Network Layer Security 1 Outline r IPsec r








































- Slides: 78

Network Layer Security 1

Outline r IPsec r Security in Routing r DDo. S at Network Layer and IP Traceback r IPv 6 Security 2

Network Layer: IP Security Overview r RFC 1636: “Security in the Internet Architecture” m Issued in 1994 by the Internet Architecture Board (IAB) m Identifies key areas for security mechanisms • Need to secure the network infrastructure from unauthorized monitoring and control of network traffic • Need to secure end-user-to-end-user traffic using authentication and encryption mechanisms m IAB included authentication and encryption as necessary security features in next generation IP (IPv 6) • The IPsec specification now exists as a set of Internet standards 3

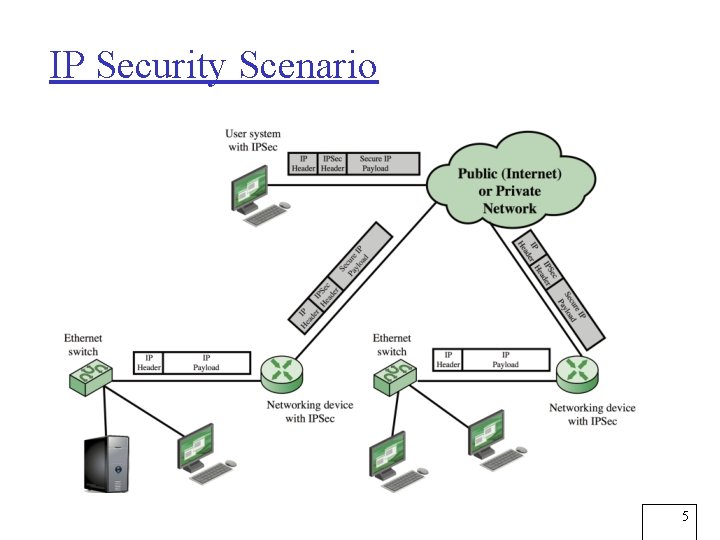
Applications of IPsec r Provides capability to secure communications across a LAN, private and public WANs, and the Internet r Examples include: m m Secure branch office connectivity over the Internet Secure remote access over the Internet Establishing extranet and intranet connectivity with partners Enhancing electronic commerce security r Principal feature of IPsec: can encrypt and/or authenticate all traffic at network (IP) level m So all distributed applications (remote logon, client/server, e-mail, file transfer, Web access) can be secured 4

IP Security Scenario 5

Benefits of IPSec r When IPsec is implemented in firewall or router, it provides strong security applicable to all traffic crossing the perimeter m Traffic within company/workgroup has no overhead from securityrelated processing IPsec in firewall resists bypass if all outside traffic must use IP and the firewall is the only way Internet traffic enters organization r IPsec below the transport layer (TCP, UDP); transparent to applications r m r IPsec can be transparent to end users m r No need to change software on a user or server system when IPsec is implemented in the firewall or router No need to train users on security mechanisms, issue keys on a peruser basis, or revoke keys when users leave organization IPsec can provide security for individual users if needed m Useful for offsite workers, setting up secure virtual subnetwork within an organization for sensitive applications 6

Routing Applications r IPsec can play vital role in the routing architecture required for internetworking r IPsec can assure that: Router advertisement comes from authorized router m Router seeking to establish or maintain a neighbor relationship with a router in another routing domain is an authorized router m Redirect message comes from the router to which the initial IP packet was sent m Routing updates are not forged m 7

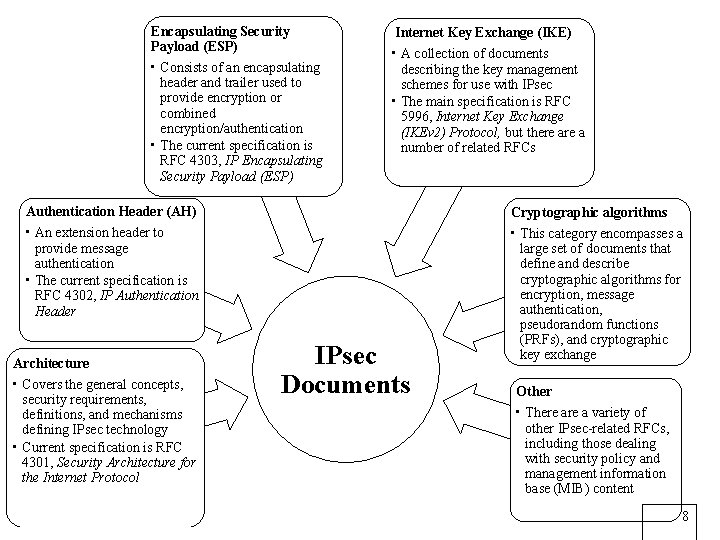
Encapsulating Security Payload (ESP) • Consists of an encapsulating header and trailer used to provide encryption or combined encryption/authentication • The current specification is RFC 4303, IP Encapsulating Security Payload (ESP) Internet Key Exchange (IKE) • A collection of documents describing the key management schemes for use with IPsec • The main specification is RFC 5996, Internet Key Exchange (IKEv 2) Protocol, but there a number of related RFCs Authentication Header (AH) Cryptographic algorithms • An extension header to provide message authentication • The current specification is RFC 4302, IP Authentication Header • This category encompasses a large set of documents that define and describe cryptographic algorithms for encryption, message authentication, pseudorandom functions (PRFs), and cryptographic key exchange Architecture • Covers the general concepts, security requirements, definitions, and mechanisms defining IPsec technology • Current specification is RFC 4301, Security Architecture for the Internet Protocol IPsec Documents Other • There a variety of other IPsec-related RFCs, including those dealing with security policy and management information base (MIB) content 8

IPsec Services r IPsec provides network layer security services by enabling a system to: m m m q Select required security protocols Determine the algorithm(s) to use for the service(s) Establish crypto keys required to provide requested services RFC 4301 lists the following services: m m m Access control Connectionless integrity Data origin authentication Reject replayed packets (form of partial sequence integrity) Confidentiality (encryption) Limited traffic flow confidentiality 9

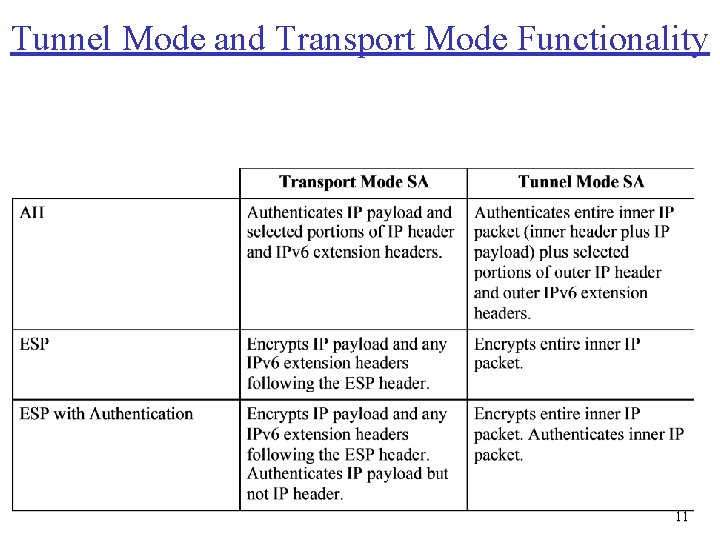
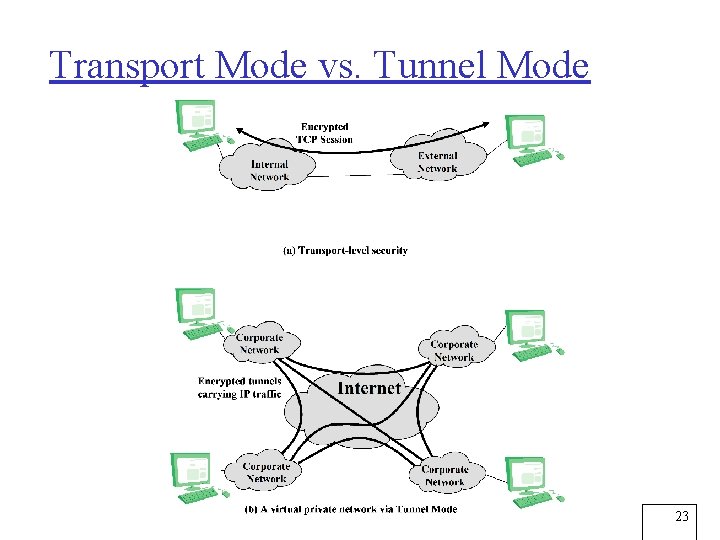
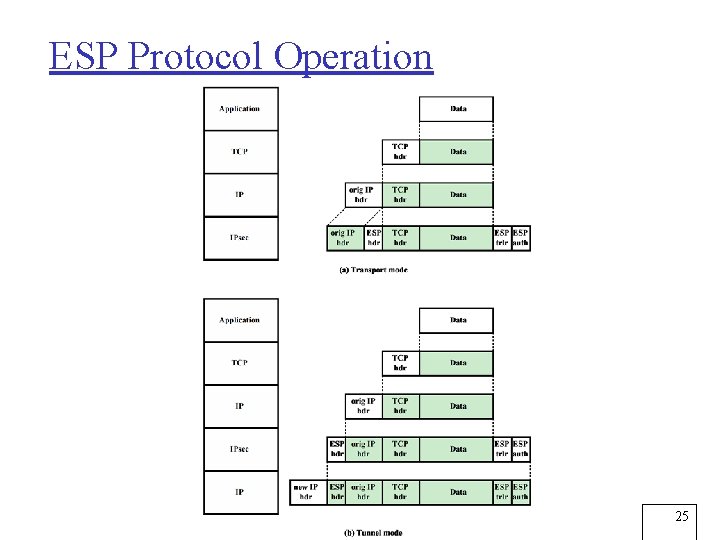
Transport and Tunnel Modes Transport Mode Tunnel Mode • Provides protection mostly for upper-layer protocols, e. g. , TCP or UDP segment, ICMP packet • Typically used for end-to-end communication between two hosts • ESP in transport mode encrypts and optionally authenticates the IP payload but not the IP header • AH in transport mode authenticates the IP payload and selected portions of the IP header • Provides protection to the entire IP packet • Used when one or both ends of a security association (SA) are a security gateway • Number of hosts on networks behind firewalls can securely communicate without implementing IPsec • ESP in tunnel mode encrypts, can authenticate entire inner IP packet, including inner IP header • AH in tunnel mode authenticates the entire inner IP packet and selected portions of outer IP header 10

Tunnel Mode and Transport Mode Functionality 11

IPsec Architecture 12

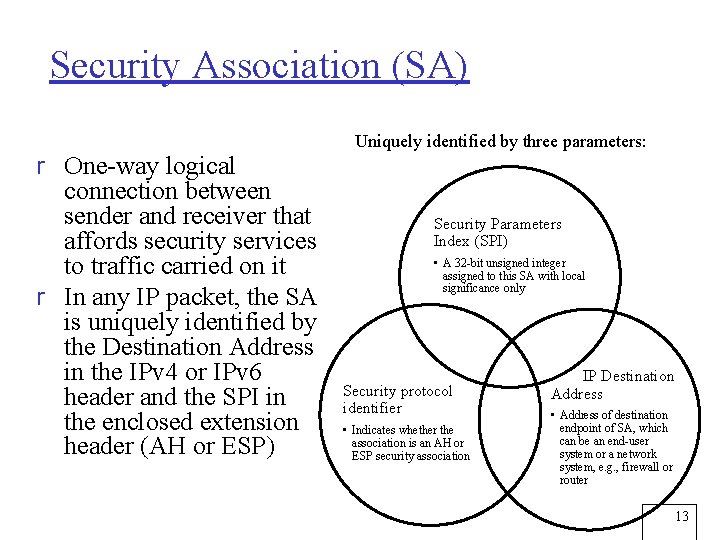
Security Association (SA) r One-way logical connection between sender and receiver that affords security services to traffic carried on it r In any IP packet, the SA is uniquely identified by the Destination Address in the IPv 4 or IPv 6 header and the SPI in the enclosed extension header (AH or ESP) Uniquely identified by three parameters: Security Parameters Index (SPI) • A 32 -bit unsigned integer assigned to this SA with local significance only Security protocol identifier • Indicates whether the association is an AH or ESP security association IP Destination Address • Address of destination endpoint of SA, which can be an end-user system or a network system, e. g. , firewall or router 13

Security Association Database (SAD) r Defines the parameters associated with each SA r Normally defined by the following parameters in a SAD entry: m m m m m Security parameter index Sequence number counter Sequence counter overflow Anti-replay window AH information ESP information Lifetime of this security association IPsec protocol mode Path MTU 14

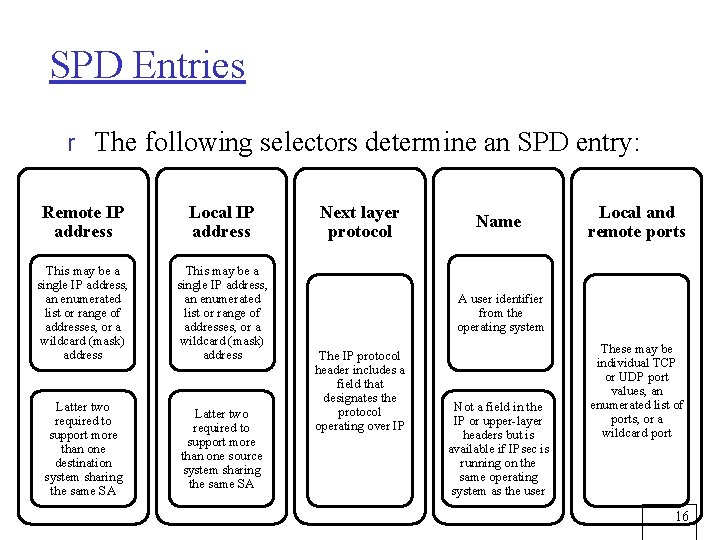
Security Policy Database (SPD) r The means by which IP traffic is related to specific SAs m Contains entries, each of which defines a subset of IP traffic and points to an SA for that traffic r In more complex environments, may be multiple entries that potentially relate to a one or more SAs associated with a single SPD entry Each SPD entry is defined by a set of IP and upperlayer protocol field values called selectors m These are used to filter outgoing traffic in order to map it into a particular SA m 15

SPD Entries r The following selectors determine an SPD entry: Remote IP address Local IP address This may be a single IP address, an enumerated list or range of addresses, or a wildcard (mask) address Latter two required to support more than one destination system sharing the same SA Latter two required to support more than one source system sharing the same SA Next layer protocol Name Local and remote ports A user identifier from the operating system The IP protocol header includes a field that designates the protocol operating over IP Not a field in the IP or upper-layer headers but is available if IPsec is running on the same operating system as the user These may be individual TCP or UDP port values, an enumerated list of ports, or a wildcard port 16

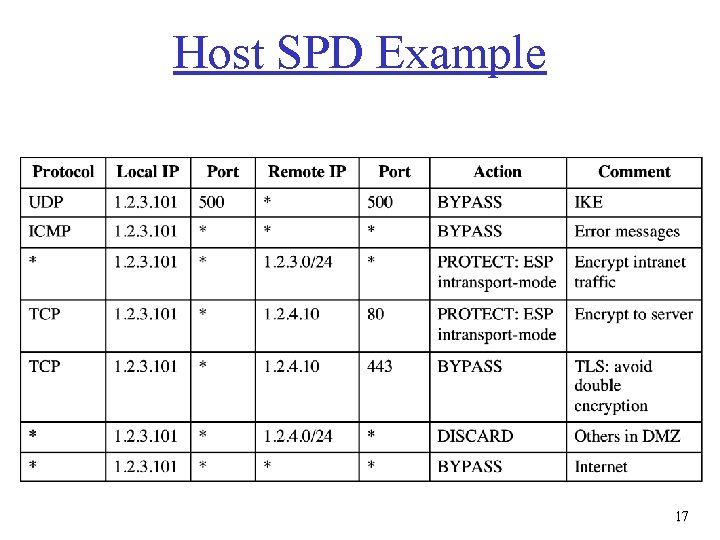
Host SPD Example 17

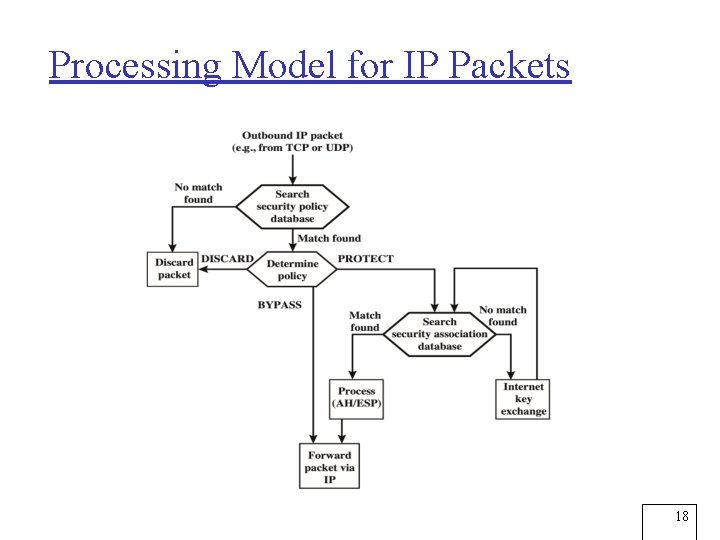
Processing Model for IP Packets 18

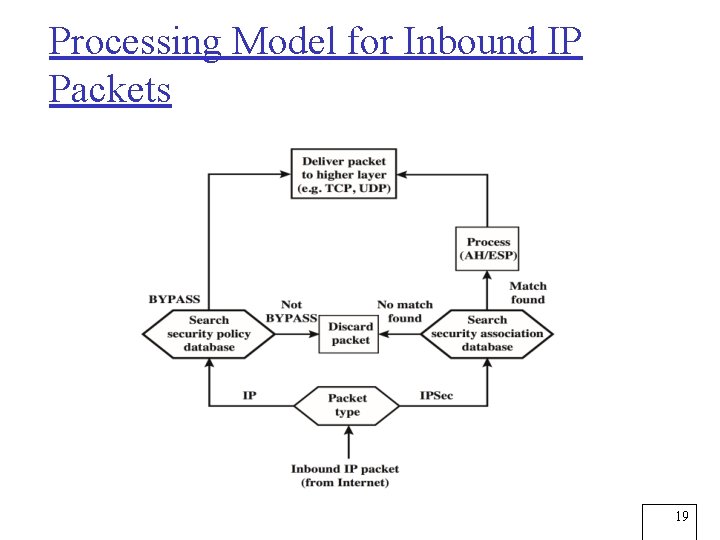
Processing Model for Inbound IP Packets 19

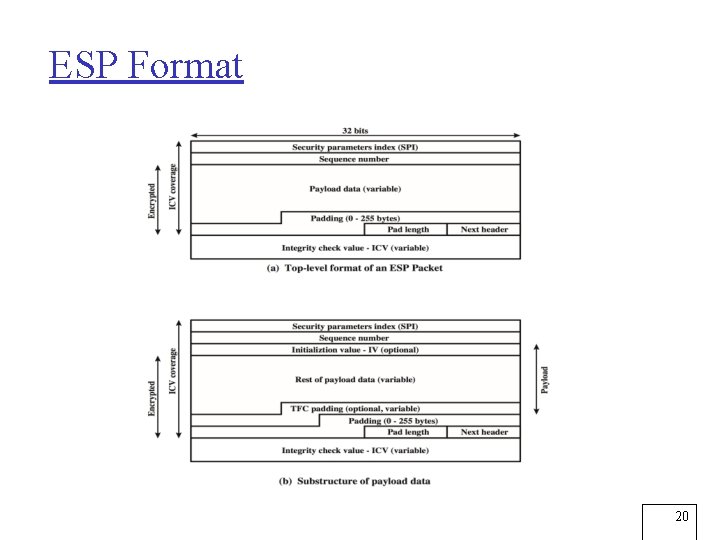
ESP Format 20

Encapsulating Security Payload (ESP) r Used to encrypt the Payload Data, Padding, Pad Length, and Next Header fields m r An optional ICV field is present only if the integrity service is selected and is provided by either a separate integrity algorithm or a combined mode algorithm that uses an ICV m m m r If the algorithm requires cryptographic synchronization data then these data may be carried explicitly at the beginning of the Payload Data field ICV is computed after the encryption is performed This order of processing facilitates reducing the impact of Do. S attacks Because the ICV is not protected by encryption, a keyed integrity algorithm must be employed to compute the ICV The Padding field serves several purposes: m m m If an encryption algorithm requires the plaintext to be a multiple of some number of bytes, the Padding field is used to expand the plaintext to the required length Used to assure alignment of Pad Length and Next Header fields Additional padding may be added to provide partial traffic-flow confidentiality by concealing the actual length of the payload 21

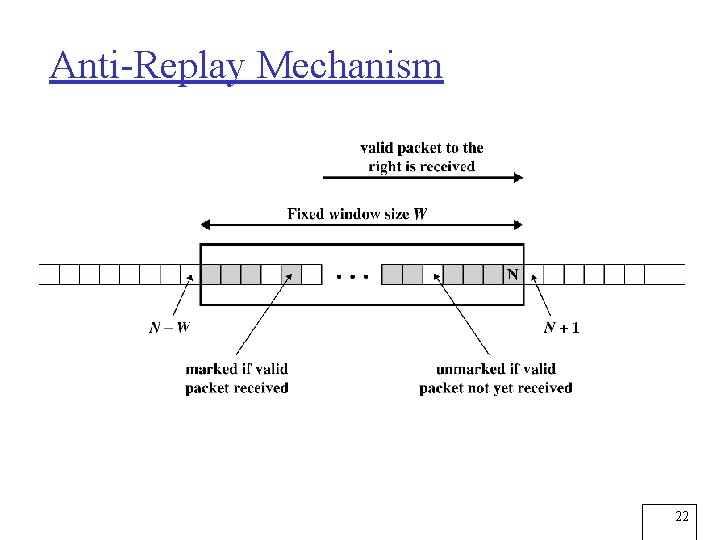
Anti-Replay Mechanism 22

Transport Mode vs. Tunnel Mode 23

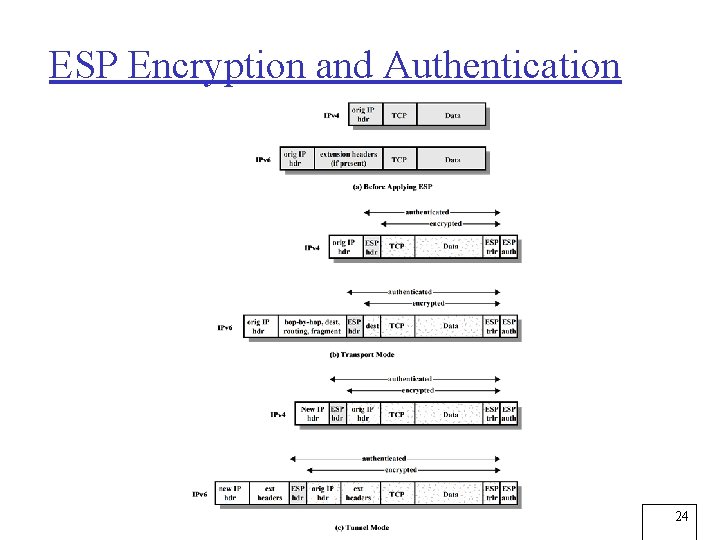
ESP Encryption and Authentication 24

ESP Protocol Operation 25

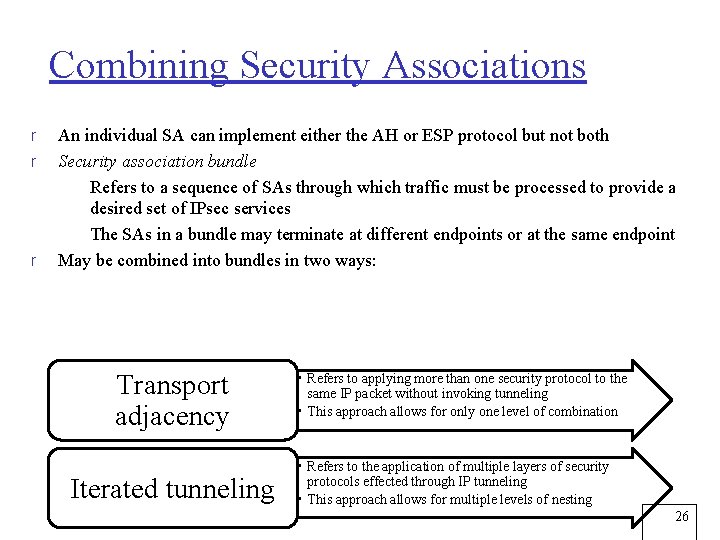
Combining Security Associations r r r An individual SA can implement either the AH or ESP protocol but not both Security association bundle m Refers to a sequence of SAs through which traffic must be processed to provide a desired set of IPsec services m The SAs in a bundle may terminate at different endpoints or at the same endpoint May be combined into bundles in two ways: Transport adjacency Iterated tunneling • Refers to applying more than one security protocol to the same IP packet without invoking tunneling • This approach allows for only one level of combination • Refers to the application of multiple layers of security protocols effected through IP tunneling • This approach allows for multiple levels of nesting 26

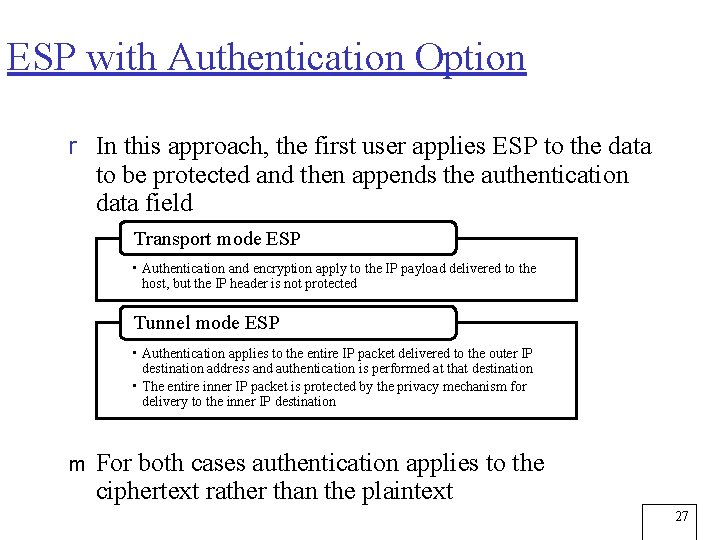
ESP with Authentication Option r In this approach, the first user applies ESP to the data to be protected and then appends the authentication data field Transport mode ESP • Authentication and encryption apply to the IP payload delivered to the host, but the IP header is not protected Tunnel mode ESP • Authentication applies to the entire IP packet delivered to the outer IP destination address and authentication is performed at that destination • The entire inner IP packet is protected by the privacy mechanism for delivery to the inner IP destination m For both cases authentication applies to the ciphertext rather than the plaintext 27

Transport Adjacency r Another way to apply authentication after encryption is to use two bundled transport SAs, with the inner being an ESP SA and the outer being an AH SA In this case ESP is used without its authentication option m Encryption is applied to the IP payload m AH is then applied in transport mode m Advantage of this approach is that the authentication covers more fields m Disadvantage is the overhead of two SAs versus one SA m 28

Transport-Tunnel Bundle r The use of authentication prior to encryption might be preferable for several reasons: m m It is impossible for anyone to intercept the message and alter the authentication data without detection It may be desirable to store the authentication information with the message at the destination for later reference r One approach is to use a bundle consisting of an inner AH transport SA and an outer ESP tunnel SA m m Authentication is applied to the IP payload plus the IP header The resulting IP packet is then processed in tunnel mode by ESP • The result is that the entire authenticated inner packet is encrypted and a new outer IP header is added 29

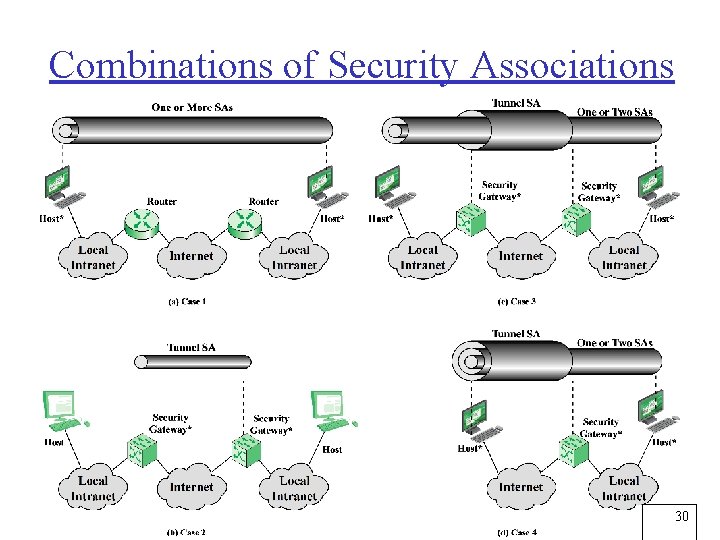
Combinations of Security Associations 30

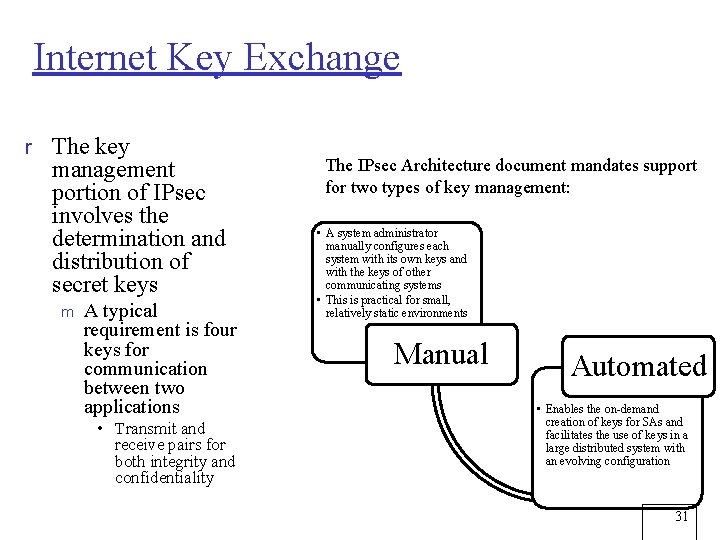
Internet Key Exchange r The key management portion of IPsec involves the determination and distribution of secret keys m A typical requirement is four keys for communication between two applications • Transmit and receive pairs for both integrity and confidentiality The IPsec Architecture document mandates support for two types of key management: • A system administrator manually configures each system with its own keys and with the keys of other communicating systems • This is practical for small, relatively static environments Manual Automated • Enables the on-demand creation of keys for SAs and facilitates the use of keys in a large distributed system with an evolving configuration 31

ISAKMP/Oakley r The default automated key management protocol of IPsec r Consists of: m Oakley Key Determination Protocol • A key exchange protocol based on the Diffie-Hellman algorithm but providing added security • Generic in that it does not dictate specific formats m Internet Security Association and Key Management Protocol (ISAKMP) • Provides a framework for Internet key management and provides the specific protocol support, including formats, for negotiation of security attributes • Consists of a set of message types that enable the use of a variety of key exchange algorithms 32

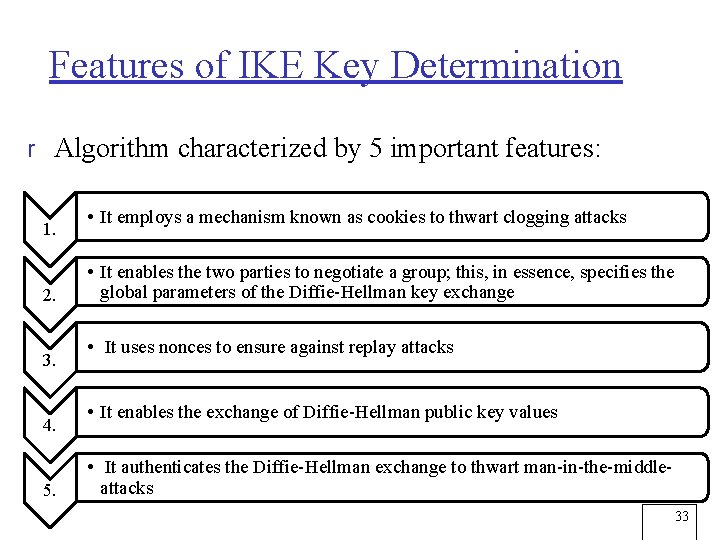
Features of IKE Key Determination r Algorithm characterized by 5 important features: 1. 2. 3. 4. 5. • It employs a mechanism known as cookies to thwart clogging attacks • It enables the two parties to negotiate a group; this, in essence, specifies the global parameters of the Diffie-Hellman key exchange • It uses nonces to ensure against replay attacks • It enables the exchange of Diffie-Hellman public key values • It authenticates the Diffie-Hellman exchange to thwart man-in-the-middleattacks 33

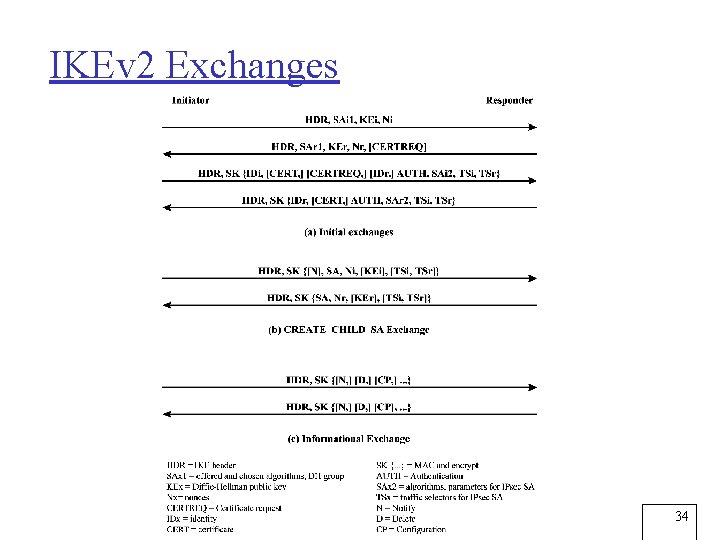
IKEv 2 Exchanges 34

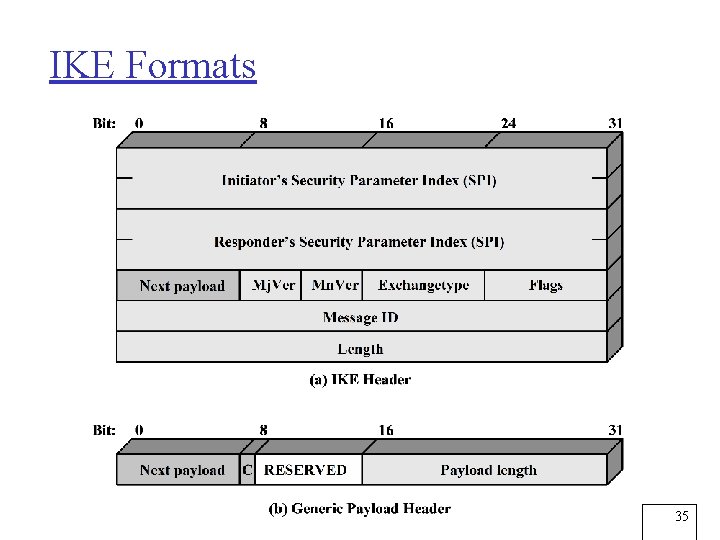
IKE Formats 35

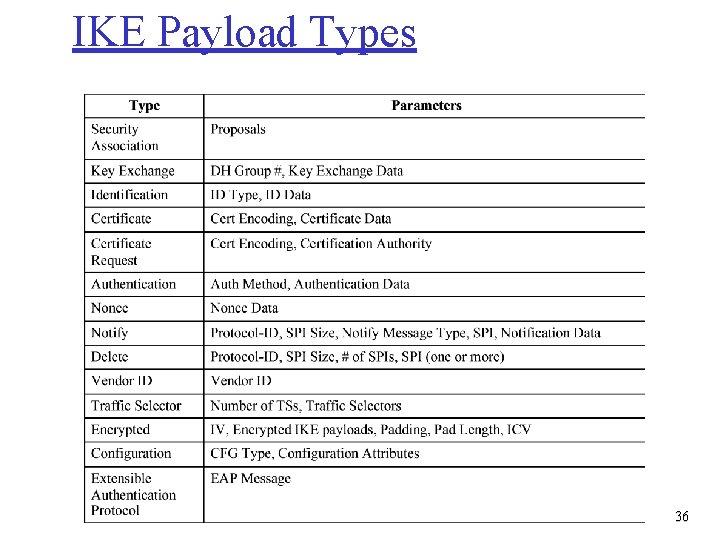
IKE Payload Types 36

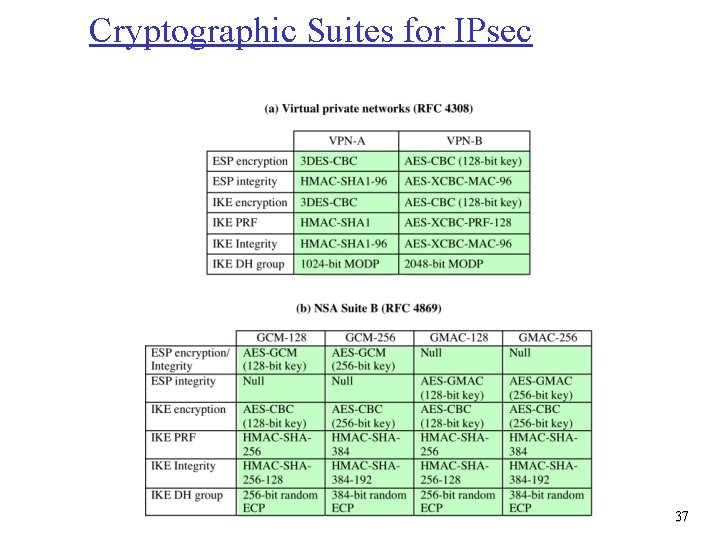
Cryptographic Suites for IPsec 37

Summary: IPsec r IP security overview m m m r m m m Security associations Security association database Security policy database IP traffic processing Cryptographic suites Encapsulating security payload m m r IP security policy m m Applications of IPsec Benefits of IPsec Routing applications IPsec documents IPsec services Transport and tunnel modes r Combining security associations m m r ESP format Encryption and authentication algorithms Padding anti-replay service Transport and tunnel modes Authentication plus confidentiality Basic combinations of security associations Internet key exchange m m Key determination protocol Header and payload formats 38

Outline r IPsec r Security in Routing r DDo. S at Network Layer and IP Traceback r IPv 6 Security 39

Routing in the Internet • The Global Internet consists of Autonomous Systems (AS) interconnected with each other: – – – Stub AS: small corporation Multihomed AS: large corporation (no transit) Transit AS: provider • Two-level routing: – Intra-AS: administrator is responsible for choice: RIP, OSPF – Inter-AS: unique standard: BGP 40

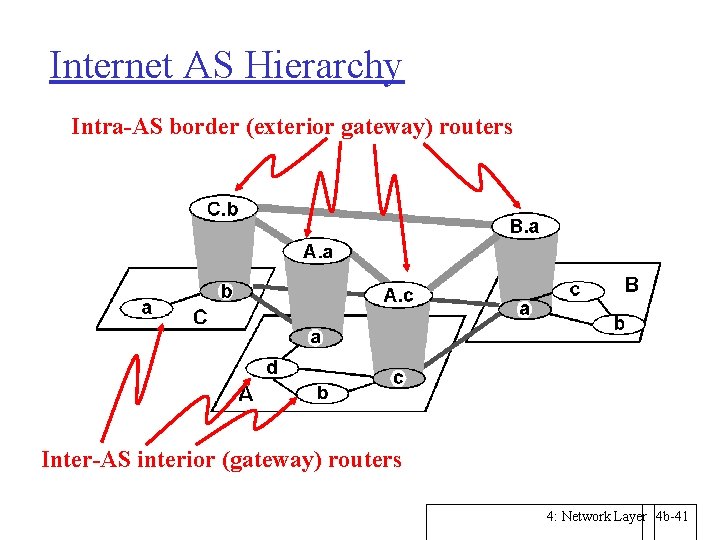
Internet AS Hierarchy Intra-AS border (exterior gateway) routers Inter-AS interior (gateway) routers 4: Network Layer 4 b-41

Intra-AS Routing r Also known as Interior Gateway Protocols (IGP) r Most common IGPs: m RIP: Routing Information Protocol (distance vector – Bellman-Ford algorithm) m OSPF: Open Shortest Path First (link state – Dijkstra’s algorithm) m IGRP: Interior Gateway Routing Protocol (Cisco proprietary) (distance vector) 4: Network Layer 4 b-42

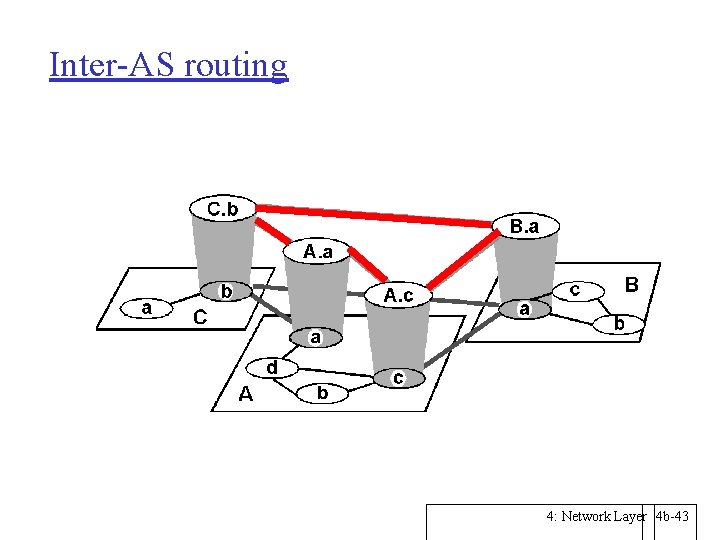
Inter-AS routing 4: Network Layer 4 b-43

Why different Intra-AS, Inter-AS routing? Policy: r Inter-AS: admin wants control over how its traffic routed, who routes through its net. r Intra-AS: single admin, so no policy decisions needed Scale: r Hierarchical routing saves table size, reduced update traffic Performance: r Intra-AS: can focus on performance r Inter-AS: policy may dominate over performance 4: Network Layer 4 b-44

Routing Security Issues r Security attacks can come from: m Misconfigured routers m IP packet handling bugs m SNMP “common” strings m Weak passwords, poor encryption m Do. S from malformed packets r However, these attacks are well-known; defense measures can defend against them 45

Routing Protocol Attacks r Intra-AS Routing Attacks m RIP Attack m OSPF Attacks r Inter-AS Routing Attacks: BGP 46

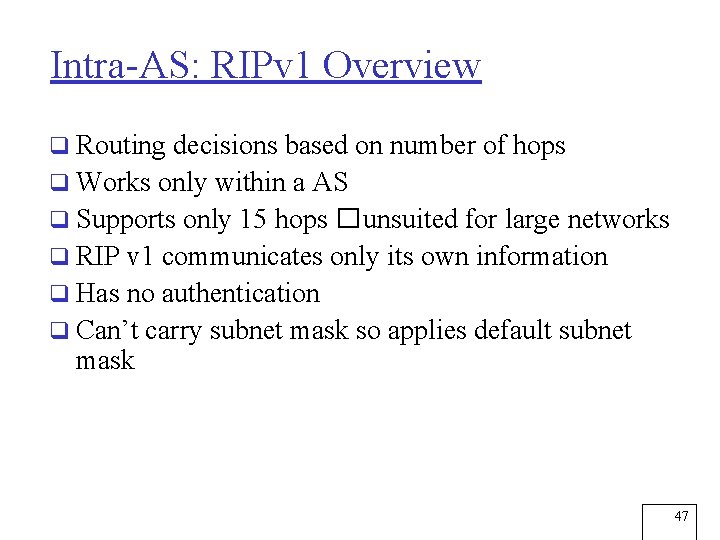
Intra-AS: RIPv 1 Overview q Routing decisions based on number of hops q Works only within a AS q Supports only 15 hops � unsuited for large networks q RIP v 1 communicates only its own information q Has no authentication q Can’t carry subnet mask so applies default subnet mask 47

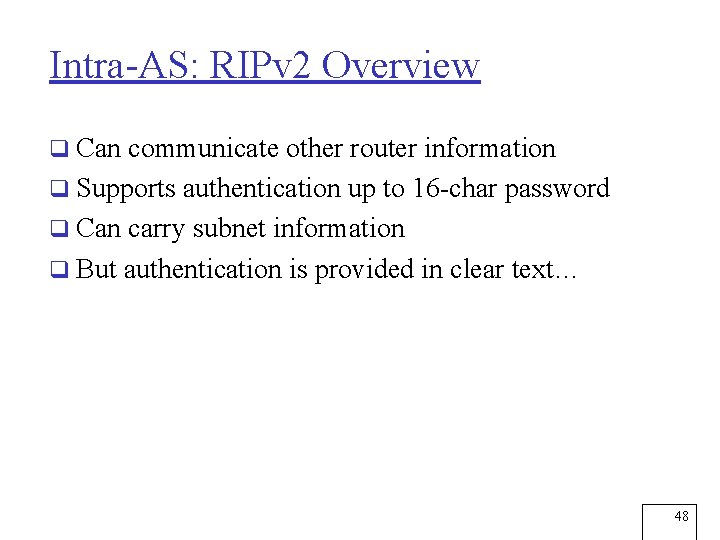
Intra-AS: RIPv 2 Overview q Can communicate other router information q Supports authentication up to 16 -char password q Can carry subnet information q But authentication is provided in clear text… 48

Intra-AS: RIP Attack q Identify RIP router via nmap scan: nmap –v –s. U –p 520 q Determine routing table: If you are on same physical segment, sniff it q Remotely: run rprobe, sniff q q Add route using srip to redirect traffic to your system 49

Intra-AS: Safeguards (RIP Attack) q Disable RIP, use OSPF: security is better q Restrict TCP/UDP port 520 packets at border router 50

Intra-AS: OSPF Attack r OSPF: dynamic link-state routing protocol r Keeps map of entire network, chooses shortest path r Update neighbors using LSAs messages r “Hello” packets generated every 10 s, sent to 224. 0. 0. 5 r Uses protocol type 89 51

Intra-AS: OSPF Attack r Identify target: scan for proto 89 r NCSU: Ji. Nao project identified 4 OSPF attacks m Max Age attack m Sequence++ attack m Max Sequence attack m Bogus LSA attack r Attack tool: nemiss-ospf (hard to use? ) 52

Intra-AS: Safeguards: OSPF Attack r Do not use dynamic routing on hosts wherever not required r Implement MD 5 authentication m You need to deal with key expiration, changeover and coordination across routers 53

Inter-AS: BGP overview r Allows inter-domain routing between two ASs r Guarantees loop-free exchange r Only routing protocol which works on TCP (179) r Routing information is exchanged after connection establishment 54

Inter-AS: BGP Attacks r Large network backbone: special attention to security r So medium size networks are easier targets r Packet injection vulnerabilities: very dangerous r If we identify BGP routers, they have similar weaknesses as TCP: SYN flood attacks m Sequence number prediction m Do. S m Possible advertisement of bad routes m 55

Outline r IPsec r Security in Routing r DDo. S at Network Layer and IP Traceback r IPv 6 Security 56

DDo. S Attacks at Network Layer r What is a DDo. S attack? r How do we defend against a DDo. S attack? 57

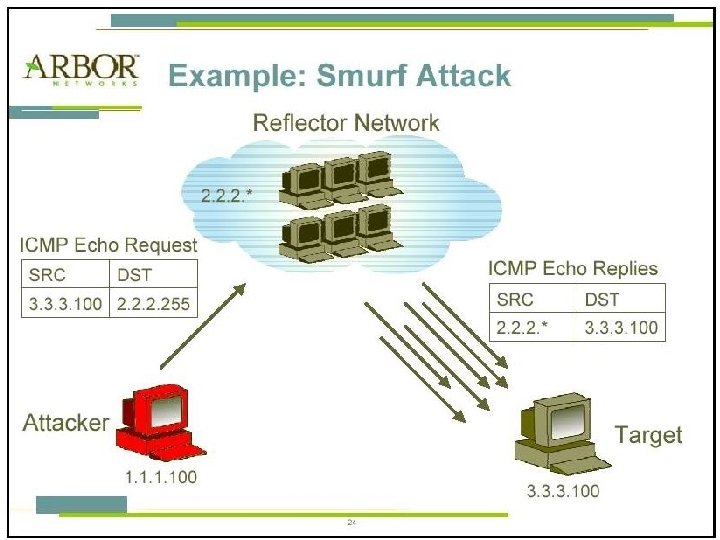
What is a DDo. S attack? q Internet DDo. S attack is real threat o On websites § Yahoo, CNN, Amazon, e. Bay, etc. (Feb. 2000) § Services were unavailable for several hours o On Internet infrastructure § 13 root DNS servers (Oct, 2002) § 7 were shut down, 2 others partially unavailable q Lack of defense mechanisms on current Internet 58

What is a DDo. S Attack? q Denial-of-Service (Do. S) attacks: o Attempt to prevent legitimate users of a service from using it q Examples of Do. S attacks include: o Flooding a network o Disrupting connections between machines o Disrupting a service q Distributed Denial-of-Service (DDo. S) Attacks o Many machines are involved in the attack against one or more victim(s) 59

60

What Makes DDo. S Attacks Possible? r Internet was designed with functionality, not security, in mind r Internet security is highly interdependent r Internet resources are limited r Power of many greater than power of a few 61

Addressing DDo. S attacks q Ingress filtering o P. Ferguson and D. Senie, RFC 2267, Jan 1998 o Block packets that has illegitimate source addresses o Disadvantage : Overhead makes routing slow q Identification of origin (Traceback problem) o IP spoofing enables attackers to hide their identity o Many IP traceback techniques are suggested q Mitigating the effect during the attack o Pushback 62

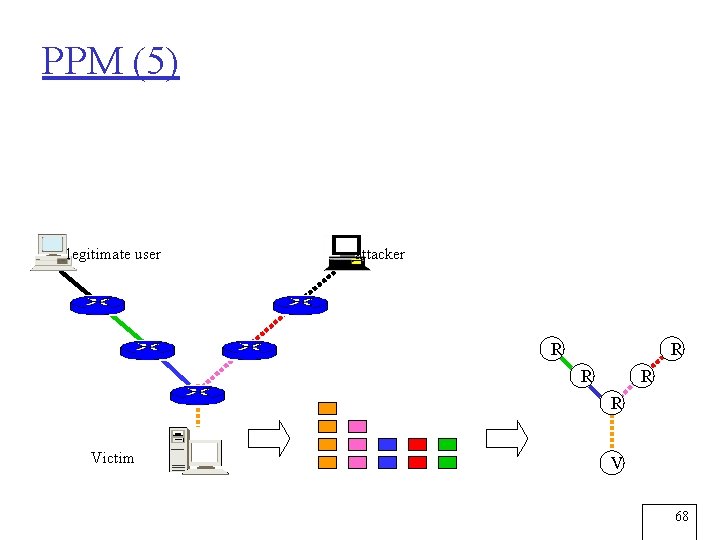
IP Traceback • Allows victim to identify attackers’ origin • Several approaches – ICMP trace messages – Probabilistic Packet Marking (PPM)* – Hash-based IP traceback – … *S. Savage, D. Weatherall, A. Karlin, and T. Anderson, “Practical Network Support for IP Traceback”, Proc. SIGCOMM 2000. 63

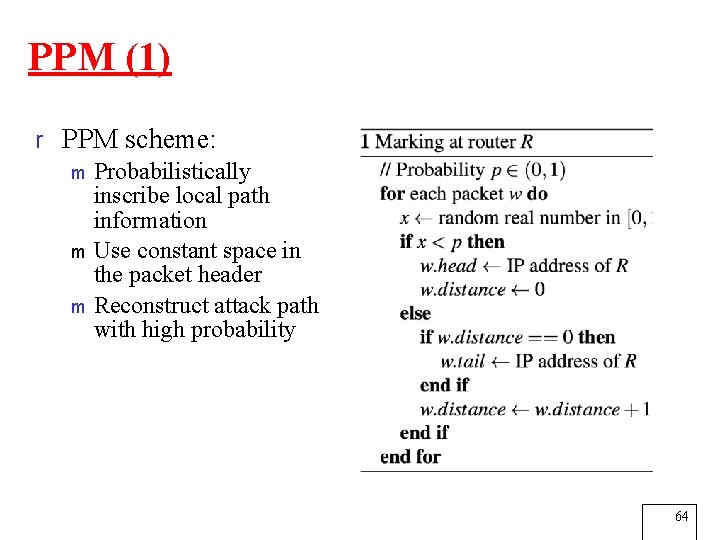
PPM (1) r PPM scheme: m Probabilistically inscribe local path information m Use constant space in the packet header m Reconstruct attack path with high probability 64

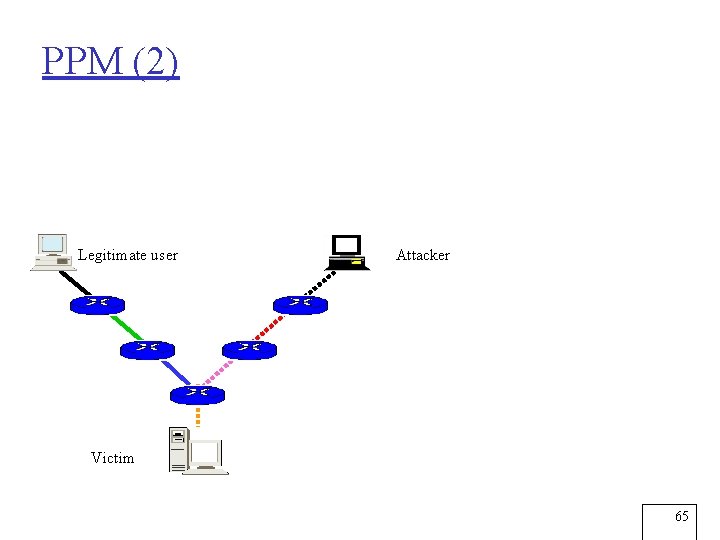
PPM (2) Legitimate user Attacker Victim 65

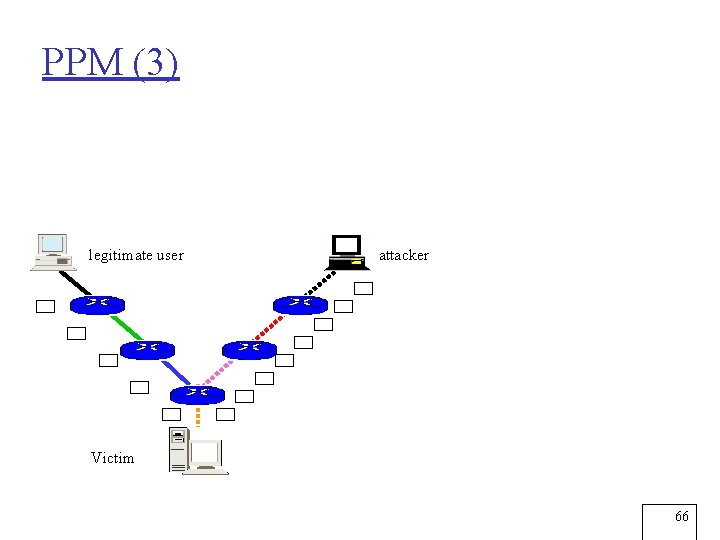
PPM (3) legitimate user attacker Victim 66

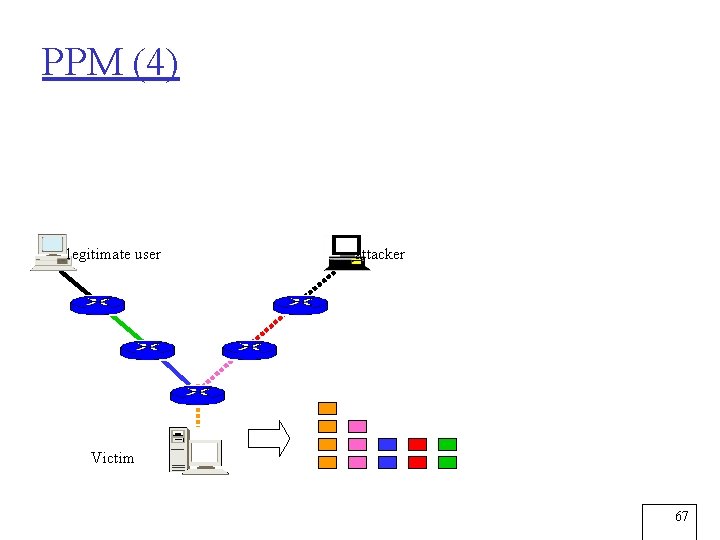
PPM (4) legitimate user attacker Victim 67

PPM (5) legitimate user attacker R R R Victim V 68

What is Pushback? r Mechanism that lets a router ask adjacent upstream routers to limit the traffic rate r How it works: A congested router asks other adjacent routers to limit the rate of traffic for that particular aggregate. m Router sends pushback message m Received routers propagates pushback m 69

Outline r IPsec r Security in Routing r DDo. S at Network Layer and IP Traceback r IPv 6 Security 70

IPv 4 Security Limitations r IP packets can be sniffed r IP addresses can be spoofed r IP connections can be hijacked 71

IPv 6 Security Features r Two header extensions proposed for IPv 6 security: m Authentication Header (AH): ensures authenticity and integrity of datagram m Encrypted Security Payload (ESP): contains encrypted data r Security Associations (SAs) used for senders and receivers to agree on security requirements, e. g. , cipher to be used r These are very similar to respective IPsec concepts 72

IPv 6 Limitations: Mandatory IPsec r IPv 6 mandates IPsec support Myth: “So IPv 6 has improved security” r IPsec already exists for IPv 4 r Problems with IPsec deployment as a general end- to-end security mechanism r Deployment of IPsec (v 6) has similar problems as those of IPsec (v 4). So IPsec (v 6) is not deployed as a general end-to-end security mechanism… 73

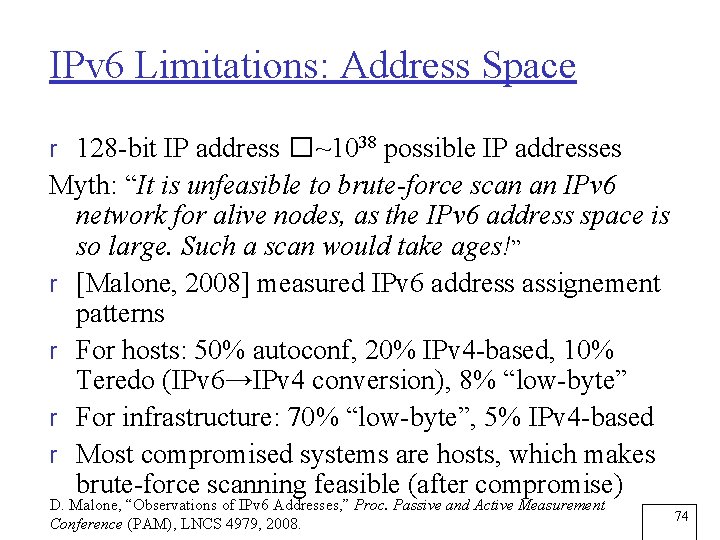
IPv 6 Limitations: Address Space r 128 -bit IP address � ~1038 possible IP addresses Myth: “It is unfeasible to brute-force scan an IPv 6 network for alive nodes, as the IPv 6 address space is so large. Such a scan would take ages!” r [Malone, 2008] measured IPv 6 address assignement patterns r For hosts: 50% autoconf, 20% IPv 4 -based, 10% Teredo (IPv 6→IPv 4 conversion), 8% “low-byte” r For infrastructure: 70% “low-byte”, 5% IPv 4 -based r Most compromised systems are hosts, which makes brute-force scanning feasible (after compromise) D. Malone, “Observations of IPv 6 Addresses, ” Proc. Passive and Active Measurement Conference (PAM), LNCS 4979, 2008. 74

IPv 6 Limitations: Autoconfiguration and Address Resolution r Based on Neighbor Discovery (ND) messages in ICMPv 6 r Stateless autoconfiguration more powerful than IPv 4 counterpart…but also provides more potential vectors for attackers to exploit r Less support in Layer 2 machines for mitigation of ND attacks r Secure Neighbor Discovery (SEND) was specified for mitigating ND security threats, employing: m m m Cryptographically-Generated Addresses (CGAs) RSA signatures (RSA signature option) Certificates r Not widely supported (e. g. , in Windows XP/Vista/7) 75

IPv 6 Conclusions r IPv 6 is in its infancy: m Few attack tools publicly available m Many bugs to be discovered… r IPv 6 not widely supported in intrusion detection systems (yet) r Much training is needed for IPv 6 networks 76

Final Remarks r IPsec provides network layer security (IPv 4): authentication, encapsulation, crypto key setup r Routing protocols (e. g. , RIP) prone to attacks r Do. S attacks possible at network layer m Mitigation: ingress filtering, traceback, etc. r IPv 6 may offer better security (in theory) m In practice, attacks can still occur m Training and safeguards needed for IPv 6 networks 77

Acknowledgement r These slides are partially based on W. Stallings, Network Security Essentials, Pearson, 2011, http: //williamstallings. com/Network. Security/Net. Sec 5 e. Instructor/ (Ch. 9) B. Rathore, “Router and Routing Protocol Attacks”, http: //www. slideshare. net/vaceitunofist/router-and-routingprotocol-attacks F. Gont, “The Truth about IPv 6 Security, ” Future. Net 2010, http: //www. gont. com. ar/talks/futurenet 2010/fgontfuturenet 2010 -ipv 6 -security. ppt 78