A Prioritized Approach to Implement the NIST CSF















- Slides: 43

A Prioritized Approach to Implement the NIST CSF using the CIS Critical Security Controls Brian Ventura SANS Community Instructor ISSA Portland, Director of Education water@bighead. org @brianwifaneye

Who am I? Brian Ventura 20+ years in Information Technology, ranging from systems administration to project management and information security. Currently an Information Security Architect in Portland, Oregon and volunteer as the Director of Education for the Portland ISSA Chapter. Brian holds his CISSP, GSEC, GCFA, and GCCC, as well as other industry certifications. As the ISSA Director of Education, Brian coordinates relevant local and online training opportunities. Timbers Army, Thorns Riveter, bike commuter, Land Cruiser enthusiast https: //www. sans. org/instructors/brian-ventura SEC 440: Critical Security Controls: Planning, Implementing and Auditing SEC 566: Implementing and Auditing the Critical Security Controls - In-Depth MGT 414: SANS Training Program for CISSP® Certification Coming Soon… SEC 401: Security Essentials Bootcamp Style


City of Portland Delivery of services and value to Bureaus Align security strategy with business risk

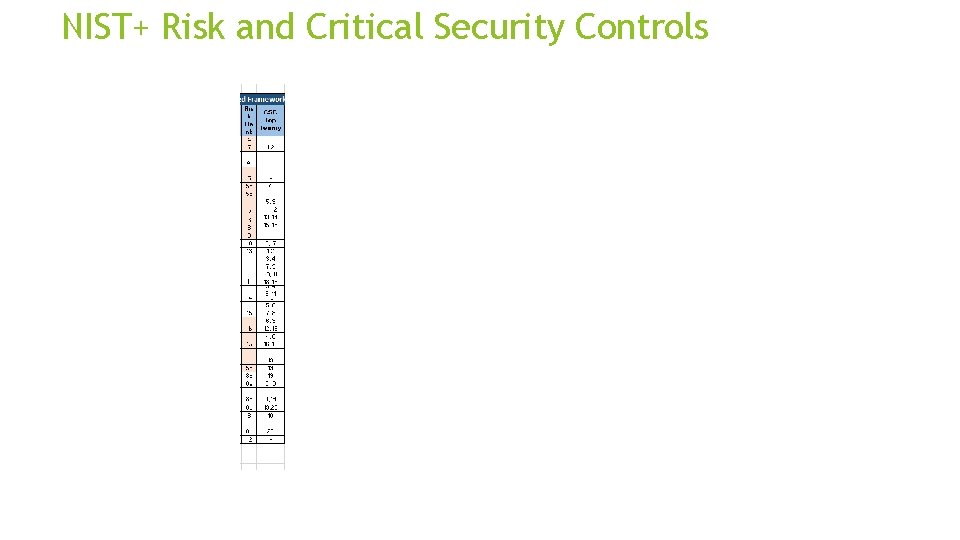
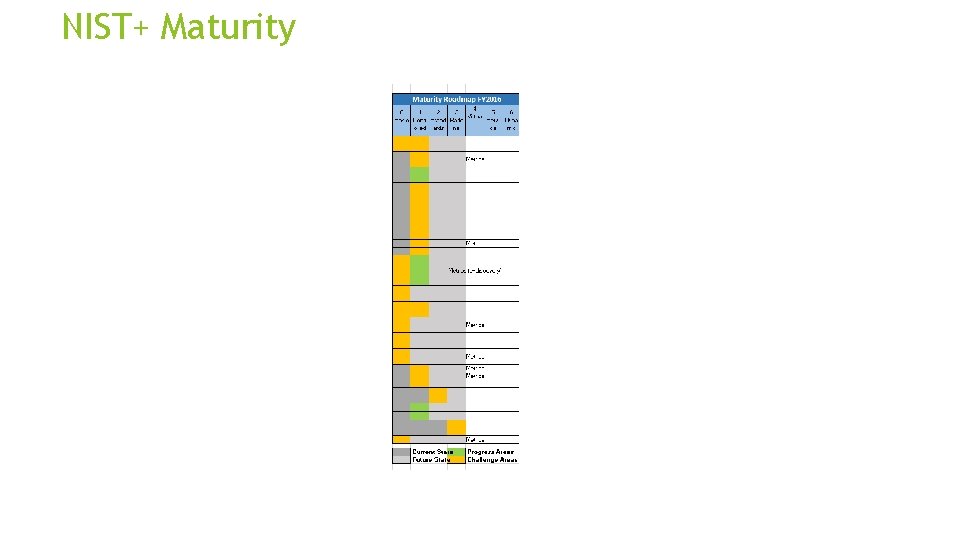
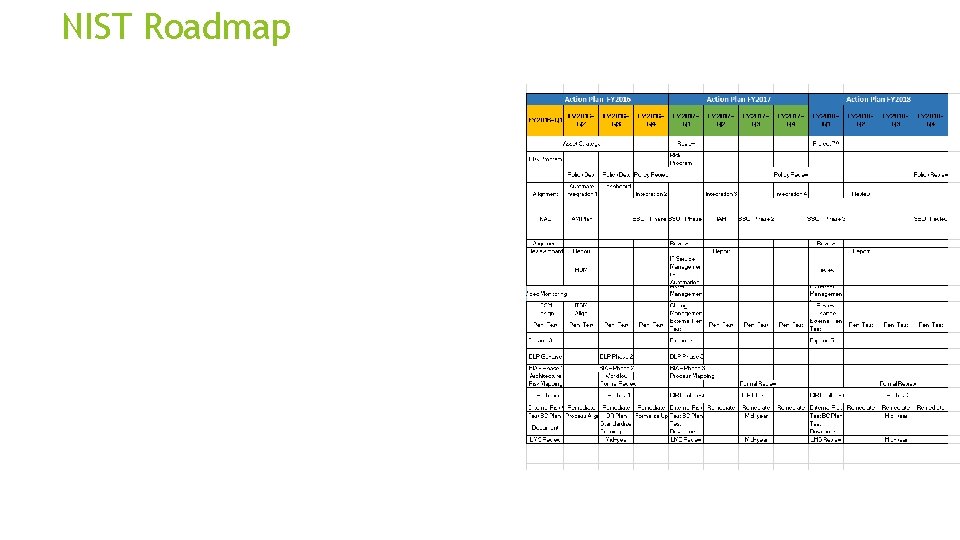
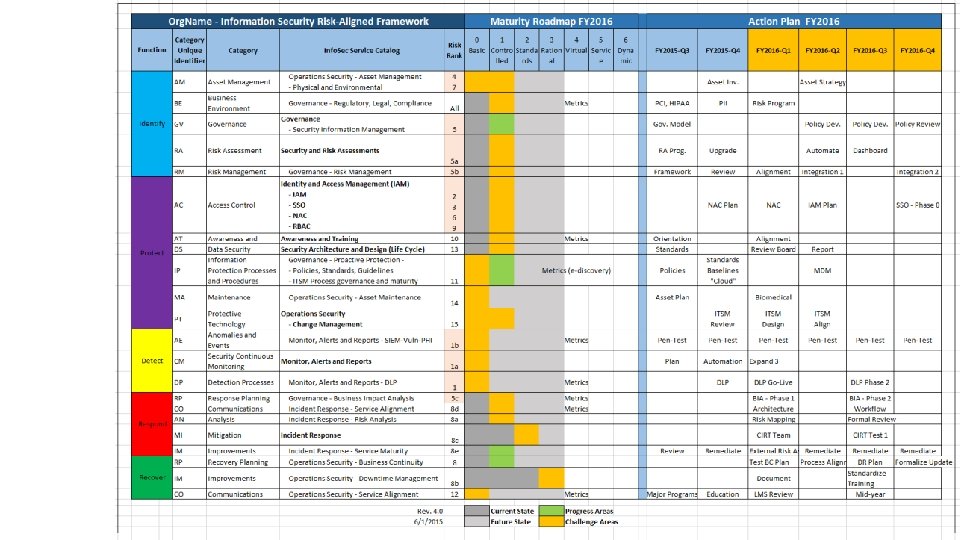
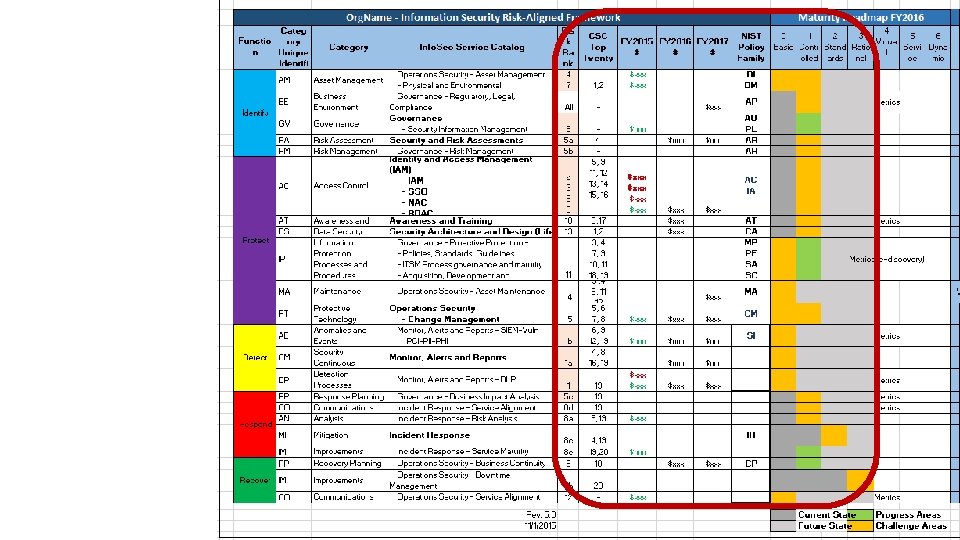
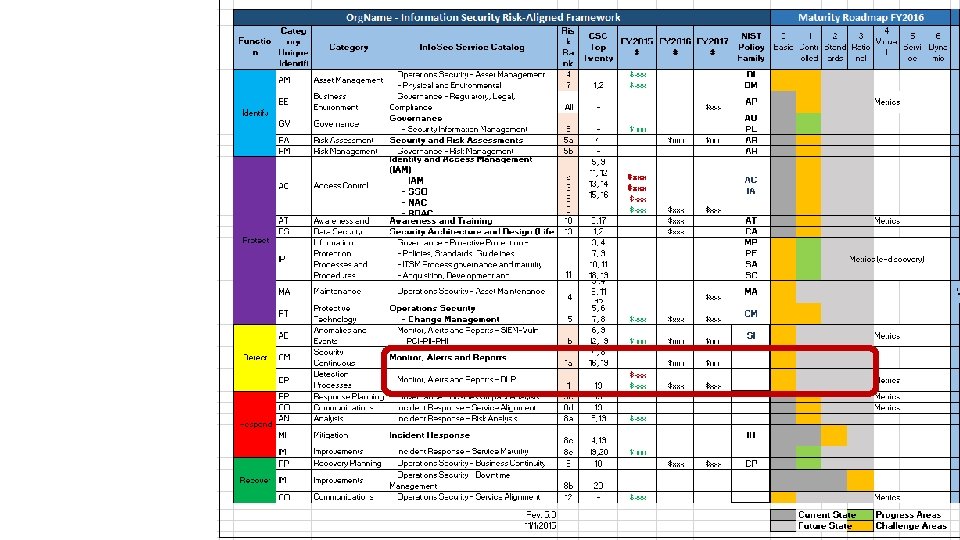
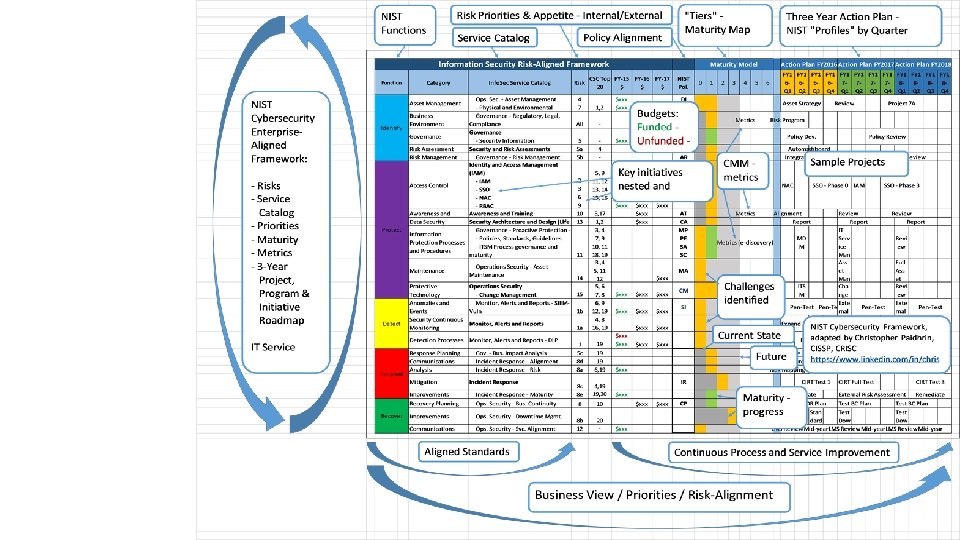
NIST Framework+ City of Portland’s Adoption of CSF • Risk & remediation prioritization • Maturity gaps and selective metrics • Alignment of business risk to CSC • Budget & resource prioritization

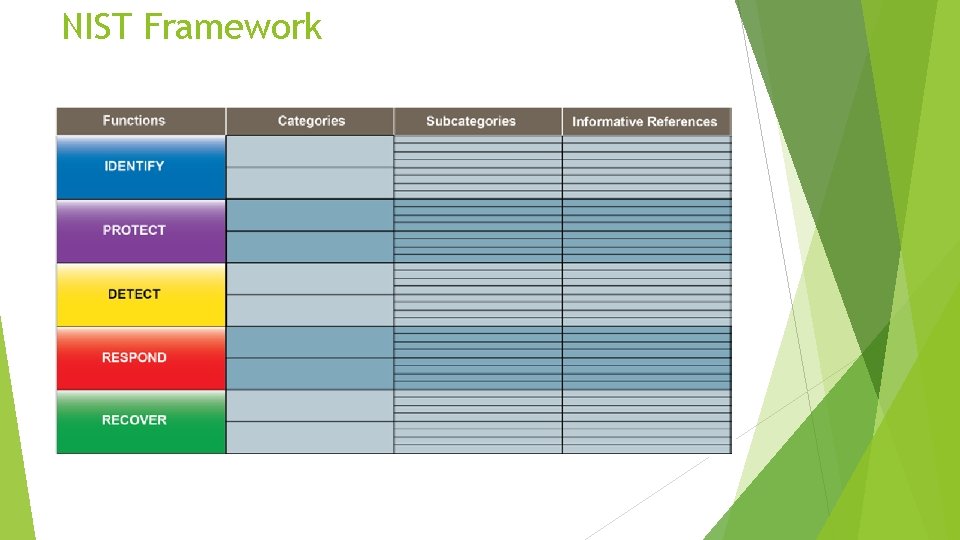
NIST Framework



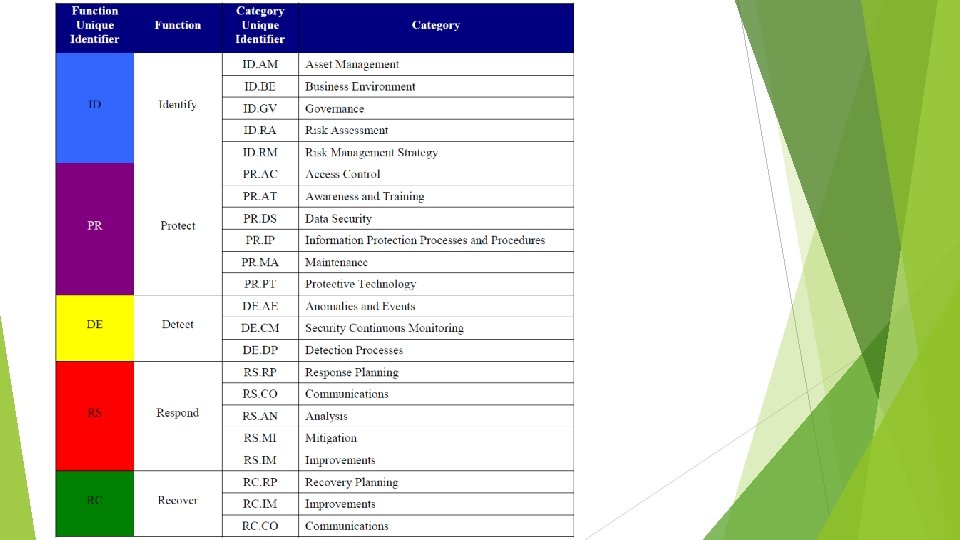
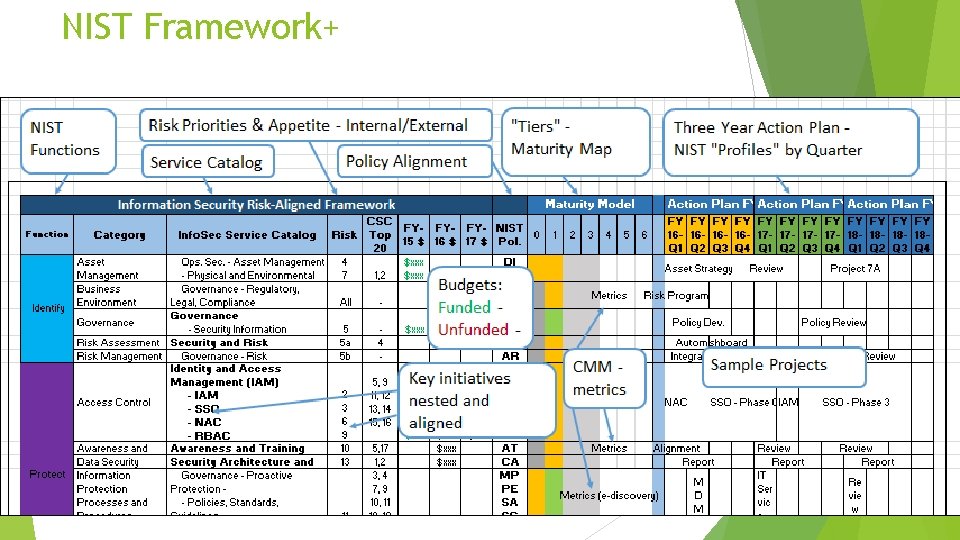
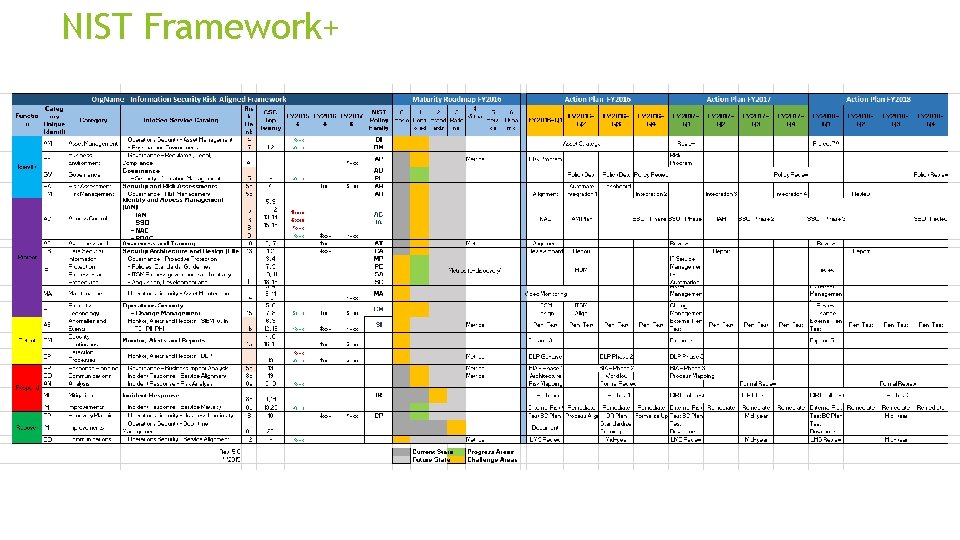
NIST Framework+

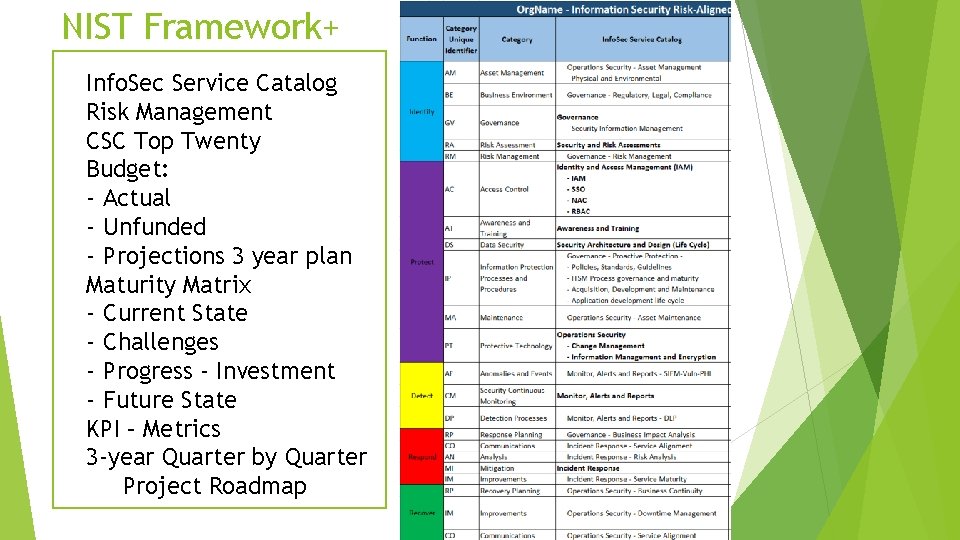
NIST Framework+ Info. Sec Service Catalog Risk Management CSC Top Twenty Budget: - Actual - Unfunded - Projections 3 year plan Maturity Matrix - Current State - Challenges - Progress - Investment - Future State KPI – Metrics 3 -year Quarter by Quarter Project Roadmap

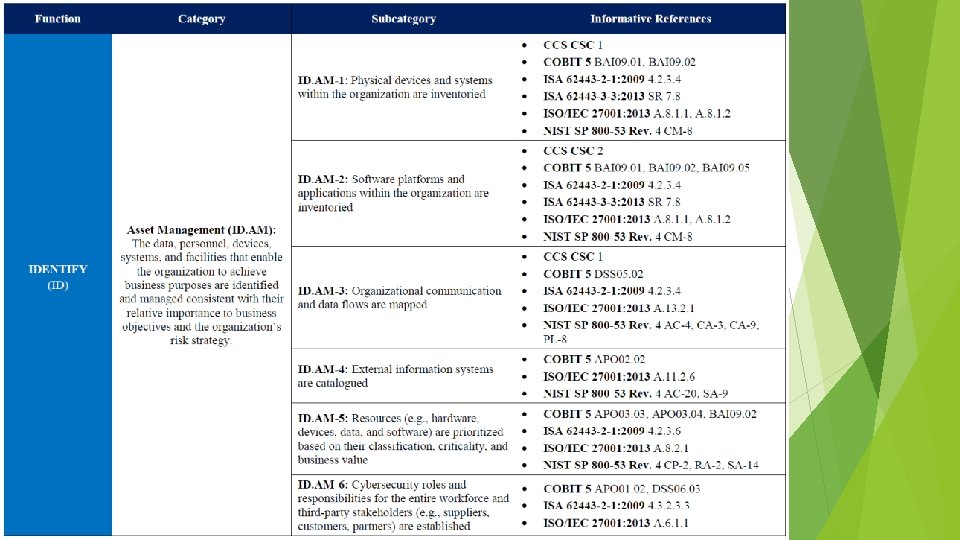
NIST Framework+

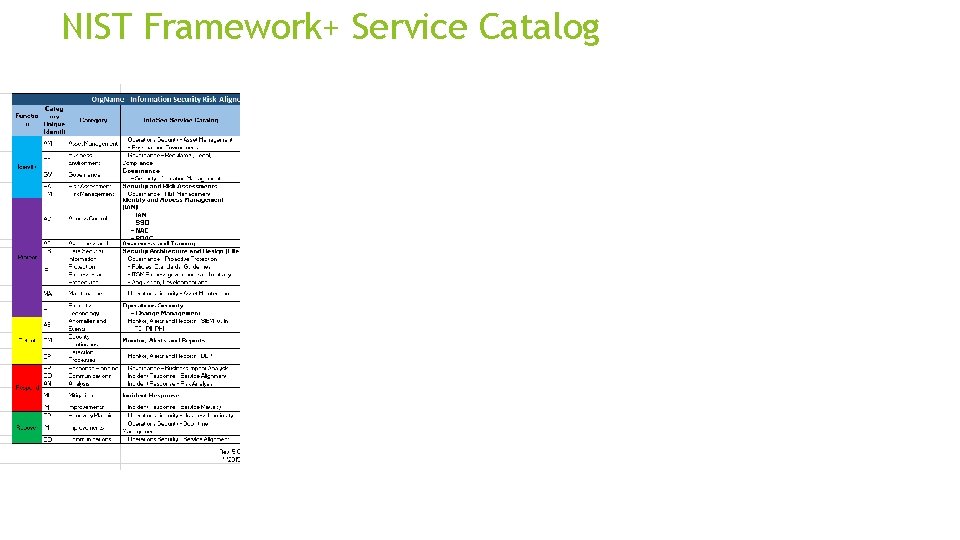
NIST Framework+ Service Catalog

NIST+ Risk and Critical Security Controls

NIST+ Budget

NIST+ Maturity

NIST Roadmap


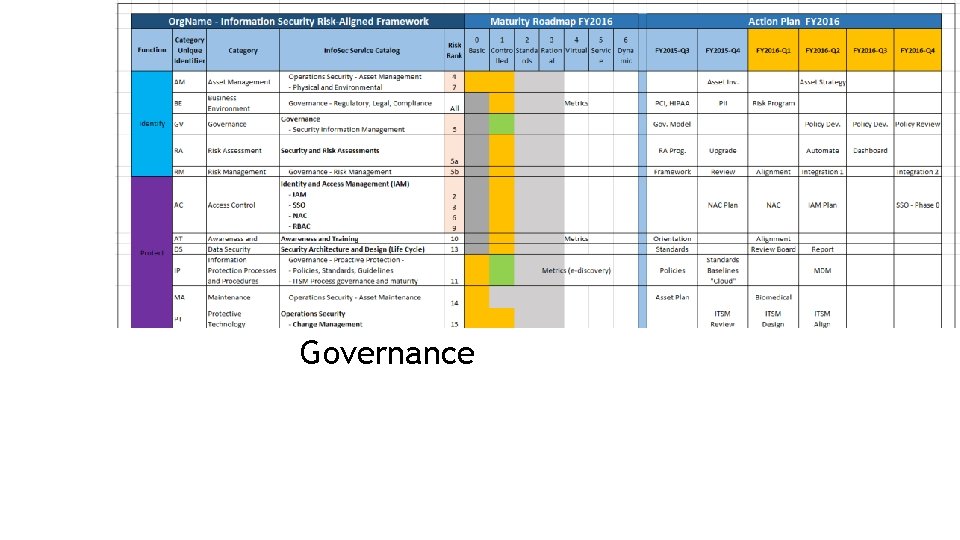
Governance

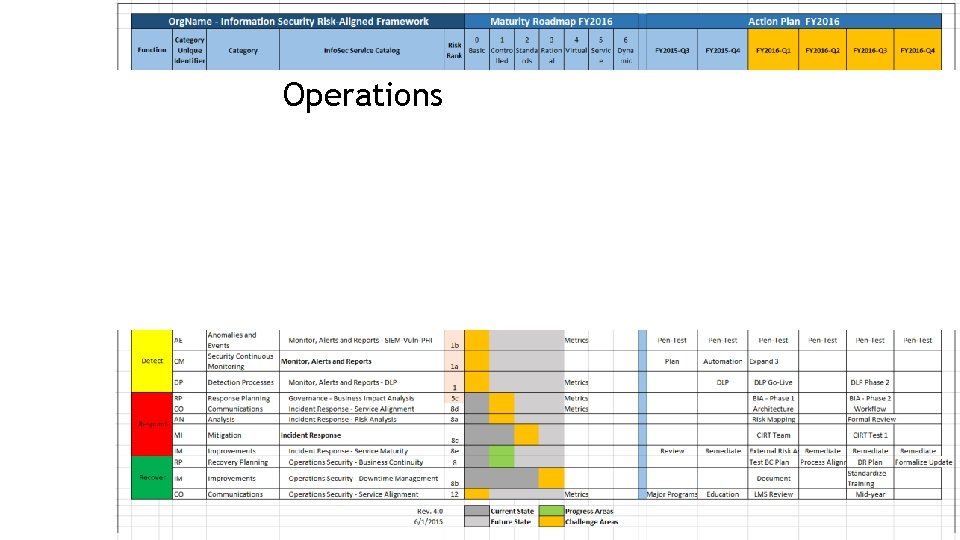
Operations




CIS Critical Security Controls Foundational Cyber Hygiene controls Prioritized order

CIS Critical Security Controls 1. Inventory of Authorized and Unauthorized Devices 11. Secure Configurations for Network Devices 2. Inventory of Authorized and Unauthorized Software 12. Boundary Defense 3. Secure Configurations for Hardware and Software 14. Controlled Access Based on the Need to Know 4. Continuous Vulnerability Assessment and Remediation 15. Wireless Access Control 5. Controlled Use of Administrative Privileges 13. Data Protection 16. Account Monitoring and Control 17. Security Skills Assessment and 6. Maintenance, Monitoring, and Analysis of Audit Appropriate Training to Fill Gaps Logs 18. Application Software Security 7. Email and Web Browser Protections 8. Malware Defenses 9. Limitation and Control of Network Ports 19. Incident Response and Management 20. Penetration Tests and Red Team Exercises

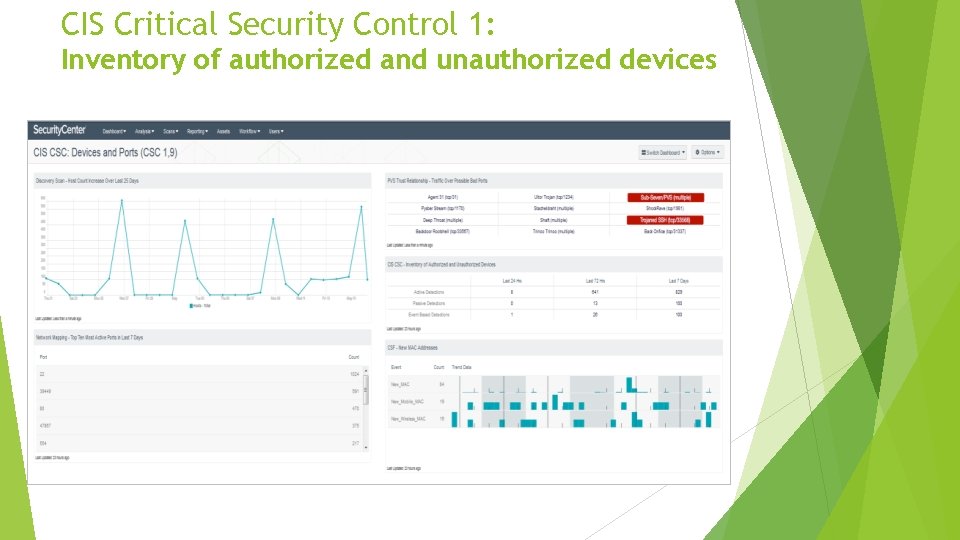
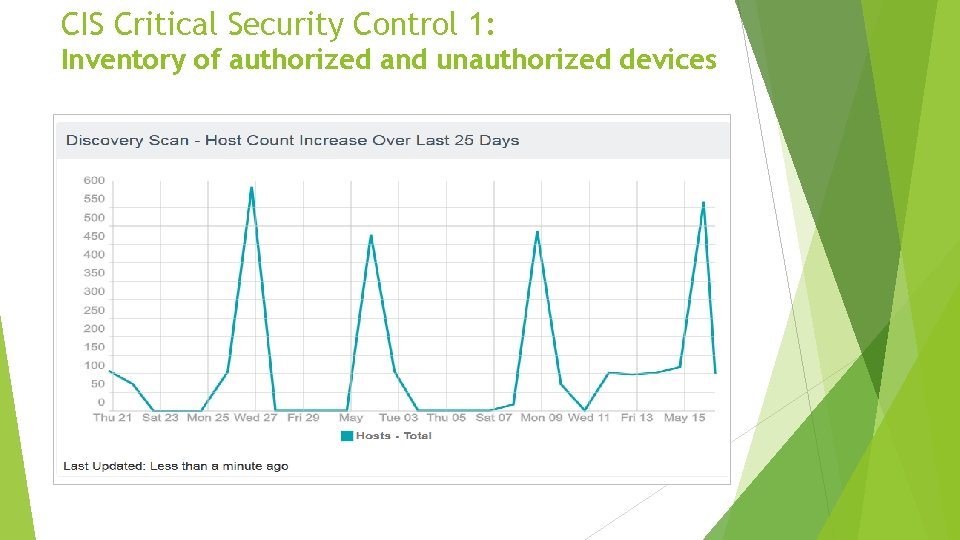
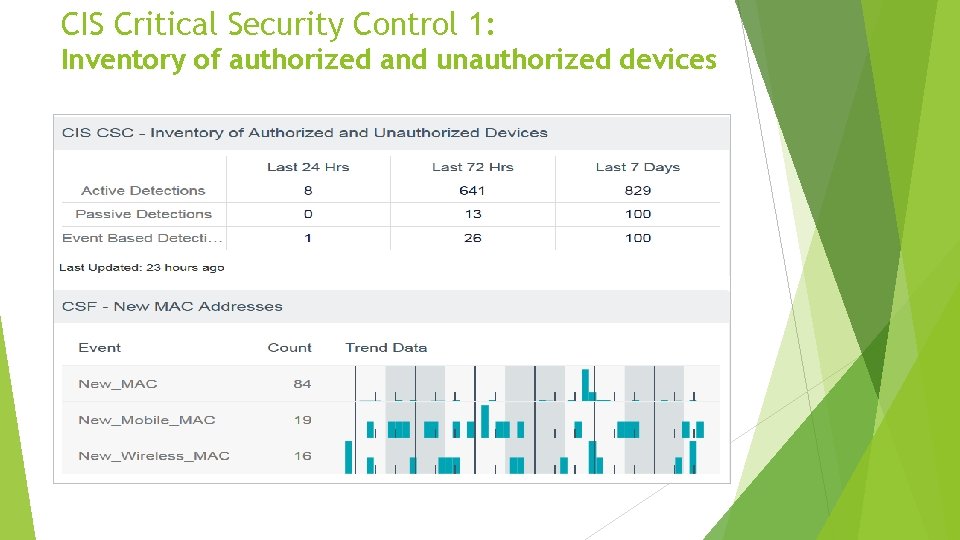
CIS Critical Security Control 1: Inventory of authorized and unauthorized devices Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access. • Workstations, servers, printers, TVs, phones, what else? How do we find these?

CIS Critical Security Control 1: Inventory of authorized and unauthorized devices

CIS Critical Security Control 1: Inventory of authorized and unauthorized devices

CIS Critical Security Control 1: Inventory of authorized and unauthorized devices

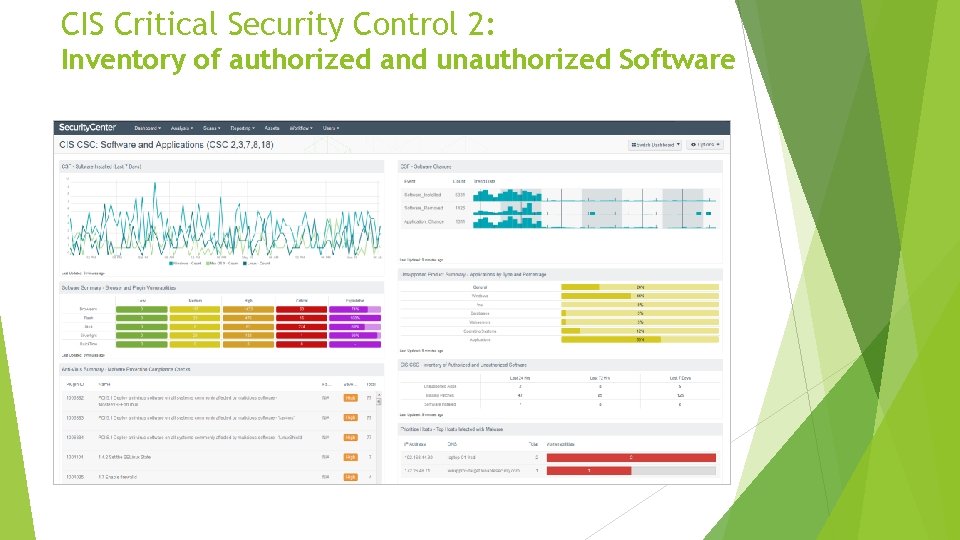
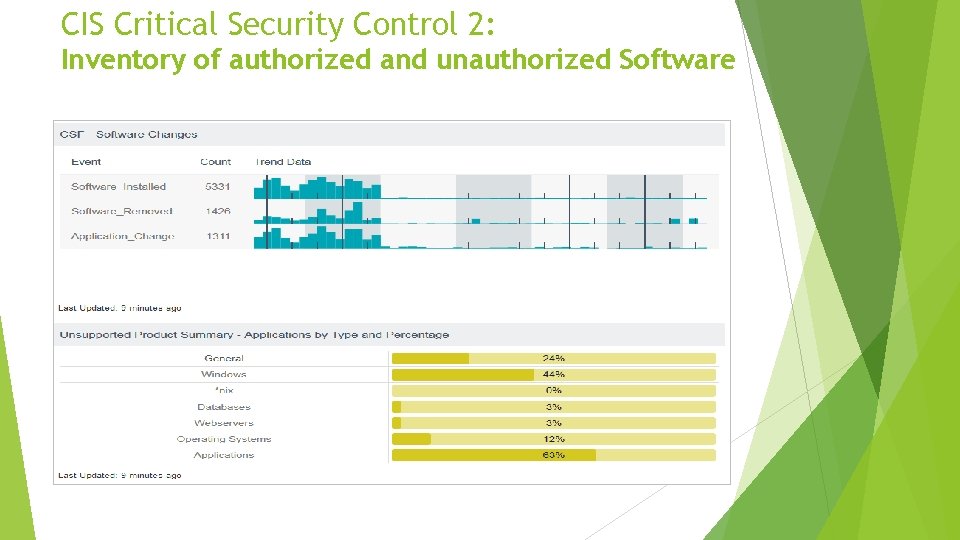
CIS Critical Security Control 2: Inventory of authorized and unauthorized Software Actively manage (inventory, track, and correct) all software on the network so that only authorized software is installed and can execute, and that unauthorized and unmanaged software is found and prevented from installation or execution. • We need an inventory and a way to manage appropriate use of software!

CIS Critical Security Control 2: Inventory of authorized and unauthorized Software

CIS Critical Security Control 2: Inventory of authorized and unauthorized Software

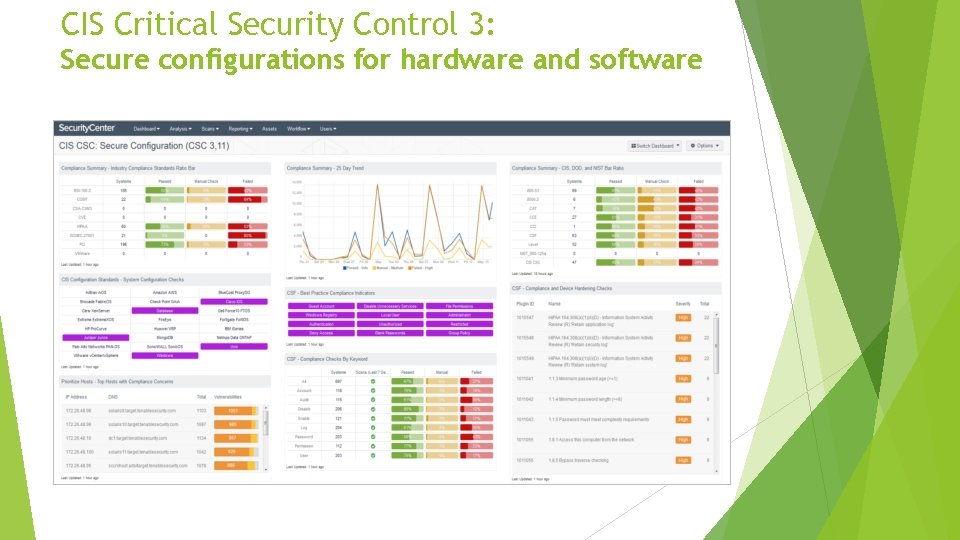
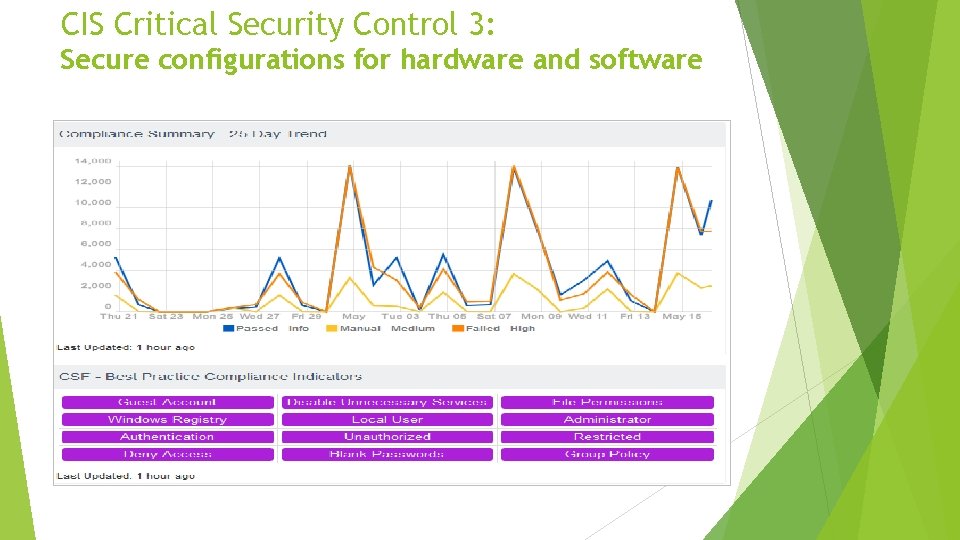
CIS Critical Security Control 3: Secure configurations for hardware and software Establish, implement, and actively manage (track, report on, correct) the security configuration of laptops, servers, and workstations using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings. • Example: Is our webserver using TLS for authentication/sensitive data transfers? Are our users using strong passwords?

CIS Critical Security Control 3: Secure configurations for hardware and software

CIS Critical Security Control 3: Secure configurations for hardware and software

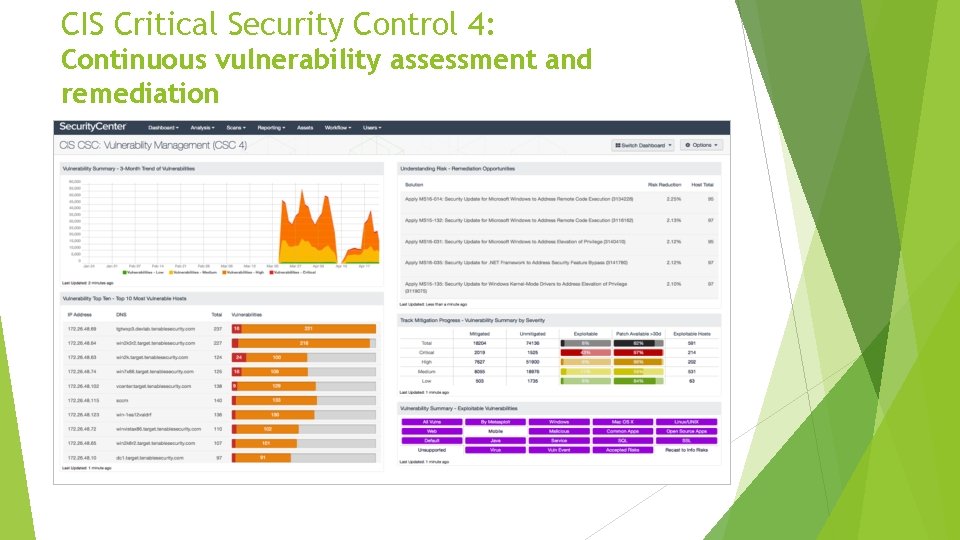
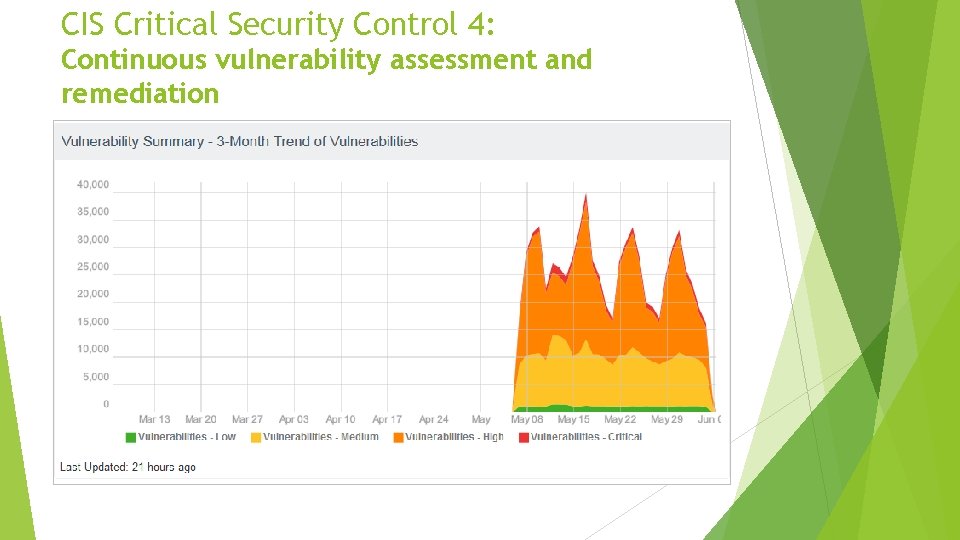
CIS Critical Security Control 4: Continuous vulnerability assessment and remediation Continuously acquire, assess, and take action on new information in order to identify vulnerabilities, remediate, and minimize the window of opportunity for attackers. • Are there vulnerabilities in our installed versions of Java, Flash, Windows, others?

CIS Critical Security Control 4: Continuous vulnerability assessment and remediation

CIS Critical Security Control 4: Continuous vulnerability assessment and remediation

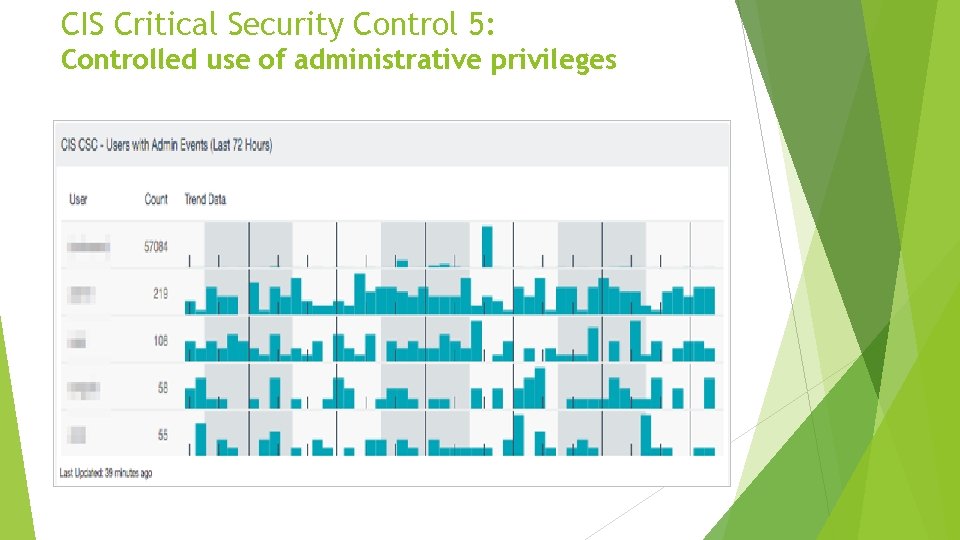
CIS Critical Security Control 5: Controlled use of administrative privileges The misuse of administrative privileges is a primary method for attackers to move laterally inside a target enterprise. • This applies to any device: workstations, servers, applications, appliances, network devices.

CIS Critical Security Control 5: Controlled use of administrative privileges

CIS Critical Security Control 5: Controlled use of administrative privileges

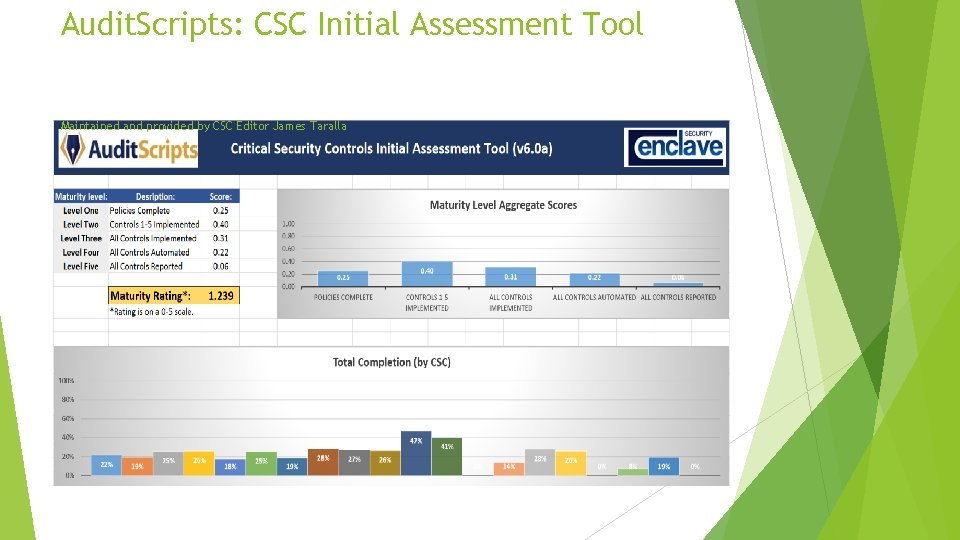
Audit. Scripts: CSC Initial Assessment Tool Maintained and provided by CSC Editor James Taralla

Questions?

Links and Resources Center for Internet Security (CIS): https: //www. cisecurity. org/ NIST Cyber Security Framework (CSF): http: //www. nist. gov/cyberframework/ CIS Critical Security Controls (CSC): https: //www. cisecurity. org/critical-controls. cfm Auditscripts resources (provided by James Tarala, CSC Editor): https: //www. auditscripts. com/freeresources/critical-security-controls/ CSF planning spreadsheet: http: //www. tenable. com/whitepapers/nist-csfimplementation-planning-tool https: //www. sans. org/instructors/brian-ventura