Hacking Team RCS Remote Control System Remote Control
![]Hacking Team[ RCS Remote Control System ]Hacking Team[ RCS Remote Control System](https://slidetodoc.com/presentation_image_h/c340f4032134226fa61a81254445fa8a/image-1.jpg)











- Slides: 24
![Hacking Team RCS Remote Control System ]Hacking Team[ RCS Remote Control System](https://slidetodoc.com/presentation_image_h/c340f4032134226fa61a81254445fa8a/image-1.jpg)
]Hacking Team[ RCS Remote Control System

Remote Control System

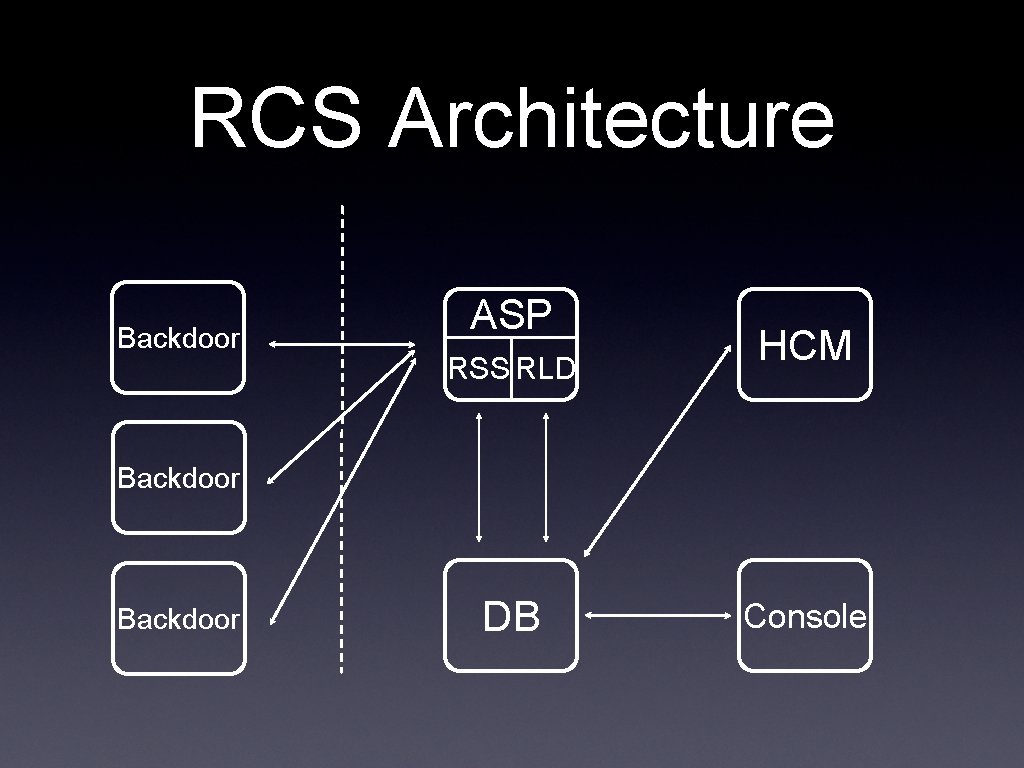
RCS Architecture Backdoor ASP RSS RLD HCM Backdoor DB Console

RCS Internals Backdoor ASP RSS RLD HCM Stealth monitoring program written both in C++ and ASM. Connects to ASP using an encrypted channel. It uses an event/actions paradigm and it is made up of different agents that can be activated separately. It is composed by two different windows services: RSS and RLD. RSS is responsible for the communication with the Backdoor. RLD decrypts the logs and sends them to the DB. It is used to create the configurations for the Backdoors. It communicates with ASP thru the DB in order to send the configurations to the Backdoors. It is used to create infection vectors such as melted executables, CD/USB, etc.

RCS Internals DB Console All the information about users, activities, targets, backdoors and logs are contained into the DB. All the other components talk to the DB thru an XML-RPC interface. This is the main visualization tool. It can be used to administrate users, groups, activities, targets and backdoors. It is used to browse the logs too. It is accessed by different users with different profiles (a user can only see logs from the activities assigned to him).

Backdoor

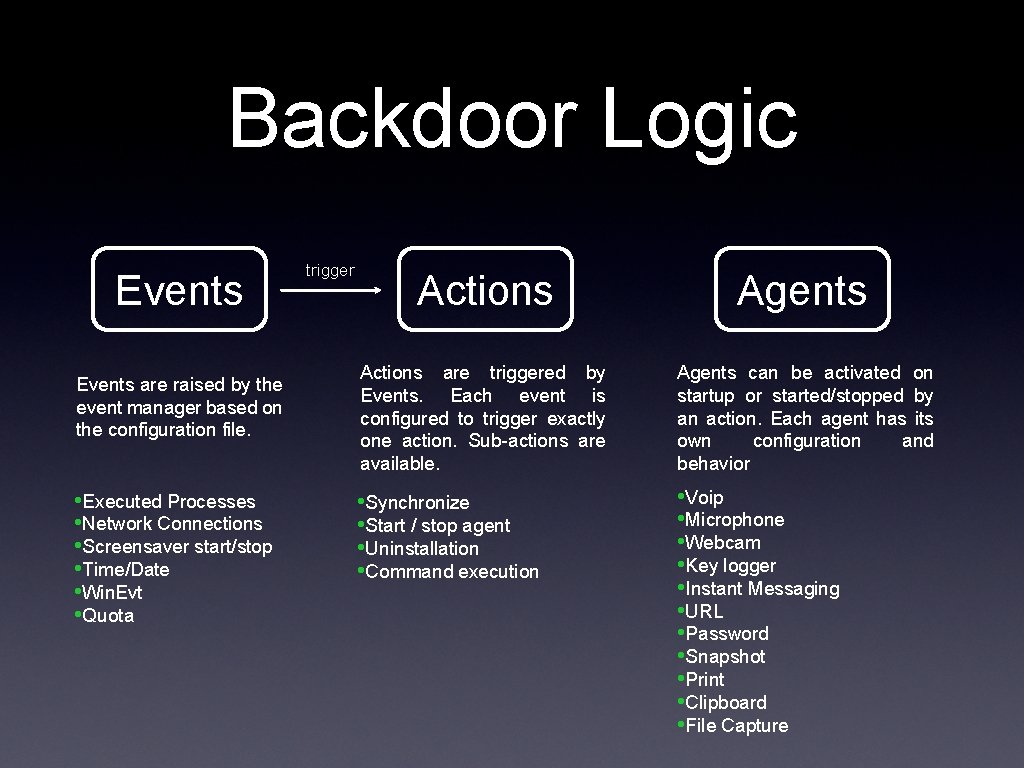
Backdoor Logic Events are raised by the event manager based on the configuration file. • Executed Processes • Network Connections • Screensaver start/stop • Time/Date • Win. Evt • Quota trigger Actions Agents Actions are triggered by Events. Each event is configured to trigger exactly one action. Sub-actions are available. Agents can be activated on startup or started/stopped by an action. Each agent has its own configuration and behavior • Synchronize • Start / stop agent • Uninstallation • Command execution • Voip • Microphone • Webcam • Key logger • Instant Messaging • URL • Password • Snapshot • Print • Clipboard • File Capture

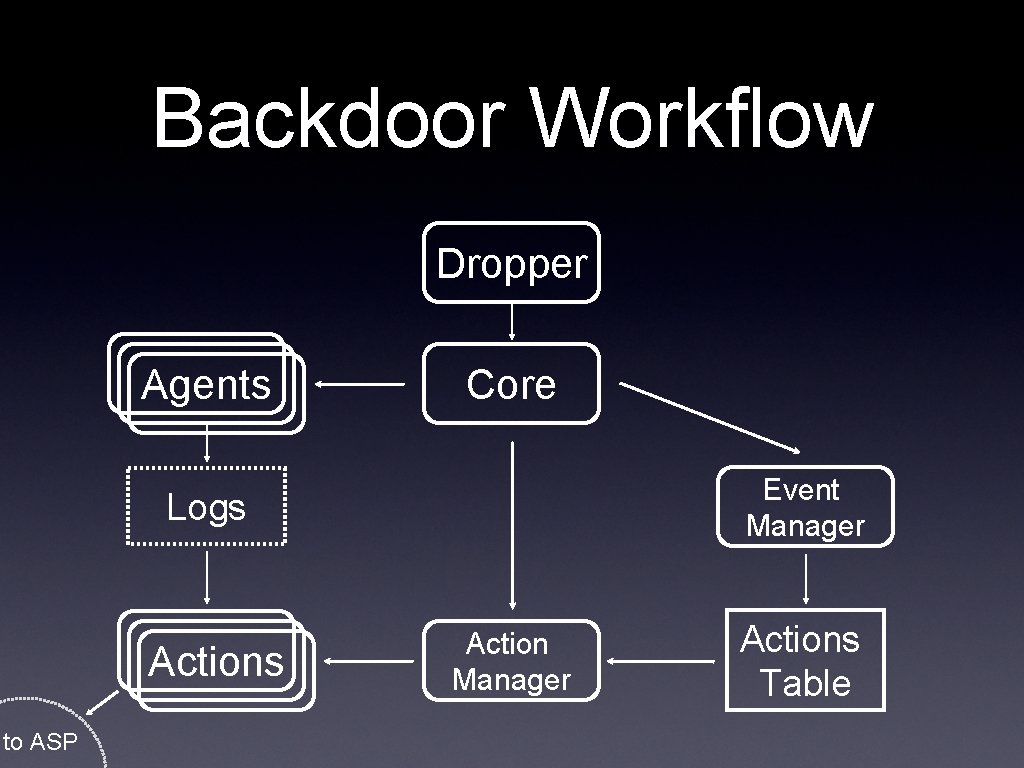
Backdoor Workflow Dropper Agents Core Event Manager Logs Actions to ASP Action Manager Actions Table

HCM

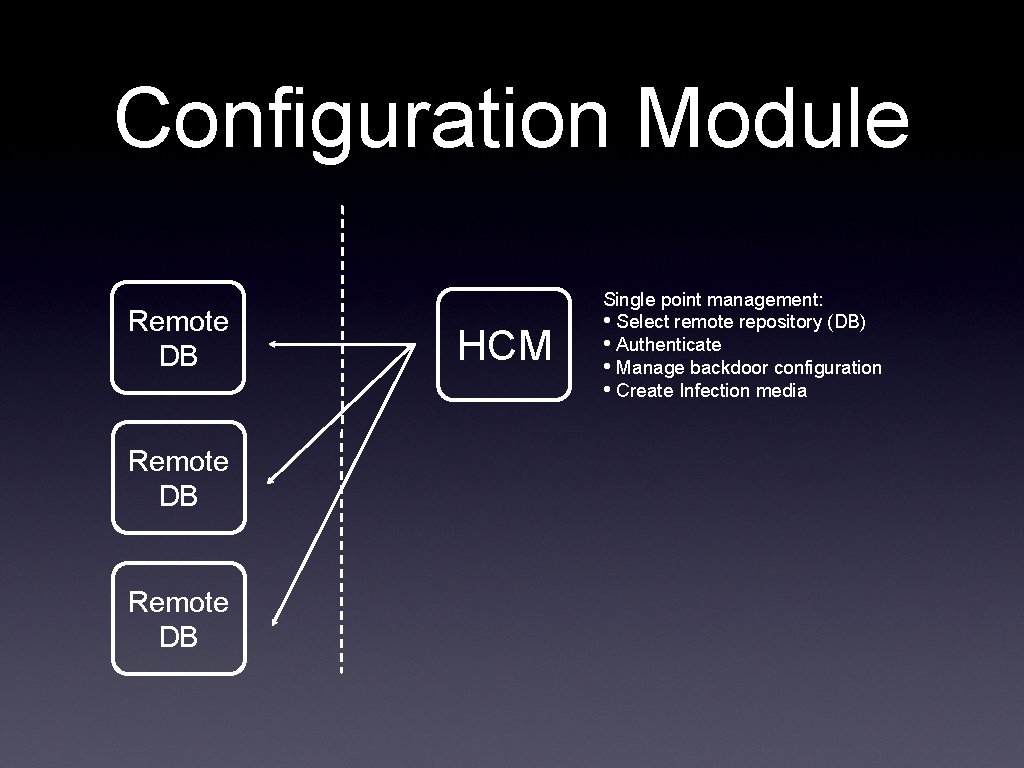
Configuration Module Remote DB HCM Single point management: • Select remote repository (DB) • Authenticate • Manage backdoor configuration • Create Infection media

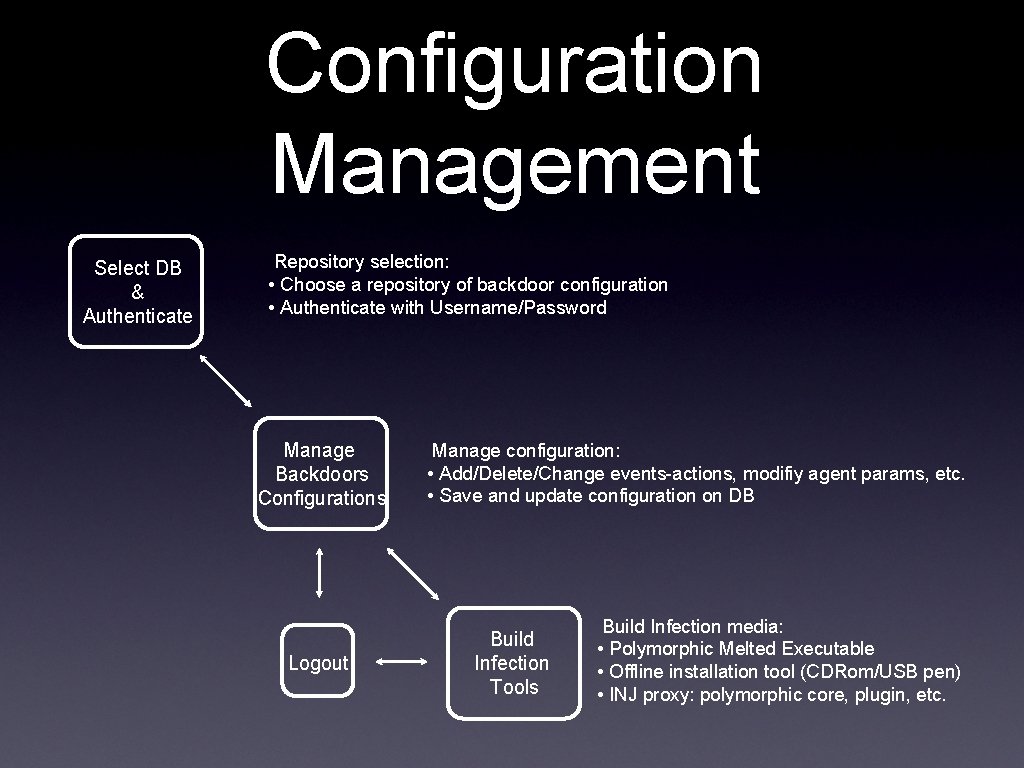
Configuration Management Select DB & Authenticate Repository selection: • Choose a repository of backdoor configuration • Authenticate with Username/Password Manage Backdoors Configurations Logout Manage configuration: • Add/Delete/Change events-actions, modifiy agent params, etc. • Save and update configuration on DB Build Infection Tools Build Infection media: • Polymorphic Melted Executable • Offline installation tool (CDRom/USB pen) • INJ proxy: polymorphic core, plugin, etc.

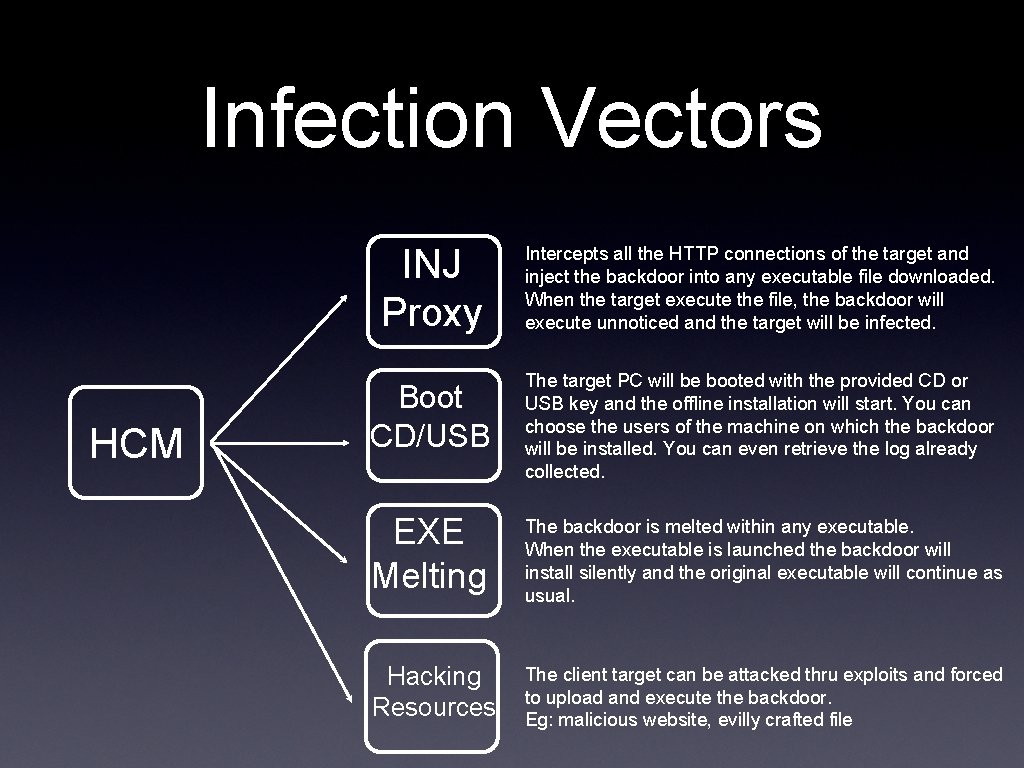
Infection Vectors HCM INJ Proxy Intercepts all the HTTP connections of the target and inject the backdoor into any executable file downloaded. When the target execute the file, the backdoor will execute unnoticed and the target will be infected. Boot CD/USB The target PC will be booted with the provided CD or USB key and the offline installation will start. You can choose the users of the machine on which the backdoor will be installed. You can even retrieve the log already collected. EXE Melting The backdoor is melted within any executable. When the executable is launched the backdoor will install silently and the original executable will continue as usual. Hacking Resources The client target can be attacked thru exploits and forced to upload and execute the backdoor. Eg: malicious website, evilly crafted file

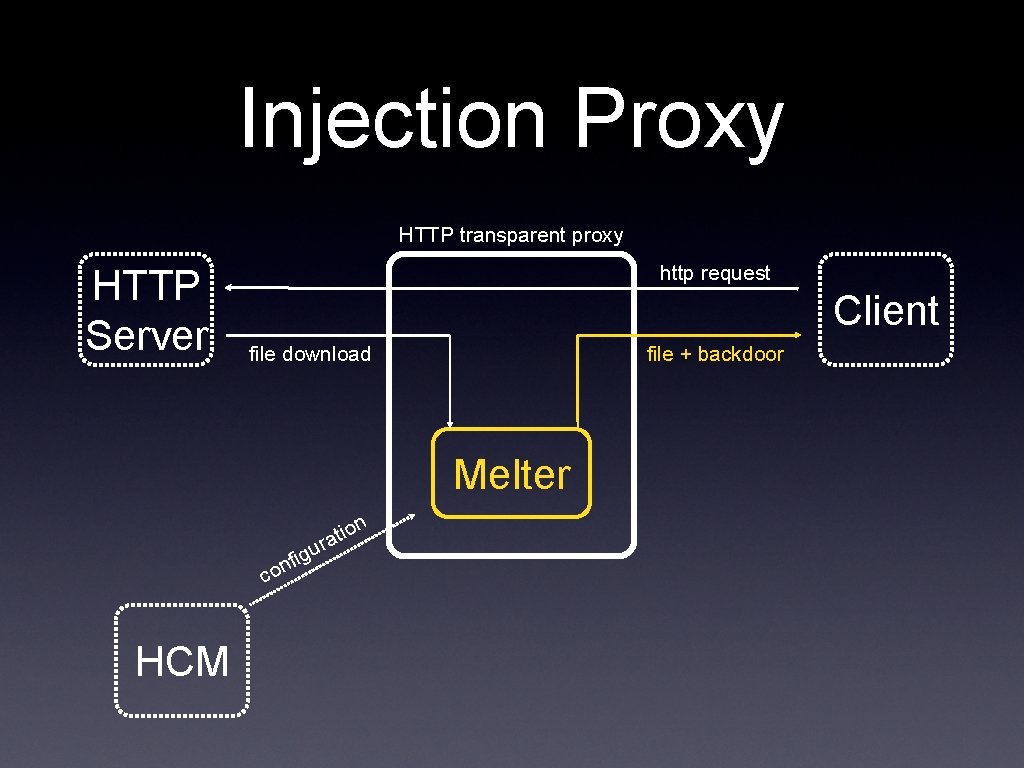
Injection Proxy

Injection Proxy HTTP transparent proxy HTTP Server http request Client file download file + backdoor Melter n co HCM g nfi u io rat

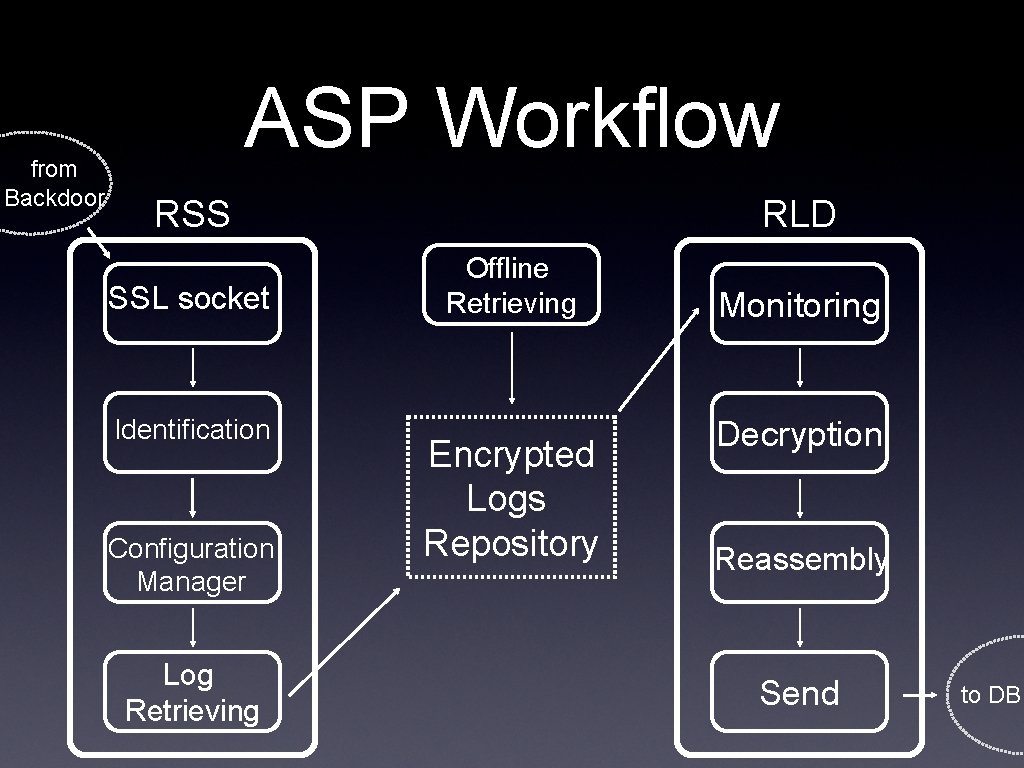
ASP

from Backdoor ASP Workflow RSS SSL socket Identification Configuration Manager Log Retrieving RLD Offline Retrieving Encrypted Logs Repository Monitoring Decryption Reassembly Send to DB

ASP Internals • Encrypted communications • Mutual authentication with the backdoors (prevents MITM and spoofing attacks) • Multi-threaded • Two independent window services for communication (RSS) and decryption (RLD) • Hidden behind a fake web server

DB

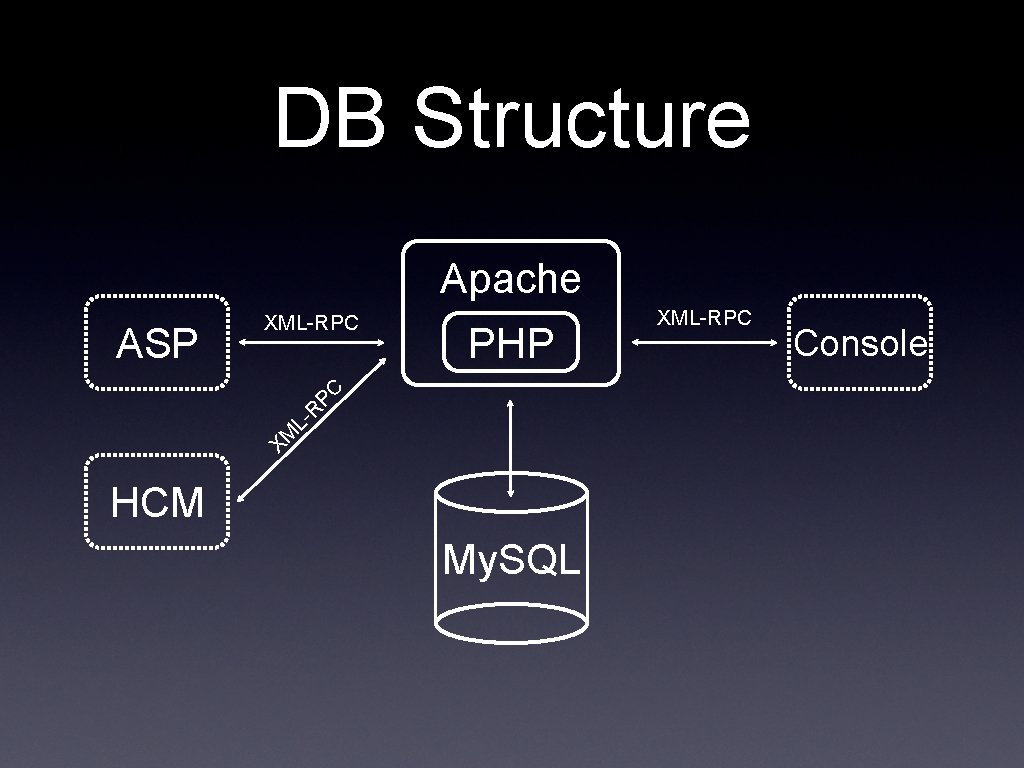
DB Structure Apache PHP XM L- R PC ASP XML-RPC HCM My. SQL XML-RPC Console

DB data organization • Users and Groups • Activities, Targets and Backdoors • Logs • Audit Logs • Binaries and Certificates • Encryption Keys • Configurations

Console

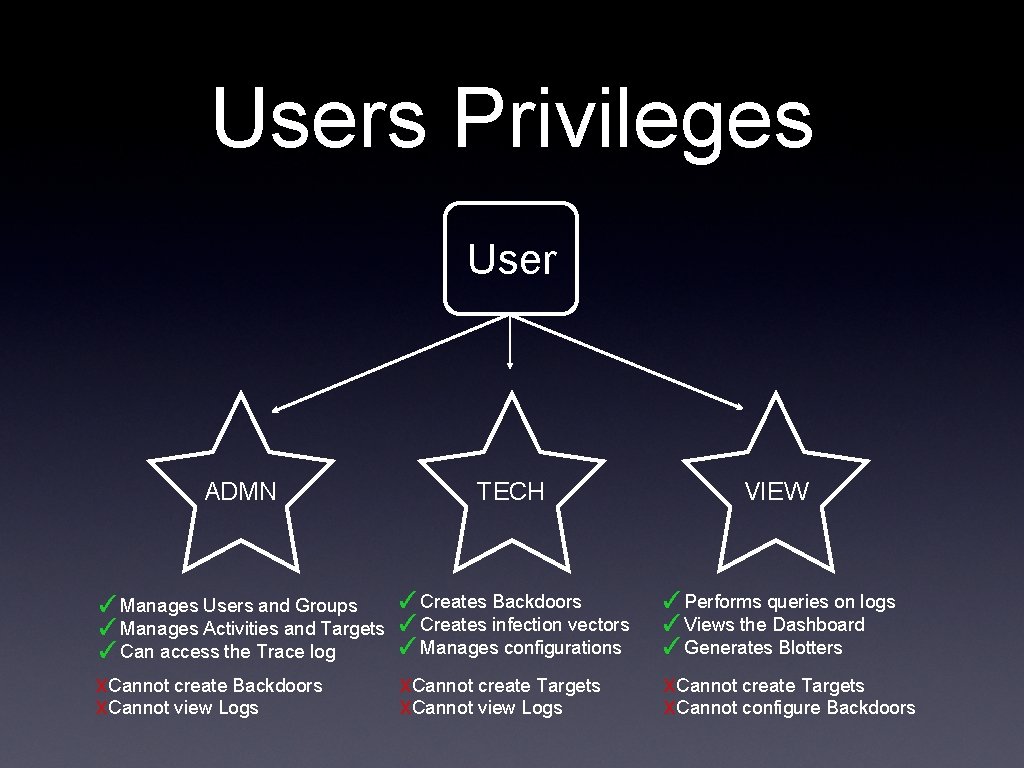
Users Privileges User ADMN TECH VIEW ✓Manages Users and Groups ✓Manages Activities and Targets ✓Can access the Trace log x. Cannot create Backdoors x. Cannot view Logs ✓Creates Backdoors ✓Creates infection vectors ✓Manages configurations ✓Performs queries on logs ✓Views the Dashboard ✓Generates Blotters x. Cannot create Targets x. Cannot view Logs x. Cannot create Targets x. Cannot configure Backdoors

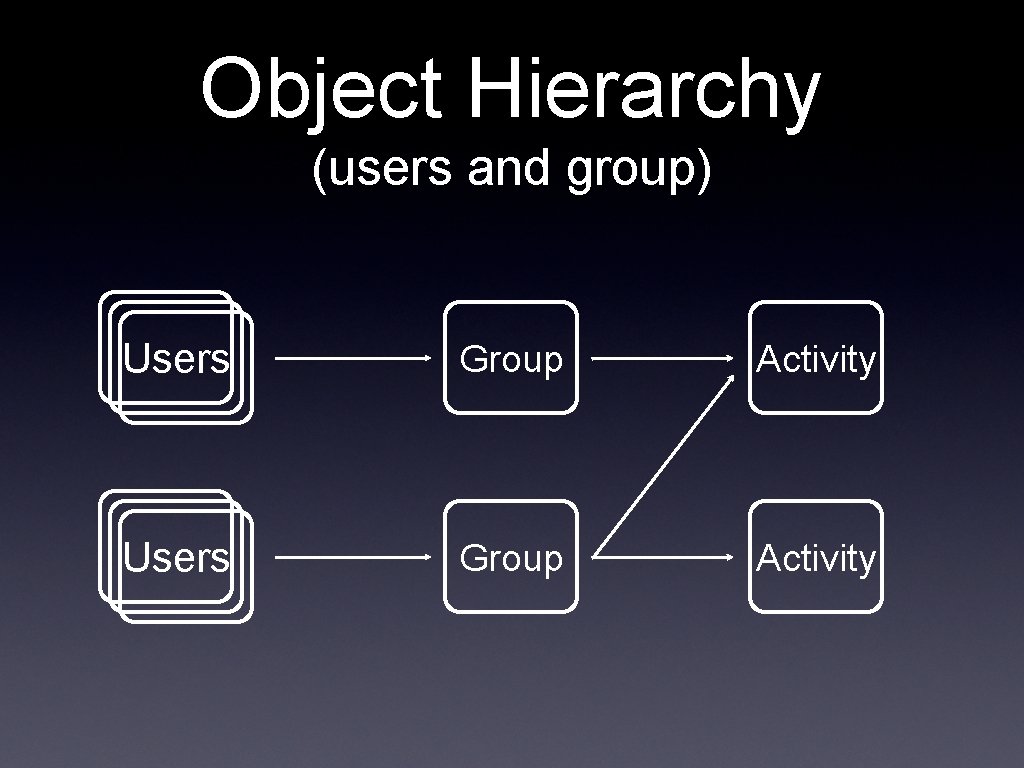
Object Hierarchy (users and group) Users Group Activity

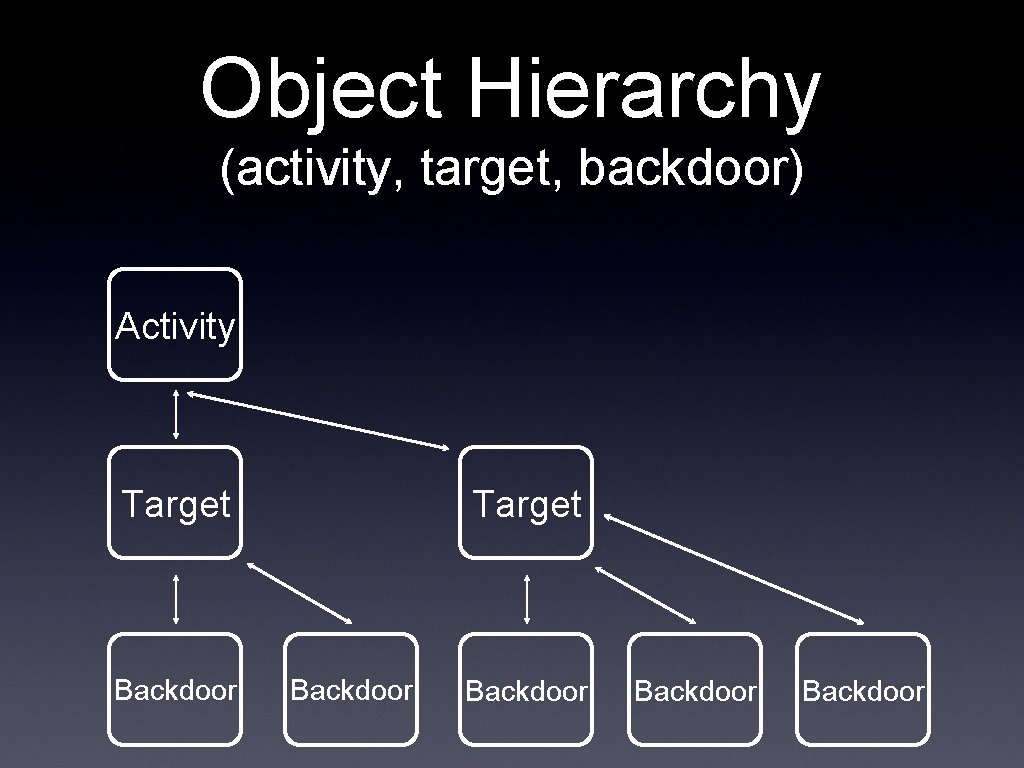
Object Hierarchy (activity, target, backdoor) Activity Target Backdoor Backdoor