NIST National Institute of Standards and Technology NIST














































- Slides: 72




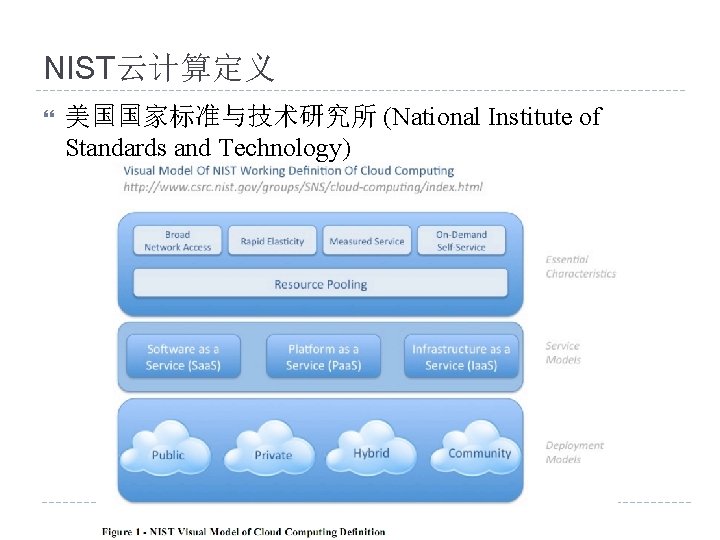
NIST云计算定义 美国国家标准与技术研究所 (National Institute of Standards and Technology)

NIST云计算定义 Cloud computing is a model for enabling convenient, ondemand network access to a shared pool of configurable computing resources (e. g. , networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction. This cloud model promotes availability and is composed of five essential characteristics, three service models, and four deployment models.

基本特征 On-demand self-service. A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service’s provider. Broad network access. Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms (e. g. , mobile phones, laptops, and PDAs). Resource pooling. The provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to consumer demand. There is a sense of location independence in that the customer generally has no control or knowledge over the exact location of the provided resources but may be able to specify location at a higher level of abstraction (e. g. , country, state, or datacenter). Examples of resources include storage, processing, memory, network bandwidth, and virtual machines. Rapid elasticity. Capabilities can be rapidly and elastically provisioned, in some cases automatically, to quickly scale out and rapidly released to quickly scale in. To the consumer, the capabilities available for provisioning often appear to be unlimited and can be purchased in any quantity at any time. Measured Service. Cloud systems automatically control and optimize resource use by leveraging a metering capability at some level of abstraction appropriate to the type of service (e. g. , storage, processing, bandwidth, and active user accounts). Resource usage can be monitored, controlled, and reported providing transparency for both the provider and consumer of the utilized service.

服务模型 Cloud Software as a Service (Saa. S). The capability provided to the consumer is to use the provider’s applications running on a cloud infrastructure. The applications are accessible from various client devices through a thin client interface such as a web browser (e. g. , web-based email). The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, storage, or even individual application capabilities, with the possible exception of limited userspecific application configuration settings. Cloud Platform as a Service (Paa. S). The capability provided to the consumer is to deploy onto the cloud infrastructure consumer-created or acquired applications created using programming languages and tools supported by the provider. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, or storage, but has control over the deployed applications and possibly application hosting environment configurations. Cloud Infrastructure as a Service (Iaa. S). The capability provided to the consumer is to provision processing, storage, networks, and other fundamental computing resources where the consumer is able to deploy and run arbitrary software, which can include operating systems and applications. The consumer does not manage or control the underlying cloud infrastructure but has control over operating systems, storage, deployed applications, and possibly limited control of select networking components (e. g. , host firewalls).

部署模型 Private cloud. The cloud infrastructure is operated solely for an organization. It may be managed by the organization or a third party and may exist on premise or off premise. Community cloud. The cloud infrastructure is shared by several organizations and supports a specific community that has shared concerns (e. g. , mission, security requirements, policy, and compliance considerations). It may be managed by the organizations or a third party and may exist on premise or off premise. Public cloud. The cloud infrastructure is made available to the general public or a large industry group and is owned by an organization selling cloud services. Hybrid cloud. The cloud infrastructure is a composition of two or more clouds (private, community, or public) that remain unique entities but are bound together by standardized or proprietary technology that enables data and application portability (e. g. , cloud bursting for load-balancing between clouds).

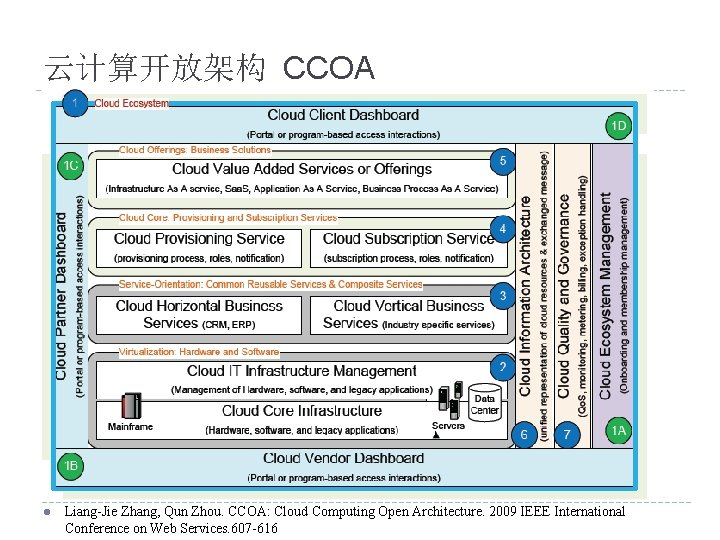
云计算开放架构 CCOA l Liang-Jie Zhang, Qun Zhou. CCOA: Cloud Computing Open Architecture. 2009 IEEE International Conference on Web Services. 607 -616









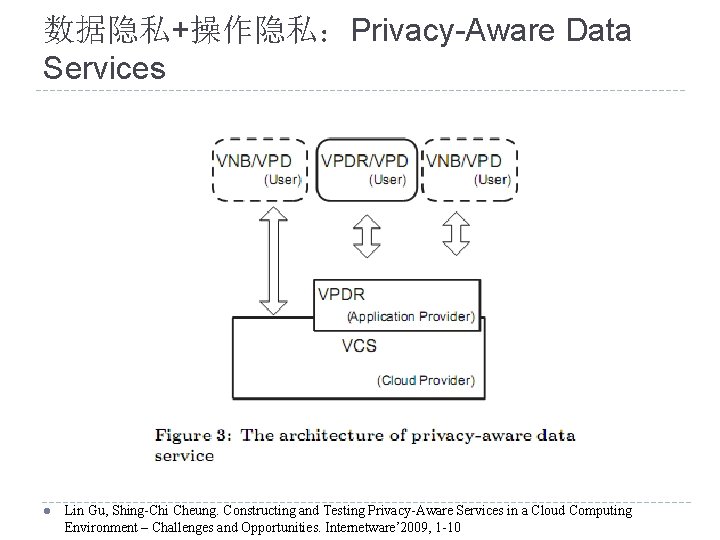
云隐私分类 数据隐私 Data Privacy 用来保护用户和其数据之间的关联关系 操作隐私 Operational Privacy l Data Privacy and Operational Privacy 数据(Data)和逻辑(Logic)是软件产品的两个主 要组成部分 Algorithms + Data Structures = Program 保护用户和用户发起的操作之间的关联关系 防止服务带来的隐私泄漏 Lin Gu, Shing-Chi Cheung. Constructing and Testing Privacy-Aware Services in a Cloud Computing Environment – Challenges and Opportunities. Internetware’ 2009, 1 -10


加密:Fully homomorphic encryption Encrypt: putting things inside the box Anyone can do this (imagine a mail-drop) ci Enc(mi) Decrypt: Taking things out of the box Only Alice can do it, requires the key m* Dec(c*) Process: Assembling the jewelry Anyone can do it, computing on ciphertext c* Process(c 1, …, cn) m* = Dec(c*) is “the ring”, made from “raw materials” mi l Craig Gentry: Fully homomorphic encryption using ideal lattices. STOC 2009: 169 -178 l Marten van Dijk, Craig Gentry, Shai Halevi, Vinod Vaikuntanathan: Fully Homomorphic Encryption over the Integers. EUROCRYPT 2010: 24 -43

硬件加密:Privacy as a Service l Wassim Itani, Ayman Kayssi, Ali Chehab. Privacy as a Service: Privacy-Aware Data Storage and Processing in Cloud Computing Architectures. 2009 Eighth IEEE International Conference on Dependable, Automonic and Secure Computing. 2009: 711 -716

Privacy as a Service Pas. S proposed as the first practical cloud computing privacy solution. Relies on cryptographic coprocessors for providing a trusted and isolated execution environment in cloud computing.


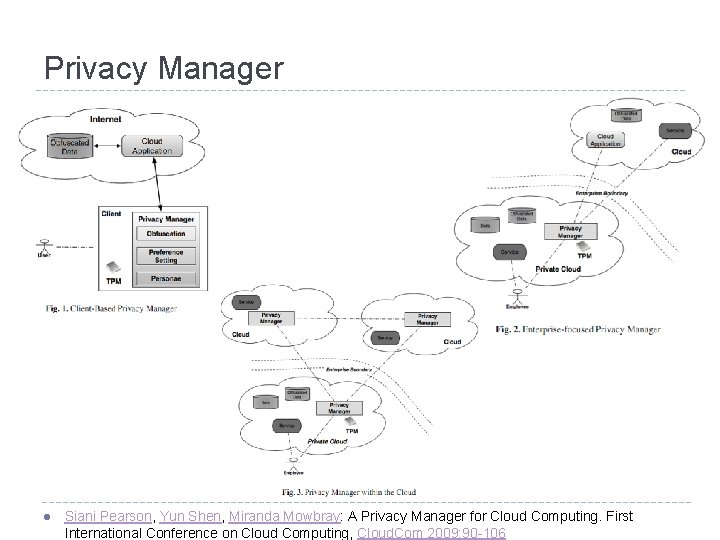
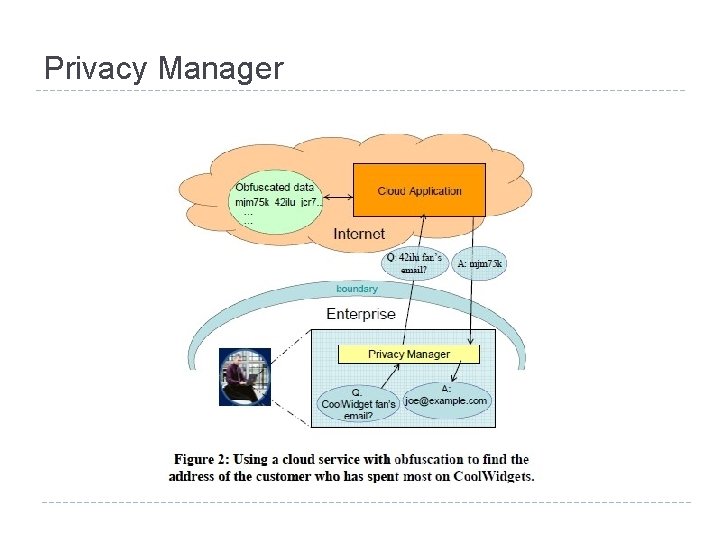
Privacy Manager l Siani Pearson, Yun Shen, Miranda Mowbray: A Privacy Manager for Cloud Computing. First International Conference on Cloud Computing, Cloud. Com 2009: 90 -106

Privacy Manager


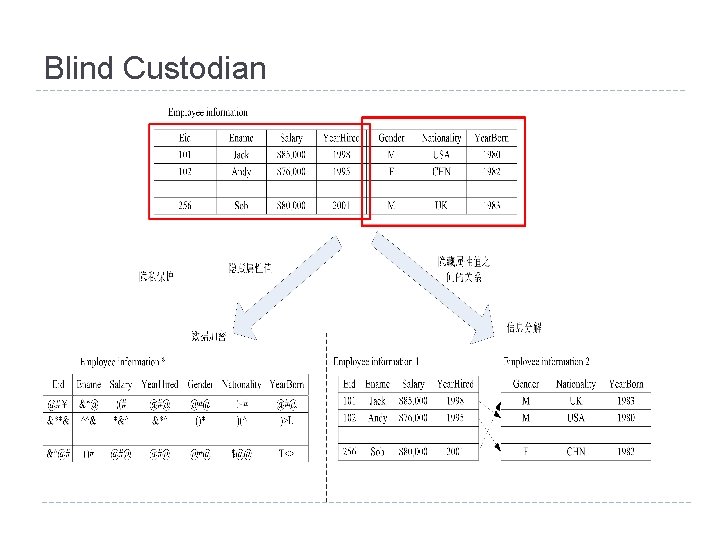
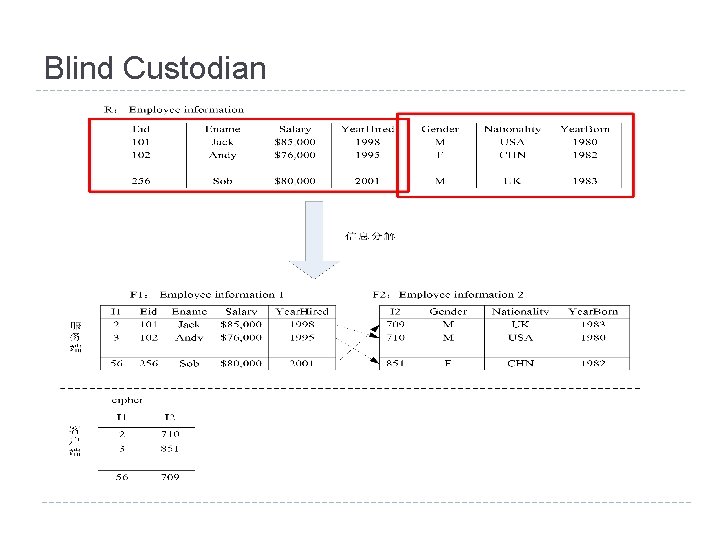
Blind Custodian


Blind Custodian

数据隐私+操作隐私:Privacy-Aware Data Services l Lin Gu, Shing-Chi Cheung. Constructing and Testing Privacy-Aware Services in a Cloud Computing Environment – Challenges and Opportunities. Internetware’ 2009, 1 -10









Securing Clouds Goal: protect a cloud against insider adversaries from Iaa. S layer l. Santos et al. , Towards Trusted Cloud Computing, 2009 USENIX Annual Technical Conference (USENIX '09) , Workshop on Hot Topics in Cloud Computing, Hot. Cloud 2009 l. Krautheim, Private Virtual Infrastructure for Cloud Computing, Hot. Cloud 2009 l. Wood et al. , The Case for Enterprise-Ready Virtual Private Clouds, Hot. Cloud 2009

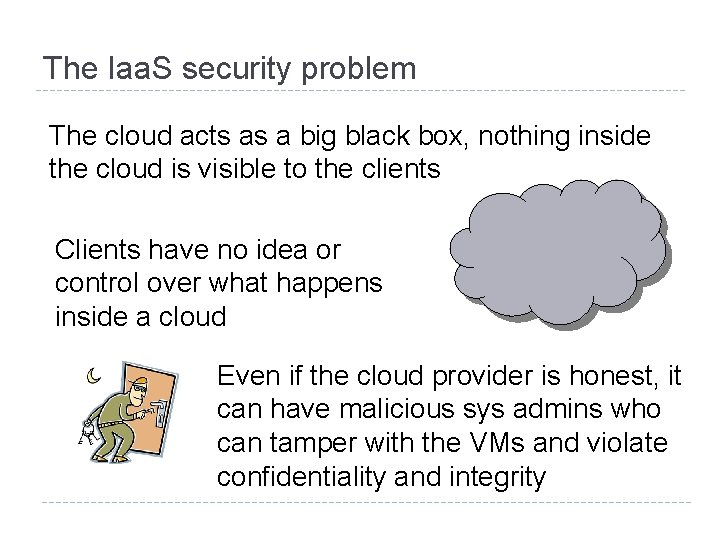
The Iaa. S security problem The cloud acts as a big black box, nothing inside the cloud is visible to the clients Clients have no idea or control over what happens inside a cloud Even if the cloud provider is honest, it can have malicious sys admins who can tamper with the VMs and violate confidentiality and integrity

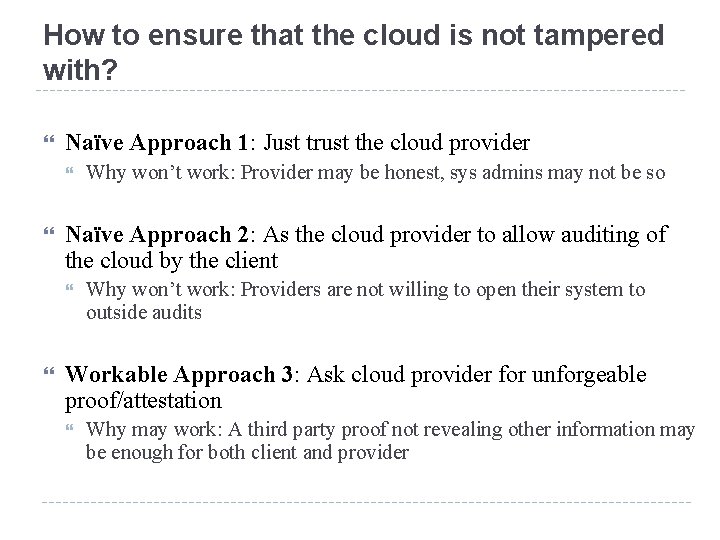
How to ensure that the cloud is not tampered with? Naïve Approach 1: Just trust the cloud provider Naïve Approach 2: As the cloud provider to allow auditing of the cloud by the client Why won’t work: Provider may be honest, sys admins may not be so Why won’t work: Providers are not willing to open their system to outside audits Workable Approach 3: Ask cloud provider for unforgeable proof/attestation Why may work: A third party proof not revealing other information may be enough for both client and provider

How to audit with a third party? Allow third party access to cloud? Use trusted hardware

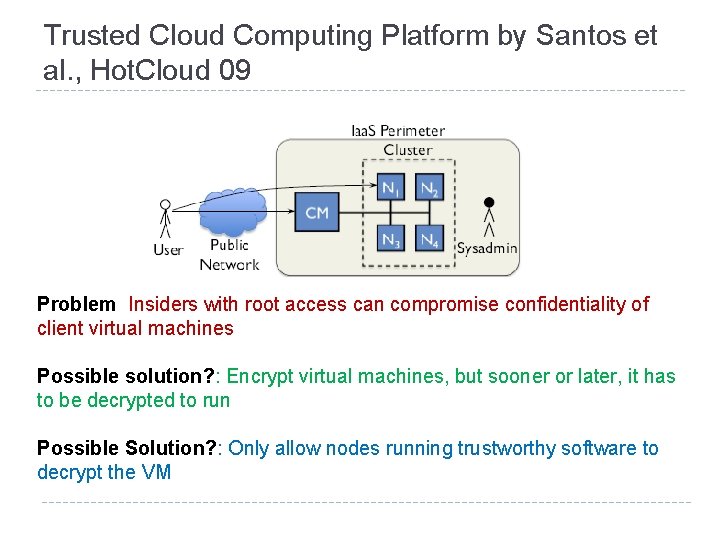
Trusted Cloud Computing Platform by Santos et al. , Hot. Cloud 09 Problem Insiders with root access can compromise confidentiality of client virtual machines Possible solution? : Encrypt virtual machines, but sooner or later, it has to be decrypted to run Possible Solution? : Only allow nodes running trustworthy software to decrypt the VM

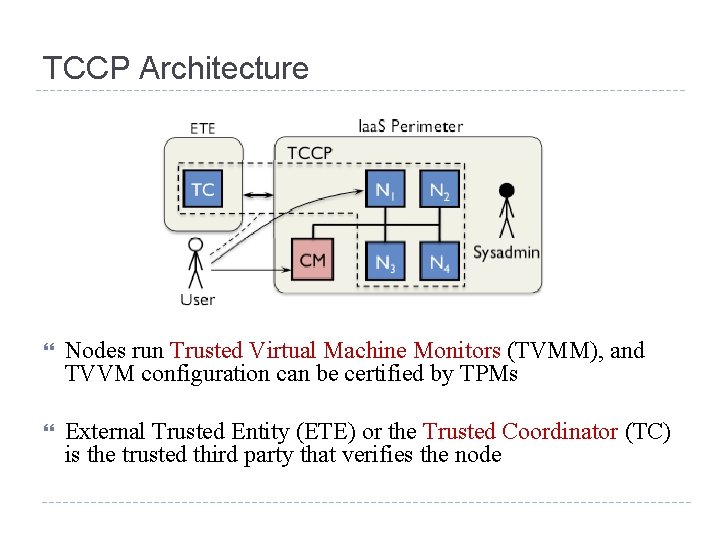
TCCP Architecture Nodes run Trusted Virtual Machine Monitors (TVMM), and TVVM configuration can be certified by TPMs External Trusted Entity (ETE) or the Trusted Coordinator (TC) is the trusted third party that verifies the node


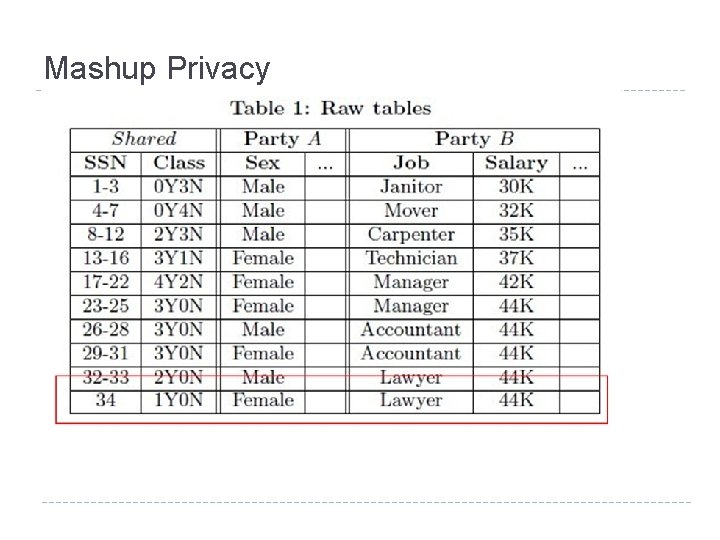
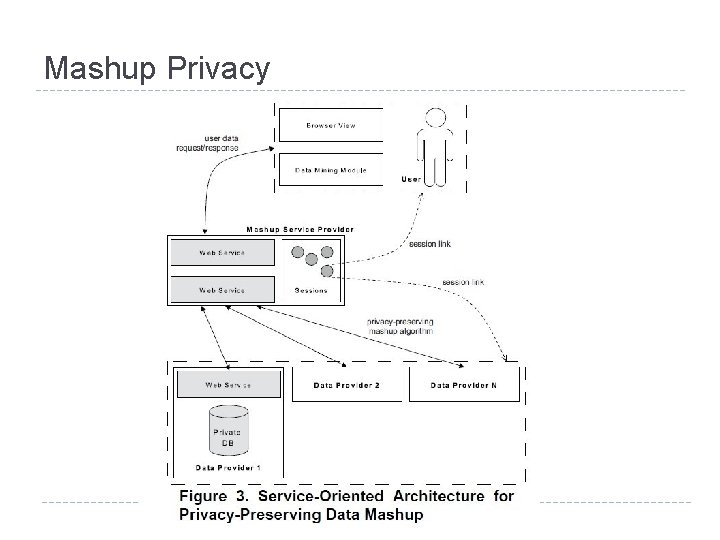
Mashup Privacy l 针对多个数据源Mashup时泄露隐私风险,建立一种安 全有效的隐私保护机制, Mashup后的数据不仅满足隐 私保护要求,还可以进行普通的查询和特定的数据挖 掘 作。 针对分析性数据 Thomas Trojer, Benjamin C. M. Fung, Patrick C. K. Hung: Service-Oriented Architecture for Privacy. Preserving Data Mashup. ICWS 2009: 767 -774


Mashup Privacy

Mashup Privacy



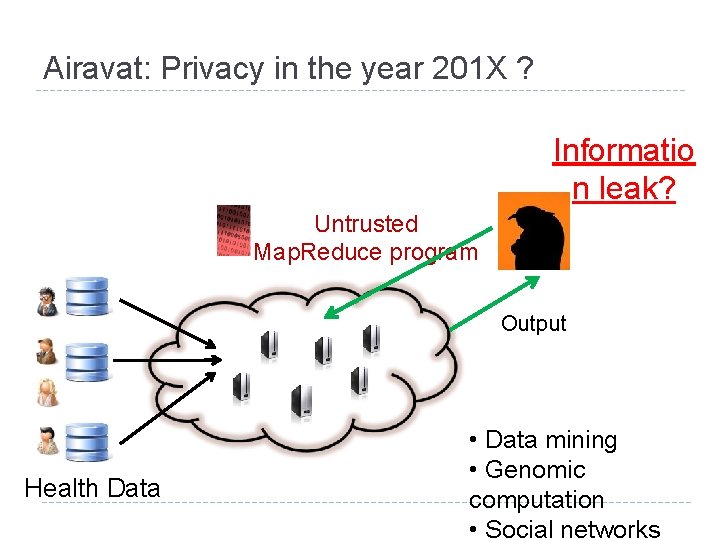
Airavat: Privacy in the year 201 X ? Informatio n leak? Untrusted Map. Reduce program Output Health Data • Data mining • Genomic computation • Social networks

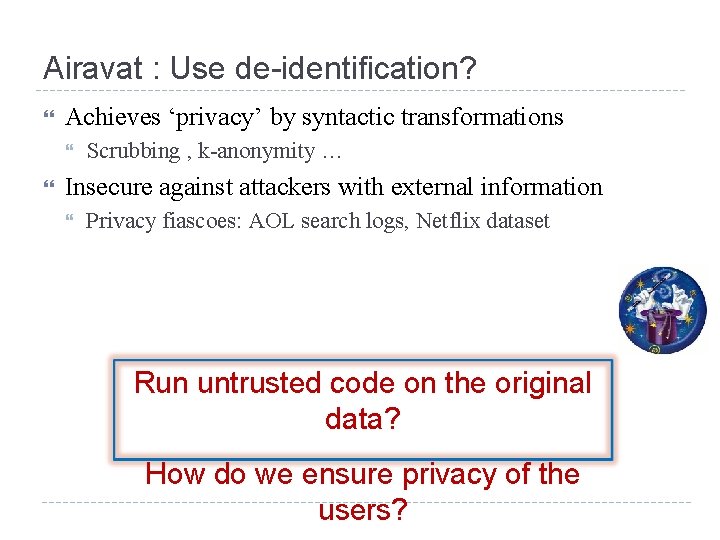
Airavat : Use de-identification? Achieves ‘privacy’ by syntactic transformations Scrubbing , k-anonymity … Insecure against attackers with external information Privacy fiascoes: AOL search logs, Netflix dataset Run untrusted code on the original data? How do we ensure privacy of the users?

Airavat : Audit the untrusted code? Audit all Map. Reduce programs for correctness? Aim: Confine the code instead of auditing Hard to do! Enlightenment? Also, where is the source code?

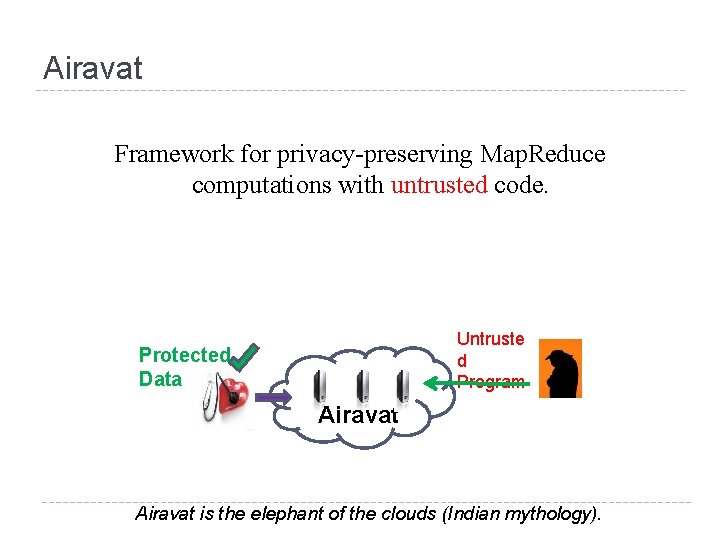
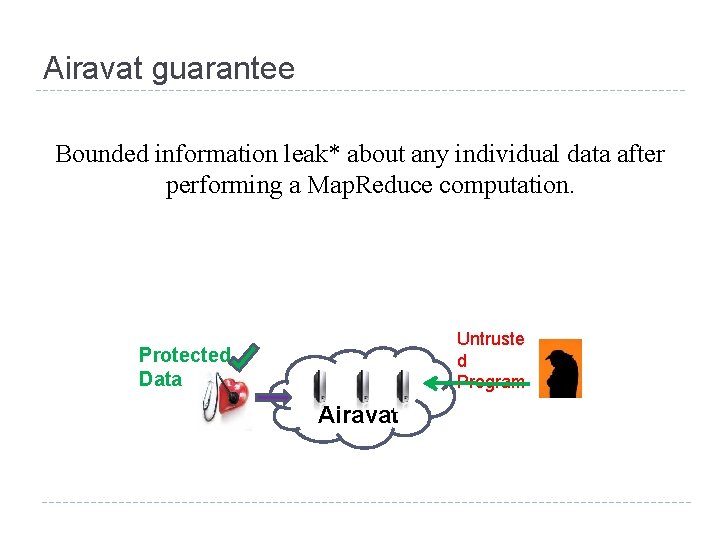
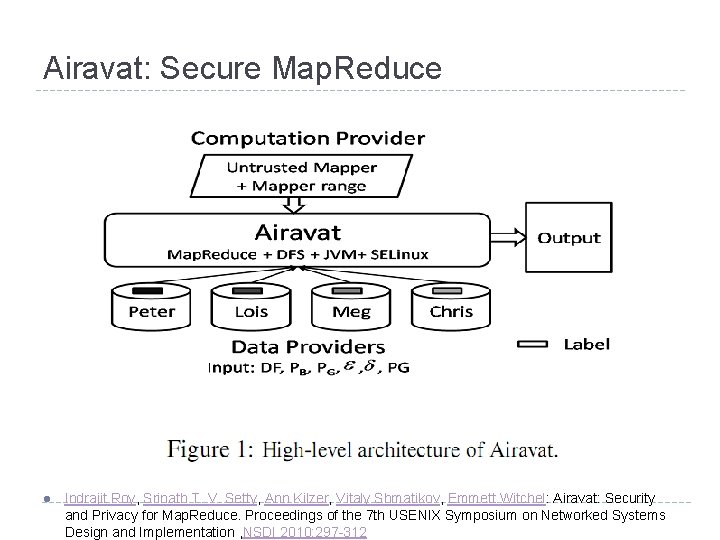
Airavat Framework for privacy-preserving Map. Reduce computations with untrusted code. Untruste d Program Protected Data Airavat is the elephant of the clouds (Indian mythology).

Airavat guarantee Bounded information leak* about any individual data after performing a Map. Reduce computation. Untruste d Program Protected Data Airavat

Airavat: Secure Map. Reduce l Indrajit Roy, Srinath T. V. Setty, Ann Kilzer, Vitaly Shmatikov, Emmett Witchel: Airavat: Security and Privacy for Map. Reduce. Proceedings of the 7 th USENIX Symposium on Networked Systems Design and Implementation , NSDI 2010: 297 -312

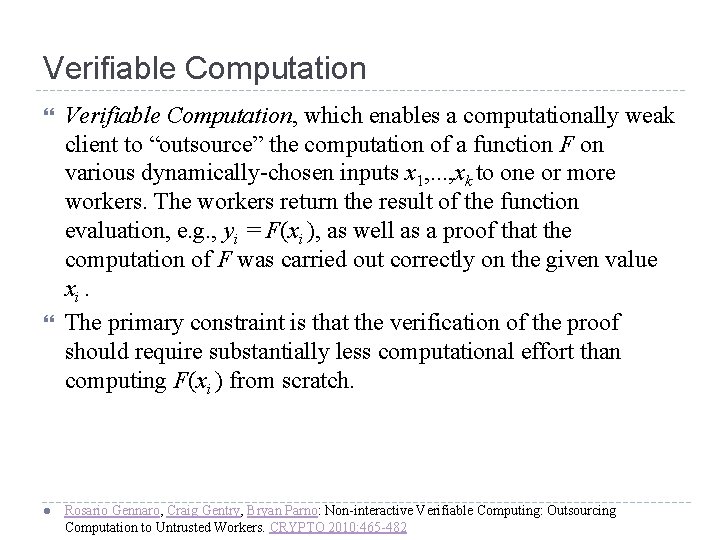
Verifiable Computation l Verifiable Computation, which enables a computationally weak client to “outsource” the computation of a function F on various dynamically-chosen inputs x 1, . . . , xk to one or more workers. The workers return the result of the function evaluation, e. g. , yi = F(xi ), as well as a proof that the computation of F was carried out correctly on the given value xi. The primary constraint is that the verification of the proof should require substantially less computational effort than computing F(xi ) from scratch. Rosario Gennaro, Craig Gentry, Bryan Parno: Non-interactive Verifiable Computing: Outsourcing Computation to Untrusted Workers. CRYPTO 2010: 465 -482

云数据管理 No. SQL DBMS based Database in the Cloud


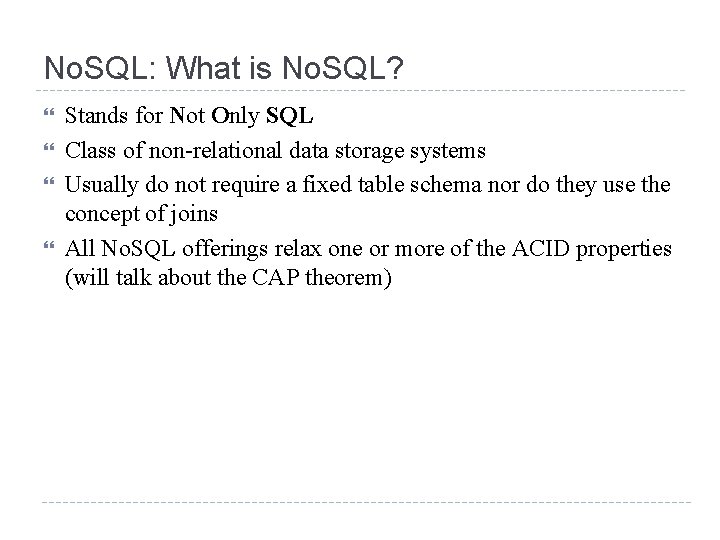
No. SQL: What is No. SQL? Stands for Not Only SQL Class of non-relational data storage systems Usually do not require a fixed table schema nor do they use the concept of joins All No. SQL offerings relax one or more of the ACID properties (will talk about the CAP theorem)

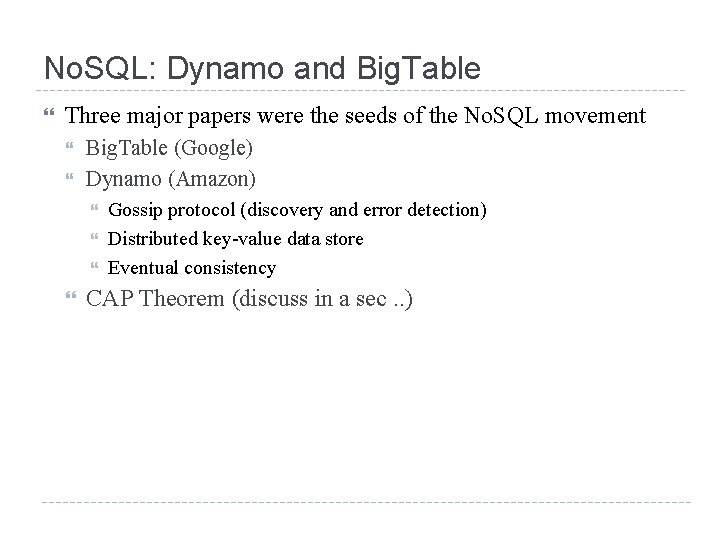
No. SQL: Dynamo and Big. Table Three major papers were the seeds of the No. SQL movement Big. Table (Google) Dynamo (Amazon) Gossip protocol (discovery and error detection) Distributed key-value data store Eventual consistency CAP Theorem (discuss in a sec. . )

No. SQL: CAP Theorem l Consistency(一致性):即数据一致性,简单的说,就是数据复制到 了N台机器,如果有更新,要N机器的数据是一起更新的。 Availability(可用性):好的响应性能,此项意思主要就是速度。 Partition tolerance(分区容错性):这里是说好的分区方法,体现具体 一点,简单地可理解为是节点的可扩展性。 定理:任何分布式系统只可同时满足二点,没法三者兼顾。 忠告:架构师不要将精力浪费在如何设计能满足三者的完美分布式系 统,而是应该进行取舍。 To scale out, you have to partition. That leaves either consistency or availability to choose from In almost all cases, you would choose availability over consistency Eric A. Brewer. Towards Robust Distributed Systems. 2000, http: //www. cs. berkeley. edu/~brewer/cs 262 b-2004/PODC-keynote. pdf

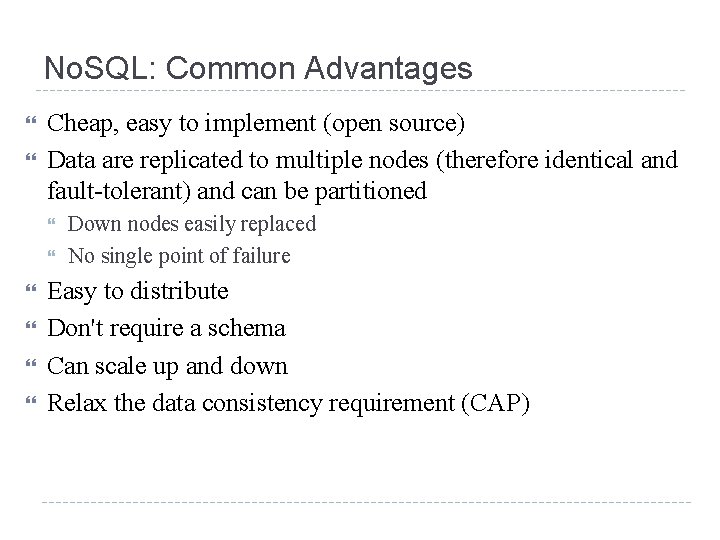
No. SQL: Common Advantages Cheap, easy to implement (open source) Data are replicated to multiple nodes (therefore identical and fault-tolerant) and can be partitioned Down nodes easily replaced No single point of failure Easy to distribute Don't require a schema Can scale up and down Relax the data consistency requirement (CAP)

No. SQL: What am I giving up? joins group by order by ACID transactions SQL as a sometimes frustrating but still powerful query language easy integration with other applications that support SQL

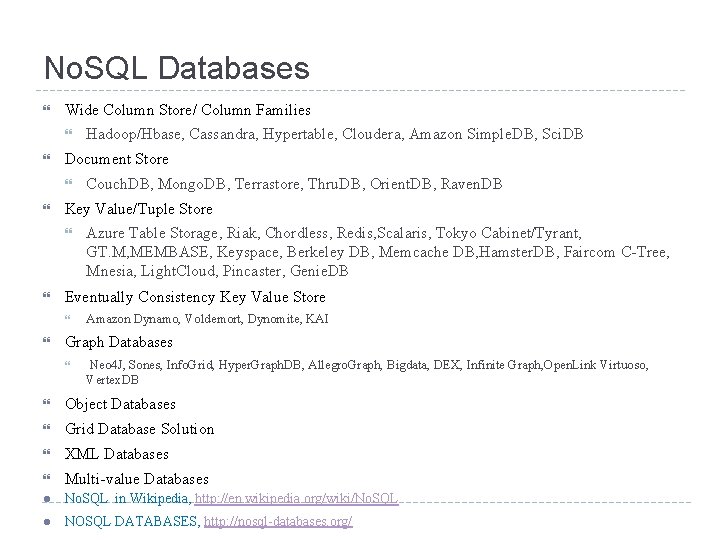
No. SQL Databases Wide Column Store/ Column Families Document Store Azure Table Storage, Riak, Chordless, Redis, Scalaris, Tokyo Cabinet/Tyrant, GT. M, MEMBASE, Keyspace, Berkeley DB, Memcache DB, Hamster. DB, Faircom C-Tree, Mnesia, Light. Cloud, Pincaster, Genie. DB Eventually Consistency Key Value Store Couch. DB, Mongo. DB, Terrastore, Thru. DB, Orient. DB, Raven. DB Key Value/Tuple Store Hadoop/Hbase, Cassandra, Hypertable, Cloudera, Amazon Simple. DB, Sci. DB Amazon Dynamo, Voldemort, Dynomite, KAI Graph Databases Neo 4 J, Sones, Info. Grid, Hyper. Graph. DB, Allegro. Graph, Bigdata, DEX, Infinite Graph, Open. Link Virtuoso, Vertex. DB Object Databases Grid Database Solution XML Databases Multi-value Databases l No. SQL in Wikipedia, http: //en. wikipedia. org/wiki/No. SQL l NOSQL DATABASES, http: //nosql-databases. org/

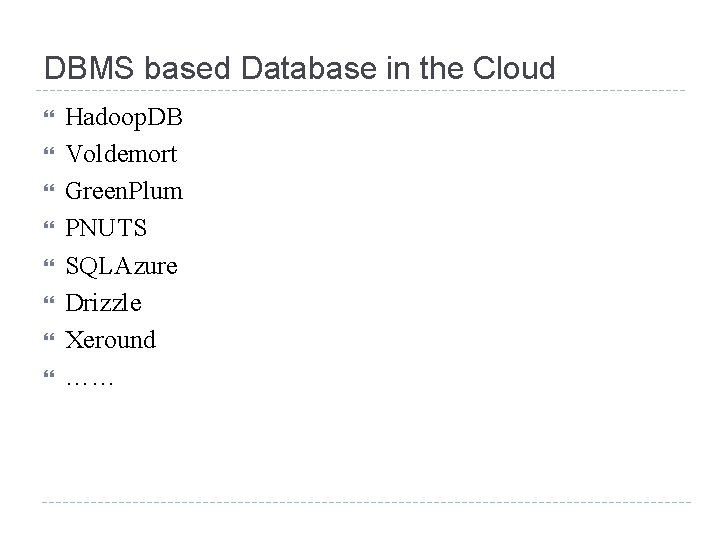
DBMS based Database in the Cloud Hadoop. DB Voldemort Green. Plum PNUTS SQLAzure Drizzle Xeround ……

Scalable Transactions for Web Applications in the Cloud 云平台良好的伸缩性和高可用性是有代价的。 仅支持对于主键(primary-key)的数据查询,不支持次 键(secondary-key)查询和连接查询(join queries)。 只支持最终数据一致性(eventual data consistency):即 任何数据更新可以在一个有限但不确定的时间后变得 可见。 某些应用需要一致性支持,如支付服务和在线拍卖, 有必要提供事务数据一致性(transactional data consistency)支持。 l. Zhou Wei, Guillaume Pierre, Chi-Hung Chi: Scalable Transactions for Web Applications in the Cloud. 15 th International Euro-Par Conference on Euro-Par 2009 Parallel Processing, Euro-Par 2009: 442453


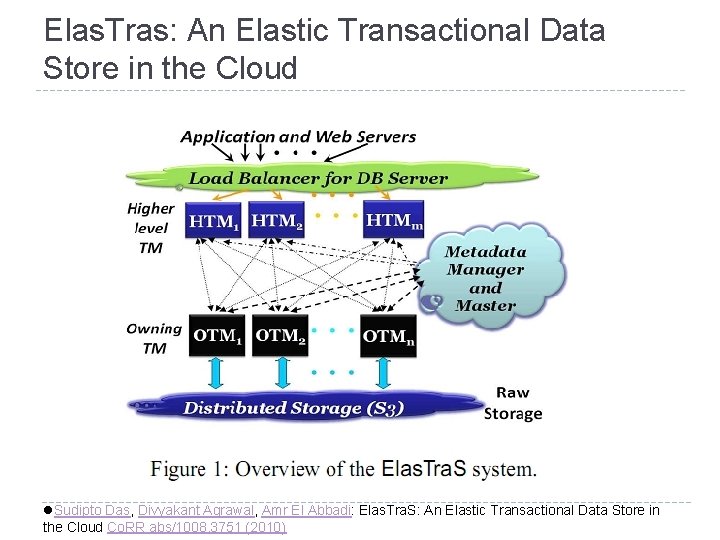
Elas. Tras: An Elastic Transactional Data Store in the Cloud l. Sudipto Das, Divyakant Agrawal, Amr El Abbadi: Elas. Tra. S: An Elastic Transactional Data Store in the Cloud Co. RR abs/1008. 3751 (2010)


 National institute of standards and technology
National institute of standards and technology Spike unist internship
Spike unist internship National assistive technology research institute
National assistive technology research institute National institute of agricultural technology
National institute of agricultural technology Vidhyadeep institute of engineering and technology
Vidhyadeep institute of engineering and technology Masdar institute of science and technology
Masdar institute of science and technology Madhav institute of technology and science
Madhav institute of technology and science Elearning adveti
Elearning adveti Sagar institute of research and technology
Sagar institute of research and technology Kigali institute of science and technology
Kigali institute of science and technology Bms institute of technology and management
Bms institute of technology and management Iist pune
Iist pune Shri dadaji institute of technology and science
Shri dadaji institute of technology and science Prof ram meghe institute of technology and research
Prof ram meghe institute of technology and research Mandava institute of engineering and technology
Mandava institute of engineering and technology Swami vivekanand institute of technology and management
Swami vivekanand institute of technology and management Corporate institute of science and technology bhopal
Corporate institute of science and technology bhopal Customer service standards table
Customer service standards table Regulatory agencies
Regulatory agencies Swedish national road and transport research institute
Swedish national road and transport research institute European telecommunications standards institute
European telecommunications standards institute Korean agency for technology and standards
Korean agency for technology and standards Shaala siddhi mission statement example
Shaala siddhi mission statement example Calc institute of technology
Calc institute of technology Waterford kamhlaba vacancies
Waterford kamhlaba vacancies Grenoble
Grenoble Gastechnology
Gastechnology Field stop vs aperture stop
Field stop vs aperture stop Dbs institute of technology
Dbs institute of technology Materials technology institute
Materials technology institute Sri lanka institute of information technology colors
Sri lanka institute of information technology colors Prajnanananda institute of technology & management
Prajnanananda institute of technology & management Monohakobi
Monohakobi Netherlands maritime institute of technology (nmit)
Netherlands maritime institute of technology (nmit) Stevens institute of technology
Stevens institute of technology Reel to reel institute
Reel to reel institute Kth royal institute of technology notable alumni
Kth royal institute of technology notable alumni Brno institute of technology
Brno institute of technology Sri lanka institute of information technology affiliations
Sri lanka institute of information technology affiliations Monohakobi technology institute
Monohakobi technology institute Illinois institute of technology toefl requirement
Illinois institute of technology toefl requirement Fromme423
Fromme423 Theory of probability is applied to in surveying
Theory of probability is applied to in surveying Itg gopeshwar
Itg gopeshwar Saigon institute for techniques & technology
Saigon institute for techniques & technology Hong kong institute for data science
Hong kong institute for data science Dublin institute of technology college of business
Dublin institute of technology college of business Communication research
Communication research Addis ababa university institute of technology
Addis ababa university institute of technology Mozambique national institute of meteorology
Mozambique national institute of meteorology Toshiba 1b japanasia
Toshiba 1b japanasia National university polytechnic institute
National university polytechnic institute National wind institute
National wind institute National institute on drug abuse
National institute on drug abuse National human genome research institute
National human genome research institute National human genome research institute
National human genome research institute National human genome research institute
National human genome research institute National human genome research institute
National human genome research institute National food service management institute
National food service management institute National electronics complex of pakistan
National electronics complex of pakistan National research institute of brewing
National research institute of brewing National technical university kharkiv polytechnic institute
National technical university kharkiv polytechnic institute National research center kurchatov institute
National research center kurchatov institute National research center kurchatov institute
National research center kurchatov institute National eye institute
National eye institute National institute of statistics romania
National institute of statistics romania National institute of agricultural botany
National institute of agricultural botany Ranipril
Ranipril Dr adarsh kumar national heart institute
Dr adarsh kumar national heart institute National yunlin university of science and technology
National yunlin university of science and technology National technology transfer
National technology transfer National unification and the national state
National unification and the national state Ohio technology standards
Ohio technology standards