Michael Krausz CEO CCO i s c Group







































































- Slides: 91

Michael Krausz, CEO & CCO i. s. c. Group – Vienna – London – Hong Kong – United States Stressless ISMS How Shakespeare helps with building an ISMS – A practical guide

Introduction and Overview The Stressless ISMS – A Practical Guide

Are we a startup? The Stressless ISMS – A Practical Guide

No, 21 years and counting, in the UK market since 2017 The Stressless ISMS – A Practical Guide

Smallest customer we ever built an ISMS with? The Stressless ISMS – A Practical Guide

1 employee… The Stressless ISMS – A Practical Guide

…with 1 Mio in revenues The Stressless ISMS – A Practical Guide

Largest customer we built an ISMS with? The Stressless ISMS – A Practical Guide

150, 000 employees The Stressless ISMS – A Practical Guide

Typical customer size? The Stressless ISMS – A Practical Guide

70 to 200 employees The Stressless ISMS – A Practical Guide

Founded: 1998 Projects in 28 countries on four continents Subsidiaries in Vienna, London, Hong Kong, New York, Salt Lake City Consulting - Investigation ISO 27001 / ISO 27018 ISO 27001 Certification Assistance Program© GDPR compliance assistance - Comprehensive Security Check © Sophisticated or low-cost penetration testing Setting up security departments CSO / CISO-as-a-service DSB / DPO-as-a-service - Policies & Procedures Awareness - Pen-Testing / IT-Forensics Suppert in case of severe breaches of white collar crime in conjunction with cyber crime Training - Regular and on-demand training - Strategic learning and knowledge management Rapid Response Deployment Teams The Stressless ISMS – A Practical Guide

Michael Krausz § Studies: physics, computer science, law § Certified professional investigator § Lead Auditor ISO 27001 (and working as such) § Certified ISMS-Manager and ISMS-Auditor § Certified Data Protection Officer § Author of: § Managing Information Security Breaches – Real Life Stories, 2 nd edition § The True Cost of Information Security Breaches & Cybercrime The Stressless ISMS – A Practical Guide

i. s. c. projects are. . . §. . . a blabber-free zone – we hate hypes and buzzwords §. . . targeted, directed, objective-focused §. . . in budget and on time §. . . fun for those with a sense of humour The Stressless ISMS – A Practical Guide

Workshop Contents Part 1 – The Stressless ISMS and how Shakespeare can help (10: 00 to 11: 00) Part 2 – Anecdotes from cases of severe information security breaches (11: 15 to 12: 00) The Stressless ISMS – A Practical Guide

Part 1 – A Practical Guide to Building an ISMS The Stressless ISMS - A Practical Guide

Where does the stress come from? The Stressless ISMS – A Practical Guide

Motivators behind an ISMS project § You WANT § You SHOULD § You MUST The Stressless ISMS – A Practical Guide

Motivators behind an ISMS project “Better three hours too soon than a minute too late. ” The Stressless ISMS – A Practical Guide

The potential toxicity of an ISMS project for an organisation Timeline Investment Appetite Quality Short and Long. Term side effects The Stressless ISMS – A Practical Guide

The potential toxicity of an ISMS project for an organisation Timeline Quality The Stressless ISMS – A Practical Guide

The potential toxicity of an ISMS project for an organisation Timeline Investment Appetite The Stressless ISMS – A Practical Guide

The potential toxicity of an ISMS project for an organisation Timeline Short and Long. Term side effects The Stressless ISMS – A Practical Guide

The potential toxicity of an ISMS project for an organisation Investment Appetite Quality Short and Long. Term side effects The Stressless ISMS – A Practical Guide

The potential toxicity of an ISMS project for an organisation Investment Appetite Quality Short and Long. Term side effects The Stressless ISMS – A Practical Guide

The potential toxicity of an ISMS project for an organisation Timeline Investment Appetite Quality Short and Long. Term side effects The Stressless ISMS – A Practical Guide

Choose ONE optimization variable and choose it wisely. Make sure the choice is YOURS. (Ahh, there was something about want – should – must, right? ) The Stressless ISMS – A Practical Guide

The potential toxicity of an ISMS project for an organisation Short and Long-Term side effects § § § § Attrition of staff CISO can‘t do his/her job due to role conflicts Budget too low => ineffectiveness abounds Ineffective security measures Interoperability issues Tainted or destroyed supplier relationships Slowing down business processes „Certificate-only“ ISMS The Stressless ISMS – A Practical Guide

What is the earliest point in time you should start certification proceedings? The Stressless ISMS – A Practical Guide

After your ISMS has been running for one year. The Stressless ISMS – A Practical Guide

…why? The Stressless ISMS – A Practical Guide

…and who’s doing that? ? The Stressless ISMS – A Practical Guide

Setting up the ISMS Step by Step The Stressless ISMS – A Practical Guide

Knowing your status The Stressless ISMS – A Practical Guide

The Stressless ISMS – A Practical Guide

Key Elements of an ISMS The Stressless ISMS – A Practical Guide

Key Elements § Risk Management Process § The Risk to Control Chain (Req => Process => Asset => Risk => Control) § CISO / ISMS-Manager Role § Sound Operations § Secure Development Process § Physical Security § Incident Management § Supplier Management § Business Continuity Management The Stressless ISMS – A Practical Guide

POLICY – PRACTICE – PROOF “What is past is prologue. ” The Stressless ISMS – A Practical Guide

POLICY – PRACTICE – PROOF If there is Proof but neither Policy nor Practice, what is this situation called? The Stressless ISMS – A Practical Guide

POLICY – PRACTICE – PROOF FRAUD The Stressless ISMS – A Practical Guide

POLICY – PRACTICE – PROOF - The auditor’s view: “Talking isn’t doing. It is a kind of good deed to say well; and yet words are not deeds. ” The Stressless ISMS – A Practical Guide

POLICY – PRACTICE – PROOF - The auditor’s view – i. s. c. Audit Rule #1 What isn’t documented doesn’t exist! The Stressless ISMS – A Practical Guide

Cunning and Context or… “The empty vessel makes the loudest sound. ” The Stressless ISMS – A Practical Guide

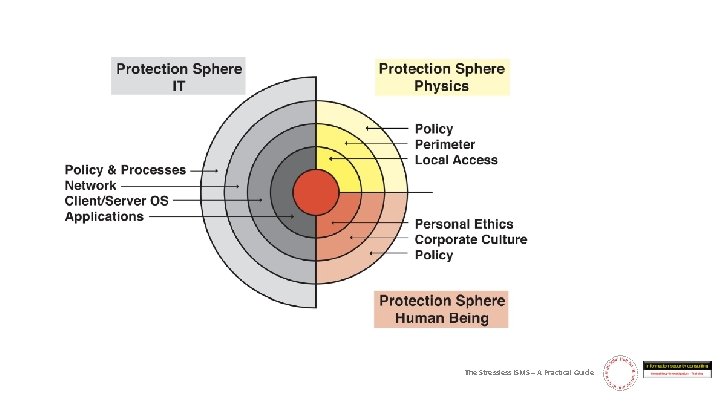
A scope, my kingdom for a scope! The Stressless ISMS – A Practical Guide

A pest on both your houses! The relationship between business and IT The Stressless ISMS – A Practical Guide

If the likelihood is 50: 50, which of the 50 s is the good one? …or… The Stressless ISMS – A Practical Guide

“There are many events in the womb of time, which will be delivered. ” The Stressless ISMS – A Practical Guide

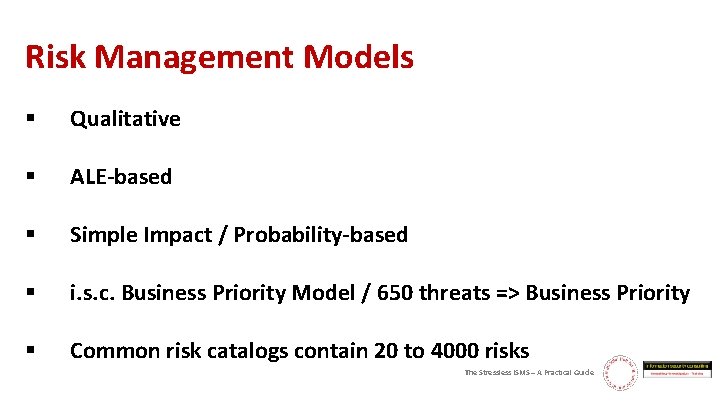
Risk Management Models § Qualitative § ALE-based § Simple Impact / Probability-based § i. s. c. Business Priority Model / 650 threats => Business Priority § Common risk catalogs contain 20 to 4000 risks The Stressless ISMS – A Practical Guide

After doing risk analysis… The Stressless ISMS – A Practical Guide

“I shall the effect of this good lesson keeps as watchman to my heart. ” The Stressless ISMS – A Practical Guide

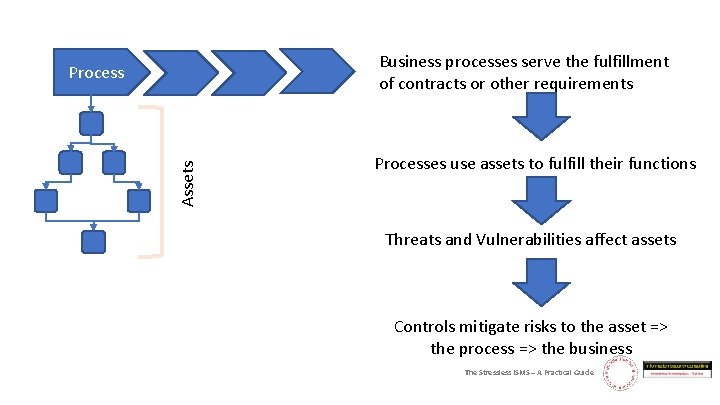
Asses and Assets - The CMDB “‘Tis best to weigh the enemy more mighty than he seems. ” The Stressless ISMS – A Practical Guide

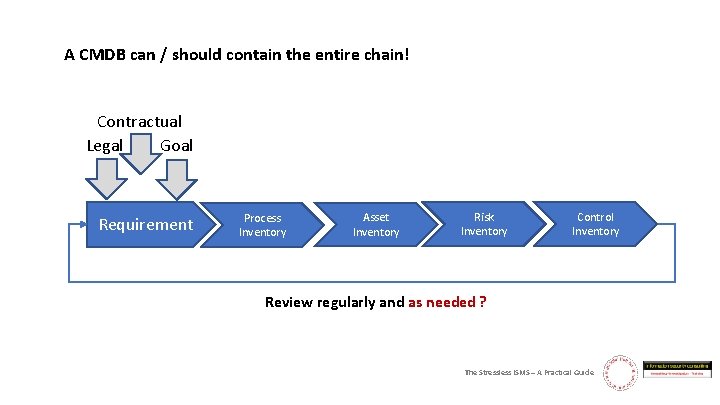
Business processes serve the fulfillment of contracts or other requirements Assets Processes use assets to fulfill their functions Threats and Vulnerabilities affect assets Controls mitigate risks to the asset => the process => the business The Stressless ISMS – A Practical Guide

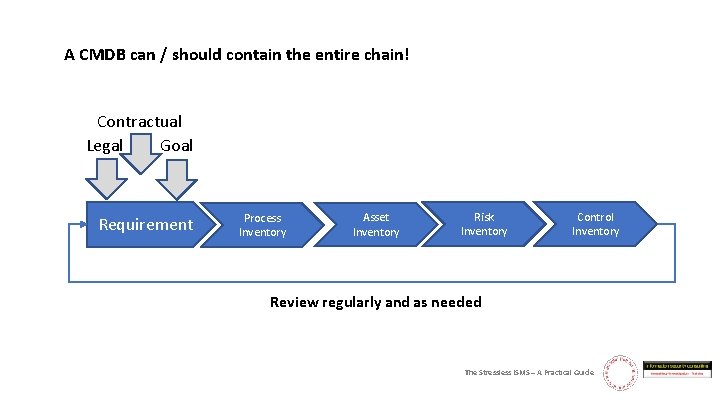
A CMDB can / should contain the entire chain! Contractual Legal Goal Requirement Process Inventory Asset Inventory Risk Inventory Control Inventory Review regularly and as needed The Stressless ISMS – A Practical Guide

A CMDB can / should contain the entire chain! Contractual Legal Goal Requirement Process Inventory Asset Inventory Risk Inventory Control Inventory Review regularly and as needed ? The Stressless ISMS – A Practical Guide

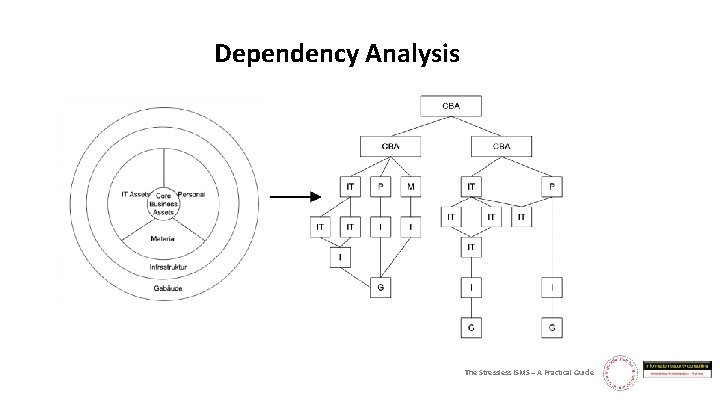
Dependency Analysis “Things won are done, joy’s soul lies in the doing. ” The Stressless ISMS – A Practical Guide

Dependency Analysis The Stressless ISMS – A Practical Guide

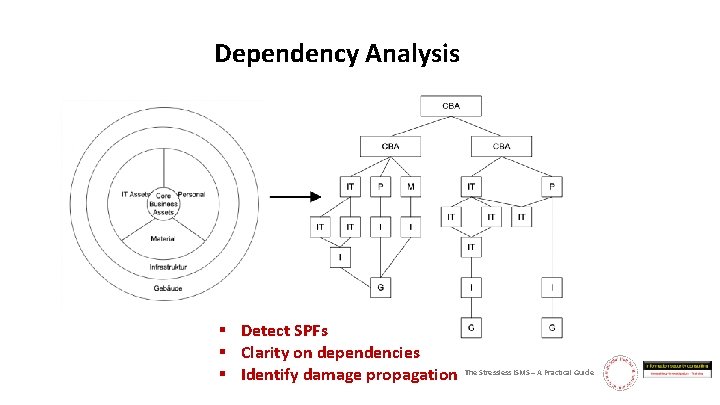
Dependency Analysis § Detect SPFs § Clarity on dependencies § Identify damage propagation The Stressless ISMS – A Practical Guide

Setting up Security Departments – “Now is the winter of our discontent. ” The Stressless ISMS – A Practical Guide

The ideal security department § CISO § Operations § Operating systems and networks // Network Pen. Testing § Specialized OSes as needed § Applications incl. databases § Development § Secure Development Process / Vuln. Mgmt. / App. Pent. Testing The Stressless ISMS – A Practical Guide

The ideal security department § CISO § Data Protection Officer § Reports to CISO, but with extensive audit rights § Incident and Breach Management § A former police officer or cybercrime expert § Policies / Procedures and Awareness § Strong IT background, but skilled in documentation § Project Security § Identifies security requirements in new projects and supports projects The Stressless ISMS – A Practical Guide

. . . in practice. . . § Actual need is not specified, CISO left to define his/her own job § CISO too technical, no people or process skills § The department grows gradually => lot of interaction with top management needed § Sloppiness when defining objectives and tasks § 1 st year: soft targets § 2 nd year: target should be nailed down The Stressless ISMS – A Practical Guide

Questions: § Why does the DPO report to the CISO? § To whom should the CISO report? § What‘s the ideal qualification profile for a CISO? The Stressless ISMS – A Practical Guide

Policy Trees Build it – don’t buy it! “Modest doubt is called the beacon of the wise. ” The Stressless ISMS – A Practical Guide

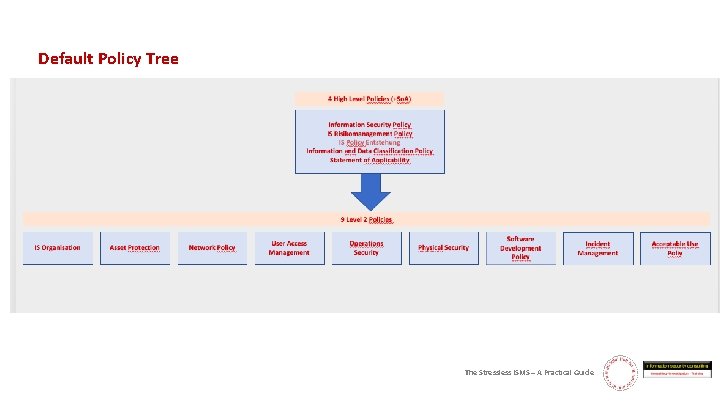
Default Policy Tree The Stressless ISMS – A Practical Guide

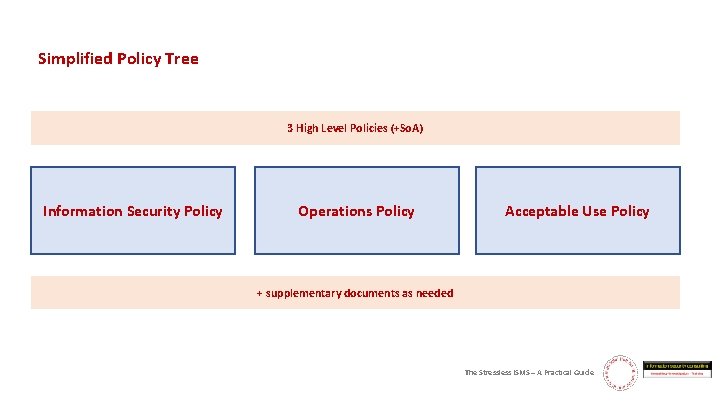
Simplified Policy Tree 3 High Level Policies (+So. A) Information Security Policy Operations Policy Acceptable Use Policy + supplementary documents as needed The Stressless ISMS – A Practical Guide

Awareness “No, I will be the pattern of all patience. ” The Stressless ISMS – A Practical Guide

Awareness: § Information must be digestable and targeted! § Different user groups require different training § Regular effort? § WOW people, but be careful (i. e. do not overwhelm). § Policies apply to EVERYBODY, even Top Management The Stressless ISMS – A Practical Guide

Vulnerabilities, Threats, and Fornication (of malware) The Stressless ISMS – A Practical Guide

Vulnerabilities, Threats, and Fornication § Know thy systems (CMDB) ! § Have a Vulnerability Management Process in place! § Know thy status! (Appropriate Tools) § Include risk acceptance in the process The Stressless ISMS – A Practical Guide

Incident Management The Stressless ISMS – A Practical Guide

Incident Management § Have a classification scheme to assess event severity levels! – Not every event is an incident. § Have a clear internal communications process! § Have your law enforcement contacts ready! § Be prepared to have first assessment completed within 3 days or less (GDPR) or have a good reason why notification was not necessary (PII only)! The Stressless ISMS – A Practical Guide

Supplier Management “Let no such man be trusted. ” The Stressless ISMS – A Practical Guide

Supplier Management § Know thy supplier ! § Will ISO 27001 be enough? § The right to audit! The right to audit? § The supplier refuses to sign your policy – now what? The Stressless ISMS – A Practical Guide

Business Continuity „Doubt thou IT is prepared. Doubt that disaster looms. Doubt docs to be a liar, But never doubt thy BIA. “ The Stressless ISMS – A Practical Guide

How many pages for a BCP? The Stressless ISMS – A Practical Guide

30 to 400 The Stressless ISMS – A Practical Guide

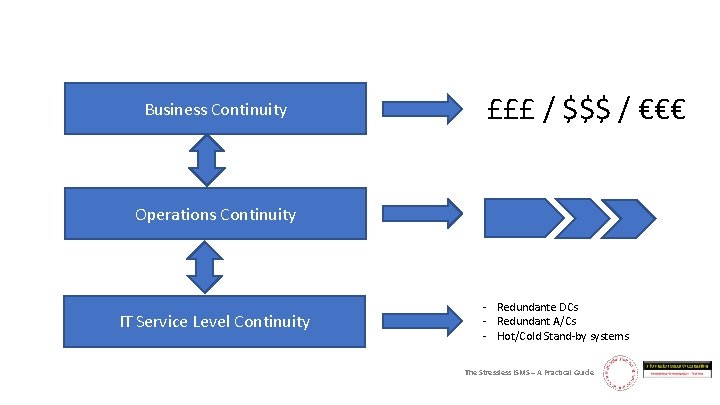
Business Continuity £££ / $$$ / €€€ Operations Continuity IT Service Level Continuity - Redundante DCs - Redundant A/Cs - Hot/Cold Stand-by systems The Stressless ISMS – A Practical Guide

Part II – Case Studies The Stressless ISMS - A Practical Guide

Case Studies § The Ex-Bank § Ransomware undressed § From hacks to riches The Stressless ISMS - A Practical Guide

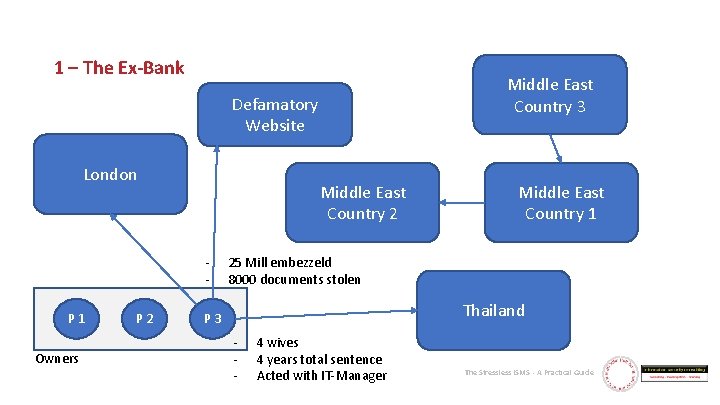
1 – The Ex-Bank Middle East Country 3 Defamatory Website London Middle East Country 2 - P 1 Owners P 2 Middle East Country 1 25 Mill embezzeld 8000 documents stolen Thailand P 3 - 4 wives 4 years total sentence Acted with IT-Manager The Stressless ISMS - A Practical Guide

1 – The Ex-Bank § Emergency Audit in Middle East 1 – 61 severe vulnerabilities – First Ever Urgent Customer Alert Issued § Audit at HQ – mostly harmless, but some oddities found § Defamatory website taken down § Documents acquired The Stressless ISMS - A Practical Guide

1 – The Ex-Bank § Yeah – Jackpot ! – The guy laundered money for the Taliban § Reaction of Austrian AML authority: “Not my circus, not my monkeys” § Contact with British authorities established, all info handed over. Case closed. The Stressless ISMS - A Practical Guide

2 – Ransomware undressed § U. S. corporation with EU subsidiary § Reception receives E-Mail containing a CV § Reception forwards to HR § HR opens Word File => BANG! The Stressless ISMS - A Practical Guide

2 – Ransomware undressed § Corporation contacts DPA (why? Just why? ) § Uneasiness spreads in U. S. HQ due to some U. S. laws being applicable, as well. § Ransomware is reverse-engineered to identify true purpose § Result: Only ransomware, no PII exfiltrated The Stressless ISMS - A Practical Guide

3 – From Hacks to Riches Company X sells online services and provides forums to users. Company X monitors these to learn what users think about the company. The Stressless ISMS - A Practical Guide

3 – From Hacks to Riches One fine day, the following posting appears: “Do you want to found your own online services company? – I got 4 million user accounts from Company X to sell. ” The Stressless ISMS - A Practical Guide

3 – From Hacks to Riches Next Steps: • Investigation starts • Once a name and a likeness are established (14 ½ years old), contact with police is established. • Police reaction: “Ahhh, that guy, we know him, I got a file somewhere over here. ” • Family is on holiday => Raid on day of return from holiday The Stressless ISMS - A Practical Guide

3 – From Hacks to Riches • Interview conducted • No Cybercrime established, but fraud • Fraud? – Guy promised to have 4 million records, only had 10. 000 • Perpetrator was granted plea bargain without entry into criminal records database The Stressless ISMS - A Practical Guide

3 – From Hacks to Riches • Years later, while reading morning tea newspaper: “Guy Y’s company secures 2 nd round VC funding for new and innovative business idea! – At only 21 years of age” • Yeah, right. ROFL The Stressless ISMS - A Practical Guide

5 KEY TAKE AWAYS The Stressless ISMS - A Practical Guide

5 KEY TAKE AWAYS (1) There are more than 5. (2) Do not accept a CISO job, if you don’t report to Top Management (3) Invest most time in your risk profile / the risk management process (4) Be a bridge between business and IT (5) Build awareness (6) Include people early in every task to avoid hassles later (7) Adapt processes to company size and complexity. (8) Stimulate a fault-tolerant learning culture. The Stressless ISMS - A Practical Guide