COMP 421 CMPET 401 COMMUNICATIONS and NETWORKING CLASS






































- Slides: 81

COMP 421 /CMPET 401 COMMUNICATIONS and NETWORKING CLASS 2

OSI Reference Model a. Developed by the International Standards Organization (ISO) to facilitate the international standardization of communications protocols a. For U. S. : ANSI (American National Standard Institute) - www. ansi. org a. OSI is ISO's Basic Reference Model for Open Systems Interconnect (hence: ISO/OSI) a. The Reference Model itself is not a Network Architecture (does not specify any protocols or services)

The ISO/OSI Reference Model a. The model describes computer communications protocols in a general sense to facilitate discussion a. No assumptions are made regarding: u. Programming language bindings u. Operating system bindings u. Applications programming interfaces a. Development of the model started in the mid-1970’s a. Biggest Problems u. Very long time to complete the model and protocol standards u. Very hard to understand the detailed standards u. Difficult (expensive) to get the standards documents

OSI MODEL

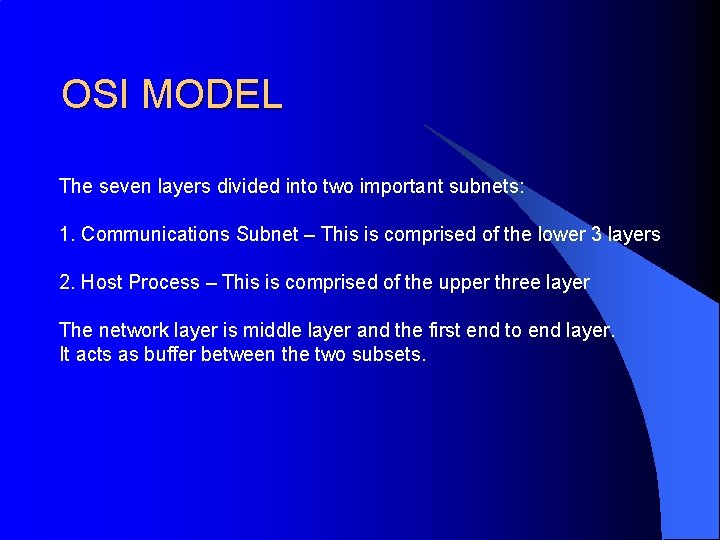
OSI MODEL The seven layers divided into two important subnets: 1. Communications Subnet – This is comprised of the lower 3 layers 2. Host Process – This is comprised of the upper three layer The network layer is middle layer and the first end to end layer. It acts as buffer between the two subsets.

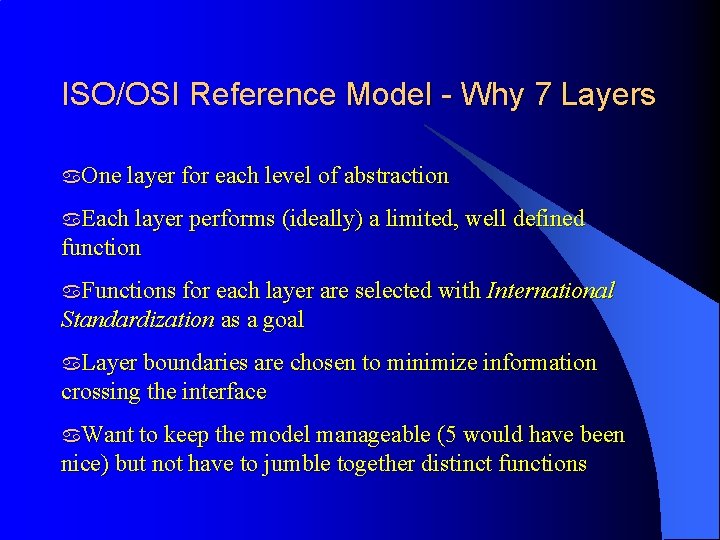
ISO/OSI Reference Model - Why 7 Layers a. One layer for each level of abstraction a. Each layer performs (ideally) a limited, well defined function a. Functions for each layer are selected with International Standardization as a goal a. Layer boundaries are chosen to minimize information crossing the interface a. Want to keep the model manageable (5 would have been nice) but not have to jumble together distinct functions

OSI Model App Process X Application Data Application AH Presentation SH Transport TH Network NH Data Link FAC Physical Application Data Unit Presentation PH Session App Process Y Session Data Unit Transport Data Unit BITS Network FCS F Data Link Physical Communication Path Physical Transmission Medium

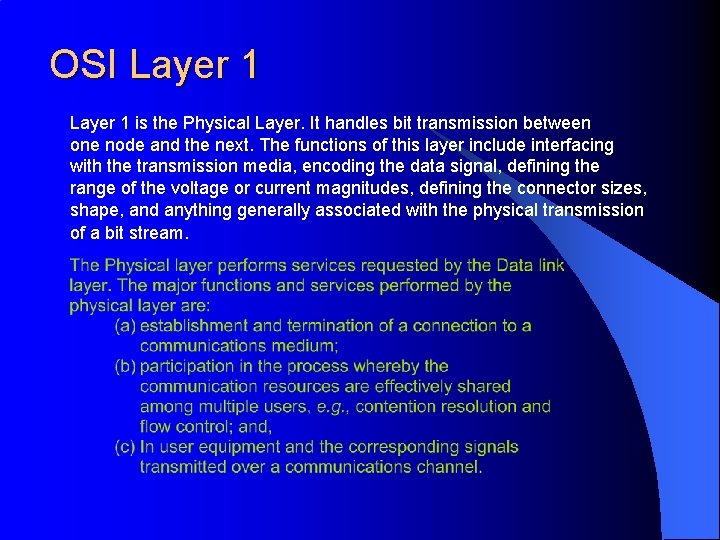
OSI Layer 1 is the Physical Layer. It handles bit transmission between one node and the next. The functions of this layer include interfacing with the transmission media, encoding the data signal, defining the range of the voltage or current magnitudes, defining the connector sizes, shape, and anything generally associated with the physical transmission of a bit stream.

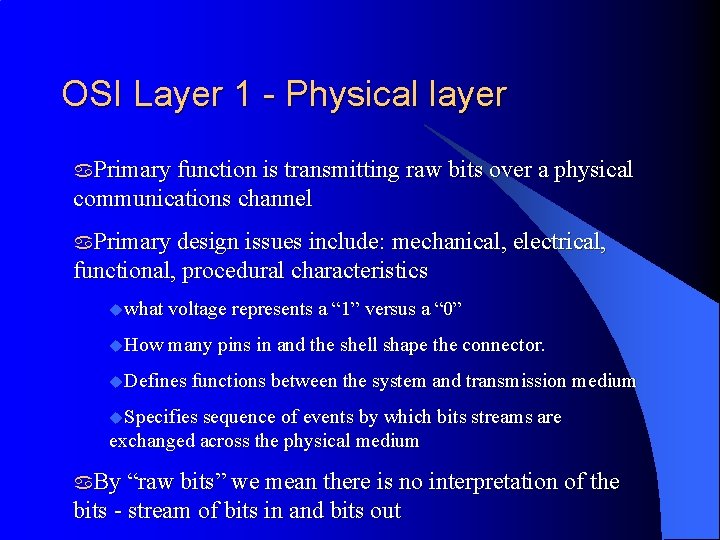
OSI Layer 1 - Physical layer a. Primary function is transmitting raw bits over a physical communications channel a. Primary design issues include: mechanical, electrical, functional, procedural characteristics uwhat voltage represents a “ 1” versus a “ 0” u. How many pins in and the shell shape the connector. u. Defines functions between the system and transmission medium u. Specifies sequence of events by which bits streams are exchanged across the physical medium a. By “raw bits” we mean there is no interpretation of the bits - stream of bits in and bits out

OSI Layer 2 - Data Link layer a. Primary function is to make Layer 1 into what appears to be a channel free of undetected errors a. Deals with data in chunks (typically 100 s-1000 s of bytes) generally called Frames a. This layer must create/recognize frame boundaries uremember - Physical layer does not care uoften requires special bit patterns to signal boundaries umay have to deal with possibility of pattern appearing in data

OSI Layer 2 In other words it maintains the reliable communications link between adjacent nodes. The DLL inserts addresses in the data frame and provides error control for the data.

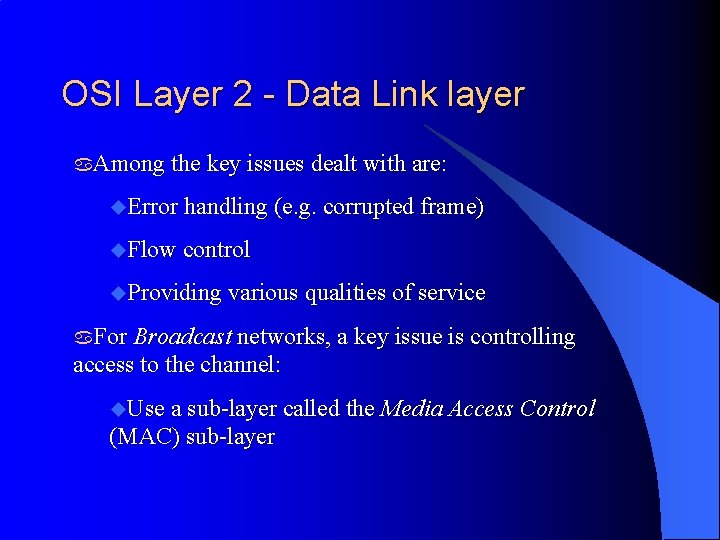
OSI Layer 2 - Data Link layer a. Among the key issues dealt with are: u. Error handling (e. g. corrupted frame) u. Flow control u. Providing various qualities of service a. For Broadcast networks, a key issue is controlling access to the channel: u. Use a sub-layer called the Media Access Control (MAC) sub-layer

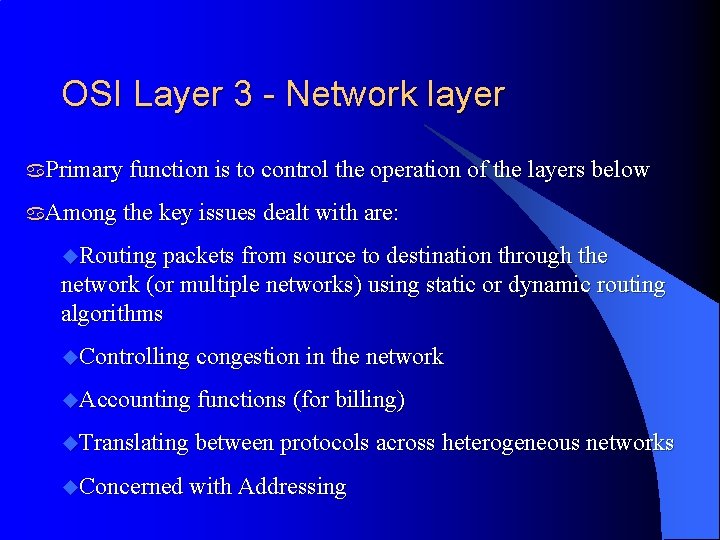
OSI Layer 3 - Network layer a. Primary function is to control the operation of the layers below a. Among the key issues dealt with are: u. Routing packets from source to destination through the network (or multiple networks) using static or dynamic routing algorithms u. Controlling congestion in the network u. Accounting functions (for billing) u. Translating between protocols across heterogeneous networks u. Concerned with Addressing

OSI Layer 3 This layer establishes the path for the traveling data packet

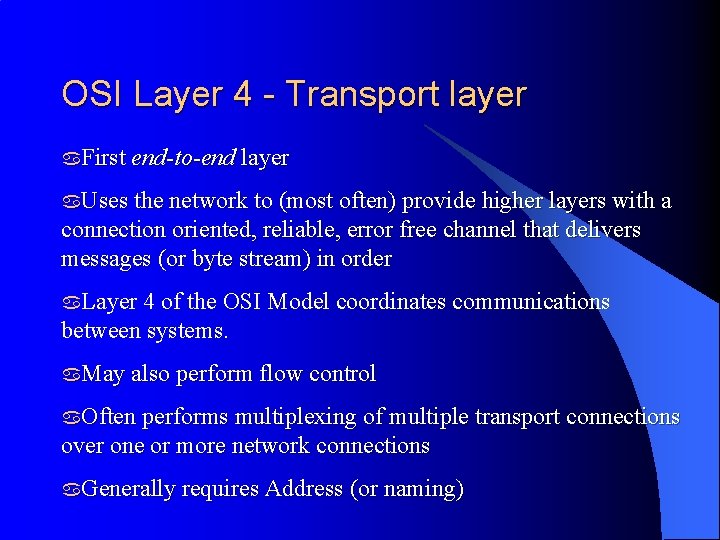
OSI Layer 4 - Transport layer a. First end-to-end layer a. Uses the network to (most often) provide higher layers with a connection oriented, reliable, error free channel that delivers messages (or byte stream) in order a. Layer 4 of the OSI Model coordinates communications between systems. a. May also perform flow control a. Often performs multiplexing of multiple transport connections over one or more network connections a. Generally requires Address (or naming)

OSI Layer 4 This layer provides reliable delivery of host messages originating at layer 7 the same way as the DLL assures reliable delivery of frames between adjacent nodes. This is the layer responsible for Segmenting long messages in smaller units (packets) and then Reassembling them at the other end.

OSI Layer 5 - Session layer a. Manages dialog control (e. g. may manage who’s turn it is to talk in a high-level half-duplex protocol) a. Manages synchronization of transactions which may need to be able to roll back in case of a crash a. Sort of an unwanted layer, this layer is usually very thin and little more than a pass through for most protocols a. Key services provided include: a. Dialogue discipline a. Grouping - data mark as belonging to a special group a. Recovery – checkpoint mechanism

OSI Layer 5 In other words it establishes and terminates process to process communications Sessions between hosts.

OSI Layer 6 - Presentation layer a. Rather than being concerned with moving information, the Presentation layer is concerned with the interpretation of information representation a. Ensures that the syntax and meaning is the same for each participant in a communication a. Provides for standard representation and may provide capabilities for conversion of data

OSI Layer 6 Simply put this layer establishes the syntax in which data is exchanged between the two hosts. It provides a data manipulation function rather than a communication function (data compression and data encryption are examples of this layers activities)

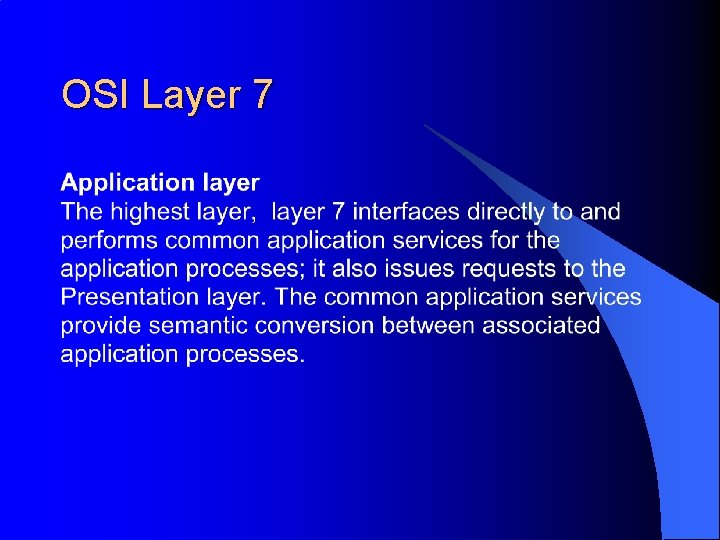
OSI Layer 7 - Application layer a. The layer where end-user applications live a. This is the highest level of abstraction and the level which is of primary importance (for most users) a. All the rest of the layers exist to support these applications a. Layering exists so we can move these around to different machines, and so they can communicate across any platforms - Open Systems Interconnect

OSI Layer 7

OSI Examples

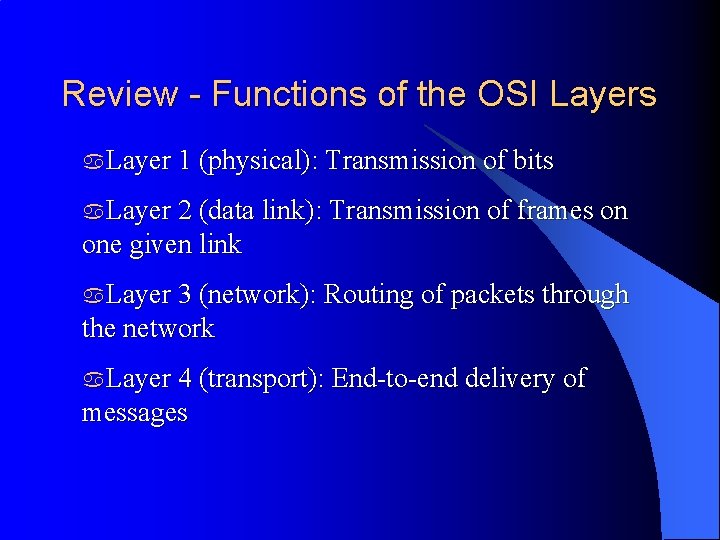
Review - Functions of the OSI Layers a. Layer 1 (physical): Transmission of bits a. Layer 2 (data link): Transmission of frames on one given link a. Layer 3 (network): Routing of packets through the network a. Layer 4 (transport): End-to-end delivery of messages

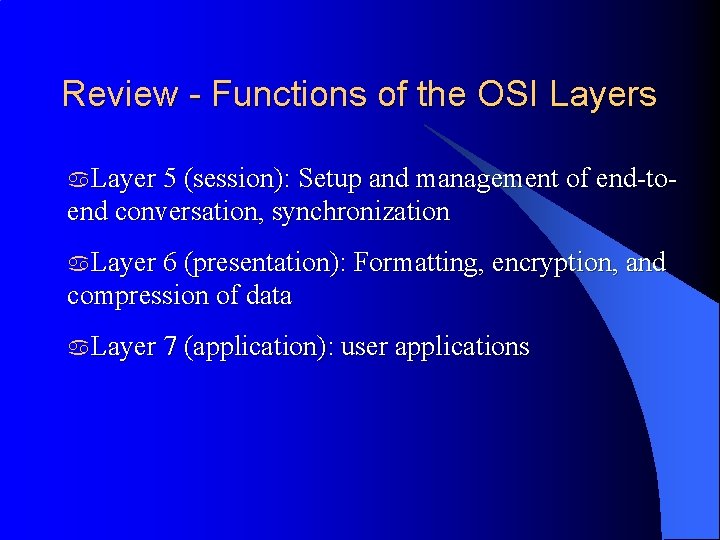
Review - Functions of the OSI Layers a. Layer 5 (session): Setup and management of end-to- end conversation, synchronization a. Layer 6 (presentation): Formatting, encryption, and compression of data a. Layer 7 (application): user applications

Introduction to TCP/IP

What is TCP/IP l. Transmission Control Protocol/Internet Protocol l. TCP/IP refers to an entire suite of networking protocols, developed for use on the Internet l. TCP and IP are certainly two of the most important

TCP/IP Protocol Suite n. Advanced Research Project Agency (ARPA) of Do. D sponsored the development of ARPANET in 1970 s. n. TCP/IP has been adopted as the ARPANET protocol suite n. TCP/IP became popular by the inclusion of this protocol in BSD Unix system (a version of Unix developed by University of California @ Berkley)

TCP/IP (cont. ) n. Transport Layer-TCP (Transmission Control Protocol) • Provides fully reliable, connection-oriented service • Byte-stream transmission n. Network Layer- IP (Internet Protocol) • IP provides datagram service (used in packet switching) • It is connectionless unreliable service • IP handles routing

TCP/IP Characteristics l. TCP/IP provides the services necessary to interconnect computers and to interconnect networks, creating the Internet l. Independence from underlying network topology, physical network hardware, and OS l. Unique IP Address l. Universal connectivity throughout the network l. Standardize high-level protocols

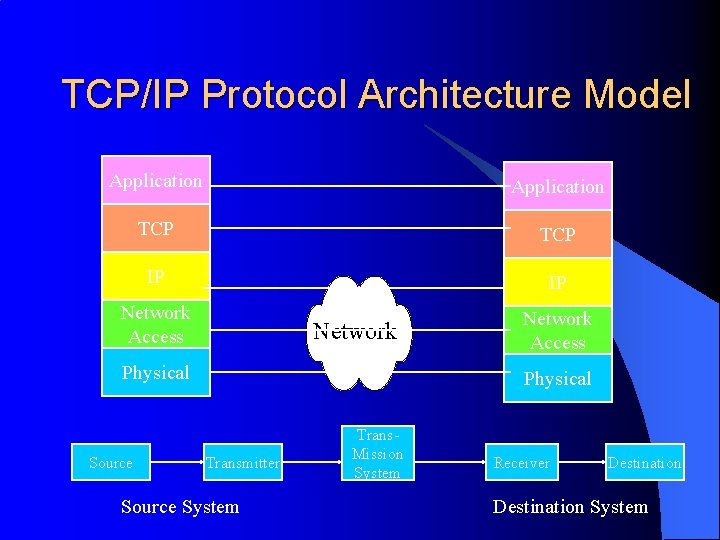
TCP/IP Protocol Architecture Model Application TCP IP IP Network Access Network Physical Source Network Access Physical Transmitter Source System Trans. Mission System Receiver Destination System

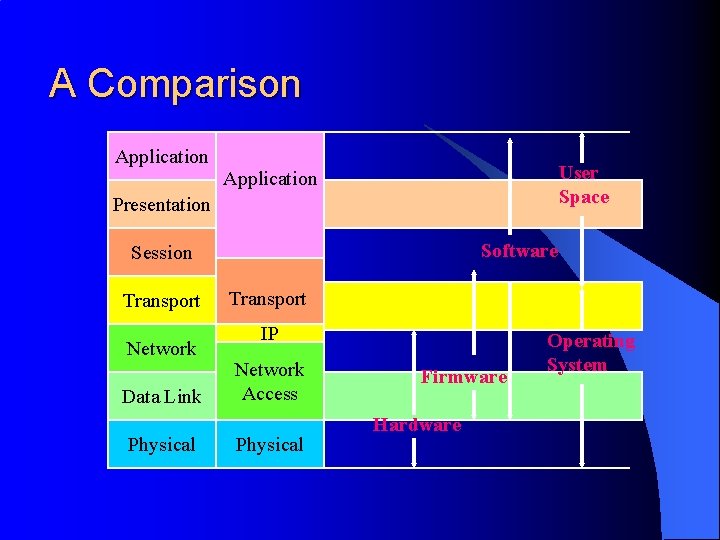
A Comparison Application User Space Application Presentation Software Session Transport Network Data Link Physical Transport IP Network Access Physical Firmware Hardware Operating System

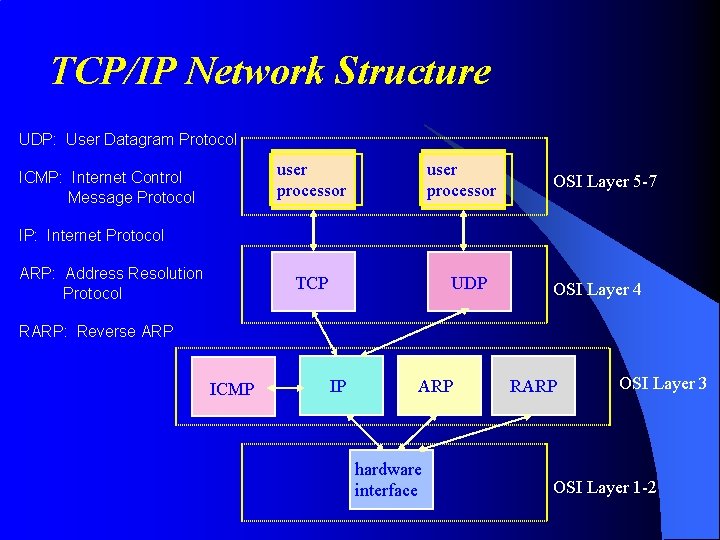
TCP/IP Network Structure UDP: User Datagram Protocol user processor ICMP: Internet Control Message Protocol user processor OSI Layer 5 -7 IP: Internet Protocol ARP: Address Resolution Protocol TCP UDP OSI Layer 4 RARP: Reverse ARP ICMP IP ARP hardware interface RARP OSI Layer 3 OSI Layer 1 -2

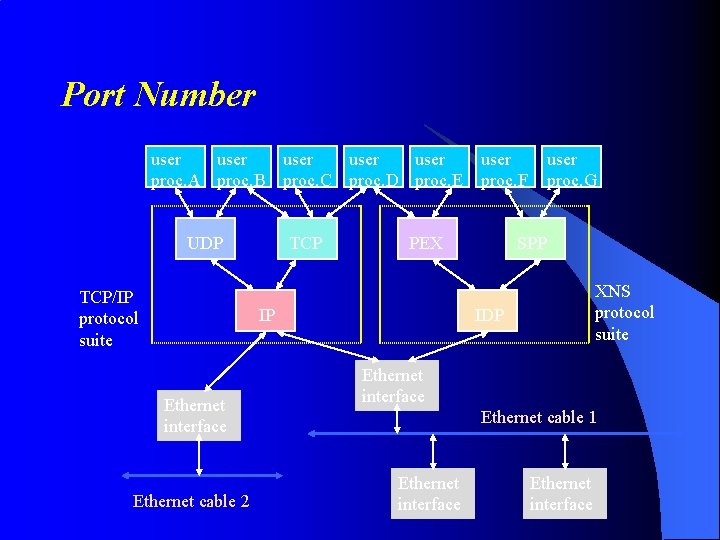
Port Number user user proc. A proc. B proc. C proc. D proc. E UDP TCP/IP protocol suite TCP PEX IP Ethernet interface Ethernet cable 2 user proc. F user proc. G SPP XNS protocol suite IDP Ethernet interface Ethernet cable 1 Ethernet interface

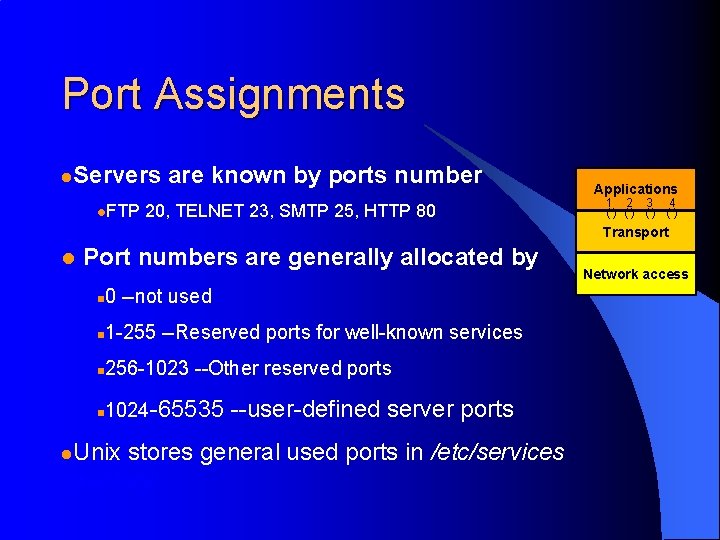
Port Assignments l. Servers l. FTP are known by ports number 20, TELNET 23, SMTP 25, HTTP 80 Applications 1 2 3 4 () () Transport l Port numbers are generally allocated by n 0 --not used n 1 -255 --Reserved ports for well-known services n 256 -1023 --Other reserved ports n 1024 -65535 l. Unix --user-defined server ports stores general used ports in /etc/services directory Network access

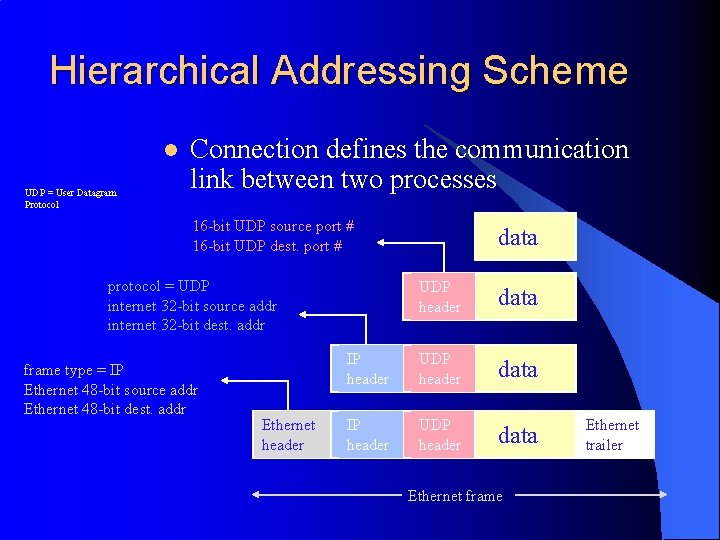
Hierarchical Addressing Scheme l UDP = User Datagram Protocol Connection defines the communication link between two processes 16 -bit UDP source port # 16 -bit UDP dest. port # protocol = UDP internet 32 -bit source addr internet 32 -bit dest. addr frame type = IP Ethernet 48 -bit source addr Ethernet 48 -bit dest. addr Ethernet header data UDP header data IP header UDP header data Ethernet frame Ethernet trailer

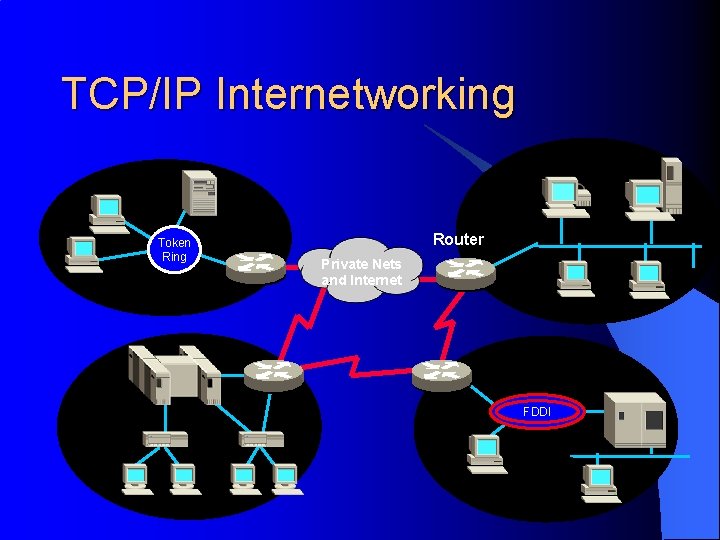
TCP/IP Internetworking Token Ring Router Private Nets and Internet FDDI

LAN and Devices LANs are designed to : Operate within a limited geographic area l Allow multi-access to high-bandwidth media l Control the network privately under local administration l Provide full-time connectivity to local services l Connect physically adjacent devices l Bridge Hub Ethernet Switch Router ATM Switch

Wide-Area Networks and Devices WANs are designed to : Operate over geography of telecommunications carriers l Allow access over serial interfaces operating at lower speeds l Control the network subject to regulated public services l Provide full-time and part-time connectivity l Connect devices separated over wide, even global areas l Router X. 25 or Modem Frame Relay CSU/DSU Switch TA/NT 1 S Comm. Server Multiplexor stat mux ATM Switch

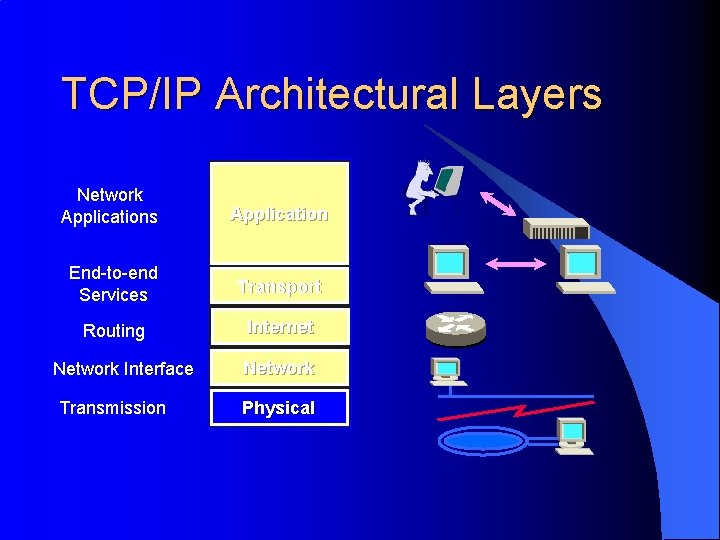
TCP/IP Architectural Layers Network Applications Application End-to-end Services Transport Routing Internet Network Interface Transmission Network Physical

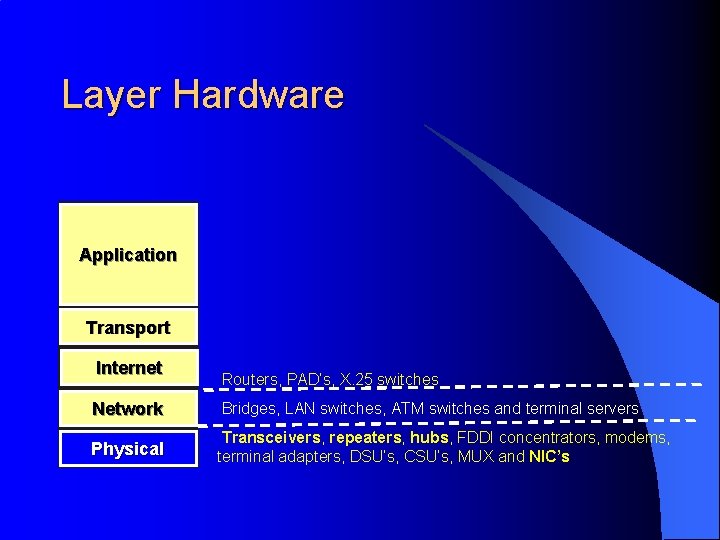
Layer Hardware Application Transport Internet Routers, PAD’s, X. 25 switches Network Bridges, LAN switches, ATM switches and terminal servers Physical Transceivers, repeaters, hubs, FDDI concentrators, modems, terminal adapters, DSU’s, CSU’s, MUX and NIC’s

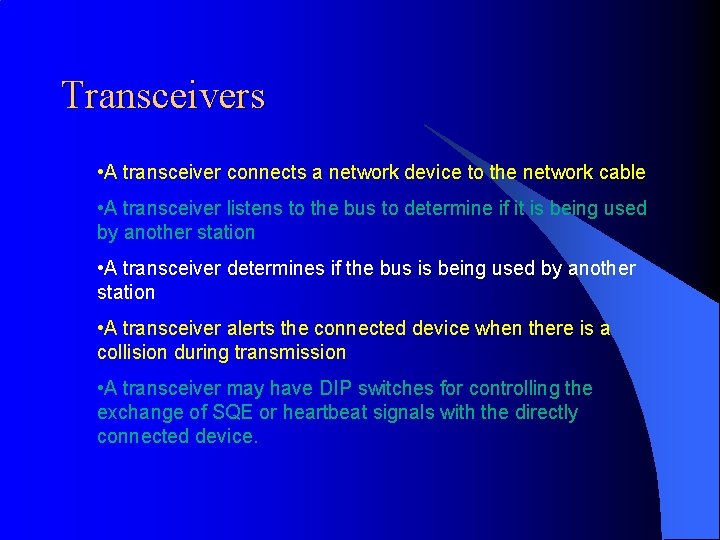
Transceivers • A transceiver connects a network device to the network cable • A transceiver listens to the bus to determine if it is being used by another station • A transceiver determines if the bus is being used by another station • A transceiver alerts the connected device when there is a collision during transmission • A transceiver may have DIP switches for controlling the exchange of SQE or heartbeat signals with the directly connected device.

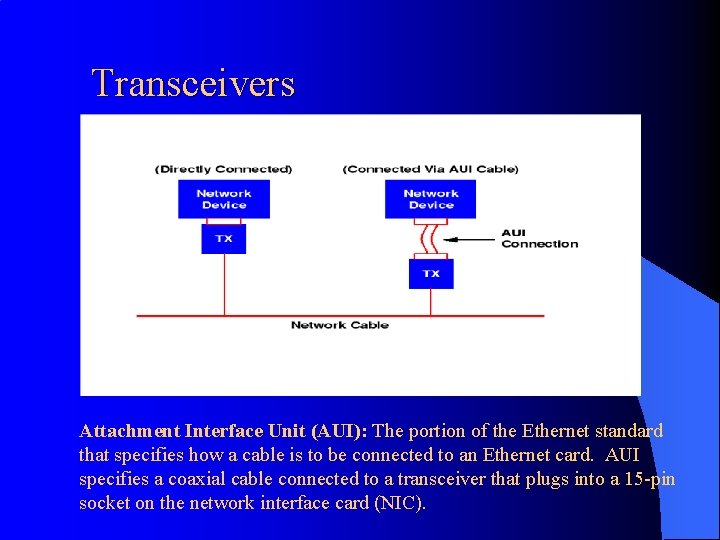
Transceivers Attachment Interface Unit (AUI): The portion of the Ethernet standard that specifies how a cable is to be connected to an Ethernet card. AUI specifies a coaxial cable connected to a transceiver that plugs into a 15 -pin socket on the network interface card (NIC).

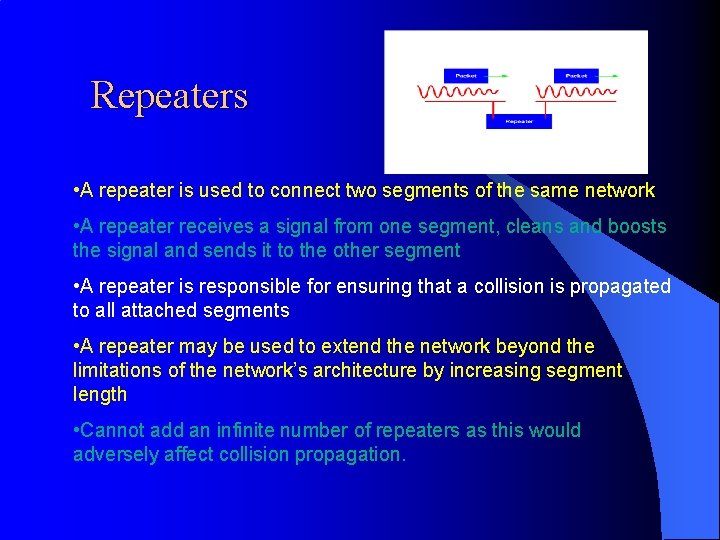
Repeaters • A repeater is used to connect two segments of the same network • A repeater receives a signal from one segment, cleans and boosts the signal and sends it to the other segment • A repeater is responsible for ensuring that a collision is propagated to all attached segments • A repeater may be used to extend the network beyond the limitations of the network’s architecture by increasing segment length • Cannot add an infinite number of repeaters as this would adversely affect collision propagation.

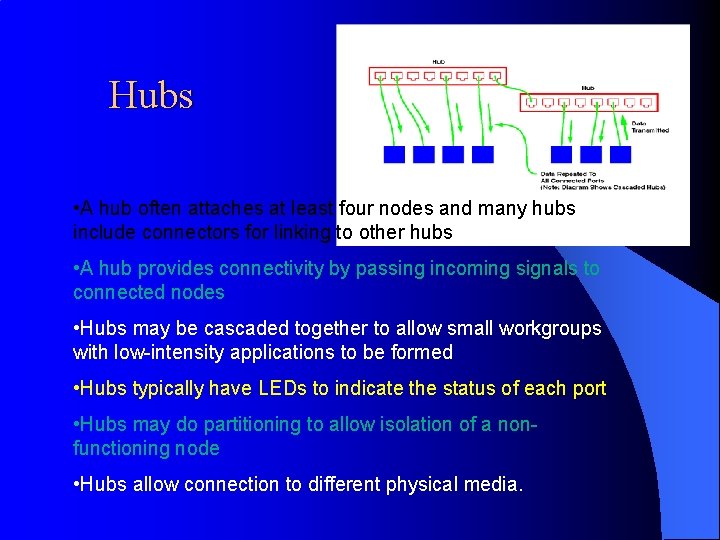
Hubs • A hub often attaches at least four nodes and many hubs include connectors for linking to other hubs • A hub provides connectivity by passing incoming signals to connected nodes • Hubs may be cascaded together to allow small workgroups with low-intensity applications to be formed • Hubs typically have LEDs to indicate the status of each port • Hubs may do partitioning to allow isolation of a nonfunctioning node • Hubs allow connection to different physical media.

NIC’s • A NIC is an internetworking device that is a component part of a much larger host • NICs are used to connect the systems to the network • NICs will be different for each type of host system and type of network topology (and for each bus type) • Remote access is achieved through remote access to the host system • When installing a NIC it is important to consider the network topology, cabling and electrical considerations to avoid network disruption.

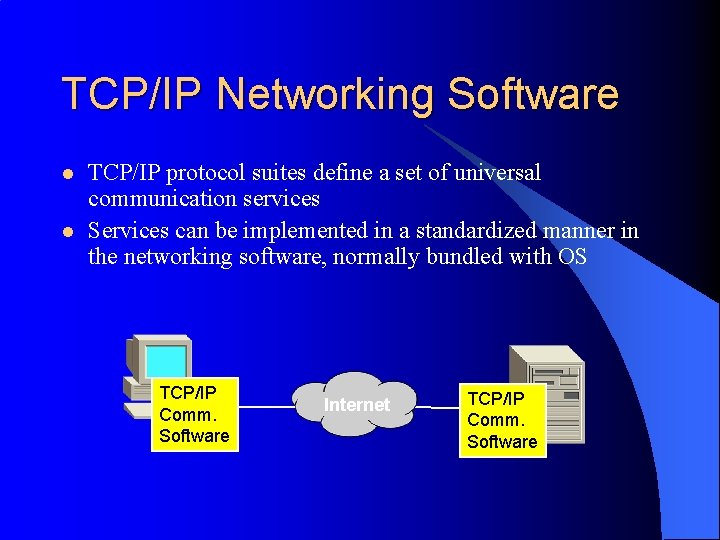
TCP/IP Networking Software l l TCP/IP protocol suites define a set of universal communication services Services can be implemented in a standardized manner in the networking software, normally bundled with OS TCP/IP Comm. Software Internet TCP/IP Comm. Software

TCP/IP and Internet l 1957 USSR sputnik, USA established ARPA l 1969 ARPA funded ARPANET l 1971 Network with 15 nodes l 1974 Cerf/Kahn Protocol l 1973 Ethernet (Ph. D Dissertation Bob Metcalfe) l 1982/83 l 1983 TCP/IP as a core protocol 4. 2 BSD Unix with TCP/IP from UCB (univ. of California @ Berkley)

TCP/IP Standards

Internet Technical Bodies l. ISOC - Internet Society. Professional society to promote the use of Internet for research and scholar communication and collaboration l. IAB - Internet Architecture Board. Technical oversight and coordination, falls under ISOC l. IETF - Internet Engineering Task force. Current protocols and specifications for standardization. Meets 3 times a year, organized in working groups l. IRTF - Internet Research Task force. Research oriented for future.

Internet Administrations l. DDN - the USA Defense Data Network is the government organization that has overall responsibilty for administrating the Internet l. DDN NIC (Network Information Center) nassigns unique names and addresses ncollects and distributes information about TCP/IP protocols l. IANA Internet Assigned Numbers Authority nassigns value for network parameters, name of services, identifiers l. NOC (Network Operations Center) nmanages communication links

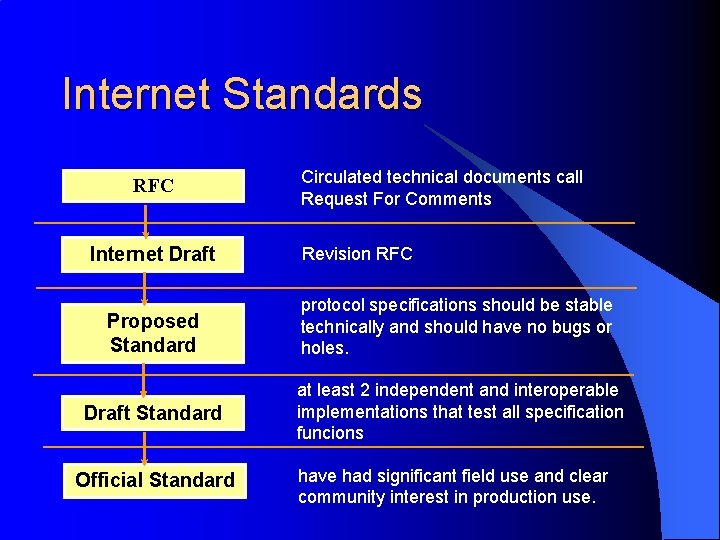
Internet Standards RFC Internet Draft Circulated technical documents call Request For Comments Revision RFC Proposed Standard protocol specifications should be stable technically and should have no bugs or holes. Draft Standard at least 2 independent and interoperable implementations that test all specification funcions Official Standard have had significant field use and clear community interest in production use.

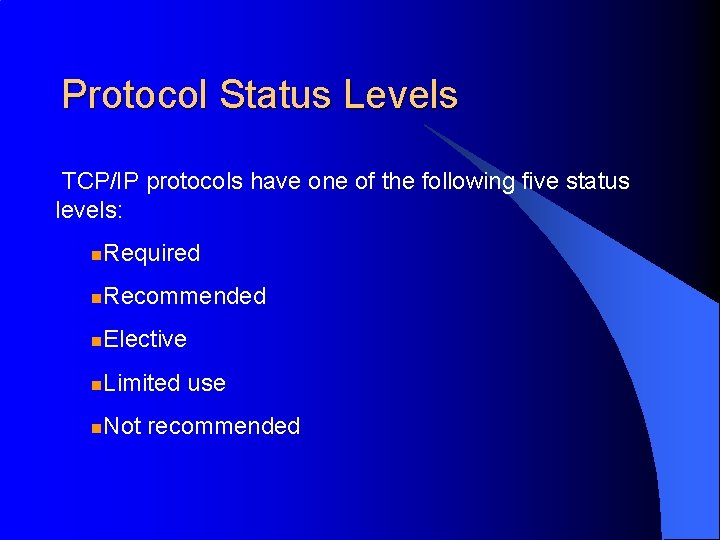
Protocol Status Levels TCP/IP protocols have one of the following five status levels: n. Required n. Recommended n. Elective n. Limited n. Not use recommended

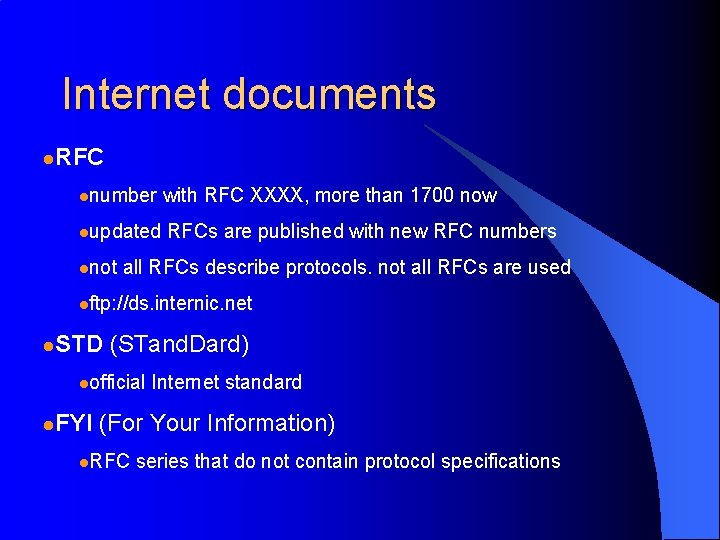
Internet documents l. RFC lnumber lupdated lnot with RFC XXXX, more than 1700 now RFCs are published with new RFC numbers all RFCs describe protocols. not all RFCs are used lftp: //ds. internic. net l. STD (STand. Dard) lofficial l. FYI Internet standard (For Your Information) l. RFC series that do not contain protocol specifications

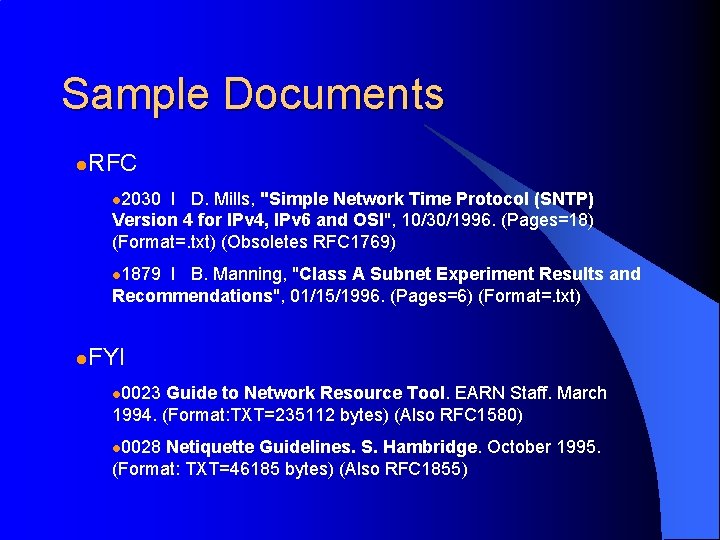
Sample Documents l. RFC l 2030 I D. Mills, "Simple Network Time Protocol (SNTP) Version 4 for IPv 4, IPv 6 and OSI", 10/30/1996. (Pages=18) (Format=. txt) (Obsoletes RFC 1769) l 1879 I B. Manning, "Class A Subnet Experiment Results and Recommendations", 01/15/1996. (Pages=6) (Format=. txt) l. FYI l 0023 Guide to Network Resource Tool. EARN Staff. March 1994. (Format: TXT=235112 bytes) (Also RFC 1580) l 0028 Netiquette Guidelines. S. Hambridge. October 1995. (Format: TXT=46185 bytes) (Also RFC 1855)

Wireless LANs

Wireless LANs • Why RF? • IEEE 802. 11 activities • RF Technologies - 2. 4 GHz/5 GHz • Wireless LAN Topology Basics • Customers WLAN requirements • Building-to-Building Bridges

IEEE 802. 11

IEEE 802. 11 The IEEE 802. 11 standard defines the protocol for two types of networks; Ad-hoc and client/server networks. An Ad-hoc network is a simple network where communications are established between multiple stations in a given coverage area without the use of an access point or server. The standard specifies the etiquette that each station must observe so that they all have fair access to the wireless media. It provides methods for arbitrating requests to use the media to ensure that throughput is maximized for all of the users in the base service set.

IEEE 802. 11 The IEEE 802 standards committee formed the 802. 11 Wireless Local Area Networks Standards Working Group in 1990. The 802. 11 -working group took on the task of developing a global standard for radio equipment and networks operating in the 2. 4 GHz unlicensed frequency band for data rates of 1 and 2 Mbps. The standard does not specify technology or implementation but simply specifications for the physical layer and Media Access Control (MAC) layer. The standard allows for manufacturers of wireless LAN radio equipment to build interoperable network equipment.

IEEE 802. 11 The membership of the committee consists of individuals from a number of companies and universities, who research, manufacture, install and use products in wireless LAN network applications. Manufacturers of semiconductors, computers, radio equipment, WLAN systems solution providers, University research labs and end-users make up the core group. Companies globally represent the working group from the United States, Canada, Europe, Israel and the Pacific Rim.

IEEE 802. 11 Standard Activities • 802. 11 a - 5 GHz- Ratified in 1999 • 802. 11 b - 11 Mb 2. 4 GHz- ratified in 1999 • 802. 11 d - Additional regulatory domains • 802. 11 e - Quality of Service • 802. 11 f - Inter-Access Point Protocol (IAPP) • 802. 11 g - Higher Datarate (>20 m. Bps) 2. 4 GHz • 802. 11 h - Dynamic Frequency Selection and Transmit Power Control mechanisms • 802. 11 i - Authentication and security

IEEE 802. 11 Physical Layer Implementation Choices The Physical Layer in any network defines the modulation and signaling characteristics for the transmission of data. At the physical layer, two RF transmission methods and one infrared are defined. Operation of the WLAN in unlicensed RF bands requires the of spread spectrum modulation to meet the requirements for operation in most countries. The RF transmission techniques in the standard are Frequency Hopping (FH) and Direct Sequence (DS) spread spectrum.

IEEE 802. 11 Both architectures are defined for operation in the 2. 4 GHz (ISM) frequency band. Each occupies 83 Mhz of bandwidth ranging from 2. 400 GHz to 2. 483 GHz. Differential BPSK (DBPSK) and DQPSK is the modulation for the direct sequence. Frequency hopping uses 2 -4 level Gaussian FSK as the modulation signaling method. The radiated RF power at the antenna is set by the rules governed by FCC part 15 for operation in the United States. Antenna gain is also limited to 6 d. Bi maximum.

Range of a Radio Link • The range of a RF radio link can be calculated by using the following items: Transmitter power Receiver sensitivity (at a given data rate) Path loss in free space (increases as Frequency increases) Antenna system gain (includes cable losses)

IEEE 802. 11 Operating Frequency Ranges Lower Limit 2. 402 GHz 2. 473 GHz 2. 447 GHz 2. 448 GHz Upper Limit 2. 480 GHz 2. 495 GHz 2. 473 GHz 2. 482 GHz Regulatory Range 2. 400 -2. 4835 GHz 2. 471 -2. 497 GHz 2. 445 -2. 475 GHz 2. 4465 -2. 4835 GHz Geography North America* Europe* Japan* Spain* France* The radiated power is limited to 1 W for the United States, 10 m. W per 1 Mhz in Europe and 10 m. W for Japan. There are different frequencies approved for use in Japan, United States and Europe and any WLAN product must meet the requirements for the country in which it is sold.

IEEE 802. 11 The MAC Layer The MAC layer specification for 802. 11 has similarities to the 802. 3 Ethernet wired line standard. The protocol for 802. 11 uses a protocol scheme know as carrier-sense, multiple access, collision avoidance (CSMA/CA). This protocol avoids collisions instead of detecting a collision like the algorithm used in 802. 3. It is difficult to detect collisions in a RF transmission network and it is for this reason that collision avoidance is used. The MAC layer operates together with the physical layer by sampling the energy over the medium transmitting data.

IEEE 802. 11 The physical layer uses a clear channel assessment (CCA) algorithm to determine if the channel is clear. This is accomplished by measuring the RF energy at the antenna and determining the strength of the received signal. This measured signal is commonly known as RSSI. If the received signal strength is below a specified threshold the channel is declared clear and the MAC layer is given the clear channel status for data transmission. If the RF energy is above threshold, data transmissions are deferred in accordance with the protocol rules. The standard provides another option for CCA that can be alone or with the RSSI measurement. Carrier sense can be used to determine if the channel is available.

IEEE 802. 11

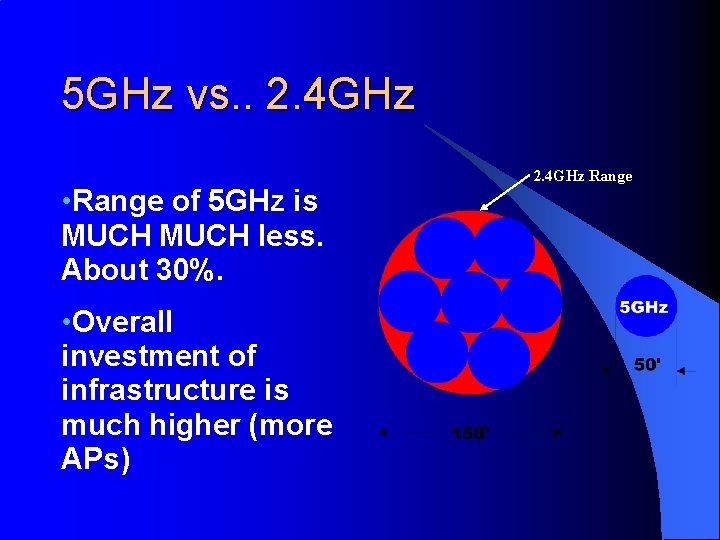
Comparing Radio specs 5 Ghz vs. 2. 4 GHz 2. 4 Ghz (Cisco 350) 5 Ghz (802. 11 a) TX Power 20 d. Bm (11 Mbps) 12 d. Bm (6 Mbps) RX Sens. -85 d. Bm (11 Mbps) -79 d. Bm (6 Mbps) (100 m. W) (16 m. W) Results= 14 d. Bm less for 5 Ghz than 2. 4 @similar rates. 14 d. B less > 50% range reduction

5 GHz vs. . 2. 4 GHz Range • Range of 5 GHz is MUCH less. About 30%. • Overall investment of infrastructure is much higher (more APs) 4 5 1 2 7 3 6

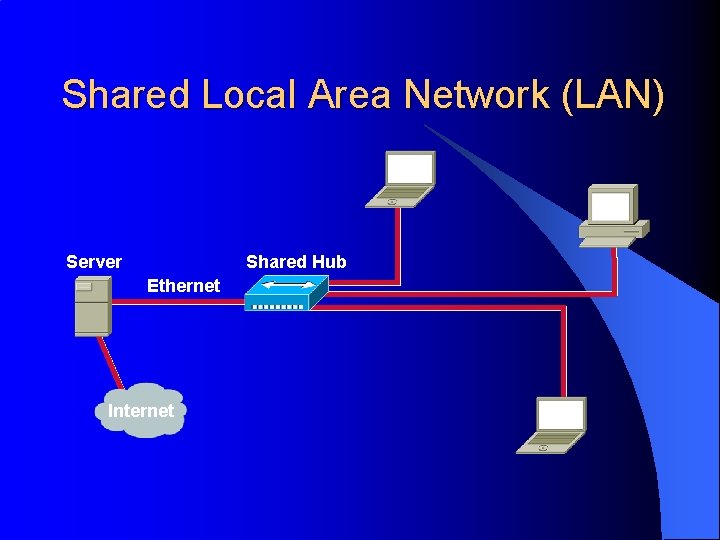
Shared Local Area Network (LAN) Server Shared Hub Ethernet Internet

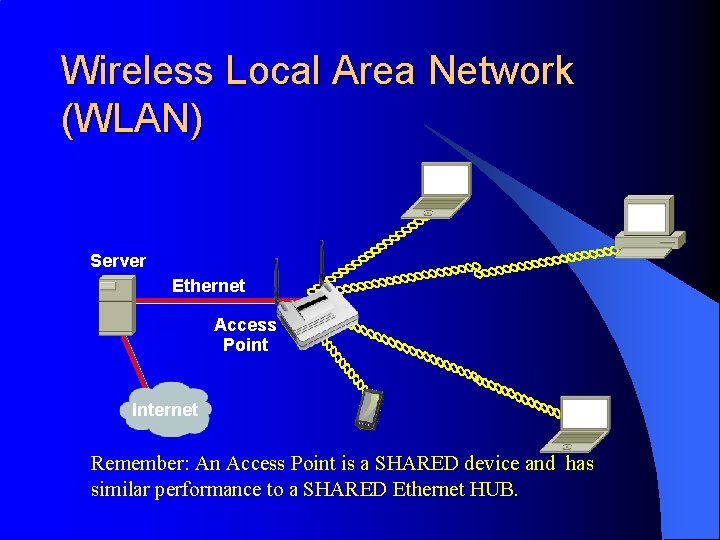
Wireless Local Area Network (WLAN) Server Ethernet Access Point Internet Remember: An Access Point is a SHARED device and has similar performance to a SHARED Ethernet HUB.

Typical Single Cell Configuration Wireless Cell LAN Backbone Wireless Clients

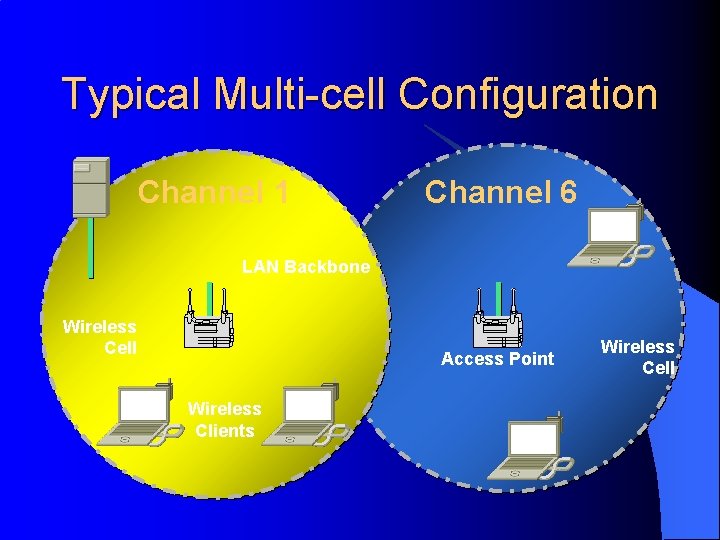
Typical Multi-cell Configuration Channel 1 Channel 6 LAN Backbone Wireless Cell Access Point Wireless Clients Wireless Cell

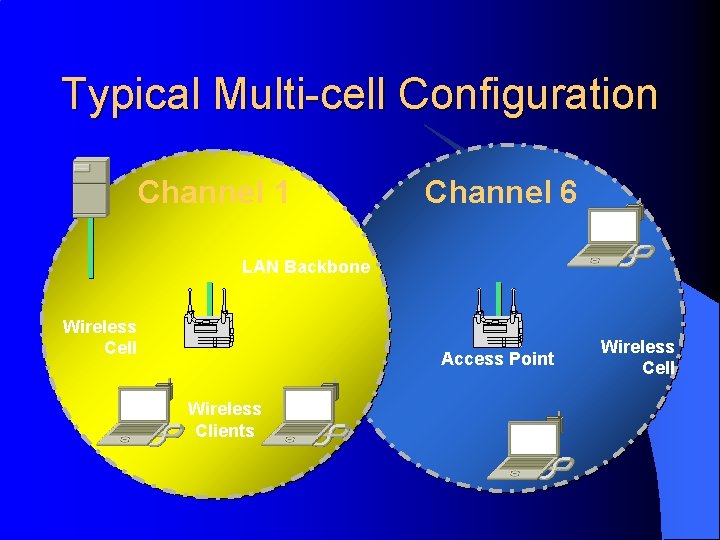
Typical Multi-cell Configuration Channel 1 Channel 6 LAN Backbone Wireless Cell Access Point Wireless Clients Wireless Cell

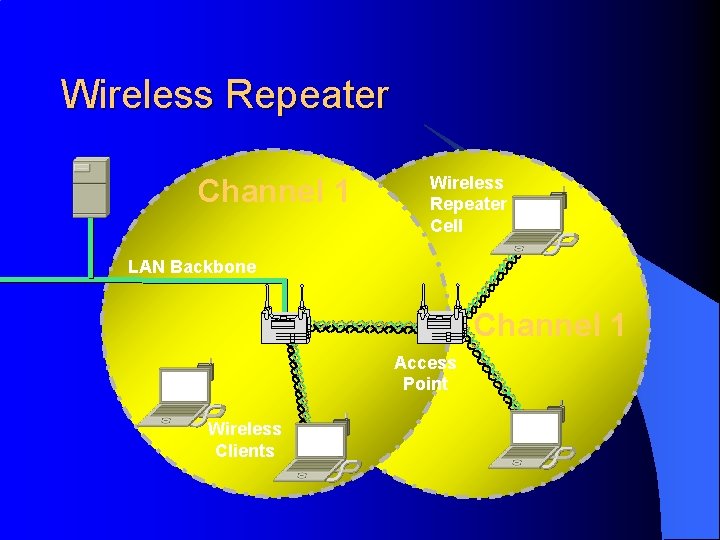
Wireless Repeater Channel 1 Wireless Repeater Cell LAN Backbone Channel 1 Access Point Wireless Clients

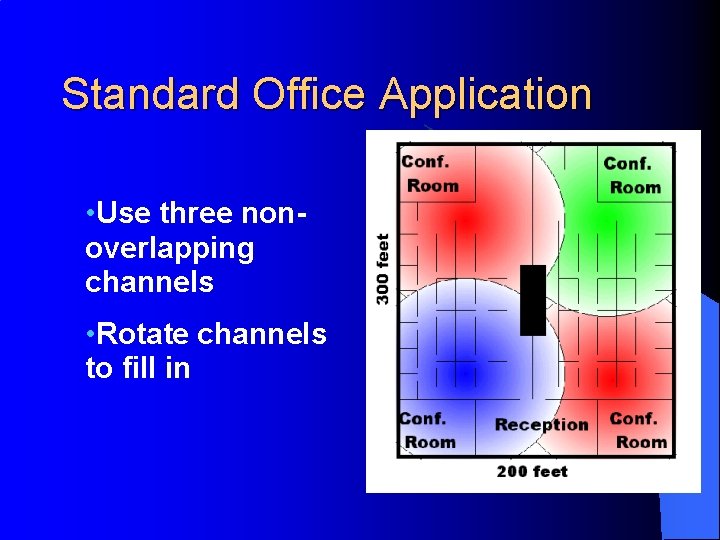
Standard Office Application • Use three nonoverlapping channels • Rotate channels to fill in

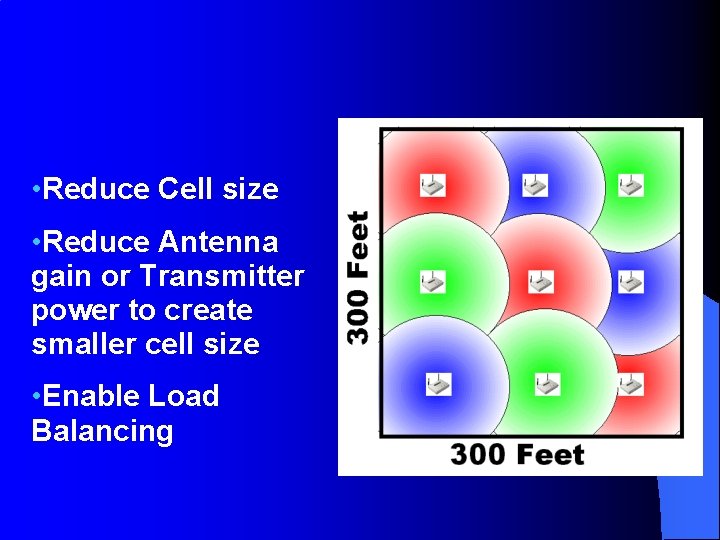
• Reduce Cell size • Reduce Antenna gain or Transmitter power to create smaller cell size • Enable Load Balancing

Mixed Antenna Example Maximum Coverage Autorate Negotiation Wireless for Students Di. Pole Indoor, Patch Outdoor Channel 11 Channel 6 Class 2 Class 3 850’ Class 1 Class 4 Hallway Class 8 Class 9 Channel 6 Class 10 Class 11 Channel 1 Building Courtyard 1000’

END Class 2