IGI Technical Introduction incl Planning for a Deployment














- Slides: 33

IGI Technical Introduction incl. Planning for a Deployment David Edwards Technical Enablement – Identity Governance

Aim of this module: Introduce the product from a technical perspective to help with deployment planning 3 IBM Security

Agenda • Key Concepts of IGI • Architectural Overview of IGI - Overview and components - Product requirements - Deployment options - IGI functional components • Planning Considerations • Class Lab setup 4 IBM Security

Module Outcomes At the end of this module you should: • Understand the key concepts of IGI • Be able to describe the architecture and components of IGI • Know how to find the detailed product requirements • Understand some of the deployment considerations • Have setup the Lab environment for this course 5 IBM Security

Key Concepts of IGI

Identity Management and Identity Governance Identity Management • Managing “who has access to what” • Focused on managing users and their access • Usually involves reconciliation and provisioning • Users = people or identities; employees, contractors, customers - Users normally reside in a repository – HR system, directory, AD etc. - Will often hold attributes of users – jobcode, position code, manager, office location etc. - Can be used for role-based or attribute-based provisioning - May drive identity management off changes to user data • Access is the accounts and access rights on target systems - Accounts will include logon id and password, and other account attributes - Access rights may be account attributes (e. g. AUDITOR flag) or group membership (e. g. AD group) • May also be a permission and right to access a resource (e. g. READ Sales Report) • Roles are used to simplify identity management • Includes workflow for review/approval of access requests 7 IBM Security

Identity Management and Identity Governance • Focused on ensuring there are processes to control “who has access to what” • Includes: - Risk Policies • Separation of Duties (So. D) • Sensitive Access (SA) - Processes for managing risk, including mitigations - Business activities • The auditor view of job functions, “Purchase Order Create” & “Purchase Order Approve” - Recertification (or attestation) to periodically review access • Reviewing user access • Reviewing how roles are defined • Reviewing risks and mitigations - Reporting 8 IBM Security

Typical Identity Governance and Intelligence actors Employee / User Manager / Dept. Manager Application Manager Risk Manager Security Officer / Reviewer Supervisor Operator 9 IBM Security § § Self-service access requests and password management Can delegate (be delegated) access § § Performs certifications Initiates access requests / Approves self-service requests Initiates and approves third-party delegations Performs certifications regarding organizational unit and entitlement visibility § § § Approves access requests Resolves unmatched or orphaned accounts Models permission to business activity mapping § § Approves violation escalated access requests Performs access violations mitigation campaigns § § Certification supervisor Locks and unlocks user accounts § Manually performs access fulfillment requests

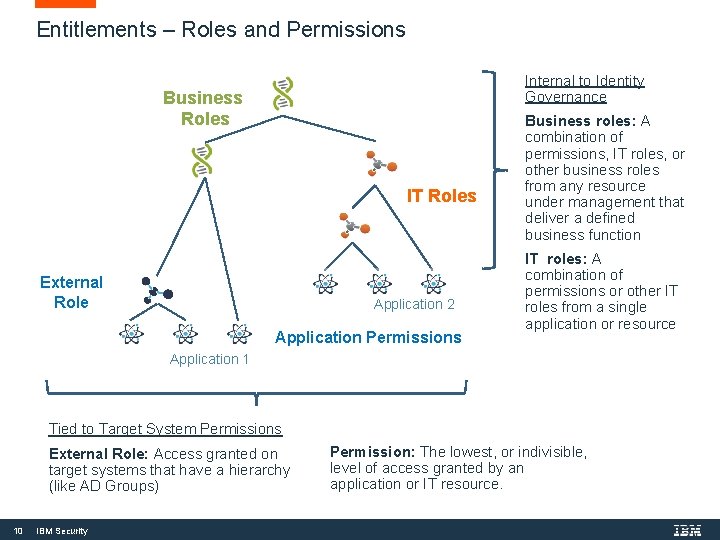
Entitlements – Roles and Permissions Internal to Identity Governance Business Roles IT Roles External Role Application 2 Application Permissions Business roles: A combination of permissions, IT roles, or other business roles from any resource under management that deliver a defined business function IT roles: A combination of permissions or other IT roles from a single application or resource Application 1 Tied to Target System Permissions External Role: Access granted on target systems that have a hierarchy (like AD Groups) 10 IBM Security Permission: The lowest, or indivisible, level of access granted by an application or IT resource.

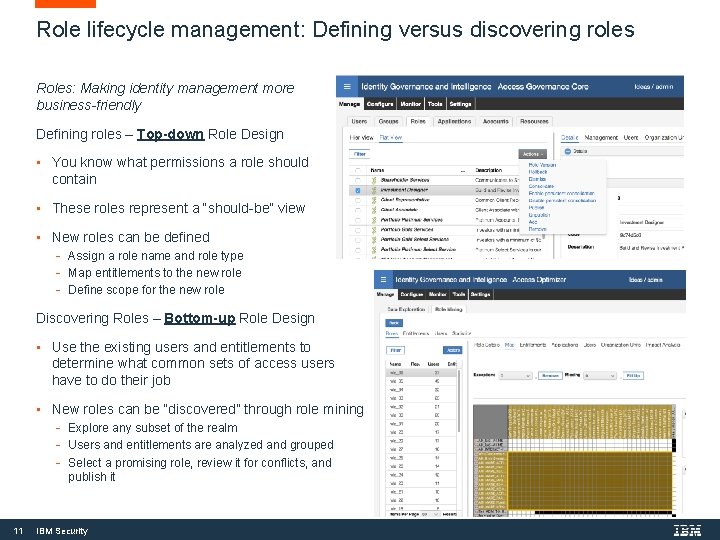
Role lifecycle management: Defining versus discovering roles Roles: Making identity management more business-friendly Defining roles – Top-down Role Design • You know what permissions a role should contain • These roles represent a “should-be” view • New roles can be defined - Assign a role name and role type - Map entitlements to the new role - Define scope for the new role Discovering Roles – Bottom-up Role Design • Use the existing users and entitlements to determine what common sets of access users have to do their job • New roles can be “discovered” through role mining - Explore any subset of the realm - Users and entitlements are analyzed and grouped - Select a promising role, review it for conflicts, and publish it 11 IBM Security

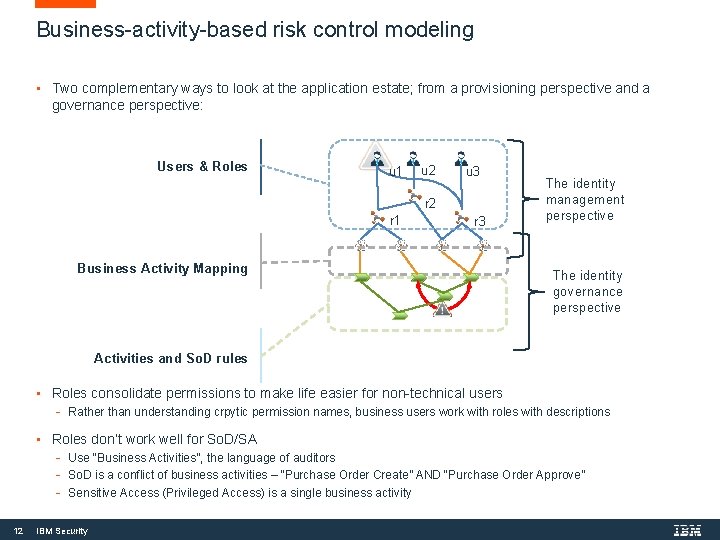
Business-activity-based risk control modeling • Two complementary ways to look at the application estate; from a provisioning perspective and a governance perspective: Users & Roles u 1 u 2 u 3 r 2 r 1 Business Activity Mapping r 3 The identity management perspective The identity governance perspective Activities and So. D rules • Roles consolidate permissions to make life easier for non-technical users - Rather than understanding crpytic permission names, business users work with roles with descriptions • Roles don’t work well for So. D/SA - Use “Business Activities”, the language of auditors - So. D is a conflict of business activities – “Purchase Order Create” AND “Purchase Order Approve” - Sensitive Access (Privileged Access) is a single business activity 12 IBM Security

Certification campaigns • Certification campaigns are a formal process for automating the periodic review of a given relationship • The Access Certifier tool allows nontechnical lines of business management to enforce accurate and timely access decisions with simple approve or revoke selections applied to the assignments being examined • Five types of certification campaigns are supported 13 Campaign Type Description Organization unit assignment Review entitlements for visibility violations User assignment Review entitlements for user access violations Risk violation mitigation Review for unmitigated risk violations Entitlement Review by application manager of entitlement use Account Review account access for target applications IBM Security

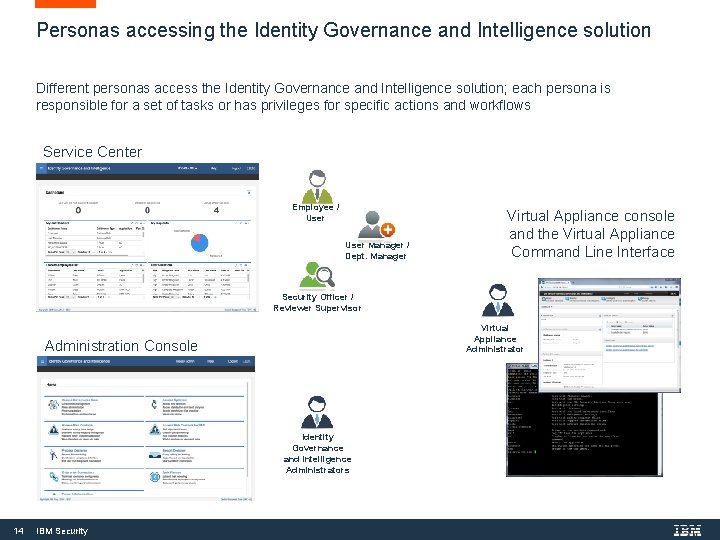
Personas accessing the Identity Governance and Intelligence solution Different personas access the Identity Governance and Intelligence solution; each persona is responsible for a set of tasks or has privileges for specific actions and workflows Service Center Employee / User Manager / Dept. Manager Virtual Appliance console and the Virtual Appliance Command Line Interface Security Officer / Reviewer Supervisor Virtual Appliance Administrator Administration Console Identity Governance and Intelligence Administrators 14 IBM Security

Virtual Appliance Administrator tasks The Virtual Appliance Administrator is responsible for the initial setup and activation of the Identity Governance and Intelligence Virtual Appliance (VA) and for its day-to-day administration, such as the following tasks • Monitor proper functioning of the whole solution • Apply upgrades and Fix Packs to the Virtual Appliance • Virtual Appliance administrator maintenance tasks • Troubleshoot issues and work with IBM Customer Support should a complex issue arise 15 IBM Security

Let’s look at how the product is put together before diving into the functions Architectural Overview of IGI

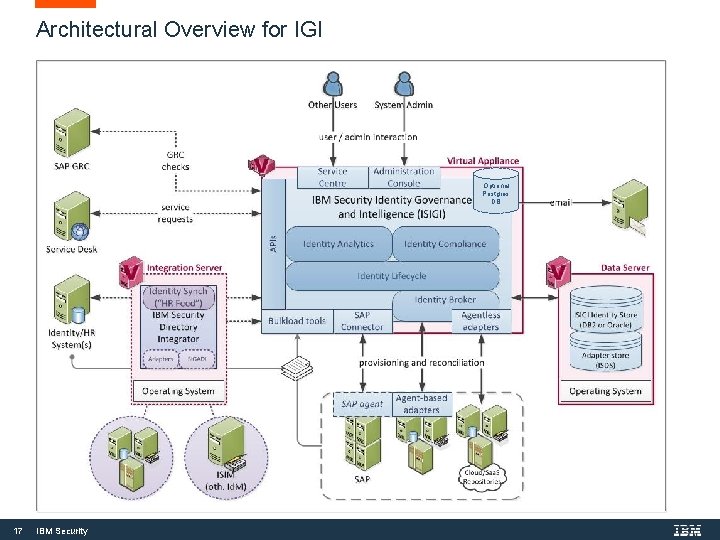
Architectural Overview for IGI Optional Postgres DB 17 IBM Security

Architectural Overview for IGI • Identity Governance and Intelligence (IGI) Server - Implemented as a Virtual Appliance (VA) NOT software - Three licensed components; Lifecycle, Compliance and Analytics - Also includes: • The Broker (aka Identity Brokerage) for managing provisioning to target systems using adapters • IBM Tivoli Directory Integrator (TDI) for running adapters • Enterprise Connectors, including SAP-specific connectors • APIs – Java and REST • Bulkload tools for fast loading of identity objects - Two user interfaces • Administration Console – for system administration of IGI • Service Center – for role-based identity governance functions (e. g. employee, user manager) • Adapters and Connectors - May be agent-based (deployed to target systems) or agentless - Covered in more detail later • Data Stores - IGI Database • Stores all IGI data, such as objects and policies • Remote DB 2 or Oracle instance, or onboard (VA) Postgres DB - IGI Directory • Used as a cache for reconciliation and provisioning with the Broker • Uses a remote IBM Security Directory Server (SDS) instance (runs on DB 2) 18 IBM Security

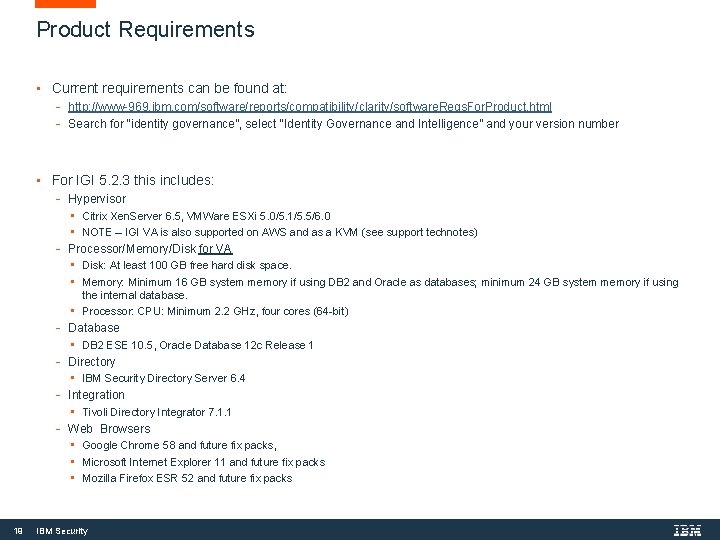
Product Requirements • Current requirements can be found at: - http: //www-969. ibm. com/software/reports/compatibility/clarity/software. Reqs. For. Product. html - Search for “identity governance”, select “Identity Governance and Intelligence” and your version number • For IGI 5. 2. 3 this includes: - Hypervisor - - 19 • Citrix Xen. Server 6. 5, VMWare ESXi 5. 0/5. 1/5. 5/6. 0 • NOTE – IGI VA is also supported on AWS and as a KVM (see support technotes) Processor/Memory/Disk for VA • Disk: At least 100 GB free hard disk space. • Memory: Minimum 16 GB system memory if using DB 2 and Oracle as databases; minimum 24 GB system memory if using the internal database. • Processor: CPU: Minimum 2. 2 GHz, four cores (64 -bit) Database • DB 2 ESE 10. 5, Oracle Database 12 c Release 1 Directory • IBM Security Directory Server 6. 4 Integration • Tivoli Directory Integrator 7. 1. 1 Web Browsers • Google Chrome 58 and future fix packs, • Microsoft Internet Explorer 11 and future fix packs • Mozilla Firefox ESR 52 and future fix packs IBM Security

Deployment Options • Many – depends on the functional and non-functional requirements • Examples: - All-in-one deployment • Only deploy the VA and use the on-board database • All integration with external systems via bulkload or enterprise connectors • Good for a governance-only deployment or a standalone user training environment - Two-box deployment • Deploy a single VA with a separate server for the database, directory and any integration components • Good for small governance+lifecycle deployment - Three-box deployment • Deploy; VA, data server (DB and LDAP) and integration server (TDI plus adapters/integrations) • Good for larger deployments, can tune the different components independently • HA and DR - Virtual Appliance uses clustering mechanism • Allows for one master and up to three replicas • Fail-over built into the firmware - IGI server is also basically stateless, so could have multiple instances behind a load-balancer - Data replication mechanisms available for DB 2 and SDS - Discussed in more detail in the delivery/deployment training 20 IBM Security

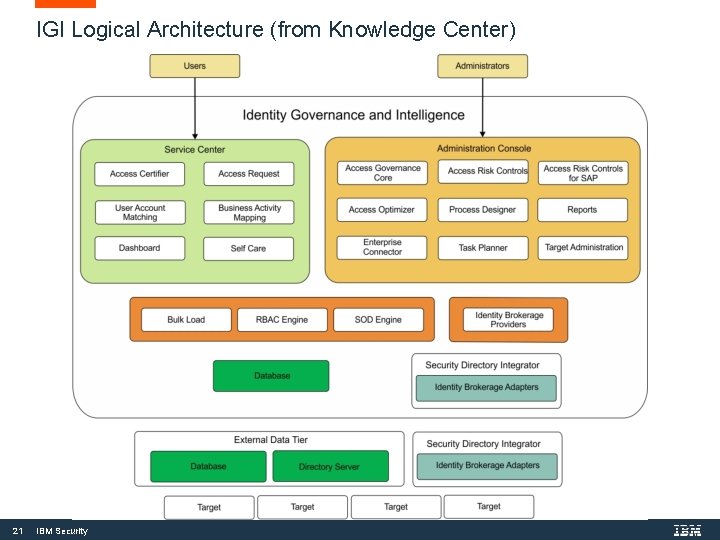
IGI Logical Architecture (from Knowledge Center) 21 IBM Security

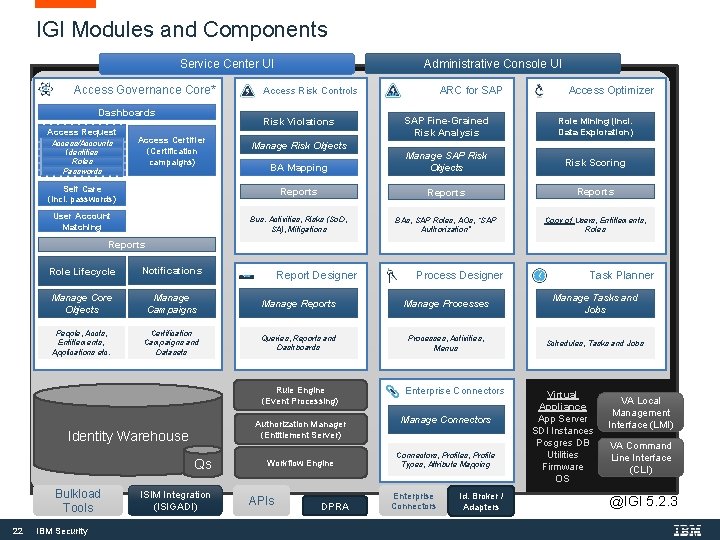
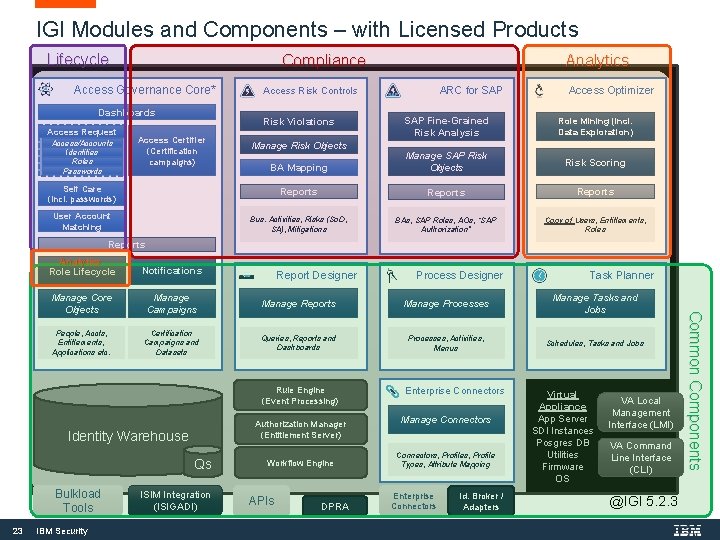
IGI Modules and Components Administrative Console UI Service Center UI Access Governance Core* Dashboards ARC for SAP Access Risk Controls Access Optimizer SAP Fine-Grained Risk Analysis Role Mining (incl. Data Exploration) BA Mapping Manage SAP Risk Objects Risk Scoring Self Care (incl. passwords) Reports User Account Matching Bus. Activities, Risks (So. D, SA), Mitigations BAs, SAP Roles, AOs, “SAP Authorization” Copy of Users, Entitlements, Roles Access Request Access/Accounts Identities Roles Passwords Risk Violations Access Certifier (Certification campaigns) Manage Risk Objects Reports Role Lifecycle Notifications Manage Core Objects Manage Campaigns Manage Reports Manage Processes Manage Tasks and Jobs People, Accts, Entitlements, Applications etc. Certification Campaigns and Datasets Queries, Reports and Dashboards Processes, Activities, Menus Schedules, Tasks and Jobs Report Designer Rule Engine (Event Processing) Authorization Manager (Entitlement Server) Identity Warehouse Qs Bulkload Tools 22 IBM Security ISIM Integration (ISIGADI) Workflow Engine APIs DPRA Process Designer Enterprise Connectors Manage Connectors, Profiles, Profile Types, Attribute Mapping Enterprise Connectors Id. Broker / Adapters Task Planner Virtual Appliance App Server SDI Instances Posgres DB Utilities Firmware OS VA Local Management Interface (LMI) VA Command Line Interface (CLI) @IGI 5. 2. 3

IGI Modules and Components – with Licensed Products Lifecycle Analytics Compliance Access Governance Core* Dashboards ARC for SAP Access Risk Controls Access Optimizer SAP Fine-Grained Risk Analysis Role Mining (incl. Data Exploration) BA Mapping Manage SAP Risk Objects Risk Scoring Self Care (incl. passwords) Reports User Account Matching Bus. Activities, Risks (So. D, SA), Mitigations BAs, SAP Roles, AOs, “SAP Authorization” Copy of Users, Entitlements, Roles Access Request Access/Accounts Identities Roles Passwords Risk Violations Access Certifier (Certification campaigns) Manage Risk Objects Reports Analytics Role Lifecycle Notifications Manage Core Objects Manage Campaigns Manage Reports Manage Processes Manage Tasks and Jobs People, Accts, Entitlements, Applications etc. Certification Campaigns and Datasets Queries, Reports and Dashboards Processes, Activities, Menus Schedules, Tasks and Jobs Report Designer Authorization Manager (Entitlement Server) Identity Warehouse Qs Bulkload Tools 23 IBM Security ISIM Integration (ISIGADI) Workflow Engine APIs DPRA Enterprise Connectors Manage Connectors, Profiles, Profile Types, Attribute Mapping Enterprise Connectors Id. Broker / Adapters Task Planner Virtual Appliance App Server SDI Instances Posgres DB Utilities Firmware OS VA Local Management Interface (LMI) VA Command Line Interface (CLI) @IGI 5. 2. 3 Common Components Rule Engine (Event Processing) Process Designer

Typical considerations when planning a deployment Deployment Considerations

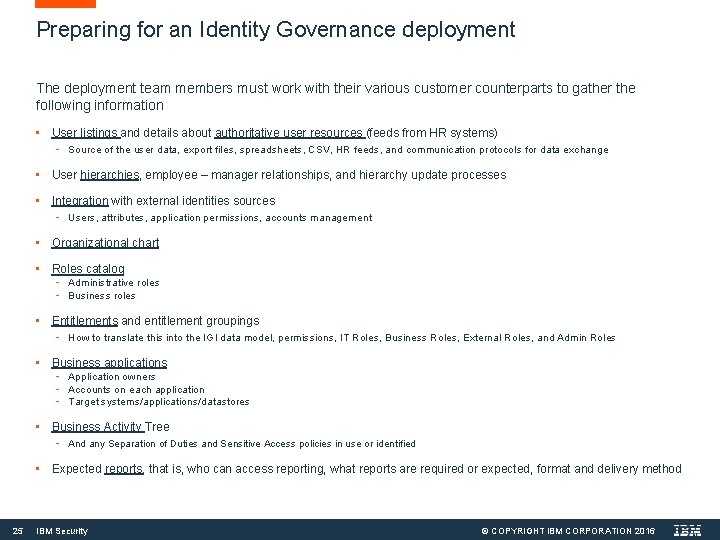
Preparing for an Identity Governance deployment The deployment team members must work with their various customer counterparts to gather the following information • User listings and details about authoritative user resources (feeds from HR systems) - Source of the user data, export files, spreadsheets, CSV, HR feeds, and communication protocols for data exchange • User hierarchies, employee – manager relationships, and hierarchy update processes • Integration with external identities sources - Users, attributes, application permissions, accounts management • Organizational chart • Roles catalog - Administrative roles - Business roles • Entitlements and entitlement groupings - How to translate this into the IGI data model, permissions, IT Roles, Business Roles, External Roles, and Admin Roles • Business applications - Application owners - Accounts on each application - Target systems/applications/datastores • Business Activity Tree - And any Separation of Duties and Sensitive Access policies in use or identified • Expected reports, that is, who can access reporting, what reports are required or expected, format and delivery method 25 IBM Security © COPYRIGHT IBM CORPORATION 2016

Identify business processes around Identity Governance Business processes impacted by the Identity Governance solution • User creation, user termination • User assignment to organizational units • Role lifecycle management Role creation, removal, and consolidation • Role assignments • Access lifecycle management • Identity reconciliations such as users, attributes, application permissions, accounts • Segregation of Duties (So. D) and Sensitive Accesses (SA) management • Mitigations of risks • Periodic risk analysis • Role delegations • Periodic recertification 26 IBM Security © COPYRIGHT IBM CORPORATION 2016

Identify key stakeholders • Identify key stakeholders and define their duties - Access lifecycle management approvers - So. D & mitigation controls evaluator or approvers - User managers - Risk managers - Supervisors to certification campaigns • Don’t forget stakeholders that do not use the Identity Governance solution directly - HR - CIO/CFO - Legal 27 IBM Security © COPYRIGHT IBM CORPORATION 2016

Module Summary Questions? You should now: • Understand the key concepts of IGI • Be able to describe the architecture and components of IGI • Know how to find the detailed product requirements • Understand some of the deployment considerations • Have setup the Lab environment for this course 31 IBM Security

Common structure and controls Appendix – IGI User Interface

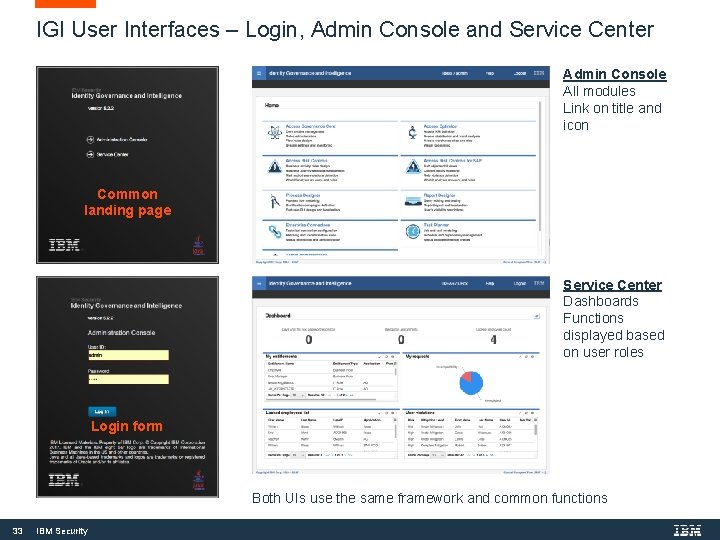
IGI User Interfaces – Login, Admin Console and Service Center Admin Console All modules Link on title and icon Common landing page Service Center Dashboards Functions displayed based on user roles Login form Both UIs use the same framework and common functions 33 IBM Security

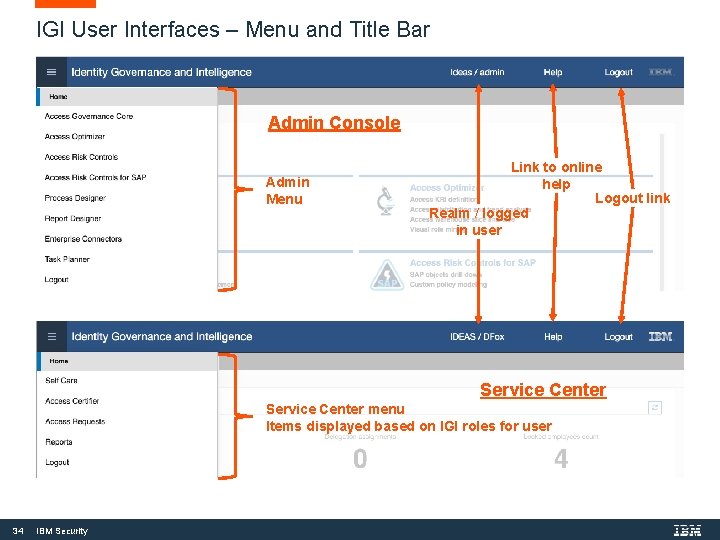
IGI User Interfaces – Menu and Title Bar Admin Console Admin Menu Link to online help Logout link Realm / logged in user Service Center menu Items displayed based on IGI roles for user 34 IBM Security

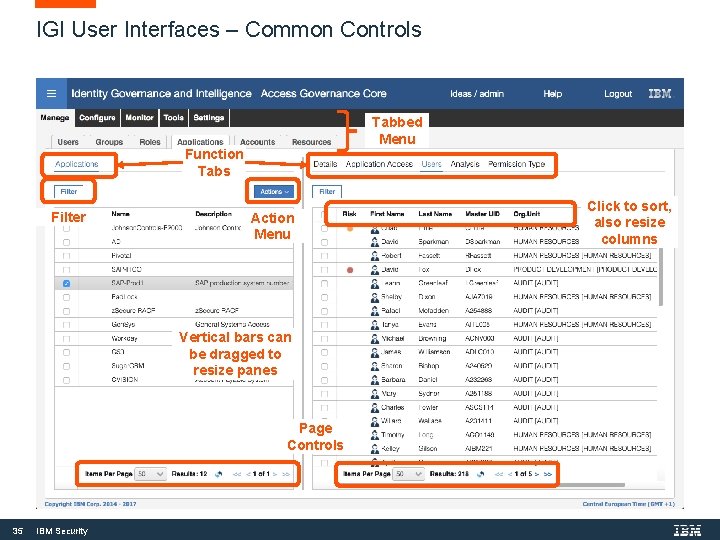
IGI User Interfaces – Common Controls Tabbed Menu Function Tabs Filter Action Menu Vertical bars can be dragged to resize panes Page Controls 35 IBM Security Click to sort, also resize columns

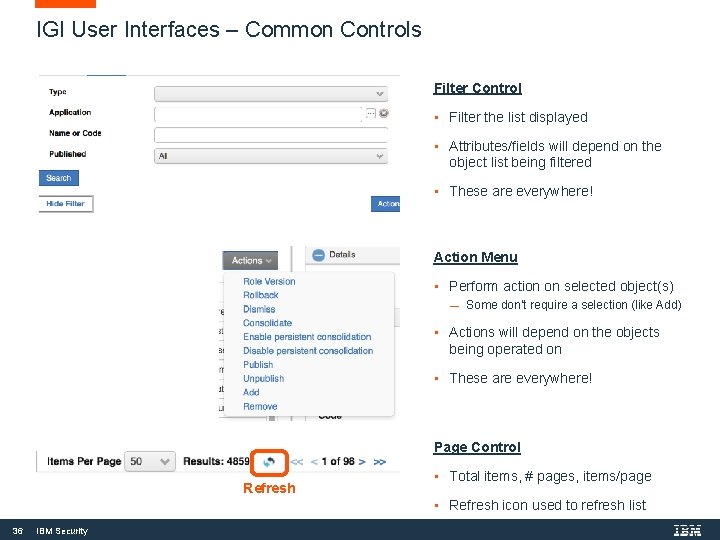
IGI User Interfaces – Common Controls Filter Control • Filter the list displayed • Attributes/fields will depend on the object list being filtered • These are everywhere! Action Menu • Perform action on selected object(s) Some don’t require a selection (like Add) • Actions will depend on the objects being operated on • These are everywhere! Page Control Refresh • Total items, # pages, items/page • Refresh icon used to refresh list 36 IBM Security

THANK YOU FOLLOW US ON: ibm. com/securityintelligence. com xforce. ibmcloud. com @ibmsecurity youtube/user/ibmsecuritysolutions © Copyright IBM Corporation 2016. All rights reserved. The information contained in these materials is provided for informational purposes only, and is provided AS IS without warranty of any kind, express or implied. IBM shall not be responsible for any damages arising out of the use of, or otherwise related to, these materials. Nothing contained in these materials is intended to, nor shall have the effect of, creating any warranties or representations from IBM or its suppliers or licensors, or altering the terms and conditions of the applicable license agreement governing the use of IBM software. References in these materials to IBM products, programs, or services do not imply that they will be available in all countries in which IBM operates. Product release dates and / or capabilities referenced in these materials may change at any time at IBM’s sole discretion based on market opportunities or other factors, and are not intended to be a commitment to future product or feature availability in any way. IBM, the IBM logo, and other IBM products and services are trademarks of the International Business Machines Corporation, in the United States, other countries or both. Other company, product, or service names may be trademarks or service marks of others. Statement of Good Security Practices: IT system security involves protecting systems and information through prevention, detection and response to improper access from within and outside your enterprise. Improper access can result in information being altered, destroyed, misappropriated or misused or can result in damage to or misuse of your systems, including for use in attacks on others. No IT system or product should be considered completely secure and no single product, service or security measure can be completely effective in preventing improper use or access. IBM systems, products and services are designed to be part of a lawful, comprehensive security approach, which will necessarily involve additional operational procedures, and may require other systems, products or services to be most effective. IBM DOES NOT WARRANT THAT ANYSYSTEMS, PRODUCTS OR SERVICES ARE IMMUNE FROM, OR WILL MAKE YOUR ENTERPRISE IMMUNE FROM, THE MALICIOUS OR ILLEGAL CONDUCT OF ANY PARTY.