ISA 662 IKE Key management for IPSEC Prof

















- Slides: 28

ISA 662 IKE Key management for IPSEC Prof. Ravi Sandhu

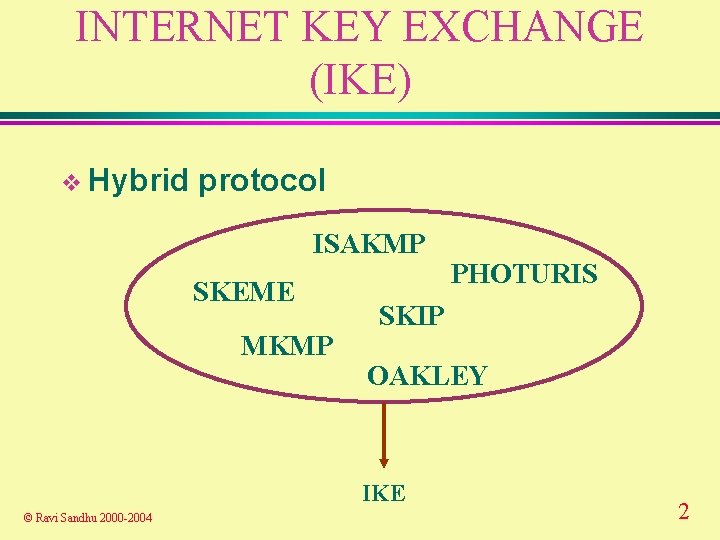
INTERNET KEY EXCHANGE (IKE) v Hybrid protocol ISAKMP SKEME MKMP SKIP OAKLEY IKE © Ravi Sandhu 2000 -2004 PHOTURIS 2

ISAKMP v Internet security association and key management protocol v separates key management from key exchanges v complex general protocol used in a specific way in IKE Ø can v for apply to protocols other than IPSEC uses UDP over IP © Ravi Sandhu 2000 -2004 3

IKE v ISAKMP phase 1: establishes ISAKMP SA Ø Main mode (DH with identity protection) Ø Aggressive mode (DH without identity protection) v Between phases Ø New group mode v ISAKMP phase 2: establishes SA for target protocol Ø Quick mode © Ravi Sandhu 2000 -2004 4

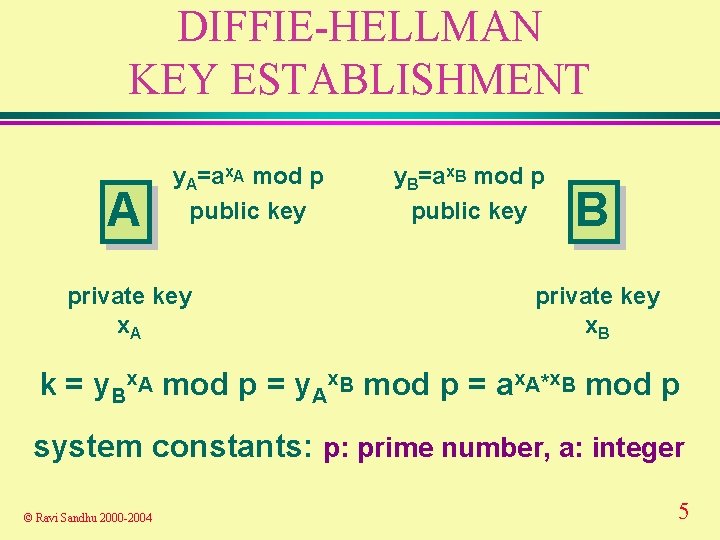
DIFFIE-HELLMAN KEY ESTABLISHMENT A y. A=ax. A mod p public key private key x. A y. B=ax. B mod p public key B private key x. B k = y. Bx. A mod p = y. Ax. B mod p = ax. A*x. B mod p system constants: p: prime number, a: integer © Ravi Sandhu 2000 -2004 5

PERFECT FORWARD SECRECY v Use a different DH key-pair on each exchange v DH public keys need to be authenticated Ø authentication techniques can be done by many v Loss of long-term (authentication) keys does not disclose session keys © Ravi Sandhu 2000 -2004 6

PHASE 1 AUTHENTICATION ALTERNATIVES v public-key signature v preshared-key v public-key encryption v revised public-key encryption © Ravi Sandhu 2000 -2004 7

COOKIE EXCHANGE v v Phase 1 employs cookie exchange to thwart (not prevent) denial of service attacks A -> B: Cookie_Request Ø v B -> A: Cookie_Response Ø v A’s cookie, 64 bit random number includes A and B’s cookies all further Phase 1 and Phase 2 messages include both cookies Ø Ø ISAKMP SA is identified by both cookies IPSEC protocol SA is identified by SPI © Ravi Sandhu 2000 -2004 8

COOKIE GENERATION v hash over Ø IP Source and Destination Address Ø UDP Source and Destination Ports Ø a locally generated random secret Ø timestamp © Ravi Sandhu 2000 -2004 9

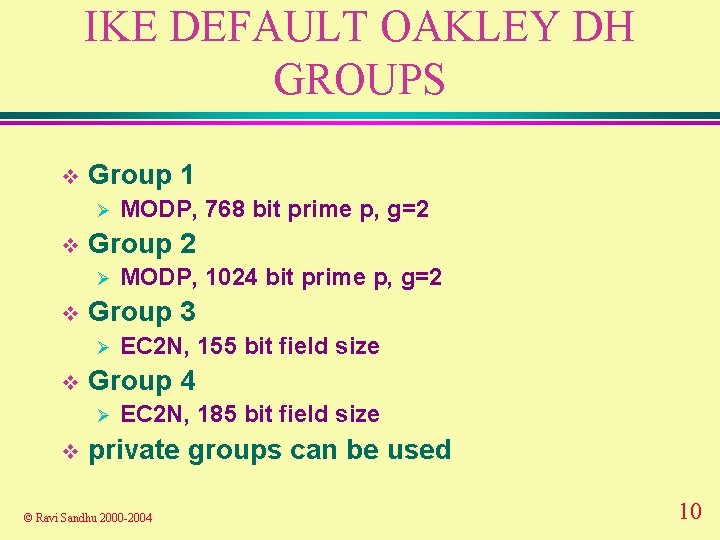
IKE DEFAULT OAKLEY DH GROUPS v Group 1 Ø v Group 2 Ø v EC 2 N, 155 bit field size Group 4 Ø v MODP, 1024 bit prime p, g=2 Group 3 Ø v MODP, 768 bit prime p, g=2 EC 2 N, 185 bit field size private groups can be used © Ravi Sandhu 2000 -2004 10

IKE NOTATION © Ravi Sandhu 2000 -2004 11

IKE NOTATION © Ravi Sandhu 2000 -2004 12

SKEYS, HASH AND SIG © Ravi Sandhu 2000 -2004 13

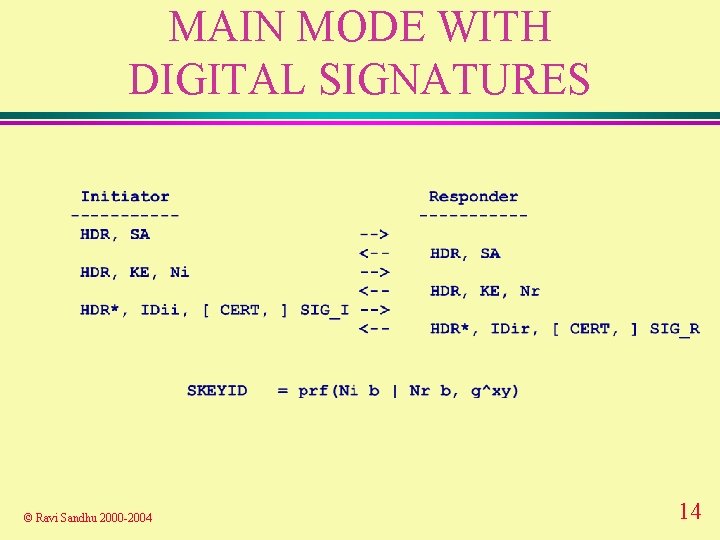
MAIN MODE WITH DIGITAL SIGNATURES © Ravi Sandhu 2000 -2004 14

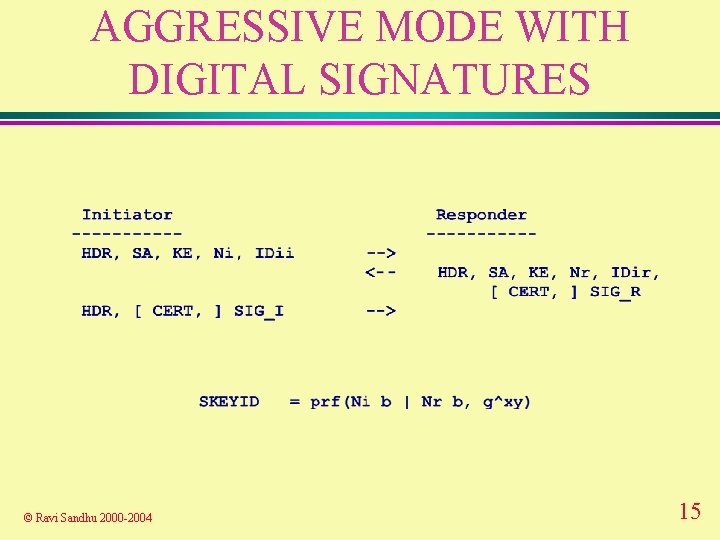
AGGRESSIVE MODE WITH DIGITAL SIGNATURES © Ravi Sandhu 2000 -2004 15

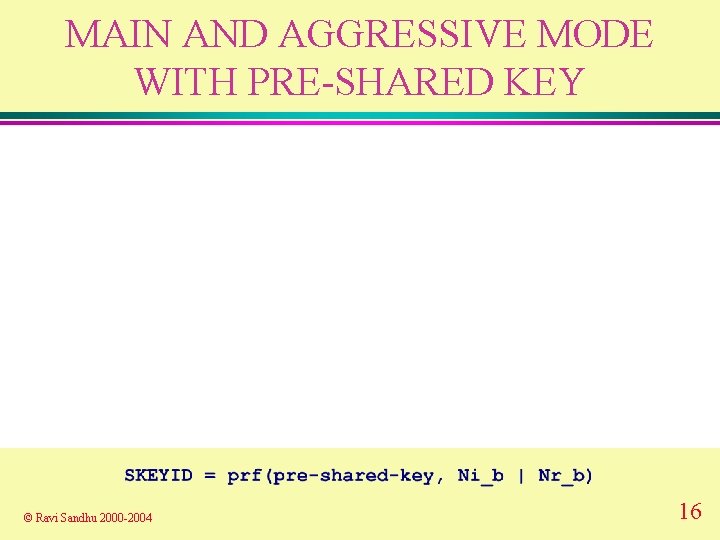
MAIN AND AGGRESSIVE MODE WITH PRE-SHARED KEY © Ravi Sandhu 2000 -2004 16

MAIN MODE WITH PUBLIC KEY ENCRYPTION © Ravi Sandhu 2000 -2004 17

AGGRESSIVE MODE WITH PUBLIC KEY ENCRYPTION © Ravi Sandhu 2000 -2004 18

AUTHENTICATION WITH PUBLIC-KEY ENCRYPTION does not provide non-repudiation v provides additional security since attacked must break both v Ø Ø DH key exchange public-key encryption provides identity protection in aggressive mode v revised protocol reduces public-key operations v © Ravi Sandhu 2000 -2004 19

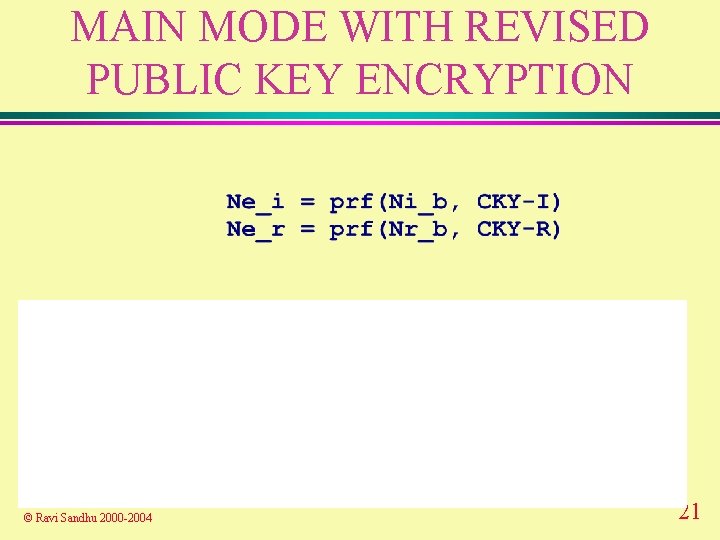
MAIN MODE WITH REVISED PUBLIC KEY ENCRYPTION © Ravi Sandhu 2000 -2004 20

MAIN MODE WITH REVISED PUBLIC KEY ENCRYPTION © Ravi Sandhu 2000 -2004 21

AGGRESSIVE MODE WITH REVISED PUBLIC KEY ENCRYPTION © Ravi Sandhu 2000 -2004 22

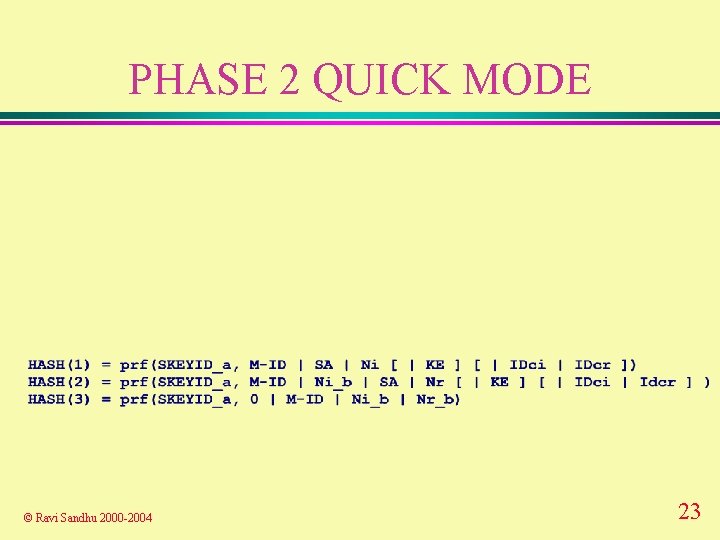
PHASE 2 QUICK MODE © Ravi Sandhu 2000 -2004 23

PHASE 2 QUICK MODE © Ravi Sandhu 2000 -2004 24

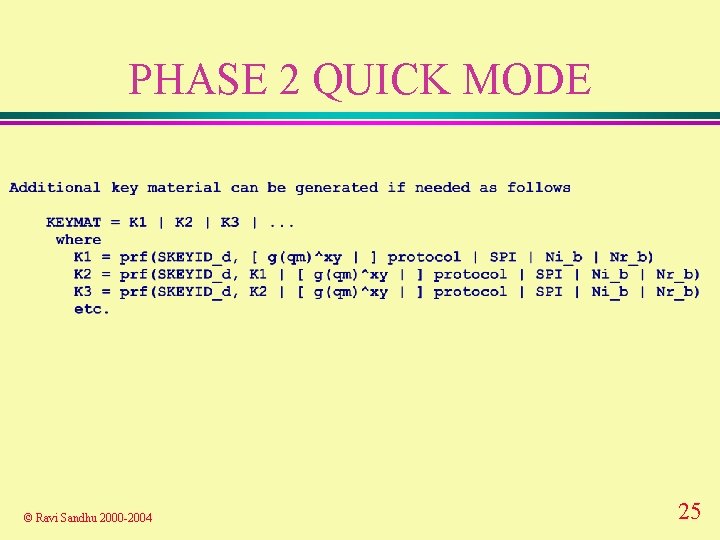
PHASE 2 QUICK MODE © Ravi Sandhu 2000 -2004 25

PHASE 2 QUICK MODE © Ravi Sandhu 2000 -2004 26

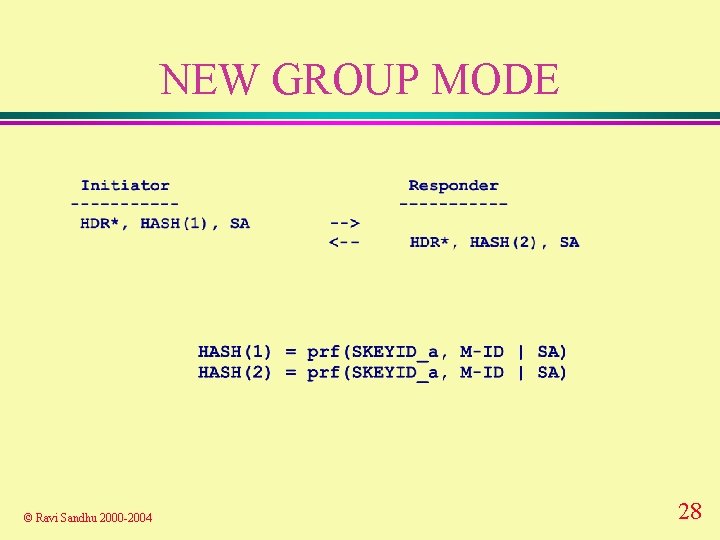
NEW GROUP MODE v sandwiched between phase 1 and 2 v group can be negotiated in phase 1 v new group mode allows nature of group to be hidden Ø in phase 1 only group id is communicated in clear © Ravi Sandhu 2000 -2004 27

NEW GROUP MODE © Ravi Sandhu 2000 -2004 28