Prof Venugopal Iyengar Director IOTM M Sc DIRM























































- Slides: 75

Prof. Venugopal Iyengar Director, IOTM M. Sc; DIRM; DTT; DCS; DCM; Certified Information System Auditor [CISA - ISACA] Certified Information Security Manger [CISM – ISACA] Certified Information System Security Professional [CISSP - (ISC)2] Attended Certified Business Continuity Advanced Course leading to CBLE 2000 by DRI Asia Certified Auditor - Quality Management System (QMS) ISO 9001: 2000 Certified Auditor - Information Security Management System (ISMS) BS ISO 27001: 2005 Certified Auditor – Business Continuity Management (BMS) BS 25999: 2007 Certified for Information Technology Service Management (ITSMS) ISO 20000 Criteria for ‘Certification of Inspection Lab’ ISO/IEC 17020 Associate Member, Association of Certified Fraud Examiners (USA) [ACFE] Member of QAT, TEC, JPA and CSE for Education Board of ISACA, Illinois, USA Member, GRATF-ASIA ISACA Member of the Expert Committee for e. Security Program, Dept. of IT, MC&IT, Go. I President Emeritus, ISACA Mumbai Chapter (2005 -06) Recipient of Microsoft MVP award in 2006 for contribution to global security community Recipient of “Pillar of Hindustani Society” award in 2008 for contribution to IS Audit and Info. Sec Global Professional Community from TACCI & IMCC Ex-Test Supervisor, (ISC)2 Asia Pacific, India Operations Life Member - Computer Society of India Life Member - Quality Forum-Netherlands Life Member - Cine Technician Association of South India Life Member - National Library International Member – ACFE, IEEE, ISA (Internet Security Alliance), ISACA, ISC 2, Associated with BCAS, BCC&I, BSI, CII, IBA, ICAI, ICSI, IRQS, MAIT, NASSCOM, TLF, UL

Information System Audit JBIMS-MIM III-Semester IV Jul-Sep 2012

IS Audit - Contents 1. Basic principles of IS Audit 1. 2. 3. 4. 5. 6. 7. 2. 3. IT Governance, IS Organization, IS functions, Segregation of duties, Separation of duties, Include IT Strategy Committee and IS Steering Committee Risk Management 1. 2. 3. 4. 5. 6. 7. 8. 4. 5. 6. Need for IS Audit Types of audit Auditing methods and procedure Audit Program, Audit Schedule, and Audit Plan Conducting Audit reporting Audit follow-ups Identification of Information Assets from core processes, threats, vulnerabilities, Analysis of risks, techniques for managing risk. Understanding control objectives and controls Physical & Environmental controls Operational and communication controls Network and Telecommunication controls Application controls and Database Controls Incident and response management Business continuity and Disaster Management as a business control Emerging role of information systems auditors

Session 1 Basic principles of Audit Control

Business Objective

Why Information Technology? • To facilitate achievement of BUSINESS GOALS of an organization • at what COST? • NOT loosing CONTROLS over Information Technology

and hence, • understand • identify and • apply controls

Asset Safeguarding • Asset = Resource, Process, Product, Computing infrastructure, . . . etc. • Threat = Occurrence of any event that causes understandable impact on organisation • Vulnerability = Weakness or Absence of safeguard • Safeguard = Control or COUNTER MEASURE employed to reduce RISK associated with SPECIFIC THREAT or Group of THREATS

CONTROLS • implemented to mitigate risk • reduce the potential loss

Controls can be • • Directive Preventive Detective Corrective

Implementation of Controls through • • Administrative Controls Logical Controls Physical Controls Environmental Controls

Administrative Controls • • Policy Procedure Awareness / Training Background checks Work habits checks Vacation history increased supervision

Logical Controls Restriction of access to system e. g. • encryption • smart cards • acl • transmission protocol

Physical Controls • • Guards locking door securing server rooms securing laptops protection of cables separation of duties backing up of files

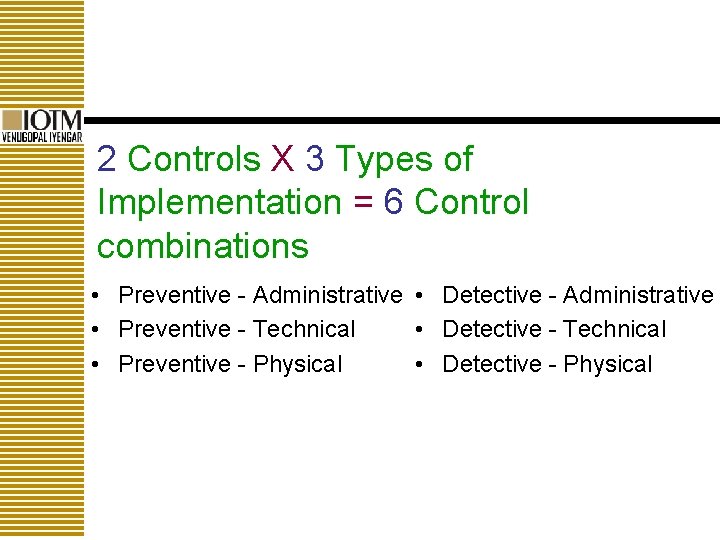
2 Controls X 3 Types of Implementation = 6 Control combinations • Preventive - Administrative • Detective - Administrative • Preventive - Technical • Detective - Technical • Preventive - Physical • Detective - Physical

Additional Controls • Deterrent Controls OR Directive Controls • Application Controls • Transaction Controls – input – processing – output – change – test

Deterrent Controls OR Directive Controls Used to encourage compliance with external controls such as regulatory compliance. Meant to compliment other controls such as Preventive controls and Detective controls.

Hardware Controls • • Hardware maintenance Maintenance Accounts Diagnostic Port Control Hardware Physical Control

Software Controls • • • Anti virus management software testing software utilities safe software storage backup controls

Application Controls SLA guarantees • turn around time • average response time • number of on-line users • system utilisation roles • system uptime • volume of transaction • production problems

Physical and Technical Controls • • • Facility control requirement facility access control devices intrusion detection and alarms Computer inventory control media storage requirement

Facility control requirement • • • Guards dogs fencing lighting locks cctv

Facility access control devices • security access cards – photo imaging cards – digital coded cards – wireless proximity readers • biometric devices – iris scan – Finger scan

Intrusion detection and alarms • Perimeter intrusion detection – photo electric sensors – dry contact switches • Motion detectors – wave pattern – capacitance – audio detectors • Alarm systems – local – central – auxiliary

Computer inventory control • PC physical controls – cable locks – port control – switch control – peripheral switch controls – electronic security boards

Media storage requirement • • • data backup CD’s diskettes hard drives paper print out / reports ONSITE & OFFSITE

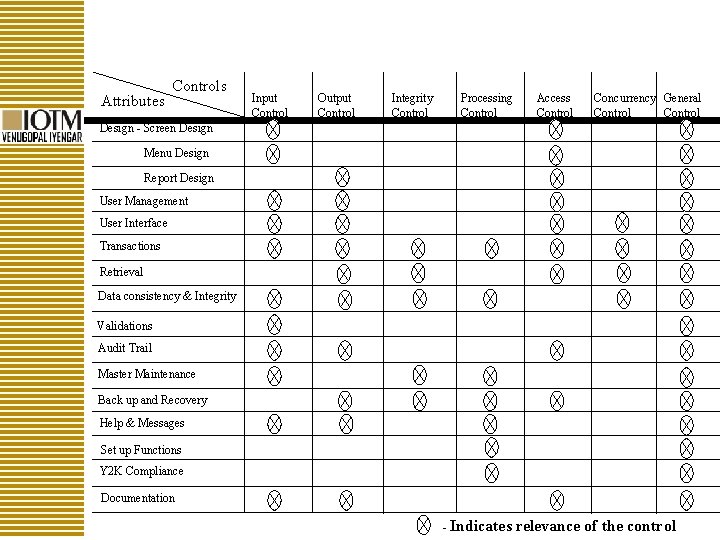
Attributes Controls Input Control Output Control Integrity Control Processing Control Access Control Concurrency General Control Design - Screen Design Menu Design Report Design User Management User Interface Transactions Retrieval Data consistency & Integrity Validations Audit Trail Master Maintenance Back up and Recovery Help & Messages Set up Functions Y 2 K Compliance Documentation - Indicates relevance of the control

Control Classifications • Preventive • Detective • Corrective

and hence controls of all types Are important To safeguard assets and achieve Company’s Business Goals

Session 2 Types of Audit & Auditing methods. Management Audits of IT in an organization

Types of Audit – Classification Type 1 • Statutory Audits • Compliance Audits

Types of Audit – Classification Type 2 1. Financial Audit 2. Management Audit 3. Quality Audit 4. Information System Audit 5. Information System Security Audit 6. Information Security Audit 7. Information Technology Audit 8. Fire & Safety Audits 9. Network Audit 10. Tele Communication Audit

Auditing Method

Audit Phases Audit Subject : Identify area to be audited Audit Objective : Purpose Audit Scope : Specific system, function, or unit for review Preaudit Planning : resources, technical skill, source of information like flow charts, policies, standards, … + location Audit procedure and steps for data gathering : identify approach to verify and test controls. Interview list, departmental policies, work instructions, etc Procedure for evaluating the test or review results : Procedure for communicating with management : Audit report preparation : Audit follow-ups :

IT Audit and IT Governance • Management Method for auditing IT • Relationship to IT Governance

Tool for IT Governance 1. 2. 3. 4. 5. Management Reporting Governing IT and IS – BSC Operational Improvements Process Improvements Certification

COBIT as a Tool for IT Governance 1. 2. 3. 4. 5. Management model Business Goals Information Criteria IT Resources 4 Phases (PO, AI, DS, ME)


Audit Planning (Short & Long term) Short term planning – issues that will be covered during the year Long term planning – organizations strategic IT direction and IT environment Analysis should occur annually after taking into account – new control issues – changing technologies – enhanced evaluation techniques Reviewed and approved by – senior management and audit committee Communicated to – relevant levels of management

Audit Planning (Requirements) • Gain an understanding of the business – purpose, objective, processes and technology • • Perform risk analysis Conduct an internal control review Set the audit scope and objective Develop the audit approach or audit strategy

Audit Planning (Understanding Business) • Touring key organization facilities • Reading background material including industry publications, annual reports and independent financial analysis reports • Reviewing long-term strategic plans • Interviewing key managers to understand business issues • Reviewing prior reports

Laws and Regulations • Government Requirements – Country laws, state laws, other acts (IT Act, FEMA, etc) • External Requirements – Industry specific (Trans-border, Banking, etc) • Regulations – – Establishment Organization Responsibilities Correlation to Financial & Operational Audit

Standards and Guidelines for IS Auditing • Standards for Information Systems Auditing • Guidelines for IS Auditing • Code of Professional Ethics

Standards for Information Systems Auditing Objectives of IS Audit Standards are to inform • IS auditors of the minimum level of acceptable performance required to meet professional responsibilities set out in the Code of Professional Ethics for IS Auditors. • Management and other interested parties of the profession’s expectations concerning the work of practitioners.

Standards for Information Systems Auditing Framework • Standard – Define mandatory requirements for IS auditing and reporting • Guidelines – Provide guidance in applying IS auditing standards • Procedure – Provide documented information on how to meet standards while performing Information systems audit

Session 3 Risks involved in deploying IT such as fraud, hacking, etc

What do we cook today? • An Attempt

Let us look at Information Security Management Concept Confidentiality Destruction / Denial Alteration Integrity Availability Disclosure and the reverse of Information Security

RISK Risk = probability that a particular threat that will exploit a particular vulnerability of the system

Risk Management Concepts There a number of basic risk management concepts that must be thoroughly understood by the ISM. They include but are not limited to: • • • Threats Vulnerabilities Exposures Risks Impacts Controls Countermeasures Resource valuation Information asset classification Criticality Sensitivity Redundancy • • • Robustness and resilience Hot, warm and cold sites Recovery Time Objectives (RTO’s) Recovery Point Objectives (RPO’s) Incident response Business case development Project management Baselines Security technologies Governance Strategies Policies, standards and procedures

Deploying IT – discuss challenges, remediation • System Requirement • Resource Requirement • Infrastructure – Inhouse – Outsource • Operation – In-house – Outsource • Monitor, measure, govern for reporting

Risk Mgmt. – Frauds, Hacking • Pre-implementation • During Implementation • Post implementation • Frauds can take place during. … s e all these phases as c se e • Hacking can take place post th n i k s implementation i R sc i D s s u

Session 4 Analysis of risks, techniques for managing risk. Physical security, system and application controls and audit trails. Disaster Management Issues

RISK Management vs Assesment Risk Analysis is part of Risk Management Risk Analysis – identifying security risk – determining magnitude – identifying areas that needs safegaurds

Techniques of managing risk

Physical Security

System Control

Application Control

Audit Trails

Disaster Management Ensure that the IS Auditor “understands and can provide assurance that in the event of a disruption the business continuity and disaster recovery processes will ensure the timely resumption of IT services while minimizing the business impact”

Objective There are three (3) tasks within this content area: 1. Evaluate the adequacy of backup and restore provisions to ensure the availability of information required to resume processing. 2. Evaluate the organization’s disaster recovery plan to ensure that it enables the recovery of IT processing capabilities in the event of a disaster. 3. Evaluate the organization’s business continuity plan to ensure its ability to continue essential business operations during the period of an IT disruption.

Recovery/Continuity Planning Process • Risks could cause an organization to suffer: • Inability to maintain critical customer services • Damage to market share, reputation or brand • Failure to protect the company assets including intellectual properties and personnel • Business control failure • Failure to meet legal or regulatory requirements

Recovery/Continuity Planning Process • Business’ Ability to Continue Operations • Rigorous planning & commitment of resources • Risk assessment to identify critical business processes • Reduction of risk for unexpected disruption to critical functions • Assure continuity of minimum level of service for critical operations • Responsibility of senior management • Address all functions & assets to continue as viable organization

Recovery/Continuity Planning Process • Phases of the Business Continuity Planning Process – Creation of a business continuity and disaster recovery policy – Business impact analysis – Classification of operations and criticality analysis – Development of a business continuity plan and disaster recovery procedures – Training and awareness program – Testing and implementation of plan – Monitoring

Business Impact Analysis (BIA) • Criticality of information resources • Issues to consider for BIA • Different business processes • Critical information resources related to critical business processes • Critical recovery time period before significant losses are incurred • Systems risk ranking

Developing Recovery Strategies • Selection of an appropriate strategy is based on: – Business impact analysis – Criticality analysis • Metrics that help in determining the recovery strategies – – – Recovery Point Objective (RPO) Recovery Time Objective (RTO) Interruption Window Service Delivery Objective (SDO) Maximum Tolerable Outages

Recovery Alternatives • Types of Off-site Backup Facilities • Hot sites - Fully equipped facility • Warm sites - Partially equipped but lacking processing power • Cold sites - Basic environment

Recovery Alternatives • Types of Off-site Backup Facilities • Duplicate information processing facility • Mobile sites Reciprocal agreement Contract with hot, warm or cold site Procuring alternative hardware facilities

Recovery Alternatives • Types of Off-site Backup Facilities • Procuring alternative hardware facilities ü Vendor or third-party ü Off-the-shelf ü Credit agreement or emergency credit cards

Organization and Assignment of Responsibilities • • • Incidence Response Team Emergency Action Team Damage Assessment Team Emergency Management Team Off-site Storage Team Software Team Applications Team Security Team Emergency Operations Team Salvage Team Relocation Team … etc.

Components of an Effective Business Continuity Plan A BCP may consist of more than one plan document: – – – – Business continuity plan (BCP) Business recovery (or resumption) plan (BRP) Continuity of operations plan (COOP) Continuity of support plan/IT contingency plan Crisis communications plan Incident response plan Disaster recovery plan (DRP) Occupant emergency plan (OEP)

Auditing Recovery/ Continuity Plans § Review Business Continuity Plan § Evaluate Prior Test Results § Evaluate Off-site Storage § Interview Key Personnel § Evaluate Security at Off-site Facility § Review Alternative Processing Contract § Review Insurance Coverage

Session 5 Exposure in the context of Internet and E-commerce. Use of encryption, firewalls, electronic signatures and third party authentication techniques.

Session 6 Emerging role of information systems auditors

Thank you Venugopal Iyengar veai 1@vsnl. net
 Venugopal iyengar
Venugopal iyengar Dr parameswaran venugopal
Dr parameswaran venugopal Puneeth iyengar
Puneeth iyengar Arpana iyengar
Arpana iyengar The art of choosing ted talk
The art of choosing ted talk Iyengar frases
Iyengar frases Iyengar framing
Iyengar framing Srividya iyengar
Srividya iyengar Radha iyengar md
Radha iyengar md Organigrama con consejo de administracion
Organigrama con consejo de administracion Jeff james director
Jeff james director David warren director
David warren director Procolombia organigrama
Procolombia organigrama Hardy it director
Hardy it director El pianista basada en hechos reales
El pianista basada en hechos reales Use case diagram esempi
Use case diagram esempi Dekalb county athletic director
Dekalb county athletic director Director ict
Director ict Brian gordon director
Brian gordon director Director ejecutivo organigrama
Director ejecutivo organigrama Mathematica 사용법
Mathematica 사용법 Director como lider
Director como lider Rotaract club activities
Rotaract club activities Juniper nms
Juniper nms Program vizita penitenciar miercurea ciuc
Program vizita penitenciar miercurea ciuc Traffic director triage
Traffic director triage Eft director's office
Eft director's office Non realistic theatre
Non realistic theatre Territory sales manager
Territory sales manager Hx4kkkskzay -site:youtube.com
Hx4kkkskzay -site:youtube.com Salaam bombay! nominations
Salaam bombay! nominations Hadie perkas
Hadie perkas A television news director wishes to use three news stories
A television news director wishes to use three news stories Landing t
Landing t Pla director sociosanitari
Pla director sociosanitari ²orange
²orange Un vector es un segmento que tiene
Un vector es un segmento que tiene Director class
Director class English comic actor and film director
English comic actor and film director Director regional de alajuela
Director regional de alajuela Silver director income in vestige
Silver director income in vestige Director devil wears prada
Director devil wears prada Cyp assistant director
Cyp assistant director Usana ranking
Usana ranking Deputy medical director
Deputy medical director Robert stevenson director
Robert stevenson director Uit rgpv director
Uit rgpv director Director
Director Que es desarrollo profesional
Que es desarrollo profesional Area director
Area director Types of authoring tools in multimedia
Types of authoring tools in multimedia Tugas pengarah syarikat
Tugas pengarah syarikat Qualification of a director
Qualification of a director Features of macromedia director
Features of macromedia director Ortho-para director
Ortho-para director Director of labour market enforcement
Director of labour market enforcement Directors brief
Directors brief Con ganas de triunfar director
Con ganas de triunfar director Organigrama
Organigrama Director socializer relater thinker test
Director socializer relater thinker test The newsroom director
The newsroom director Discussion director examples
Discussion director examples The text-based director, also known as the
The text-based director, also known as the Change management picture
Change management picture Assistant director vicky
Assistant director vicky Director of technical education hp
Director of technical education hp Director hand signals
Director hand signals Moral acrostic
Moral acrostic Sub director
Sub director Child development teacher permit
Child development teacher permit Director de el espectador
Director de el espectador Actor director musician
Actor director musician Director personality type
Director personality type Director casa de asigurari de sanatate calarasi
Director casa de asigurari de sanatate calarasi Directorate of accounts and treasuries
Directorate of accounts and treasuries English comic actor and film director
English comic actor and film director