LWIP LTEWLAN Radio Level Integration with IPsec Tunnel















- Slides: 30


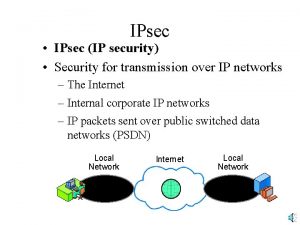
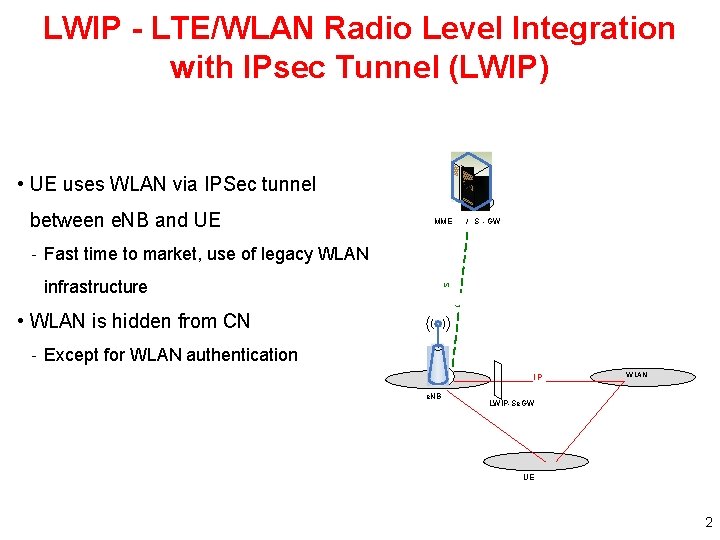
LWIP - LTE/WLAN Radio Level Integration with IPsec Tunnel (LWIP) • UE uses WLAN via IPSec tunnel between e. NB and UE MME / S - GW - Fast time to market, use of legacy WLAN S infrastructure 1 • WLAN is hidden from CN - Except for WLAN authentication IP e. NB WLAN LWIP-Se. GW UE 2

Motivation • LWIP was introduced in Release-13 to address the operator needs – To leverage the capacity available from the large incumbent WLAN network base where modifications to WLAN – As required by LWA would not be feasible because of hardware, architectural or operational constraints • The use of WLAN resources in downlink and uplink is controlled by the e. NB, and bypasses the LTE user plane protocol stack • LWIP allows use of combined LTE and WLAN capacity for a user by allowing either inter-bearer distribution or intra-bearer per IP flow distribution across the LTE and WLAN radio links 3

Overview • LWIP is controlled by e. NB, based on UE measurement reporting – LWIP feature allows a UE in RRC_CONNECTED to be configured by the e. NB to utilize WLAN radio resources via IPsec tunnelling • Connectivity between e. NB and WLAN is over IP (TS 36. 300 Section 22 A. 3) 4

LWIP Tunnel • IP packets transferred between the UE and LWIP-Se. GW are encapsulated using IPSec –Provide security to the packets that traverse WLAN –Uplink and downlink data supported over WLAN –Multiple bearers can be offloaded via IPSec • The IP packets are then transported between the LWIPSe. GW and e. NB – The end to end path between the UE and e. NB via the WLAN network is referred to as the LWIP tunnel 5

Security and Transparence • For security reasons IPsec tunnel is terminated in LWIP-Se. GW in e. NB • Single IPSec tunnel per UE for UL and DL data • IPsec tunnel is transparent to WLAN infrastructure • There are no standardized network interfaces in LWIP 6

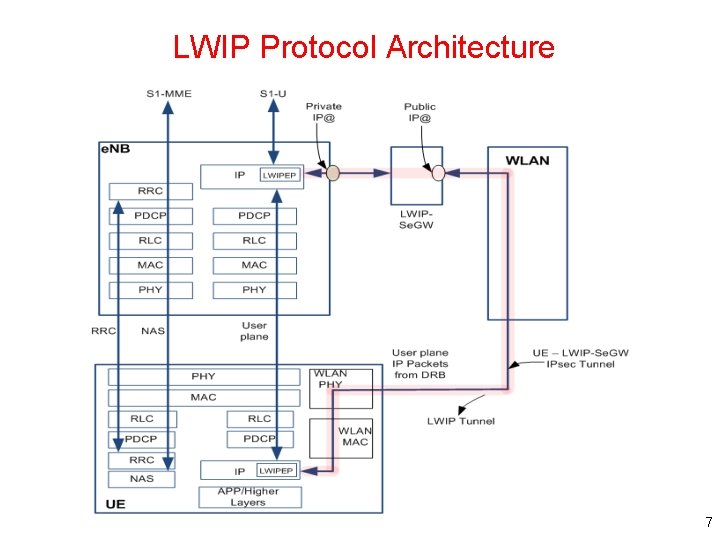
LWIP Protocol Architecture 7

LWIP Protocol Stack 8

Security Gateway (Se. GW) • The use of insecure third party broadband for backhauling mobile voice and multimedia data from small cells exposes the mobile operator’s core network to IP-based attacks, user identity theft and fraud • The Se. GW provides market-leading IP Security/Internet Key Exchange Version 2 (IPsec/IKEv 2) tunnel performance – The Se. GW is a carrier class gateway for secure, scalable fixed mobile convergence solutions • The Se. GW provides mobile operators with a complete Security Gateway solution for security and aggregation of 3 G (HNB), 4 G LTE (He. NB) and 3 GPP 2 cdma cellular small cells, including femtocells, picocells or metrocells 9

Definitions, Symbols and Abbreviations • The terms and definitions given in TR 21. 905 – Data Radio Bearer -DRB – Internet Protocol -IP – LTE/WLAN Radio Level Integration Using Ipsec(security) Tunnel -LWIP – LWIP Encapsulation Protocol -LWIPEP – Generic Routing and Encapsulation -GRE – Packet Data Convergence Protocol -PDCP – Protocol Data Unit -PDU – Radio Resource Control -RRC – Service Access Point -SAP – Service Data Unit -SDU 10

Bearer over LWIP Tunnel • The data bearer refers to the EPS bearer mapped to the Data Radio Bearer (DRB) which is maintained on the LTE side – The DRB configuration on the LTE access corresponding to the data bearer using IPsec resources shall not be released • A single IPSec tunnel is used per UE for all the data bearers that are configured to send and/ or receive data over WLAN – Each data bearer may be configured so that traffic for that bearer can be routed over the IPsec tunnel in either only downlink or both uplink and downlink over WLAN • The RRC_Connection_Reconfiguration message provides the necessary parameters for the UE to initiate the establishment of the IPSec tunnel for the DRB 11

DL/UL of a Data Bearer • For the DL of a data bearer, the packets received from the IPsec tunnel are forwarded directly to upper layers • For the UL, the e. NB configures the UE to route the uplink data either via LTE or via WLAN using RRC signaling – If routed via WLAN then all UL traffic of the data bearer is offloaded to the WLAN – UL bearer packets sent over the LWIP tunnel are encapsulated using LWIPEP as specified in TS 36. 361 with the ‘Key’ field in the LWIPEP header populated with the DRB Identity associated with offloaded UL bearer 12

Release of a LWIP Tunnel • The release of the IPSec tunnel is initiated by the e. NB • Upon receiving the Handover Command or on transition to RRC_IDLE state, the UE shall autonomously release IPsec tunnel configuration and the use of it by the data bearers • A UE supporting LWIP may be configured for WLAN measurements as per subclause 22 A. 1. 5. 13

LWIP Mobility • The same mobility concept as specified in 22 A. 1. 4 for LWA is also used for LWIP • Since WT node does not exist in LWIP operation, WT related description and procedures does not apply to LWIP • Mobility Set should be considered as the set of WLAN APs across which UE can perform mobility without informing the e. NB, when applying the concept for LWIP operation 14

Issue with Multiple WLAN Interworking • E-UTRAN does not configure LWIP with DC, LWA or RCLWI simultaneously for the same UE. • If LWIP and RAN assisted WLAN interworking are simultaneously configured for the same UE, in RRC Connected, the UE only applies LWIP 15

LWIP Operation • LWIP Tunnel Setup and Data Bearer Configuration The UE uses the parameters in the new radio resource configuration to setup the IPsec tunnel with the LWIP-Se. GW to complete the establishment of the LWIP tunnel with the e. NB over the WLAN access e. NB may add or remove data bearers to utilise the LWIP tunnel at any time after the establishment of the LWIP tunnel by sending the RRCConnection. Reconfiguration message to the UE 16

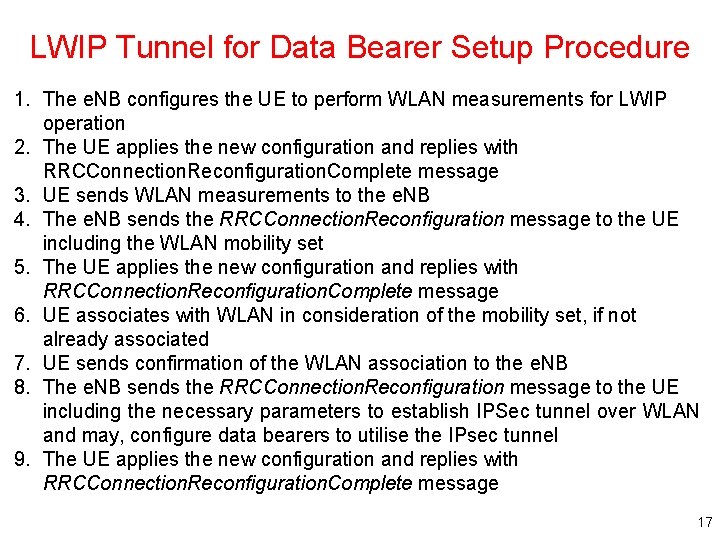
LWIP Tunnel for Data Bearer Setup Procedure 1. The e. NB configures the UE to perform WLAN measurements for LWIP operation 2. The UE applies the new configuration and replies with RRCConnection. Reconfiguration. Complete message 3. UE sends WLAN measurements to the e. NB 4. The e. NB sends the RRCConnection. Reconfiguration message to the UE including the WLAN mobility set 5. The UE applies the new configuration and replies with RRCConnection. Reconfiguration. Complete message 6. UE associates with WLAN in consideration of the mobility set, if not already associated 7. UE sends confirmation of the WLAN association to the e. NB 8. The e. NB sends the RRCConnection. Reconfiguration message to the UE including the necessary parameters to establish IPSec tunnel over WLAN and may, configure data bearers to utilise the IPsec tunnel 9. The UE applies the new configuration and replies with RRCConnection. Reconfiguration. Complete message 17

Reconfiguration to Remove WLAN Resources 18

Remove Reconfiguration Procedure UE and e. NB have the LWIP tunnel setup via WLAN 1. The UE is configured to receive data from a data bearer over the LWIP tunnel 2. The e. NB determines that it needs to remove the WLAN resources for the data bearer 3. The e. NB sends the RRCConnection. Reconfiguration message to the UE including the necessary parameters to remove WLAN resources for the data bearer 4. The UE applies the new configuration and replies with RRCConnection. Reconfiguration. Complete message 5. UE stops receiving data for the data bearer over the LWIP tunnel 19

LWIP Tunnel Release 20

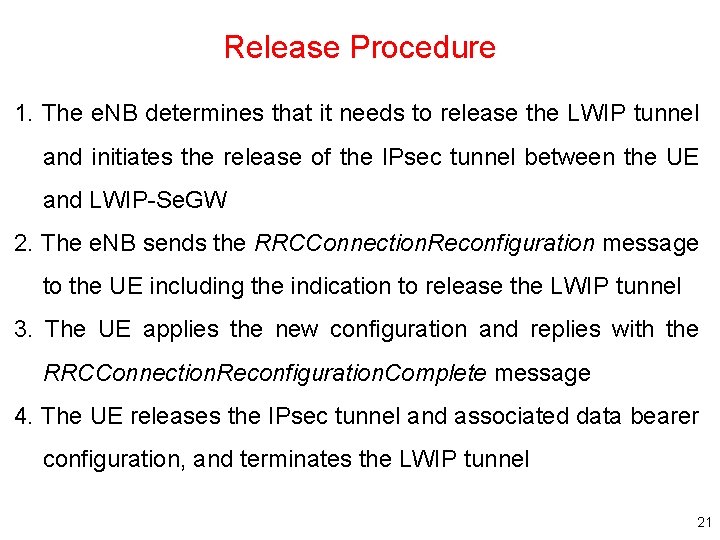
Release Procedure 1. The e. NB determines that it needs to release the LWIP tunnel and initiates the release of the IPsec tunnel between the UE and LWIP-Se. GW 2. The e. NB sends the RRCConnection. Reconfiguration message to the UE including the indication to release the LWIP tunnel 3. The UE applies the new configuration and replies with the RRCConnection. Reconfiguration. Complete message 4. The UE releases the IPsec tunnel and associated data bearer configuration, and terminates the LWIP tunnel 21

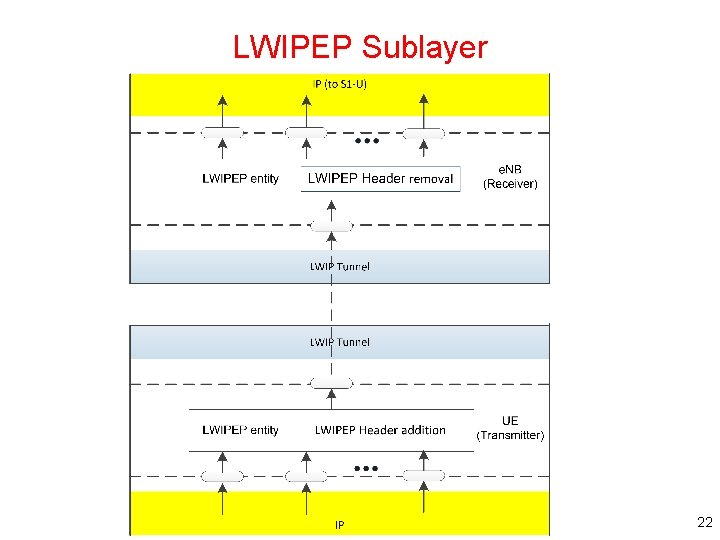
LWIPEP Sublayer 22

LWIPEP Entity • RRC is in control of the LWIPEP configuration • Functions of the LWIPEP sublayer are performed by LWIPEP entities • For an LWIPEP entity configured at the e. NB – There is a peer LWIPEP entity configured at the UE and vice versa • The LWIPEP entity responsible for – Encapsulating LWIPEP SDUs is referred to as the transmitter – Decapsulating LWIPEP PDUs is referred to as the receiver 23

LWIPEP Operation • An LWIPEP entity receives/delivers LWIPEP SDUs from/to upper layers (i. e. IP) and sends/receives LWIPEP PDUs to/from its peer LWIPEP entity via an LWIP Tunnel • In the uplink direction: – At the UE, when an LWIPEP entity receives an LWIPEP SDU from upper layers, it constructs the corresponding LWIPEP PDU and delivers it to lower layers – At the e. NB, when an LWIPEP entity receives an LWIPEP PDU from lower layers, it reassembles the corresponding LWIPEP SDU and delivers it to upper layers 24

LWIP Services • Services provided to upper layers – The following services are provided by LWIPEP to upper layers (i. e. IP): transfer of user plane data • Services expected from lower layers – The following services are expected by LWIPEP from lower layers (i. e. LWIP Tunnel): transfer of user plane data • Functions – The following functions are supported by the LWIPEP sublayer: • Transfer of user plane data • Identification of the DRB identity to which the LWIPEP SDU belongs 25

LWIP Procedures • Data transfer procedures – UL data transfer procedures • When receiving an LWIPEP SDU from upper layers, the LWIPEP entity shall form the LWIPEP PDU – Handling of unknown, unforeseen and erroneous protocol data – When an LWIPEP entity receives an LWIPEP PDU that contains reserved or invalid values, the LWIPEP entity shall: • discard the received PDU 26

LWIPEP Data PDU • An LWIPEP data PDU consists of the LWIPEP header and the LWIPEP SDU 27

LWIPEP Data Bit Strings • LWIPEP data PDU – An LWIPEP PDU is a bit string that is byte aligned (i. e. multiple of 8 bits) in length • Bit strings are represented by tables in which – The most significant bit is the leftmost bit of the first line of the table, – The least significant bit is the rightmost bit on the last line of the table, and – More generally the bit string is to be read from left to right and then in the reading order of the lines • The bit order of each parameter field within an LWIPEP PDU is represented with – the first and most significant bit in the leftmost bit and – the last and least significant bit in the rightmost bit 28

Formats and Parameters • The LWIPEP Header is a GRE header as specified in RFC 2890 and has a fixed size of eight bytes including the Key field • The UE shall set the 5 LSB's of the Key field in the GRE header to the DRB Identity associated with the LWIPEP SDU and set the remaining MSB's to '0‘ • All other optional fields are unused, and the values of other fields shall be set as specified in RFC 2784 [4] and RFC 2890 29

References • 3 GPP TS 36. 300: “E-UTRA and E-UTRAN Overall Description; Stage 2”, Section 22 A. 3 • 3 GPP TS 36. 361: “LTE/WLAN Radio Level Integration Using IPsec Tunnel (LWIP) Encapsulation; Protocol Specification” • 3 GPP TR 21. 905: “Vocabulary for 3 GPP Specifications” • 3 GPP TS 36. 331: “E-UTRA RRC Protocol Specification” • IETF RFC 2784: “Generic Routing Encapsulation (GRE)” • IETF RFC 2890: “Key and Sequence Number Extensions to GRE” 30
 Lwip ipsec
Lwip ipsec Vpnsa
Vpnsa Vpp ipsec
Vpp ipsec Ipsec protocol suite
Ipsec protocol suite Ssl protocol stack
Ssl protocol stack Ip security ipsec
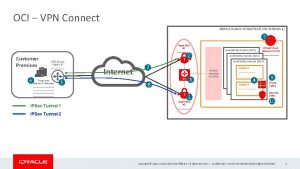
Ip security ipsec Oracle cloud ipsec
Oracle cloud ipsec Ipsec
Ipsec Ipsec
Ipsec Vpn and ipsec concepts
Vpn and ipsec concepts Ipsec key management
Ipsec key management Ipsec
Ipsec Ipsec
Ipsec Ovn ipsec
Ovn ipsec Ncsu vpn
Ncsu vpn Untangle ipsec vpn setup
Untangle ipsec vpn setup Awin support
Awin support Forward integration and backward integration
Forward integration and backward integration Forward and backward integration
Forward and backward integration Simultaneous integration examples
Simultaneous integration examples Middle level integration
Middle level integration How deep is the channel tunnel
How deep is the channel tunnel Tunnel terminology
Tunnel terminology Hard rock
Hard rock Induction preheating furnace
Induction preheating furnace Anton anderson memorial tunnel
Anton anderson memorial tunnel Tunnel sequence interview
Tunnel sequence interview Depyrogenation tunnel zones
Depyrogenation tunnel zones Tunnel finisher
Tunnel finisher Polytunnel irrigation
Polytunnel irrigation Zebedee tunnel
Zebedee tunnel