INTRODUCTION TO GAME HACKING Disclaimer Sole purpose of











- Slides: 23

INTRODUCTION TO GAME HACKING

Disclaimer • Sole purpose of this presentation is giving people insight into how the game hackers achieve their unfair activities and gain advantage over normal players. • Don’t do anything negatively impacts anyone.

Overview • Whoami • Importance of game security • Differences between usual binaries and game binaries • How do online games work? • What is the entry point of cheaters? • What is a must for these entries and how can they get it? • Cat and mouse game begins

whoami Yusuf Kocadaş • Final year Computer Engineering Student • Reverse engineering enthusiast • Formerly intern at TUBITAK BILGEM

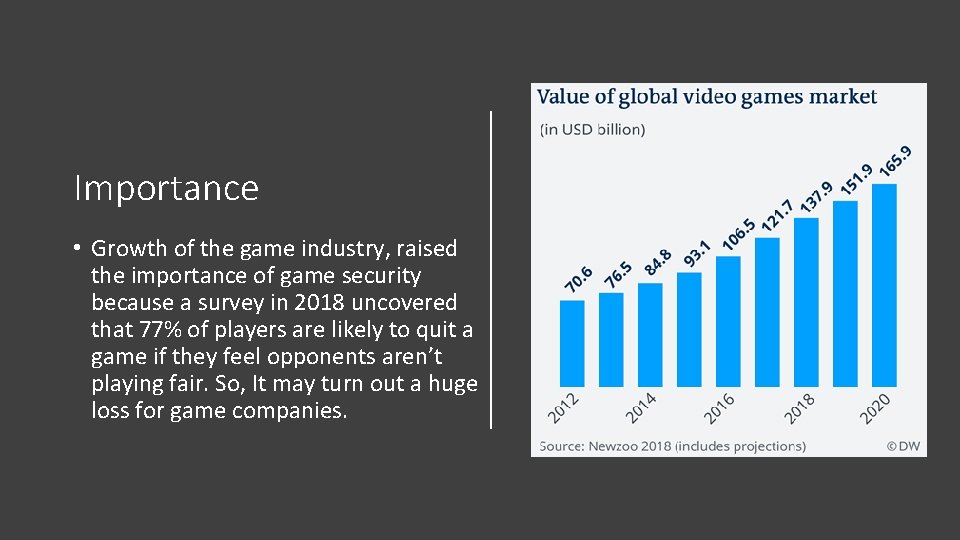
Importance • Growth of the game industry, raised the importance of game security because a survey in 2018 uncovered that 77% of players are likely to quit a game if they feel opponents aren’t playing fair. So, It may turn out a huge loss for game companies.

Game binaries • Thiscalling convention appears more than usual • Includes many graphical things • Continuously, data receiving and sending • It may directly send data to other players’ game clients • Launcher • Most of them weekly updated • Packed

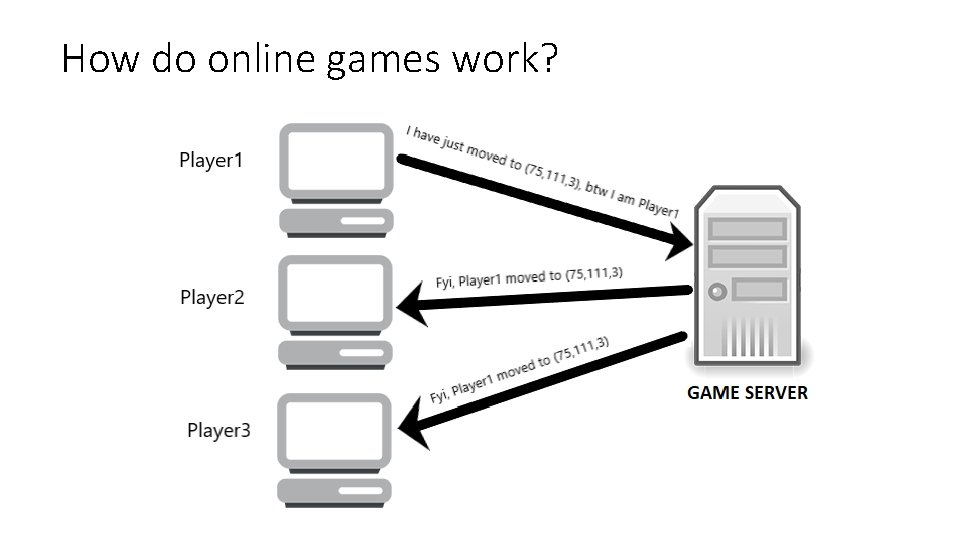
How do online games work?

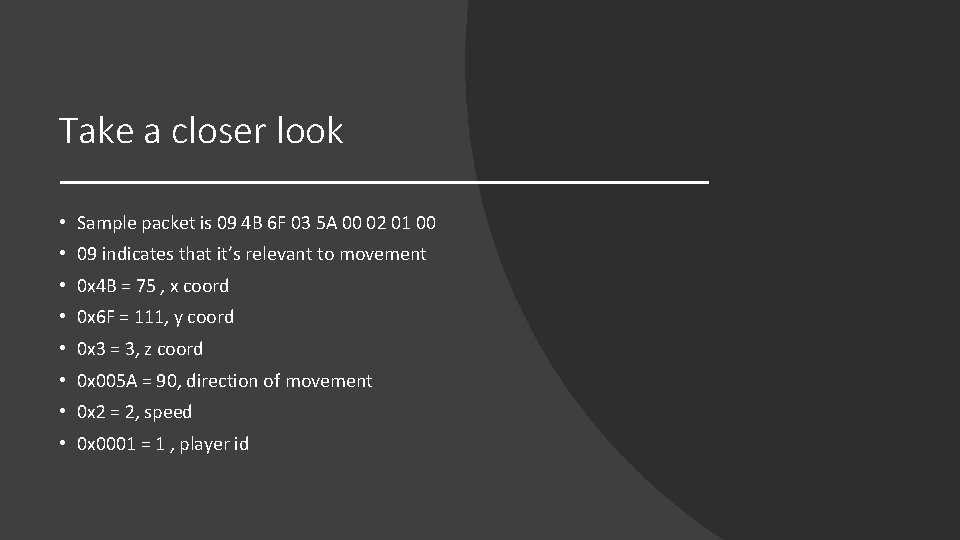
Take a closer look • Sample packet is 09 4 B 6 F 03 5 A 00 02 01 00 • 09 indicates that it’s relevant to movement • 0 x 4 B = 75 , x coord • 0 x 6 F = 111, y coord • 0 x 3 = 3, z coord • 0 x 005 A = 90, direction of movement • 0 x 2 = 2, speed • 0 x 0001 = 1 , player id

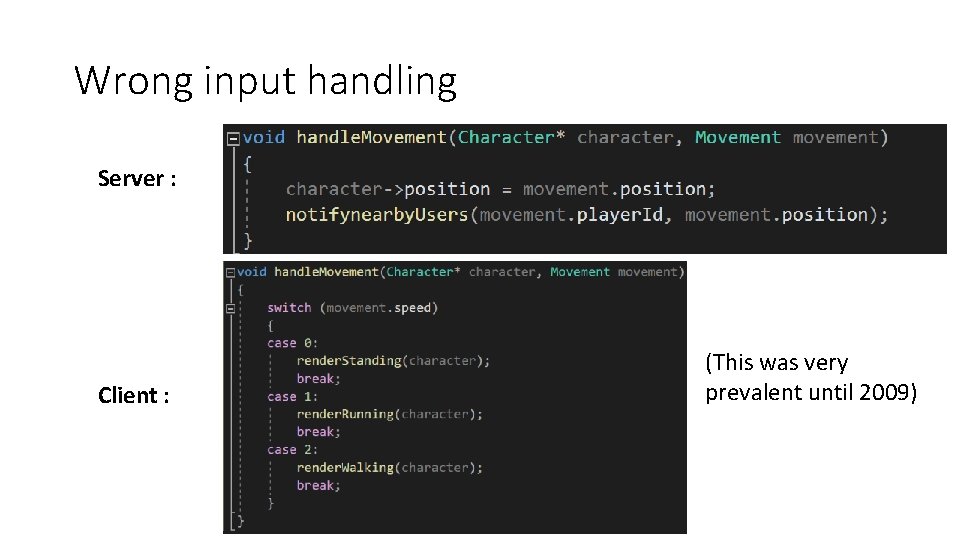
Wrong input handling Server : Client : (This was very prevalent until 2009)

Vulnerabilities • Attacker can teleport his character by changing x, y, z fields of packet • Attacker can teleport someone else’s character by changing player id field of packet • Attacker can hide itself or someone else.

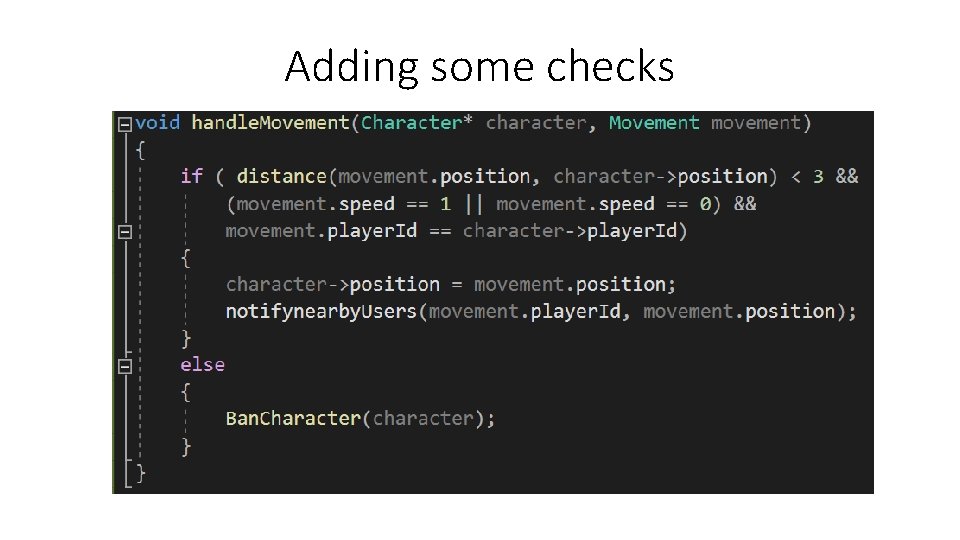
Adding some checks

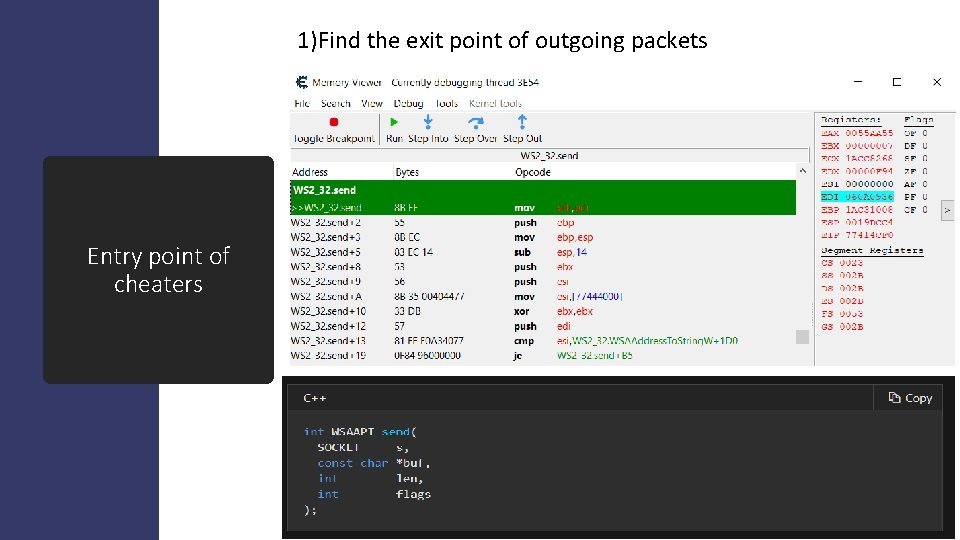
1)Find the exit point of outgoing packets Entry point of cheaters

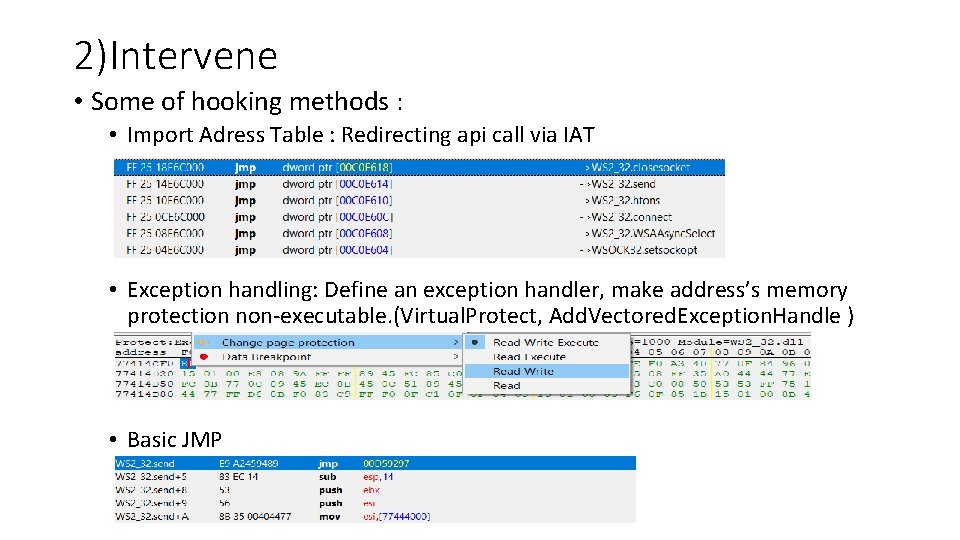
2)Intervene • Some of hooking methods : • Import Adress Table : Redirecting api call via IAT • Exception handling: Define an exception handler, make address’s memory protection non-executable. (Virtual. Protect, Add. Vectored. Exception. Handle ) • Basic JMP

3) Start fuzzing • Analyze packets • Interpret • Craft your own packets • Send packets and get responses

But… • There is a guy between you and the game…

Anti-Cheat • Anti-cheat software is designed to prevent players of online games from gaining unfair advantage through the use of third-party tools, usually taking the form of software hooks. (Wikipedia) • 1) Game-specific Anti-Cheats : Determines game-critical functions and files, focuses on these. (Riot’s Anti-Cheat) • 2) General Anti-Cheats : Mostly focuses on general things like api hooking, dll injection, heartbeat, handle, process and window enumeration, anti-debugging and reversing techniques. (Valve Anti-Cheat, XIGNCODE, Battle. Eye)

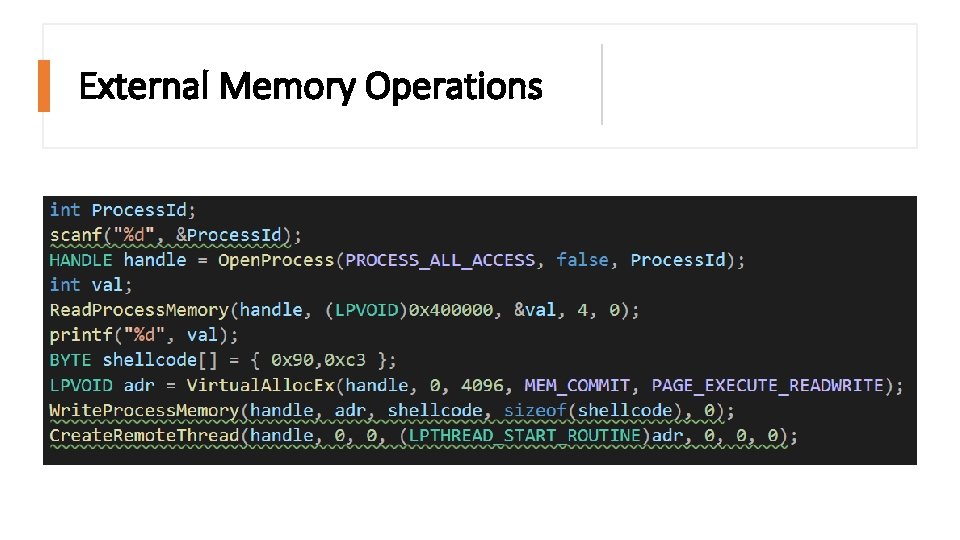
External Memory Operations

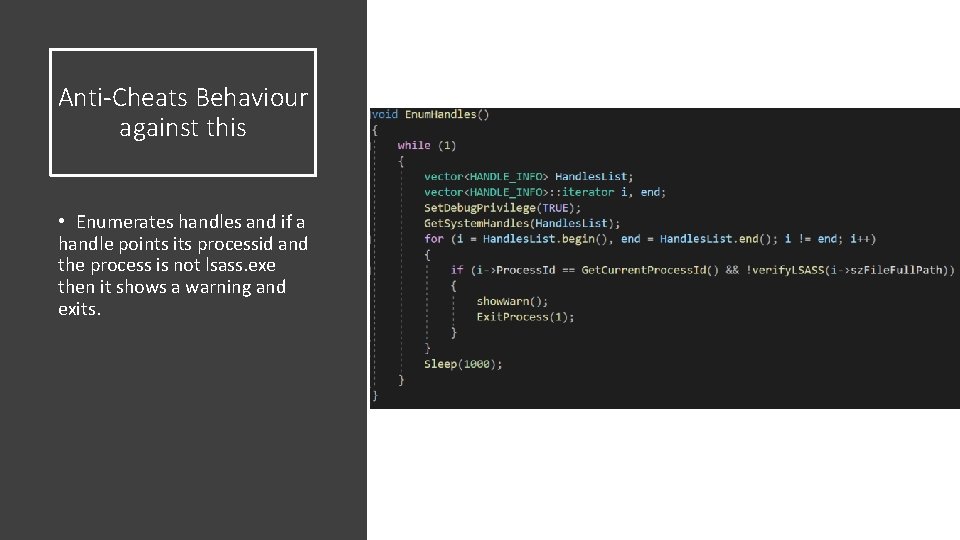
Anti-Cheats Behaviour against this • Enumerates handles and if a handle points its processid and the process is not lsass. exe then it shows a warning and exits.


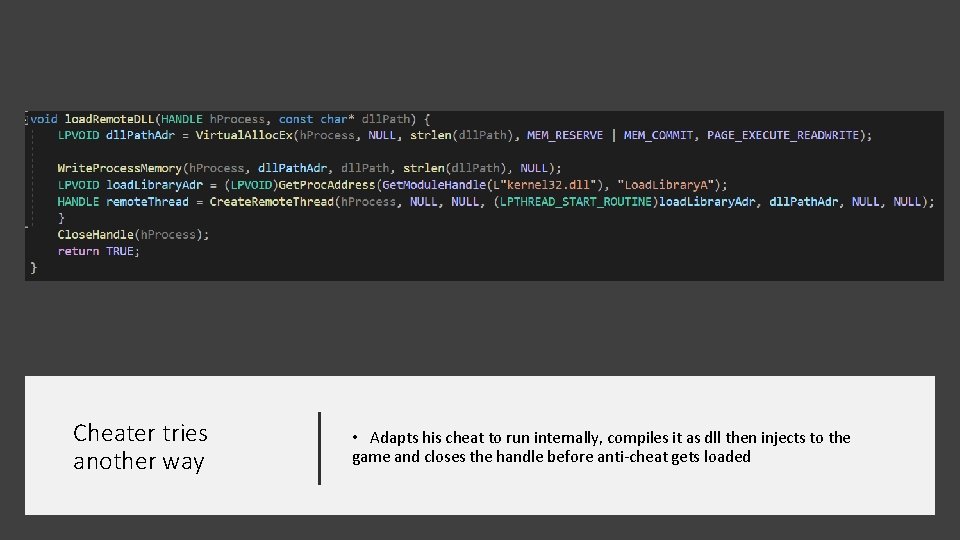
Cheater tries another way • Adapts his cheat to run internally, compiles it as dll then injects to the game and closes the handle before anti-cheat gets loaded

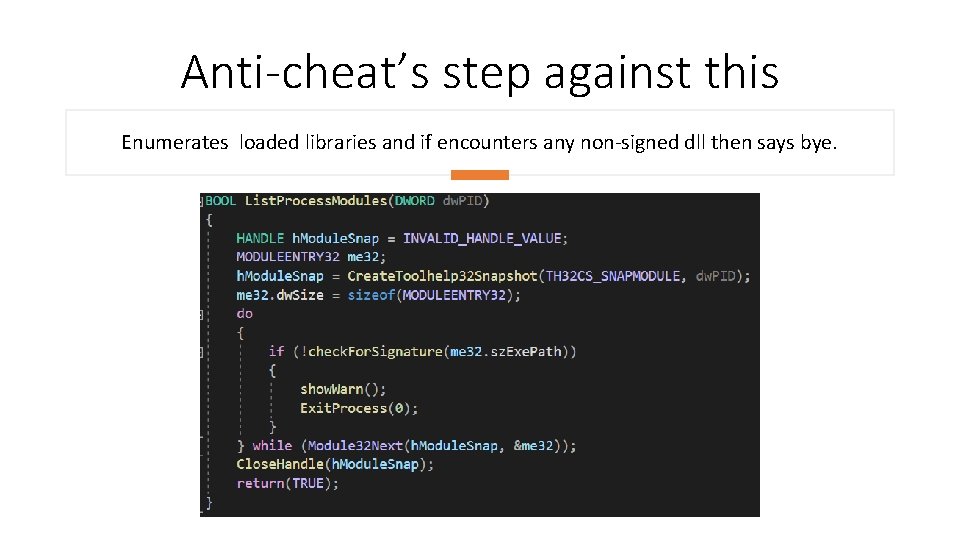
Anti-cheat’s step against this Enumerates loaded libraries and if encounters any non-signed dll then says bye.

There's always a third way Direct Memory Access(DMA) is a method that allows an input/output (I/O) device to send or receive data directly to or from the main memory. • Hardware-based • Has its own difficulties • Limited

Contact