Network Security IPsec Tuomas Aura T110 5241 Network


![IPsec architecture [RFC 4301] Node A Session Key IKE(v 2) PAD SPD Security Policy IPsec architecture [RFC 4301] Node A Session Key IKE(v 2) PAD SPD Security Policy](https://slidetodoc.com/presentation_image_h/2f9bed0328fb125e3114ec987e429031/image-4.jpg)
![Internet Key Exchange (IKE) IKE(v 1) [RFC 2407, 2408, 2409] Framework for authenticated key-exchange Internet Key Exchange (IKE) IKE(v 1) [RFC 2407, 2408, 2409] Framework for authenticated key-exchange](https://slidetodoc.com/presentation_image_h/2f9bed0328fb125e3114ec987e429031/image-5.jpg)


![Session protocol § Encapsulated Security Payload (ESP) [RFC 4303] § Encryption and/or MAC for Session protocol § Encapsulated Security Payload (ESP) [RFC 4303] § Encryption and/or MAC for](https://slidetodoc.com/presentation_image_h/2f9bed0328fb125e3114ec987e429031/image-10.jpg)

![Peer authorization database (PAD) IPsec spec [RFC 4301] defines a database that maps authenticated Peer authorization database (PAD) IPsec spec [RFC 4301] defines a database that maps authenticated](https://slidetodoc.com/presentation_image_h/2f9bed0328fb125e3114ec987e429031/image-26.jpg)



- Slides: 29

Network Security: IPsec Tuomas Aura T-110. 5241 Network security Aalto University, Nov-Dec 2011

IPsec: Architecture and protocols 2

Internet protocol security (IPsec) Network-layer security protocol Protects IP packets between two hosts or gateways Transparent to transport layer and applications IP addresses used to as host identifiers Two steps: 1. IKE creates security associations 2. ESP session protocol protects data Specified by Internet Engineering Task Force (IETF) Original goal: encryption and authentication layer that will replace all others Security was a sales point for IPv 6; now also in IPv 4 3
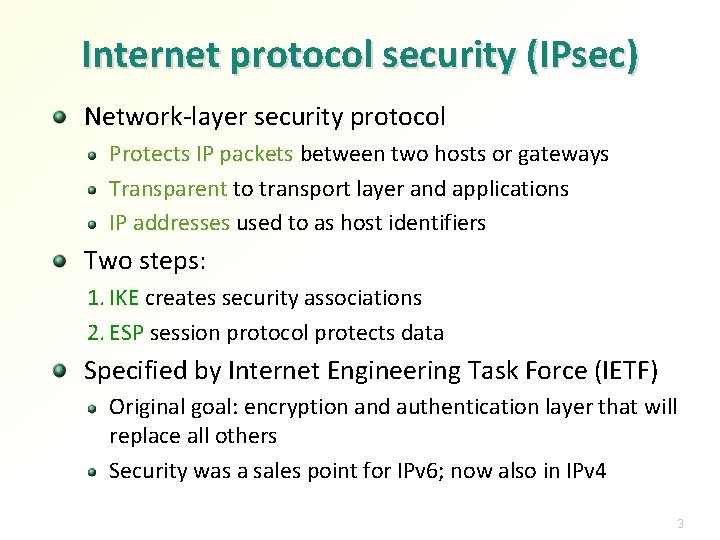
![IPsec architecture RFC 4301 Node A Session Key IKEv 2 PAD SPD Security Policy IPsec architecture [RFC 4301] Node A Session Key IKE(v 2) PAD SPD Security Policy](https://slidetodoc.com/presentation_image_h/2f9bed0328fb125e3114ec987e429031/image-4.jpg)
IPsec architecture [RFC 4301] Node A Session Key IKE(v 2) PAD SPD Security Policy Database IPSec SAD Security Association Database Untrusted network 1. Key exchange Node B Session Key IKE(v 2) PAD IKE SA SPD IPsec SA Pair Security Policy Database 2. ESP protects data IPSec Security Association SAD Database Security associations (SA) created by IKE, used by IPsec ESP Security policy guides SA creation and selection for use IPsec is part of the IP layer in the OS kernel; IKE is a user-space service (daemon) 4
![Internet Key Exchange IKE IKEv 1 RFC 2407 2408 2409 Framework for authenticated keyexchange Internet Key Exchange (IKE) IKE(v 1) [RFC 2407, 2408, 2409] Framework for authenticated key-exchange](https://slidetodoc.com/presentation_image_h/2f9bed0328fb125e3114ec987e429031/image-5.jpg)
Internet Key Exchange (IKE) IKE(v 1) [RFC 2407, 2408, 2409] Framework for authenticated key-exchange protocols, typically with Diffie-Hellman Multiple authentication methods: certificates, pre-shared key, Kerberos Two phases: Main Mode (MM) creates an ISAKMP SA (i. e. IKE SA) and Quick Mode (QM) creates IPsec SAs Main mode (identity-protection mode) and optimized aggressive mode Interoperability problems: too complex to implement and test all modes; specification incomplete IKEv 2 [RFC 4306] Redesign of IKE: fewer modes and messages, simpler to implement Initial exchanges create the IKE SA and the first IPsec SA CREATE_CHILD_SA exchange can create further IPsec SAs EAP authentication for extensions Works over UDP port 500 5

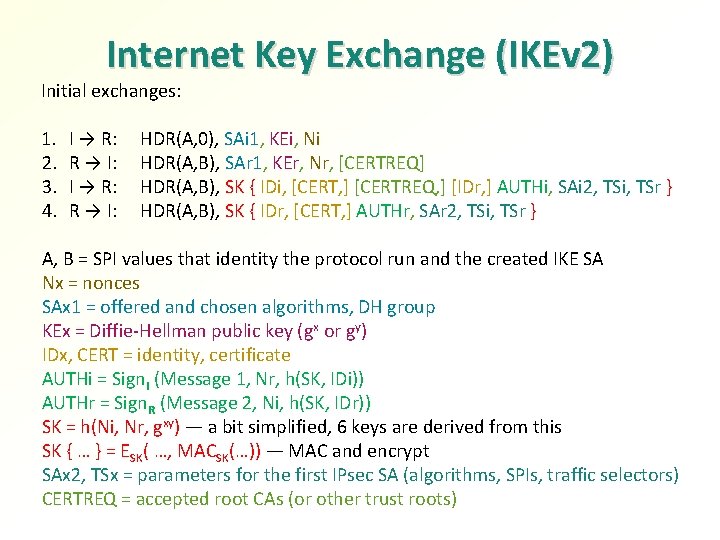
Internet Key Exchange (IKEv 2) Initial exchanges: 1. 2. 3. 4. I → R: R → I: HDR(A, 0), SAi 1, KEi, Ni HDR(A, B), SAr 1, KEr, Nr, [CERTREQ] HDR(A, B), SK { IDi, [CERT, ] [CERTREQ, ] [IDr, ] AUTHi, SAi 2, TSi, TSr } HDR(A, B), SK { IDr, [CERT, ] AUTHr, SAr 2, TSi, TSr } A, B = SPI values that identity the protocol run and the created IKE SA Nx = nonces SAx 1 = offered and chosen algorithms, DH group KEx = Diffie-Hellman public key (gx or gy) IDx, CERT = identity, certificate AUTHi = Sign. I (Message 1, Nr, h(SK, IDi)) AUTHr = Sign. R (Message 2, Ni, h(SK, IDr)) SK = h(Ni, Nr, gxy) — a bit simplified, 6 keys are derived from this SK { … } = ESK( …, MACSK(…)) — MAC and encrypt SAx 2, TSx = parameters for the first IPsec SA (algorithms, SPIs, traffic selectors) CERTREQ = accepted root CAs (or other trust roots)

Internet Key Exchange (IKEv 2) Initial exchanges: 1. 2. 3. 4. I → R: R → I: HDR(A, 0), SAi 1, KEi, Ni HDR(A, B), SAr 1, KEr, Nr, [CERTREQ] HDR(A, B), SK { IDi, [CERT, ] [CERTREQ, ] [IDr, ] AUTHi, SAi 2, TSi, TSr } HDR(A, B), SK { IDr, [CERT, ] AUTHr, SAr 2, TSi, TSr } A, B = SPI values that identity the protocol run and the created IKE SA Nx = nonces SAx 1 = offered and chosen algorithms, DH Secret, group fresh session key? KEx = Diffie-Hellman public key (gx or gy) Mutual authentication? Entity authentication and IDx, CERT = identity, certificate key confirmation? AUTHi = Sign. I (Message 1, Nr, h(SK, IDi)) Contributory? AUTHr = Sign. R (Message 2, Ni, h(SK, IDr)) Perfect forward secrecy? SK = h(Ni, Nr, gxy) — a bit simplified, 6 keys. Integrity are derived this negotiation? checkfrom for initial SK { … } = ESK( …, MACSK(…)) — MAC and encrypt Non-repudiation or plausible deniability? Identity protection? SAx 2, TSx = parameters for the first IPsec SA (algorithms, SPIs, traffic selectors) CERTREQ = accepted root CAs (or other trust roots)

IKEv 2 with a cookie exchange In the second message, responder may send a cookie (a nonce) Goal: prevent DOS attacks from a spoofed IP address 1. 2. 3. 4. 5. I → R: R → I: I → R: 6. R → I: HDR(A, 0), SAi 1, KEi, Ni HDR(A, 0), N(COOKIE) // R stores no state HDR(A, 0), N(COOKIE), SAi 1, KEi, Ni HDR(A, B), SAr 1, KEr, Nr, [CERTREQ] // R creates a state HDR(A, B), SK{ IDi, [CERT, ] [CERTREQ, ] [IDr, ] AUTH, SAi 2, TSi, TSr } HDR(A, B), ESK (IDr, [CERT, ] AUTH, SAr 2, TSi, TSr) How to bake a good cookie? For example: COOKIE = h(NR-periodic, IP addr of I, IP addr of R) where NR-periodic is a periodically changing secret random value know only by the responder R

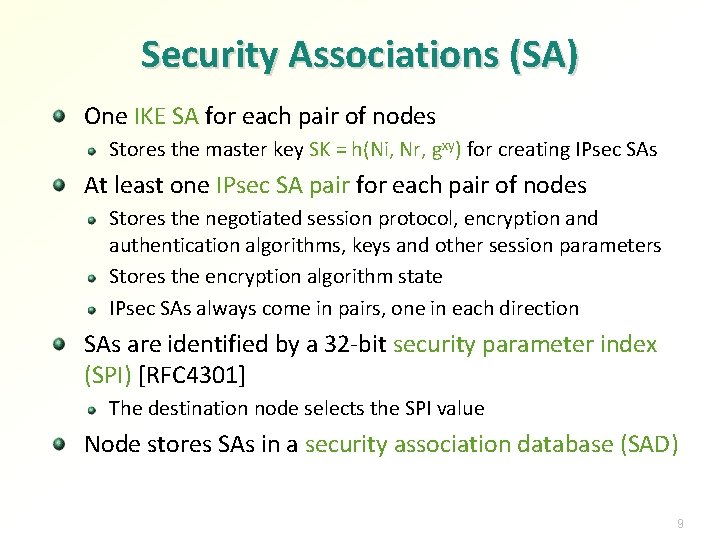
Security Associations (SA) One IKE SA for each pair of nodes Stores the master key SK = h(Ni, Nr, gxy) for creating IPsec SAs At least one IPsec SA pair for each pair of nodes Stores the negotiated session protocol, encryption and authentication algorithms, keys and other session parameters Stores the encryption algorithm state IPsec SAs always come in pairs, one in each direction SAs are identified by a 32 -bit security parameter index (SPI) [RFC 4301] The destination node selects the SPI value Node stores SAs in a security association database (SAD) 9
![Session protocol Encapsulated Security Payload ESP RFC 4303 Encryption andor MAC for Session protocol § Encapsulated Security Payload (ESP) [RFC 4303] § Encryption and/or MAC for](https://slidetodoc.com/presentation_image_h/2f9bed0328fb125e3114ec987e429031/image-10.jpg)
Session protocol § Encapsulated Security Payload (ESP) [RFC 4303] § Encryption and/or MAC for each packet § Optional replay prevention with sequence numbers § Protects the IP payload (= transport-layer PDU) only § ESP with encryption only is insecure § Old protocol: Authentication Header (AH) § Do not use for new applications § Authentication only, no encryption § Protects payload and some IP header fields 10

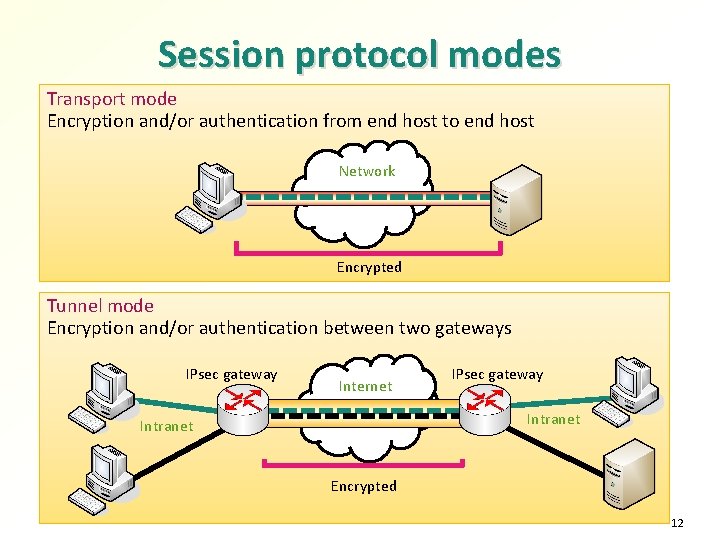
Session protocol modes Transport mode Encryption and/or authentication from end host to end host Network Encrypted Tunnel mode Encryption and/or authentication between two gateways IPsec gateway Internet IPsec gateway Intranet Encrypted 12

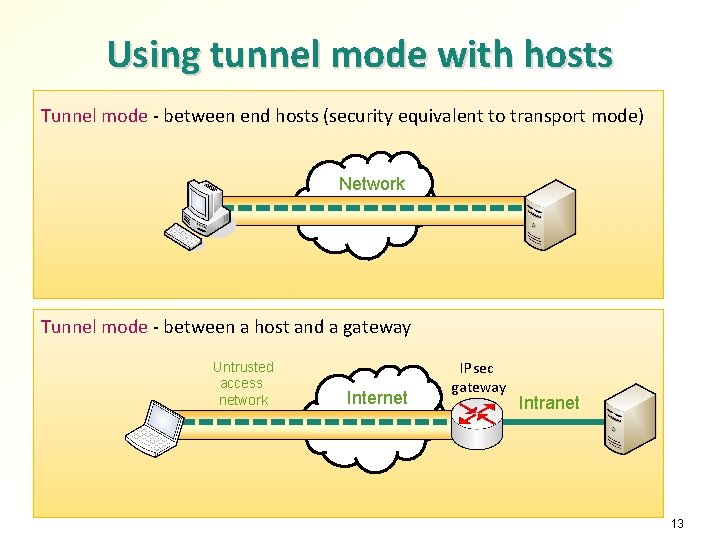
Using tunnel mode with hosts Tunnel mode - between end hosts (security equivalent to transport mode) Network Tunnel mode - between a host and a gateway Untrusted access network Internet IPsec gateway Intranet 13

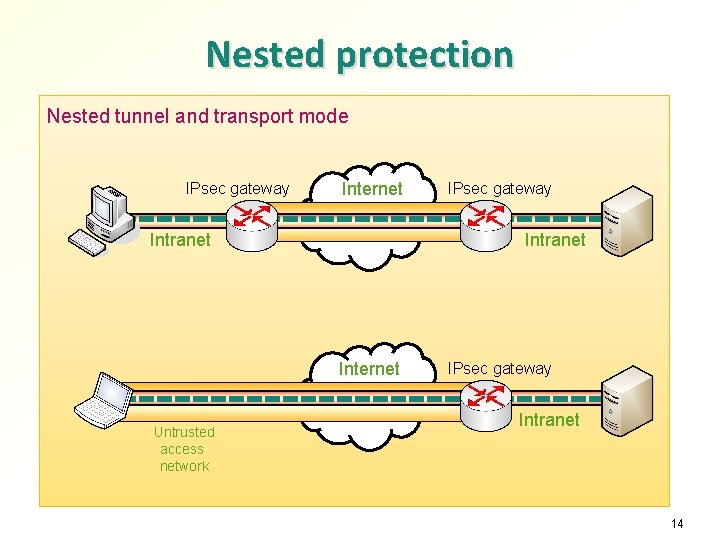
Nested protection Nested tunnel and transport mode IPsec gateway Internet Intranet Internet Untrusted access network IPsec gateway Intranet 14

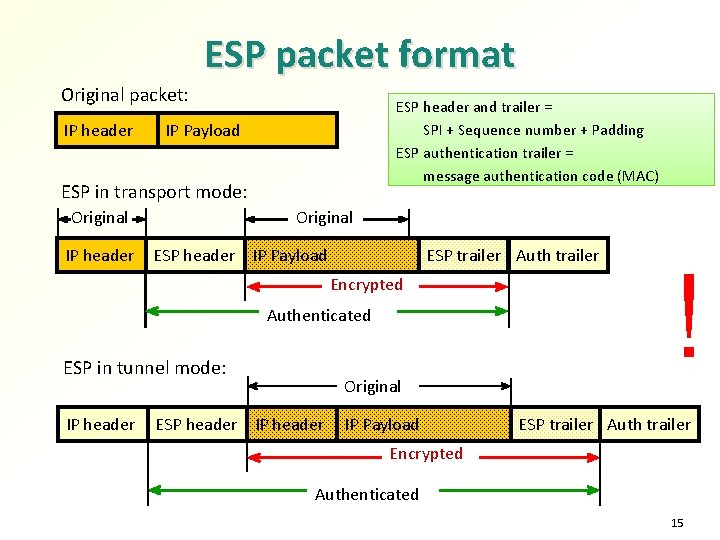
ESP packet format Original packet: IP header ESP header and trailer = SPI + Sequence number + Padding ESP authentication trailer = message authentication code (MAC) IP Payload ESP in transport mode: Original IP header Original ESP header IP Payload ESP trailer Auth trailer Encrypted Authenticated ESP in tunnel mode: IP header Original ESP header IP Payload ! ESP trailer Auth trailer Encrypted Authenticated 15

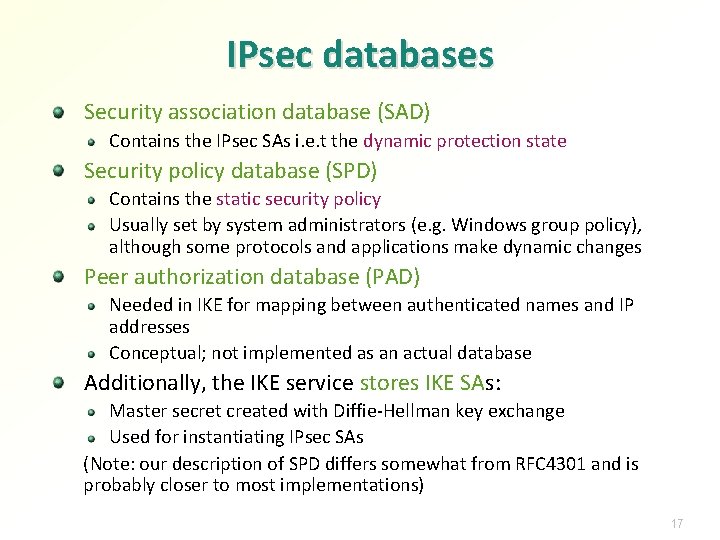
IPsec databases Security association database (SAD) Contains the IPsec SAs i. e. t the dynamic protection state Security policy database (SPD) Contains the static security policy Usually set by system administrators (e. g. Windows group policy), although some protocols and applications make dynamic changes Peer authorization database (PAD) Needed in IKE for mapping between authenticated names and IP addresses Conceptual; not implemented as an actual database Additionally, the IKE service stores IKE SAs: Master secret created with Diffie-Hellman key exchange Used for instantiating IPsec SAs (Note: our description of SPD differs somewhat from RFC 4301 and is probably closer to most implementations) 17

Security policy database (SPD) Specifies the static security policy Multi-homed nodes have a separate SPD for each network interface Policy maps inbound and outbound packets to actions SPD = linearly ordered list of policies Policy = selectors + action The first policy with matching selectors applies to each packet Policy selectors: Local and remote IP address Transport protocol (TCP, UDP, ICMP) Source and destination ports Actions: BYPASS (allow), DISCARD (block), or PROTECT specifies also the session protocol and algorithms Packet is mapped to a suitable SA If the SA does not exist, IKE is triggered to create one SPD stores pointers to previously created SA Policies at peer nodes must match if they are to communicate 18

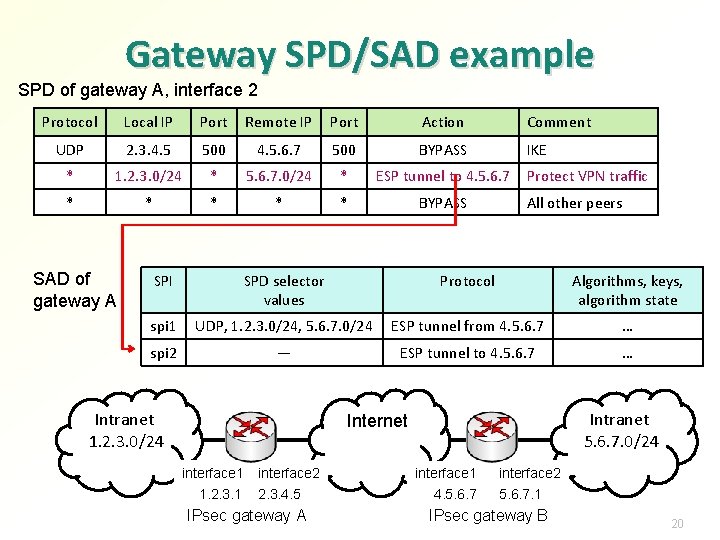
Gateway SPD/SAD example SPD of gateway A, interface 2 Protocol Local IP Port Remote IP Port Action Comment UDP 2. 3. 4. 5 500 4. 5. 6. 7 500 BYPASS IKE * 1. 2. 3. 0/24 * 5. 6. 7. 0/24 * ESP tunnel to 4. 5. 6. 7 * * * BYPASS SAD of gateway A Protect VPN traffic All other peers SPI SPD selector values Protocol Algorithms, keys, algorithm state spi 1 UDP, 1. 2. 3. 0/24, 5. 6. 7. 0/24 ESP tunnel from 4. 5. 6. 7 … spi 2 — ESP tunnel to 4. 5. 6. 7 … Intranet 1. 2. 3. 0/24 Intranet 5. 6. 7. 0/24 Internet interface 1 1. 2. 3. 1 interface 2 2. 3. 4. 5 IPsec gateway A interface 1 4. 5. 6. 7 interface 2 5. 6. 7. 1 IPsec gateway B 20

Some problems with IPsec

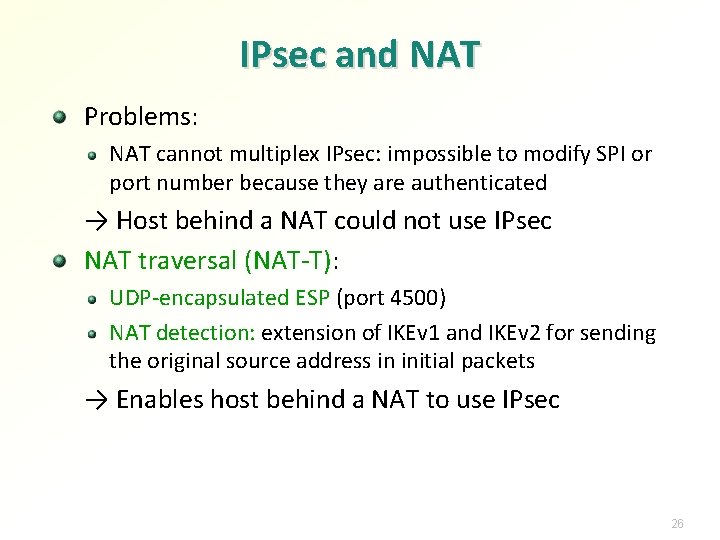
IPsec and NAT Problems: NAT cannot multiplex IPsec: impossible to modify SPI or port number because they are authenticated → Host behind a NAT could not use IPsec NAT traversal (NAT-T): UDP-encapsulated ESP (port 4500) NAT detection: extension of IKEv 1 and IKEv 2 for sending the original source address in initial packets → Enables host behind a NAT to use IPsec 26

IPsec and mobility Problem: IPsec policies and SAs are bound to IP addresses. Mobile nodes change their IP address Mobile IPv 6 helps: home address (Ho. A) is stable. But Mobile IPv 6 itself depends on IPsec for the tunnel between HA and MN. → Chicken-and-egg problem Solutions: IPsec was changed to look up inbound SAs by SPI only IPsec-based VPNs from mobile hosts do not use the IP address as selector. Instead, proprietary solutions MOBIKE mobility protocol 27

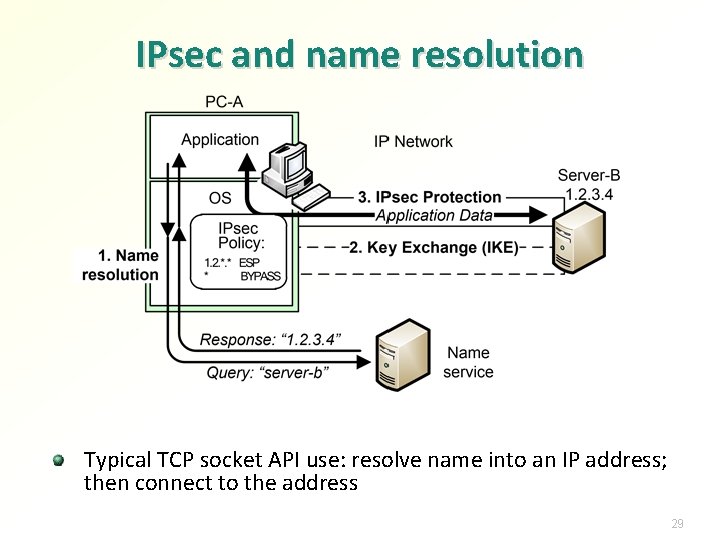
IPsec and name resolution Typical TCP socket API use: resolve name into an IP address; then connect to the address 29

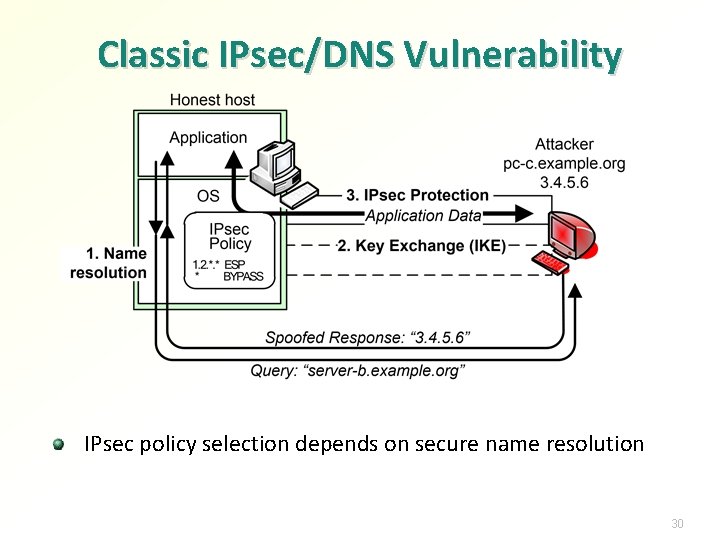
Classic IPsec/DNS Vulnerability IPsec policy selection depends on secure name resolution 30

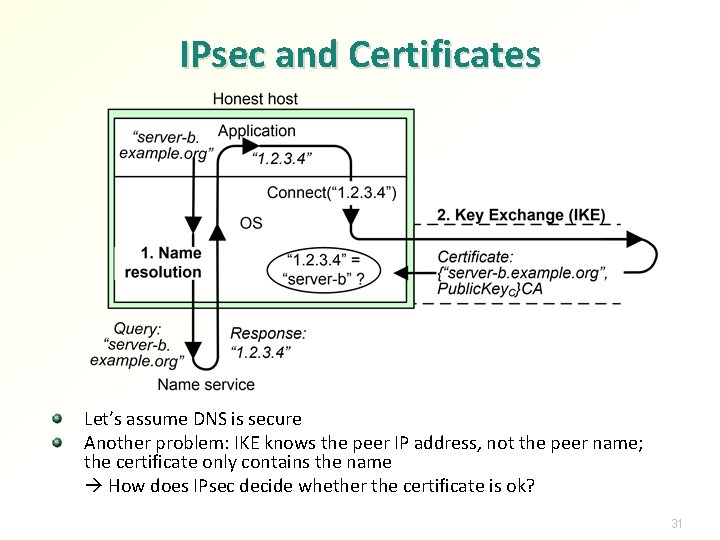
IPsec and Certificates Let’s assume DNS is secure Another problem: IKE knows the peer IP address, not the peer name; the certificate only contains the name How does IPsec decide whether the certificate is ok? 31

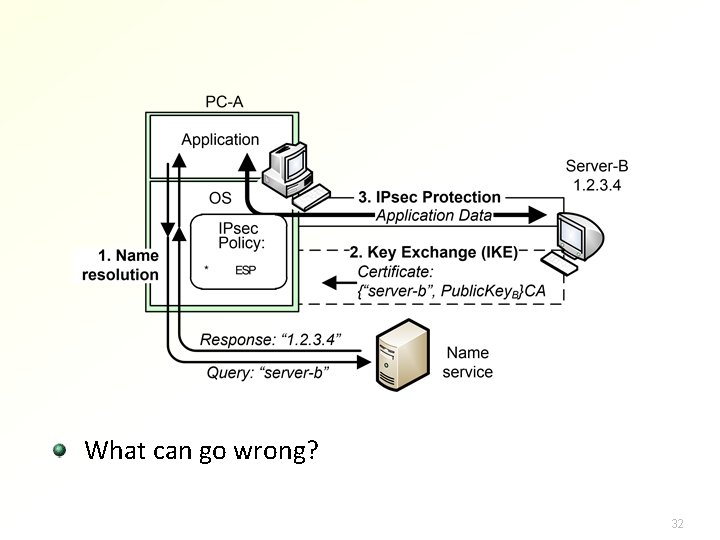
What can go wrong? 32

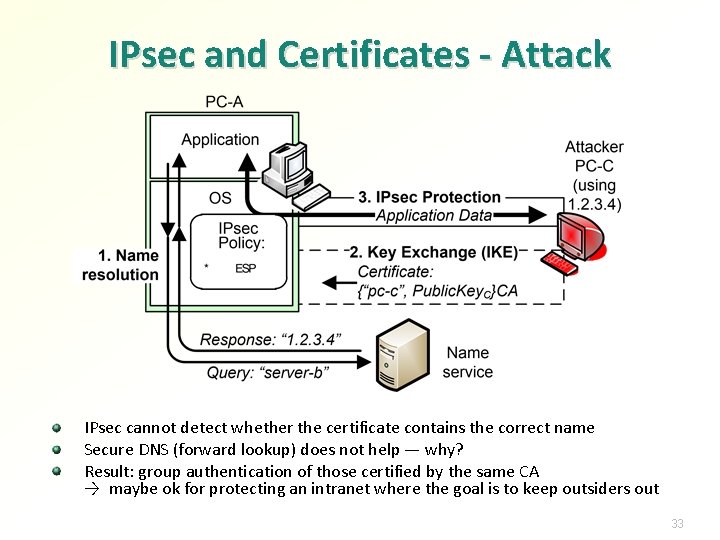
IPsec and Certificates - Attack IPsec cannot detect whether the certificate contains the correct name Secure DNS (forward lookup) does not help — why? Result: group authentication of those certified by the same CA → maybe ok for protecting an intranet where the goal is to keep outsiders out 33
![Peer authorization database PAD IPsec spec RFC 4301 defines a database that maps authenticated Peer authorization database (PAD) IPsec spec [RFC 4301] defines a database that maps authenticated](https://slidetodoc.com/presentation_image_h/2f9bed0328fb125e3114ec987e429031/image-26.jpg)
Peer authorization database (PAD) IPsec spec [RFC 4301] defines a database that maps authenticated names to the IP addresses which they are allowed to represent How implemented? Secure reverse DNS would be the best solution — but it does not exist. Other solutions: Secure DNS — both secure forward and reverse lookup needed, which is unrealistic Give up IPsec transparency — extend the socket API so that applications can query for the authenticated name and other security state Connect by name — change the socket API so that the OK knows the name to which the application wants to connect Currents situation: IPsec is only used for VPN where the gateway names and IP addresses are preconfigured 34

Puzzle of the day Consider each data field or cryptographic operation in IKEv 2. What security properties would be affected if it was not there? 35

Related reading William Stallings. Network security essentials: applications and standards, 3 rd ed. chapter 6; 4 th ed. chapters 8, 11 William Stallings. Cryptography and Network Security, 4 th ed. : chapter 16 Kaufmann, Perlman, Speciner. Network security, 2 nd ed. : chapter 17 (ignore AH) Note: chapter 18 on the older IKEv 1 is historical Dieter Gollmann. Computer Security, 2 nd ed. chapter 13. 3; 3 rd ed. chapters 16. 1– 16. 3, 17. 3 36

Exercises Why is IPsec used mainly for VPN implementations? Does IPsec VPN suffer from any of the problems mentioned in the lecture? For the IPsec policy examples of this lecture, define the IPsec policy for the peer nodes i. e. the other ends of the connections Try to configure the IPsec policy between two computers. What difficulties did you meet? Use ping and TCP to test connectivity. Use a network sniffer to observe the key exchange and to check that packets on the wire are encrypted What administrative problems arise from the fact that IPsec security policies in two communicating nodes must match? How is this solved in Windows? RFC 4301 requires that the SPD is decorrelated, i. e. that the selectors of policy entries not to overlap, i. e. that any IP packet will match at most one rule (excluding the default rule which matches all packet). Yet, the policies created by system administrators almost always have overlapping entries. Device an algorithm for transforming any IPsec policy to an equivalent decorrelated policy. Each SAD entry stores (caches) policy selector values from the policy that was used when creating it. Inbound packets are compared against these selectors to check that the packet arrives on the correct SA. What security problem would arise without this check? What security weakness does the caching have (compared to a lookup through the SPD)? Does policy decorrelation solve the problem? 37