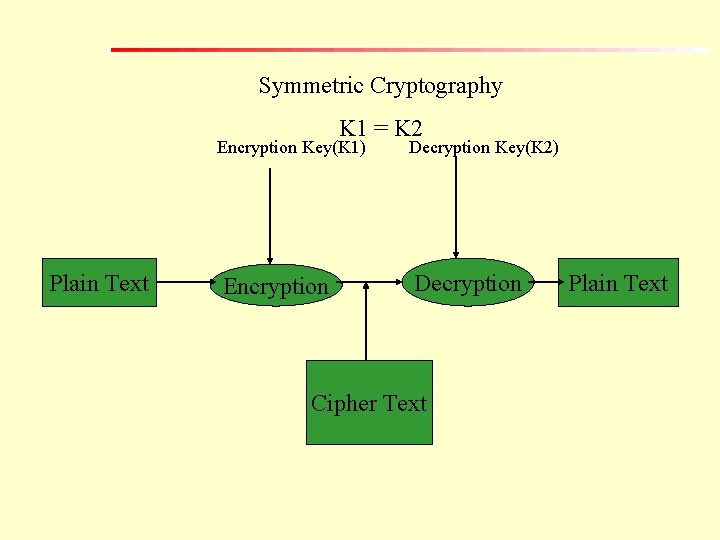
Symmetric Cryptography When a single secret key is used to maintain communication between the sender and the receiver, it is referred to as a symmetric cryptography or private-key cryptographic system. Here, both encryption and decryption use the same key.

Symmetric Cryptography K 1 = K 2 Encryption Key(K 1) Plain Text Encryption Decryption Key(K 2) Decryption Cipher Text Plain Text

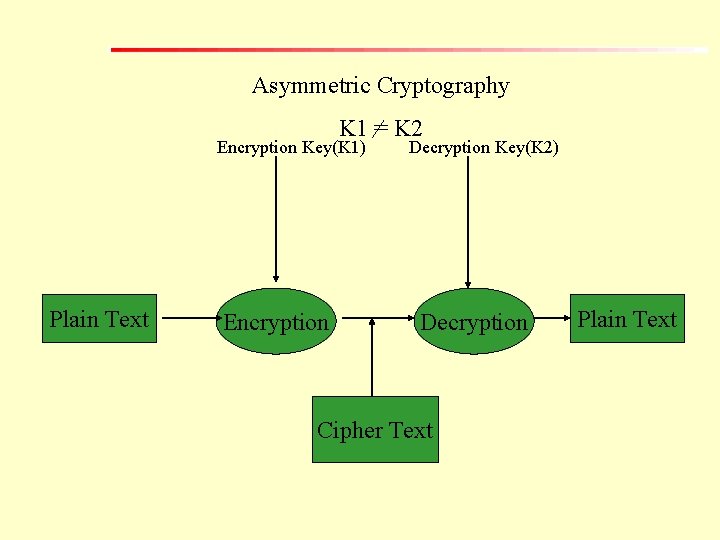
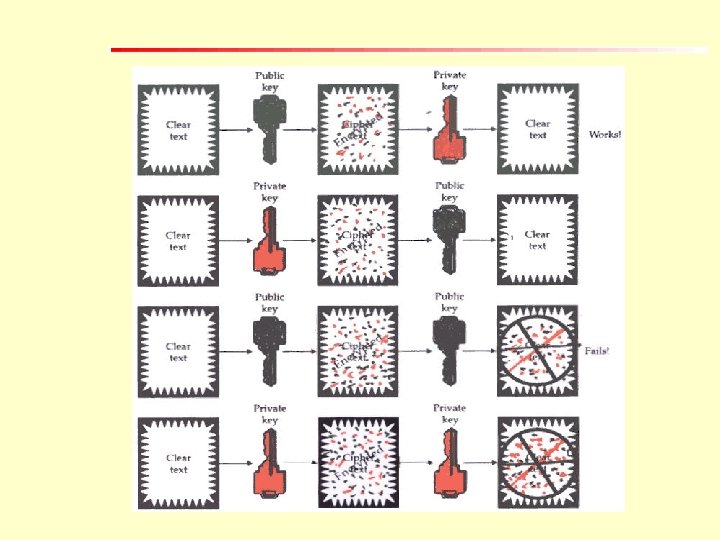
Asymmetric Cryptography For both the processes of encryption and decryption two different keys are used. It is referred to as a asymmetric cryptography or public-key cryptographic system.

Asymmetric Cryptography K 1 = K 2 Encryption Key(K 1) Plain Text Encryption Decryption Key(K 2) Decryption Cipher Text Plain Text

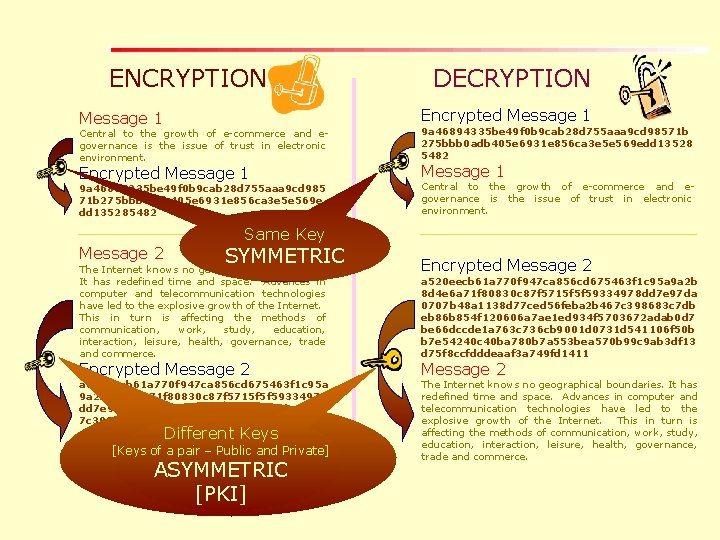
ENCRYPTION DECRYPTION Message 1 Encrypted Message 1 Central to the growth of e-commerce and egovernance is the issue of trust in electronic environment. 9 a 46894335 be 49 f 0 b 9 cab 28 d 755 aaa 9 cd 98571 b 275 bbb 0 adb 405 e 6931 e 856 ca 3 e 5 e 569 edd 13528 5482 9 a 46894335 be 49 f 0 b 9 cab 28 d 755 aaa 9 cd 985 71 b 275 bbb 0 adb 405 e 6931 e 856 ca 3 e 5 e 569 e dd 135285482 Central to the growth of e-commerce and egovernance is the issue of trust in electronic environment. Message 2 Same Key SYMMETRIC The Internet knows no geographical boundaries. It has redefined time and space. Advances in computer and telecommunication technologies have led to the explosive growth of the Internet. This in turn is affecting the methods of communication, work, study, education, interaction, leisure, health, governance, trade and commerce. Encrypted Message 2 a 520 eecb 61 a 770 f 947 ca 856 cd 675463 f 1 c 95 a 9 a 2 b 8 d 4 e 6 a 71 f 80830 c 87 f 5715 f 5 f 59334978 dd 7 e 97 da 0707 b 48 a 1138 d 77 ced 56 feba 2 b 46 7 c 398683 c 7 dbeb 86 b 854 f 120606 a 7 ae 1 ed 93 4 f 5703672 adab 0 d 7 be 66 dccde 1 a 763 c 736 cb 9001 d 0731 d 541106 f 50 bb 7 e 54240 c 40 ba 78 [Keys of a pair – Public and Private] 0 b 7 a 553 bea 570 b 99 c 9 ab 3 df 13 d 75 f 8 ccfddde aaf 3 a 749 fd 1411 Different Keys ASYMMETRIC [PKI] Encrypted Message 2 a 520 eecb 61 a 770 f 947 ca 856 cd 675463 f 1 c 95 a 9 a 2 b 8 d 4 e 6 a 71 f 80830 c 87 f 5715 f 5 f 59334978 dd 7 e 97 da 0707 b 48 a 1138 d 77 ced 56 feba 2 b 467 c 398683 c 7 db eb 86 b 854 f 120606 a 7 ae 1 ed 934 f 5703672 adab 0 d 7 be 66 dccde 1 a 763 c 736 cb 9001 d 0731 d 541106 f 50 b b 7 e 54240 c 40 ba 780 b 7 a 553 bea 570 b 99 c 9 ab 3 df 13 d 75 f 8 ccfdddeaaf 3 a 749 fd 1411 Message 2 The Internet knows no geographical boundaries. It has redefined time and space. Advances in computer and telecommunication technologies have led to the explosive growth of the Internet. This in turn is affecting the methods of communication, work, study, education, interaction, leisure, health, governance, trade and commerce.


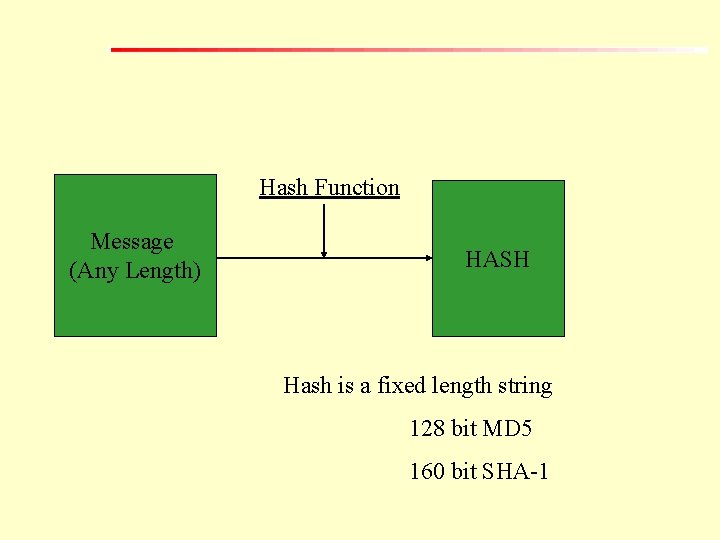
Hash Function [compression function, contraction function, message digest, finger print, cryptographic checksum, message integrity check, and manipulation detection code ] A Hash Function is a mathematical algorithm that takes a variable length input string and convert it to a fixed length output string [ called hash value]

Hash Function Message (Any Length) HASH Hash is a fixed length string 128 bit MD 5 160 bit SHA-1

Digital Signature

Basically a digital signature is a two way process, involving two parties: – The signer (creator of the digital signature) and – The recipient (verifier of the digital signature). A digital signature is complete, if and only if, the recipient successfully verifies it.

Concept of Digital Signatures Scanned but not Digital Signatures bab 3 dbfba 30 eedc 0 c 52 dacfc 144 df 4 d 9 c 6508502

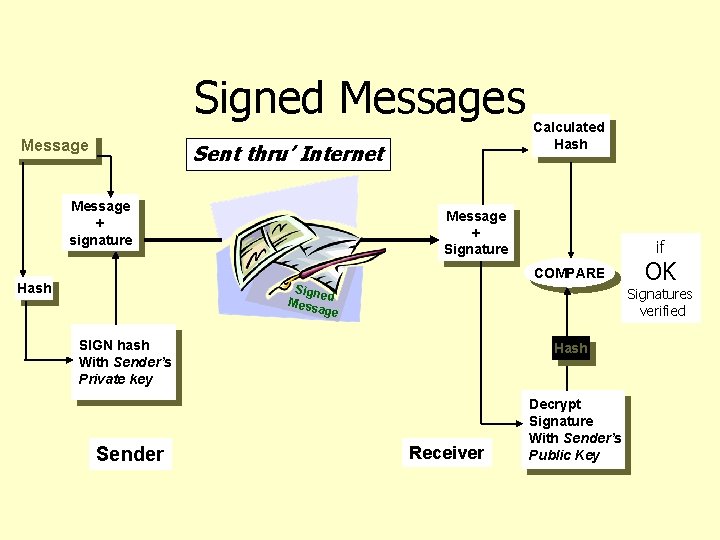
Signed Messages Message Sent thru’ Internet Message + signature Calculated Hash Message + Signature if COMPARE Hash Signe Mess d age Signatures verified SIGN hash With Sender’s Private key Sender OK Hash Receiver Decrypt Signature With Sender’s Public Key

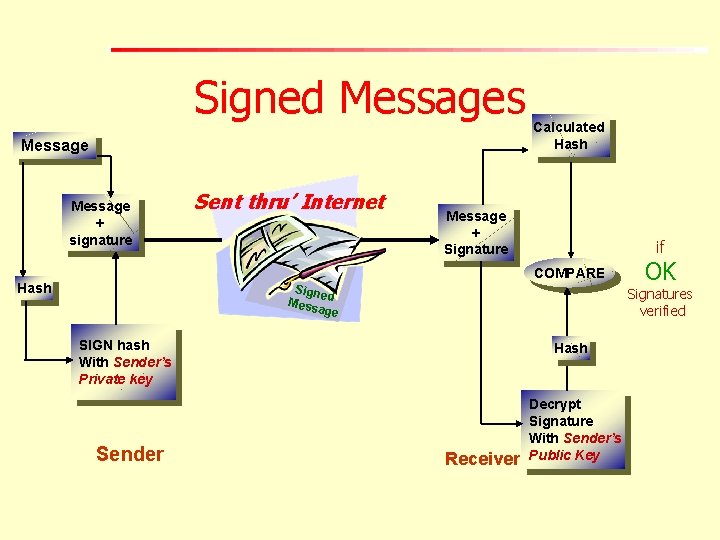
Signed Messages Message + signature Sent thru’ Internet Calculated Hash Message + Signature if COMPARE Hash Signe Mess d age Signatures verified SIGN hash With Sender’s Private key Sender OK Hash Receiver Decrypt Signature With Sender’s Public Key

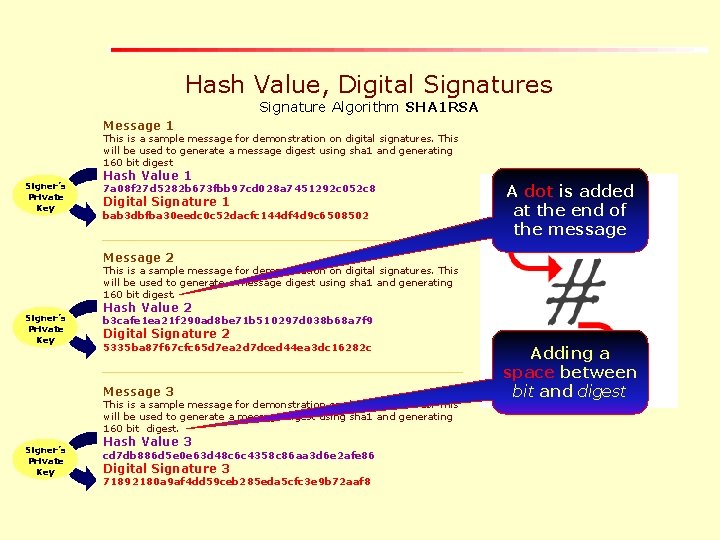
Hash Value, Digital Signatures Signature Algorithm SHA 1 RSA Message 1 This is a sample message for demonstration on digital signatures. This will be used to generate a message digest using sha 1 and generating 160 bit digest Signer’s Private Key Hash Value 1 7 a 08 f 27 d 5282 b 673 fbb 97 cd 028 a 7451292 c 052 c 8 Digital Signature 1 bab 3 dbfba 30 eedc 0 c 52 dacfc 144 df 4 d 9 c 6508502 A dot is added at the end of the message Message 2 This is a sample message for demonstration on digital signatures. This will be used to generate a message digest using sha 1 and generating 160 bit digest. Signer’s Private Key Hash Value 2 b 3 cafe 1 ea 21 f 290 ad 8 be 71 b 510297 d 038 b 68 a 7 f 9 Digital Signature 2 5335 ba 87 f 67 cfc 65 d 7 ea 2 d 7 dced 44 ea 3 dc 16282 c Message 3 This is a sample message for demonstration on digital signatures. This will be used to generate a message digest using sha 1 and generating 160 bit digest. Signer’s Private Key Hash Value 3 cd 7 db 886 d 5 e 0 e 63 d 48 c 6 c 4358 c 86 aa 3 d 6 e 2 afe 86 Digital Signature 3 71892180 a 9 af 4 dd 59 ceb 285 eda 5 cfc 3 e 9 b 72 aaf 8 Adding a space between bit and digest

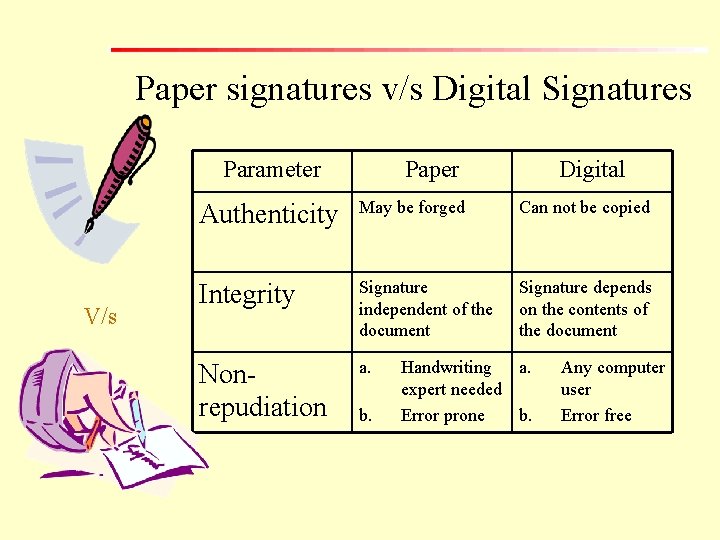
Paper signatures v/s Digital Signatures Parameter V/s Paper Digital Authenticity May be forged Can not be copied Integrity Signature independent of the document Signature depends on the contents of the document Nonrepudiation a. b. Handwriting a. expert needed Error prone b. Any computer user Error free

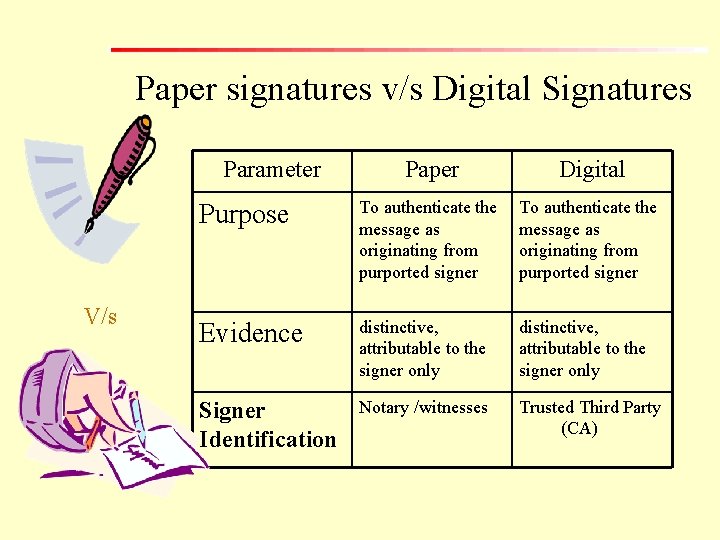
Paper signatures v/s Digital Signatures Parameter V/s Paper Digital Purpose To authenticate the message as originating from purported signer Evidence distinctive, attributable to the signer only Signer Identification Notary /witnesses Trusted Third Party (CA)

Digital signatures are based on asymmetric, or public key, cryptography and are capable of fulfilling the demand of burgeoning ecommerce by not only providing message authentication, integrity and non-repudiation function but also making it highly scalable.

The basic problem with the aforesaid digital signature regime is that it operates in online, software driven space, without human intervention. Sender sends a digitally signed message; recipient receives and verifies it. The only requirement is that both sender and the recipient to have digital signature software at their respective ends.

Law & E-Governance

Primary Legal Issues Surrounding E-Governance • Adopting a functional equivalent approach • Facilitating efficient Government-Citizen interface. • The focus is to give due legal recognition to digital signatures and electronic records.

Legal Recognition of Electronic Records and Digital Signatures • Legal recognition to electronic records and digital signatures. [Section 4& 5]. • Use of electronic records and digital signatures in government and its agencies for filing, issue, grant, receipt or payment of money [Section 6]. • Electronic records or information, whenever retained, as required by law must be retained in the format in which it was originally generated, sent or received[Section 7].

Publication of Electronic Gazette The IT Act provides that the rule, regulation, order, bye-law, notification or any other matter could now also be published in the Electronic Gazette apart from the Official Gazette [Section 8].

Limited Electronic Governance Rights It does not confer a right upon any person to insist that any Ministry or Department of the Central or State government (or any authority or body) to accept, issue, create, retain or preserve any document in the form of electronic records or to participate in any monetary transaction in the electronic form[Section 9].

Issue of Privacy

“Privacy is where technology and the law collide. ” - Richard Smith (who traced the ‘I Love You’ and ‘Melissa viruses’)

Internet is not a private network. It is a sharedinformation network. As and when you log onto the Internet and navigate on the World Wide Web, your digital profile is being created. The same technology that makes it easy for you to find what you want when you want on the Internet also makes it easy for others to learn about you.

Though the Constitution of India has not guaranteed the right to privacy as a fundamental right to the citizens but nevertheless, the Supreme Court has come to the rescue of common citizen, time and again by construing “right to privacy” as a part of the right to “ protection of life and personal liberty”.

Privacy: Three Legal Principles

• That the individual’s right to privacy exist and any unlawful invasion of privacy would make the ‘offender’ liable for the consequences in accordance with law; • That there is constitutional recognition given to the right of privacy which protects personal privacy against unlawful governmental invasion; • That the person’s “right to be let alone” is not an absolute right and may be lawfully restricted for the prevention of crime, disorder or protection of health or morals or protection of rights and freedom of others;

Freedom of Expression

Freedom of Expression The Indian Constitution lays down under Article 19 certain fundamental rights to every citizen. The Art. 19 uses the expression ‘freedom’ and mentions the several forms and aspects of it, which are secured to individuals, together with the limitations that could be, placed upon them in the general interest of the society.

Art. 19(1)(a) provides “that all the citizens shall have the right to freedom of speech and expression”. But it should be read with sub-Art. (2), which imposes reasonable restrictions imposed by the State relating to 1. 2. 3. 4. 5. 6. 7. 8. defamation; contempt of court; decency or morality; security of the State; friendly relations with foreign states; incitement to an offence; public order; and maintenance of the sovereignty and integrity of India.

Thus fundamental right to freedom of speech and expression extends to the Internet medium as well. Every citizen has a freedom to acquire or share kowledge (or information) using Internet and related resources, subject only to reasonable restrictions.

Role of CERT-IN Computer Emergency Response Team – India, the single authority for issue of instructions in the context of blocking of websites. CERT-IN has to instruct the Do. T to block the website after, 1. Verifying the authenticity of the complaint; 2. Satisfying that action of blocking of website is absolutely essential.

CERT-IN [Gazette Notification (Extraordinary) No. G. S. R. 181 (E), dated 27 th February, 2003]is based on the premise that such blocking can be challanged if it amounts to restriction of freedom of speech and expression.

However, the websites promoting hate content, slander, or defamation of others, promoting gambling, promoting racism, violence and terrorism and other such material, in addition to promoting pornography, including child pornography, and violent sex can reasonably be blocked since all such websites may not claim constitutional right of free speech. Blocking of such websites may be equated to “balanced flow of information” and not censorship.

The following officers can submit the complaint to the Director, CERT-IN: • Secretary, National Security Council Secretariat • Secretary, Ministry of Home Affairs • Foreign Secretary or a representative not below the rank of Joint Secretary • Secretaries, Dept. of Home Affairs of each of the States and of the Union Territories • CBI, IB, DG of Police of all the States • Secretaries or Heads of all (IT Departments) of all the States and Union Territories not below the rank of Joint Secretary of Central Government • Chairman of NHRC, Minorities Commission or SC or ST Commission or National Women Commission • The directive of the court

“The law is the last interpretation of the law given by the last judge. ” - Anon.
 Dsa in network security
Dsa in network security Cryptography basics
Cryptography basics Triangle quadrilateral pentagon hexagon octagon
Triangle quadrilateral pentagon hexagon octagon Metamorphic rocks
Metamorphic rocks Meta means change and morph means heat
Meta means change and morph means heat Definition of biodiversity conservation
Definition of biodiversity conservation Life bio
Life bio A digital signature needs a private key system
A digital signature needs a private key system Rsa digital signature
Rsa digital signature Pfms digital signature
Pfms digital signature Code c
Code c Diffie hellman digital signature
Diffie hellman digital signature Properties of digital signature
Properties of digital signature Rsa digital signature
Rsa digital signature Digital signature
Digital signature Digital signature authentication protocol
Digital signature authentication protocol Digital signature authentication protocol
Digital signature authentication protocol Digital signature forgery
Digital signature forgery Dss digital signature
Dss digital signature Attack on digital signature
Attack on digital signature Digital signature algorithm
Digital signature algorithm Cryptography topics crossword
Cryptography topics crossword Non-repudiation digital signature
Non-repudiation digital signature Digital signature authentication protocol
Digital signature authentication protocol New directions in cryptography
New directions in cryptography Confusion and diffusion
Confusion and diffusion Blaise de vigenere cryptography
Blaise de vigenere cryptography Principles of public key cryptosystems
Principles of public key cryptosystems Placement of encryption function
Placement of encryption function Dan boneh stanford
Dan boneh stanford Dan boneh blockchain course
Dan boneh blockchain course Wireless security in cryptography
Wireless security in cryptography 1976 new directions in cryptology
1976 new directions in cryptology Cryptography adalah
Cryptography adalah What is key management in cryptography
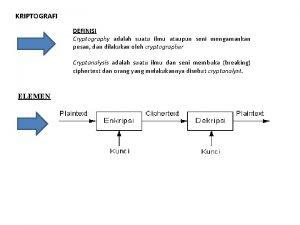
What is key management in cryptography Cryptography
Cryptography Module 06 basic cryptography
Module 06 basic cryptography Cryptography terminology
Cryptography terminology Cryptography
Cryptography Handbook of applied cryptography
Handbook of applied cryptography Cryptography board game
Cryptography board game Motivationsbasis
Motivationsbasis Cryptography vs cryptology
Cryptography vs cryptology Cryptography slides
Cryptography slides Cryptography summary
Cryptography summary