CMSC 421 Chapter 22 Operating System Concepts Windows


































- Slides: 62

CMSC 421 Chapter 22 Operating System Concepts Windows XP

Windows XP b Windows XP operating system is a 32/64 - bit preemptive multitasking operating system for AMD K 6/K 7, Intel IA 32/IA 64 and later microprocessors. It is the successor to Windows NT/2000 and the replacement for Windows 95/98.

History b Many features are from NT/2000. b Uses a client-server architecture (like Mach) to implement multiple operating system personalities, such as Win 32 and POSIX. b Comes in two versions, Personal and Professional.

Design Principles b Security b Reliability b Windows and POSIX Application Compatibility b High Performance b Extensibility b Portability b International Support

Security b Adherence to the design standards to receive U. S. Government C-2 security designation. b Extensive code review and testing, plus use of sophisticated automatic analysis tools to investigate potential defects that might represent security vulnerabilities.

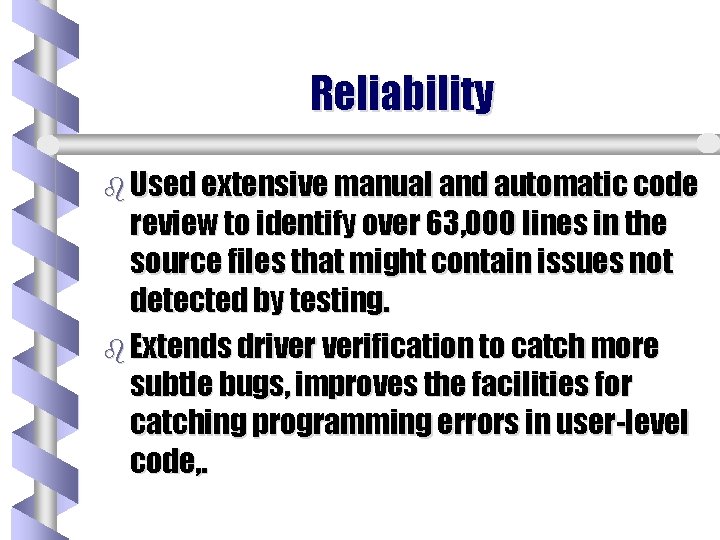
Reliability b Used extensive manual and automatic code review to identify over 63, 000 lines in the source files that might contain issues not detected by testing. b Extends driver verification to catch more subtle bugs, improves the facilities for catching programming errors in user-level code, .

Reliability -- II b Subjects third party applications, drivers and devices to a rigorous certification process. b New facilities for monitoring the health of the PC including downloading fixes for problems before they are encountered by the users.

Windows/ POSIX Application Compatibility b Application compatibility is difficult to achieve because each application checks for a particular version of Windows, may have dependence on the quirks of the implementation of APIs. b XP introduces a compatibility layer that falls between applications and the Win 32 API. This layer makes XP look “bug-for-bug” compatible with previous versions of Windows.

Windows/ POSIX Application Compatibility -- II b Maintains support for running many 16 -bit applications using a “thunking layer” that translates 16 -bit API calls into equivalent 32 -bit calls. b 64 -bit version provides a thunking layer that translates 32 -bit API calls into native 64 -bit calls.

Windows/ POSIX Application Compatibility -- III b POSIX support is a POSIX subsystem called Interix. b Most available UNIX-compatible software compiles and runs under Interix without modification.

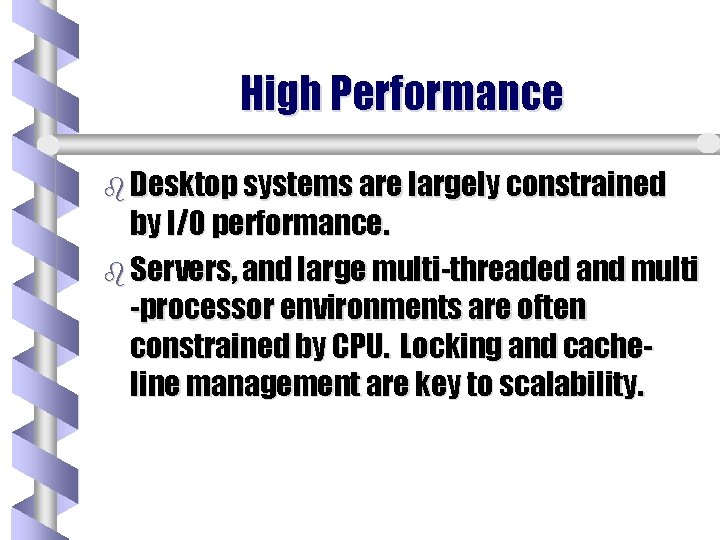
High Performance b Desktop systems are largely constrained by I/O performance. b Servers, and large multi-threaded and multi -processor environments are often constrained by CPU. Locking and cacheline management are key to scalability.

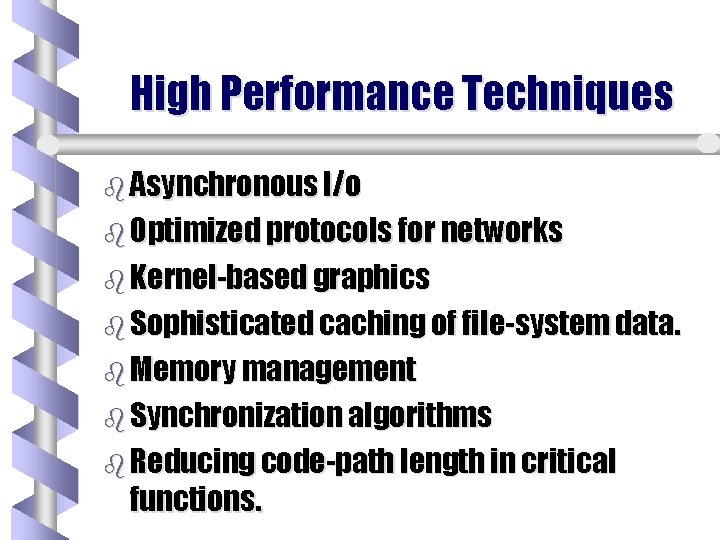
High Performance Techniques b Asynchronous I/o b Optimized protocols for networks b Kernel-based graphics b Sophisticated caching of file-system data. b Memory management b Synchronization algorithms b Reducing code-path length in critical functions.

High Performance Techniques -II b Using better algorithms and per-processor data structures. b Implementing more scalable locking protocols. b Except while executing in the kernel dispatcher, threads in the subsystems of Windows XP can be preempted by higherpriority threads.

Extensibility b Used a layered architecture. b Uses environmental subsystems to emulate different operating systems (DOS, Windows, POSIX). b Uses loadable drivers in the I/O system. b Uses RPCs for distributed processing.

Portability b Can be moved from one hardware architecture to another with relatively few changes. b Majority of the system is written in C and C++. b Processor-dependent code is isolated in DLL called hardware-abstraction layer (HAL).

Portability -- II b Only shipped on IA 32 compatible platforms, it was also tested on DEC Alpha. b “Maintaining portability is a matter of use it or loss it. ”

International Support b Uses National Language Support API. b Uses UNICODE as the native language character code. b ASCII is converted to UNICODE. b System text strings are kept in resource files that can be replaced to localize the system for different languages. b Multiple locales can be used concurrently.

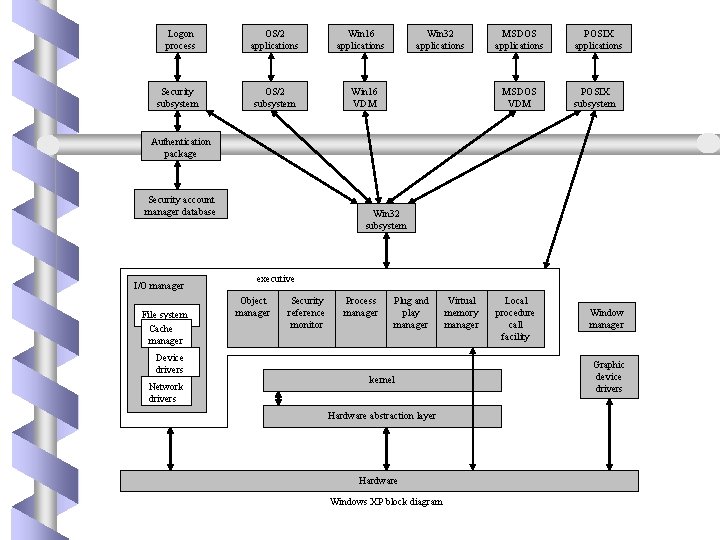
System Components b Hardware-Abstraction Layer b Kernel b Executive

Logon process Security subsystem OS/2 applications OS/2 subsystem Win 16 applications Win 32 applications Win 16 VDM MSDOS applications MSDOS VDM POSIX applications POSIX subsystem Authentication package Security account manager database I/O manager File system Cache manager Device drivers Network drivers Win 32 subsystem executive Object manager Security reference monitor Process manager Plug and play manager kernel Hardware abstraction layer Hardware Windows XP block diagram Virtual memory manager Local procedure call facility Window manager Graphic device drivers

Hardware Abstraction Layer b HAL is the layer of software that hides hardware differences from upper levels of the operating system. b HAL exports a virtual-machine interface that is used by the kernel dispatcher, the executive, and the device drivers. b Only a single version of each device driver is required.

Kernel b Kernel Dispatcher b Threads and Scheduling b Implementation of Synchronization Primitives b Software Interrupt: Async Proc Calls b Software Interrupt: Deferred Proc Calls b Exceptions and Interrupts

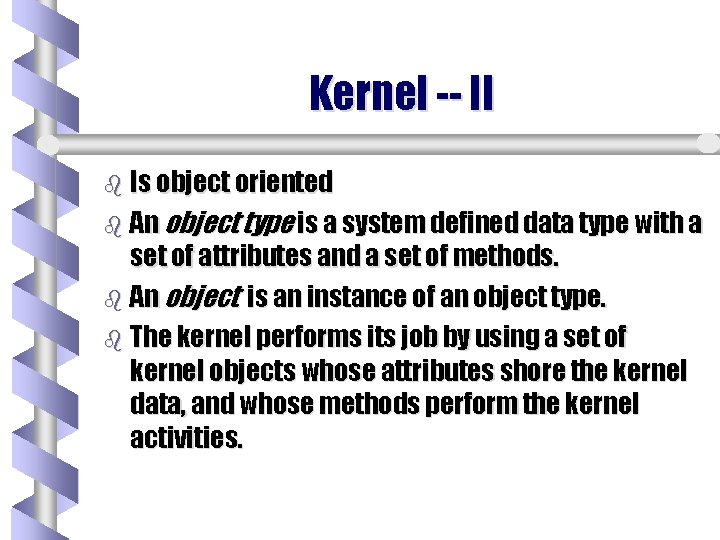
Kernel -- II b Is object oriented b An object type is a system defined data type with a set of attributes and a set of methods. b An object is an instance of an object type. b The kernel performs its job by using a set of kernel objects whose attributes shore the kernel data, and whose methods perform the kernel activities.

Kernel Dispatcher b Provides the foundation for the executive and subsystems b Most is never paged out b Can not be preempted

Kernel Dispatcher Responsibilities b Thread scheduling b Implementation of synch primitives b Timer management b Software interrupts b Exception dispatching

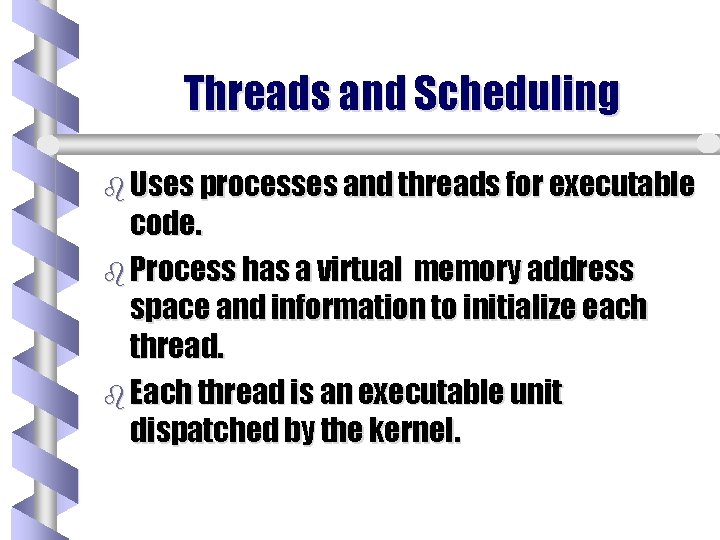
Threads and Scheduling b Uses processes and threads for executable code. b Process has a virtual memory address space and information to initialize each thread. b Each thread is an executable unit dispatched by the kernel.

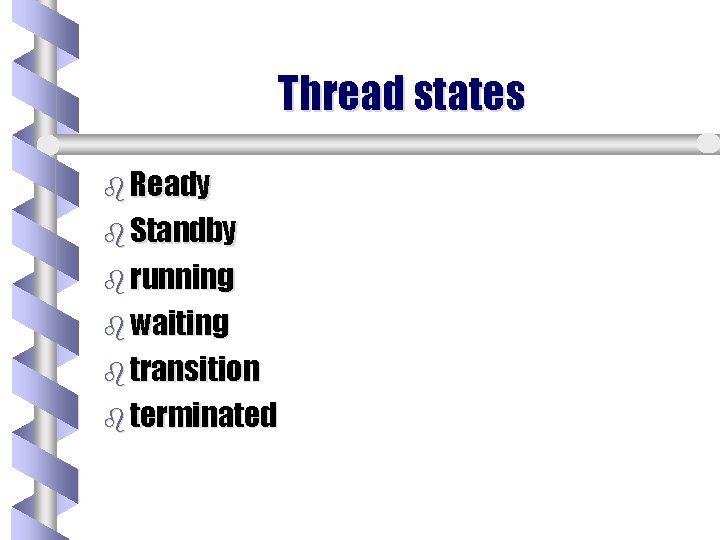
Thread states b Ready b Standby b running b waiting b transition b terminated

Priority scheme b 32 -level scheme b Variable class (0 - 15) b Real-time class (16 - 31) b Uses a queue for each priority

Implementation of Synchronization Primitives b Dispatcher objects control dispatching and synchronization b Event objects record an event occurrence b Mutant provides mutex b Semaphore object acts as a counter or a gate b Thread object is the entity that is scheduled b Timer objects keep track of time

Asynchronous Procedure Call b Break into an executing thread and call procedure. b APCs are used to begin execution of a new thread, terminate processes, and deliver notification that an asynch I/O has completed. b Queued to a specific thread b Allow the system to execute both system and user code within a process’ context

Deferred Procedure Call b DPCs are used to postpone interrupt processing. b Process timer expirations b Preempt thread execution at end of scheduling quantum

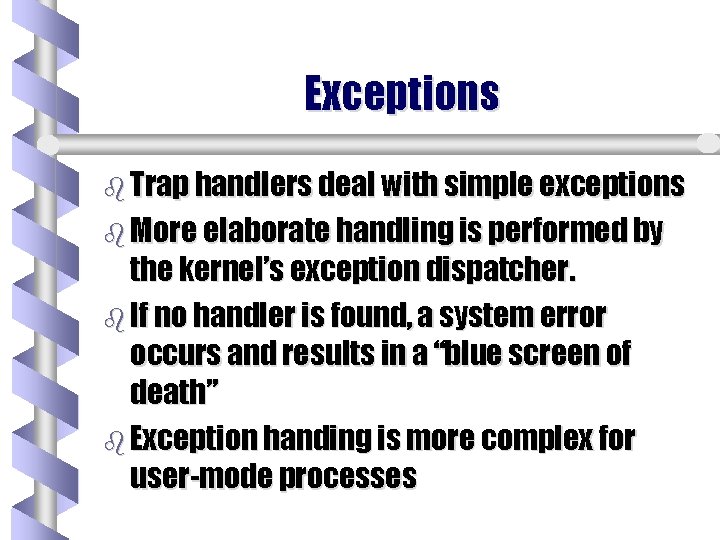
Exceptions and Interrupts b Architecture-independent exceptions • • memory-access violation integer and floating point divide by zero overflow or underflow illegal instruction data misalignment privileged instruction page read error, etc

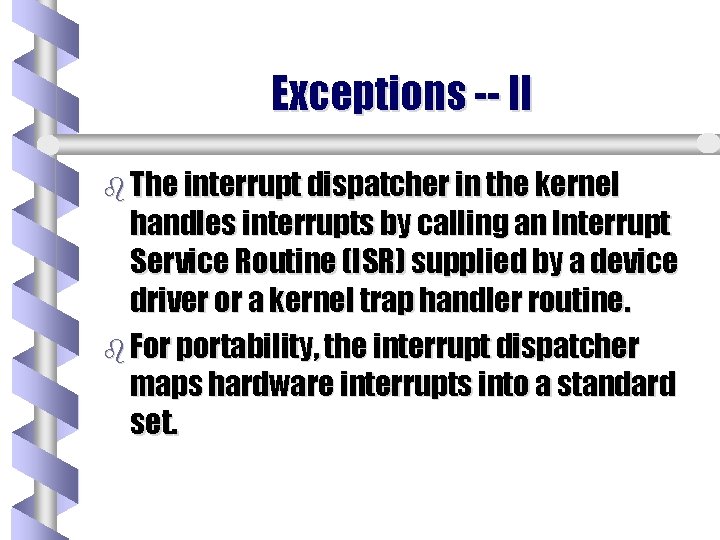
Exceptions b Trap handlers deal with simple exceptions b More elaborate handling is performed by the kernel’s exception dispatcher. b If no handler is found, a system error occurs and results in a “blue screen of death” b Exception handing is more complex for user-mode processes

Exceptions -- II b The interrupt dispatcher in the kernel handles interrupts by calling an Interrupt Service Routine (ISR) supplied by a device driver or a kernel trap handler routine. b For portability, the interrupt dispatcher maps hardware interrupts into a standard set.

Executive b Provides a set of services that all environmental subsystems use: • • • Object manager Virtual memory manager Process manager Local procedure call facility I/O manager Security reference monitor Plug-and-play and security managers registry booting

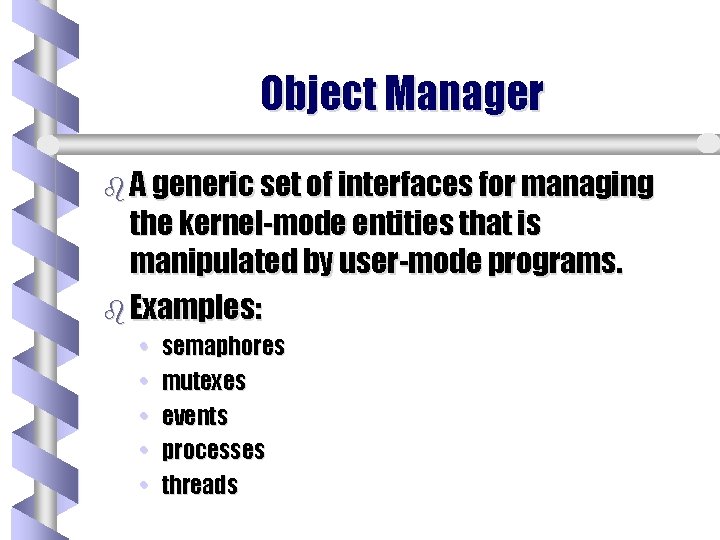
Object Manager b A generic set of interfaces for managing the kernel-mode entities that is manipulated by user-mode programs. b Examples: • • • semaphores mutexes events processes threads

Handles b Each process has an object table that track the objects used by the process b User-mode code accesses these objects using an opaque value called a handle that is returned by many APIs. b Object handles can be created by duplicating an existing handle, either from either the same or different process.

Virtual Functions b Objects are manipulated by a set of virtual functions with implementations provided by each object type: • query - gets object’s name • parse - search for an object given the object’s name • security - makes security checks on all object operations.

Virtual Memory Manager b The design of the VM Manager assumes that the underlying hardware supports virtual-to-physical mapping, a paging mechanism, transparent cache coherence on multiprocessor systems and allows multiple page-table entries to map to the same physical page frame.

Virtual Memory Manager -- II b On IA 32 processors each process has a 4 GB virtual address space. b The upper 2 GB are mostly identical for all processes, and are used by Windows XP in kernel mode to access the operating system code and data structures. b Key areas that are not identical are page table self-map, hyperspace and session space.

Page Table Self-map b The hardware uses a process’s page tables using physical page-frame numbers. b The VM manager maps the page tables into a single 4 GB region in the process’ address space so they are accessed through virtual addresses.

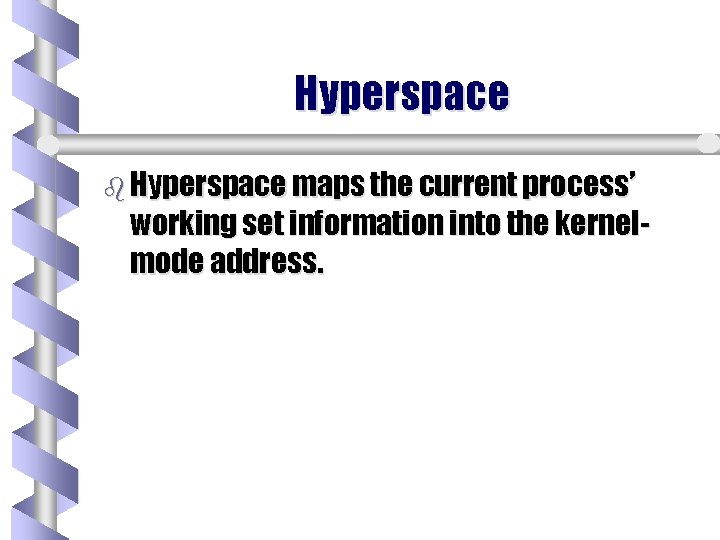
Hyperspace b Hyperspace maps the current process’ working set information into the kernelmode address.

Session Space b Session space is used to share the win 32 and other session-specific drivers between all the processes in the same terminalserver session rather than with all the processes in the system.

Process Manager b Provides services for creating, deleting, and using processes, threads, and jobs. b It has no knowledge about parent-child relationships; left to environmental subsystems. b Processes contain one or more threads. b Processes can be collected together into job objects.

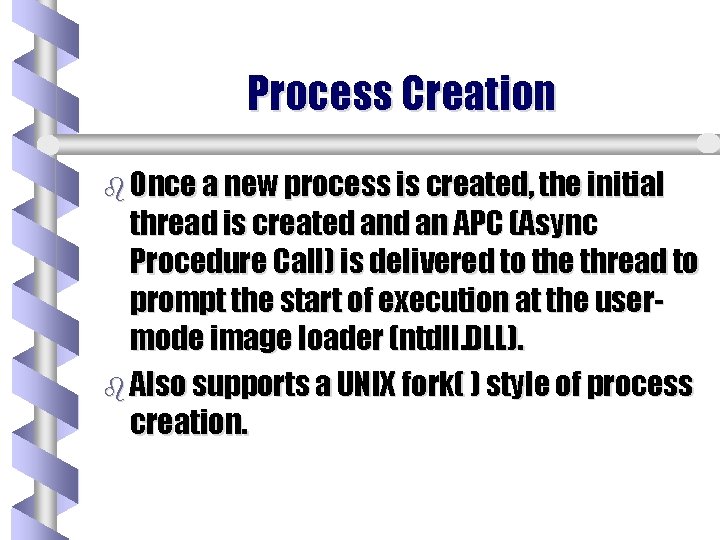
Process Creation b Once a new process is created, the initial thread is created an APC (Async Procedure Call) is delivered to the thread to prompt the start of execution at the usermode image loader (ntdll. DLL). b Also supports a UNIX fork( ) style of process creation.

Local Procedure Call Facility b XP uses a client-server model. b Environmental subsystems are servers that implement particular operating system personalities. b XP uses LPCs to pass requests and results (messages) between client and server processes within a single machine.

I/O Manager b Responsible for file-systems, device drivers, and network drivers. b Works with VM to provide memory mapped I/O operations. b Is fundamentally asynchronous. b Device drivers are written according to the Windows Driver Model (WDM) specification.

WDM b Because of the richness of the WDM, it can be an excessive amount of work to write a full WDM device driver for each new hardware device.

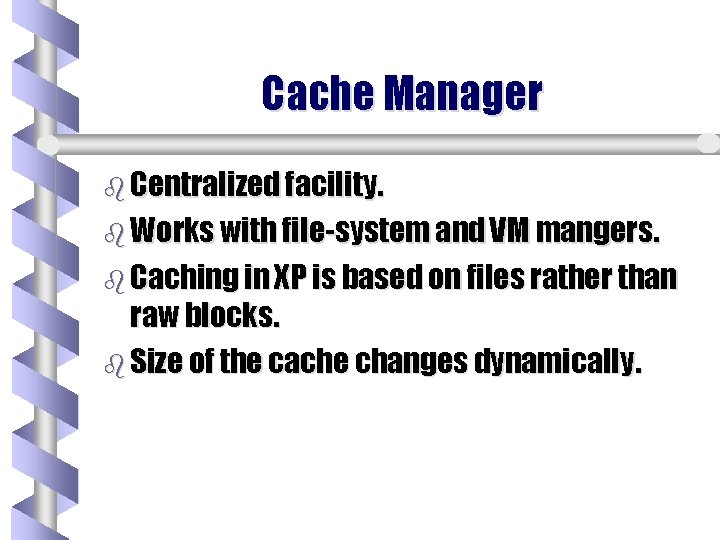
Cache Manager b Centralized facility. b Works with file-system and VM mangers. b Caching in XP is based on files rather than raw blocks. b Size of the cache changes dynamically.

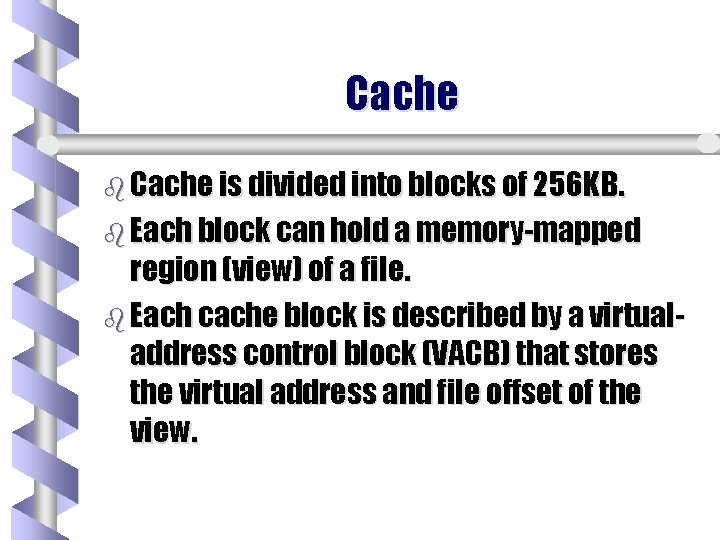
Cache b Cache is divided into blocks of 256 KB. b Each block can hold a memory-mapped region (view) of a file. b Each cache block is described by a virtualaddress control block (VACB) that stores the virtual address and file offset of the view.

Security Reference Monitor b Centralized management of system entities in the object manager enables the use of a uniform mechanism to perform run-time access validation and audit checks for every user-accessible entity in the system.

Security Tokens b The SRM is responsible for manipulating the privileges in security tokens. b Special privileges are required to perform back or restore operations, overcome certain checks as an administrator, debug processes, etc. b Restricted tokens used to restrict the damage of untrusted code.

Logging b The SRM is logging security audit events. A C 2 rating requires the ability to detect and log all unauthorized attempts to access system resources.

Plug-and-Play Managers b Recognizes and adapts to changes in the hardware configuration. b For Pn. P to work, both the device and driver must support the Pn. P standard. b Must be able to change the interrupts dynamically. b Must support dynamically configurable resources.

Registry b Configuration information is stored in an internal database -- the registry. b Entries (hives) are for system information, default user preferences, software installation, and security. b Used to boot the system.

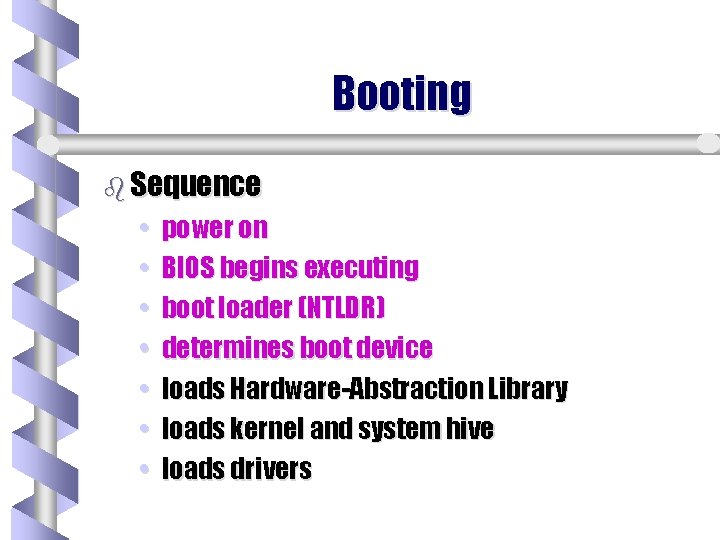
Booting b Sequence • • power on BIOS begins executing boot loader (NTLDR) determines boot device loads Hardware-Abstraction Library loads kernel and system hive loads drivers

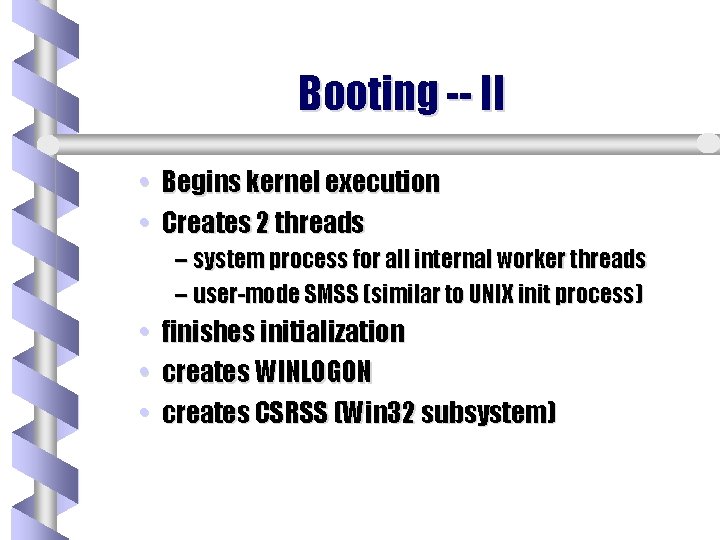
Booting -- II • Begins kernel execution • Creates 2 threads – system process for all internal worker threads – user-mode SMSS (similar to UNIX init process) • finishes initialization • creates WINLOGON • creates CSRSS (Win 32 subsystem)

Environmental Subsystem b Is user-mode processes layered over the native windows XP exec servers to run programs developed for other Oss (16 -bit Windows, DOS, and POSIX). b Win 32 calls the VM manager to load the executable code and return what type the application is.

Environmental Subsystem - II b Uses LPC subsystem to provide OS services to client processes. b Since each subsystem is run as a separate user-mode process, a crash in one has no effect on other processes. The exception is in Win 32, which provides all keyboard, mouse, and graphical display capabilities -If it fails, the system requires a reboot.

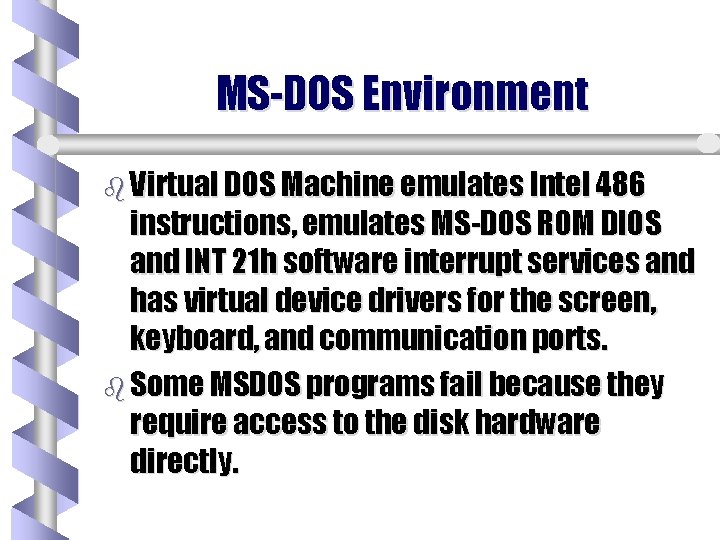
MS-DOS Environment b Virtual DOS Machine emulates Intel 486 instructions, emulates MS-DOS ROM DIOS and INT 21 h software interrupt services and has virtual device drivers for the screen, keyboard, and communication ports. b Some MSDOS programs fail because they require access to the disk hardware directly.

16 -Bit Windows Environment b VDM has Windows on Windows (WOW 32) for Windows 3. 1 software and emulates the kernel routines. b Applications that rely on the internal structure of the 16 -bit window manager may not work. b Only one Win 16 application can run at a time.

32 -Bit Windows Env. On IA 64 b Requires a “thunking” layer to translate 32 - bit Win 32 calles into the corresponding 64 bit calls. b The implementation of 32 -bit and 64 -bit windows are essential the same, IA 64 provides direction execution of IA 32 instructions. -- higher level of compatibility.
