Social Engineering Hacking your head Cristian Zaharia Security











- Slides: 23

Social Engineering Hacking your head Cristian Zaharia Security Systems Sr. Advisor Def. Camp – Bucharest 10 th-11 th of November 2016

Background • Police Officer - Computer Intrusion Investigator Certifications Ø 13 - Country Cyber-Forensics International Task Force • Computer Hacking ØJoint Romanian/FBI Task Force Forensic Investigator Cristian ZAHARIA Intelligence / Law Enforcement Information Technology Information Security My motto: Keep up the good work! • Incident Response Team Lead / Sr. Security Advisor Ø“Eyes on glass” real-time security monitoring / analysis ØSecurity standardization & training ØSecurity Incident Detection & Response best practices • Comp. TIA Security+ • Qualys. Guard Certified Specialist • Fire. Eye Junior Systems Engineer • Splunk Power User

Social Engineering


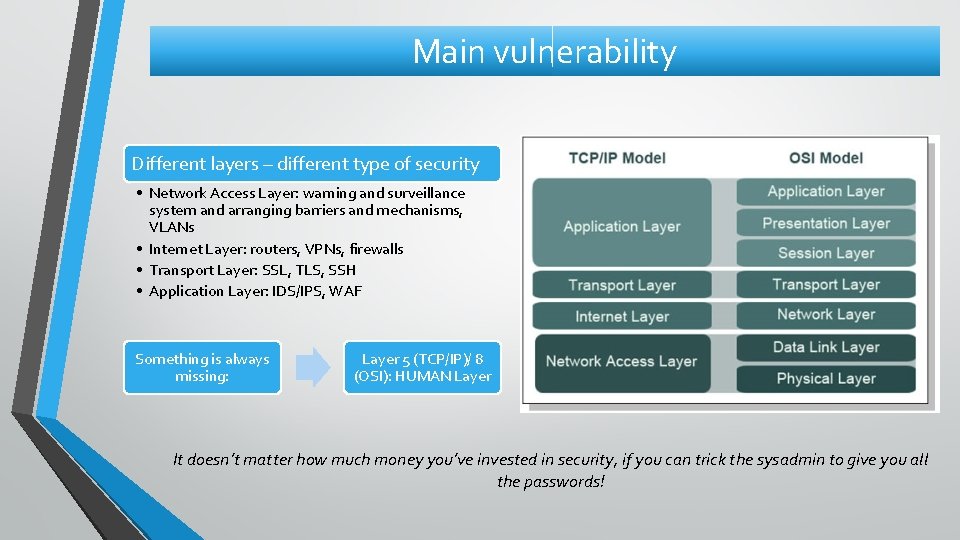
Main vulnerability Different layers – different type of security • Network Access Layer: warning and surveillance system and arranging barriers and mechanisms, VLANs • Internet Layer: routers, VPNs, firewalls • Transport Layer: SSL, TLS, SSH • Application Layer: IDS/IPS, WAF Something is always missing: Layer 5 (TCP/IP)/ 8 (OSI): HUMAN Layer It doesn’t matter how much money you’ve invested in security, if you can trick the sysadmin to give you all the passwords!

Key factor Psychology: take advantage of human psychology - the desire for something free, the susceptibility to distraction, or the desire to be liked or to be helpful.

Why We’re Vulnerable Our desire to be helpful / Moral Duty Our tendency to trust people we don’t know. Our fear of getting into trouble. Respect for Authority Chance of a Reward Cognitive biases: if someone seems kind and generous, perhaps one might believe that they are also intelligent and honest.

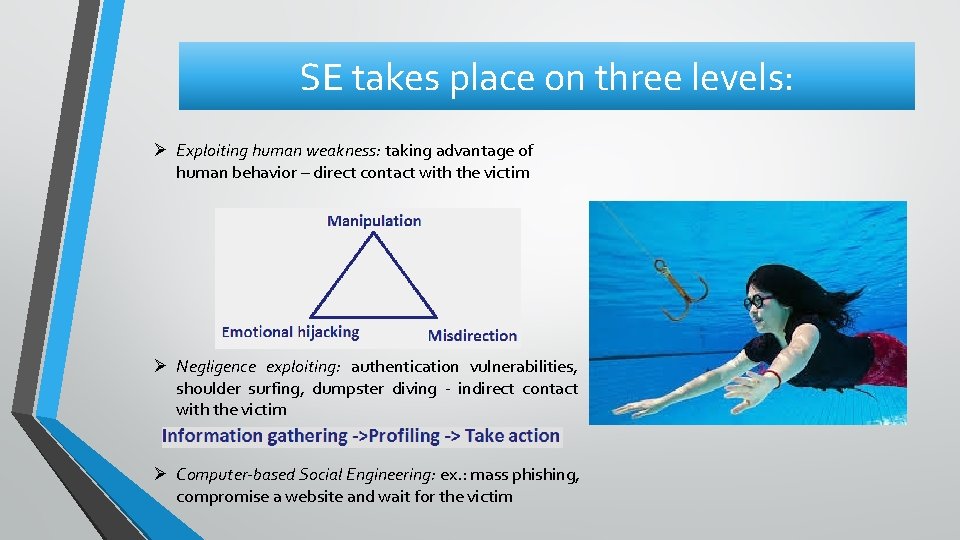
SE takes place on three levels: Ø Exploiting human weakness: taking advantage of human behavior – direct contact with the victim Ø Negligence exploiting: authentication vulnerabilities, shoulder surfing, dumpster diving - indirect contact with the victim Ø Computer-based Social Engineering: ex. : mass phishing, compromise a website and wait for the victim

First well-known case The wooden Trojan horse: a subterfuge that the Greeks used to enter the city of Troy and win the war.

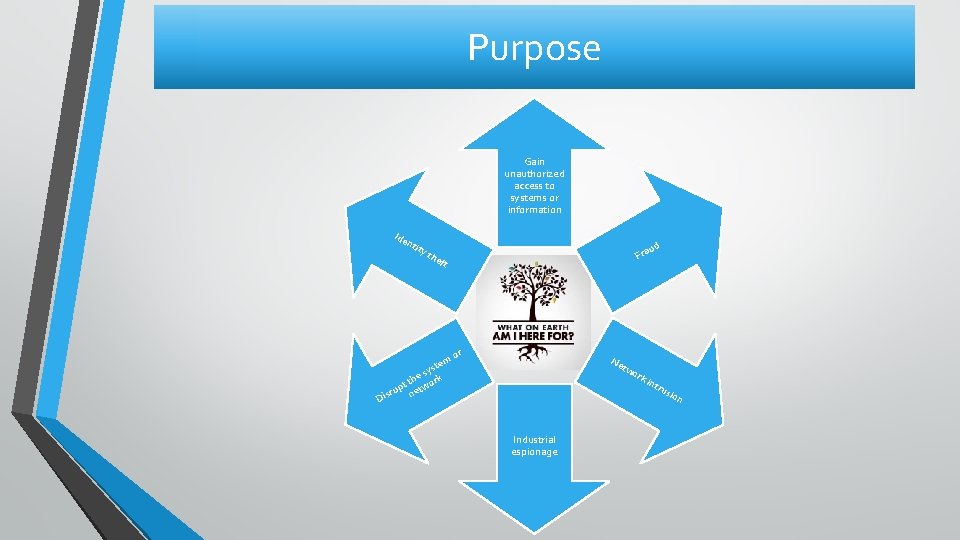
Purpose Gain unauthorized access to systems or information Ide nti ty th ud Fra eft or em yst s the rk pt etwo u r n Dis Ne tw ork int rus ion Industrial espionage

Theory in practice Fraud cases: Car Accident method - Scammers may pose as relatives or lawyers, calling or sending messages to urge the victim to wire money immediately. They’ll say they need cash to help with an emergency — like paying a hospital bill, getting out of jail, etc. Online Fraud Cases: Scam auctions - Hackerville: Ramnicu Valcea & Alexandria – millions of dollars have been sent to the criminals, during the last 10 years. Deceitful Commercial transaction : “eavesdropping” the communication between two companies with the purpose to modify the seller’s bank account written on the swift. Not paying attention to this, the money will be transferred to a different account

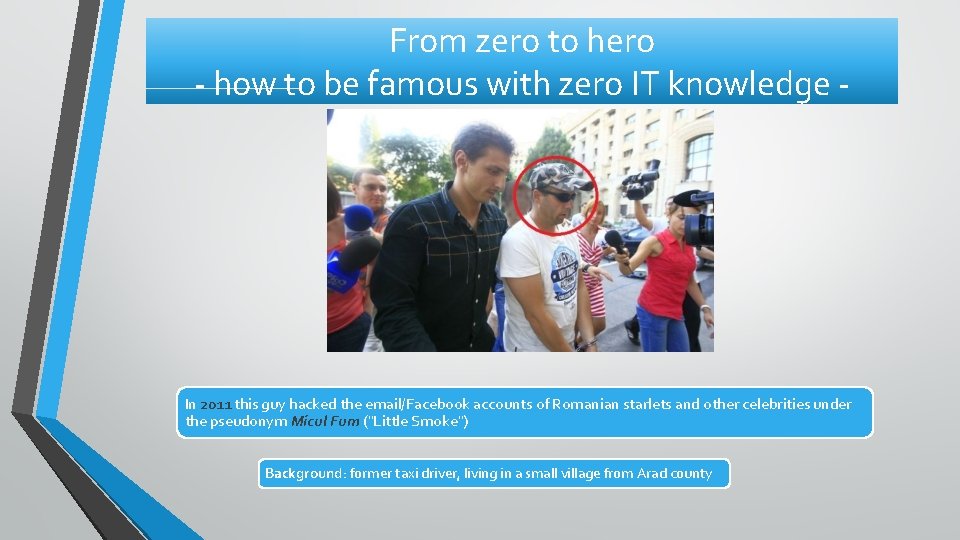
From zero to hero - how to be famous with zero IT knowledge - In 2011 this guy hacked the email/Facebook accounts of Romanian starlets and other celebrities under the pseudonym Micul Fum ("Little Smoke") Background: former taxi driver, living in a small village from Arad county

Required Tools for being in the spotlight Free working public proxies to hide his real IP address Check his IP public IP address with “IP chicken” solution

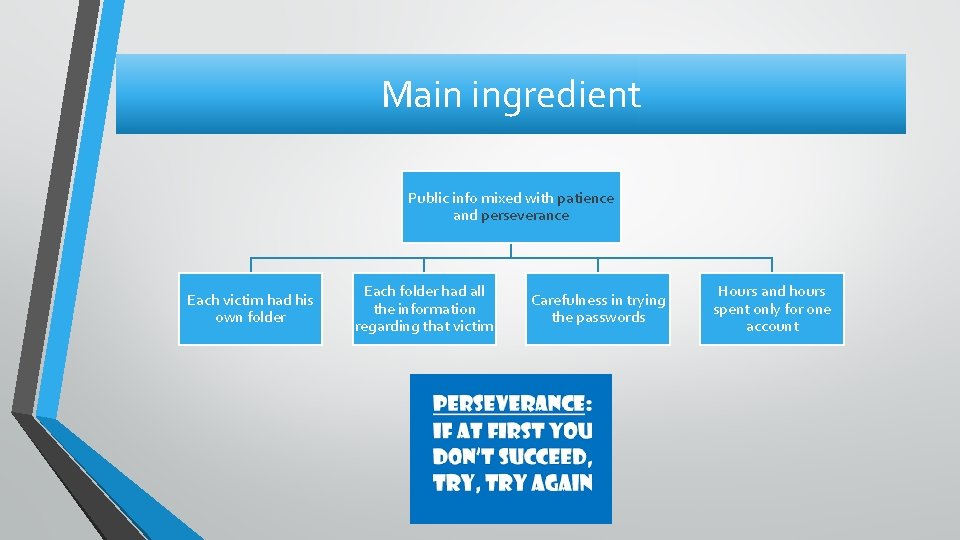
Main ingredient Public info mixed with patience and perseverance Each victim had his own folder Each folder had all the information regarding that victim Carefulness in trying the passwords Hours and hours spent only for one account

When Social Engineering flows through the veins Guccifer Case

Deja-vu Responsible for a number of high-level computer security breaches in the U. S. and Romania. Guccifer targeted celebrities, Romanian and U. S. government officials, and other prominent persons. • Same pattern: free proxies -> patience and persistence to obtain private information • No fancy equipment, only a clunky NEC desktop

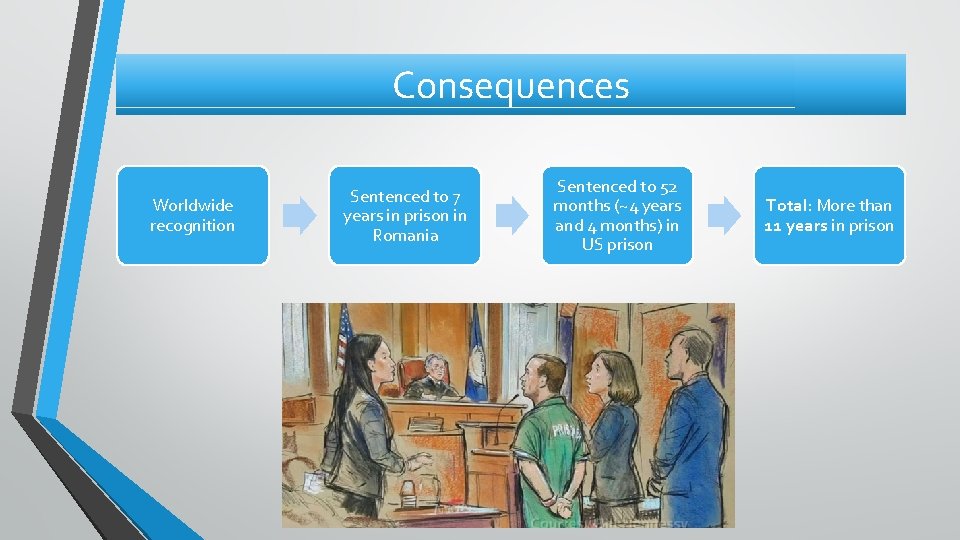
Consequences Worldwide recognition Sentenced to 7 years in prison in Romania Sentenced to 52 months (~4 years and 4 months) in US prison Total: More than 11 years in prison

This case was used for political purposes Many rumors around his actions and consequences All the tabloids wrote about secrets found in these e-mails Romanian hacker found dead in jail cell Guccifer 2. 0

Best practices to protect your PII • Be suspicious: from individuals seeking internal organizational data or PII • Stick to your guns: If you do get a feeling that someone is fishing for information that they shouldn't, trust your instincts • Pay attention to website URLs that use a variation in spelling or a different domain (e. g. , . com vs. . net). • Verify a request’s authenticity by contacting the company directly. • USE 2 -factor authentication • Continuously inform yourself about new threats and trends

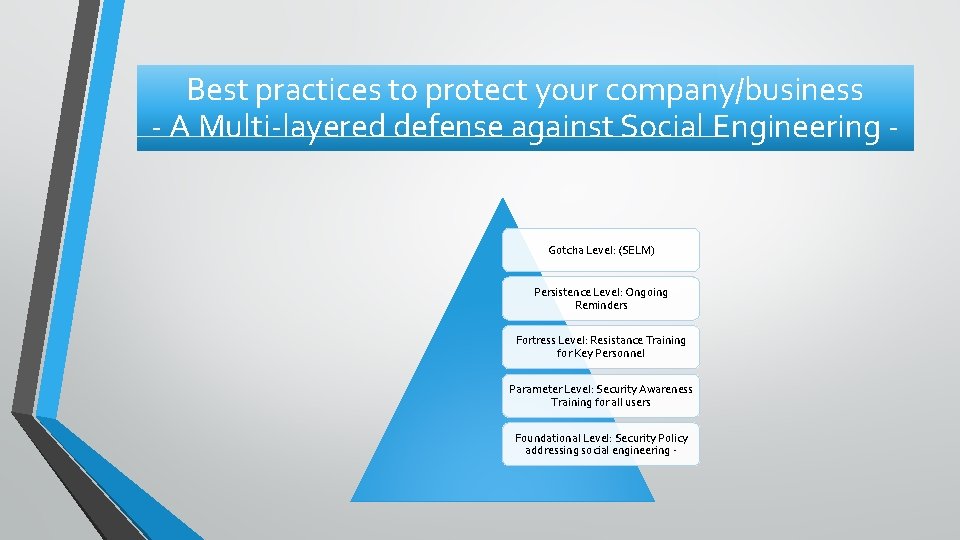
Best practices to protect your company/business - A Multi-layered defense against Social Engineering - Gotcha Level: (SELM) Persistence Level: Ongoing Reminders Fortress Level: Resistance Training for Key Personnel Parameter Level: Security Awareness Training for all users Foundational Level: Security Policy addressing social engineering -

Questions without an answer…or are they? Will we ever be safe enough against SE? Could technology and AI entirely replace the human factor? Will this “fight” against SE ever stop?

Questions?
