IPSec IP Security IPSec 126 Groep T Leuven









- Slides: 26

IPSec IP Security (IPSec) 1/26 Groep T Leuven – Information department 2003 -2004 - Information management 1

IP Security (IPSec) • • IPSec overview Authentication Header (AH) Encapsulating Security Payload (ESP) Internet Key Exchange (IKE) Main Mode negotiation Quick Mode negotiation Retransmit behavior 2/26 Groep T Leuven – Information department 2003 -2004 - Information management 2

Overall Architecture (RFC 1825) • Framework for security protocols to provide: – Data integrity – Data authentication – Data confidentiality – Security association management – Key management 3/26 Groep T Leuven – Information department 2003 -2004 - Information management 3

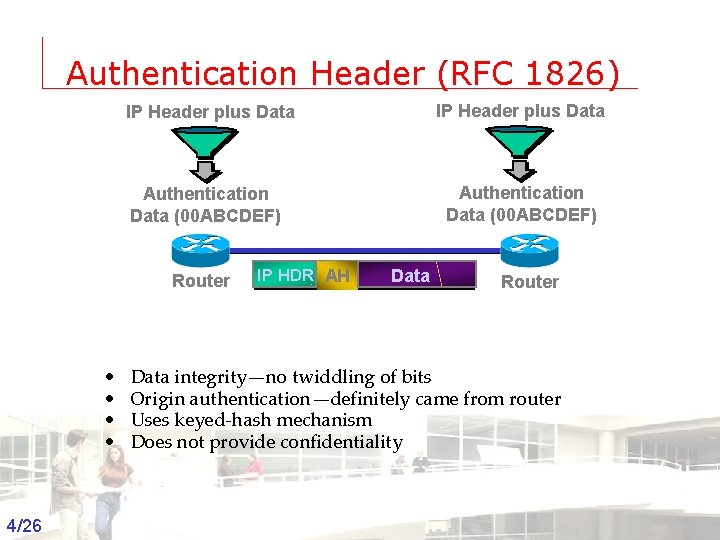
Authentication Header (RFC 1826) IP Header plus Data Authentication Data (00 ABCDEF) Router • • IP HDR AH Data Router Data integrity—no twiddling of bits Origin authentication—definitely came from router Uses keyed-hash mechanism Does not provide confidentiality 4/26 Groep T Leuven – Information department 2003 -2004 - Information management 4

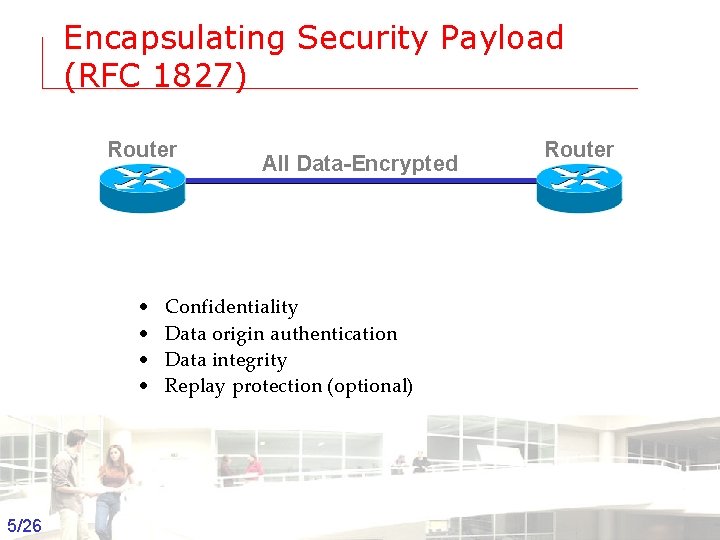
Encapsulating Security Payload (RFC 1827) Router • • All Data-Encrypted Router Confidentiality Data origin authentication Data integrity Replay protection (optional) 5/26 Groep T Leuven – Information department 2003 -2004 - Information management 5

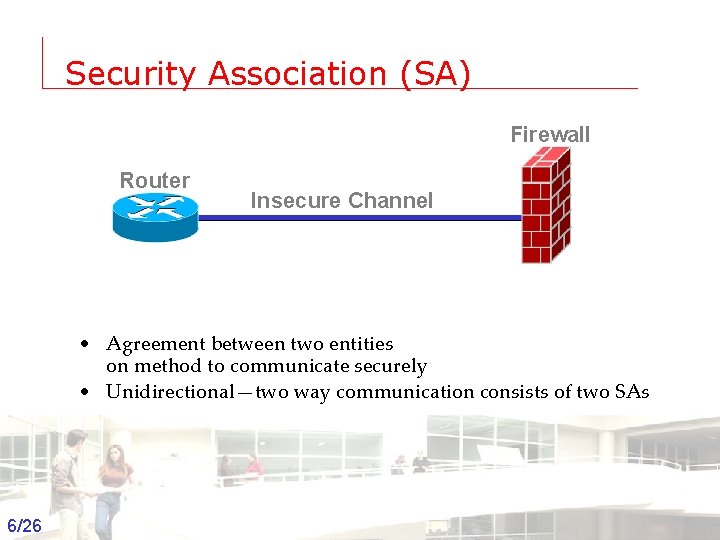
Security Association (SA) Firewall Router Insecure Channel • Agreement between two entities on method to communicate securely • Unidirectional—two way communication consists of two SAs 6/26 Groep T Leuven – Information department 2003 -2004 - Information management 6

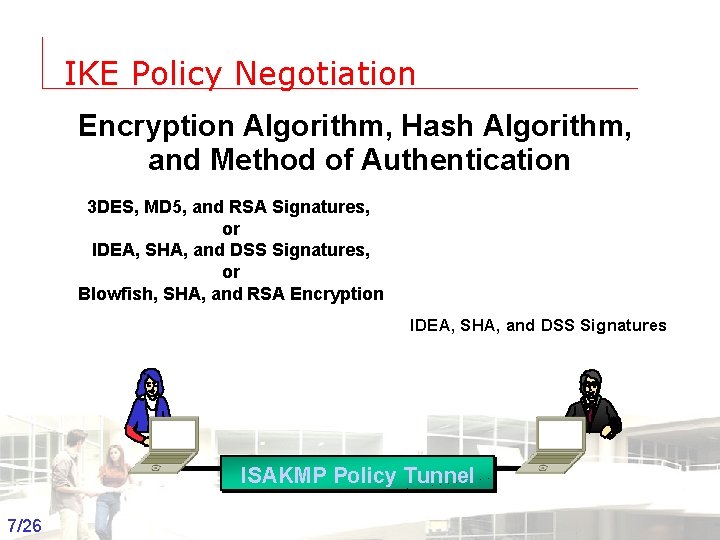
IKE Policy Negotiation Encryption Algorithm, Hash Algorithm, and Method of Authentication 3 DES, MD 5, and RSA Signatures, or IDEA, SHA, and DSS Signatures, or Blowfish, SHA, and RSA Encryption IDEA, SHA, and DSS Signatures ISAKMP Policy Tunnel 7/26 Groep T Leuven – Information department 2003 -2004 - Information management 7

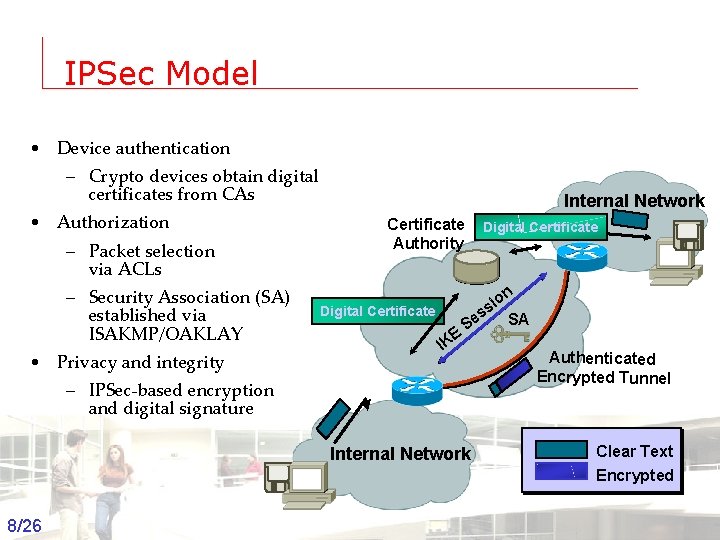
IPSec Model • Device authentication – Crypto devices obtain digital certificates from CAs • Authorization – Packet selection via ACLs – Security Association (SA) established via ISAKMP/OAKLAY • Privacy and integrity Internal Network Certificate Authority Digital Certificate E IK Digital Certificate on i ss SA e S – IPSec-based encryption and digital signature Authenticated Encrypted Tunnel Internal Network 8/26 Groep T Leuven – Information department 2003 -2004 - Information management Clear Text Encrypted 8

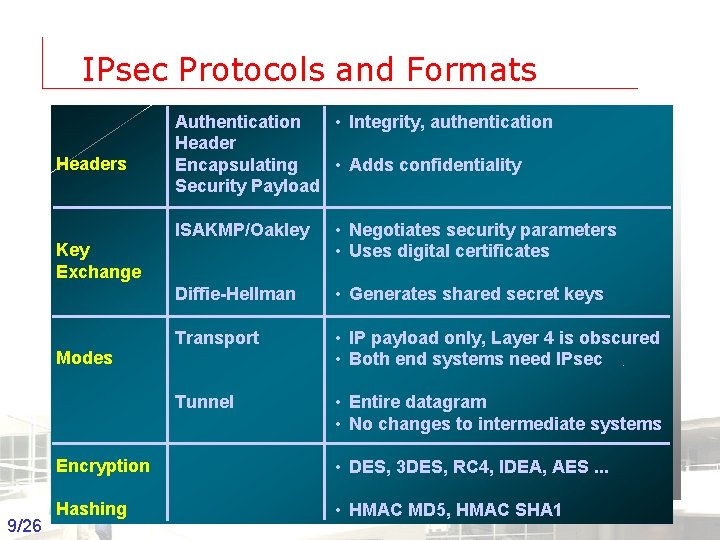
IPsec Protocols and Formats Headers Authentication • Integrity, authentication Header Encapsulating • Adds confidentiality Security Payload ISAKMP/Oakley • Negotiates security parameters • Uses digital certificates Diffie-Hellman • Generates shared secret keys Transport • IP payload only, Layer 4 is obscured • Both end systems need IPsec Tunnel • Entire datagram • No changes to intermediate systems Key Exchange Modes Encryption • DES, 3 DES, RC 4, IDEA, AES. . . Hashing • HMAC MD 5, HMAC SHA 1 9/26 Groep T Leuven – Information department 2003 -2004 - Information management 9

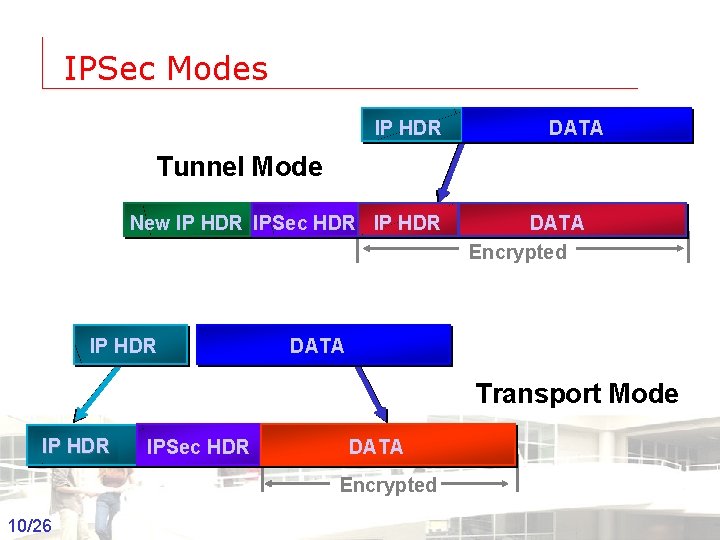
IPSec Modes IP HDR DATA Tunnel Mode New IP HDR IPSec HDR IP HDR DATA Encrypted DATA Transport Mode IP HDR IPSec HDR DATA Encrypted 10/26 Groep T Leuven – Information department 2003 -2004 - Information management 10

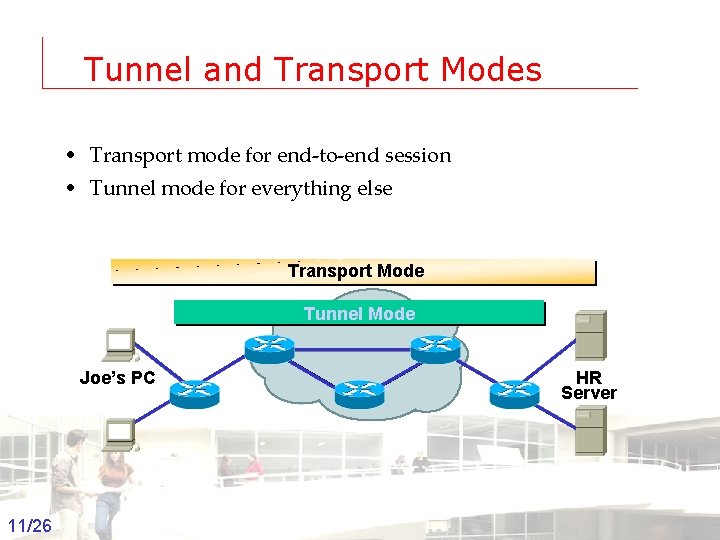
Tunnel and Transport Modes • Transport mode for end-to-end session • Tunnel mode for everything else Transport Mode Tunnel Mode Joe’s PC 11/26 Groep T Leuven – Information department HR Server 2003 -2004 - Information management 11

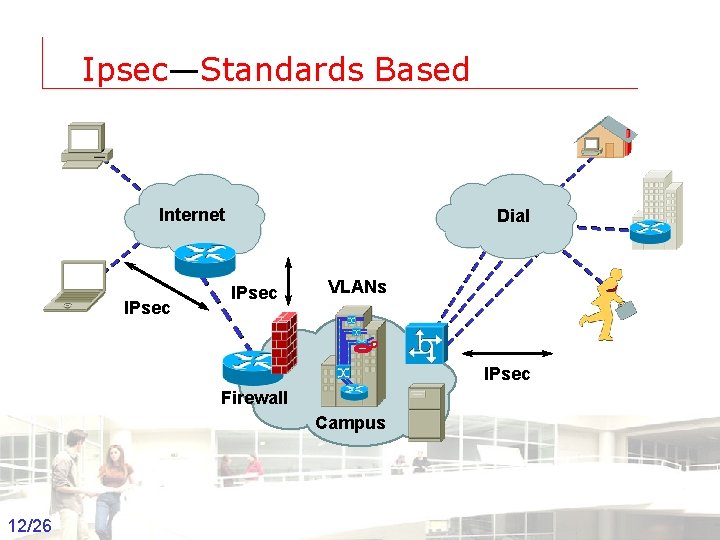
Ipsec—Standards Based Internet IPsec Dial IPsec VLANs IPsec Firewall Campus 12/26 Groep T Leuven – Information department 2003 -2004 - Information management 12

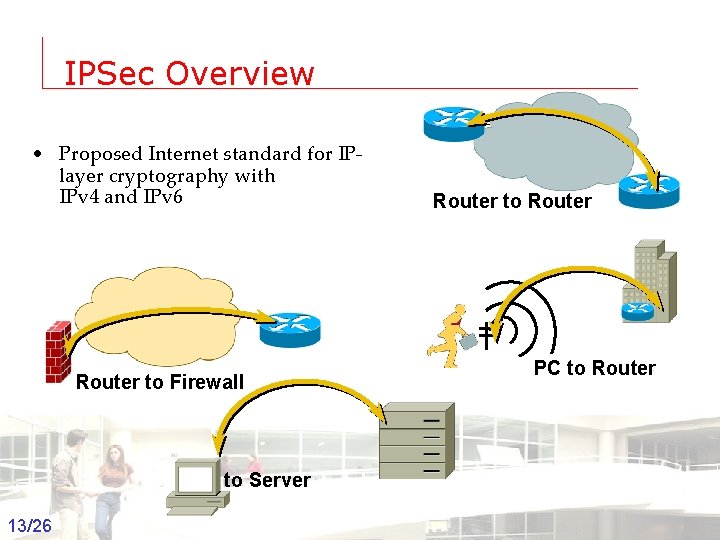
IPSec Overview • Proposed Internet standard for IPlayer cryptography with IPv 4 and IPv 6 Router to Firewall Router to Router PC to Server 13/26 Groep T Leuven – Information department 2003 -2004 - Information management 13

IPSec Process • Initiating the IPSec session – Phase one—exchanging keys – Phase two—setting up security associations • Encrypting/decrypting packets • Rebuilding security associations • Timing out security associations 14/26 Groep T Leuven – Information department 2003 -2004 - Information management 14

Initiating the IPSec Session Phase One — ISAKMP • Internet Security Association Key Management Protocol (ISAKMP) • Both sides need to agree on the ISAKMP security parameters (ISAKMP SADB) – ISAKMP parameters • Encryption algorithm • Hash algorithm • Authentication method • Diffie-Hellman modulus • Group lifetime 15/26 Groep T Leuven – Information department 2003 -2004 - Information management 15

Initiating the IPSec Session Phase Two • Both sides need to agree on the IPSec security parameters (IPSec SADB) • IPSec parameters – IPSec peer • Endpoint of IPSec tunnel – IPSec proxy • Traffic to be encrypted/decrypted – IPSec transform • Encryption and hashing – IPSec lifetime • Phase two SA regeneration time 16/26 Groep T Leuven – Information department 2003 -2004 - Information management 16

Encrypting and Decrypting Packets • Phase one and phase two completes • Security Associations (SA) are created at both IPSec endpoints • Using the negotiated SADB information – Outbound packets are encrypted – Inbound packets are decrypted 17/26 Groep T Leuven – Information department 2003 -2004 - Information management 17

Rebuilding Security Associations • To ensure that keys are not compromised they are periodically refreshed • Security associations will be rebuilt when: – The lifetime expires, or – Data volume has been exceeded, or – Another SA is attempted with identical parameters 18/26 Groep T Leuven – Information department 2003 -2004 - Information management 18

Security Associations • Combination of mutually agreed security services, protection mechanisms, and cryptographic keys • ISAKMP SA • IPSec SAs – One for inbound traffic – One for outbound traffic • Security Parameters Index (SPI) – Helps identify an SA • Creating SAs – Main Mode for ISAKMP SA – Quick Mode for IPSec SAs 19/26 Groep T Leuven – Information department 2003 -2004 - Information management 19

IPSec Headers • Authentication Header (AH) – Provides data origin authentication, data integrity, and replay protection for the entire IP datagram • Encapsulating Security Payload (ESP) – Provides data origin authentication, data integrity, replay protection, and data confidentiality for the ESP-encapsulated portion of the packet 20/26 Groep T Leuven – Information department 2003 -2004 - Information management 20

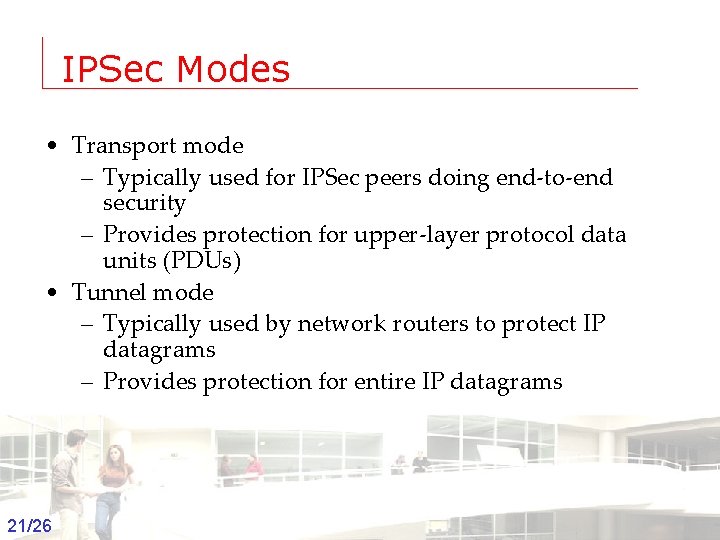
IPSec Modes • Transport mode – Typically used for IPSec peers doing end-to-end security – Provides protection for upper-layer protocol data units (PDUs) • Tunnel mode – Typically used by network routers to protect IP datagrams – Provides protection for entire IP datagrams 21/26 Groep T Leuven – Information department 2003 -2004 - Information management 21

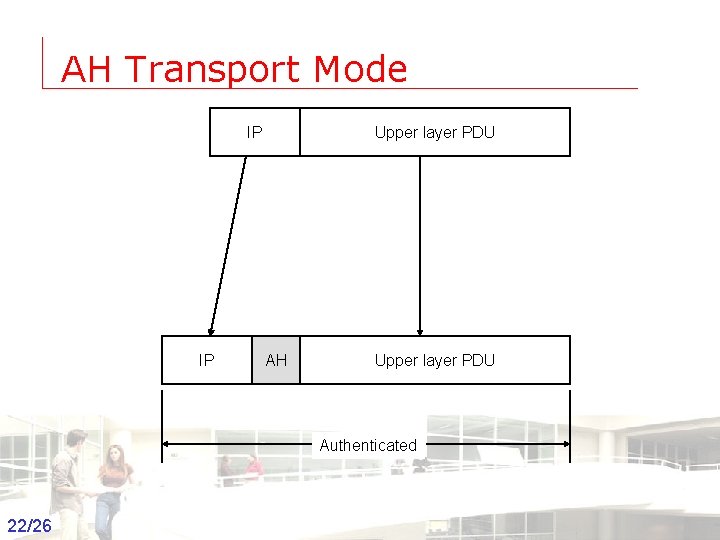
AH Transport Mode IP IP Upper layer PDU AH Upper layer PDU Authenticated 22/26 Groep T Leuven – Information department 2003 -2004 - Information management 22

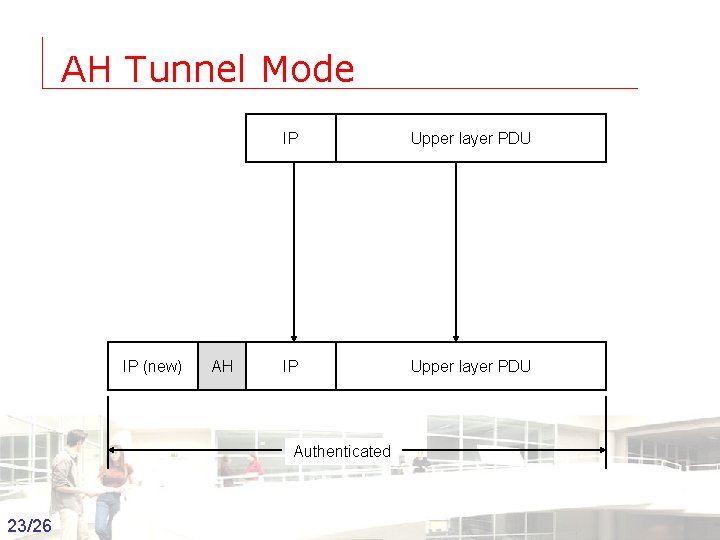
AH Tunnel Mode IP (new) AH IP Upper layer PDU Authenticated 23/26 Groep T Leuven – Information department 2003 -2004 - Information management 23

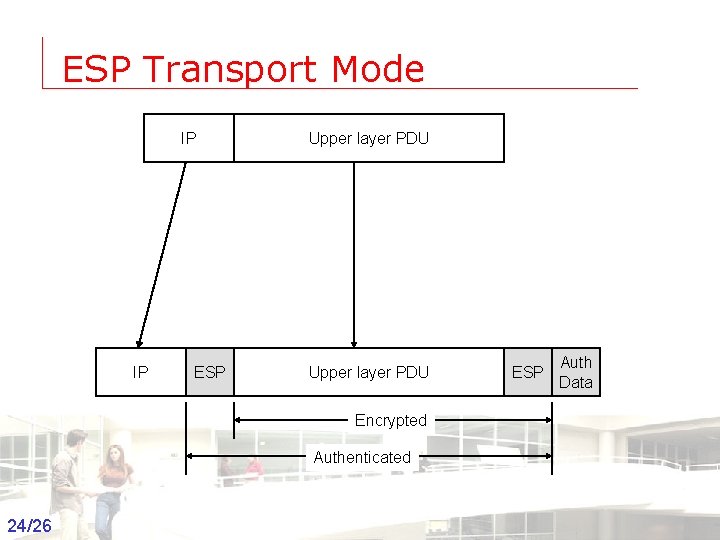
ESP Transport Mode IP IP ESP Upper layer PDU ESP Auth Data Encrypted Authenticated 24/26 Groep T Leuven – Information department 2003 -2004 - Information management 24

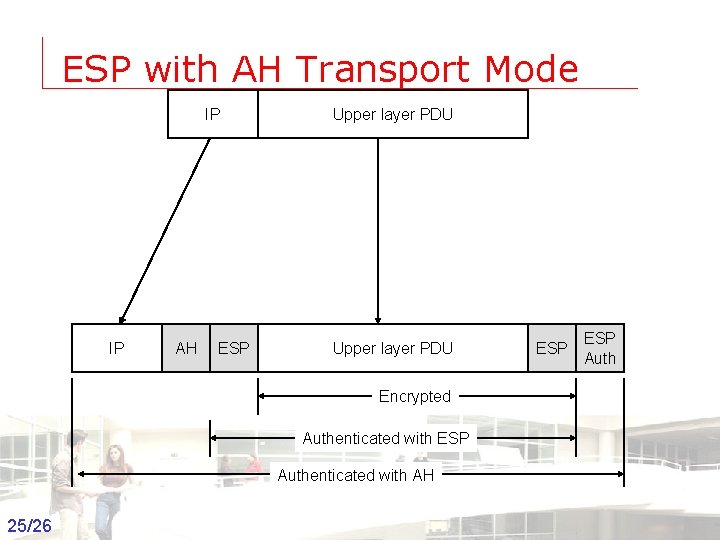
ESP with AH Transport Mode IP IP AH ESP Upper layer PDU ESP Auth Encrypted Authenticated with ESP Authenticated with AH 25/26 Groep T Leuven – Information department 2003 -2004 - Information management 25

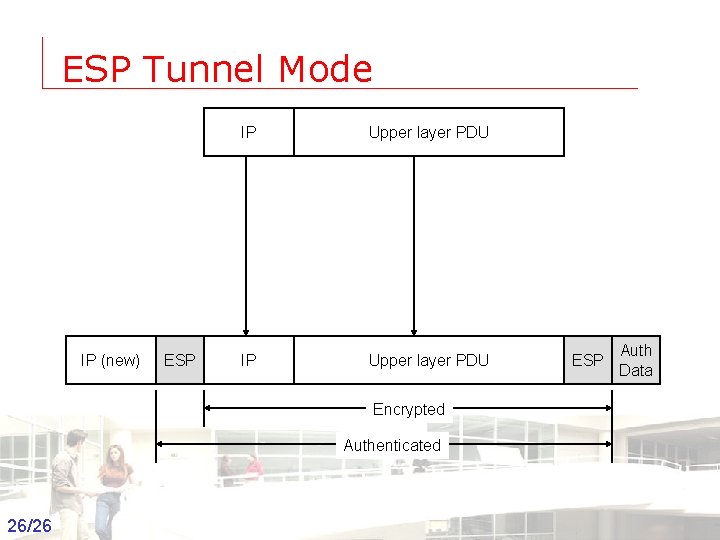
ESP Tunnel Mode IP (new) ESP IP Upper layer PDU ESP Auth Data Encrypted Authenticated 26/26 Groep T Leuven – Information department 2003 -2004 - Information management 26