Spy Shield Preserving Privacy from Spy Addons Zhuowei

















- Slides: 25

Spy. Shield: Preserving Privacy from Spy Add-ons Zhuowei Li, Xiao. Feng Wang and Jong Youl Choi Indiana University at Bloomington Dr. Xiao. Feng Wang ©

You are being WATCHED! § Spyware on the loose Ø Webroot said 89 percent of the computers it scanned INFECTED WITH SPYWARE With 30 PICIECES PER MACHINE! Dr. Xiao. Feng Wang ©

What are we going to do? § Single-layer defense is always fragile Defense in Depth Detection Contain Dr. Xiao. Feng Wang © Prevention

Spyware containment § Protect sensitive information under spyware surveillance § Complementary to spyware prevention and detection Dr. Xiao. Feng Wang ©

Spy add-on COM Interfaces BHO Dr. Xiao. Feng Wang ©

Spy. Shield BHO Dr. Xiao. Feng Wang ©

Spy. Shield BHO Dr. Xiao. Feng Wang ©

Related work § Surveillance containment Ø Bump in the Ether; Spy. Block Not for containing spy add-ons § Privilege separation Ø Prevent privilege escalations Not for control of information leaks § Sandboxing and information flow security Spy. Shield enforces access control to add-on interfaces Dr. Xiao. Feng Wang ©

Contributions § General protection against spy add-ons § Potential for fine-grained access control § Resilience to attacks § Small overheads § Ease of use Dr. Xiao. Feng Wang ©

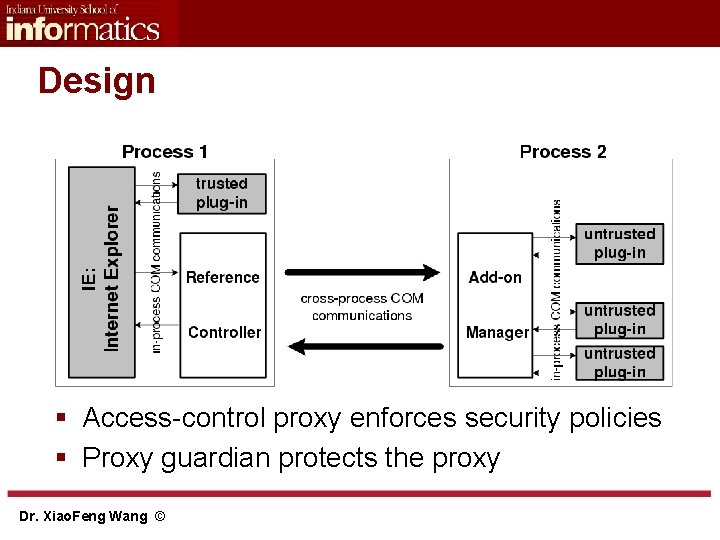
Design § Access-control proxy enforces security policies § Proxy guardian protects the proxy Dr. Xiao. Feng Wang ©

Access-control proxy § Objective: permit or deny add-ons’ access to host data § Event-driven add-ons: Ø Steal information once an event happens Ø Proxy: block the events according to security policies § Non-event-driven add-ons Ø Poll add-on interfaces Ø Proxy: control all interfaces spy add-ons might use § Direct memory access Ø Proxy: separate untrusted add-ons from the host control the channels for Inter-process communication Dr. Xiao. Feng Wang ©

Untrusted add-ons § Trusted add-ons are from known vendors § If don’t know, then don’t trust § Use hash values to classify add-ons Dr. Xiao. Feng Wang ©

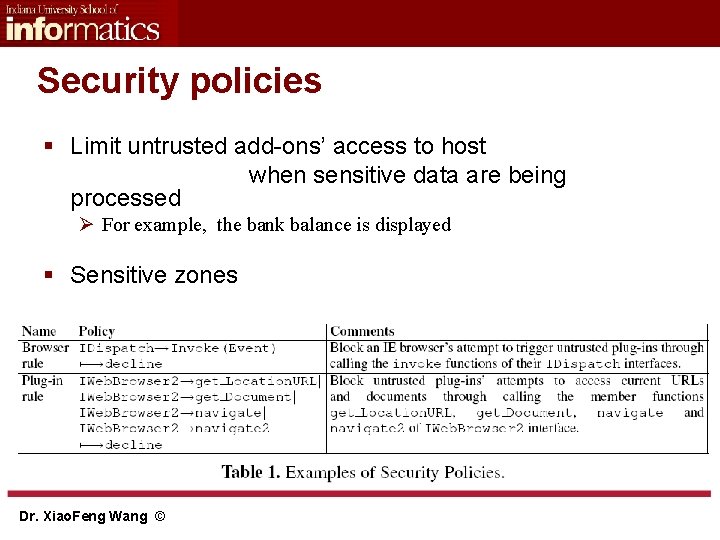
Security policies § Limit untrusted add-ons’ access to host when sensitive data are being processed Ø For example, the bank balance is displayed § Sensitive zones Dr. Xiao. Feng Wang ©

Policy setting Dr. Xiao. Feng Wang ©

Proxy guardian § Protect the proxy from being attacked § Use system call interposition § Protect data Ø Database of the hash values for trusted add-ons Ø Policies § Protect proxy processes Dr. Xiao. Feng Wang ©

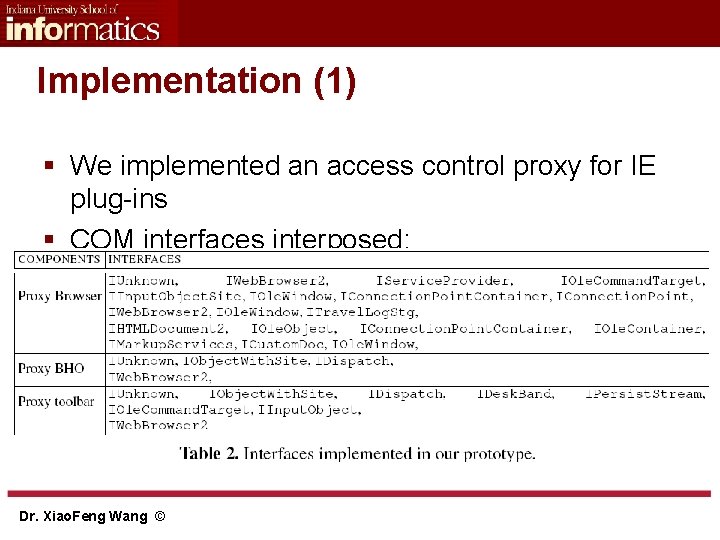
Implementation (1) § We implemented an access control proxy for IE plug-ins § COM interfaces interposed: Dr. Xiao. Feng Wang ©

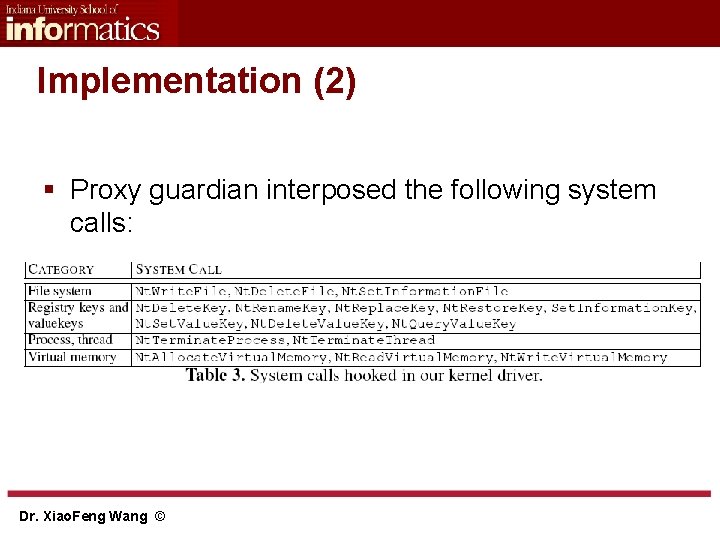
Implementation (2) § Proxy guardian interposed the following system calls: Dr. Xiao. Feng Wang ©

Evaluations § Setting: Ø Pentium 3. 2 GHz and 1 GB memory and Windows XP § Effectiveness test Ø Traffic differential analysis [Net. Spy] Ø Dangerous behavior blocked § Performance test Ø Latency for Inter-process communication Ø Processing time of function invocations Ø Web navigation Dr. Xiao. Feng Wang ©

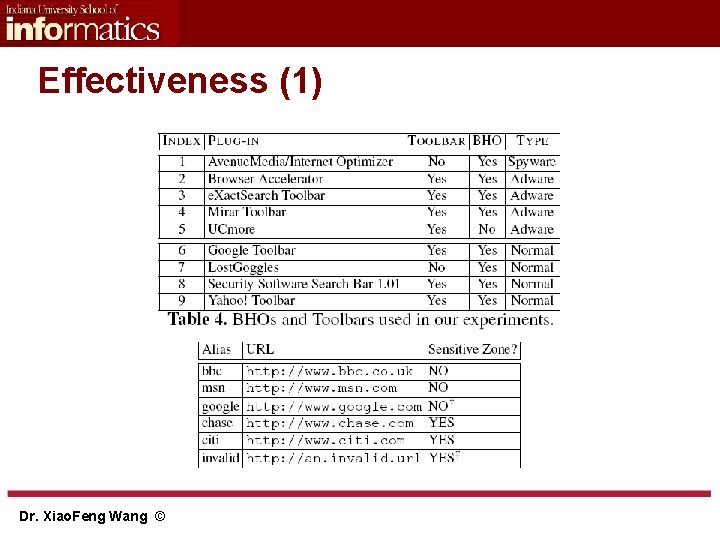
Effectiveness (1) Dr. Xiao. Feng Wang ©

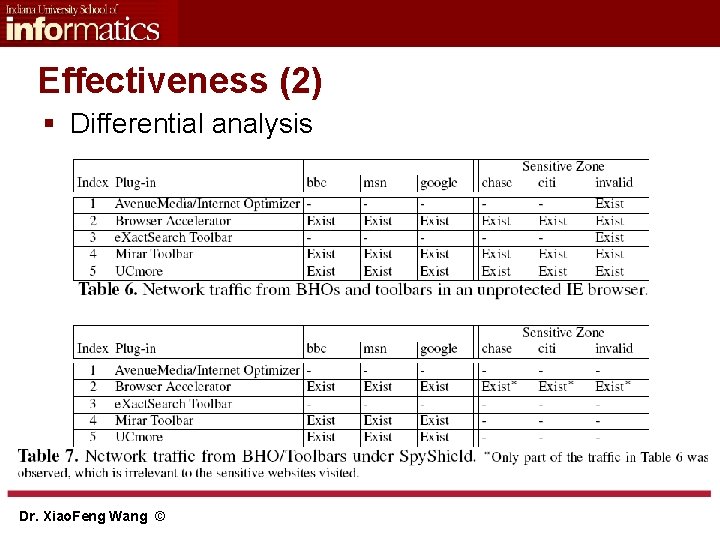
Effectiveness (2) § Differential analysis Dr. Xiao. Feng Wang ©

Effectiveness (3) § Block malicious activities Dr. Xiao. Feng Wang ©

Performance (1) § Overhead for IPC Ø 1327 times! § However, IPC only takes a SMALL portion of transaction processing time Dr. Xiao. Feng Wang ©

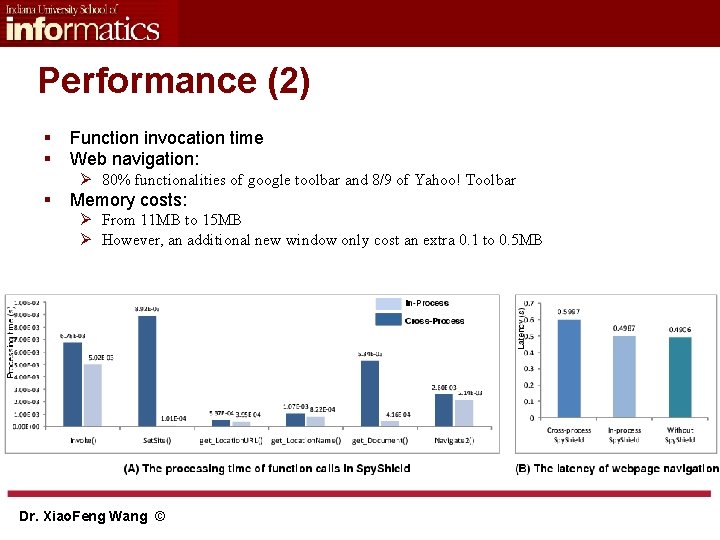
Performance (2) § § Function invocation time Web navigation: Ø 80% functionalities of google toolbar and 8/9 of Yahoo! Toolbar § Memory costs: Ø From 11 MB to 15 MB Ø However, an additional new window only cost an extra 0. 1 to 0. 5 MB Dr. Xiao. Feng Wang ©

Limitations § Limitations of the design Ø Only for protecting add-ons Ø Not for defending against kernel-level spyware § Limitations of implementation Ø Apply same policies to the whole window object How about frames? Ø Only wrap the COM interfaces for the plug-ins used in exp Dr. Xiao. Feng Wang ©

Conclusion and future work § Spy. Shield offers effective containment against Spy add-ons § Future work: develop policy model and techniques for containing standalone spyware Dr. Xiao. Feng Wang ©
 Yehuda lindell
Yehuda lindell Spy vs spy font
Spy vs spy font Privacy awareness and hipaa privacy training cvs
Privacy awareness and hipaa privacy training cvs Firefox addons for pentesting
Firefox addons for pentesting Ipcop addons
Ipcop addons Illiad addons
Illiad addons Shady addons
Shady addons Illiad addons
Illiad addons Firefox addons for pentesting
Firefox addons for pentesting Livestreampro
Livestreampro Functionionality
Functionionality Preserving food
Preserving food Orthogonal metrix
Orthogonal metrix Ecology preserving the animal kingdom
Ecology preserving the animal kingdom Nuzhat sultana
Nuzhat sultana Chapter 8 preserving your credit
Chapter 8 preserving your credit Preserving statistical validity in adaptive data analysis
Preserving statistical validity in adaptive data analysis Belen masia
Belen masia Chapter 8 preserving your credit
Chapter 8 preserving your credit They say he is spy rewrite in the other voice
They say he is spy rewrite in the other voice Opc data spy
Opc data spy Spy hansen
Spy hansen Spy - card party game взлом
Spy - card party game взлом A stiff bar that moves about a fixed point is a
A stiff bar that moves about a fixed point is a Picieces
Picieces Anstrack spy tool
Anstrack spy tool