Dynamic Taint Analysis for Automatic Detection Analysis and












- Slides: 25

Dynamic Taint Analysis for Automatic Detection, Analysis and Signature Generation of Exploits on Commodity Software Author : James Newsome and Dawn Song Published: Network and Distributed Systems Security Symposium (NDSS), Feb 2005 Presented By : Amit Shrivastava 2020/11/28 1

overview n In order to fight against new fast growing worms it is necessary to have an automatic detect and defense system. n In this paper Author proposed new technique ‘Dynamic Taint Analysis’ and showed how it can be used to detect and analyze software exploits 2020/11/28 Presented By : Amit Shrivastava 2

Motivation n n To combat against software vulnerabilities such as buffer overflow and format string. Generation of signature against new exploit. 2020/11/28 Presented By : Amit Shrivastava 3

Approaches Used Ø Attack detectors n Coarse grained detectors: Detect anomalous behavior such as scanning and do not provide detailed information about vulnerability and how it exploited. n Fine grained detectors: Detect attack on a program vulnerability, and provide detailed information about it. 2020/11/28 Presented By : Amit Shrivastava 4

Dynamic Taint Analysis § Tainted data: Data from un-trusted source § Keep track of tainted data (from un-trusted source) § Monitors program execution to track how tainted attribute propagates § Detect when tainted data is used in sensitive way 2020/11/28 Presented By : Amit Shrivastava 5

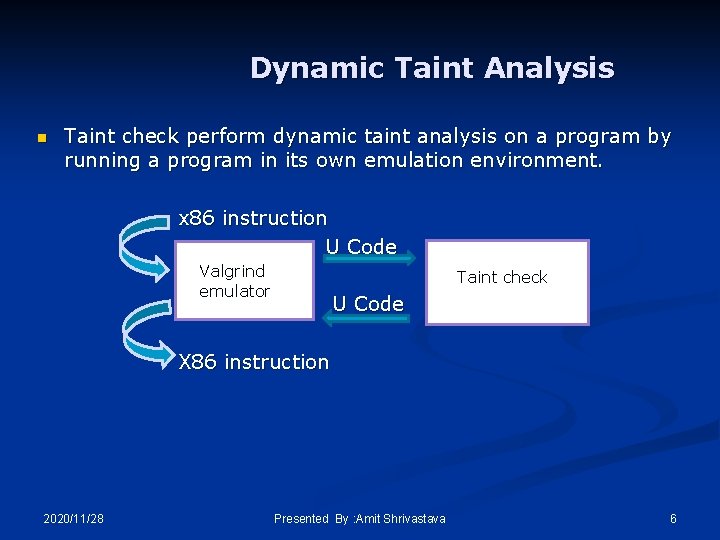
Dynamic Taint Analysis n Taint check perform dynamic running a program in its own taint analysis on a program by emulation environment. x 86 instruction U Code Valgrind emulator U Code Taint check Check X 86 instruction 2020/11/28 Presented By : Amit Shrivastava 6

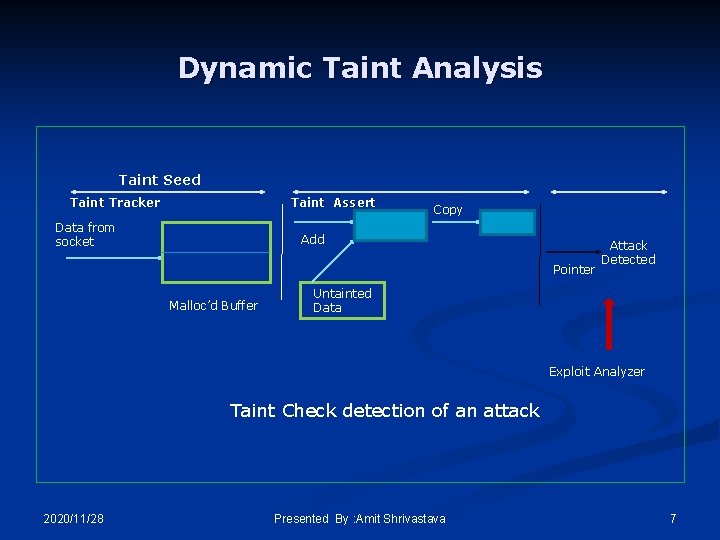
Dynamic Taint Analysis Taint Seed Taint Tracker Taint Assert Data from socket Copy Add Pointer Malloc’d Buffer Attack Detected Untainted Data Exploit Analyzer Taint Check detection of an attack 2020/11/28 Presented By : Amit Shrivastava 7

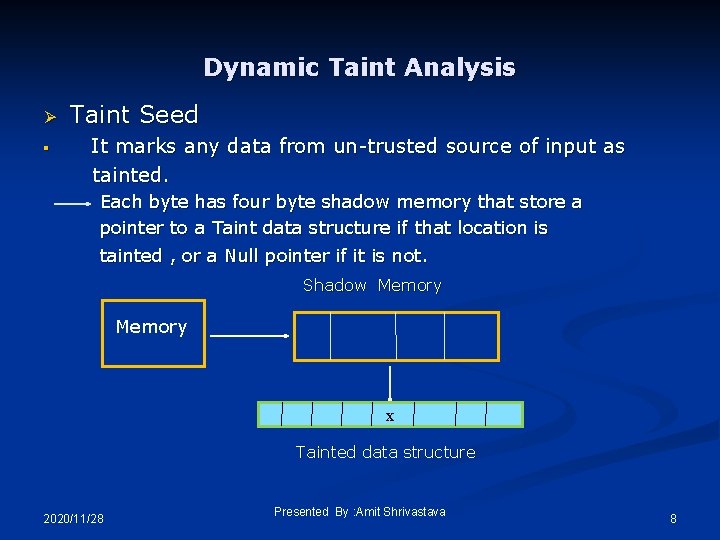
Dynamic Taint Analysis Ø § Taint Seed It marks any data from un-trusted source of input as tainted. Each byte has four byte shadow memory that store a pointer to a Taint data structure if that location is tainted , or a Null pointer if it is not. Shadow Memory x Tainted data structure 2020/11/28 Presented By : Amit Shrivastava 8

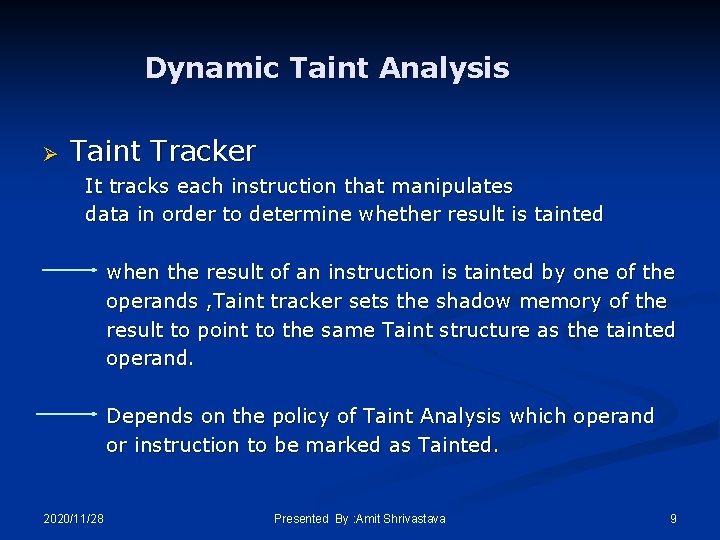
Dynamic Taint Analysis Ø Taint Tracker It tracks each instruction that manipulates data in order to determine whether result is tainted when the result of an instruction is tainted by one of the operands , Taint tracker sets the shadow memory of the result to point to the same Taint structure as the tainted operand. Depends on the policy of Taint Analysis which operand or instruction to be marked as Tainted. 2020/11/28 Presented By : Amit Shrivastava 9

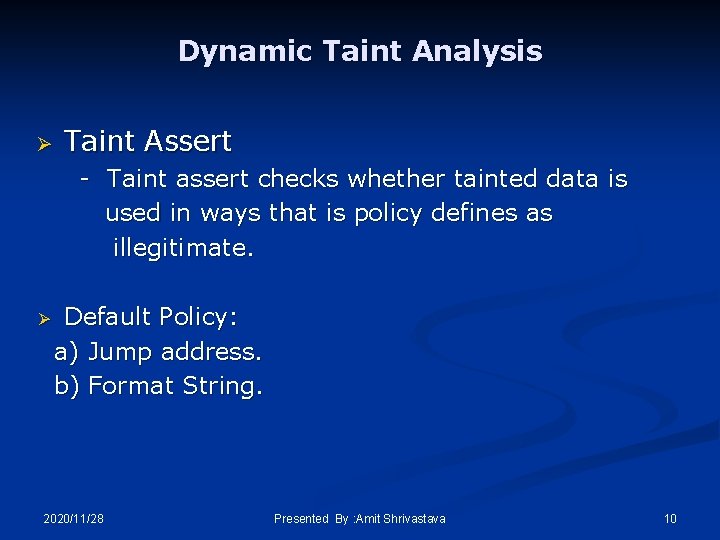
Dynamic Taint Analysis Ø Taint Assert - Taint assert checks whether tainted data is used in ways that is policy defines as illegitimate. Ø Default Policy: a) Jump address. b) Format String. 2020/11/28 Presented By : Amit Shrivastava 10

Dynamic Taint Analysis Ø Exploit Analyzer * It provide useful information about how the exploit happened and what the exploit attempt to do. Ø Usage: a) Identifying vulnerabilities. b) Generating exploit signature. 2020/11/28 Presented By : Amit Shrivastava 11

Security Analysis Ø Attack detected: a) overwrite or jump address: Jump target (such as return address and function pointer) whether altered to point to existing code. b) Format String: An attacker provide malicious format string to trick program by writing an attacker value to an attacker chosen memory address. 2020/11/28 Presented By : Amit Shrivastava 12

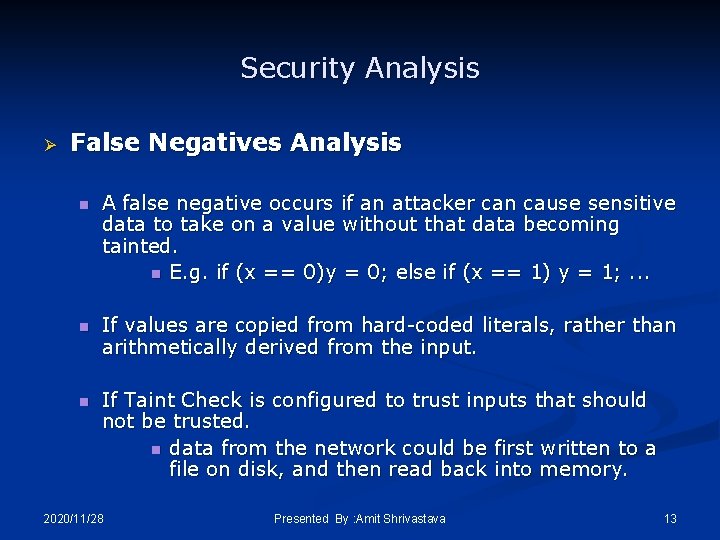
Security Analysis Ø False Negatives Analysis n A false negative occurs if an attacker can cause sensitive data to take on a value without that data becoming tainted. n E. g. if (x == 0)y = 0; else if (x == 1) y = 1; . . . n If values are copied from hard-coded literals, rather than arithmetically derived from the input. n If Taint Check is configured to trust inputs that should not be trusted. n data from the network could be first written to a file on disk, and then read back into memory. 2020/11/28 Presented By : Amit Shrivastava 13

Security Analysis Ø False Positive Analysis § Taint Check detects that tainted data is being used in an illegitimate way even when there is no attack taking place. § 2020/11/28 It indicates there is vulnerabilities in program Presented By : Amit Shrivastava 14

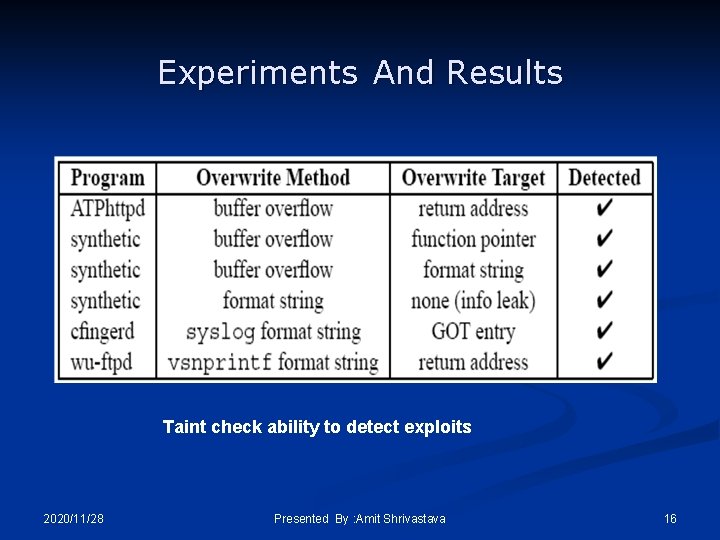
Experiments And Results n Synthetic exploit-(test programs) n n To detect n Overwritten return addresses n Overwritten function pointer n Format string vulnerability Actual exploits-(using server) n n n ATPhttpd exploit (buffer overflow) Cfingerd exploit (format string vulnerability) Wu-ftpd exploit (format string vulnerability) 2020/11/28 Presented By : Amit Shrivastava 15

Experiments And Results Taint check ability to detect exploits 2020/11/28 Presented By : Amit Shrivastava 16

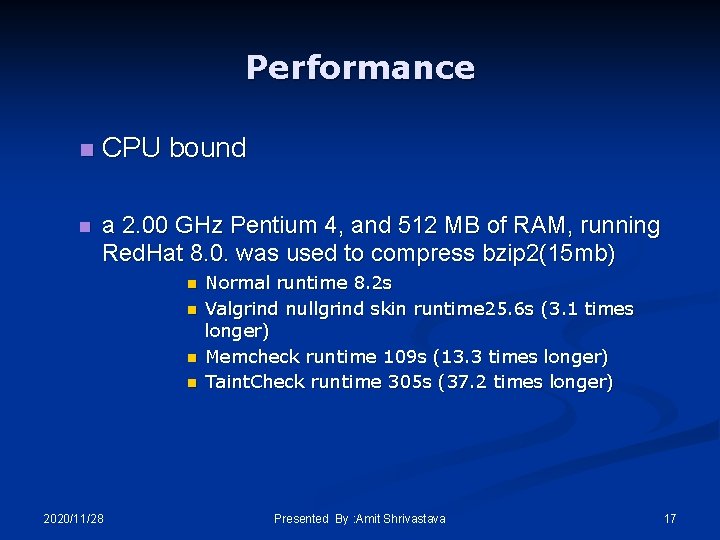
Performance n CPU bound n a 2. 00 GHz Pentium 4, and 512 MB of RAM, running Red. Hat 8. 0. was used to compress bzip 2(15 mb) n n 2020/11/28 Normal runtime 8. 2 s Valgrind nullgrind skin runtime 25. 6 s (3. 1 times longer) Memcheck runtime 109 s (13. 3 times longer) Taint. Check runtime 305 s (37. 2 times longer) Presented By : Amit Shrivastava 17

Performance Ø Short lived : cfingerd § When program start each basic block is written to cache, so penalty is acceptable. § For short lived program time taken is significantly large. n n 2020/11/28 Normal runtime for Cfingerd was 0. 0222 s Valgrind nullgrind skin runtime took 13 times longer Memcheck runtime took 32 times longer Taint. Check runtime took 13 times longer Presented By : Amit Shrivastava 18

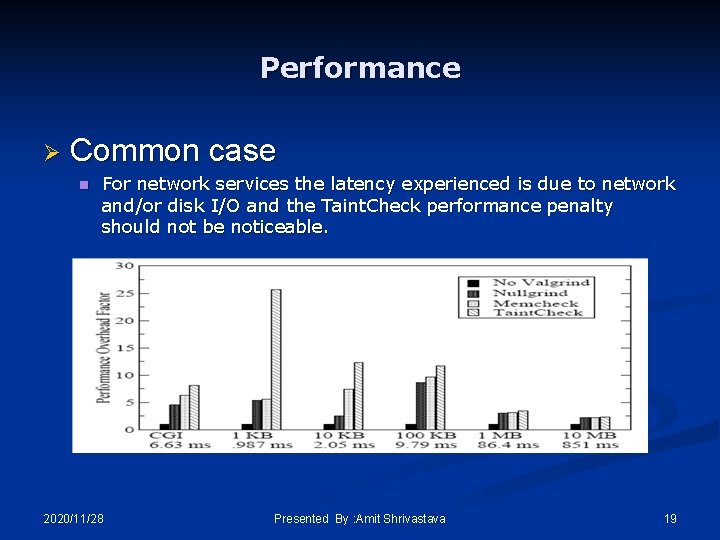
Performance Ø Common case n For network services the latency experienced is due to network and/or disk I/O and the Taint. Check performance penalty should not be noticeable. 2020/11/28 Presented By : Amit Shrivastava 19

Usage It is impractical to use Taint check individually because of its large performance overhead. n Taint check enabled honeypots n Honeypot can use taintcheck to monitor all its network and provide additional information about detected attack. q Taint check plus OS randomization It can be used to detect which request contained an attack and generate signature for attack. 2020/11/28 Presented By : Amit Shrivastava 20

Automatic signature generation n Automatic semantic analysis based signature generation 2020/11/28 Presented By : Amit Shrivastava 21

Contribution n Detection of worms without any special source code n Automatic signature generation for warms 2020/11/28 Presented By : Amit Shrivastava 22

Weakness n Automatic signature generation not explained properly. 2020/11/28 Presented By : Amit Shrivastava 23

How to Improve n More detail information about generation of automatic warm signature. 2020/11/28 Presented By : Amit Shrivastava 24

Thank You 2020/11/28 Presented By : Amit Shrivastava 25