Ethical Hacking 9182021 Ethical Hacking Why Ethical Hacking










- Slides: 21

Ethical Hacking 9/18/2021 !@ #

Ethical Hacking - ? Why – Ethical Hacking ? Ethical Hacking - Process Reporting Ethical Hacking – Commandments 2 9/18/2021 !@ #

What is Ethical Hacking Also Called – Attack & Penetration Testing, White-hat hacking, Red teaming Hacking Process of breaking into systems for: §Personal or Commercial Gains §Malicious Intent – Causing sever damage to Information & Assets Ethical Conforming to accepted professional standards of conduct Black-hat – Bad guys 3 9/18/2021 White-hat - Good Guys !@ #

What is Ethical Hacking p p p 4 It is Legal Permission is obtained from the target Part of an overall security program Identify vulnerabilities visible from Internet at particular point of time Ethical hackers possesses same skills, mindset and tools of a hacker but the attacks are done in a non-destructive manner 9/18/2021 !@ #

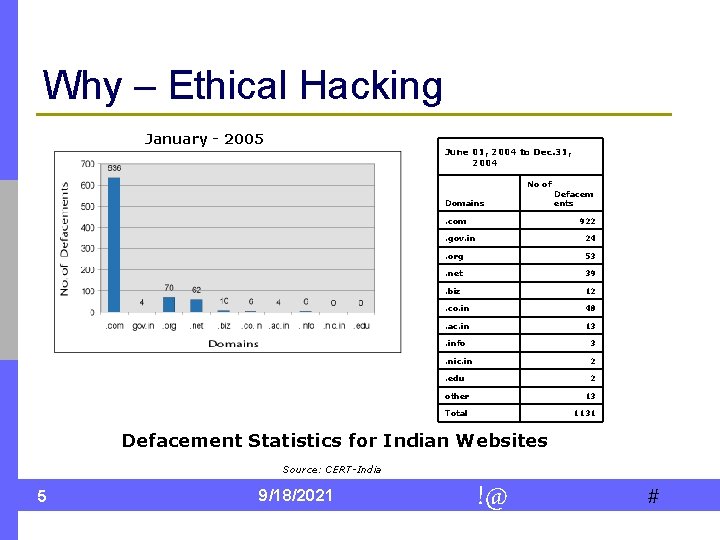
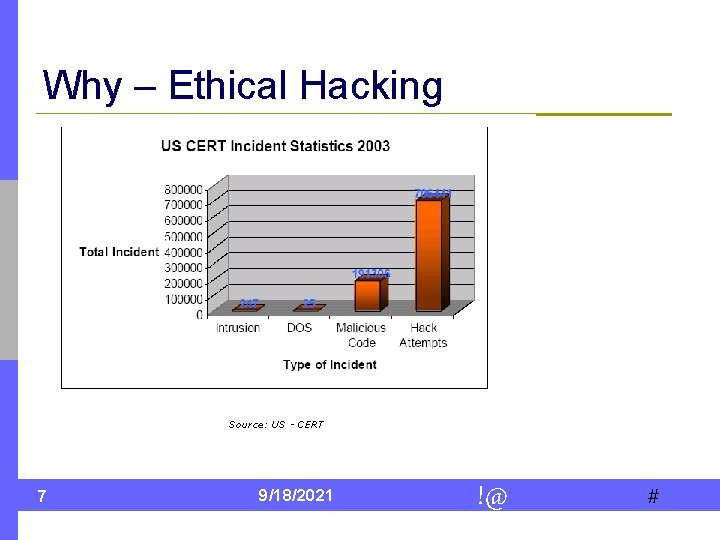
Why – Ethical Hacking January - 2005 June 01, 2004 to Dec. 31, 2004 No of Domains. com Defacem ents 922 . gov. in 24 . org 53 . net 39 . biz 12 . co. in 48 . ac. in 13 . info 3 . nic. in 2 . edu 2 other 13 Total 1131 Defacement Statistics for Indian Websites Source: CERT-India 5 9/18/2021 !@ #

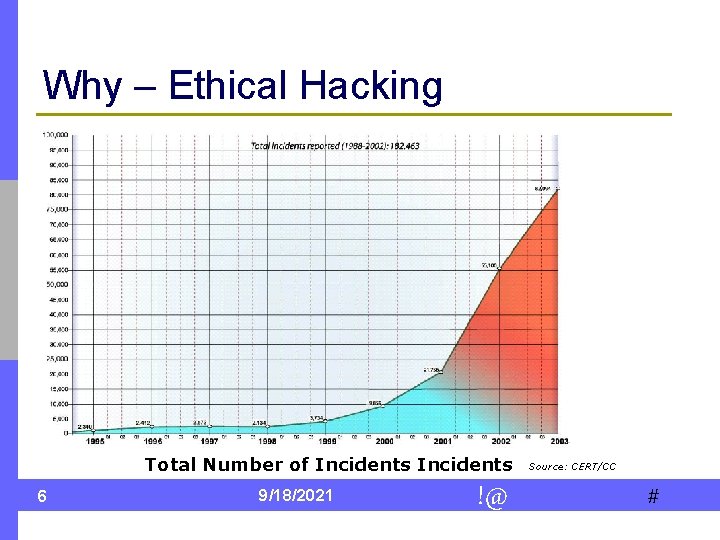
Why – Ethical Hacking Total Number of Incidents 6 9/18/2021 !@ Source: CERT/CC #

Why – Ethical Hacking Source: US - CERT 7 9/18/2021 !@ #

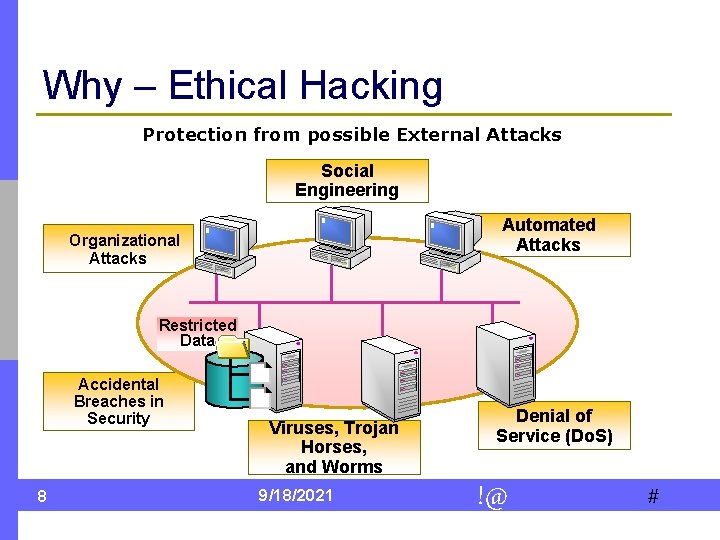
Why – Ethical Hacking Protection from possible External Attacks Social Engineering Automated Attacks Organizational Attacks Restricted Data Accidental Breaches in Security 8 Viruses, Trojan Horses, and Worms 9/18/2021 Denial of Service (Do. S) !@ #

Ethical Hacking - Process 1. 2. 3. 4. 5. 9 Preparation Footprinting Enumeration & Fingerprinting Identification of Vulnerabilities Attack – Exploit the Vulnerabilities 9/18/2021 !@ #

Preparation p p Identification of Targets – company websites, mail servers, extranets, etc. Signing of Contract n n n n 10 Agreement on protection against any legal issues Contracts to clearly specifies the limits and dangers of the test Specifics on Denial of Service Tests, Social Engineering, etc. Time window for Attacks Total time for the testing Prior Knowledge of the systems Key people who are made aware of the testing 9/18/2021 !@ #

Footprinting Collecting as much information about the target Ø DNS Servers Ø IP Ranges Ø Administrative Contacts Ø Problems revealed by administrators Information Sources p Search engines p Forums p Databases – whois, ripe, arin, apnic p Tools – PING, whois, Traceroute, DIG, nslookup, sam spade 11 9/18/2021 !@ #

Enumeration & Fingerprinting p p p Specific targets determined Identification of Services / open ports Operating System Enumeration Methods Ø Banner grabbing Ø Responses to various protocol (ICMP &TCP) commands Ø Port / Service Scans – TCP Connect, TCP SYN, TCP FIN, etc. Tools p Nmap, FScan, Hping, Firewalk, netcat, tcpdump, ssh, telnet, SNMP Scanner 12 9/18/2021 !@ #

Identification of Vulnerabilities p p p 13 Insecure Configuration Weak passwords Unpatched vulnerabilities in services, Operating systems, applications Possible Vulnerabilities in Services, Operating Systems Insecure programming Weak Access Control 9/18/2021 !@ #

Identification of Vulnerabilities Methods p Unpatched / Possible Vulnerabilities – Tools, Vulnerability information Websites p Weak Passwords – Default Passwords, Brute force, Social Engineering, Listening to Traffic p Insecure Programming – SQL Injection, Listening to Traffic p Weak Access Control – Using the Application Logic, SQL Injection 14 9/18/2021 !@ #

Identification of Vulnerabilities Tools Vulnerability Scanners - Nessus, ISS, SARA, SAINT Listening to Traffic – Ethercap, tcpdump Password Crackers – John the ripper, LC 4, Pwdump Intercepting Web Traffic – Achilles, Whisker, Legion Websites § Common Vulnerabilities & Exposures – http: //cve. mitre. org § Bugtraq – www. securityfocus. com § Other Vendor Websites 15 9/18/2021 !@ #

Attack – Exploit the vulnerabilities p p Obtain as much information (trophies) from the Target Asset Gaining Normal Access Escalation of privileges Obtaining access to other connected systems Last Ditch Effort – Denial of Service 16 9/18/2021 !@ #

Attack – Exploit the vulnerabilities Network Infrastructure Attacks § Connecting to the network through modem § Weaknesses in TCP / IP, Net. BIOS § Flooding the network to cause DOS Operating System Attacks § Attacking Authentication Systems § Exploiting Protocol Implementations § Exploiting Insecure configuration § Breaking File-System Security 17 9/18/2021 !@ #

Attack – Exploit the vulnerabilities Application Specific Attacks p p 18 Exploiting implementations of HTTP, SMTP protocols Gaining access to application Databases SQL Injection Spamming 9/18/2021 !@ #

Attack – Exploit the vulnerabilities Exploits § Free exploits from Hacker Websites § Customised free exploits § Internally Developed Tools – Nessus, Metasploit Framework, 19 9/18/2021 !@ #

Reporting Methodology p Exploited Conditions & Vulnerabilities that could not be exploited p Proof for Exploits - Trophies p Practical Security solutions p 20 9/18/2021 !@ #

Ethical Hacking - Commandments p Working Ethically n n p p 21 Trustworthiness Misuse for personal gain Respecting Privacy Not Crashing the Systems 9/18/2021 !@ #