T 305 DIGITAL COMMUNICATIONS T 305 Digital Communication










- Slides: 71

T 305: DIGITAL COMMUNICATIONS T 305: Digital Communication Faculty of Computer Studies Information Technology and Computing Block 5: Part 1 Channel Coding Arab Open University-Lebanon Tutorial 19 Block V 1

T 305: DIGITAL COMMUNICATIONS Plan n Topic 1: Introduction n Topic 2: Differential Coding and Scrambling n Topic 3: Codes for Error Detection n Topic 4: Codes for Error Correction n Topic 5: Interleaving Arab Open University-Lebanon Tutorial 19 Block V 2

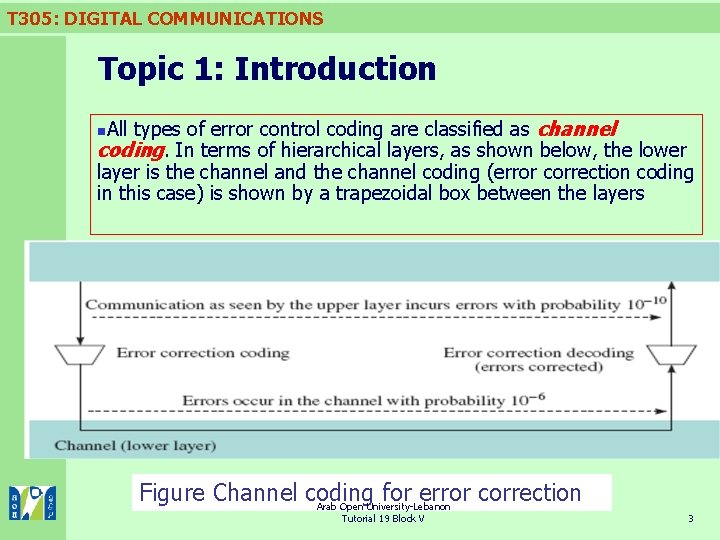
T 305: DIGITAL COMMUNICATIONS Topic 1: Introduction All types of error control coding are classified as channel coding. In terms of hierarchical layers, as shown below, the lower layer is the channel and the channel coding (error correction coding in this case) is shown by a trapezoidal box between the layers n Figure Channel coding for error correction Arab Open University-Lebanon Tutorial 19 Block V 3

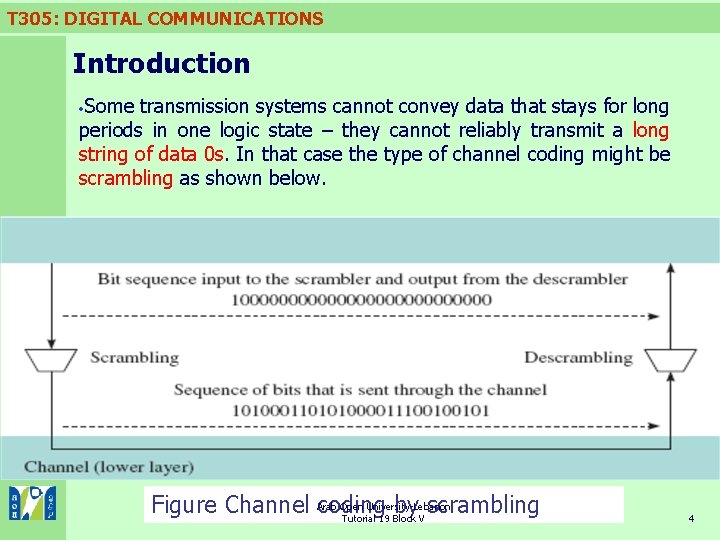
T 305: DIGITAL COMMUNICATIONS Introduction Some transmission systems cannot convey data that stays for long periods in one logic state – they cannot reliably transmit a long string of data 0 s. In that case the type of channel coding might be scrambling as shown below. Open University-Lebanon Figure Channel Arab coding by scrambling Tutorial 19 Block V 4

T 305: DIGITAL COMMUNICATIONS Introduction üNotice that channel coding involves processes at both ends of the channel. üWhatever coding is done at the transmitter is ‘undone’ at the receiver. üScrambling, for example, breaks up long strings of 0 s before sending the data through the channel, but the descrambling recreates them at the end of the channel. Arab Open University-Lebanon Tutorial 19 Block V 5

T 305: DIGITAL COMMUNICATIONS Plan n Topic 1: Introduction n Topic 2: Differential Coding and Scrambling n Topic 3: Codes for Error Detection n Topic 4: Codes for Error Correction n Topic 5: Interleaving Arab Open University-Lebanon Tutorial 19 Block V 6

T 305: DIGITAL COMMUNICATIONS Topic 2: Differential Coding and Scrambling The main characteristic that differential coding confers on data’s immunity to being complemented (means all 1 s are changed to 0 s and all 0 s are changed to 1 s). n Differential coding is not generally used on its own, but is frequently part of the process of coding or is combined directly with modulation schemes. n One noticeable feature of both differential coding and scrambling is that they are 100% efficient. For every bit input to a scrambler there is one, and only one, output bit. n Arab Open University-Lebanon Tutorial 19 Block V 7

T 305: DIGITAL COMMUNICATIONS Differential Coding n Differential coding produces an output in which the information is contained in differences between successive bits. n. The coding rule is as follows. If the input bit is a 1, the output changes state (if the previous output was 1, the current output will be 0; if the previous output was 0, the current output will be 1). n If the input bit is a 0, the current output remains the same as the previous output. n Arab Open University-Lebanon Tutorial 19 Block V 8

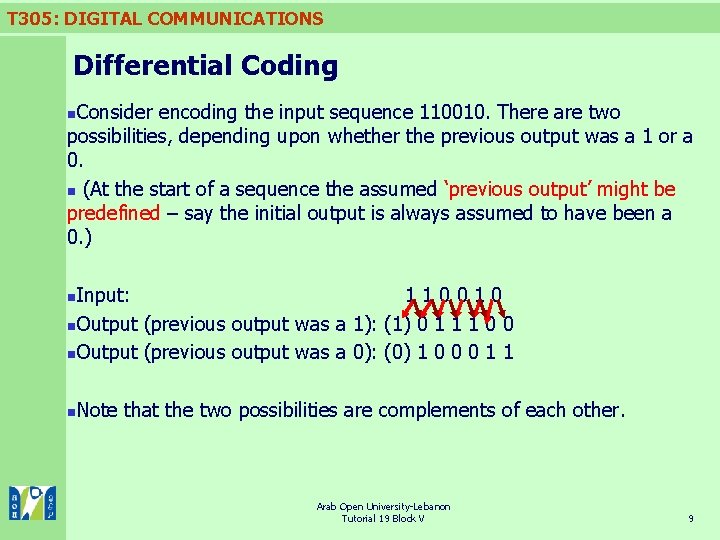
T 305: DIGITAL COMMUNICATIONS Differential Coding Consider encoding the input sequence 110010. There are two possibilities, depending upon whether the previous output was a 1 or a 0. n (At the start of a sequence the assumed ‘previous output’ might be predefined – say the initial output is always assumed to have been a 0. ) n Input: 110010 n. Output (previous output was a 1): (1) 0 1 1 1 0 0 n. Output (previous output was a 0): (0) 1 0 0 0 1 1 n n Note that the two possibilities are complements of each other. Arab Open University-Lebanon Tutorial 19 Block V 9

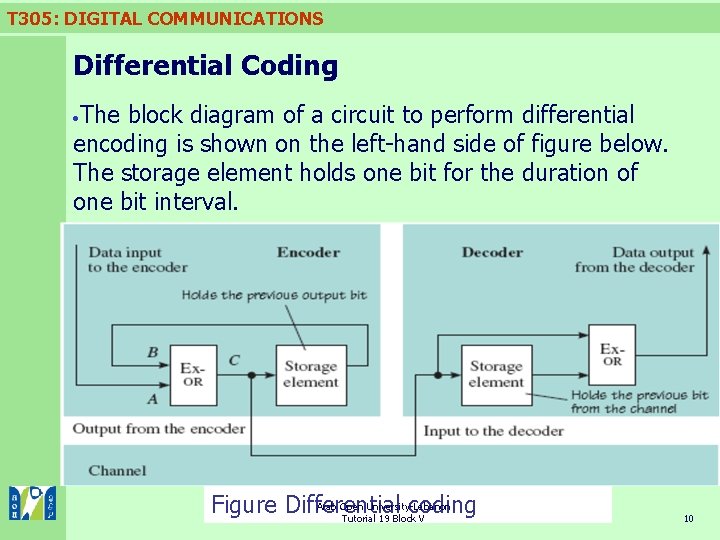
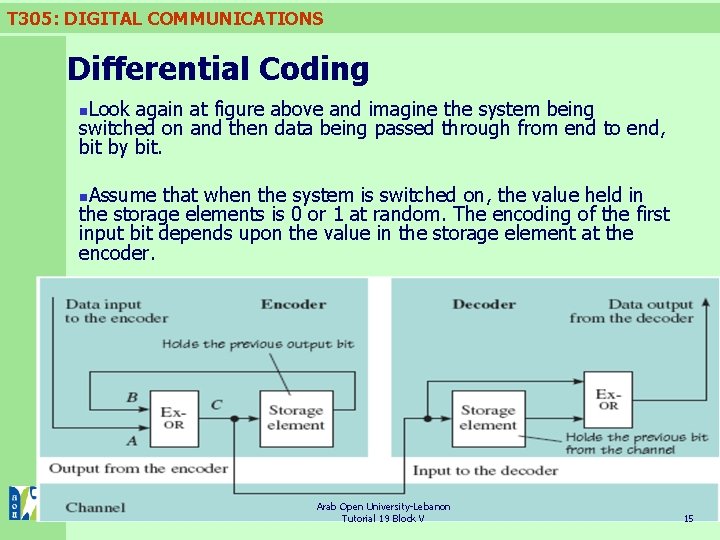
T 305: DIGITAL COMMUNICATIONS Differential Coding The block diagram of a circuit to perform differential encoding is shown on the left-hand side of figure below. The storage element holds one bit for the duration of one bit interval. Arab Open University-Lebanon Figure Differential coding Tutorial 19 Block V 10

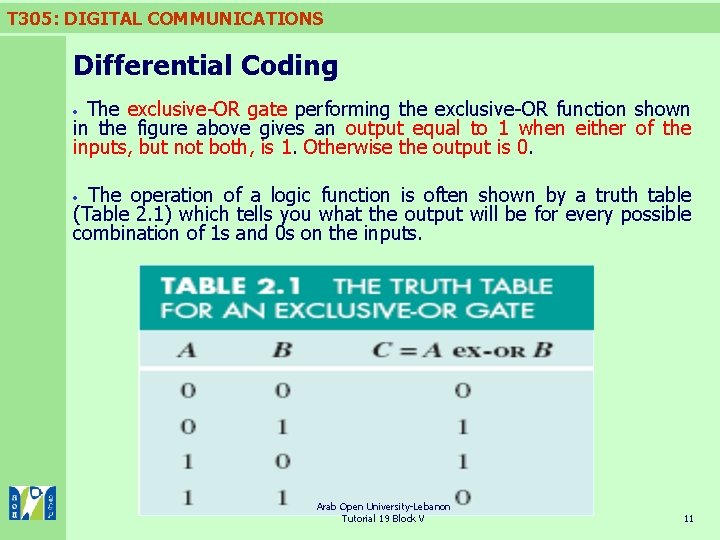
T 305: DIGITAL COMMUNICATIONS Differential Coding The exclusive-OR gate performing the exclusive-OR function shown in the figure above gives an output equal to 1 when either of the inputs, but not both, is 1. Otherwise the output is 0. The operation of a logic function is often shown by a truth table (Table 2. 1) which tells you what the output will be for every possible combination of 1 s and 0 s on the inputs. Arab Open University-Lebanon Tutorial 19 Block V 11

T 305: DIGITAL COMMUNICATIONS Differential Coding Although in the exclusive-OR function the two inputs are equivalent, think of one of the inputs, say A, as a ‘control’ and look at how the value of the control affects the relationship between the other input (B) and the output (C). n. Notice that in figure above at the start of the coding of a sequence the previous output bit is held in the storage element. n So whether the coded output is one sequence or its complement depends upon the initial state of this storage element. n Arab Open University-Lebanon Tutorial 19 Block V 12

T 305: DIGITAL COMMUNICATIONS Differential Coding For decoding, we need an output 0 if the currently received bit is the same as the previously received bit, and a 1 if it is different. n Looking at Table 2. 1, you can see that the exclusive-OR function will do this if the inputs are two successive bits. n The decoder may therefore be constructed as shown on the right-hand side of figure above, where the storage element holds the previously received bit. n Arab Open University-Lebanon Tutorial 19 Block V 13

T 305: DIGITAL COMMUNICATIONS Differential Coding With differential coding there are two possible codings for every binary sequence, but the decoder does not need to ‘know’ which of the two sequences it is decoding. n Since it just looks for differences between successive bits, whether the data is complemented or not is irrelevant. n This is the main reason for using differential encoding, because there are circumstances in which the absolute value of the received bit (whether it is a 1 or a 0) is unknown, but changes of value are easily detected. An example of this is differential phase shift keying (DPSK). n Arab Open University-Lebanon Tutorial 19 Block V 14

T 305: DIGITAL COMMUNICATIONS Differential Coding Look again at figure above and imagine the system being switched on and then data being passed through from end to end, bit by bit. n Assume that when the system is switched on, the value held in the storage elements is 0 or 1 at random. The encoding of the first input bit depends upon the value in the storage element at the encoder. n Arab Open University-Lebanon Tutorial 19 Block V 15

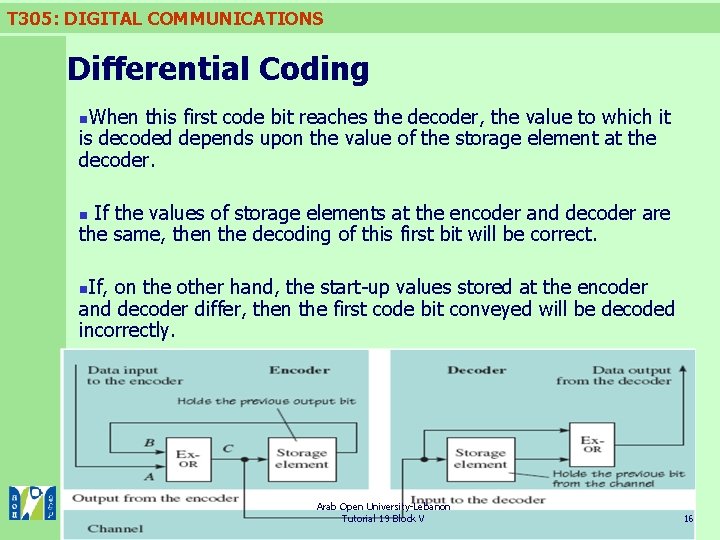
T 305: DIGITAL COMMUNICATIONS Differential Coding When this first code bit reaches the decoder, the value to which it is decoded depends upon the value of the storage element at the decoder. n If the values of storage elements at the encoder and decoder are the same, then the decoding of this first bit will be correct. n If, on the other hand, the start-up values stored at the encoder and decoder differ, then the first code bit conveyed will be decoded incorrectly. n Arab Open University-Lebanon Tutorial 19 Block V 16

T 305: DIGITAL COMMUNICATIONS Differential Coding n. In practice, systems using differential coding are typically running continuously. They may run for the duration of one call involving perhaps hundreds of thousands of bits, or for several years involving perhaps 10 15 bits or more. n. In either case, an error in one bit on start-up is of no significance whatever. n. The way in which the system synchronizes without any need for external influence, even though an error may occur on start-up, leads to differential coding being described as self-synchronizing. n. If a single code bit is inverted due to noise, it causes two errors in the decoded output at the receiver because it is involved in the decoding of two bits. n. It causes one error when it arrives at the decoder, then it is stored in the storage element at the decoder and causes an error in the next decoded bit. After that it has no effect on the data. Therefore differential encoding has an error multiplication of 2. Arab Open University-Lebanon Tutorial 19 Block V 17

T 305: DIGITAL COMMUNICATIONS Plan n Topic 1: Introduction n Topic 2: Differential Coding and Scrambling n Topic 3: Codes for Error Detection n Topic 4: Codes for Error Correction n Topic 5: Interleaving Arab Open University-Lebanon Tutorial 19 Block V 18

T 305: DIGITAL COMMUNICATIONS Topic 2: Scrambling The real data situation in which long runs of all 0 s might be quite common – due to pauses in data generation, perhaps, or when a particular channel is unused. n Scramblers, therefore, are used to break up regular patterns in data in order to make it appear random and then descramblers recover the original data at the end of the channel. n Arab Open University-Lebanon Tutorial 19 Block V 19

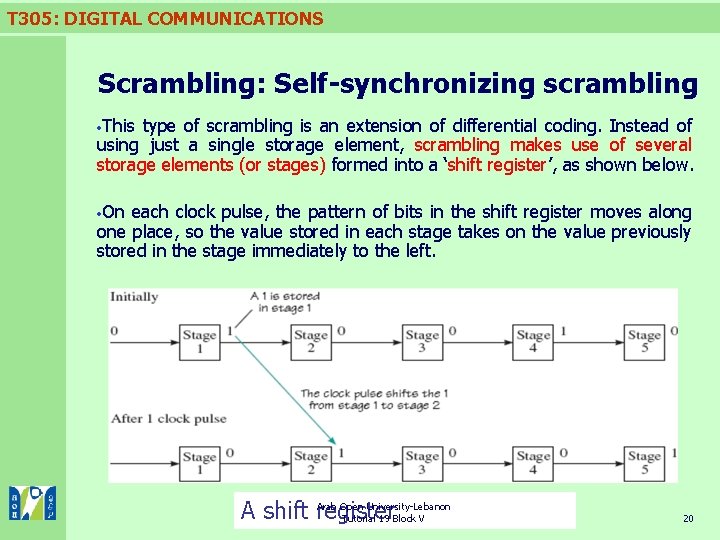
T 305: DIGITAL COMMUNICATIONS Scrambling: Self-synchronizing scrambling This type of scrambling is an extension of differential coding. Instead of using just a single storage element, scrambling makes use of several storage elements (or stages) formed into a ‘shift register’, as shown below. On each clock pulse, the pattern of bits in the shift register moves along one place, so the value stored in each stage takes on the value previously stored in the stage immediately to the left. Arab Open University-Lebanon A shift register Tutorial 19 Block V 20

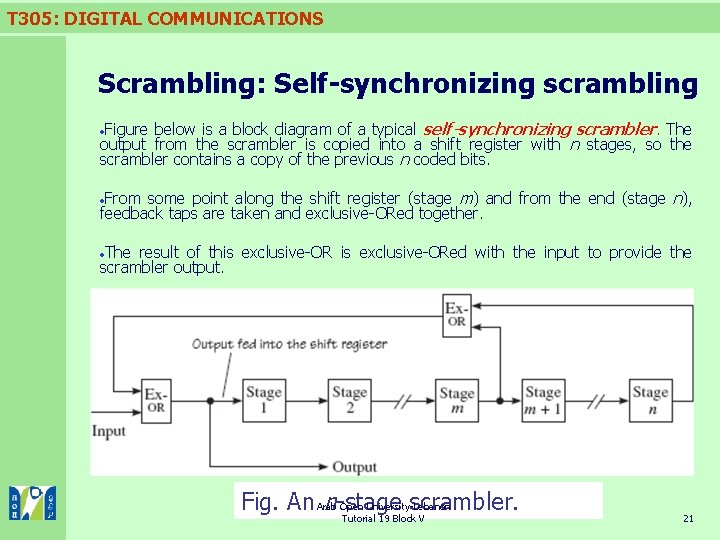
T 305: DIGITAL COMMUNICATIONS Scrambling: Self-synchronizing scrambling below is a block diagram of a typical self-synchronizing scrambler. The output from the scrambler is copied into a shift register with n stages, so the scrambler contains a copy of the previous n coded bits. Figure some point along the shift register (stage m) and from the end (stage n), feedback taps are taken and exclusive-ORed together. From The result of this exclusive-ORed with the input to provide the scrambler output. Fig. An Arab n-stage scrambler. Open University-Lebanon Tutorial 19 Block V 21

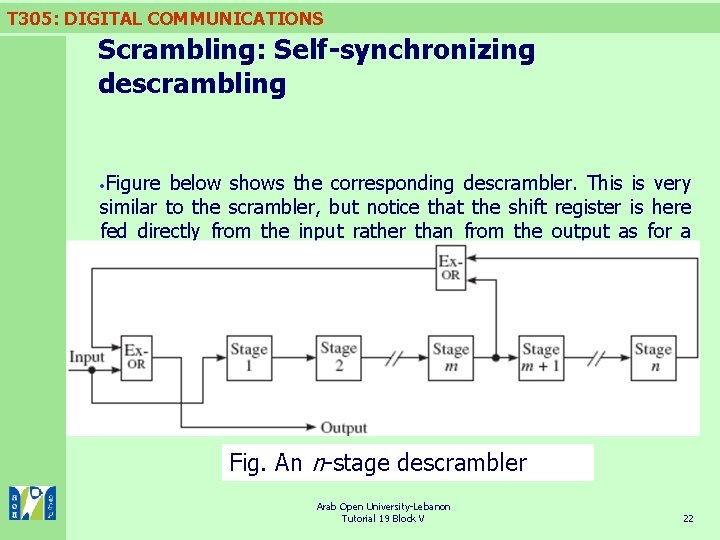
T 305: DIGITAL COMMUNICATIONS Scrambling: Self-synchronizing descrambling Figure below shows the corresponding descrambler. This is very similar to the scrambler, but notice that the shift register is here fed directly from the input rather than from the output as for a scrambler. Fig. An n-stage descrambler Arab Open University-Lebanon Tutorial 19 Block V 22

T 305: DIGITAL COMMUNICATIONS Scrambling: Self-synchronizing scrambling The encoding of each input bit (to a 1 or a 0) depends upon the value of the input bit and the feedback taps. n Since the feedback is taken from the shift register containing previous code bits, the encoding of each input bit depends upon the encoding of previous bits. n The encoding of any input sequence cannot therefore be taken in isolation, rather the encoding of a scrambler is a continuous process beginning when the device is switched on. n Furthermore, the code sequence will depend upon the starting state of the scrambler, the pattern of bits in the shift register when it is switched on. n n For an n-stage scrambler, there are 2 n possible starting states. Arab Open University-Lebanon Tutorial 19 Block V 23

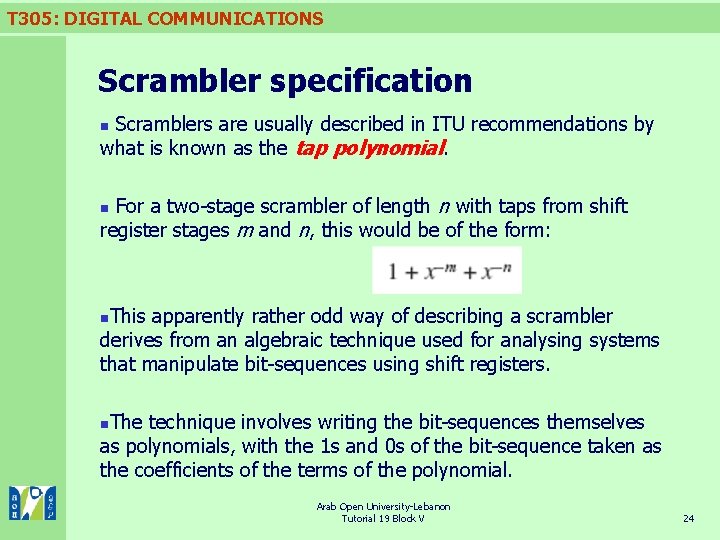
T 305: DIGITAL COMMUNICATIONS Scrambler specification Scramblers are usually described in ITU recommendations by what is known as the tap polynomial. n For a two-stage scrambler of length n with taps from shift register stages m and n, this would be of the form: n This apparently rather odd way of describing a scrambler derives from an algebraic technique used for analysing systems that manipulate bit-sequences using shift registers. n The technique involves writing the bit-sequences themselves as polynomials, with the 1 s and 0 s of the bit-sequence taken as the coefficients of the terms of the polynomial. n Arab Open University-Lebanon Tutorial 19 Block V 24

T 305: DIGITAL COMMUNICATIONS Scrambler specification x in the polynomial can be interpreted as a shift operator, such that x−n represents a delay of n bit intervals. n. The 1 + x− 3 is interpreted as 1 ‘now’, followed by 1, then 0 (because there is no x− 2), then another 1, giving 1101. n. Thus n. Notice that increasing time appears as a larger negative power to x. It is the convention to write scrambler specifications using negative powers, but they could equally well be changed to positive powers by multiplying the whole polynomial by xn: n n. In effect, this just changes the time origin by n bit intervals. Arab Open University-Lebanon Tutorial 19 Block V 25

T 305: DIGITAL COMMUNICATIONS Topic 2: Scrambling: Pseudo-random binary sequences (PRBS) general an n-stage maximal-length scrambler responds to an all 0 s input with an output sequence length of 2 n – 1 bits, provided that it is not latched. n. In n. If it were latched it would give an all 0 s output. The pattern of 1 s and 0 s in the sequence shown above looks quite random, and the same would be true for the 2 n – 1 bit-sequence from any maximal-length scrambler with an all 0 s input. n. These sequences do, in fact, have certain mathematical properties that accord with a mathematical definition of random. Among these properties are the fact that in general the 2 n – 1 bits contain 2 n/2 ones and (2 n/2) − 1 zeros, that is, as close as possible to equal numbers of 1 s and 0 s, given that the sequence has an odd number of bits. n. These sequences of 2 n – 1 bits are not truly random since they are completely determined by the scrambler. Each time we run a scrambler with a known tap polynomial and a specified starting condition on the stages, we get the same output sequence. Arab Open University-Lebanon Tutorial 19 Block V 26

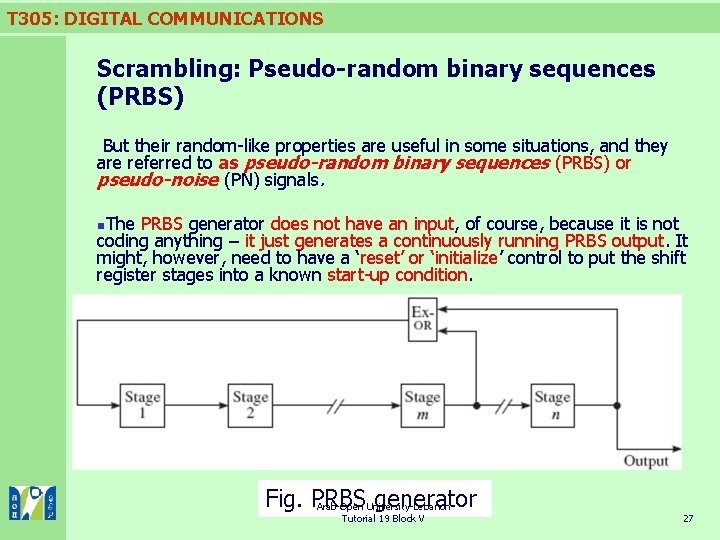
T 305: DIGITAL COMMUNICATIONS Scrambling: Pseudo-random binary sequences (PRBS) But their random-like properties are useful in some situations, and they are referred to as pseudo-random binary sequences (PRBS) or pseudo-noise (PN) signals. n. The PRBS generator does not have an input, of course, because it is not coding anything – it just generates a continuously running PRBS output. It might, however, need to have a ‘reset’ or ‘initialize’ control to put the shift register stages into a known start-up condition. Fig. PRBS generator Arab Open University-Lebanon Tutorial 19 Block V 27

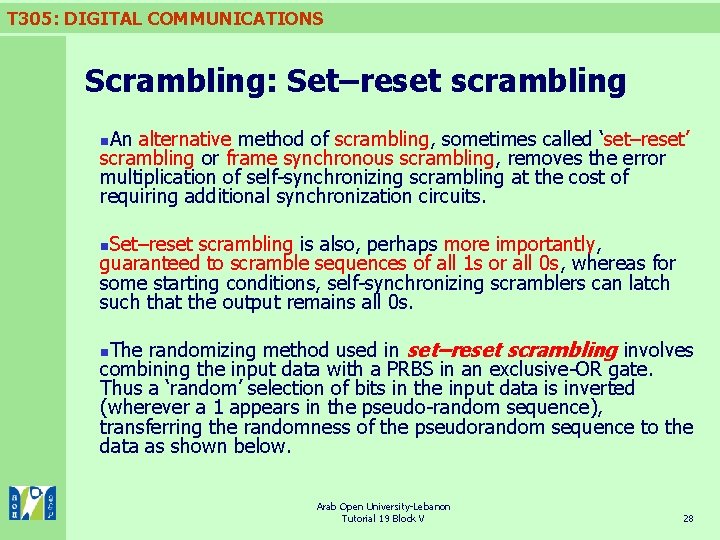
T 305: DIGITAL COMMUNICATIONS Scrambling: Set–reset scrambling An alternative method of scrambling, sometimes called ‘set–reset’ scrambling or frame synchronous scrambling, removes the error multiplication of self-synchronizing scrambling at the cost of requiring additional synchronization circuits. n Set–reset scrambling is also, perhaps more importantly, guaranteed to scramble sequences of all 1 s or all 0 s, whereas for some starting conditions, self-synchronizing scramblers can latch such that the output remains all 0 s. n The randomizing method used in set–reset scrambling involves combining the input data with a PRBS in an exclusive-OR gate. Thus a ‘random’ selection of bits in the input data is inverted (wherever a 1 appears in the pseudo-random sequence), transferring the randomness of the pseudorandom sequence to the data as shown below. n Arab Open University-Lebanon Tutorial 19 Block V 28

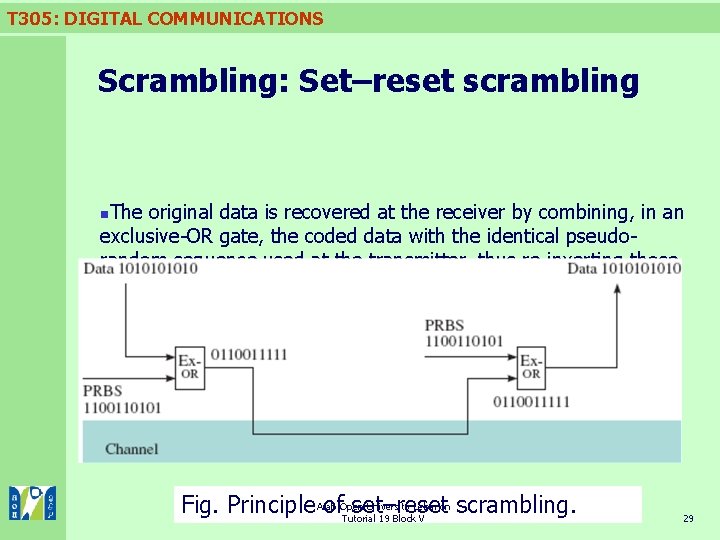
T 305: DIGITAL COMMUNICATIONS Scrambling: Set–reset scrambling The original data is recovered at the receiver by combining, in an exclusive-OR gate, the coded data with the identical pseudorandom sequence used at the transmitter, thus re-inverting those bits which were inverted at the transmitter. n University-Lebanon scrambling. Fig. Principle Arab of. Open set–reset Tutorial 19 Block V 29

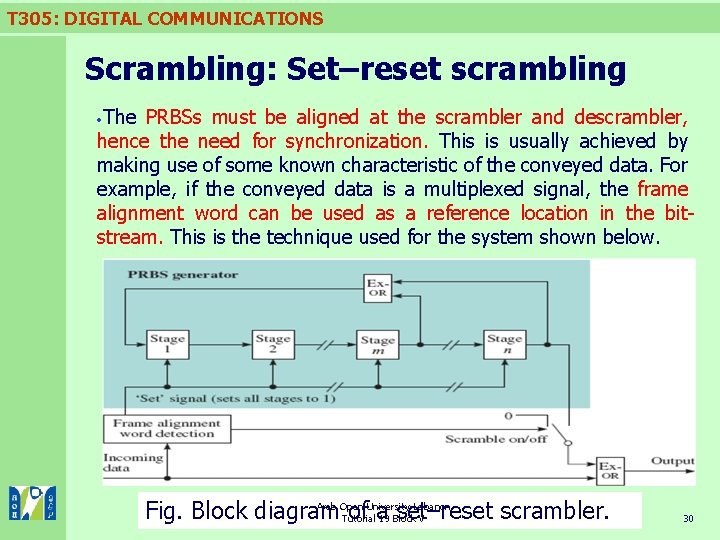
T 305: DIGITAL COMMUNICATIONS Scrambling: Set–reset scrambling The PRBSs must be aligned at the scrambler and descrambler, hence the need for synchronization. This is usually achieved by making use of some known characteristic of the conveyed data. For example, if the conveyed data is a multiplexed signal, the frame alignment word can be used as a reference location in the bitstream. This is the technique used for the system shown below. Arab Open University-Lebanon Fig. Block diagram of a 19 Block set–reset scrambler. Tutorial V 30

T 305: DIGITAL COMMUNICATIONS Scrambling: Set–reset scrambling At the end of the frame alignment word, the PRBS generators at both scrambler and descrambler are set to all 1 s, then left to run continuously until the next frame alignment word. n Since they start off in the same state at the same point in the bit-stream, the two generators are aligned. n In order for the descrambler to be able to find the frame alignment word, this section of the data is left unscrambled; hence the ‘scramble on/off’ switch. n Arab Open University-Lebanon Tutorial 19 Block V 31

T 305: DIGITAL COMMUNICATIONS Plan n Topic 1: Introduction n Topic 2: Differential Coding and Scrambling n Topic 3: Codes for Error Detection n Topic 4: Codes for Error Correction n Topic 5: Interleaving Arab Open University-Lebanon Tutorial 19 Block V 32

T 305: DIGITAL COMMUNICATIONS Topic 3: Codes for Error Detection There are broadly speaking two uses of error detection. The first is to alert the user or operator of a system to a problem. If an SDH link develops a fault, for example, it is important that the link is taken out of service and repaired. n The other use of error detection is in conjunction with retransmission to correct for errors. This is known as ARQ (automatic retransmission request) or backwards error correction. If an error in the data is spotted, the system requests retransmission of that part of the data. n Simple BIPs (bit-interleaved parity) and parity checks are therefore adequate for the first of these uses – spotting faults – but not for the second use. Error control coding covers the design of codes specifically for detecting and/or correcting errors. n Arab Open University-Lebanon Tutorial 19 Block V 33

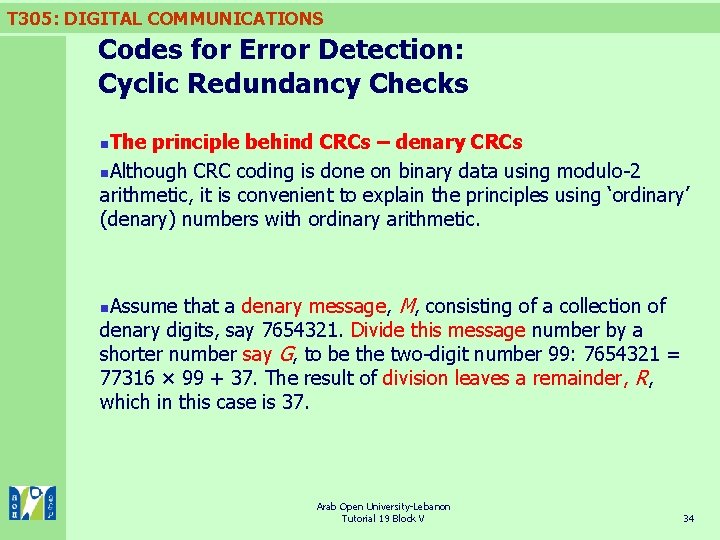
T 305: DIGITAL COMMUNICATIONS Codes for Error Detection: Cyclic Redundancy Checks The principle behind CRCs – denary CRCs n. Although CRC coding is done on binary data using modulo-2 arithmetic, it is convenient to explain the principles using ‘ordinary’ (denary) numbers with ordinary arithmetic. n Assume that a denary message, M, consisting of a collection of denary digits, say 7654321. Divide this message number by a shorter number say G, to be the two-digit number 99: 7654321 = 77316 × 99 + 37. The result of division leaves a remainder, R, which in this case is 37. n Arab Open University-Lebanon Tutorial 19 Block V 34

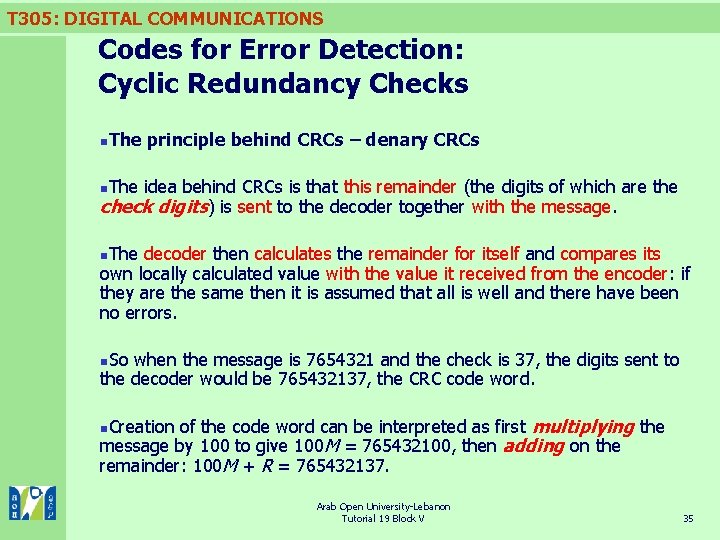
T 305: DIGITAL COMMUNICATIONS Codes for Error Detection: Cyclic Redundancy Checks n. The principle behind CRCs – denary CRCs n. The idea behind CRCs is that this remainder (the digits of which are the check digits) is sent to the decoder together with the message. n. The decoder then calculates the remainder for itself and compares its own locally calculated value with the value it received from the encoder: if they are the same then it is assumed that all is well and there have been no errors. n. So when the message is 7654321 and the check is 37, the digits sent to the decoder would be 765432137, the CRC code word. of the code word can be interpreted as first multiplying the message by 100 to give 100 M = 765432100, then adding on the remainder: 100 M + R = 765432137. n. Creation Arab Open University-Lebanon Tutorial 19 Block V 35

T 305: DIGITAL COMMUNICATIONS Codes for Error Detection: Modulo-2 cyclic redundancy checks In practice, CRCs work directly on binary sequences. The arithmetic used, however, does not treat the sequences as binary representations of ordinary denary numbers. Instead it uses a special sort of arithmetic known as modulo-2 arithmetic. n The reason for this is that modulo-2 arithmetic can be performed on binary sequences very easily and rapidly by exclusive-OR gates and shift registers. n. Also, employing modulo-2 arithmetic leads to a simplification in the method used to check for errors at a decoder; it turns out that just to divide the received sequence by G and see if there is any remainder. This simplification comes about only when working in modulo-2. n Arab Open University-Lebanon Tutorial 19 Block V 36

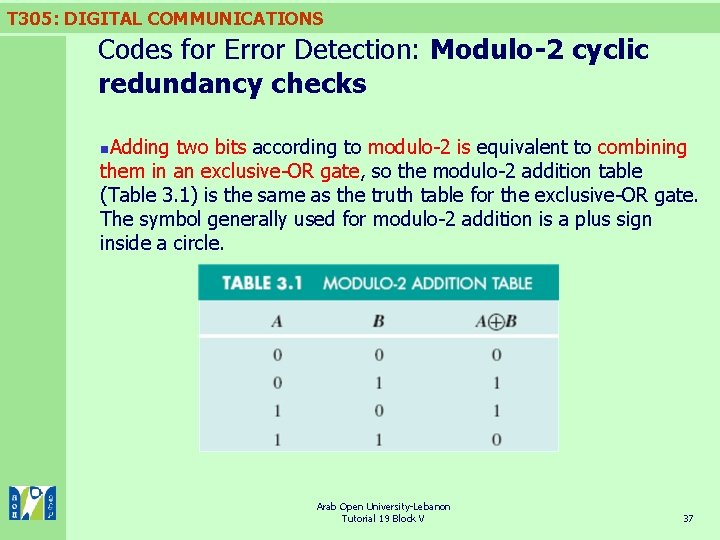
T 305: DIGITAL COMMUNICATIONS Codes for Error Detection: Modulo-2 cyclic redundancy checks Adding two bits according to modulo-2 is equivalent to combining them in an exclusive-OR gate, so the modulo-2 addition table (Table 3. 1) is the same as the truth table for the exclusive-OR gate. The symbol generally used for modulo-2 addition is a plus sign inside a circle. n Arab Open University-Lebanon Tutorial 19 Block V 37

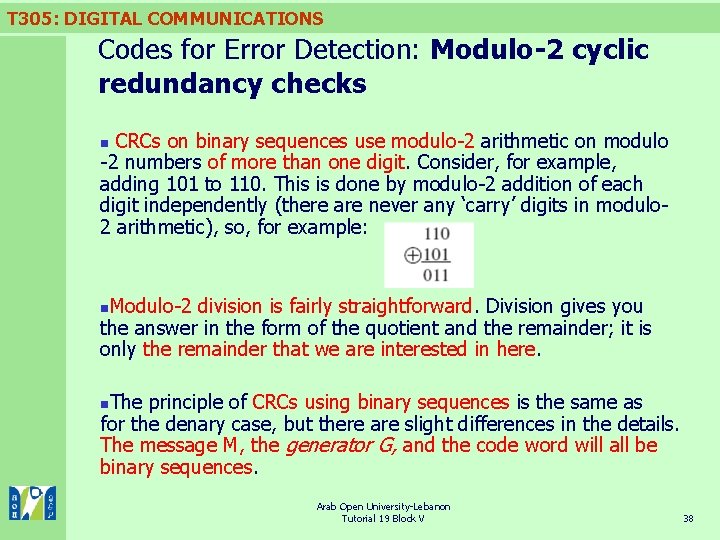
T 305: DIGITAL COMMUNICATIONS Codes for Error Detection: Modulo-2 cyclic redundancy checks CRCs on binary sequences use modulo-2 arithmetic on modulo -2 numbers of more than one digit. Consider, for example, adding 101 to 110. This is done by modulo-2 addition of each digit independently (there are never any ‘carry’ digits in modulo 2 arithmetic), so, for example: n Modulo-2 division is fairly straightforward. Division gives you the answer in the form of the quotient and the remainder; it is only the remainder that we are interested in here. n The principle of CRCs using binary sequences is the same as for the denary case, but there are slight differences in the details. The message M, the generator G, and the code word will all be binary sequences. n Arab Open University-Lebanon Tutorial 19 Block V 38

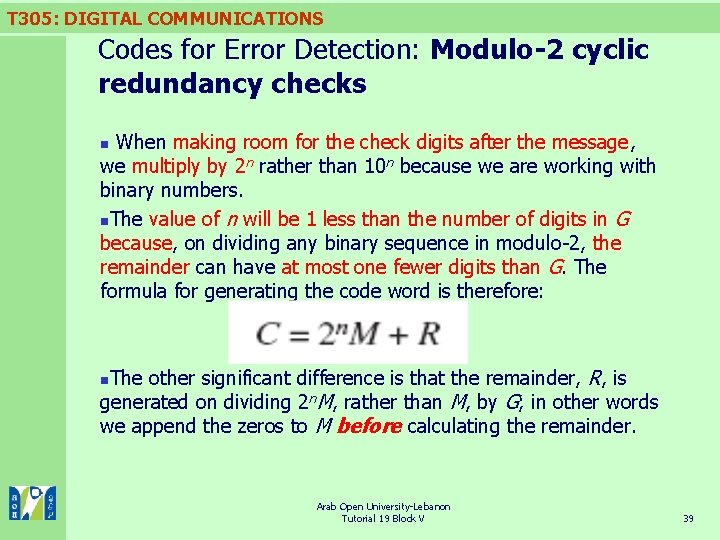
T 305: DIGITAL COMMUNICATIONS Codes for Error Detection: Modulo-2 cyclic redundancy checks When making room for the check digits after the message, we multiply by 2 n rather than 10 n because we are working with binary numbers. n. The value of n will be 1 less than the number of digits in G because, on dividing any binary sequence in modulo-2, the remainder can have at most one fewer digits than G. The formula for generating the code word is therefore: n The other significant difference is that the remainder, R, is generated on dividing 2 n. M, rather than M, by G; in other words we append the zeros to M before calculating the remainder. n Arab Open University-Lebanon Tutorial 19 Block V 39

T 305: DIGITAL COMMUNICATIONS Codes for Error Detection: Modulo-2 cyclic redundancy checks steps of the CRC calculation with G = 1011 and M = 110101 as follows: n. First put n zeros at the end of the message (multiply by 2 n). In my example n is 3 and so 2 n. M = 110101000. n. The Next find the remainder, R, on dividing (modulo-2) 2 n. M by G, i. e. , divide 110101000 by 1011 which, using the modulo-2 calculator, gives the remainder 111. n Then add the remainder to 2 n. M to form the code word C = 2 n. M + R. In this example, the code word is 110101111. n n. At the decoder the message is recovered by simply deleting the check digits (the last three digits). Checking for errors could then, in principle, proceed as for the denary scheme – locally re-creating the check digits (remainder) from the received message and seeing if they are the same as the received check digits. Arab Open University-Lebanon Tutorial 19 Block V 40

T 305: DIGITAL COMMUNICATIONS Codes for Error Detection: Modulo-2 cyclic redundancy checks Choice of G n. Larger values of CRCs give better error detection rates (98 out of 99 for G = 99, 998 out of 999 for G = 999) on the assumption that all errors are equally likely. This should not be surprising, since more digits in G means more redundancy in the encoded sequence. The choice of G in the denary system is to show that the precise value of G is important to optimize the performance of the code, and that the choice also depends upon assumptions about the nature of the probable errors. n Similar arguments apply to the selection of G for modulo-2 CRCs. The values of G chosen in practice are often those which result in codes that provide good immunity to the error patterns caused by ‘burst noise’. Burst noise causes bursts of errors. n Arab Open University-Lebanon Tutorial 19 Block V 41

T 305: DIGITAL COMMUNICATIONS Codes for Error Detection: Modulo-2 cyclic redundancy checks Choice of G n. As with scrambler specifications, the value of G is usually expressed as a polynomial: the generator polynomial. A minor difference in the convention for describing generator polynomials for CRCs compared with tap polynomials for scramblers is that the generator terms are positive powers, whereas the tap polynomial terms are negative powers. Thus the modulo-2 generator 11001 is expressed as a generator polynomial x 4 + x 3 + 1. Notice that the highest power in the polynomial (4, in the example) is one less than the number of digits in G, and is therefore equal to the number of digits appended to the message to create the code (the number of check digits). n Arab Open University-Lebanon Tutorial 19 Block V 42

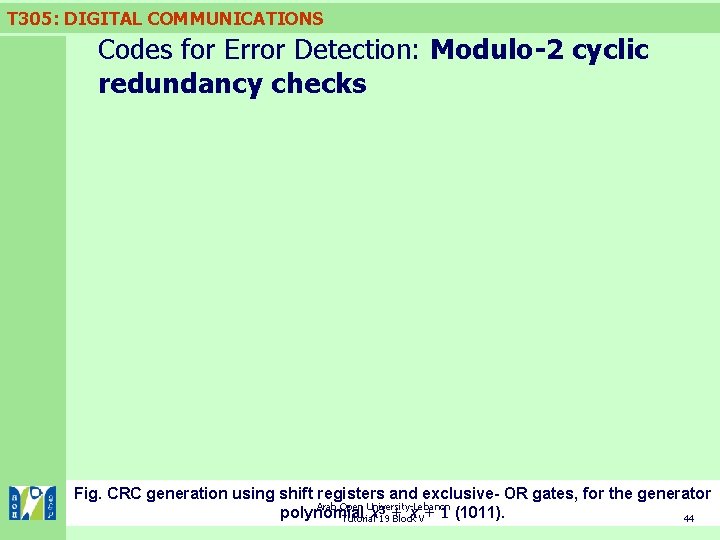
T 305: DIGITAL COMMUNICATIONS Codes for Error Detection: Modulo-2 cyclic redundancy checks n. Physical implementation of CRCs n. One of the attractions of CRCs is that they are simple to perform with hardware because they can be readily implemented using exclusive-OR gates and shift registers as shown in the next slide. value of G is built into the configuration of the shift register and associated exclusive-OR gates. Notice some of the convenient features, for example, the shift register is calculating the value of the remainder at the same time as the message is being sent to the channel. n. The n. As soon as the message has been transmitted, the check digits (forming the remainder) are immediately fed out from the shift register to the channel. Remember that the digits are transmitted with the most significant digit first, and the check digits come after the message. Arab Open University-Lebanon Tutorial 19 Block V 43

T 305: DIGITAL COMMUNICATIONS Codes for Error Detection: Modulo-2 cyclic redundancy checks Fig. CRC generation using shift registers and exclusive- OR gates, for the generator Arab Open University-Lebanon polynomial x 319+ x V+ 1 (1011). Tutorial Block 44

T 305: DIGITAL COMMUNICATIONS Codes for Error Detection: Modulo-2 cyclic redundancy checks At the decoder the message digits are fed into the shift register and, as soon as the sequence is finished, the bit values in the stages of the shift register give the value of the remainder. It is a simple process to check whether they are all zero. n If errors are detected, what happens then depends upon what the CRC is being used for. n n If it is part of an ARQ (automatic retransmission request) protocol, the receiver will send a message back to the transmitter asking for retransmission of the data, and it will be the replacement data (assuming it is now error-free) that is passed on to the next layer up. n If, on the other hand, the CRC is just being used to monitor the performance of the channel, then the value of the remainder will be forwarded to the management network and the errored data may simply be discarded. n Arab Open University-Lebanon Tutorial 19 Block V 45

T 305: DIGITAL COMMUNICATIONS Plan n Topic 1: Introduction n Topic 2: Differential Coding and Scrambling n Topic 3: Codes for Error Detection n Topic 4: Codes for Error Correction n Topic 5: Interleaving Arab Open University-Lebanon Tutorial 19 Block V 46

T 305: DIGITAL COMMUNICATIONS Topic 4: Codes for Error Correction n. Error detection codes can be combined with ARQ (automatic retransmission request) to eliminate some of the errors from the conveyed data. The idea with ARQ is that when an error or errors are detected in a segment of data (in, say, a frame) the data is retransmitted. n. There are circumstances, however, when this approach to eliminating errors is either very inefficient or impossible. For example, there may not be a return path that can be used to request the retransmission. Alternatively, the delay caused by having to wait at least the duration of one round trip for the retransmitted data might be unacceptable. n n. Also, if the probability of a frame containing an error gets too large, communication might become very inefficient or impossible as the proportion of frames having to be retransmitted increases. In all these circumstances a better approach to error control might be the use of an error-correcting code (sometimes called forward error-correcting (FEC) code. Arab Open University-Lebanon Tutorial 19 Block V 47

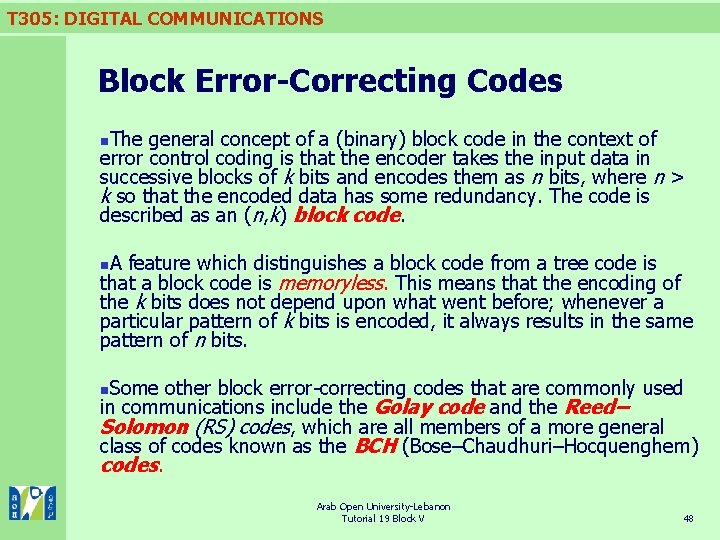
T 305: DIGITAL COMMUNICATIONS Block Error-Correcting Codes The general concept of a (binary) block code in the context of error control coding is that the encoder takes the input data in successive blocks of k bits and encodes them as n bits, where n > k so that the encoded data has some redundancy. The code is described as an (n, k) block code. n A feature which distinguishes a block code from a tree code is that a block code is memoryless. This means that the encoding of the k bits does not depend upon what went before; whenever a particular pattern of k bits is encoded, it always results in the same pattern of n bits. n Some other block error-correcting codes that are commonly used in communications include the Golay code and the Reed– Solomon (RS) codes, which are all members of a more general class of codes known as the BCH (Bose–Chaudhuri–Hocquenghem) codes. n Arab Open University-Lebanon Tutorial 19 Block V 48

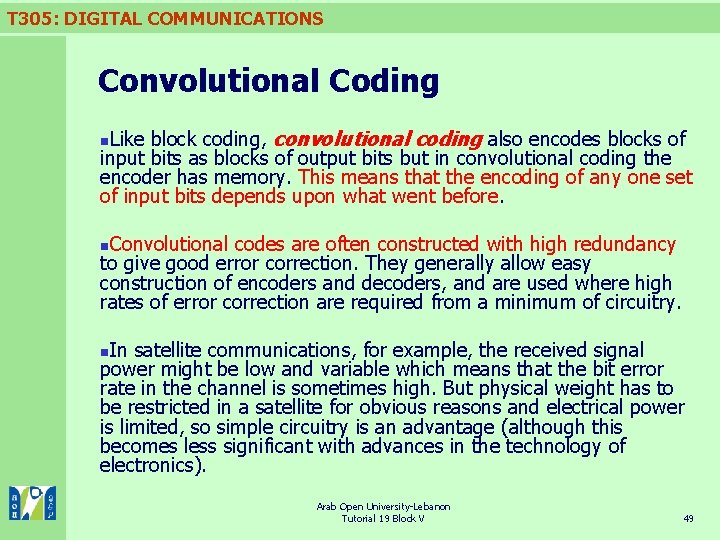
T 305: DIGITAL COMMUNICATIONS Convolutional Coding Like block coding, convolutional coding also encodes blocks of input bits as blocks of output bits but in convolutional coding the encoder has memory. This means that the encoding of any one set of input bits depends upon what went before. n Convolutional codes are often constructed with high redundancy to give good error correction. They generally allow easy construction of encoders and decoders, and are used where high rates of error correction are required from a minimum of circuitry. n In satellite communications, for example, the received signal power might be low and variable which means that the bit error rate in the channel is sometimes high. But physical weight has to be restricted in a satellite for obvious reasons and electrical power is limited, so simple circuitry is an advantage (although this becomes less significant with advances in the technology of electronics). n Arab Open University-Lebanon Tutorial 19 Block V 49

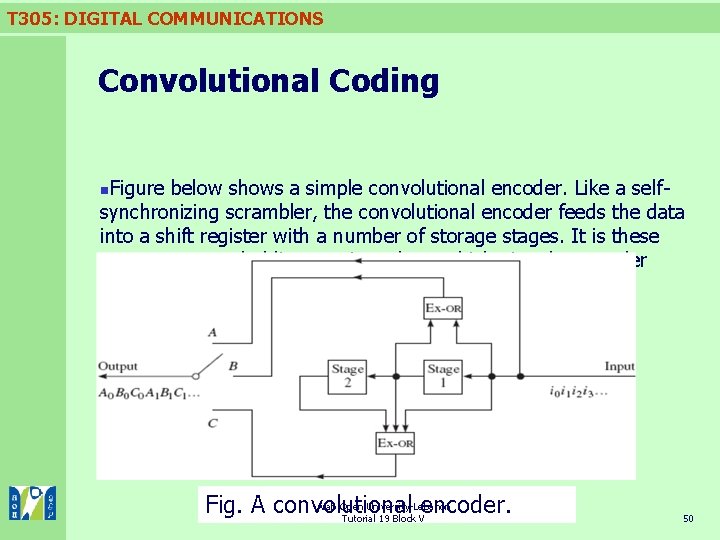
T 305: DIGITAL COMMUNICATIONS Convolutional Coding Figure below shows a simple convolutional encoder. Like a selfsynchronizing scrambler, the convolutional encoder feeds the data into a shift register with a number of storage stages. It is these storage stages, holding previous data, which give the encoder memory. n Arab Open University-Lebanon Fig. A convolutional encoder. Tutorial 19 Block V 50

T 305: DIGITAL COMMUNICATIONS Convolutional Coding n. Scramblers and convolutional encoders both combine bits using exclusive -OR gates, but whereas a scrambler has only one output bit, a convolutional encoder has several. Another significant difference is that there is no feedback in the shift register of a convolutional encoder, so the sequence entered into its shift register is input sequence, not the output as in scrambler. n. Notice that one of the exclusive-OR gates used by the convolutional encoder has three inputs. This gate performs modulo-2 addition of the three inputs, which means that the output is 0 if an even number of inputs are logic 1 and is 1 if an odd number of inputs are logic 1. n. As with block error-correcting codes, the error-correcting ability of convolutional coding comes from the decoder knowing what patterns are permitted in the received sequence and what patterns can appear only when errors have occurred. The convolutional decoder uses information not only from the block of bits currently being received but also from bits received in recent past. Arab Open University-Lebanon Tutorial 19 Block V 51

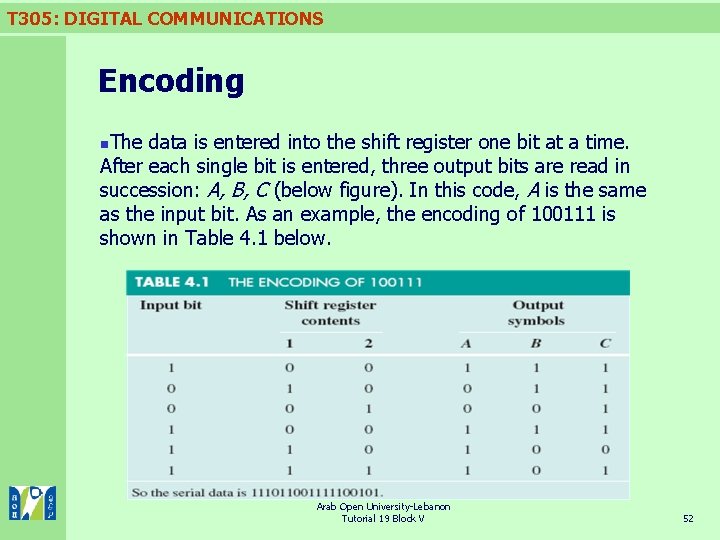
T 305: DIGITAL COMMUNICATIONS Encoding The data is entered into the shift register one bit at a time. After each single bit is entered, three output bits are read in succession: A, B, C (below figure). In this code, A is the same as the input bit. As an example, the encoding of 100111 is shown in Table 4. 1 below. n Arab Open University-Lebanon Tutorial 19 Block V 52

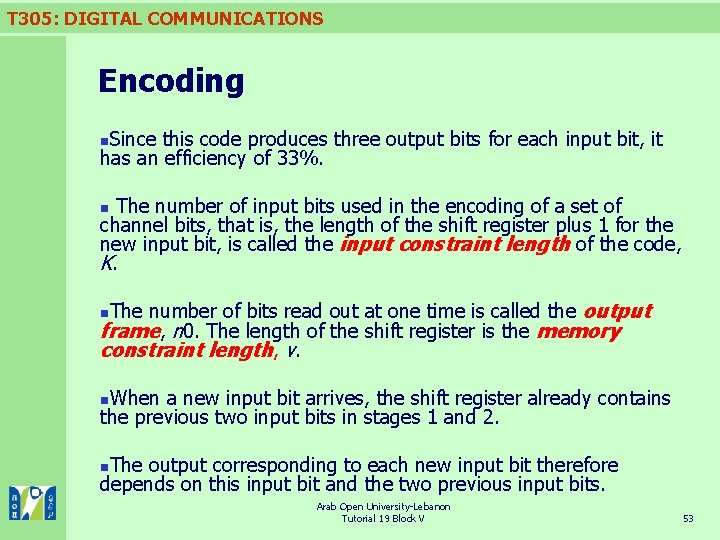
T 305: DIGITAL COMMUNICATIONS Encoding Since this code produces three output bits for each input bit, it has an efficiency of 33%. n The number of input bits used in the encoding of a set of channel bits, that is, the length of the shift register plus 1 for the new input bit, is called the input constraint length of the code, K. n The number of bits read out at one time is called the output frame, n 0. The length of the shift register is the memory constraint length, v. n When a new input bit arrives, the shift register already contains the previous two input bits in stages 1 and 2. n The output corresponding to each new input bit therefore depends on this input bit and the two previous input bits. n Arab Open University-Lebanon Tutorial 19 Block V 53

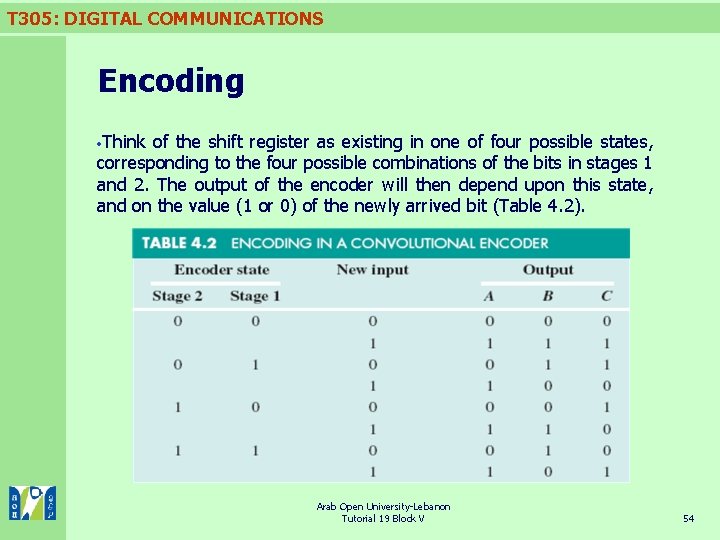
T 305: DIGITAL COMMUNICATIONS Encoding Think of the shift register as existing in one of four possible states, corresponding to the four possible combinations of the bits in stages 1 and 2. The output of the encoder will then depend upon this state, and on the value (1 or 0) of the newly arrived bit (Table 4. 2). Arab Open University-Lebanon Tutorial 19 Block V 54

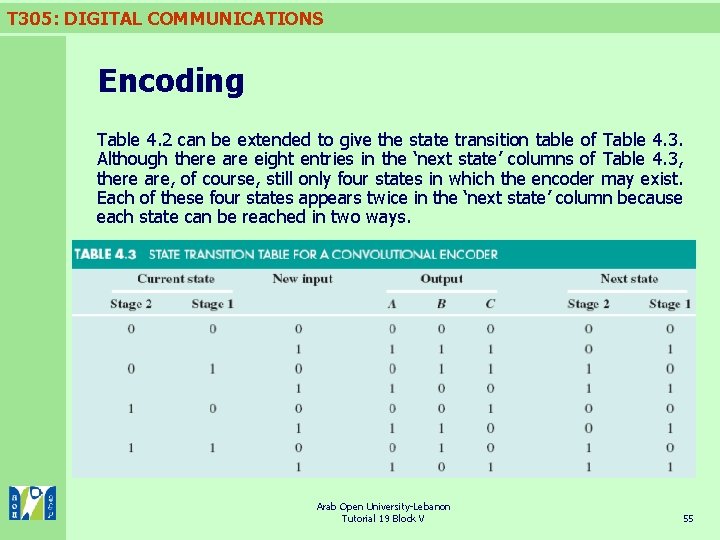
T 305: DIGITAL COMMUNICATIONS Encoding Table 4. 2 can be extended to give the state transition table of Table 4. 3. Although there are eight entries in the ‘next state’ columns of Table 4. 3, there are, of course, still only four states in which the encoder may exist. Each of these four states appears twice in the ‘next state’ column because each state can be reached in two ways. Arab Open University-Lebanon Tutorial 19 Block V 55

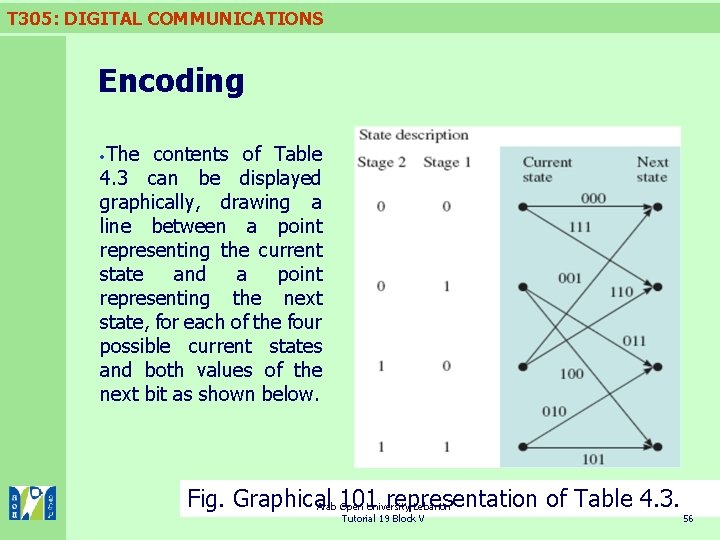
T 305: DIGITAL COMMUNICATIONS Encoding The contents of Table 4. 3 can be displayed graphically, drawing a line between a point representing the current state and a point representing the next state, for each of the four possible current states and both values of the next bit as shown below. Fig. Graphical representation of Table 4. 3. Arab 101 Open University-Lebanon Tutorial 19 Block V 56

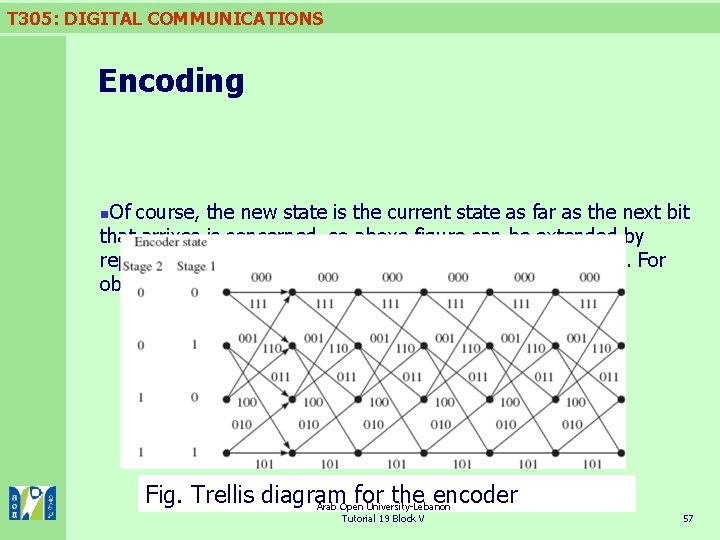
T 305: DIGITAL COMMUNICATIONS Encoding Of course, the new state is the current state as far as the next bit that arrives is concerned, so above figure can be extended by repeating it for each input bit, leading to a graph like below. For obvious reasons, this is known as a trellis diagram. n Fig. Trellis diagram for the encoder Arab Open University-Lebanon Tutorial 19 Block V 57

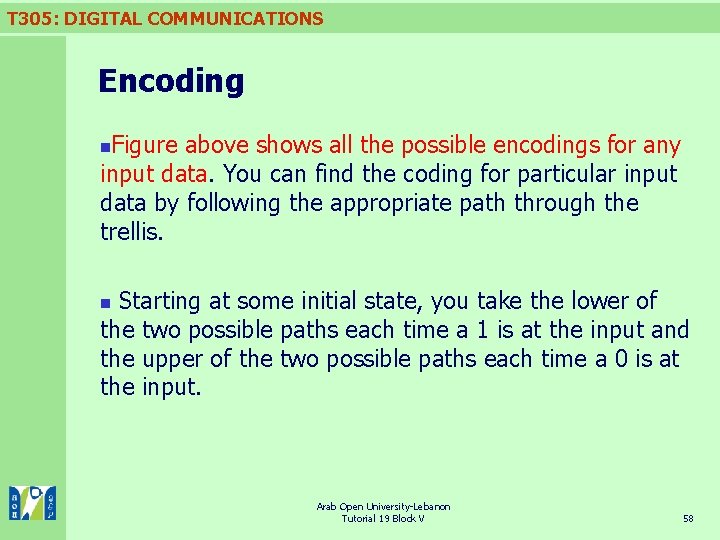
T 305: DIGITAL COMMUNICATIONS Encoding Figure above shows all the possible encodings for any input data. You can find the coding for particular input data by following the appropriate path through the trellis. n Starting at some initial state, you take the lower of the two possible paths each time a 1 is at the input and the upper of the two possible paths each time a 0 is at the input. n Arab Open University-Lebanon Tutorial 19 Block V 58

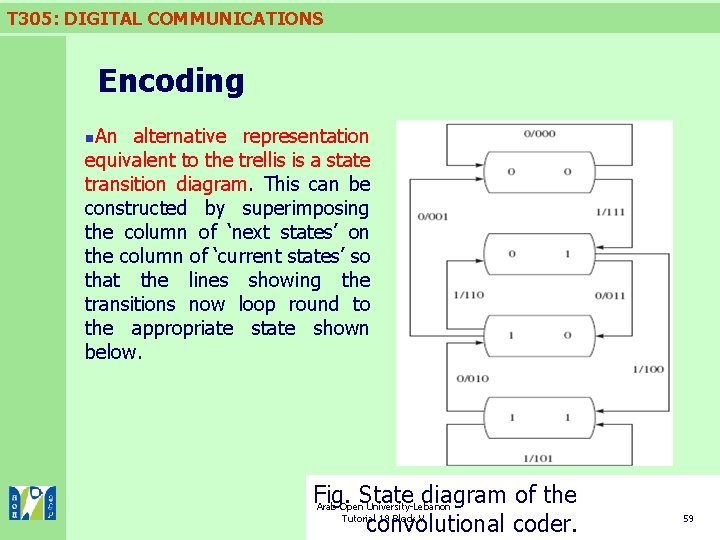
T 305: DIGITAL COMMUNICATIONS Encoding An alternative representation equivalent to the trellis is a state transition diagram. This can be constructed by superimposing the column of ‘next states’ on the column of ‘current states’ so that the lines showing the transitions now loop round to the appropriate state shown below. n Fig. State diagram of the Arab Open University-Lebanon Tutorial 19 Block V convolutional coder. 59

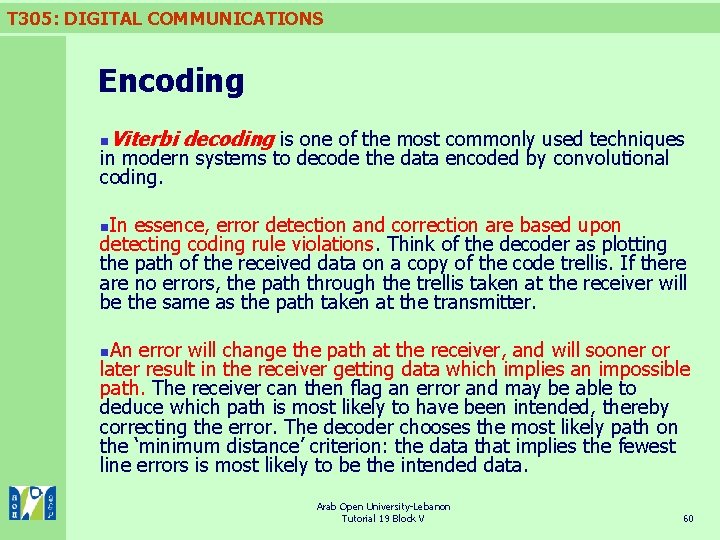
T 305: DIGITAL COMMUNICATIONS Encoding n Viterbi decoding is one of the most commonly used techniques in modern systems to decode the data encoded by convolutional coding. In essence, error detection and correction are based upon detecting coding rule violations. Think of the decoder as plotting the path of the received data on a copy of the code trellis. If there are no errors, the path through the trellis taken at the receiver will be the same as the path taken at the transmitter. n An error will change the path at the receiver, and will sooner or later result in the receiver getting data which implies an impossible path. The receiver can then flag an error and may be able to deduce which path is most likely to have been intended, thereby correcting the error. The decoder chooses the most likely path on the ‘minimum distance’ criterion: the data that implies the fewest line errors is most likely to be the intended data. n Arab Open University-Lebanon Tutorial 19 Block V 60

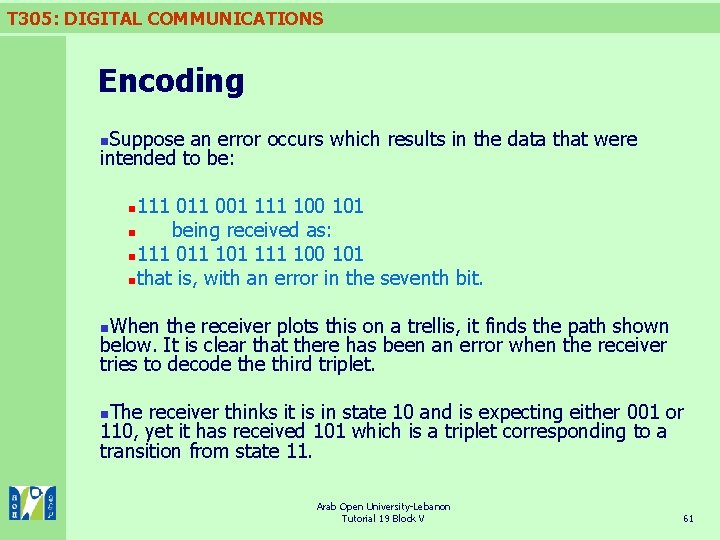
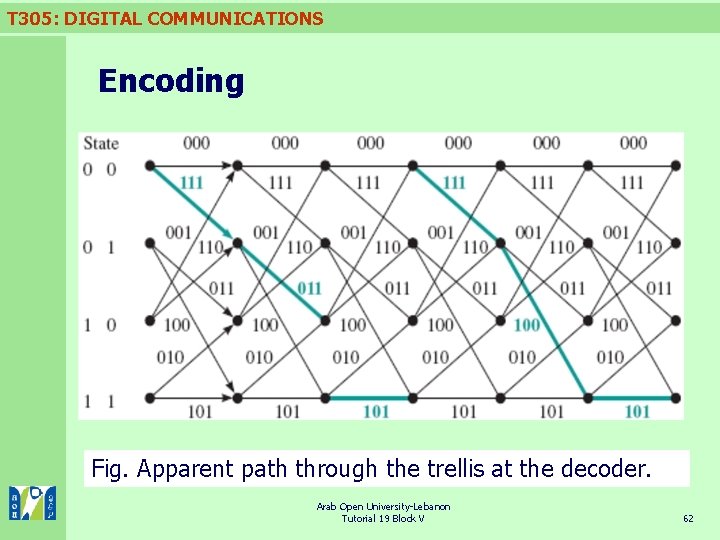
T 305: DIGITAL COMMUNICATIONS Encoding Suppose an error occurs which results in the data that were intended to be: n 111 001 111 100 101 n being received as: n 111 011 101 111 100 101 nthat is, with an error in the seventh bit. n When the receiver plots this on a trellis, it finds the path shown below. It is clear that there has been an error when the receiver tries to decode third triplet. n The receiver thinks it is in state 10 and is expecting either 001 or 110, yet it has received 101 which is a triplet corresponding to a transition from state 11. n Arab Open University-Lebanon Tutorial 19 Block V 61

T 305: DIGITAL COMMUNICATIONS Encoding Fig. Apparent path through the trellis at the decoder. Arab Open University-Lebanon Tutorial 19 Block V 62

T 305: DIGITAL COMMUNICATIONS Encoding If the convolutional encoding is being used on a finite length of data (rather than running continuously), tail digits will be added to the input data to return the encoder to the all 0 s state. n The number of tail digits (all of which are 0) required is equal to the memory constraint length of the encoder. n Since decoding of a received block of bits may not be decided upon until after the receipt of several more blocks (when the survivor paths agree on the decoding), Viterbi decoding involves a delay in the receiver. n Arab Open University-Lebanon Tutorial 19 Block V 63

T 305: DIGITAL COMMUNICATIONS Plan n Topic 1: Introduction n Topic 2: Differential Coding and Scrambling n Topic 3: Codes for Error Detection n Topic 4: Codes for Error Correction n Topic 5: Interleaving Arab Open University-Lebanon Tutorial 19 Block V 64

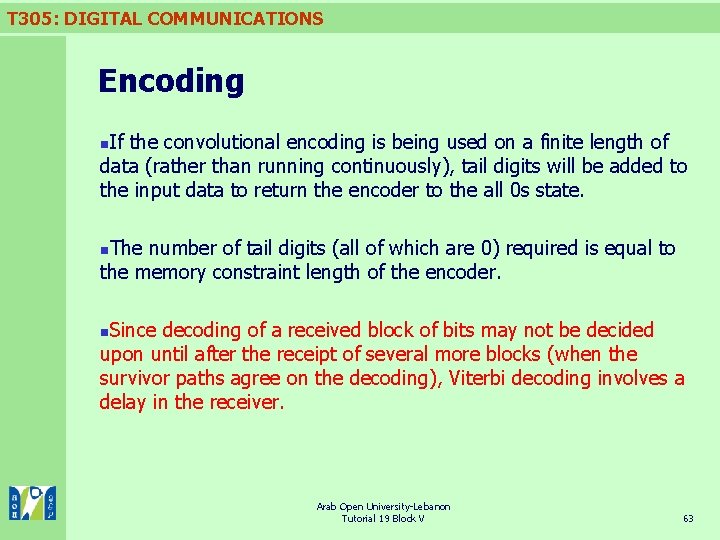
T 305: DIGITAL COMMUNICATIONS Topic 5: Interleaving Most error-correcting codes, both block codes and convolutional codes, cannot correct many errors if they occur close together. Typically, the codes can correct between one and five errors in blocks of data of perhaps 10 to 100 bits. n In practice, errors often do not occur like this at all: in many cases we get bursts of tens or even hundreds of errors occurring very infrequently, and no errors for the rest of the time. A technique which can be employed to allow error-correcting codes to protect against bursts is interleaving. n Figure below shows how interleaving might be used in association with (7, 4) Hamming code so that it is able to correct up to four consecutive errors. Four consecutive code words are interleaved by writing the words into a 4 × 7 matrix of memory locations row by row, and reading out column by column. n Arab Open University-Lebanon Tutorial 19 Block V 65

T 305: DIGITAL COMMUNICATIONS Topic 5: Interleaving Arab Open University-Lebanon Tutorial 19 Block V 66

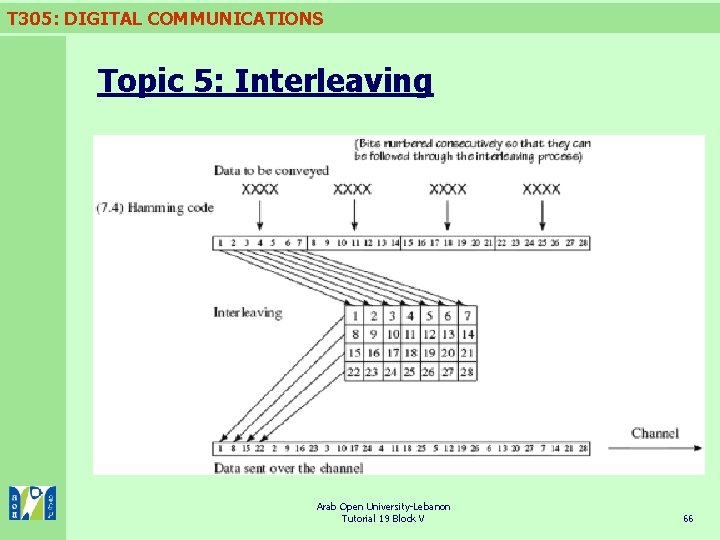
T 305: DIGITAL COMMUNICATIONS Topic 5: Interleaving Fig. Interleaving with a 4 Arab×Open 7 University-Lebanon matrix for burst-error protection Tutorial 19 Block V 67

T 305: DIGITAL COMMUNICATIONS Interleaving The interleaving is undone at the receiver by writing the received bits into a matrix column by column, and reading out row by row. n If we now have a burst of four errors on the channel, so that four consecutive bits in the data arriving at the receiver are errored, the un-interleaving has the effect of spreading out the errors so that each of the four code words contains only a single error, which can be corrected. n The interleaving takes place after the coding at the transmitter, and the un-interleaving takes place before the decoding at the receiver. That is, the sequence is coding–interleaving– channel–uninterleaving–decoding. n Arab Open University-Lebanon Tutorial 19 Block V 68

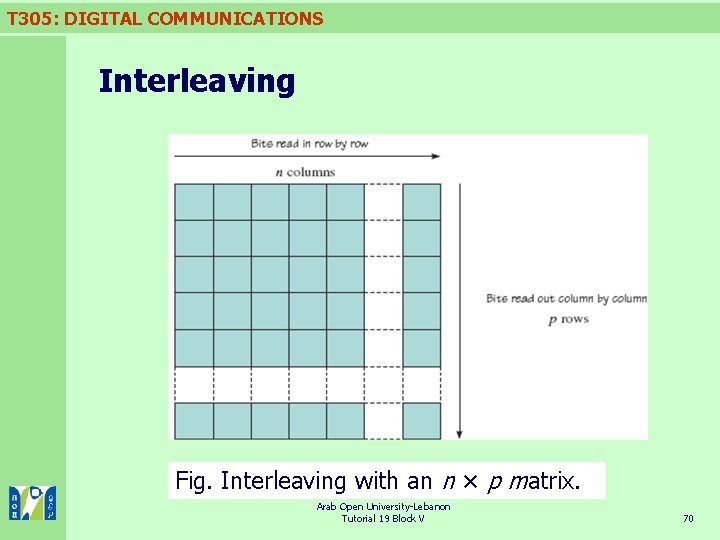
T 305: DIGITAL COMMUNICATIONS Interleaving As an estimate of the delay, we can assume that the whole of the matrix will be completed before we can start sending data to the channel, causing a delay of p × 7 bits at the encoder. n Similarly, if we complete the matrix at the decoder before reading data out, we incur another delay of p × 7 bits. The total delay would therefore be 14 p bits. n More generally, if we were interleaving p code words from a block error correcting code with code words of length n bits (using a matrix with dimensions p rows and n columns shown below), the total delay will be 2 pn bits on the assumption that we fill both matrices before reading out from them. n Arab Open University-Lebanon Tutorial 19 Block V 69

T 305: DIGITAL COMMUNICATIONS Interleaving Fig. Interleaving with an n × p matrix. Arab Open University-Lebanon Tutorial 19 Block V 70

T 305: DIGITAL COMMUNICATIONS Topic 6: Preparation for Next Tutorial n Overview the contents of the Modeling Activities Pulses and systems. Arab Open University-Lebanon Tutorial 19 Block V 71