CrackingResistant Password Vaults Using Natural Language Encoders Rahul




![Modern Password Crackers [Weir et al. 2010] [Veras et al. 2014] … Password Leaks Modern Password Crackers [Weir et al. 2010] [Veras et al. 2014] … Password Leaks](https://slidetodoc.com/presentation_image_h2/8cdc7b7041f914c667009c1e899e8830/image-26.jpg)












- Slides: 62

Cracking-Resistant Password Vaults Using Natural Language Encoders Rahul Chatterjee UW-Madison & Cornell University (Fall 2015) Joseph Bonneau Stanford University Ari Juels Cornell Tech (Jacobs Inst. ) Thomas Ristenpart UW-Madison & Cornell Tech (next week)

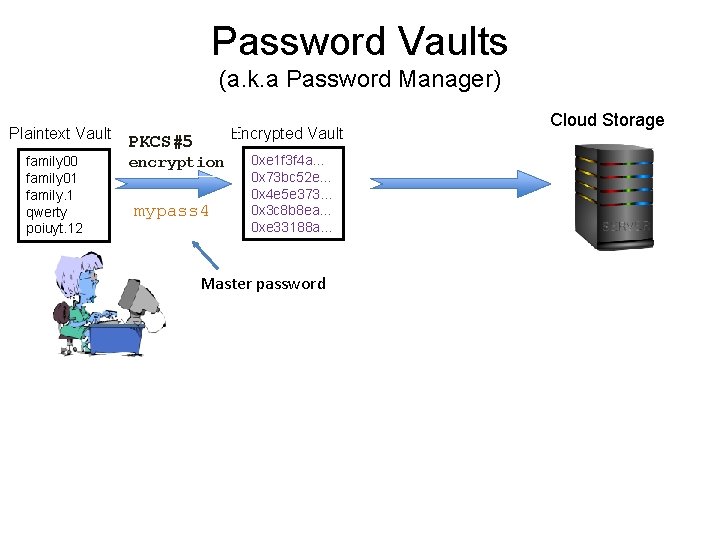
Password Vaults (a. k. a Password Manager) Plaintext Vault family 00 family 01 family. 1 qwerty poiuyt. 12 Encrypted Vault PKCS#5 encryption mypass 4 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… Master password Cloud Storage

Password Vaults Increasing in Popularity And many more….

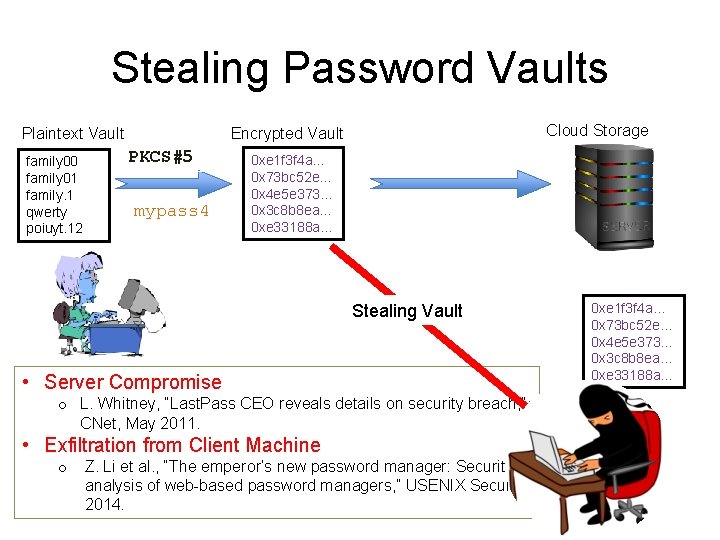
Stealing Password Vaults Plaintext Vault family 00 family 01 family. 1 qwerty poiuyt. 12 Cloud Storage Encrypted Vault PKCS#5 mypass 4 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… Stealing Vault • Server Compromise o L. Whitney, “Last. Pass CEO reveals details on security breach, ” CNet, May 2011. • Exfiltration from Client Machine o Z. Li et al. , “The emperor’s new password manager: Security analysis of web-based password managers, ” USENIX Security, 2014. 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a…

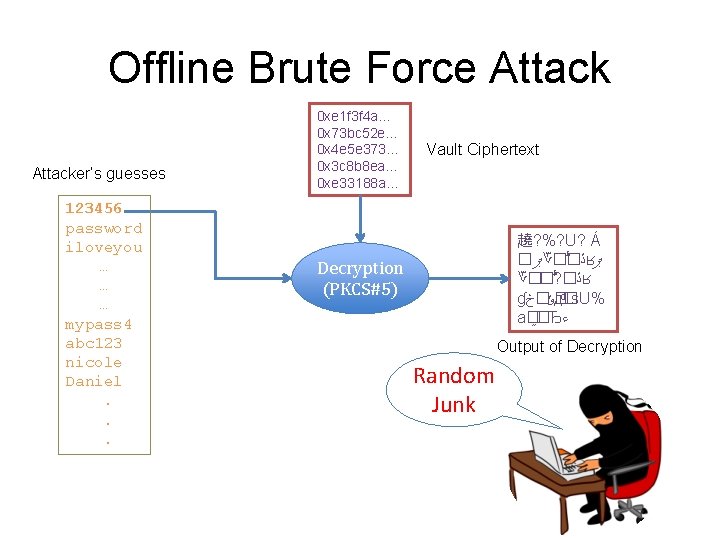
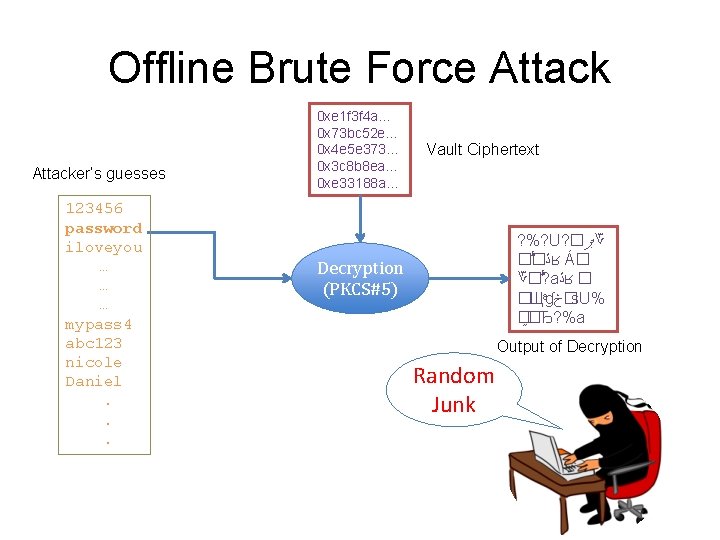
Offline Brute Force Attacker’s guesses 123456 password iloveyou … … … mypass 4 abc 123 nicole Daniel. . . 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… Vault Ciphertext 趬? %? U? Á � ޕ ؆� � ڐ ʁ ޕ ؆�� ? � ڐ ʁ ɠ �ݸ�څ д �s. U% a� �Ђ ﺀ Decryption (PKCS#5) Output of Decryption Random Junk

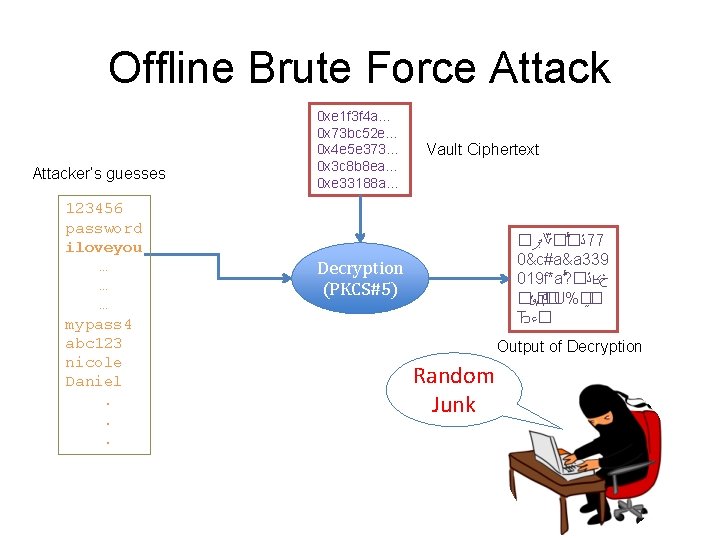
Offline Brute Force Attacker’s guesses 123456 password iloveyou … … … mypass 4 abc 123 nicole Daniel. . . 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… Vault Ciphertext ? %? U? � ޕ ؆ � � ڐ ʁ Á� ؆� ? a ڐ ʁ � �Щ ɠ �څ s. U% � �Ђ? %a Decryption (PKCS#5) Output of Decryption Random Junk

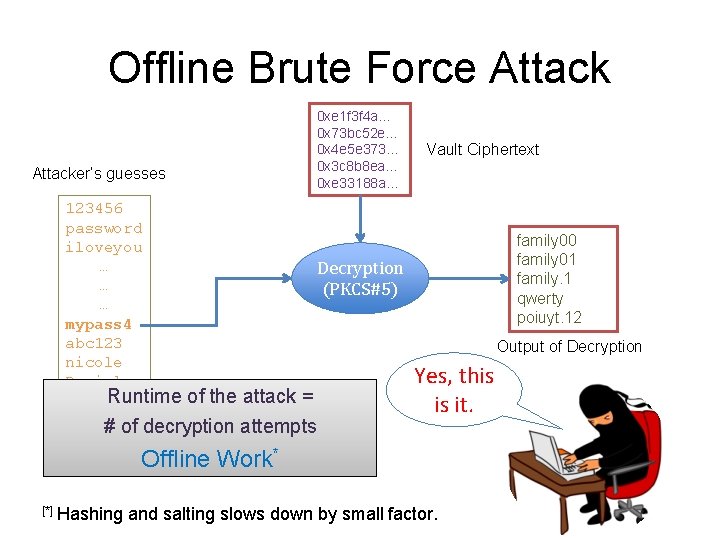
Offline Brute Force Attacker’s guesses 123456 password iloveyou … … … mypass 4 abc 123 nicole Daniel. . . 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… Vault Ciphertext � ޕ ؆� � ڐ 77 0&c#a&a 339 019 f*a ? � ڐ ʁ څ � �ݸ д �U%� � Ђ �ﺀ Decryption (PKCS#5) Output of Decryption Random Junk

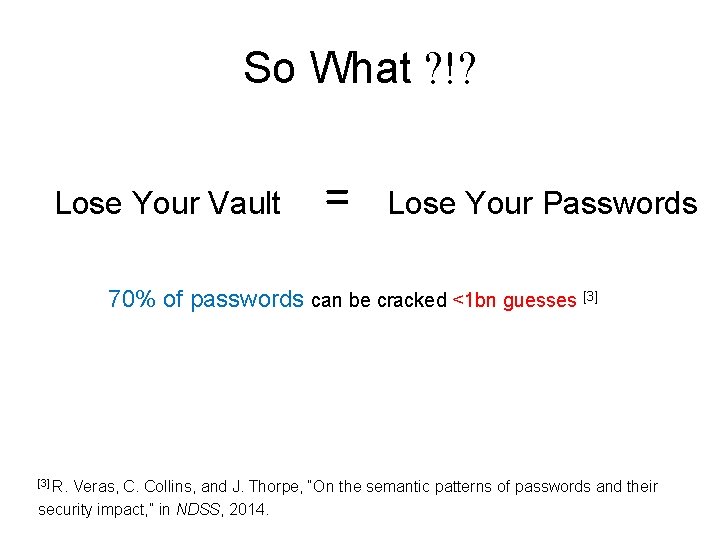
Offline Brute Force Attacker’s guesses 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… 123456 password iloveyou … Decryption … (PKCS#5) … mypass 4 abc 123 nicole Daniel. Runtime of the attack =. # of decryption attempts. Offline Work* [*] Hashing Vault Ciphertext family 00 family 01 family. 1 qwerty poiuyt. 12 Output of Decryption Yes, this is it. and salting slows down by small factor.

So What ? !? Lose Your Vault = Lose Your Passwords 70% of passwords can be cracked <1 bn guesses [3] R. Veras, C. Collins, and J. Thorpe, “On the semantic patterns of passwords and their security impact, ” in NDSS, 2014.

Our Contribution • Goal: – Prevent offline attack on password vaults • How ? – Decoy Techniques • Show existing decoy techniques have a subtle vulnerability – Kamouflage by Bojinov et al. can degrade security compared to standard password-based encryption • Build a new mechanism: Natural Language Encoder (NLE) – Honey Encryption – No. Crack: new password vault system with decoys

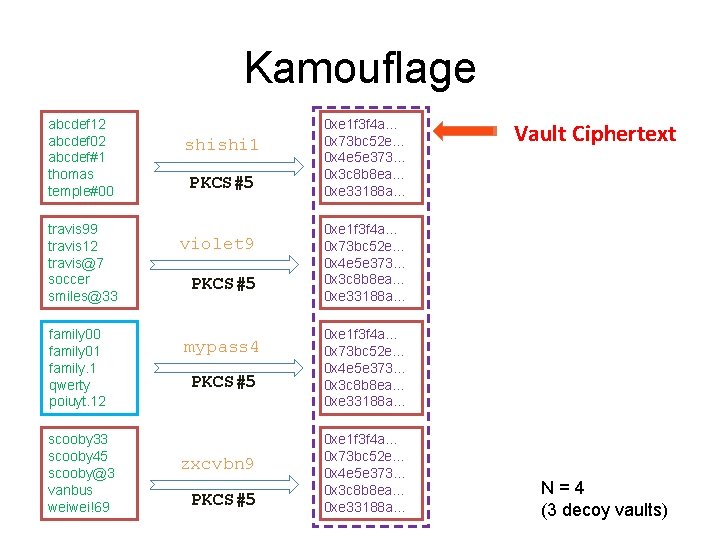
Kamouflage abcdef 12 abcdef 02 abcdef#1 thomas temple#00 travis 99 travis 12 travis@7 soccer smiles@33 family 00 family 01 family. 1 qwerty poiuyt. 12 scooby 33 scooby 45 scooby@3 vanbus weiwei!69 shishi 1 PKCS#5 violet 9 PKCS#5 mypass 4 PKCS#5 zxcvbn 9 PKCS#5 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… Vault Ciphertext 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… N=4 (3 decoy vaults)

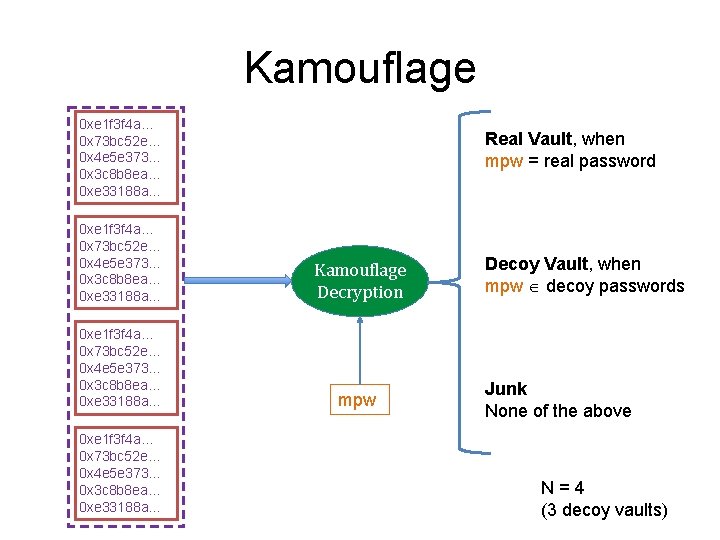
Kamouflage 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… Real Vault, when mpw = real password 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… Kamouflage Decryption 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… mpw 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… Decoy Vault, when mpw decoy passwords Junk None of the above N=4 (3 decoy vaults)

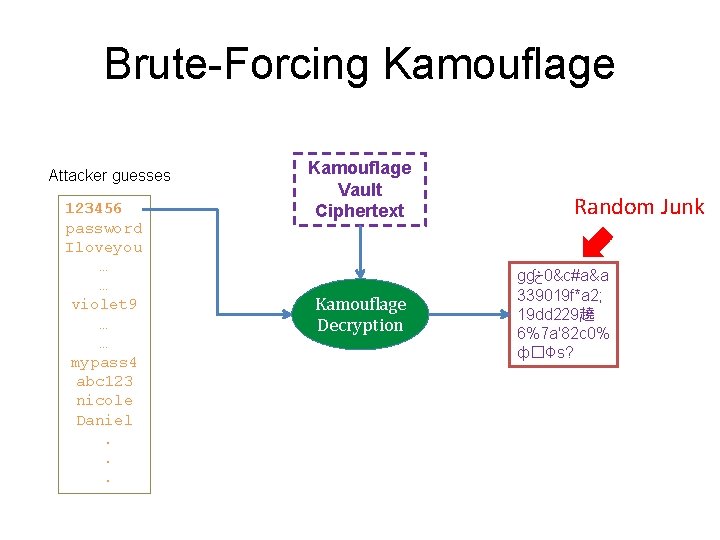
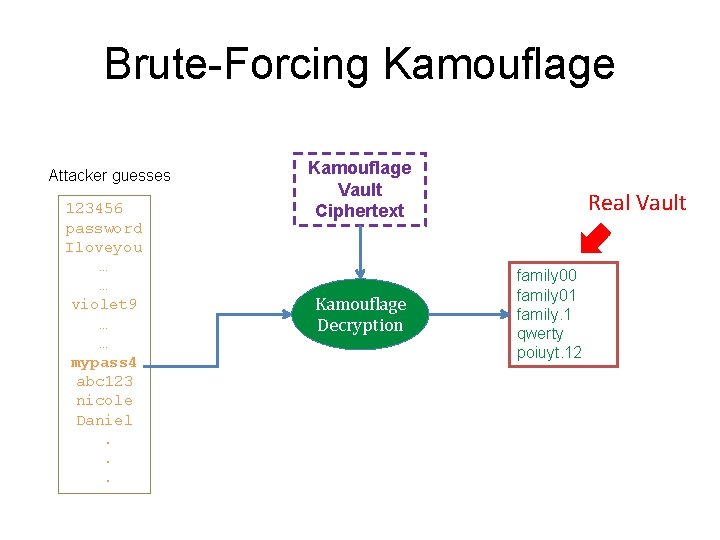
Brute-Forcing Kamouflage Attacker guesses 123456 password Iloveyou … … violet 9 … … mypass 4 abc 123 nicole Daniel. . . Kamouflage Vault Ciphertext Kamouflage Decryption Random Junk ɡɠ څ 0&c#a&a 339019 f*a 2; 19 dd 229趬 6%7 a'82 c 0% ф� �Фs?

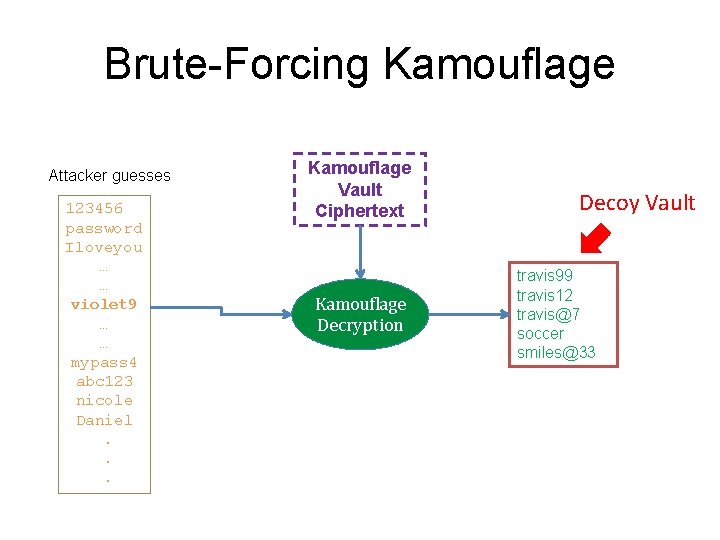
Brute-Forcing Kamouflage Attacker guesses 123456 password Iloveyou … … violet 9 … … mypass 4 abc 123 nicole Daniel. . . Kamouflage Vault Ciphertext Kamouflage Decryption Decoy Vault travis 99 travis 12 travis@7 soccer smiles@33

Brute-Forcing Kamouflage Attacker guesses 123456 password Iloveyou … … violet 9 … … mypass 4 abc 123 nicole Daniel. . . Kamouflage Vault Ciphertext Kamouflage Decryption Real Vault family 00 family 01 family. 1 qwerty poiuyt. 12

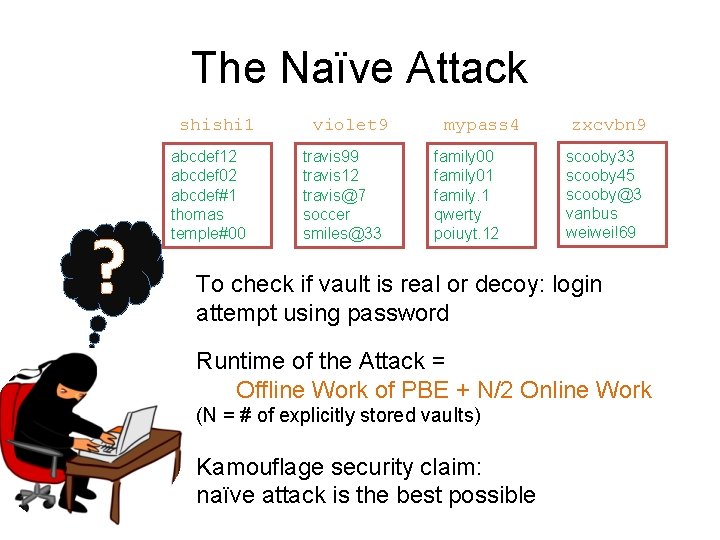
The Naïve Attack shishi 1 ? abcdef 12 abcdef 02 abcdef#1 thomas temple#00 violet 9 travis 99 travis 12 travis@7 soccer smiles@33 mypass 4 family 00 family 01 family. 1 qwerty poiuyt. 12 zxcvbn 9 scooby 33 scooby 45 scooby@3 vanbus weiwei!69 To check if vault is real or decoy: login attempt using password Runtime of the Attack = Offline Work of PBE + N/2 Online Work (N = # of explicitly stored vaults) Kamouflage security claim: naïve attack is the best possible

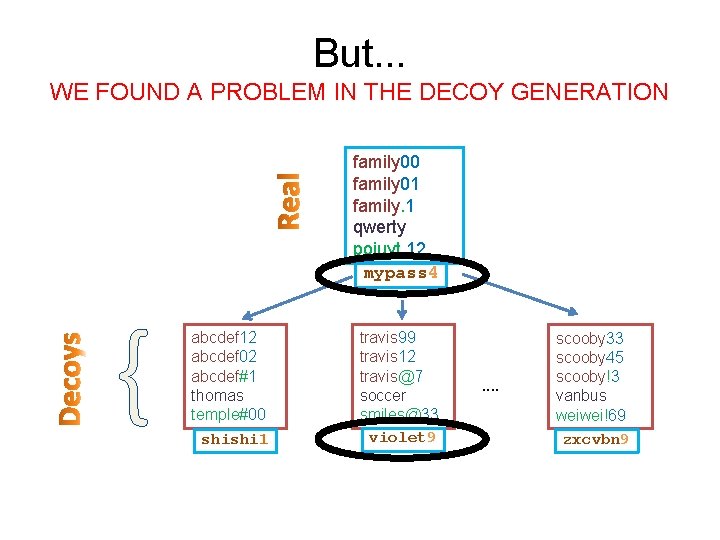
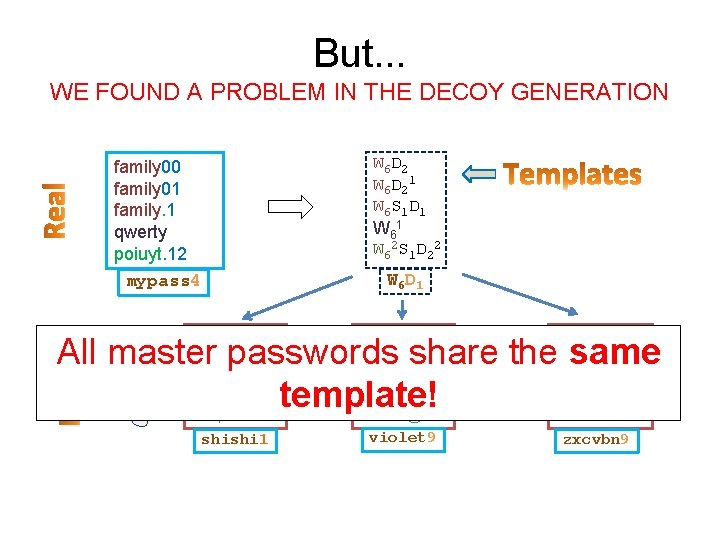
But. . . WE FOUND A PROBLEM IN THE DECOY GENERATION family 00 family 01 family. 1 qwerty poiuyt. 12 mypass 4 { abcdef 12 abcdef 02 abcdef#1 thomas temple#00 shishi 1 travis 99 travis 12 travis@7 soccer smiles@33 violet 9 . . scooby 33 scooby 45 scooby!3 vanbus weiwei!69 zxcvbn 9

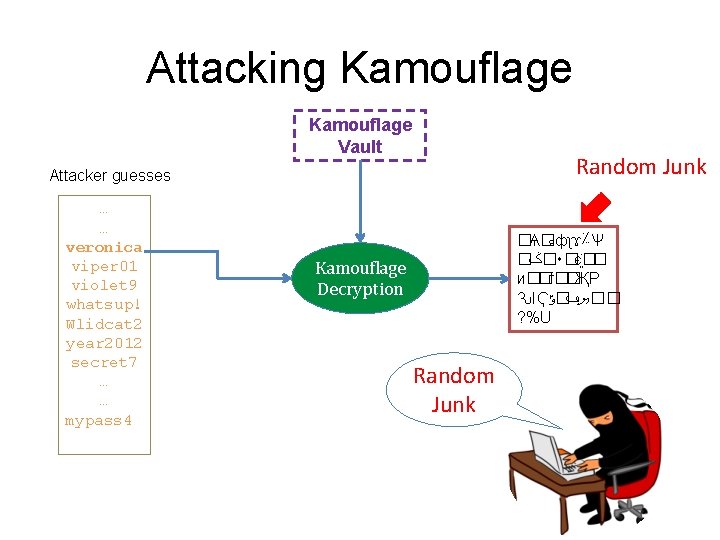
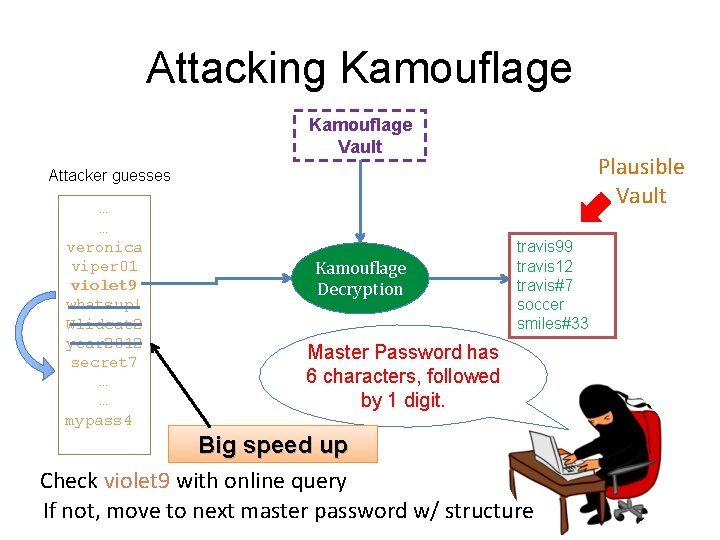
Attacking Kamouflage Vault Random Junk Attacker guesses … … veronica viper 01 violet 9 whatsup! Wlidcat 2 year 2012 secret 7 … … mypass 4 �Ѧ� � ﺀ фʅɤ؉Ѱ � �ݢ ٠�є �� и��ѓ��ҖР ԄΙҀ ��ޔݠ�ݹ ? %U Kamouflage Decryption Random Junk

Attacking Kamouflage Vault Plausible Vault Attacker guesses … … veronica viper 01 violet 9 whatsup! Wlidcat 2 year 2012 secret 7 … … mypass 4 Kamouflage Decryption travis 99 travis 12 travis#7 soccer smiles#33 Master Password has 6 characters, followed by 1 digit. Big speed up Check violet 9 with online query If not, move to next master password w/ structure

Attack Results Kamouflage claimed (for N=103): 100% offline work of standard Password Based Encryption + N/2 = 500 expected online queries Simulations with Yahoo password leak: 50% offline work of standard Password Based Encryption + 11 expected online queries

The situation so far… • Standard encryption vulnerable to brute force attacks • Kamouflage can be less secure than standard encryption

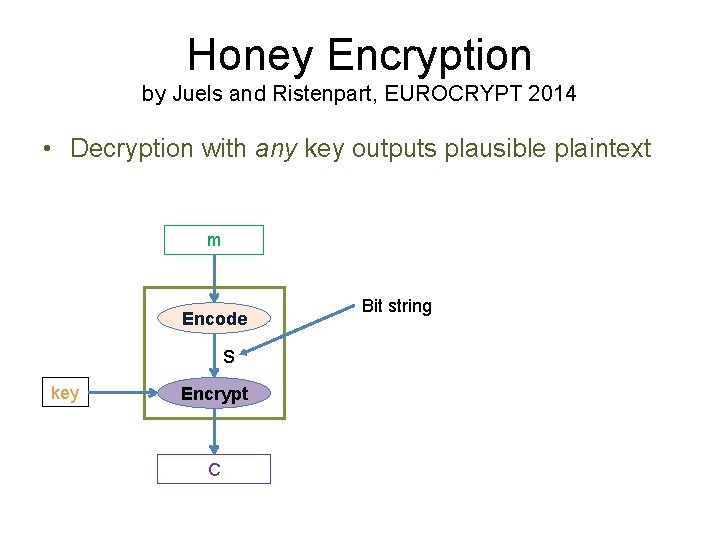
Honey Encryption by Juels and Ristenpart, EUROCRYPT 2014 • Decryption with any key outputs plausible plaintext m Encode s key Encrypt C Bit string

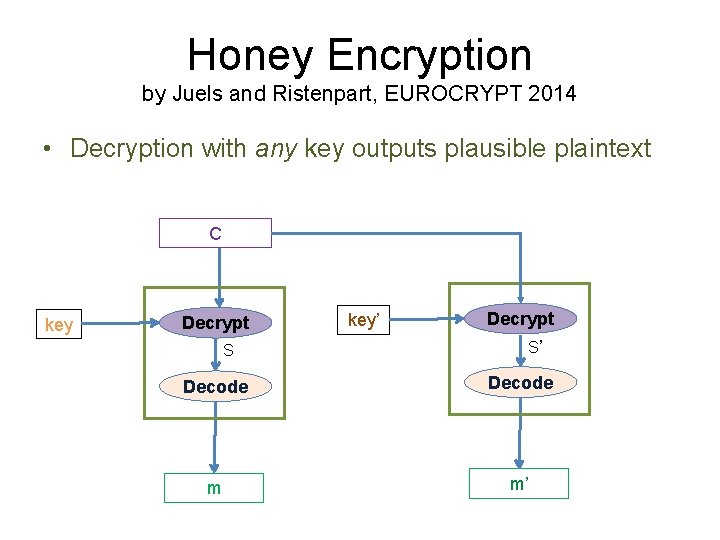
Honey Encryption by Juels and Ristenpart, EUROCRYPT 2014 • Decryption with any key outputs plausible plaintext C key Decrypt S key’ Decrypt S’ Decode m m’

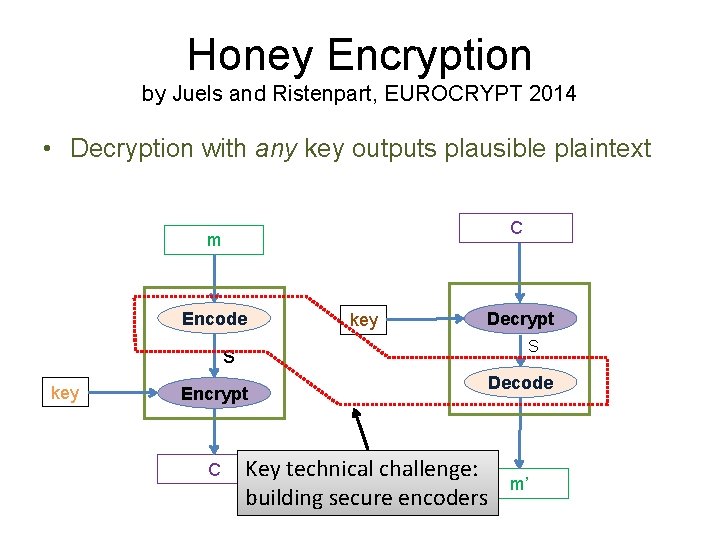
Honey Encryption by Juels and Ristenpart, EUROCRYPT 2014 • Decryption with any key outputs plausible plaintext C m Encode key Decrypt S s key Encrypt C Key technical challenge: building secure encoders Decode m’

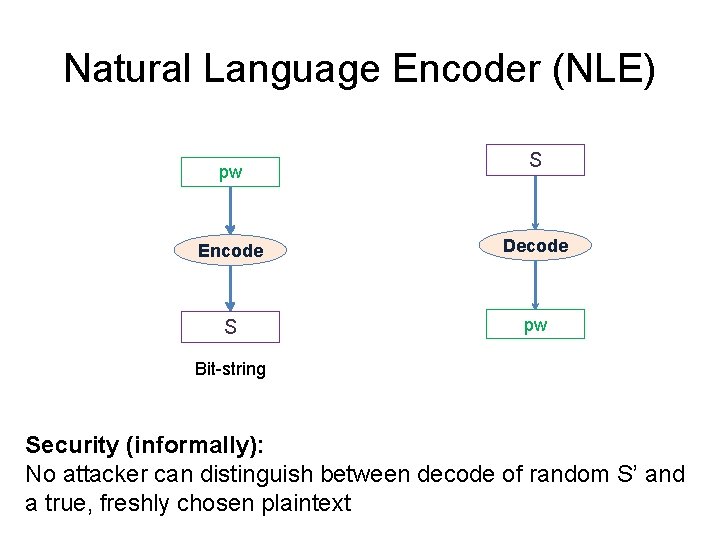
Natural Language Encoder (NLE) pw S Encode Decode S pw Bit-string Security (informally): No attacker can distinguish between decode of random S’ and a true, freshly chosen plaintext
![Modern Password Crackers Weir et al 2010 Veras et al 2014 Password Leaks Modern Password Crackers [Weir et al. 2010] [Veras et al. 2014] … Password Leaks](https://slidetodoc.com/presentation_image_h2/8cdc7b7041f914c667009c1e899e8830/image-26.jpg)
Modern Password Crackers [Weir et al. 2010] [Veras et al. 2014] … Password Leaks Training Model of password distribution Cracker 123456 password iloveyou … … Use model to sample passwords in the order of their likelihood Better Password Model Better Crackers

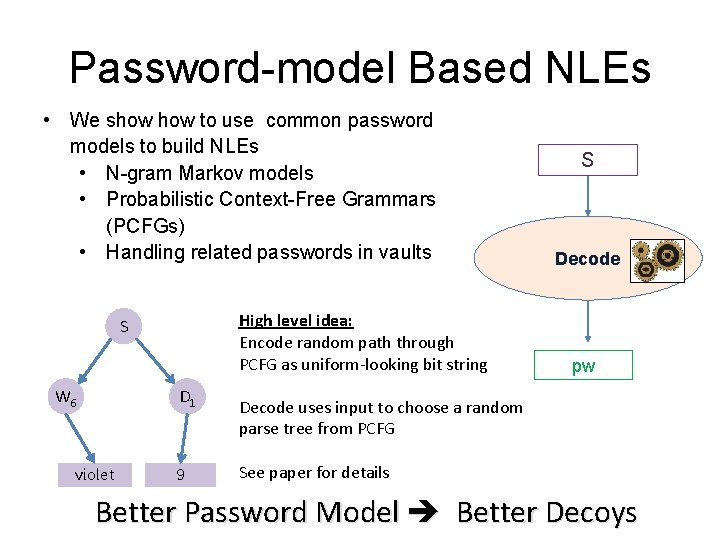
Password-model Based NLEs • We show to use common password models to build NLEs • N-gram Markov models • Probabilistic Context-Free Grammars (PCFGs) • Handling related passwords in vaults High level idea: Encode random path through PCFG as uniform-looking bit string S W 6 D 1 violet 9 S Decode pw Decode uses input to choose a random parse tree from PCFG See paper for details Better Password Model Better Decoys

No. Crack (a new kind of password vault) 1. NLE + HE = decrypt w/ wrong master password gives realistic password vault 2. Supports machine generated random passwords 3. Domain privacy, easy online sync etc. k ac Cr No

Security of No. Crack • Security goal: output of Decrypt should look “real” • Machine learning classifiers • Yahoo leak dataset, 50% attack success: No. Crack Kamouflage Offline work 20, 000 10, 000 Online work 6, 666 11 Attacker will have to make many online queries

Limitations/Future Work • Side information about the victim might decrease online work significantly • Master password related to the passwords inside the vault • Website password restrictions • Improved attacks Note: security never worse than standard password-based encryption

Summary • We showed an effective attack against only prior work on decoy techniques. #Kamouflage. Vulnerable • We devised a new mechanism to create decoys. #Natural. Language. Encoder k ac Cr No • Prototype of a Password Vault that utilizes NLE and HE, and offers most of the functionalities of modern password vaults. #No. Crack Code and data available at: https: //pages. cs. wisc. edu/~rchat/projects/No. Crack. html

Bibliography H. Bojinov, E. Bursztein, X. Boyen, and D. Boneh, “Kamouflage: Loss-resistant password management, ” in ESORICS, 2010 [1] Joseph Bonneau. The science of guessing: analyzing an anonymized corpus of 70 million passwords. In SP, 2012 [2] R. Veras, C. Collins, and J. Thorpe, “On the semantic patterns of passwords and their security impact, ” in NDSS, 2014. [3] M. Weir, S. Aggarwal, B. de Medeiros, and B. Glodek, “Password cracking using probabilistic context-free grammars, ” SP 09, 2009 [4] A. Juels and T. Ristenpart, “Honey Encryption: Beyond the bruteforce barrier, ” in EUROCRYPT, 2014 [5]


Issues with Kamouflage • All master passwords share same template – Learning the template of the master password is N times more likely – After learning the template only try the passwords that matches the template • Replacements are selected with uniform probability – real master password is way more probable than decoys, needs very few online queries only. – Kamouflage+ also fails.

But. . . WE FOUND A PROBLEM IN THE DECOY GENERATION family 00 family 01 family. 1 qwerty poiuyt. 12 mypass 4 { abcdef 12 abcdef 02 abcdef#1 thomas temple#00 shishi 1 W 6 D 21 W 6 S 1 D 1 W 62 S 1 D 22 W 6 D 1 travis 99 travis 12 travis@7 soccer smiles@33 violet 9 scooby 33 scooby 45 scooby!3 vanbus weiwei!69 zxcvbn 9 All master passwords share the same. . template!

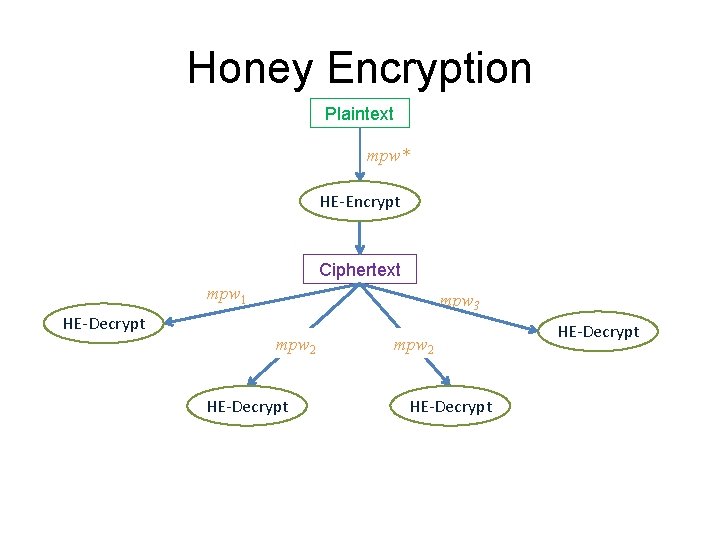
Honey Encryption Plaintext mpw* HE-Encrypt Ciphertext mpw 1 HE-Decrypt mpw 3 mpw 2 HE-Decrypt

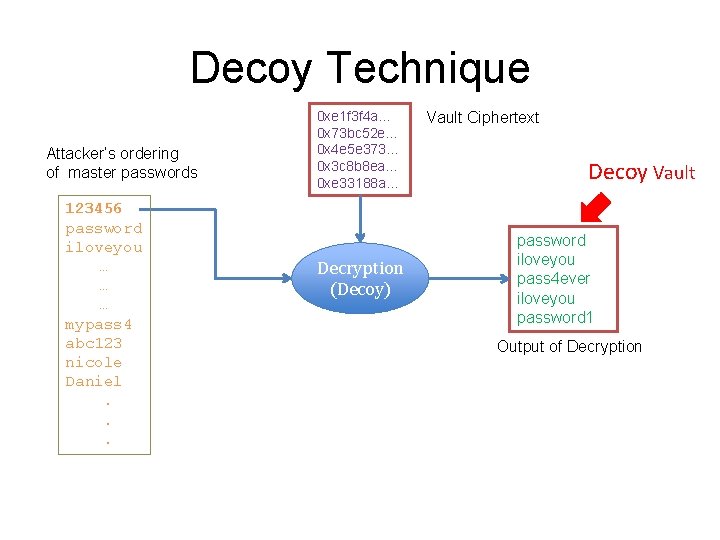
Decoy Technique Attacker’s ordering of master passwords 123456 password iloveyou … … … mypass 4 abc 123 nicole Daniel. . . 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… Decryption (Decoy) Vault Ciphertext Decoy Vault password iloveyou pass 4 ever iloveyou password 1 Output of Decryption

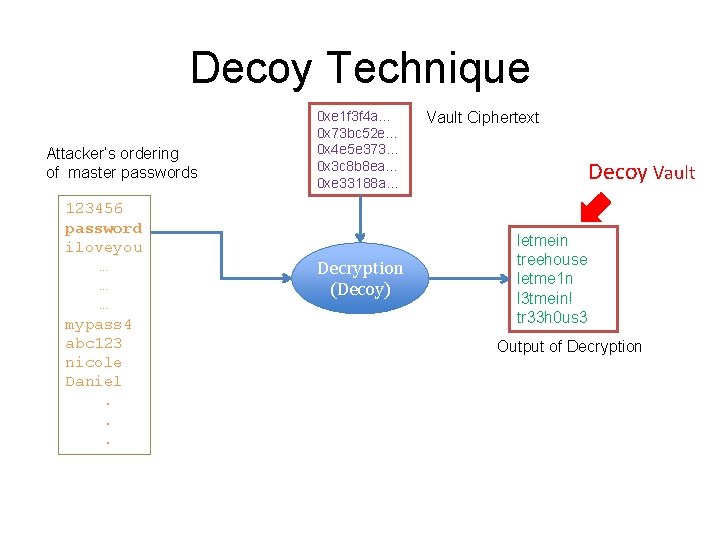
Decoy Technique Attacker’s ordering of master passwords 123456 password iloveyou … … … mypass 4 abc 123 nicole Daniel. . . 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… Decryption (Decoy) Vault Ciphertext Decoy Vault letmein treehouse letme 1 n l 3 tmein! tr 33 h 0 us 3 Output of Decryption

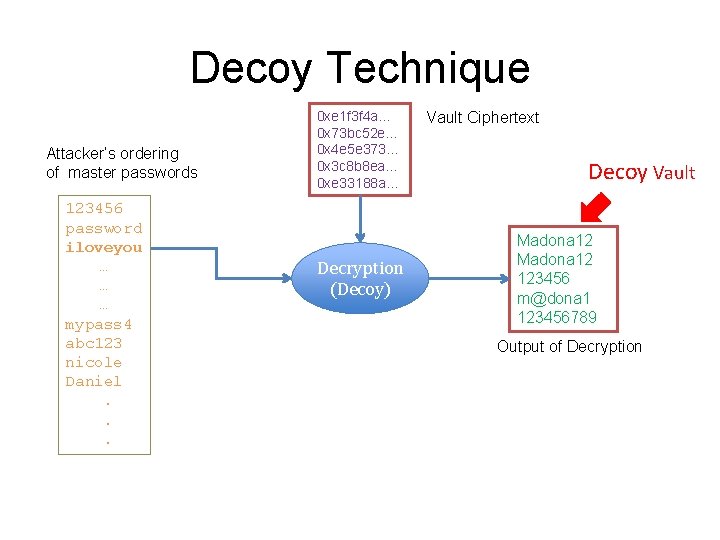
Decoy Technique Attacker’s ordering of master passwords 123456 password iloveyou … … … mypass 4 abc 123 nicole Daniel. . . 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… Decryption (Decoy) Vault Ciphertext Decoy Vault Madona 12 123456 m@dona 1 123456789 Output of Decryption

Decoy Technique Attacker’s ordering of master passwords 123456 password Iloveyou … … … mypass 4 abc 123 nicole Daniel. . . 0 xe 1 f 3 f 4 a… 0 x 73 bc 52 e… 0 x 4 e 5 e 373… 0 x 3 c 8 b 8 ea… 0 xe 33188 a… Decryption (Decoy) Vault Ciphertext Real Vault family 00 family 01 family. 1 qwerty poiuyt. 12 Output of Decryption

New Decoys Technique • Honey Encryption by Juels and Ristenpart, EUROCRYPT 2014. – – Decryption Never Fails! Wrong pass Decoy Text (fresh sample) Cool Idea , But needs an encoder to covert between uniform bit-string and plain text distribution – Showed for toy distribution. – For real distributions, it was left as an open problem. We show to build the encoder for Natural Languages, e. g. , Password Vaults

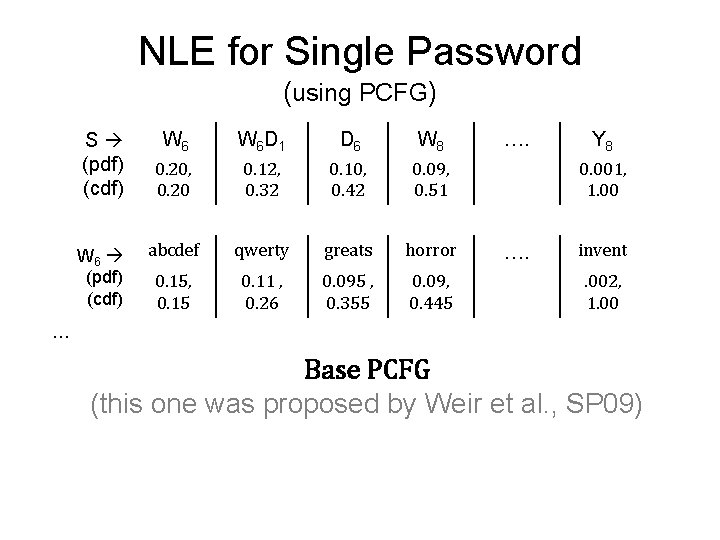
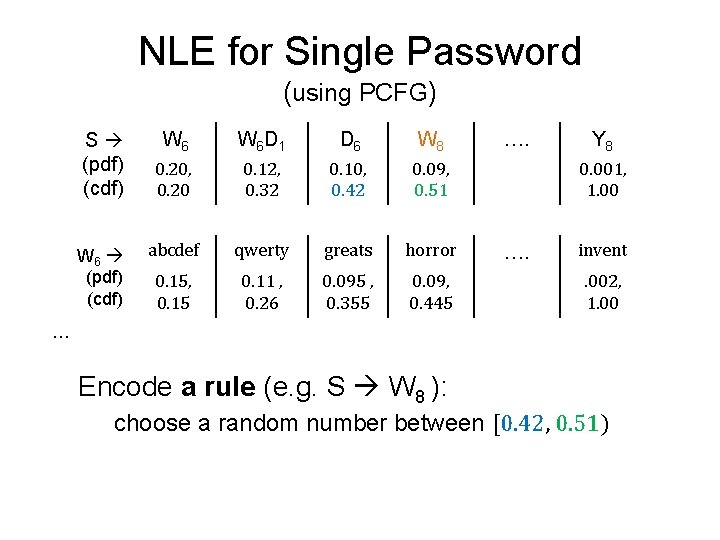
NLE for Single Password (using PCFG) S (pdf) (cdf) W 6 W 6 D 1 D 6 W 8 0. 20, 0. 20 0. 12, 0. 32 0. 10, 0. 42 0. 09, 0. 51 abcdef qwerty greats horror 0. 15, 0. 15 0. 11 , 0. 26 0. 095 , 0. 355 0. 09, 0. 445 …. Y 8 0. 001, 1. 00 …. invent. 002, 1. 00 … Base PCFG (this one was proposed by Weir et al. , SP 09)

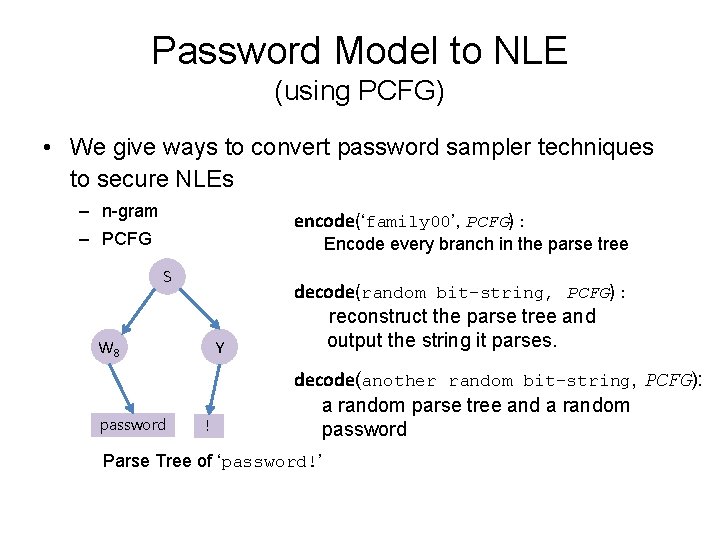
Password Model to NLE (using PCFG) • We give ways to convert password sampler techniques to secure NLEs – n-gram encode(‘family 00’, PCFG) : – PCFG Encode every branch in the parse tree S W 8 password Y ! decode(random bit-string, PCFG) : reconstruct the parse tree and output the string it parses. decode(another random bit-string, PCFG): a random parse tree and a random password Parse Tree of ‘password!’

NLE for Single Password (using PCFG) S (pdf) (cdf) W 6 W 6 D 1 D 6 W 8 0. 20, 0. 20 0. 12, 0. 32 0. 10, 0. 42 0. 09, 0. 51 abcdef qwerty greats horror 0. 15, 0. 15 0. 11 , 0. 26 0. 095 , 0. 355 0. 09, 0. 445 …. Y 8 0. 001, 1. 00 …. invent. 002, 1. 00 … Encode a rule (e. g. S W 8 ): choose a random number between [0. 42, 0. 51)

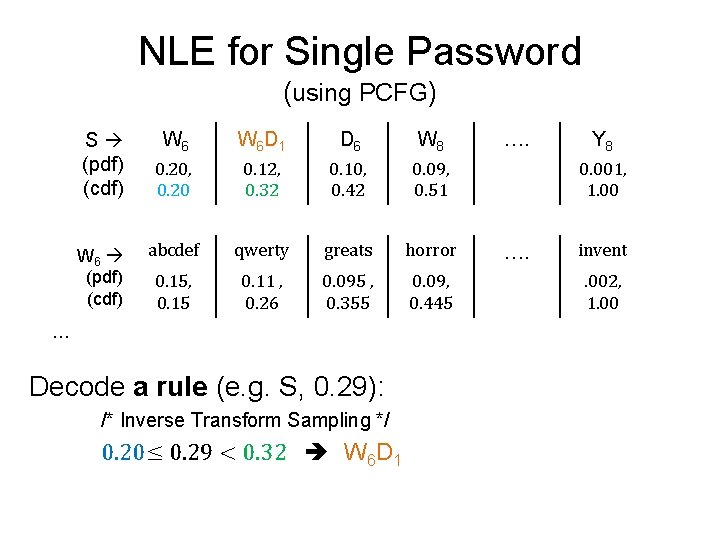
NLE for Single Password (using PCFG) S (pdf) (cdf) W 6 W 6 D 1 D 6 W 8 0. 20, 0. 20 0. 12, 0. 32 0. 10, 0. 42 0. 09, 0. 51 abcdef qwerty greats horror 0. 15, 0. 15 0. 11 , 0. 26 0. 095 , 0. 355 0. 09, 0. 445 … Decode a rule (e. g. S, 0. 29): /* Inverse Transform Sampling */ 0. 20≤ 0. 29 < 0. 32 W 6 D 1 …. Y 8 0. 001, 1. 00 …. invent. 002, 1. 00

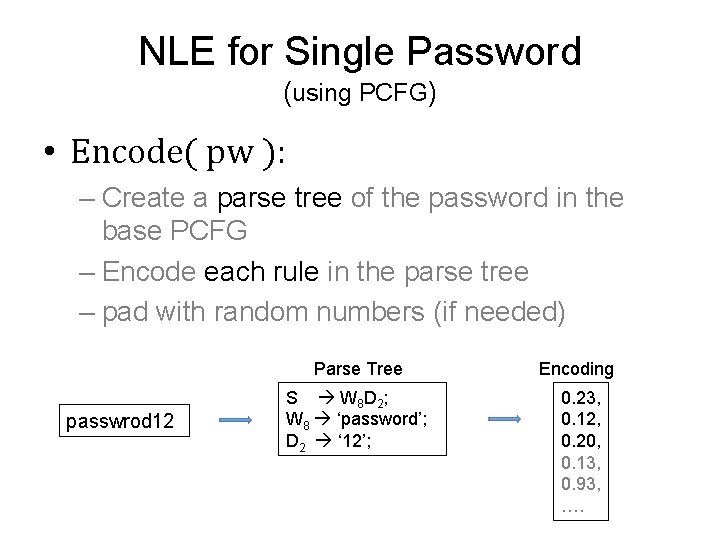
NLE for Single Password (using PCFG) • Encode( pw ): – Create a parse tree of the password in the base PCFG – Encode each rule in the parse tree – pad with random numbers (if needed) passwrod 12 Parse Tree Encoding S W 8 D 2 ; W 8 ‘password’; D 2 ‘ 12’; 0. 23, 0. 12, 0. 20, 0. 13, 0. 93, ….

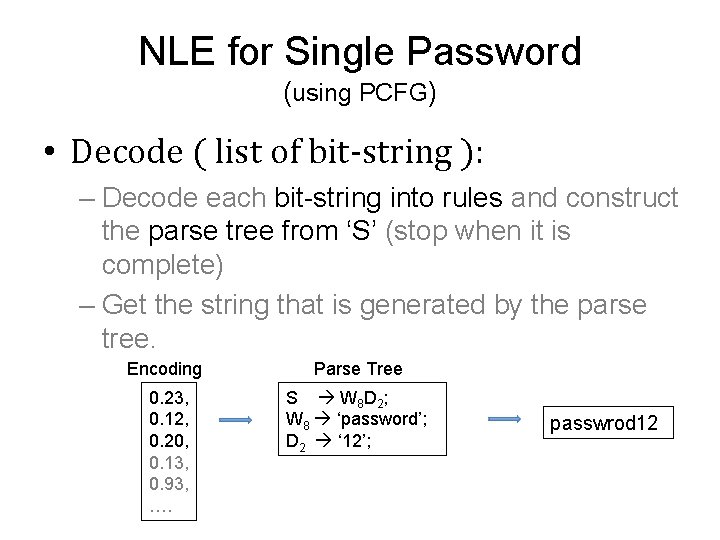
NLE for Single Password (using PCFG) • Decode ( list of bit-string ): – Decode each bit-string into rules and construct the parse tree from ‘S’ (stop when it is complete) – Get the string that is generated by the parse tree. Encoding Parse Tree 0. 23, 0. 12, 0. 20, 0. 13, 0. 93, …. S W 8 D 2 ; W 8 ‘password’; D 2 ‘ 12’; passwrod 12

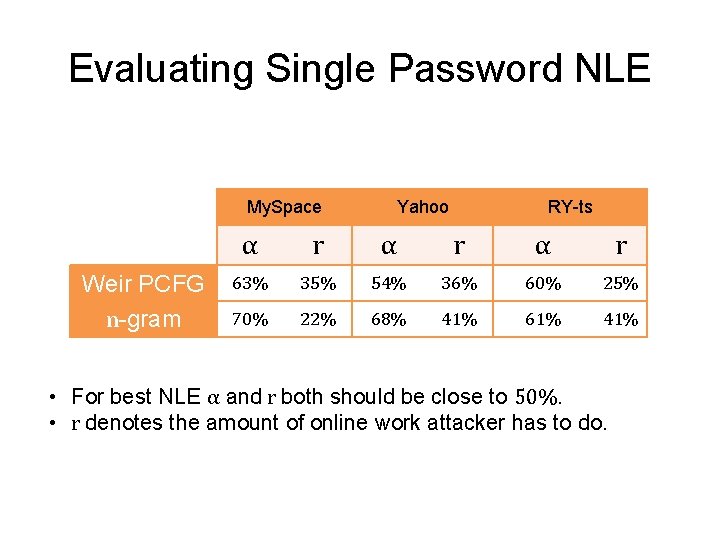
Evaluating Single Password NLE • • • Classifiers for decoy and real passwords Trained the Base PCFG with RY-tr leak (#Decoy) Tested with RY-ts, My. Space , Yahoo leaks (#Real) 1 -in-q experiment Metric of Evaluation: 1. Accuracy of classification (α) 2. Rank-of-real based on classifier’s confidence (r) • Report average over all the passwords in each of the test leaks

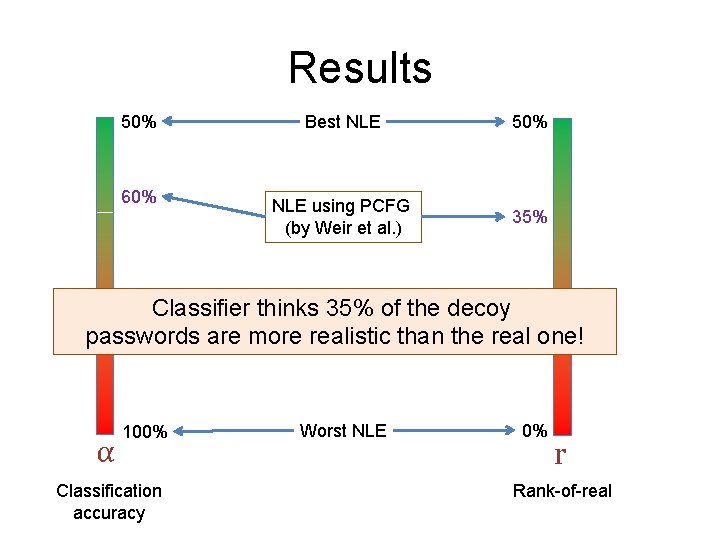
Results 50% 60% Best NLE 50% NLE using PCFG (by Weir et al. ) 35% Classifier thinks 35% of the decoy passwords are more realistic than the real one! α 100% Classification accuracy Worst NLE 0% r Rank-of-real

Evaluating Single Password NLE My. Space Weir PCFG n-gram Yahoo RY-ts α r α r 63% 35% 54% 36% 60% 25% 70% 22% 68% 41% 61% 41% • For best NLE α and r both should be close to 50%. • r denotes the amount of online work attacker has to do.

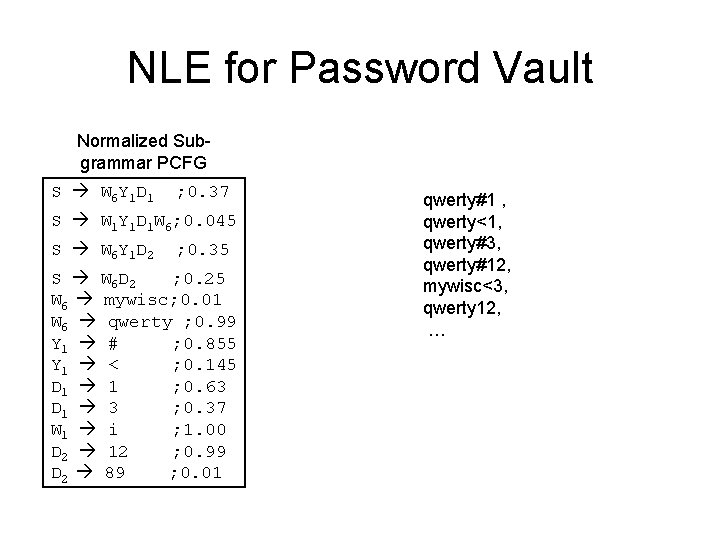
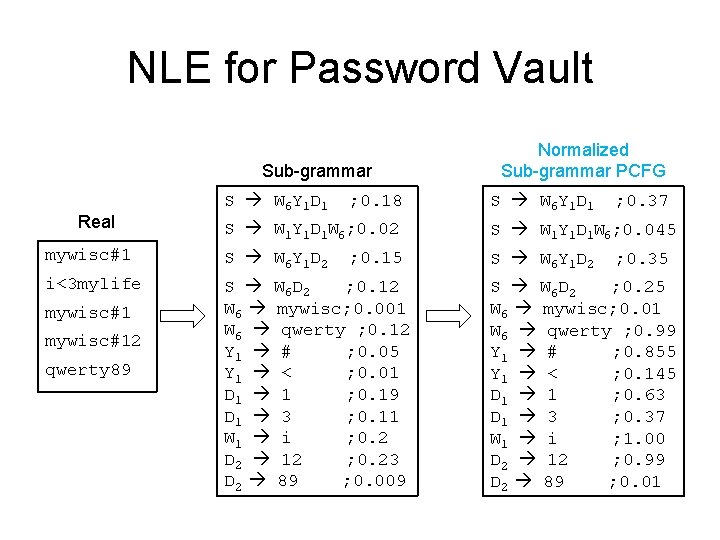
NLE for Password Vault • Sub-grammar PCFG – Hierarchical model (sort of) – Sample a sub-grammar – then sample passwords from the sub-grammar • How to sample a sub-grammar ? – a sub-grammar is again a set of rules – Sample rules from the base PCFG – Borrow the probabilities of each rule as well (for best results please normalize before use!)

NLE for Password Vault Normalized Subgrammar PCFG S W 6 Y 1 D 1 ; 0. 37 S W 1 Y 1 D 1 W 6; 0. 045 S W 6 Y 1 D 2 ; 0. 35 S W 6 D 2 ; 0. 25 W 6 mywisc; 0. 01 W 6 qwerty ; 0. 99 Y 1 # ; 0. 855 Y 1 < ; 0. 145 D 1 1 ; 0. 63 D 1 3 ; 0. 37 W 1 i ; 1. 00 D 2 12 ; 0. 99 D 2 89 ; 0. 01 qwerty#1 , qwerty<1, qwerty#3, qwerty#12, mywisc<3, qwerty 12, …

NLE for Password Vault Sub-grammar Real S W 6 Y 1 D 1 ; 0. 18 Normalized Sub-grammar PCFG S W 6 Y 1 D 1 ; 0. 37 S W 1 Y 1 D 1 W 6; 0. 02 S W 1 Y 1 D 1 W 6; 0. 045 mywisc#1 S W 6 Y 1 D 2 i<3 mylife S W 6 D 2 ; 0. 12 W 6 mywisc; 0. 001 W 6 qwerty ; 0. 12 Y 1 # ; 0. 05 Y 1 < ; 0. 01 D 1 1 ; 0. 19 D 1 3 ; 0. 11 W 1 i ; 0. 2 D 2 12 ; 0. 23 D 2 89 ; 0. 009 mywisc#12 qwerty 89 ; 0. 15 ; 0. 35 S W 6 D 2 ; 0. 25 W 6 mywisc; 0. 01 W 6 qwerty ; 0. 99 Y 1 # ; 0. 855 Y 1 < ; 0. 145 D 1 1 ; 0. 63 D 1 3 ; 0. 37 W 1 i ; 1. 00 D 2 12 ; 0. 99 D 2 89 ; 0. 01

Evaluating Password Vault NLE • Same setup except – with more feature vectors • Repeat Count • Edit distance • n-gram structure – Tested against: subset of Pastebin Vault leak (#Real) • Expected rank (r ) > 37%. – At an average 37% of all the decoy vaults call for an online query!! – Online work = 37% of the Offline work

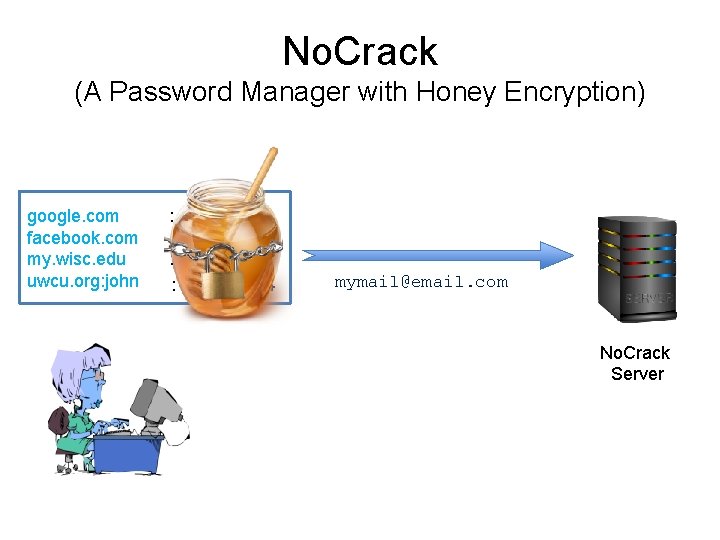
No. Crack (A Password Manager with Honey Encryption) google. com facebook. com my. wisc. edu uwcu. org: john : family 00 : family 01 : family. 1 : da#F 7+w. F 4 mymail@email. com No. Crack Server

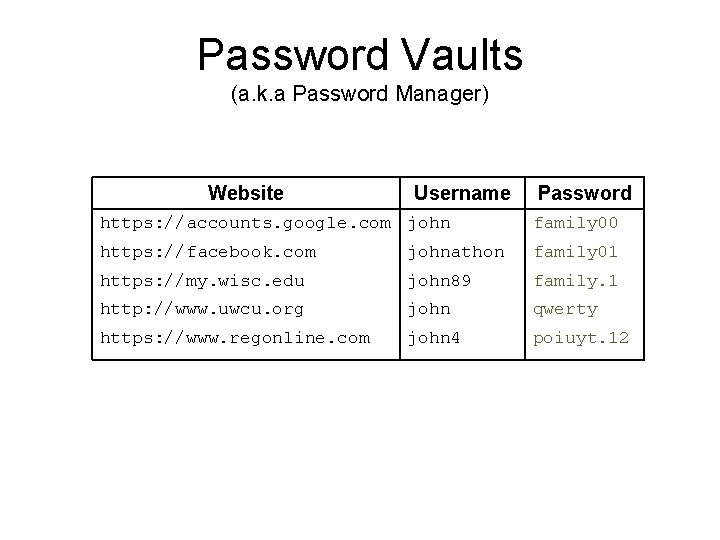
Password Vaults (a. k. a Password Manager) Website Username Password https: //accounts. google. com john family 00 https: //facebook. com johnathon family 01 https: //my. wisc. edu john 89 family. 1 http: //www. uwcu. org john qwerty https: //www. regonline. com john 4 poiuyt. 12

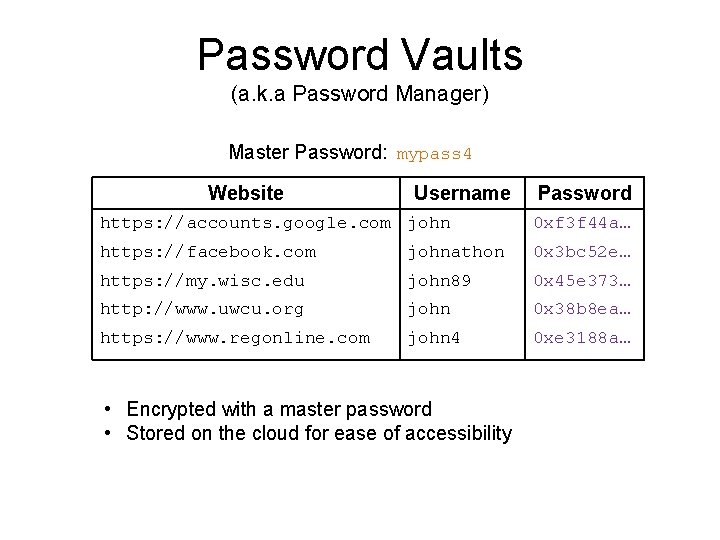
Password Vaults (a. k. a Password Manager) Master Password: mypass 4 Website Username Password https: //accounts. google. com john 0 xf 3 f 44 a… https: //facebook. com johnathon 0 x 3 bc 52 e… https: //my. wisc. edu john 89 0 x 45 e 373… http: //www. uwcu. org john 0 x 38 b 8 ea… https: //www. regonline. com john 4 0 xe 3188 a… • Encrypted with a master password • Stored on the cloud for ease of accessibility

Summary of Our Work ck a Cr No Weakness in only prior work Kamouflage

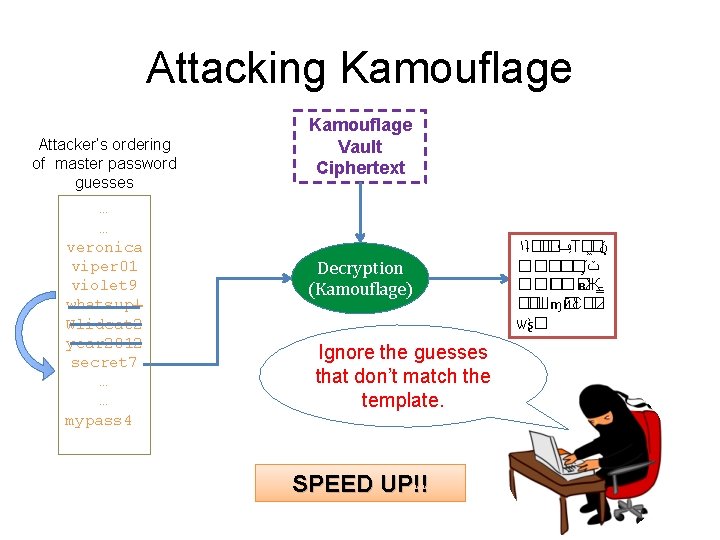
Attacking Kamouflage Attacker’s ordering of master password guesses … … veronica viper 01 violet 9 whatsup! Wlidcat 2 year 2012 secret 7 … … mypass 4 Kamouflage Vault Ciphertext Decryption (Kamouflage) Ignore the guesses that don’t match the template. SPEED UP!! ١ʇ�� � ݠ Т� � � ݩ ����� ΄ ݖ ��� ʙЖ ـ ��Шɱ� йԐ�� ѡʂ �

NLE for Password Vault {John#1, John 12, john 123, John@123} Independent samples from the base PCFG {qwerty, john#1, password, wow 1!} • Challenge: – How to model related passwords? • Sub-grammar Approach

Security Evaluation for NLEs • Security goal: output of Decode should look “real” • 1 -in-q experiment: – Attacker given list with 1 real and q-1 decoys generated by Decode – Can attacker “Sort the list” so that real is at top? • Best machine learning classifiers we found: – ~35% of decoy passwords are perceived to be more real than the real one by our best classifier! – Ideal would be 50% Attacker will have to make many online queries

Security Evaluation for NLEs • Security goal: output of Decode should look “real” • Experimented with machine learning-based attacks • Best attack we could find: – q decryptions – q/3 online queries on average • Ideal security: q/2 online queries Attacker will have to make many online queries