Hacking Defense 1 CS 478 CIS 678 Network






![Reconnaissance: Traceroute: Provides list of routers between source and destination To run: • [bash]$ Reconnaissance: Traceroute: Provides list of routers between source and destination To run: • [bash]$](https://slidetodoc.com/presentation_image/3ff9dd4da3b18ca8151fe9a89dd95392/image-12.jpg)
























- Slides: 65

Hacking & Defense 1 CS 478 /CIS 678 Network Security Dr. Susan Lincke

Network Security Hacking & Defense Part 1 Text: • Computer Security: Principles and Practice, W Stallings, L Brown • Chapter 12 Operating System Security Objectives: The student should be able to: • Define traceroute, ping sweep, port scanning, finger printing, man-in-the-middle, spoofing, directory traversal, SQL injection, Nessus, nmap, native virtualization, hosted virtualization • List 3 attacks and countermeasures for each of the hacking steps: 1) Footprint, 2) Scan/Enumerate, 3) Gain Access , and 4) Exploit (3 attacks only) • Describe the 3 major steps of hardening a computer. Explain the reason and methods of each of the steps. Class Time: Lecture: • Hacking • General Controls • Lab 1: Footprinting Total: 1 hour 1/2 hour 1 hour 2. 5 hours

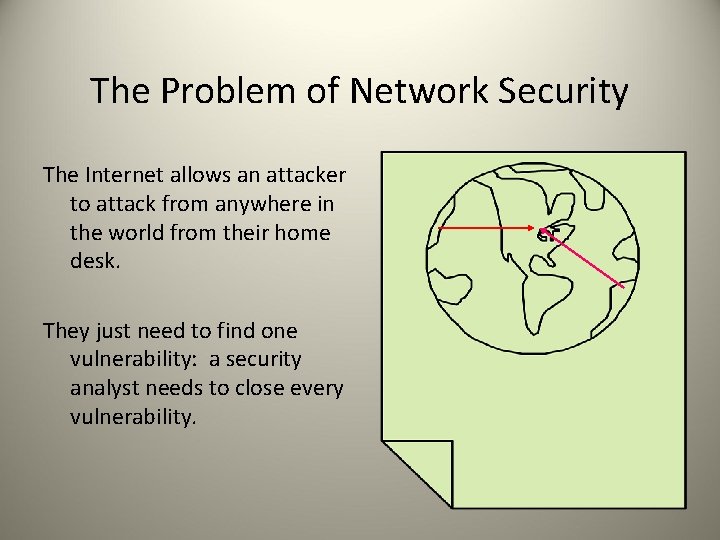
The Problem of Network Security The Internet allows an attacker to attack from anywhere in the world from their home desk. They just need to find one vulnerability: a security analyst needs to close every vulnerability.

Traditional Hacking The traditional way to break into a bank/museum/store include: 1. Reconnaissance or Footprint: – – – 2. 3. 4. When are the worst guards off duty? When are there fewest people? What is the lingo? Scan & Enumerate: – – Where are the goods? Is there a back door? Who is the person to contact for social engineering? Gain Access: – Break in Exploit: – – – Dig tunnel to have continual access Find out needed information: payment card or company secrets Establish good social engineering relationship to access further info.

Traditional Network Hacking The traditional way to hack into a system the steps include: 1. Reconnaissance: Get a big picture of what the network is 1 b. Initial break-in: Social Engineering: Phishing: establish base residence to… 2. Scan & Enumerate: Identify reachable hosts, services, OS/service versions 3. Gain Access: Break in 3 b. Establish persistence, hide tracks, escalate privileges 4. Exploit: Obtain information: payment card or corporate info; continual access

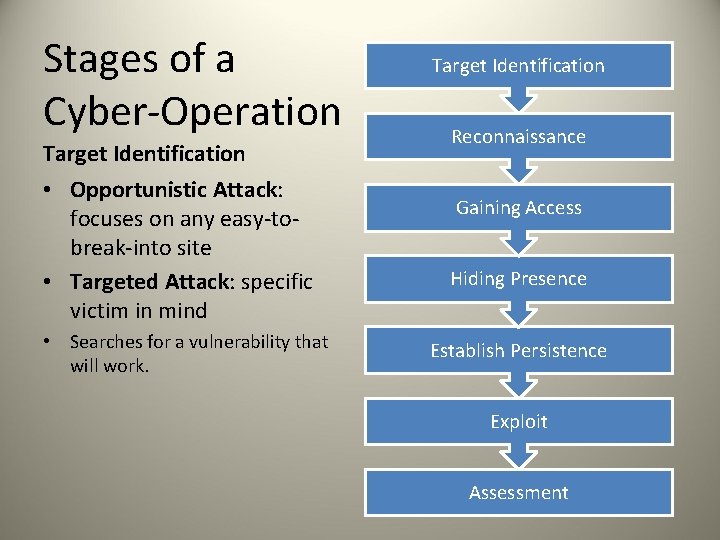
Stages of a Cyber-Operation Target Identification • Opportunistic Attack: focuses on any easy-tobreak-into site • Targeted Attack: specific victim in mind • Searches for a vulnerability that will work. Target Identification Reconnaissance Gaining Access Hiding Presence Establish Persistence Exploit Assessment

Hacking Networks Phase 1: Reconnaissance / Footprint • Physical Break-In • Dumpster Diving • Google, Newsgroups, Web sites • Who. Is Database & Sam Spade • Social Engineering • Domain Name Server Interrogations • Shoulder surfing “Hi Ann, This is Tom, the Admin. We are having a bad problem. What is your password? ” Registrant: Microsoft Corporation One Microsoft Way Redmond, WA 98052 US Domain name: MICROSOFT. COM Administrative Contact: Administrator, Domain domains@microsoft. com One Microsoft Way Redmond, WA 98052 US +1. 4258828080 Technical Contact: Hostmaster, MSN msnhst@microsoft. com One Microsoft Way Redmond, WA 98052 US +1. 4258828080 Registration Service Provider: DBMS Veri. Sign, dbms-support@verisign. com 800 -579 -2848 x 4 Please contact DBMS Veri. Sign for domain updates, DNS/Nameserver changes, and general domain support questions. Registrar of Record: TUCOWS, INC. Record last updated on 27 -Aug-2006. Record expires on 03 -May-2014. Record created on 02 -May-1991. Domain servers in listed order: NS 3. MSFT. NET 213. 199. 144. 151 NS 1. MSFT. NET 207. 68. 160. 190 NS 4. MSFT. NET 207. 46. 66. 126 NS 2. MSFT. NET 65. 54. 240. 126 NS 5. MSFT. NET 65. 55. 238. 126

Reconnaisance / Footprinting: Gather information about target. Stages include: • Determine scope of activity: What is out there & what does hacker hope to accomplish? • Search company web pages: locations, subsidiaries, contact names, phone numbers, email, privacy or security policies, links to organization’s other web servers. • Monitor HTML comment tags not publicly shown • Perform open-source searches for info on target: news, press releases • www. sec. gov EDGAR database lists publicly traded companies: recentlylisted or recently-acquired often vulnerable • Network Enumeration: Discover networks attached to the domains • Obtain information from whois databases • Identify domain names: ms. com and Microsoft. com • Network Reconnaissance: Learn network topology via DNS interrogation and network commands (e. g. , traceroute)

Network Reconnaissance: Learn network topology • DNS: Domain Name Server maps IP addresses to hostnames and vice versa – DNS Interrogation: Learn location of web, email, firewall servers – Zone transfers dump the contents of the DNS database to a secondary site (intention: backup site)

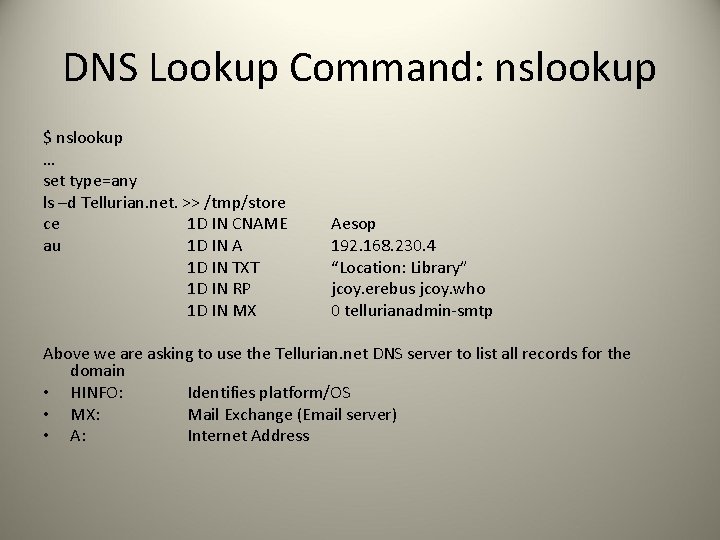
DNS Lookup Command: nslookup $ nslookup … set type=any ls –d Tellurian. net. >> /tmp/store ce 1 D IN CNAME au 1 D IN A 1 D IN TXT 1 D IN RP 1 D IN MX Aesop 192. 168. 230. 4 “Location: Library” jcoy. erebus jcoy. who 0 tellurianadmin-smtp Above we are asking to use the Tellurian. net DNS server to list all records for the domain • HINFO: Identifies platform/OS • MX: Mail Exchange (Email server) • A: Internet Address

DNS Controls To Guard Security: • Don’t give away information! • Exclude internal network information in external name servers • Eliminate HINFO records from name servers • Prevent or restrict zone transfers to authorized machines/users • Restrict access to internal DNS from outside • Disable inbound connections to TCP port 53: TCP zone transfer, UDP name lookups • UDP name lookups sent as TCP requests when > 512 bytes • Log inbound connections to port 53 to track potential attacks
![Reconnaissance Traceroute Provides list of routers between source and destination To run bash Reconnaissance: Traceroute: Provides list of routers between source and destination To run: • [bash]$](https://slidetodoc.com/presentation_image/3ff9dd4da3b18ca8151fe9a89dd95392/image-12.jpg)
Reconnaissance: Traceroute: Provides list of routers between source and destination To run: • [bash]$ traceroute cs. uwp. edu • [DOS]: tracert • Traceroute can be run from multiple locations to learn multiple entry points into network • How traceroute operates: – Traceroute uses ICMP_TIME_EXCEEDED messages – Windows: Uses ICMP echo request packet – UNIX: uses UDP or ICMP with –I option To Guard Security: • Do not permit pings from outside the network • Block ICMP and UDP at network edge (firewall or router) • Note: Blocking only ICMP or UDP may allow access, since both may be used • Detect attacks • Use IDS systems to detect traceroute requests • www. snort. org: Free IDS program detects these • Roto. Router: www. ussrback. com/UNIX/loggers/ rr. c. gz: generates fake responses to traceroutes.

Reconnaissance: Whois & Initial Break-in Whois provides information on: • Registrar: Sponsoring company • Organizational/Point of contact: Contact information Whois databases include: • www. whois. com Guard Security by: • Posting fictitious name in whois database • Keep contact information, contact registration in registry up-todate • Ensure secure access to registry (AOL was defrauded in 1998) • Guard personnel books

Initial Break-in: 1 b: Social Engineering Attacks Social Engineering: break into company via human interface – via phone or email • Poses as a trusted user, manager, admin Phishing: sending an email pretending to be someone else Water Hole: Infected website infects visitors. Shoulder surfing: Reads terminal info by looking over someone’s shoulder • Reading login/passwords or other confidential info Tailgating: Passing an ID check point by walking out of view of the guard with others Goal: Establish a hold internal to the network • Launch attacks from internal network

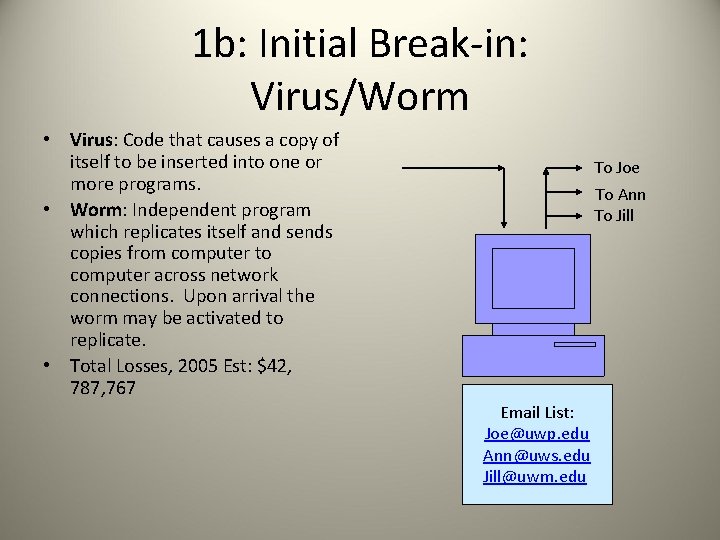
1 b: Initial Break-in: Virus/Worm • Virus: Code that causes a copy of itself to be inserted into one or more programs. • Worm: Independent program which replicates itself and sends copies from computer to computer across network connections. Upon arrival the worm may be activated to replicate. • Total Losses, 2005 Est: $42, 787, 767 To Joe To Ann To Jill Email List: Joe@uwp. edu Ann@uws. edu Jill@uwm. edu

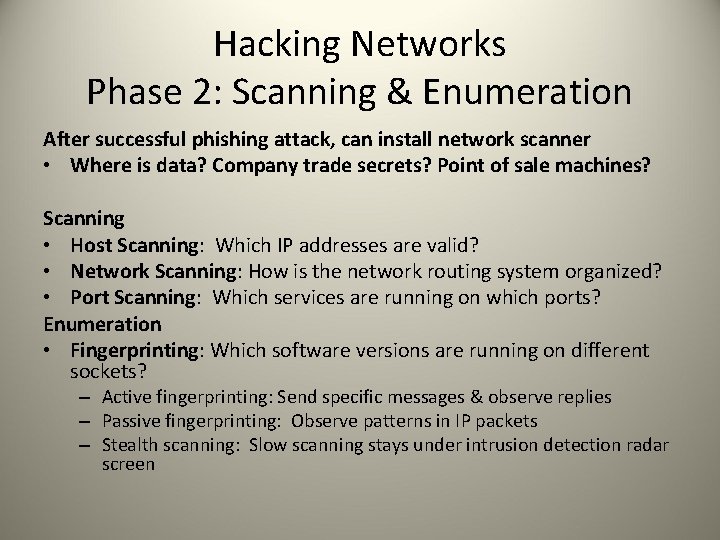
Hacking Networks Phase 2: Scanning & Enumeration After successful phishing attack, can install network scanner • Where is data? Company trade secrets? Point of sale machines? Scanning • Host Scanning: Which IP addresses are valid? • Network Scanning: How is the network routing system organized? • Port Scanning: Which services are running on which ports? Enumeration • Fingerprinting: Which software versions are running on different sockets? – Active fingerprinting: Send specific messages & observe replies – Passive fingerprinting: Observe patterns in IP packets – Stealth scanning: Slow scanning stays under intrusion detection radar screen

2: Hacking Networks: Scanning & Enumeration: Scanning Tools • War Driving: Net. Stumbler • War Dialing: Dialing numbers looking for modems • Network Mapping: Nmap • Vulnerability-Scanning Tools: Nessus

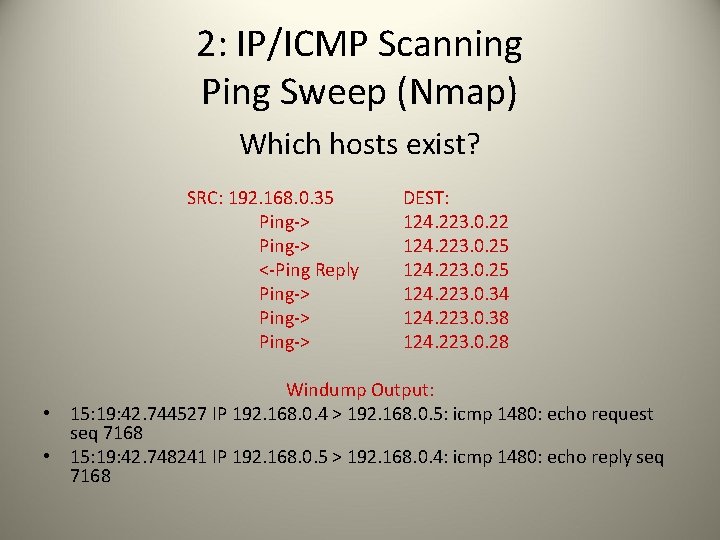
2: IP/ICMP Scanning Ping Sweep (Nmap) Which hosts exist? SRC: 192. 168. 0. 35 Ping-> <-Ping Reply Ping-> DEST: 124. 223. 0. 22 124. 223. 0. 25 124. 223. 0. 34 124. 223. 0. 38 124. 223. 0. 28 Windump Output: • 15: 19: 42. 744527 IP 192. 168. 0. 4 > 192. 168. 0. 5: icmp 1480: echo request seq 7168 • 15: 19: 42. 748241 IP 192. 168. 0. 5 > 192. 168. 0. 4: icmp 1480: echo reply seq 7168

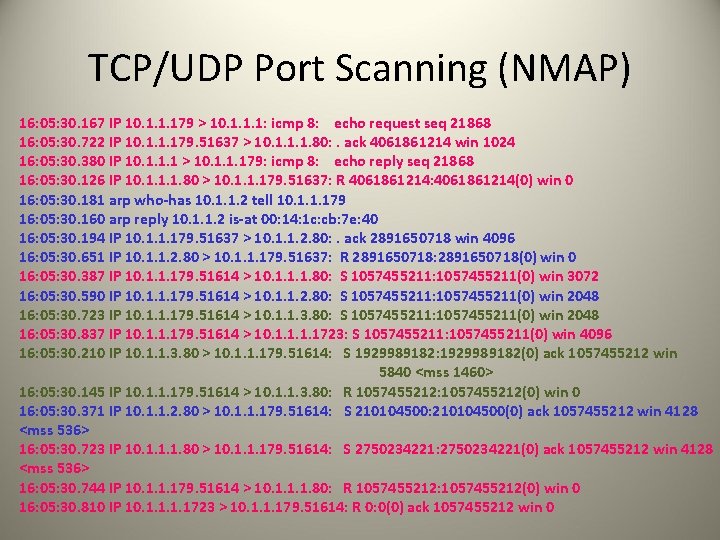
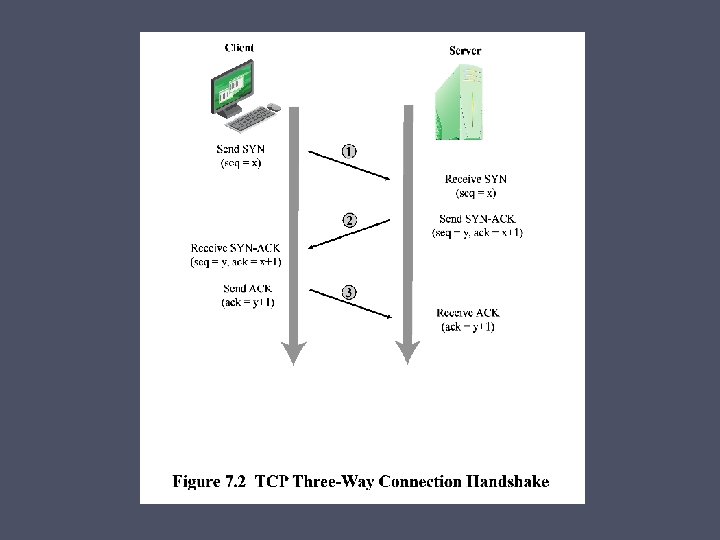
2: Which ports exist? Initiate a TCP connection: SYN, ACK Windump of establish connection: • 14: 50. 191132 IP 192. 168. 0. 4. 1226 > 192. 168. 0. 5. 23: S 262694098: 262694098(0) win 16384 (DF) • 14: 50. 192200 IP 192. 168. 0. 5. 23 > 192. 168. 0. 4. 1226: S 116356462: 116356462(0) ack 262694099 win 17520 (DF) • 14: 50. 192249 IP 192. 168. 0. 4. 1226 > 192. 168. 0. 5. 23: . ack 1 win 17520 (DF)

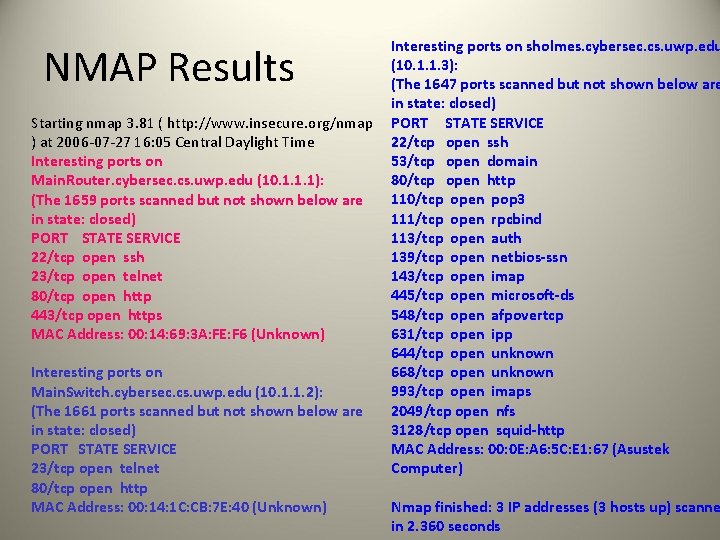
TCP/UDP Port Scanning (NMAP) 16: 05: 30. 167 IP 10. 1. 1. 179 > 10. 1. 1. 1: icmp 8: echo request seq 21868 16: 05: 30. 722 IP 10. 1. 1. 179. 51637 > 10. 1. 1. 1. 80: . ack 4061861214 win 1024 16: 05: 30. 380 IP 10. 1. 1. 1 > 10. 1. 1. 179: icmp 8: echo reply seq 21868 16: 05: 30. 126 IP 10. 1. 1. 1. 80 > 10. 1. 1. 179. 51637: R 4061861214: 4061861214(0) win 0 16: 05: 30. 181 arp who-has 10. 1. 1. 2 tell 10. 1. 1. 179 16: 05: 30. 160 arp reply 10. 1. 1. 2 is-at 00: 14: 1 c: cb: 7 e: 40 16: 05: 30. 194 IP 10. 1. 1. 179. 51637 > 10. 1. 1. 2. 80: . ack 2891650718 win 4096 16: 05: 30. 651 IP 10. 1. 1. 2. 80 > 10. 1. 1. 179. 51637: R 2891650718: 2891650718(0) win 0 16: 05: 30. 387 IP 10. 1. 1. 179. 51614 > 10. 1. 1. 1. 80: S 1057455211: 1057455211(0) win 3072 16: 05: 30. 590 IP 10. 1. 1. 179. 51614 > 10. 1. 1. 2. 80: S 1057455211: 1057455211(0) win 2048 16: 05: 30. 723 IP 10. 1. 1. 179. 51614 > 10. 1. 1. 3. 80: S 1057455211: 1057455211(0) win 2048 16: 05: 30. 837 IP 10. 1. 1. 179. 51614 > 10. 1. 1723: S 1057455211: 1057455211(0) win 4096 16: 05: 30. 210 IP 10. 1. 1. 3. 80 > 10. 1. 1. 179. 51614: S 1929989182: 1929989182(0) ack 1057455212 win 5840 <mss 1460> 16: 05: 30. 145 IP 10. 1. 1. 179. 51614 > 10. 1. 1. 3. 80: R 1057455212: 1057455212(0) win 0 16: 05: 30. 371 IP 10. 1. 1. 2. 80 > 10. 1. 1. 179. 51614: S 210104500: 210104500(0) ack 1057455212 win 4128 <mss 536> 16: 05: 30. 723 IP 10. 1. 1. 1. 80 > 10. 1. 1. 179. 51614: S 2750234221: 2750234221(0) ack 1057455212 win 4128 <mss 536> 16: 05: 30. 744 IP 10. 1. 1. 179. 51614 > 10. 1. 1. 1. 80: R 1057455212: 1057455212(0) win 0 16: 05: 30. 810 IP 10. 1. 1723 > 10. 1. 1. 179. 51614: R 0: 0(0) ack 1057455212 win 0

Interesting ports on sholmes. cybersec. cs. uwp. edu (10. 1. 1. 3): (The 1647 ports scanned but not shown below are in state: closed) Starting nmap 3. 81 ( http: //www. insecure. org/nmap PORT STATE SERVICE 22/tcp open ssh ) at 2006 -07 -27 16: 05 Central Daylight Time 53/tcp open domain Interesting ports on 80/tcp open http Main. Router. cybersec. cs. uwp. edu (10. 1. 1. 1): 110/tcp open pop 3 (The 1659 ports scanned but not shown below are 111/tcp open rpcbind in state: closed) 113/tcp open auth PORT STATE SERVICE 139/tcp open netbios-ssn 22/tcp open ssh 143/tcp open imap 23/tcp open telnet 445/tcp open microsoft-ds 80/tcp open http 548/tcp open afpovertcp 443/tcp open https 631/tcp open ipp MAC Address: 00: 14: 69: 3 A: FE: F 6 (Unknown) 644/tcp open unknown 668/tcp open unknown Interesting ports on 993/tcp open imaps Main. Switch. cybersec. cs. uwp. edu (10. 1. 1. 2): 2049/tcp open nfs (The 1661 ports scanned but not shown below are 3128/tcp open squid-http in state: closed) MAC Address: 00: 0 E: A 6: 5 C: E 1: 67 (Asustek PORT STATE SERVICE Computer) 23/tcp open telnet 80/tcp open http Nmap finished: 3 IP addresses (3 hosts up) scanne MAC Address: 00: 14: 1 C: CB: 7 E: 40 (Unknown) in 2. 360 seconds NMAP Results

Scan Types TCP connect scan: Performs 3 -way handshake TCP SYN: SYN/ACK TCP FIN: FIN RST (UNIX) TCP Xmas. Tree scan: FIN/URG/PUSH RST TCP Null: no flags RST TCP ACK: ACK Is firewall stateful? TCP Windows: Identify system via window size reporting • TCP RCP: Identify RCP ports, program names and version numbers • UDP Scan: If inactive ICMP port unreachable • •

Scanner - Controls To Guard Security: • Detect attack • Detect ping sweeps and incoming ICMP traffic for port scans via IDS/IPS • Identify attacker and possible time of attack • Prevent attacks • Filter all incoming sessions from ports except those that are expressly permitted • Filter traffic from attack source IP addresses • Filter all ICMP traffic or – Filter ICMP TIMESTAMP and ADDRESS MASK packet requests • Minimal: Allow ECHO_REPLY, HOST_UNREACHABLE, TIME_EXCEEDED into demilitarized zone (DMZ)

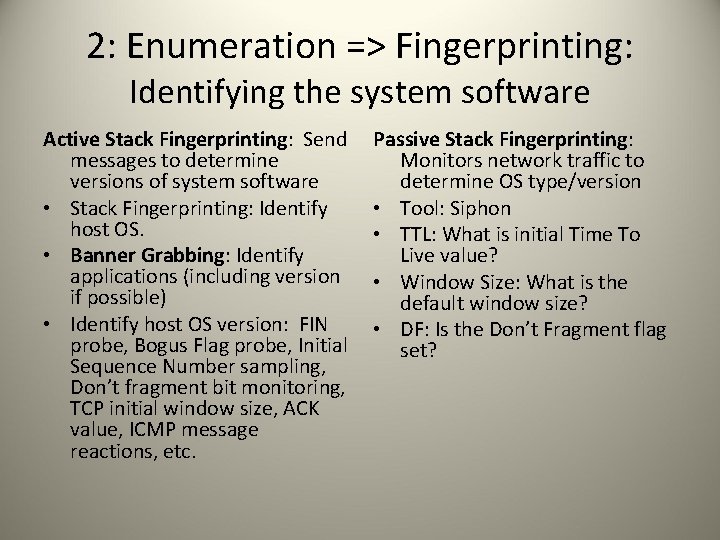
2: Enumeration => Fingerprinting: Identifying the system software Active Stack Fingerprinting: Send messages to determine versions of system software • Stack Fingerprinting: Identify host OS. • Banner Grabbing: Identify applications (including version if possible) • Identify host OS version: FIN probe, Bogus Flag probe, Initial Sequence Number sampling, Don’t fragment bit monitoring, TCP initial window size, ACK value, ICMP message reactions, etc. Passive Stack Fingerprinting: Monitors network traffic to determine OS type/version • Tool: Siphon • TTL: What is initial Time To Live value? • Window Size: What is the default window size? • DF: Is the Don’t Fragment flag set?

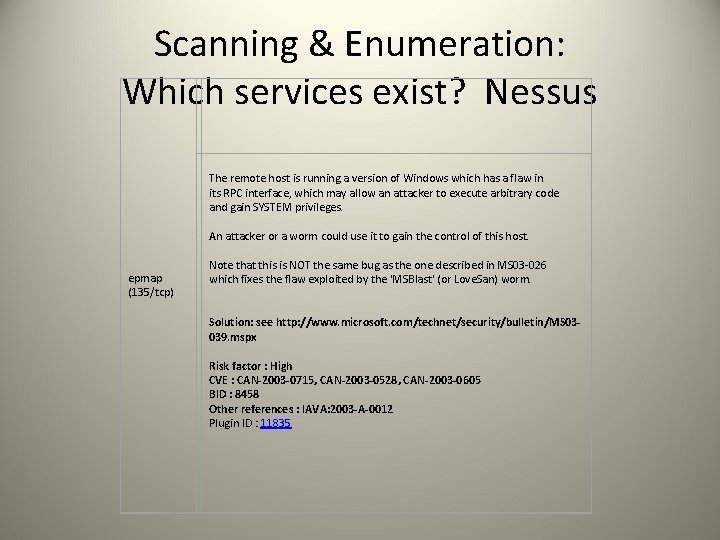
Scanning & Enumeration: Which services exist? Nessus The remote host is running a version of Windows which has a flaw in its RPC interface, which may allow an attacker to execute arbitrary code and gain SYSTEM privileges. An attacker or a worm could use it to gain the control of this host. epmap (135/tcp) Note that this is NOT the same bug as the one described in MS 03 -026 which fixes the flaw exploited by the 'MSBlast' (or Love. San) worm. Solution: see http: //www. microsoft. com/technet/security/bulletin/MS 03039. mspx Risk factor : High CVE : CAN-2003 -0715, CAN-2003 -0528, CAN-2003 -0605 BID : 8458 Other references : IAVA: 2003 -A-0012 Plugin ID : 11835

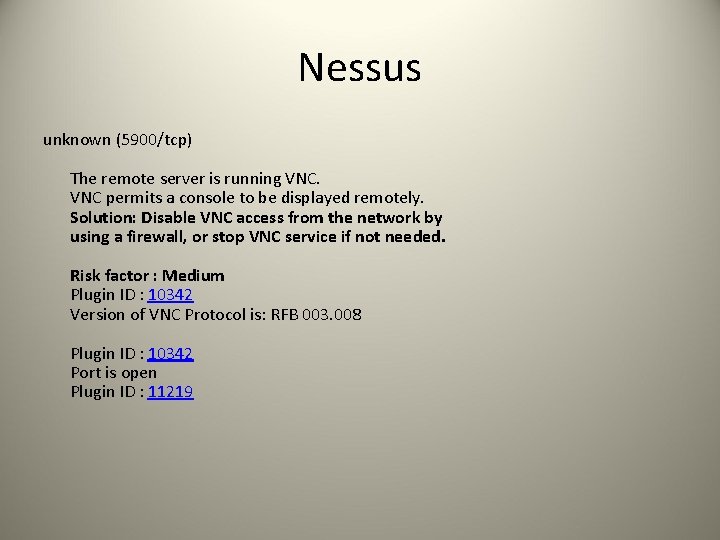
Nessus unknown (5900/tcp) The remote server is running VNC permits a console to be displayed remotely. Solution: Disable VNC access from the network by using a firewall, or stop VNC service if not needed. Risk factor : Medium Plugin ID : 10342 Version of VNC Protocol is: RFB 003. 008 Plugin ID : 10342 Port is open Plugin ID : 11219

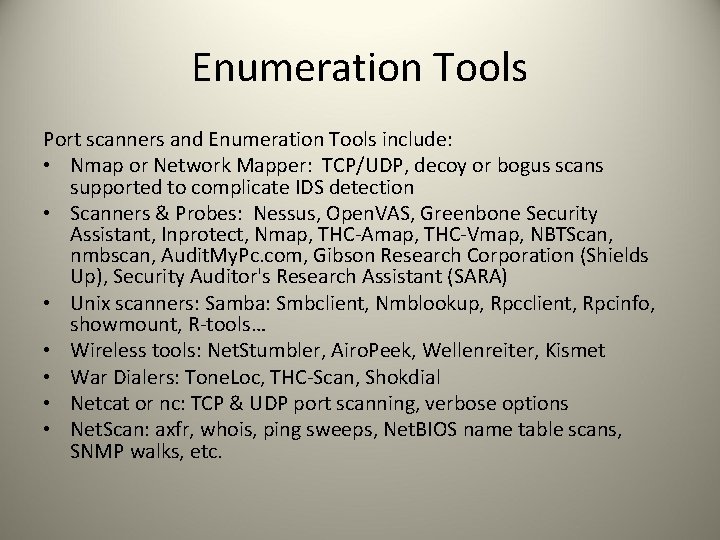
Enumeration Tools Port scanners and Enumeration Tools include: • Nmap or Network Mapper: TCP/UDP, decoy or bogus scans supported to complicate IDS detection • Scanners & Probes: Nessus, Open. VAS, Greenbone Security Assistant, Inprotect, Nmap, THC-Amap, THC-Vmap, NBTScan, nmbscan, Audit. My. Pc. com, Gibson Research Corporation (Shields Up), Security Auditor's Research Assistant (SARA) • Unix scanners: Samba: Smbclient, Nmblookup, Rpcclient, Rpcinfo, showmount, R-tools… • Wireless tools: Net. Stumbler, Airo. Peek, Wellenreiter, Kismet • War Dialers: Tone. Loc, THC-Scan, Shokdial • Netcat or nc: TCP & UDP port scanning, verbose options • Net. Scan: axfr, whois, ping sweeps, Net. BIOS name table scans, SNMP walks, etc.

Enumeration Controls To Guard Security: • Evaluate computer from the inside • Enumeration tools help the administrator to determine available services and evaluate vulnerabilities – MS Baseline Security Analyzer (MBSA) – NESSUS • Evaluate computer from the outside • Scan to find unnecessary services from outside FW – Can use nmap or www. grc. com (Leak. Test) to scan your own machine or network • Disable all unnecessary services – UNIX: comment out unnecessary services in /etc/inetd. conf – WINDOWS: Disable services via Control Panel/Services

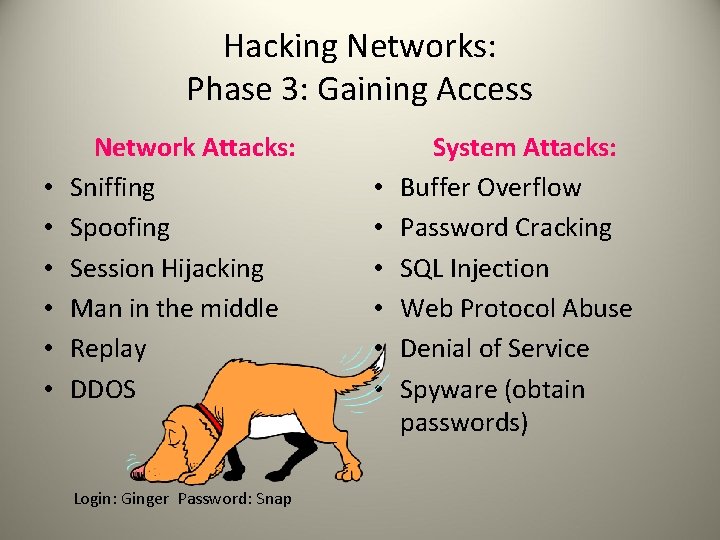
Hacking Networks: Phase 3: Gaining Access • • • Network Attacks: Sniffing Spoofing Session Hijacking Man in the middle Replay DDOS Login: Ginger Password: Snap • • • System Attacks: Buffer Overflow Password Cracking SQL Injection Web Protocol Abuse Denial of Service Spyware (obtain passwords)

3. Gaining Access: System Attacks… Buffer Overflows • Overflowing input buffers to corrupt system stack and cause code execution with intention of gaining access. • Requires zero privilege • Can exploit any node. Directory Traversal • Using www. cs. uwp. edu/. . /cmd. exe Password Attacks: • Automatically guessing passwords SQL Injection

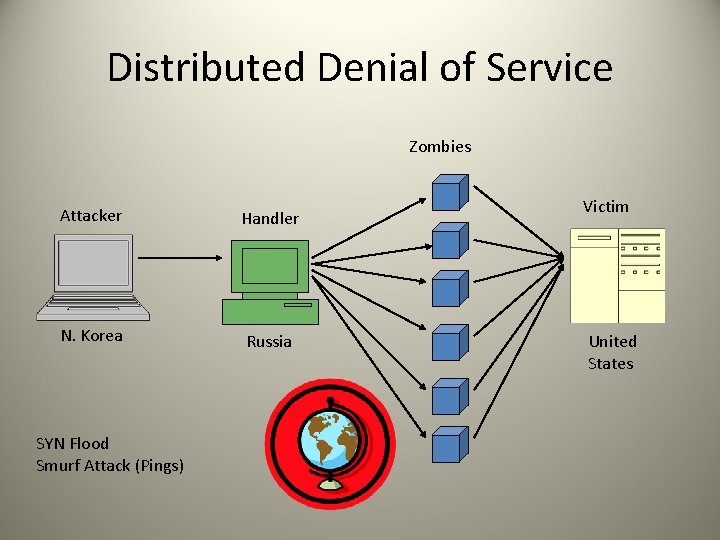
3. Gaining Access: Network Attacks • Distributed Denial of Service: Zombies attack one victim. • Spoofing: Pretending to be another network node (e. g. , IP, MAC, email spoofing) • Man in the Middle: Insert oneself between two communicating nodes: a form of spoofing • Sniffing or Eavesdropping: e. g. , Wireshark • Replay: Capture a packet and resend it • DNS Poisoning: Giving DNS false addresses; providing false information: e. g. , ARP poisoning • Session Hijacking: Generating fake packets to alter communication between two points

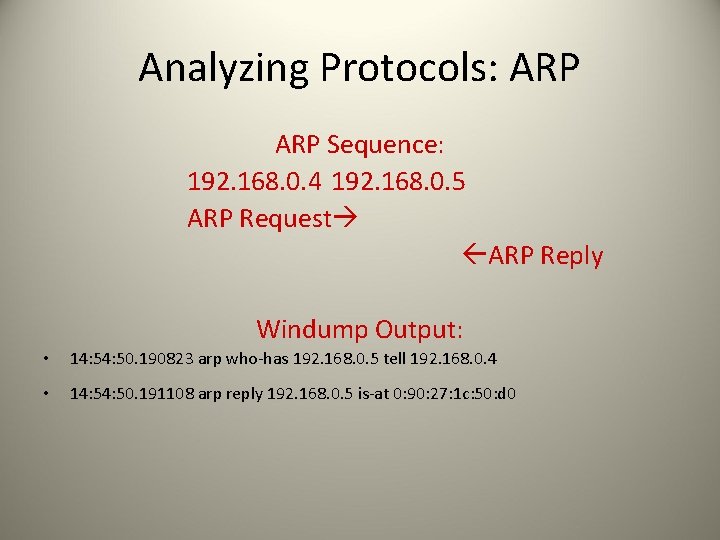
Analyzing Protocols: ARP Sequence: 192. 168. 0. 4 192. 168. 0. 5 ARP Request ARP Reply Windump Output: • 14: 50. 190823 arp who-has 192. 168. 0. 5 tell 192. 168. 0. 4 • 14: 50. 191108 arp reply 192. 168. 0. 5 is-at 0: 90: 27: 1 c: 50: d 0

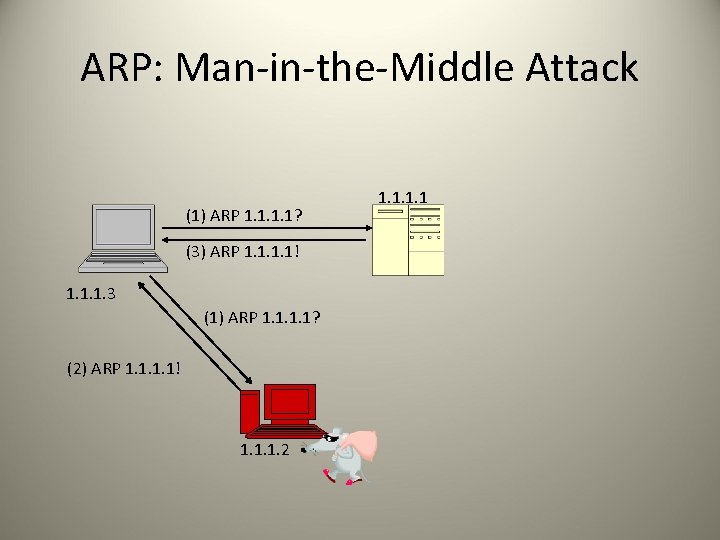
ARP: Man-in-the-Middle Attack (1) ARP 1. 1? (3) ARP 1. 1! 1. 1. 1. 3 (1) ARP 1. 1? (2) ARP 1. 1! 1. 1. 1. 2 1. 1

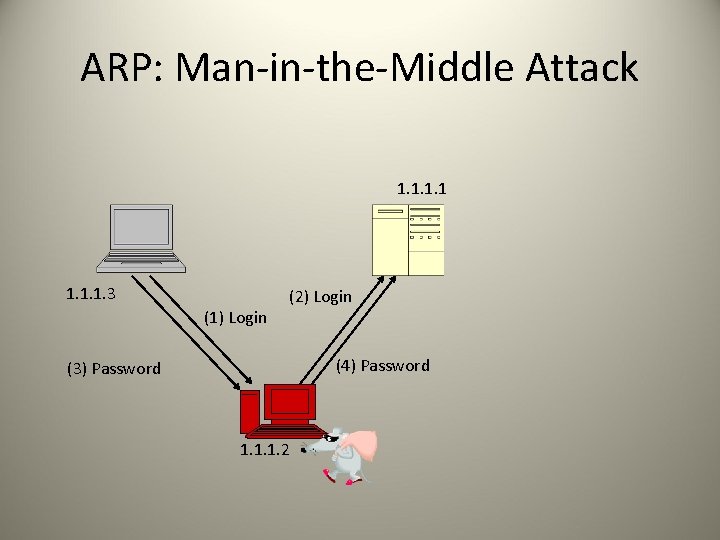
ARP: Man-in-the-Middle Attack 1. 1. 3 (1) Login (2) Login (4) Password (3) Password 1. 1. 1. 2

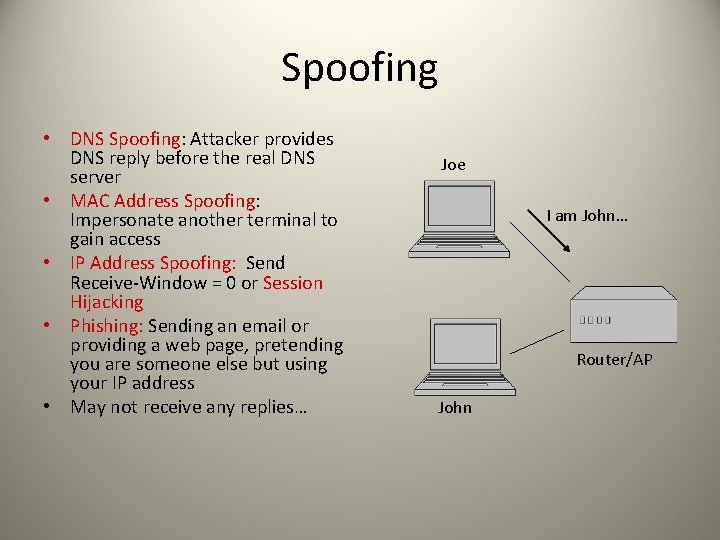
Spoofing • DNS Spoofing: Attacker provides DNS reply before the real DNS server • MAC Address Spoofing: Impersonate another terminal to gain access • IP Address Spoofing: Send Receive-Window = 0 or Session Hijacking • Phishing: Sending an email or providing a web page, pretending you are someone else but using your IP address • May not receive any replies… Joe I am John… Router/AP John

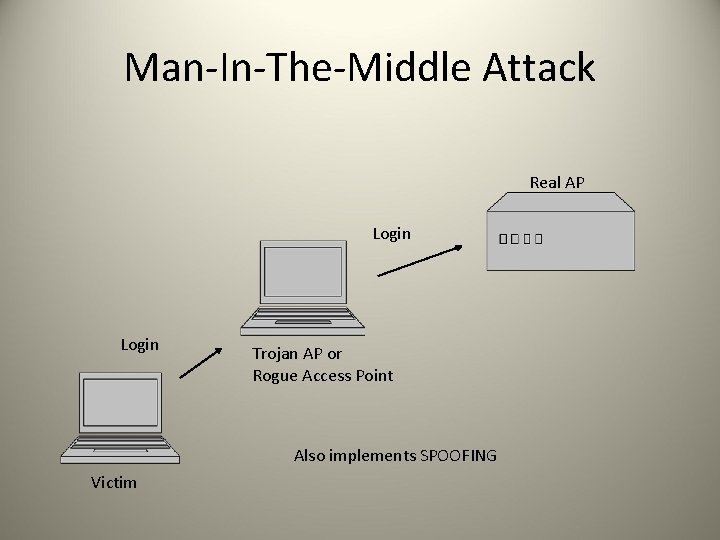
Man-In-The-Middle Attack Real AP Login Trojan AP or Rogue Access Point Also implements SPOOFING Victim

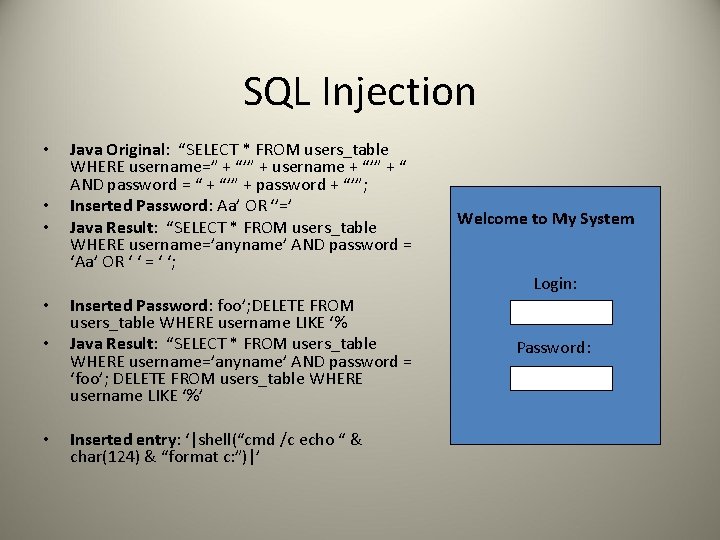
SQL Injection • • • Java Original: “SELECT * FROM users_table WHERE username=” + “’” + username + “’” + “ AND password = “ + “’” + password + “’”; Inserted Password: Aa’ OR ‘’=’ Java Result: “SELECT * FROM users_table WHERE username=’anyname’ AND password = ‘Aa’ OR ‘ ‘ = ‘ ‘; • Inserted Password: foo’; DELETE FROM users_table WHERE username LIKE ‘% Java Result: “SELECT * FROM users_table WHERE username=’anyname’ AND password = ‘foo’; DELETE FROM users_table WHERE username LIKE ‘%’ • Inserted entry: ‘|shell(“cmd /c echo “ & char(124) & “format c: ”)|’ • Welcome to My System Login: Password:

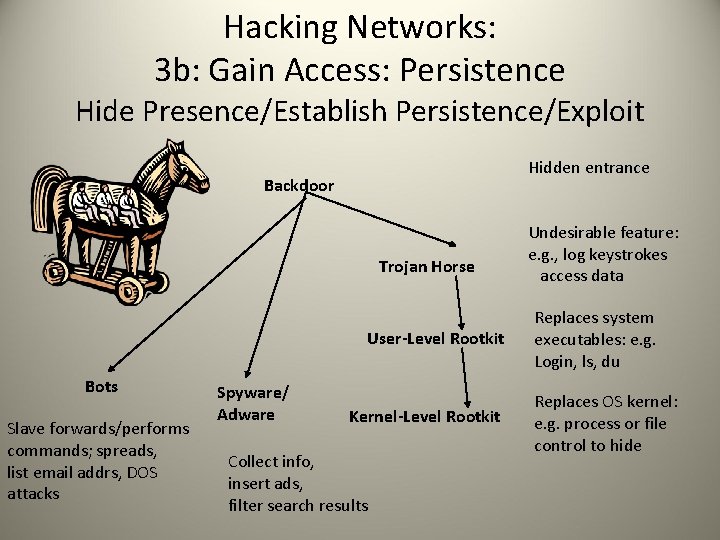
Hacking Networks: 3 b: Gain Access: Persistence Hide Presence/Establish Persistence/Exploit Hidden entrance Backdoor Trojan Horse User-Level Rootkit Bots Slave forwards/performs commands; spreads, list email addrs, DOS attacks Spyware/ Adware Kernel-Level Rootkit Collect info, insert ads, filter search results Undesirable feature: e. g. , log keystrokes access data Replaces system executables: e. g. Login, ls, du Replaces OS kernel: e. g. process or file control to hide

3 b: Gaining Access: Persistence Establish Persistence/Hide Presence Escalation of Privileges: • Password Guessing • Keystroke Logger: Learn passwords • Exploit known vulnerabilities of software • Session Hijacking: Take over existing session After Break-In: • Create backdoors for reentry • Weaken security • Hide tracks: Delete logs

Gaining Access: Auditing Checks: • Be careful of false positives and false negatives! • Slow responses can result in negative (wrong) conclusion • Vulnerabilities may be eligible only if combined with a particular version of OS • Vulnerability tests can have bugs • A vulnerability may exist – but the context may not exist for the application • Specific network h/w may impact test (e. g. , load balancing, firewall proxies) Therefore: • Use two tools to test! • Determine if vulnerability exist in context of OS, applications, etc. • Treat information as confidential

Exploit: • Exfiltrate data: corporate secrets, payment card info • Launch DOS/DDOS attacks • Web defacement • Establish continual access STAGE 4: EXPLOIT

Distributed Denial of Service Zombies Attacker Handler N. Korea Russia SYN Flood Smurf Attack (Pings) Victim United States




DNS Amplification Attacks • Use packets directed at a legitimate DNS server as the intermediary system • Attacker creates a series of DNS requests containing the spoofed source address of the target system • Exploit DNS behavior to convert a small request to a much larger response (amplification) • • Target is flooded with responses Basic defense against this attack is to prevent the use of spoofed source addresses

A Few…. GENERAL CONTROLS

Key security mechanisms • Maximize software security – Patch OS, applications, 3 rd Party applications with autoupdate – Configure security settings carefully • Restrict access – Restrict admin privileges – Disable unnecessary accounts – Password controls • Restrict number of services – White-list approved applications – Uninstall or disable unnecessary services

Plan to Maximize Security Design security into the system • Security in Requirements • Authentication & Access Control • Configure properly first time Careful administration • Logs, synchronized clocks • Local/remote management

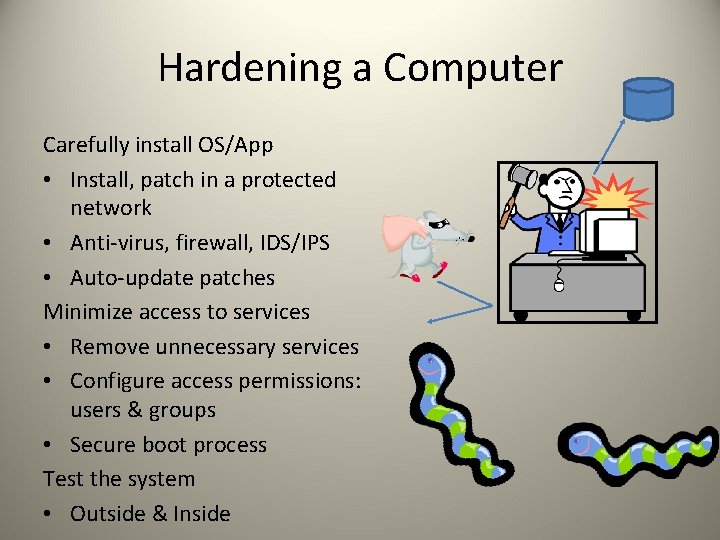
Hardening a Computer Carefully install OS/App • Install, patch in a protected network • Anti-virus, firewall, IDS/IPS • Auto-update patches Minimize access to services • Remove unnecessary services • Configure access permissions: users & groups • Secure boot process Test the system • Outside & Inside

Install Additional Security Controls • Anti-virus software – Also for smart-phones • IDS/IPS: traffic monitoring, file integrity checking (tripwire) • Firewall: Can restrict input to certain ports, or protocols • Check for rogue machines, systems • Whitelist applications (if possible) – Only certain set of executables may run

Remove Unnecessary Services • If every app has 1 vulnerability, then fewer apps are better • Remove unnecessary services – – Customize installation Remove OS services and capabilities Balance between usability & security Remove, don’t disable • Restrict account access – Restrict default accounts – Change default passwords • Minimize access to existing services – Restrict elevated privileges – Use elevated privileges minimally – Log privileged actions GUEST

Securing Applications • Install in protected network • Limit permissions – Web application should have minimal permissions – Permissions can be increased for certain actions – Set file permissions for administrator versus web user • UNIX Chroot jail limits file system access • Set security settings: logs, account lockout, password, banners • Add controls as necessary: Encryption, digital certificate

Security Maintenance • Monitor log information – Detective technique catches after-the-fact – System, network, application – Allocate sufficient space, best off-line • Perform regular backups – Archive: retain copies of data over time – Off-site storage works for fires, disasters, on-site thief • Regularly test system security – Automate: daily tests, hourly, every 10 minutes • Patch & update critical software • Recover from Security compromises

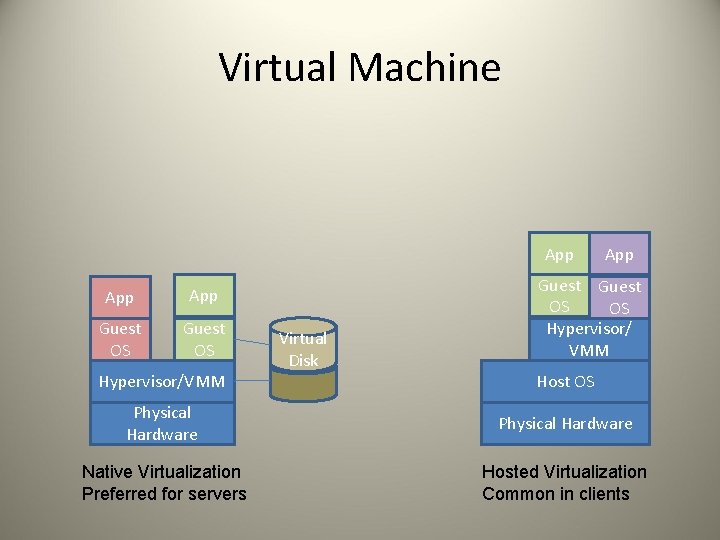
Virtual Machine App App Guest OS Hypervisor/VMM Virtual Disk App Guest OS OS Hypervisor/ VMM Host OS Physical Hardware Native Virtualization Preferred for servers Hosted Virtualization Common in clients

Virtual Machine Security • Plan for security: Each VM is one isolated function • Secure host system, hypervisor, guest OSes, guest applications • Restrict administrator access to the virtualized solution

From: Hacking Exposed: Network Security Secrets & Solutions A Few…. SPECIFIC APPLICATIONS ONLY LET IN SPECIFICALLY PERMITTED APPLICATIONS WHY ARE SOME PORTS IMPORTANT TO CLOSE?

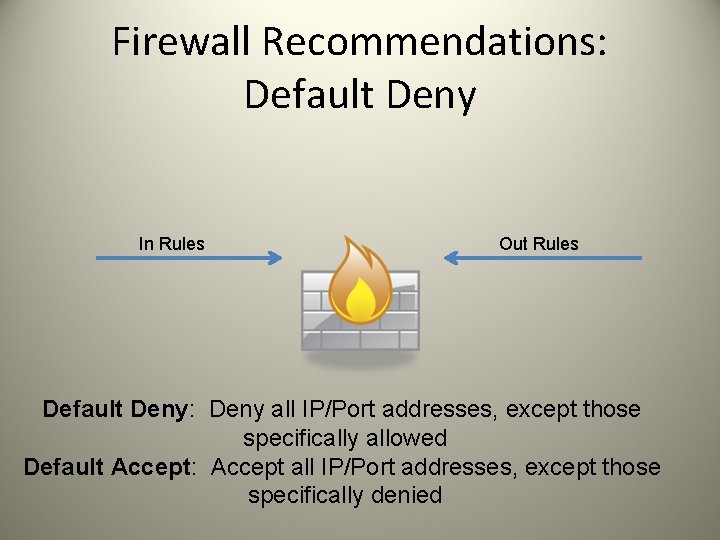
Firewall Recommendations: Default Deny In Rules Out Rules Default Deny: Deny all IP/Port addresses, except those specifically allowed Default Accept: Accept all IP/Port addresses, except those specifically denied

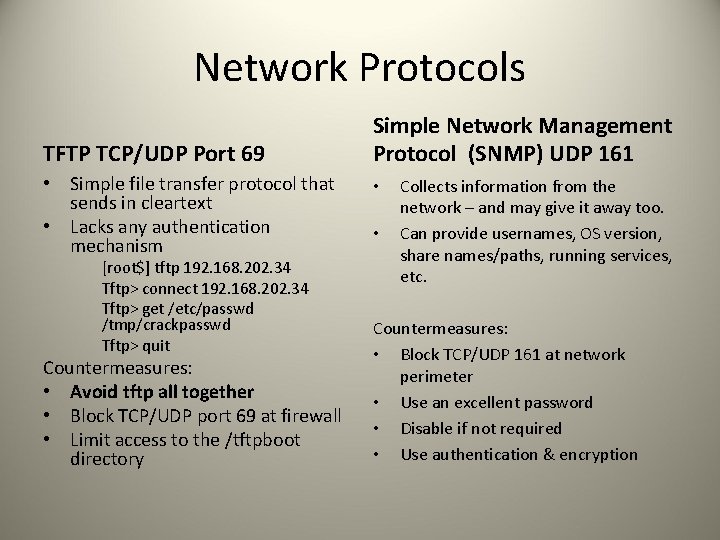
Network Protocols TFTP TCP/UDP Port 69 • Simple file transfer protocol that sends in cleartext • Lacks any authentication mechanism [root$] tftp 192. 168. 202. 34 Tftp> connect 192. 168. 202. 34 Tftp> get /etc/passwd /tmp/crackpasswd Tftp> quit Countermeasures: • Avoid tftp all together • Block TCP/UDP port 69 at firewall • Limit access to the /tftpboot directory Simple Network Management Protocol (SNMP) UDP 161 • • Collects information from the network – and may give it away too. Can provide usernames, OS version, share names/paths, running services, etc. Countermeasures: • Block TCP/UDP 161 at network perimeter • Use an excellent password • Disable if not required • Use authentication & encryption

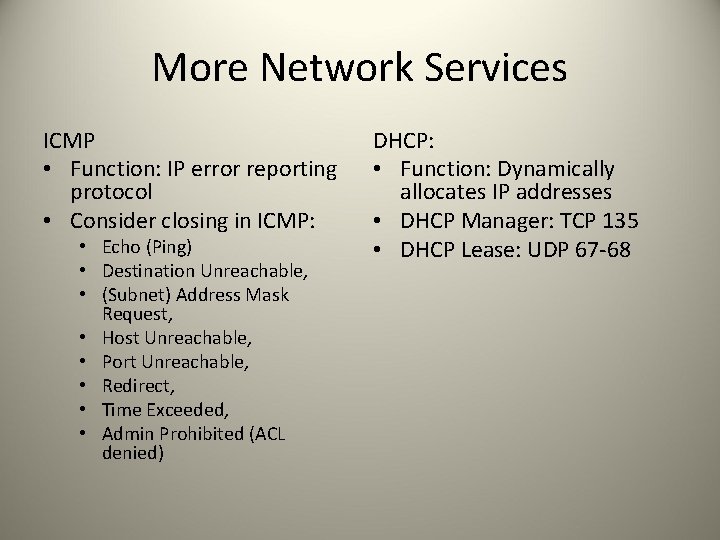
More Network Services ICMP • Function: IP error reporting protocol • Consider closing in ICMP: • Echo (Ping) • Destination Unreachable, • (Subnet) Address Mask Request, • Host Unreachable, • Port Unreachable, • Redirect, • Time Exceeded, • Admin Prohibited (ACL denied) DHCP: • Function: Dynamically allocates IP addresses • DHCP Manager: TCP 135 • DHCP Lease: UDP 67 -68

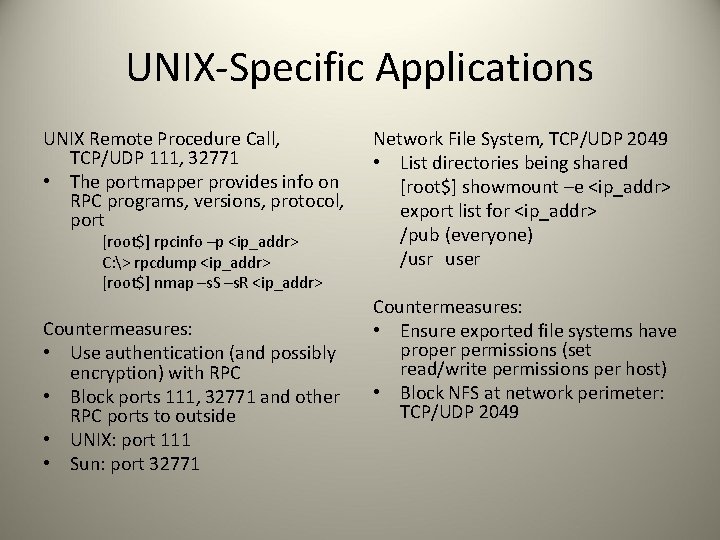
UNIX-Specific Applications UNIX Remote Procedure Call, TCP/UDP 111, 32771 • The portmapper provides info on RPC programs, versions, protocol, port [root$] rpcinfo –p <ip_addr> C: > rpcdump <ip_addr> [root$] nmap –s. S –s. R <ip_addr> Countermeasures: • Use authentication (and possibly encryption) with RPC • Block ports 111, 32771 and other RPC ports to outside • UNIX: port 111 • Sun: port 32771 Network File System, TCP/UDP 2049 • List directories being shared [root$] showmount –e <ip_addr> export list for <ip_addr> /pub (everyone) /usr user Countermeasures: • Ensure exported file systems have proper permissions (set read/write permissions per host) • Block NFS at network perimeter: TCP/UDP 2049

Windows-Specific Applications After Windows 2000: • Domain Name Server (DNS): UDP 53 • Lightweight Directory Access Protocol (LDAP): Selecting My Network Places to search to in Active Directory Server – TCP/UDP 389; TCP port 3268 – TCP 3269: Global Catalog – TCP 636: LDAP SSL • Server Message Block (SMB) Direct Hosting: Working with a service within My Network Places (e. g. , print): TCP port 445 (older: 137 -139) • Kerberos: Encrypted Authentication: TCP/UDP 88. – TCP/UDP 464 – TCP 544: KShell

Surely Port 80 & 443 should be kept open? We have webpages encrypted (port 443) and unencrypted (port 80). We leave these open. • Crackers know port 80 & 443 are usually open • Malware can use these ports to get in (command & control, botnets) • So… which servers serve web pages? Permit for them only (encrypted/unencrypted) • Clients should not have ports 80 & 443 open

Additional Resources • SANS has webcasts, documents, news – https: //www. sans. org/security-resources/ • US National Institute of Standards and Technology (NIST) – https: //www. nist. gov/topics/information-technology • Web pages for MS Windows for security tools, checklists, and guides: – www. microsoft. com/en-us/security/default. aspx • Recognize Trojans – Close off all ports used by Trojan horses: – Port 80 (web) can also be used by trojans and other applications when their normal port is closed

Summary of Controls Vendor-Independent Controls to Minimize Security Risks • Filter incoming connections for all ports, except those that are needed • Build machines – OS, Applications – in a controlled environment • Ensure machines run minimal services • Run software with patches installed – auto-update patches • Restrict access to services (data, configuration files) based on need • Display warnings against trespassing • Collect and monitor logs via remote server (login attempts, changes in permissions, accounts, or log/audit settings, file/printer accesses, etc. ) • Ensure remote administration uses strong authentication and encryption controls • Partition services and hardware in network to maximize security • Use IDS/IPS to detect attack patterns