Spy Aware Investigating the Privacy Leakage Signatures in




- Slides: 22

Spy. Aware: Investigating the Privacy Leakage Signatures in App Execution Traces Hui Xu, Yangfan Zhou, Cuiyun Gao, Yu Kang, Michael R. Lyu hxu@cse. cuhk. edu. hk 1

Private Data Is Valuable Big Data Machine Learning Recommendation 2

Whether a Leakage Is Legitimate? Depends on: † User Preference † Software Functionality 3

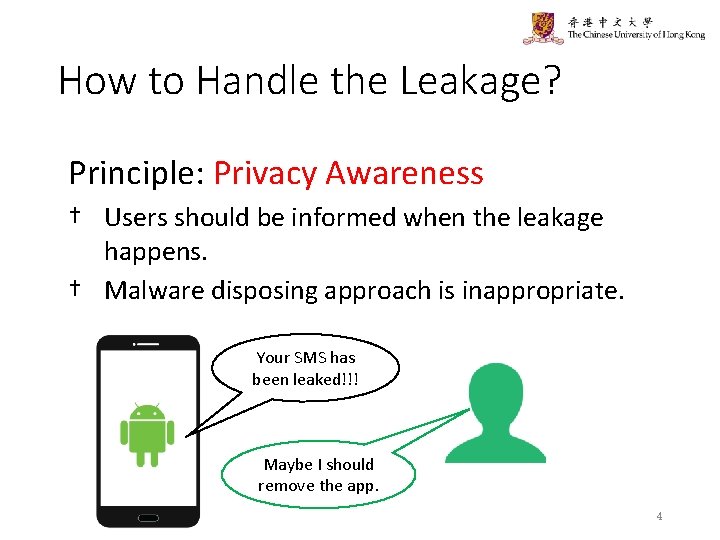
How to Handle the Leakage? Principle: Privacy Awareness † Users should be informed when the leakage happens. † Malware disposing approach is inappropriate. Your SMS has been leaked!!! Maybe I should remove the app. 4

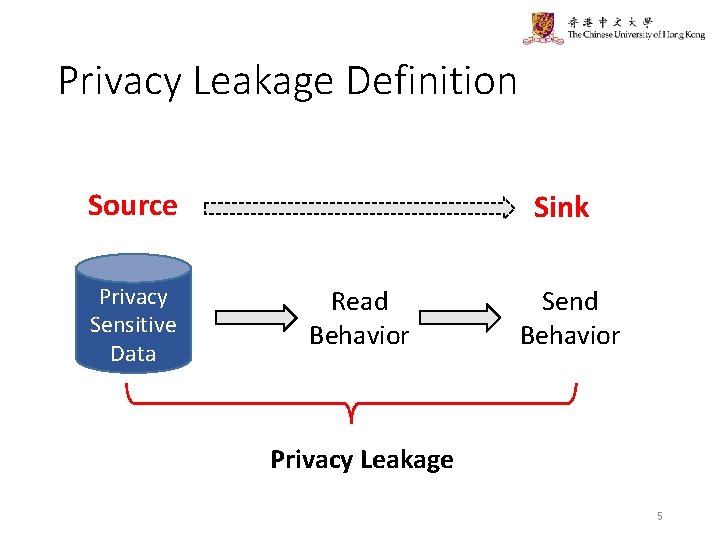
Privacy Leakage Definition Source Privacy Sensitive Data Sink Read Behavior Send Behavior Privacy Leakage 5

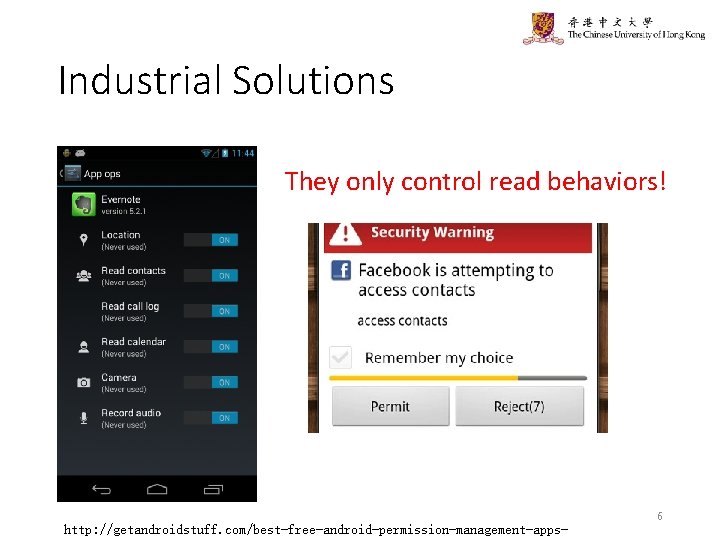
Industrial Solutions They only control read behaviors! 6 http: //getandroidstuff. com/best-free-android-permission-management-apps-

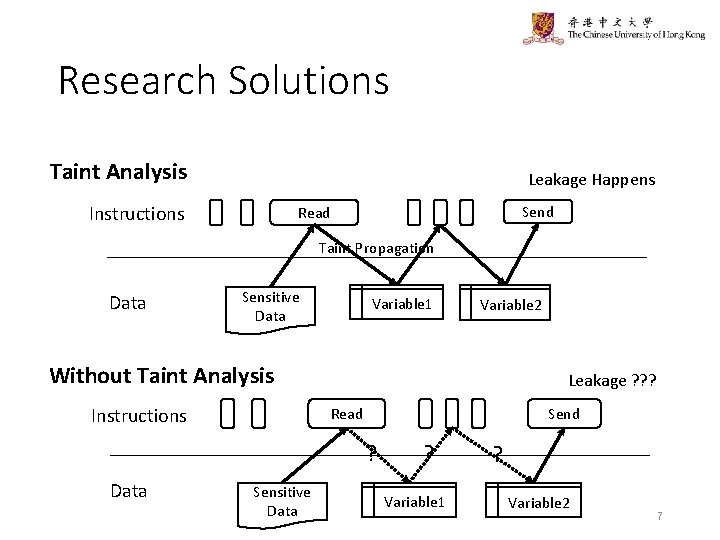
Research Solutions Taint Analysis Leakage Happens Instructions Send Read Taint Propagation Data Sensitive Data Variable 1 Variable 2 Without Taint Analysis Instructions Leakage ? ? ? Read Send ? Data Sensitive Data ? Variable 1 ? Variable 2 7

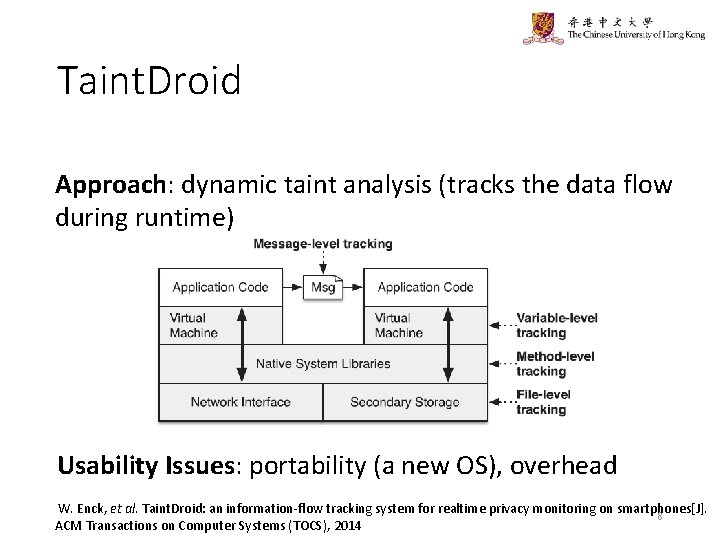
Taint. Droid Approach: dynamic taint analysis (tracks the data flow during runtime) Usability Issues: portability (a new OS), overhead W. Enck, et al. Taint. Droid: an information-flow tracking system for realtime privacy monitoring on smartphones[J]. 8 ACM Transactions on Computer Systems (TOCS), 2014

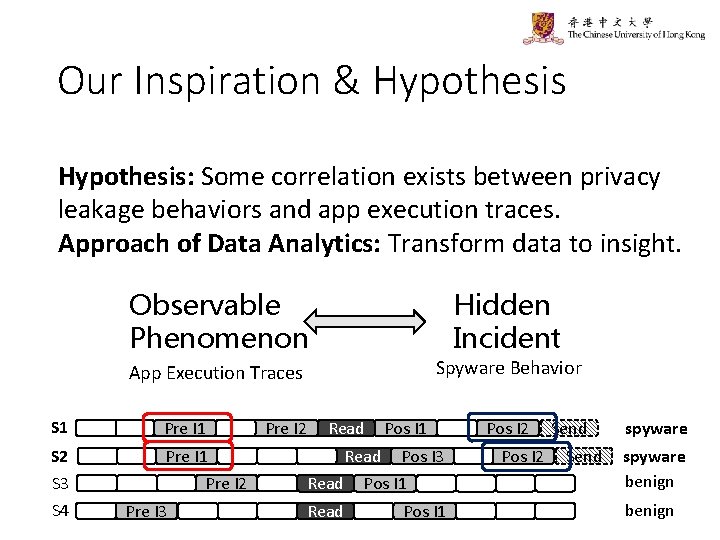
Our Inspiration & Hypothesis: Some correlation exists between privacy leakage behaviors and app execution traces. Approach of Data Analytics: Transform data to insight. Observable Phenomenon Hidden Incident Spyware Behavior App Execution Traces S 1 Pre I 1 S 2 S 3 Pre I 1 S 4 Pre I 2 Pre I 3 Pre I 2 Read Pos I 1 Pos I 3 Pos I 1 Pos I 2 Send spyware 9 benign

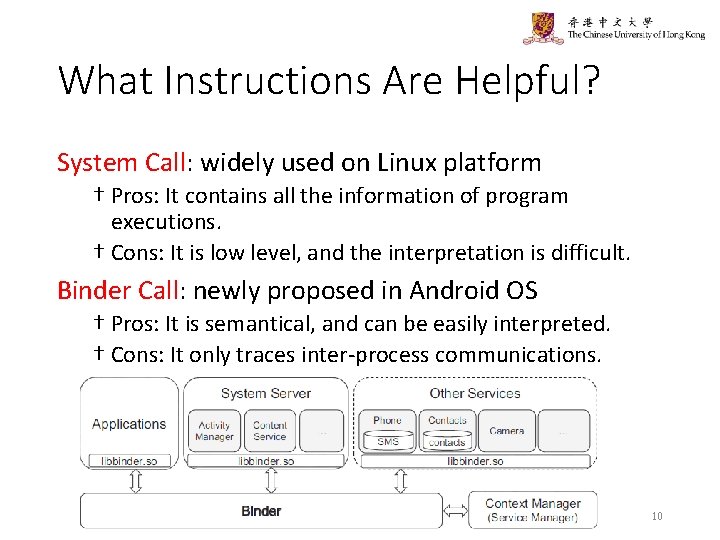
What Instructions Are Helpful? System Call: widely used on Linux platform † Pros: It contains all the information of program executions. † Cons: It is low level, and the interpretation is difficult. Binder Call: newly proposed in Android OS † Pros: It is semantical, and can be easily interpreted. † Cons: It only traces inter-process communications. 10

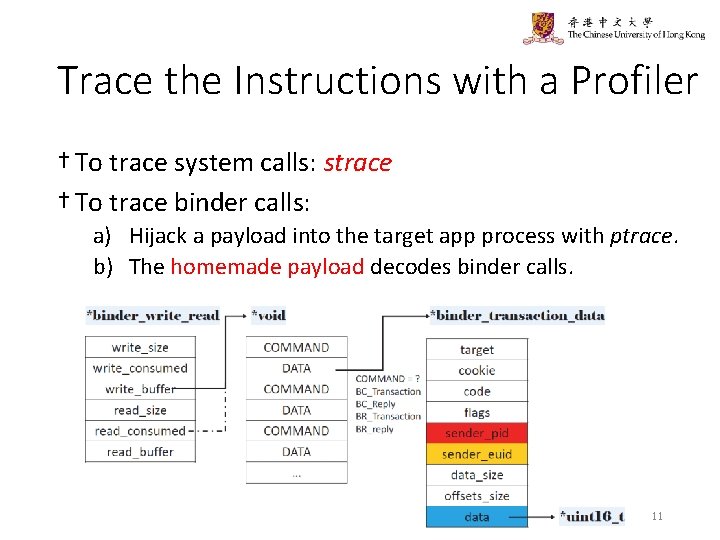
Trace the Instructions with a Profiler † To trace system calls: strace † To trace binder calls: a) Hijack a payload into the target app process with ptrace. b) The homemade payload decodes binder calls. 11

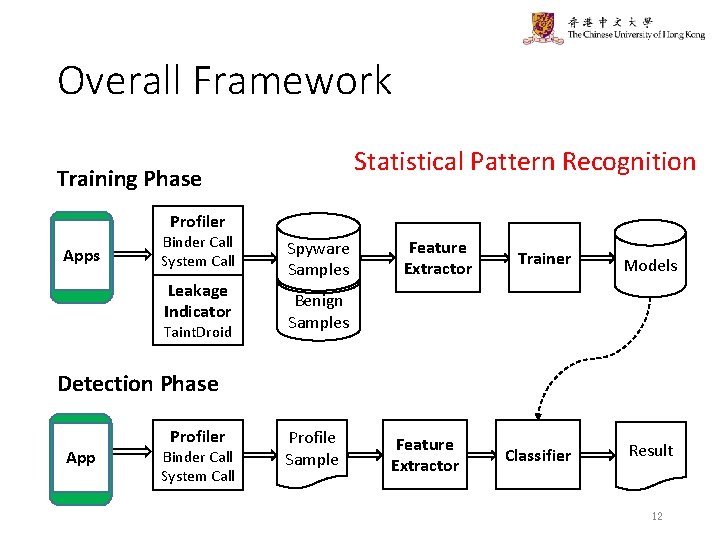
Overall Framework Statistical Pattern Recognition Training Phase Profiler Apps Binder Call System Call Leakage Indicator Taint. Droid Spyware Samples Feature Extractor Trainer Models Classifier Result Benign Samples Detection Phase App Profiler Binder Call System Call Profile Sample Feature Extractor 12

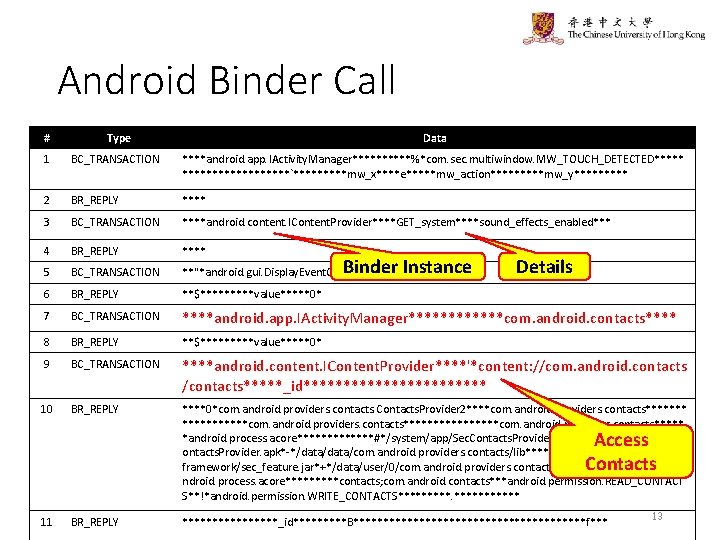
Android Binder Call # Type Data 1 BC_TRANSACTION ****android. app. IActivity. Manager*****%*com. sec. multiwindow. MW_TOUCH_DETECTED*********`*****mw_x****e*****mw_action*****mw_y***** 2 BR_REPLY **** 3 BC_TRANSACTION ****android. content. IContent. Provider****GET_system****sound_effects_enabled*** 4 BR_REPLY **** 5 BC_TRANSACTION **"*android. gui. Display. Event. Connection** 6 BR_REPLY **$*****value*****0* 7 BC_TRANSACTION ****android. app. IActivity. Manager******com. android. contacts**** 8 BR_REPLY **$*****value*****0* 9 BC_TRANSACTION ****android. content. IContent. Provider****'*content: //com. android. contacts /contacts*****_id************ 10 BR_REPLY ****0*com. android. providers. contacts. Contacts. Provider 2****com. android. providers. contacts***********com. android. providers. contacts***** *android. process. acore*******#*/system/app/Sec. Contacts. Provider. apk*#*/system/app/Sec. C ontacts. Provider. apk*-*/data/com. android. providers. contacts/lib*****!*/system/ framework/sec_feature. jar*+*/data/user/0/com. android. providers. contacts***********a ndroid. process. acore*****contacts; com. android. contacts***android. permission. READ_CONTACT S**!*android. permission. WRITE_CONTACTS****** Binder Instance Details Access Contacts 11 BR_REPLY ********_id*****B********************f*** 13

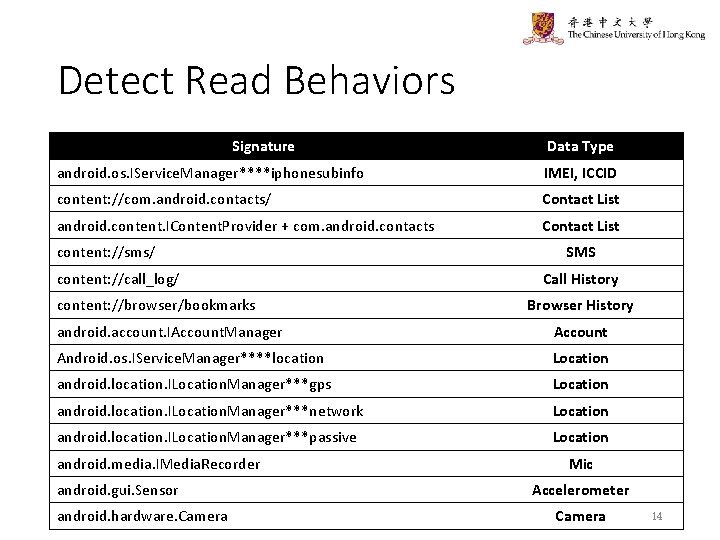
Detect Read Behaviors Signature Data Type android. os. IService. Manager****iphonesubinfo IMEI, ICCID content: //com. android. contacts/ Contact List android. content. IContent. Provider + com. android. contacts Contact List content: //sms/ content: //call_log/ content: //browser/bookmarks SMS Call History Browser History android. account. IAccount. Manager Account Android. os. IService. Manager****location Location android. location. ILocation. Manager***gps Location android. location. ILocation. Manager***network Location android. location. ILocation. Manager***passive Location android. media. IMedia. Recorder android. gui. Sensor android. hardware. Camera Mic Accelerometer Camera 14

Binder Call-based Features Approach: a) Use BR_TRANSACTION; discard BR_REPLY. b) Strip details and retain the destination instance name. c) Choose discriminative instances. †Leakage happens automatically when starting a new activity: üandroid. app. IActivity. Manager †Network communications are generally performed in a stand alone thread: üadroid. app. IApplication. Thread †Apps may check current network connection status before communication: üandroid. net. IConnectivity. Manager, android. net. wifi. IWifi. Manager †Messenger is a common method to pass event or values between threads: üandroid. os. IMessenger †Leakages may happen when an app is querying the server: 15 ücom. android. . . view. IInput. Method. Manager

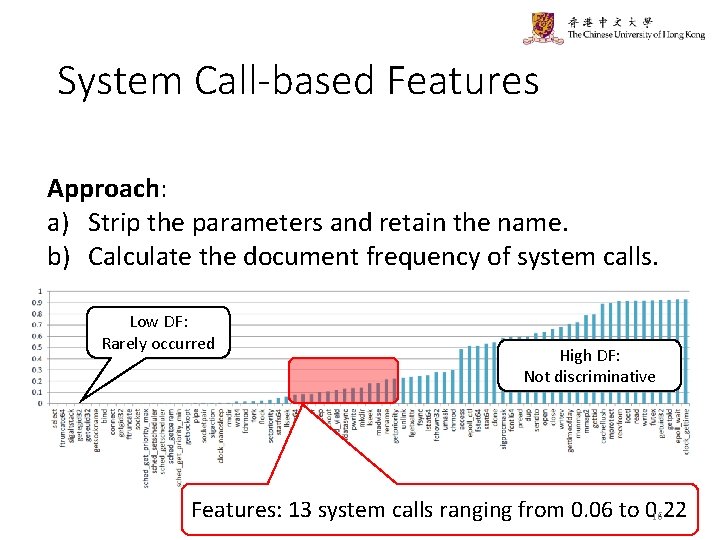
System Call-based Features Approach: a) Strip the parameters and retain the name. b) Calculate the document frequency of system calls. Low DF: Rarely occurred High DF: Not discriminative Features: 13 system calls ranging from 0. 06 to 0. 22 16

Extract Features for Each Sample Terms: † A Sample: We separate the sequence of instructions into samples according to touch operations. † A sample is a suspicious sample, if it includes at least one read behavior according to the binder call. Steps: a) Judge whether a sample is a suspicious sample. b) Discard the sample if it is nonsuspicious. c) Extract features for only suspicious ones. Reason: Android app is UI oriented. 17

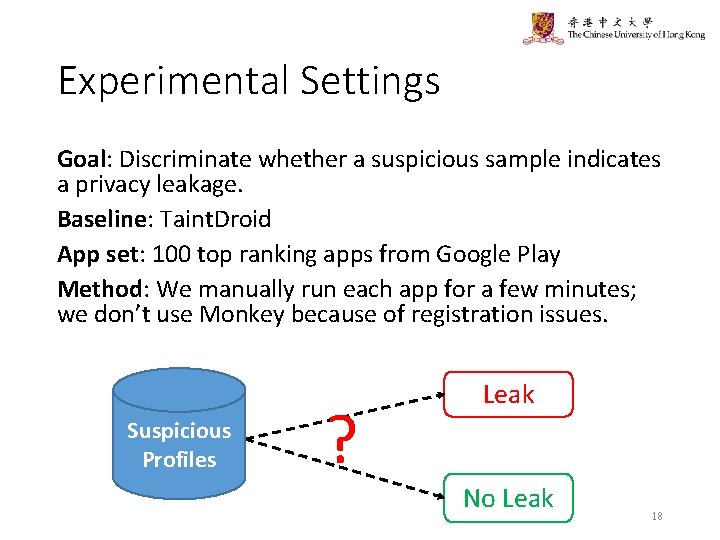
Experimental Settings Goal: Discriminate whether a suspicious sample indicates a privacy leakage. Baseline: Taint. Droid App set: 100 top ranking apps from Google Play Method: We manually run each app for a few minutes; we don’t use Monkey because of registration issues. Suspicious Profiles ? Leak No Leak 18

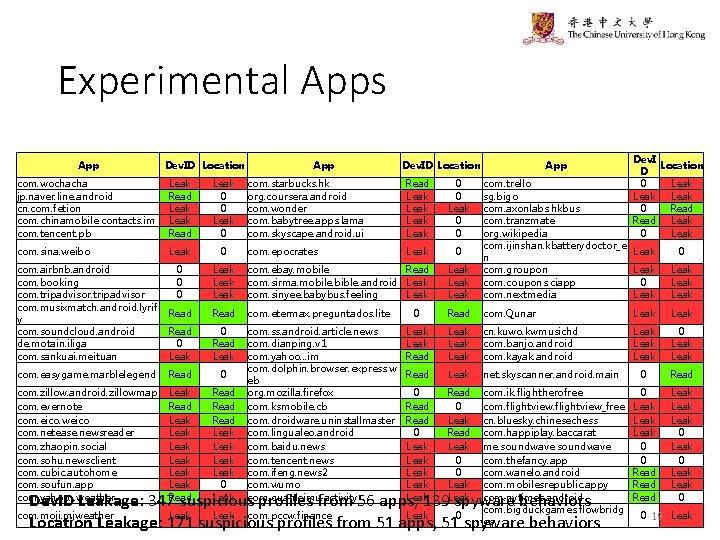
Experimental Apps App Dev. ID Location com. wochacha jp. naver. line. android cn. com. fetion com. chinamobile. contacts. im com. tencent. pb Leak Read Leak 0 0 Leak 0 com. sina. weibo Leak 0 App Dev. ID Location com. starbucks. hk org. coursera. android com. wonder com. babytree. apps. lama com. skyscape. android. ui Read Leak 0 0 Leak 0 0 com. epocrates Leak 0 App Dev. I Location D 0 Leak 0 Read Leak 0 Leak com. airbnb. android com. booking com. tripadvisor com. musixmatch. android. lyrif y com. soundcloud. android de. motain. iliga com. sankuai. meituan 0 0 0 Leak com. ebay. mobile Read com. sirma. mobile. bible. android Leak com. sinyee. babybus. feeling Leak com. trello sg. bigo com. axonlabs. hkbus com. tranzmate org. wikipedia com. ijinshan. kbatterydoctor_e Leak n com. groupon Leak com. coupons. ciapp 0 com. nextmedia Leak Read com. etermax. preguntados. lite 0 Read com. Qunar Leak Read 0 Leak 0 Read Leak Leak cn. kuwo. kwmusichd com. banjo. android com. kayak. android Leak 0 Leak com. easygame. marblelegend Read 0 Read Leak net. skyscanner. android. main 0 Read com. zillow. android. zillowmap com. evernote com. eico. weico com. netease. newsreader com. zhaopin. social com. sohu. newsclient com. cubic. autohome com. soufun. app com. yahoo. . . weather Leak Read Leak Leak Read Leak 0 Leak com. ss. android. article. news com. dianping. v 1 com. yahoo. . . im com. dolphin. browser. express. w eb org. mozilla. firefox com. ksmobile. cb com. droidware. uninstallmaster com. lingualeo. android com. baidu. news com. tencent. news com. ifeng. news 2 com. wumo com. quanleimu. activity 0 Read 0 Leak Leak Read 0 Leak Read Leak 0 0 Leak com. ik. flightherofree com. flightview_free cn. bluesky. chinesechess com. happiplay. baccarat me. soundwave com. thefancy. app com. wanelo. android com. mobilesrepublic. appy com. nytimes. android com. bigduckgames. flowbridg es 0 Leak 0 0 Read Leak 0 Leak 0 Dev. ID Leakage: 347 suspicious profiles from 56 apps, 139 spyware behaviors Leak com. pccw. finance Leak Location Leakage: 171 suspicious profiles from 51 apps, 510 spyware behaviors com. moji. mjweather 0 0 Leak 19 Leak

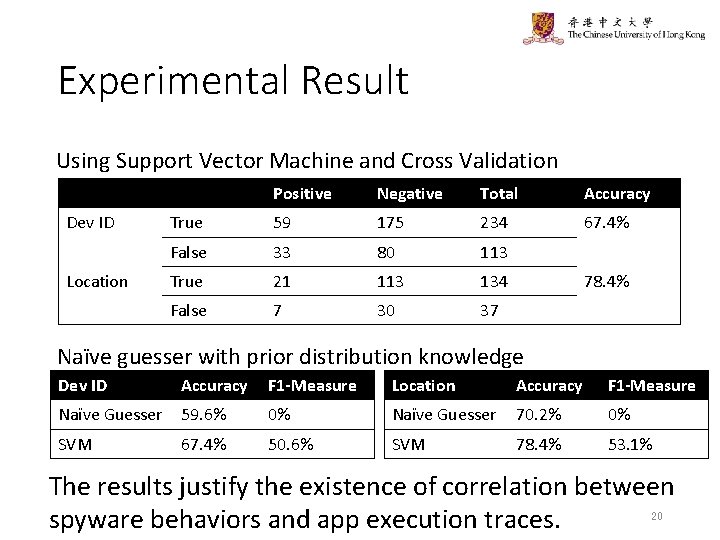
Experimental Result Using Support Vector Machine and Cross Validation Dev ID Location Positive Negative Total Accuracy True 59 175 234 67. 4% False 33 80 113 True 21 113 134 False 7 30 37 78. 4% Naïve guesser with prior distribution knowledge Dev ID Accuracy F 1 -Measure Location Accuracy F 1 -Measure Naïve Guesser 59. 6% 0% Naïve Guesser 70. 2% 0% SVM 67. 4% 50. 6% SVM 78. 4% 53. 1% The results justify the existence of correlation between 20 spyware behaviors and app execution traces.

Summary † Spyware awareness is an appropriate way for combating privacy leakage. † Detecting privacy leakage precisely is difficult: using dynamic taint analysis approach † We propose to discriminate privacy leakage events through app execution traces, which include binder call and system call. † We design a set of tools, and justify the correlation between privacy leakage events and app execution traces through real-world experiments. 21

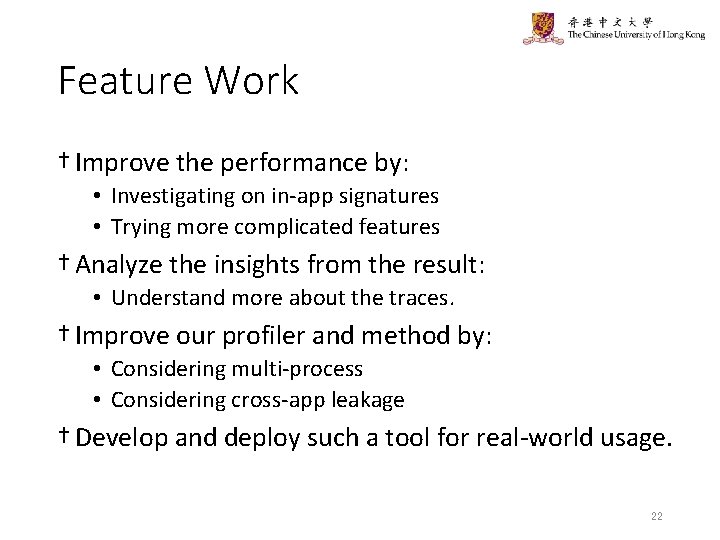
Feature Work † Improve the performance by: • Investigating on in-app signatures • Trying more complicated features † Analyze the insights from the result: • Understand more about the traces. † Improve our profiler and method by: • Considering multi-process • Considering cross-app leakage † Develop and deploy such a tool for real-world usage. 22
 Spy vs spy font
Spy vs spy font Spy aware
Spy aware Privacy awareness and hipaa awareness training cvs
Privacy awareness and hipaa awareness training cvs 15 key signatures
15 key signatures Rsa digital signature
Rsa digital signature Exchange 2007 signatures
Exchange 2007 signatures Uncitral model law on international commercial arbitration
Uncitral model law on international commercial arbitration Beadgcf flats
Beadgcf flats Uncitral model law on electronic transferable records
Uncitral model law on electronic transferable records Ocaml signatures
Ocaml signatures Minimum distance classifier
Minimum distance classifier Intruders use virus signatures fabricate
Intruders use virus signatures fabricate Martin kreitman
Martin kreitman Compact multi-signatures for smaller blockchains
Compact multi-signatures for smaller blockchains The air leakage rate for a combination vehicle
The air leakage rate for a combination vehicle Schottky mosfet
Schottky mosfet Chassis leakage current
Chassis leakage current Leakage point
Leakage point Synchronous dynamic pass transistor circuits
Synchronous dynamic pass transistor circuits Effects of electric current on human body
Effects of electric current on human body Subthreshold leakage current equation
Subthreshold leakage current equation Nfpa 99 leakage current limits
Nfpa 99 leakage current limits Gate induced drain leakage
Gate induced drain leakage