TCPIP Example IP Security IPSec l IPSec is
























- Slides: 59


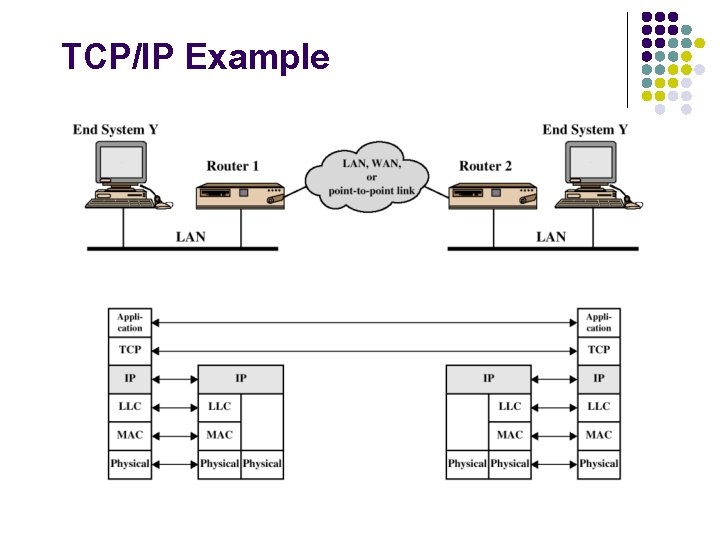
TCP/IP Example


IP Security (IPSec) l IPSec is a framework of open standards developed by the Internet Engineering Task Force (IETF). Creates secure, authenticated, reliable communications over IP networks

IPSec Security Services l l Connectionless integrity Data origin authentication Confidentiality (encryption) Access control

IP Security Mode l l Transport Mode Tunnel Mode

Transport Mode Encrypted Tunnel A Encrypted B

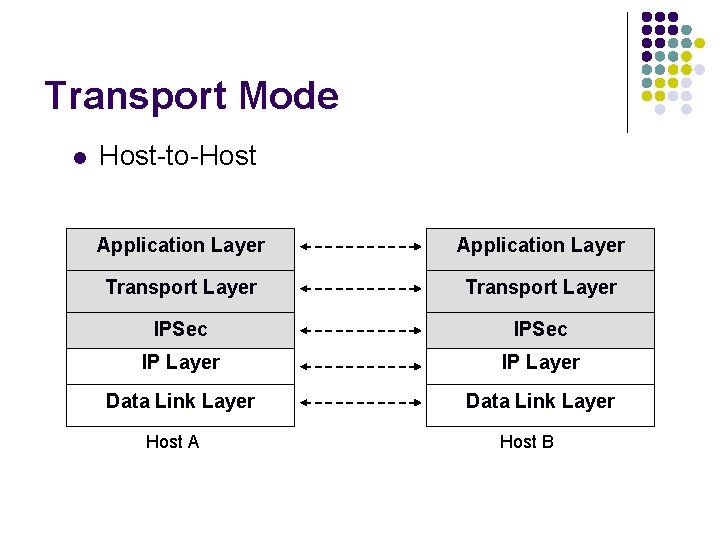
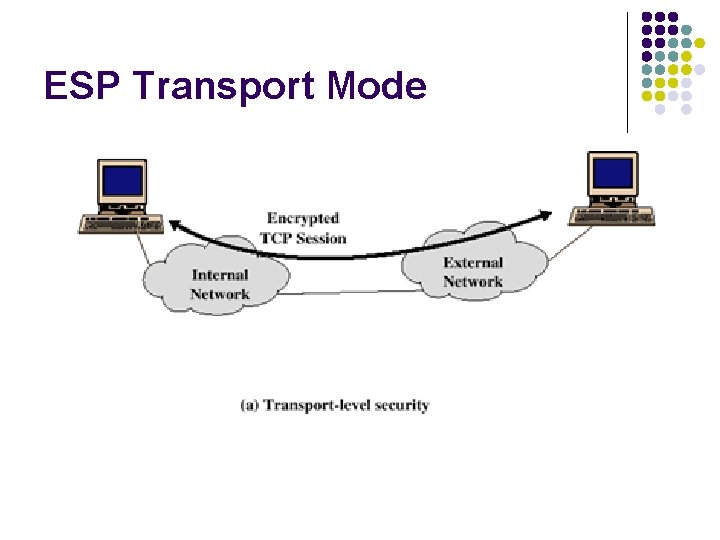
Transport Mode l Host-to-Host Application Layer Transport Layer IPSec IP Layer Data Link Layer Host A Host B

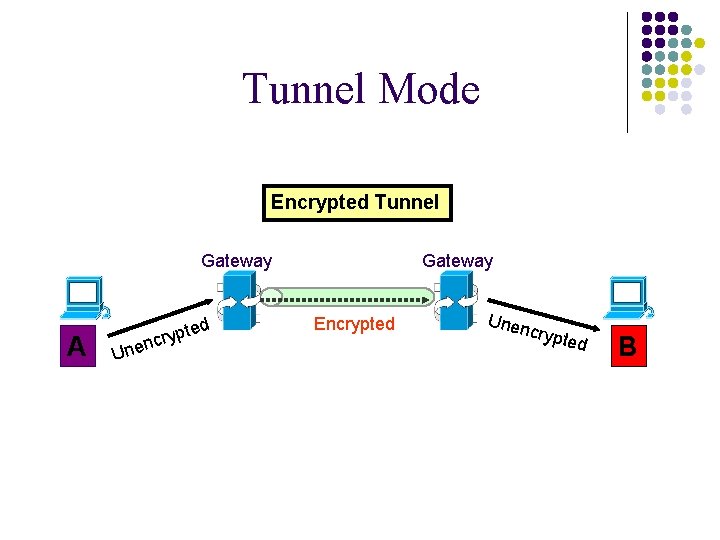
Tunnel Mode Encrypted Tunnel Gateway A n Une ted cryp Gateway Encrypted Unen crypt ed B

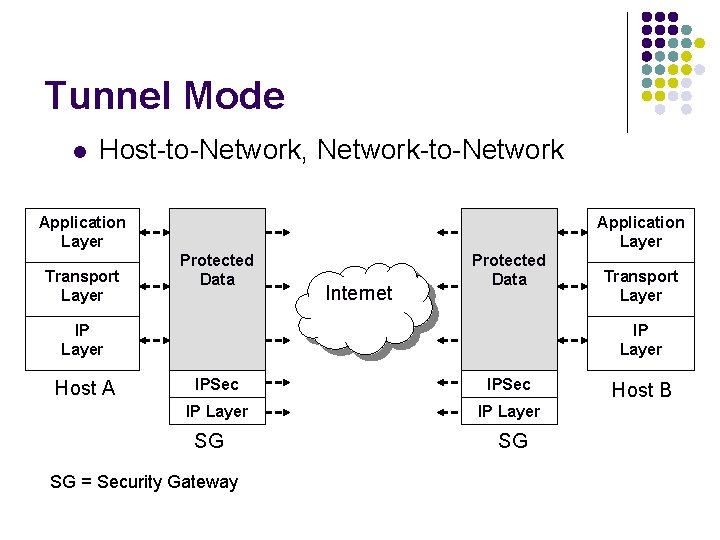
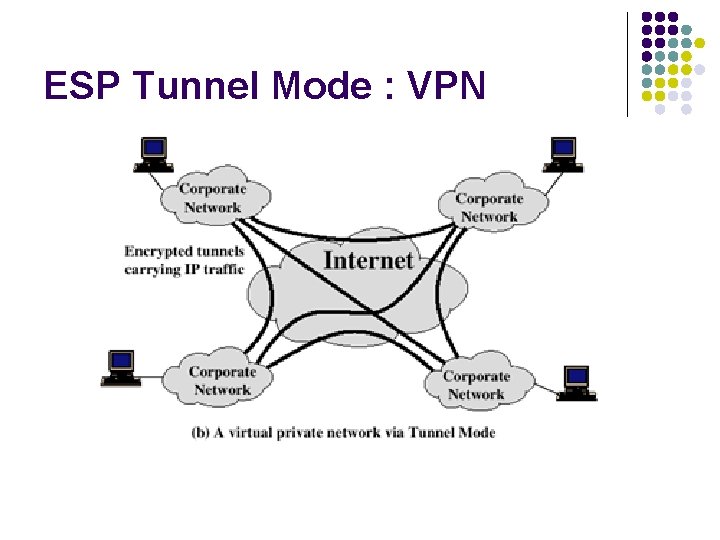
Tunnel Mode l Host-to-Network, Network-to-Network Application Layer Transport Layer Application Layer Protected Data Internet Protected Data IP Layer Host A Transport Layer IPSec IP Layer SG SG = Security Gateway SG Host B

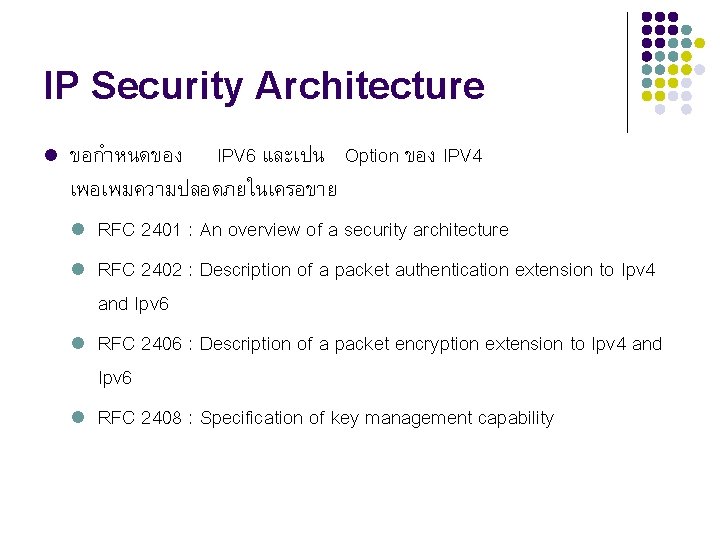
IP Security Architecture l ขอกำหนดของ IPV 6 และเปน Option ของ IPV 4 เพอเพมความปลอดภยในเครอขาย l RFC 2401 : An overview of a security architecture l RFC 2402 : Description of a packet authentication extension to Ipv 4 and Ipv 6 l RFC 2406 : Description of a packet encryption extension to Ipv 4 and Ipv 6 l RFC 2408 : Specification of key management capability


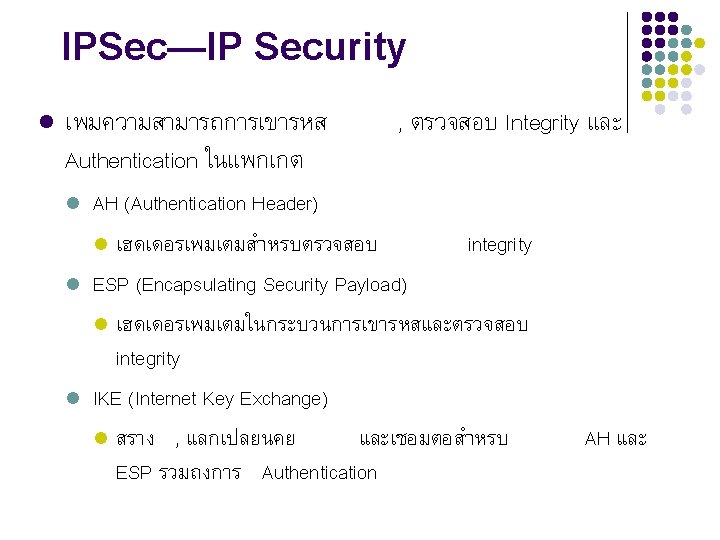
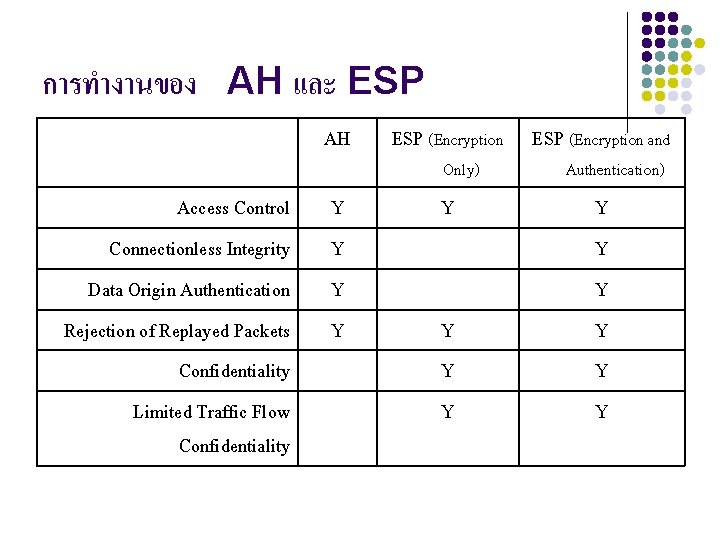
การทำงานของ AH และ ESP Access Control Connectionless Integrity Data Origin Authentication Rejection of Replayed Packets Confidentiality Limited Traffic Flow Confidentiality AH ESP (Encryption and Y Y Y Only) Y Y Y Authentication)

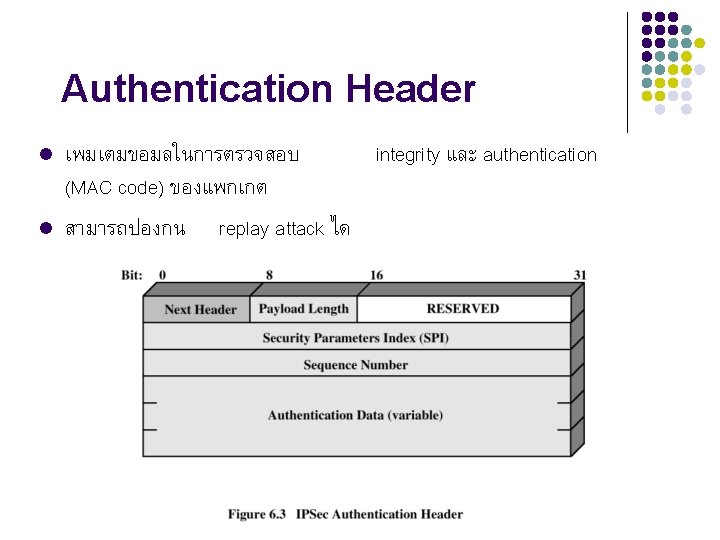
Authentication Header


Normal Packet

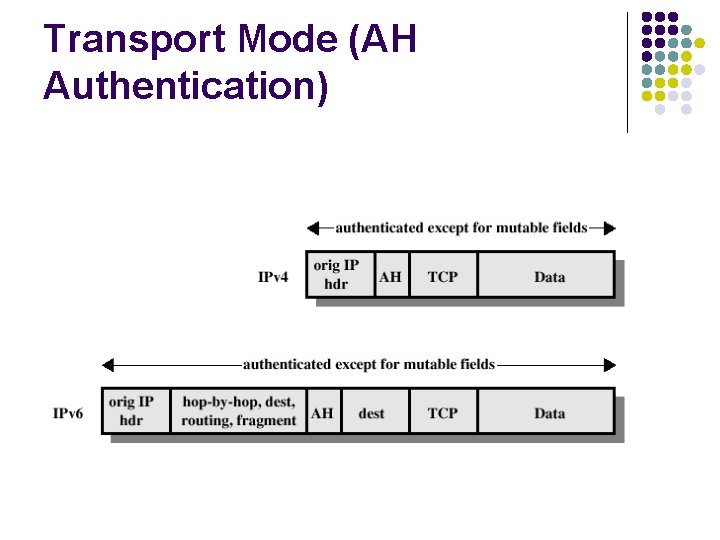
Transport Mode (AH Authentication)

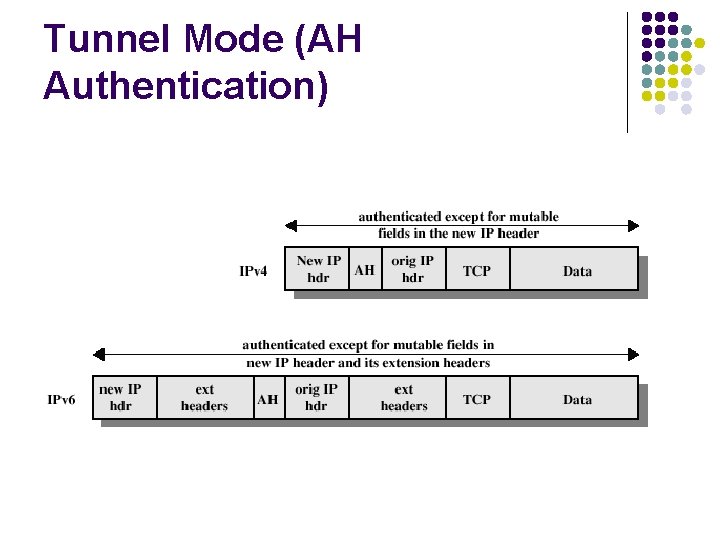
Tunnel Mode (AH Authentication)

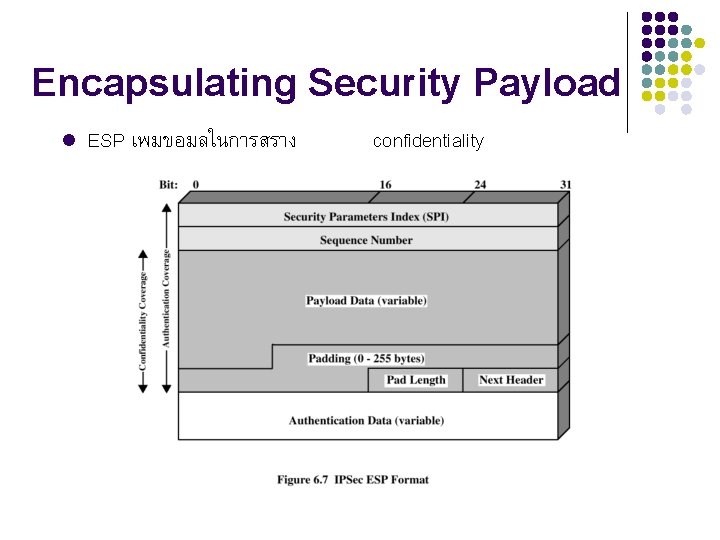
Encapsulating Security Payload

Encapsulating Security Payload l ESP เพมขอมลในการสราง confidentiality

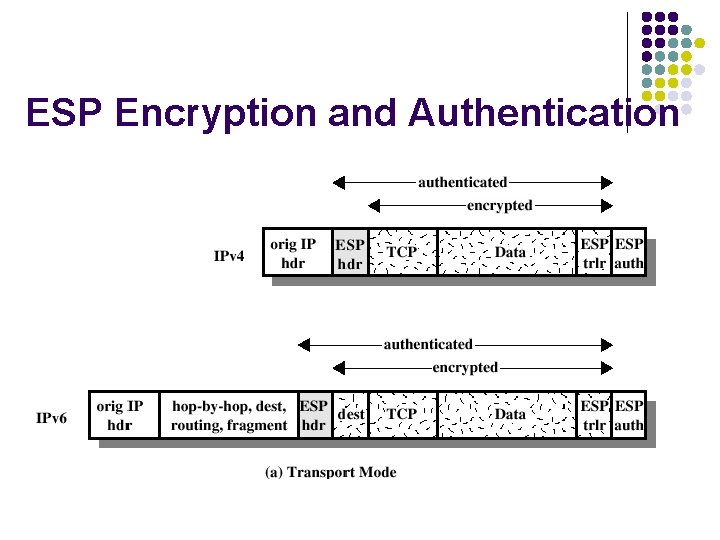
ESP Encryption and Authentication

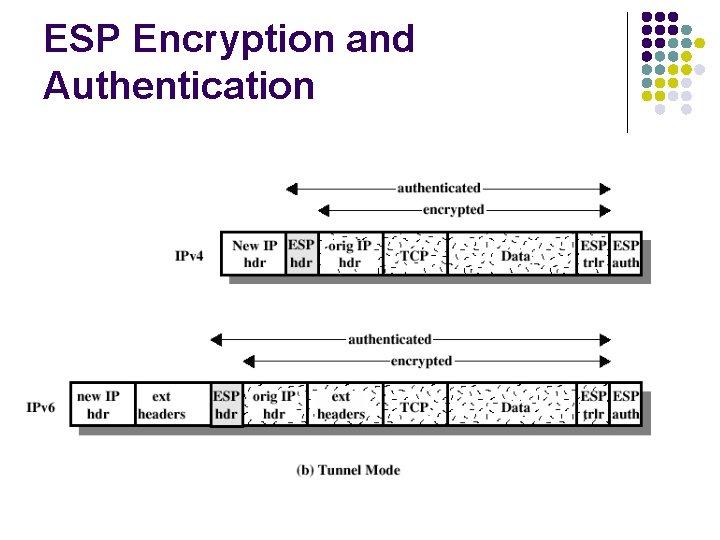
ESP Encryption and Authentication

Encryption and Authentication Algorithms l Encryption: l l l l Three-key triple DES RC 5 IDEA Three-key triple IDEA CAST Blowfish Authentication: l l HMAC-MD 5 -96 HMAC-SHA-1 -96

ESP Transport Mode

ESP Tunnel Mode : VPN


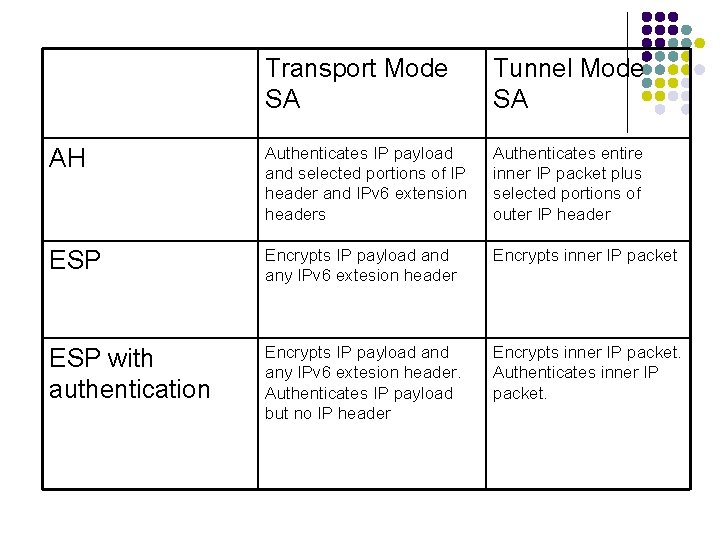
Transport Mode SA Tunnel Mode SA AH Authenticates IP payload and selected portions of IP header and IPv 6 extension headers Authenticates entire inner IP packet plus selected portions of outer IP header ESP Encrypts IP payload any IPv 6 extesion header Encrypts inner IP packet ESP with authentication Encrypts IP payload any IPv 6 extesion header. Authenticates IP payload but no IP header Encrypts inner IP packet. Authenticates inner IP packet.

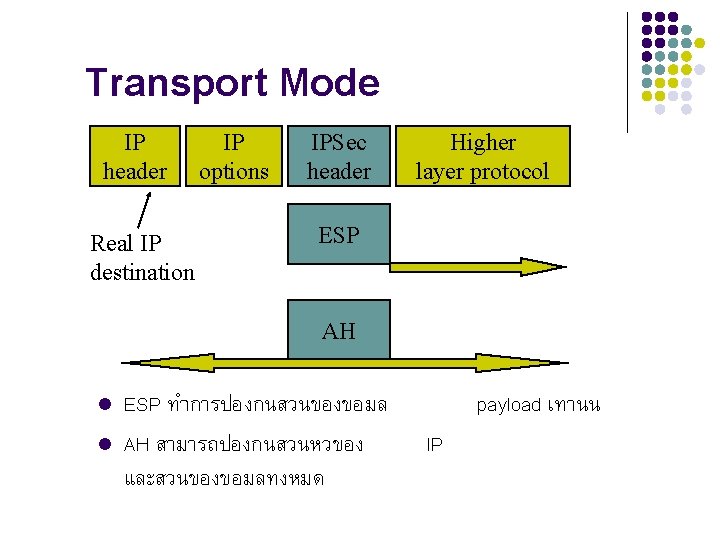
Transport Mode IP header Real IP destination IP options IPSec header Higher layer protocol ESP AH l l ESP ทำการปองกนสวนของขอมล AH สามารถปองกนสวนหวของ และสวนของขอมลทงหมด payload เทานน IP

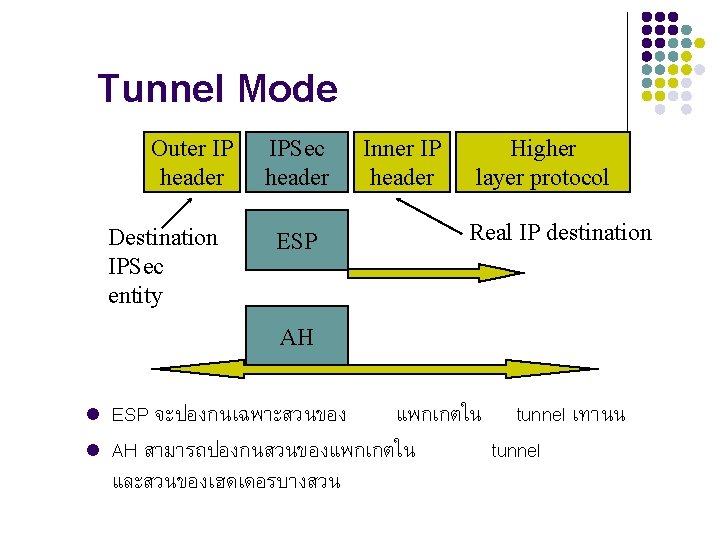
Tunnel Mode Outer IP header Destination IPSec entity IPSec header ESP Inner IP header Higher layer protocol Real IP destination AH l l ESP จะปองกนเฉพาะสวนของ แพกเกตใน tunnel เทานน AH สามารถปองกนสวนของแพกเกตใน tunnel และสวนของเฮดเดอรบางสวน

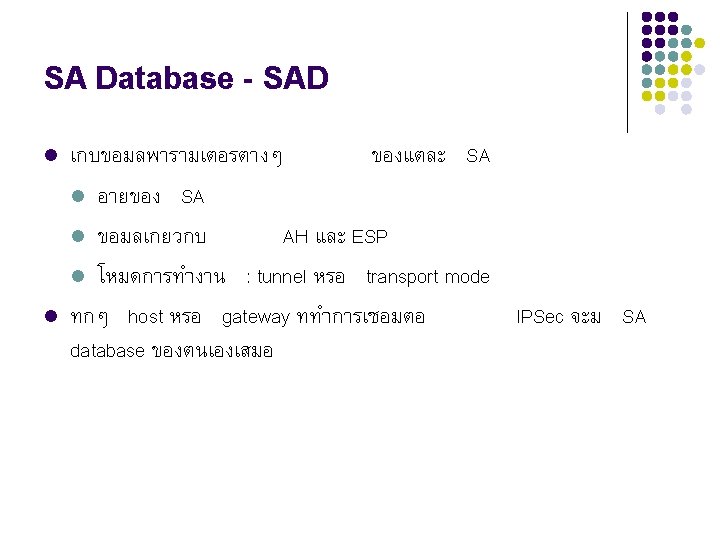
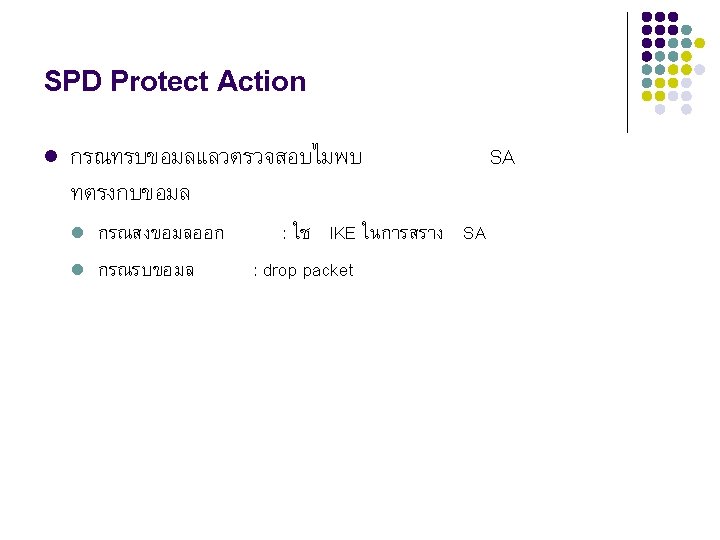
องคประกอบของ IP Security Process l l l Security Association (SA) Security Association Database (SAD) Security Policy Database (SPD)

Outbound/Inbound IPSec Processing l The inbound and the outbound IPSec processing are completely independent. Packet

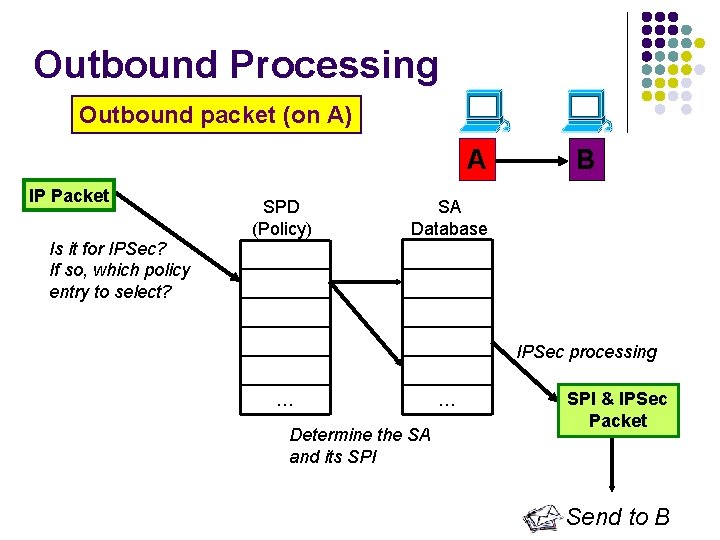
Outbound Processing Outbound packet (on A) A IP Packet Is it for IPSec? If so, which policy entry to select? SPD (Policy) B SA Database IPSec processing … Determine the SA and its SPI … SPI & IPSec Packet Send to B

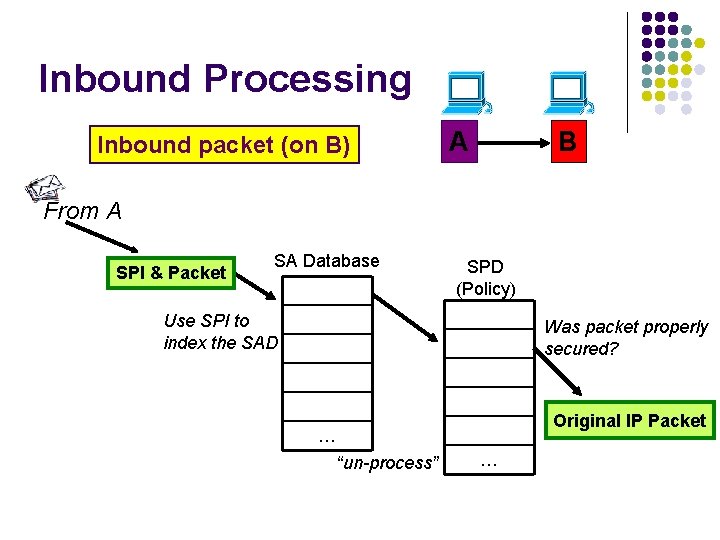
Inbound Processing Inbound packet (on B) A B From A SPI & Packet SA Database SPD (Policy) Use SPI to index the SAD Was packet properly secured? Original IP Packet … “un-process” …

Security Association Method



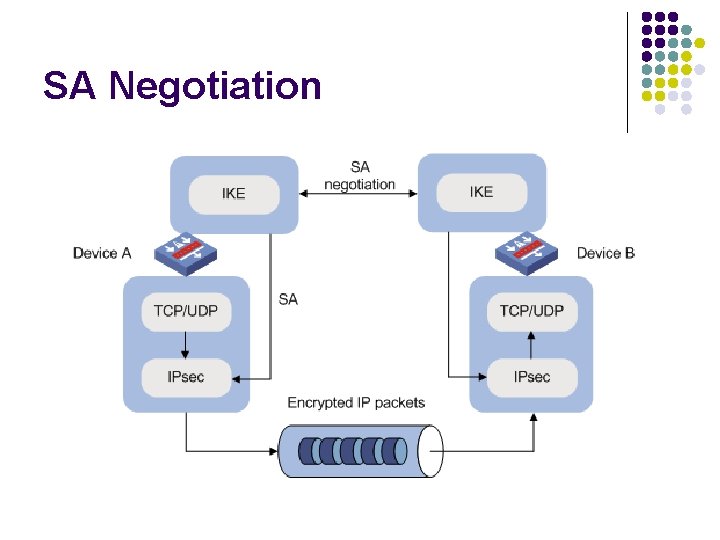
SA Negotiation

IKE l l IKE is an application layer protocol using UDP and functions as the signaling protocol of IPsec. IKE negotiates SAs for IPsec and delivers negotiated parameters and generated keys to IPsec uses the SAs set up through IKE negotiation for encryption and/or authentication of IP packets. IKE related protocols include: l l l RFC 2408: Internet Security Association and Key Management Protocol (ISAKMP) RFC 2409: The Internet Key Exchange (IKE) RFC 2412: The OAKLEY Key Determination Protocol









Combination of Security Association




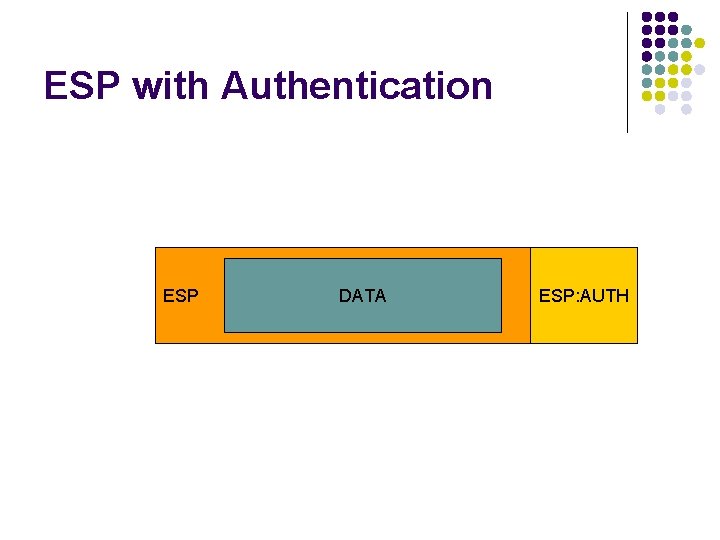
ESP with Authentication ESP DATA ESP: AUTH

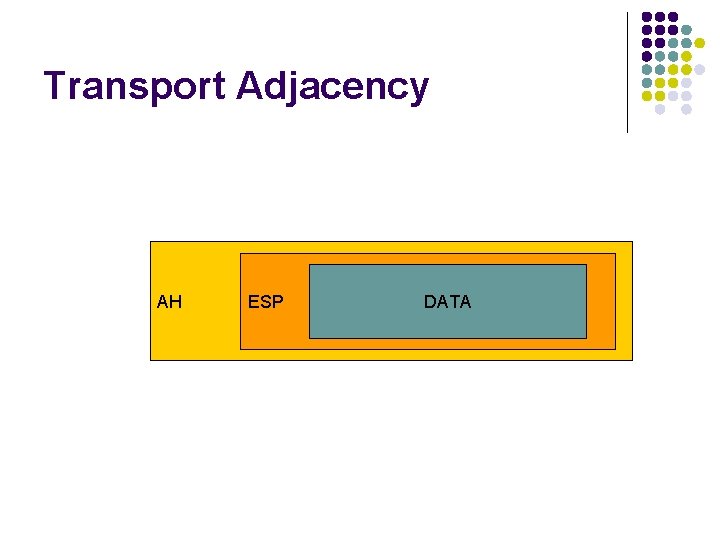
Transport Adjacency AH ESP DATA

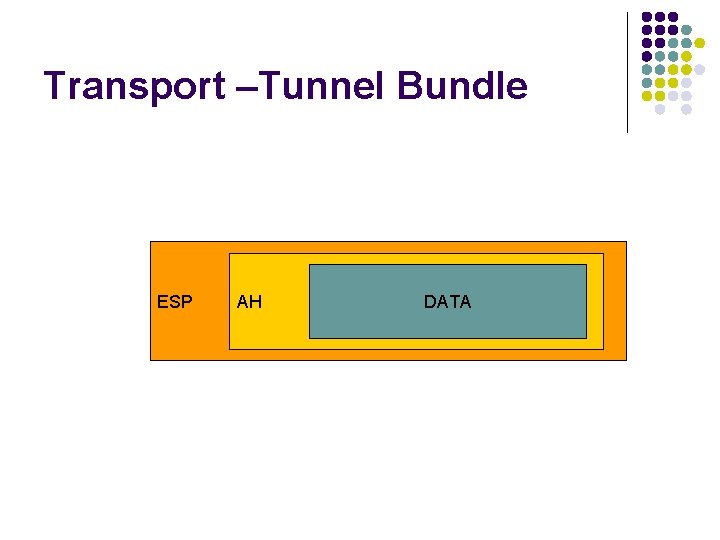
Transport –Tunnel Bundle ESP AH DATA


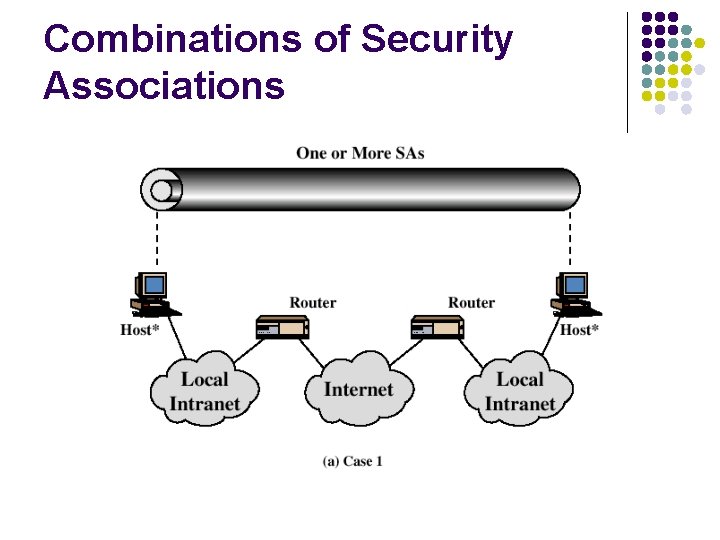
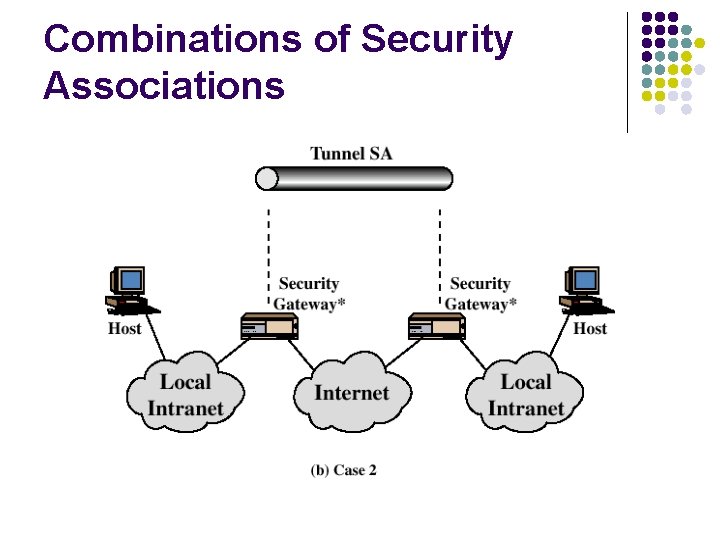
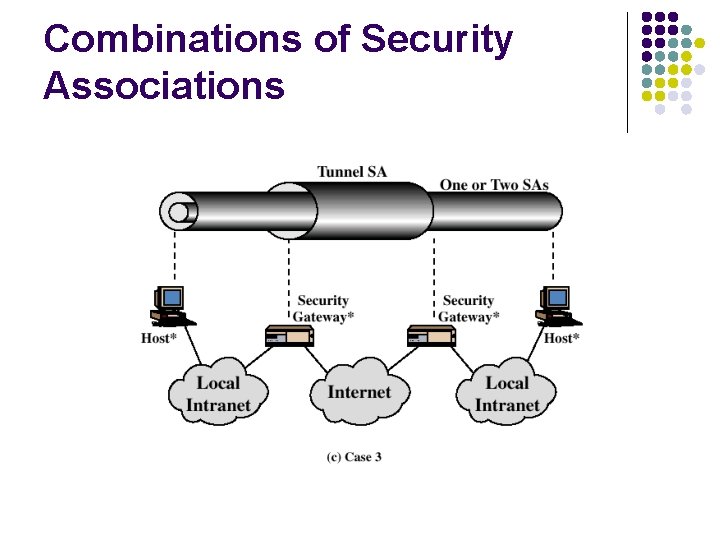
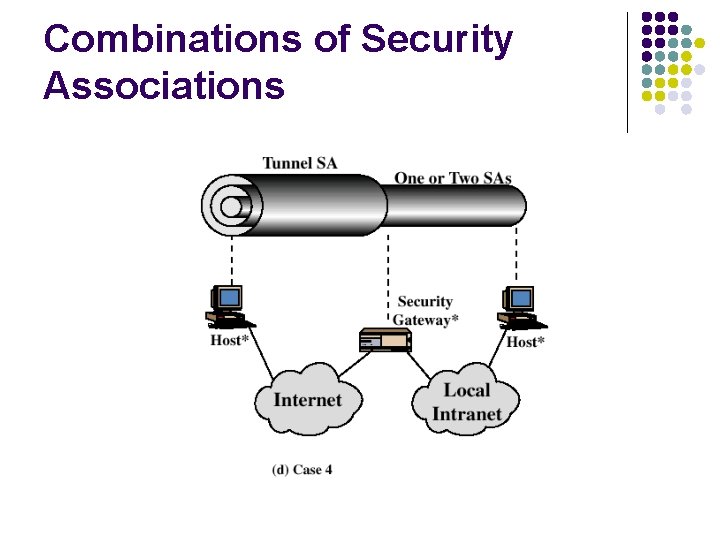
Combinations of Security Associations

Combinations of Security Associations

Combinations of Security Associations

Combinations of Security Associations
