KMIP and NIST 800 57 KMIP and NIST








- Slides: 10

KMIP and NIST 800 -57 KMIP and NIST– what matches and what does not

Current States • KMIP: • • Preactive Active Deactivated Compromised Destroyed Compromised NIST 800 -57: • • • Pre-Activation Active Suspended Deactivated Compromised Destroyed

Transitions: Preactive • KMIP: • Preactive upon generation • Preactive to Destroyed (Unused Keys) • Preactive to Compromised (Unused Keys) • Preactive to Active – keys placed into service • NIST 800 -57: • Preactive upon generation • Preactive to Destroyed (Unused Keys) • Preactive to Compromised (Unused Keys) • Preactive to Active – keys placed into service

Transitions: Active • KMIP: • Active to Compromised (Compromise of the Key Material) • Active to Deactivated (End of cryptoperiod, lease, usage period or rekeyed) NIST 800 -57: • Active to Destroyed (replacing RBG, ephemeral keys, authorization keys)*** • Active to Compromised (Compromise of the Key Material) • Active Suspended (800 -57 says keys but probably means certificates) • Active to Deactivated (End of cryptoperiod, lease, usage period or rekeyed)

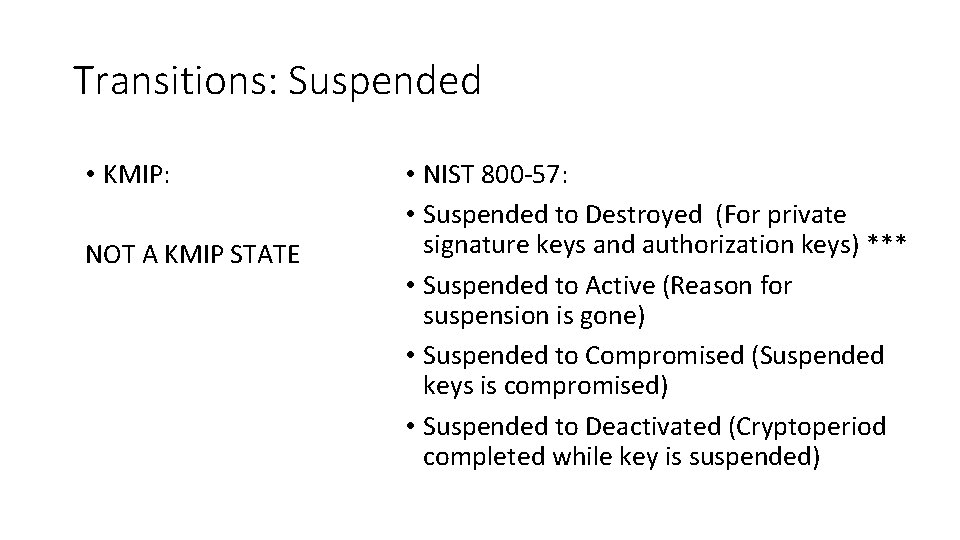
Transitions: Suspended • KMIP: NOT A KMIP STATE • NIST 800 -57: • Suspended to Destroyed (For private signature keys and authorization keys) *** • Suspended to Active (Reason for suspension is gone) • Suspended to Compromised (Suspended keys is compromised) • Suspended to Deactivated (Cryptoperiod completed while key is suspended)

Transitions: Deactivated • KMIP: • Deactivated to Compromised (Deactivated Material is compromised) Revoke (reason compromise) • Deactivated to Destroyed (Key is no longer needed – including no longer need to archive) • Note this includes archived keys • NIST 800 -57: • Deactivated to Compromised (Deactivated Material is compromised) • Deactivated to Destroyed (Key is no longer needed – including no longer need to archive) • Note this includes archived keys

Transitions: Compromised • KMIP: • Compromise to Destroyed Compromised • NIST 800 -57: • Compromised to Destroyed

Transitions: Destroyed • KMIP: • Destroyed to Destroyed Compromise (Revoke operation with reason of Compromise) - Notes that KMIP authorized revoking destroyed keys Notes that destroyed compromise is different state • NIST 800 -57: • If destroyed data was found to be compromised after the fact, compromised date should be recorded • Retain metadata (transition dates, key identifier, cryptoperiod)

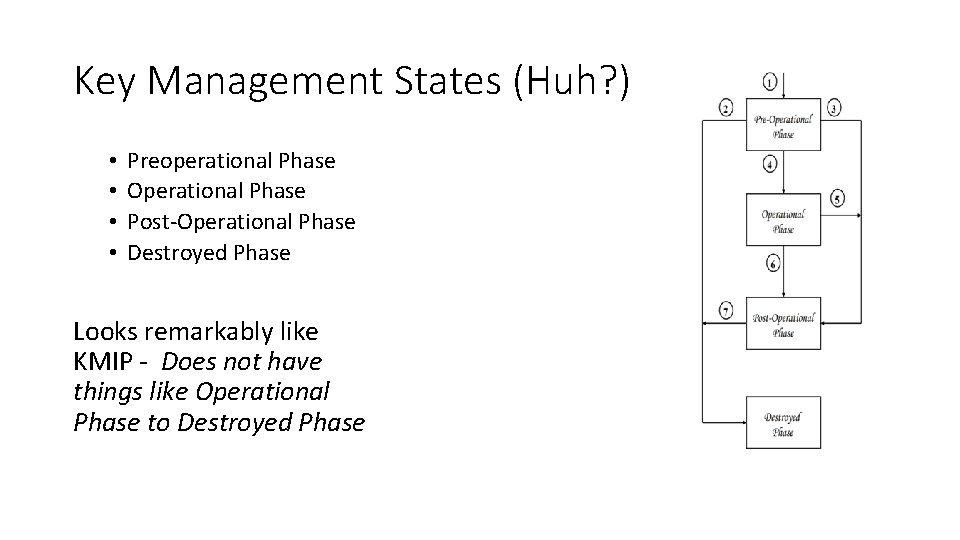
Key Management States (Huh? ) • • Preoperational Phase Operational Phase Post-Operational Phase Destroyed Phase Looks remarkably like KMIP - Does not have things like Operational Phase to Destroyed Phase

Next Steps • What do we want to respond about? • Look at Suspended for KMIP • Before we do – Suspended deals with certificates, do we see value looking at it for other managed object types. • Comments on State Transitions • Destroying an Active key just seems wrong. • DO different keys require different management models • Active Ephemeral Keys can be destroyed and Certificates can be suspended so where is the box drawn around?