Security and Privacy Issues in Epassports Ari Juels













































- Slides: 60

Security and Privacy Issues in E-passports Ari Juels, David Molnar, and David Wagner Presented By Anudeep Jassal

Outline Introduction Radio Frequency identification (RFID) Biometrics Security and Privacy Threats Cryptography in E-passports Related Work Strengthening Today’s E-passport Future Issues in E-passport Conclusion

Introduction What is an E-passport? n New Generation of Identity cards. n Same as traditional passport with addition of an integrated chip.

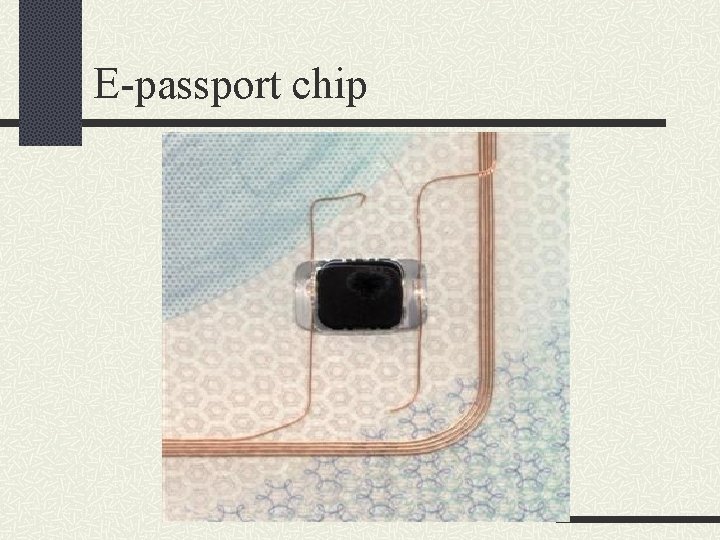
Introduction n Combination of RFID and Biometric Technology. n The chip will store the same data visually displayed on the data page of the passport n Biometric identifier in the form of the digital image of the passport photograph.

E-passport chip

Introduction n Unique chip identification number and digital signatures to protect the stored data from alteration. Goal: n n n To reduce fraud. Identity check. Enhance security.

Introduction “The data stored on the chip is protected from alteration by the latest digital signature technology. As the Department of State implements this new technology, it will include passport features that will protect the security and privacy of passport bearers. We will share more information about these measures once testing is completed. The Department of State will not issue passports incorporating integrated circuits until privacy-related concerns have been addressed. The Department of State is currently coordinating testing of components for possible use in the new passport. Once testing has ended and a final passport configuration that meets the security and privacy needs of our citizens has been completed, electronic passports will be phased in at all 16 passport issuance locations in the domestic United States. ” -- US Department of State

E-passport Logo

US-VISIT mandated adoption of biometrically enabled passports by October 2006 by 27 nations in its Visa. Waiver Program (VWP). US-VISIT program requires visitors traveling to US must have two index fingers scanned and digital photograph taken to match and authenticate their travel documents at the port of entry. These passports are based on the guidelines issued by International Civil Aviation Organization (ICAO). ICAO is responsible for setting international passport standards.

ICAO Guidelines: n n Call for incorporation of RFID chips are used to store and retrieve data in a wireless manner. Biometric identity verification (face recognition). Additionally specifies fingerprints and iris data as optional biometrics.


Malaysia has already deployed e-passports. E-passports generated in 1998 included a chip containing an image of the thumbprint of the passport holder. Second generation e-passports rolled out in 2003 contained extracted fingerprint information. Today 5, 000 first generation and 125, 000 second generation e-passports in circulation.

What is RFID? Radio Frequency Identification: automatic identification method that relies on storing and retrieving data remotely using devices called RFID tags or transponders. An object which can be applied to incorporated into animal, product or a person for the purpose of identification using radiowaves.


RFID Two types of tags: Active and passive E-passports use passive tags.

Passive tags • No Internal power supply • Obtain operating power generated from the reader. • Small in size, lighter and less expensive. • Shorter read range. • Embedded in a sticker or under the skin

Active tags • Powered by internal battery • More reliable than passive tags due to the ability for active tags to conduct a "session" with a reader • More memory size upto 1 MB. • Long read range. • Bigger size, more expensive and limited operational lifetime.

Supply chain vs Passport tags Supply Chain RFID tags: n simple, cheap, n no support for cryptography, n single identifier Passport RFID tags: n shorter intended read range, n tamper resistant, n cryptography.

Biometric authentication is the verification of human identity through measurement of biological characteristics. Mechanism by which human beings authenticate each other. Three Biometrics favored in e-passport deployment: n n n Face recognition: automated analog of the ordinary human process of face recognition. Fingerprint : Iris:

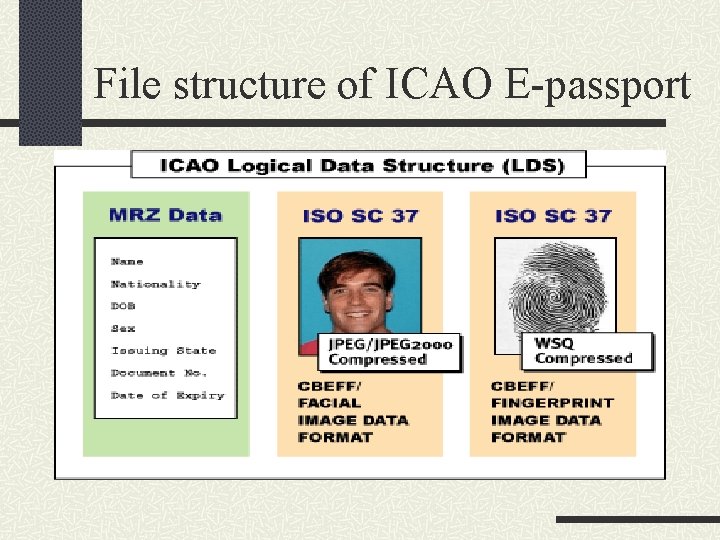
File structure of ICAO E-passport

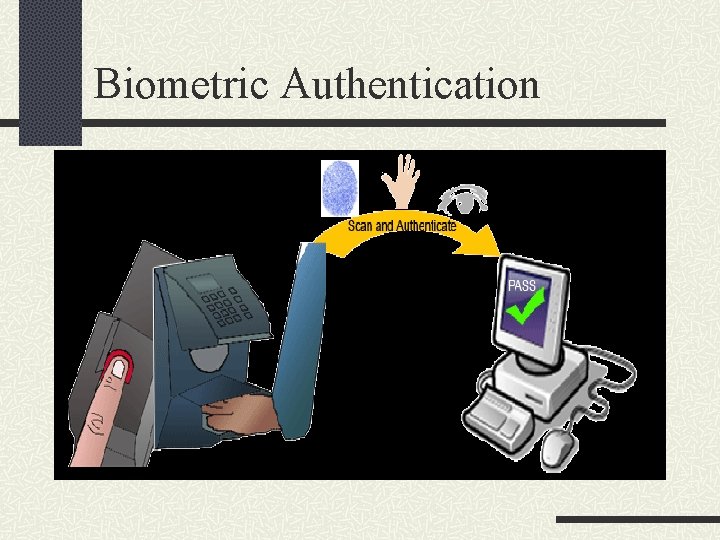
Biometric Authentication An authenticated user enrolls by presenting an initial, high quality biometric image to the sensor. The system stores information extracted during enrollment in a data structure known as a template. To prove identity during authentication session the user again presents the biometric to a sensor. The verifying entity compares the freshly presented biometric information with that contained in the template for the user.

Biometric Authentication

E-Passport Security and Privacy Threats Clandestine scanning Clandestine tracking Skimming and cloning Eavesdropping Biometric data-leakage Cryptographic weaknesses

Security And Privacy Threats Clandestine Scanning: n n The ICAO guidelines do not require authenticated or encrypted communications between passports and readers. An unprotected e-passport chip is subject to shortrange illegal scanning with leakage of sensitive personal information.

Security And Privacy Threats Clandestine tracking: n n The standard for e-passport RFID chips stipulates the emission without authentication of a chip ID on protocol initiation. If this ID is different for every passport it could enable tracking the movements of the passport holder by unauthorized parties.

Security And Privacy Threats Skimming and cloning: n n Baseline ICAO regulations require digital signatures on e-passport data. These signatures allow the reader to verify that the data came from the correct passportissuing authority. No defense against cloning since the digital signatures do not bind the data to a particular passport or chip.

Security And Privacy Threats Eavesdropping: n Faraday cages do not prevent eavesdropping on legitimate passport-to-reader communications. n Eavesdropping problematic for three reasons: n Function Creep : e-passports will be used in new areas like e-commerce. n Feasibility: maybe feasible at longer distance. n Detection Difficulty: it is purely passive and does not involve powered signal emission.

Security And Privacy Threats Biometric data leakage: n n Baseline ICAO regulations require digitized headshots (Secrecy needed for authentication). Automation required with e-passports and physical environment is not strictly controlled.

Security And Privacy Threats Cryptographic weaknesses: n n ICAO guidelines include an optional mechanism for authenticating and encrypting passport-to-reader communications. No mechanism to revoke access once a reader knows the k key. K key allows passport to talk to legitimate reader before releasing RFID tag information. K key used to encrypt all data transmitted between the passport and the reader.

E-Passport Threats Data Leakage Threats: n Vulnerable to surreptitious reading. n RFID readers installed in doorway could be read from anyone passing through the doorway. n Could be set up as a part of security checkpoints at airports, sporting events or concerts. Could be placed in shops or entrances of the buildings. n Problematic since the RFID chip contains sensitive information like passport holder’s name, date of birth, passport number. n RFID protocols executed by e-passport may also leak information. It uses a special UID value which is fixed and different for each e-passport, it acts as a static identifier for tracking the movement of e-passports.

E-Passport Threats Identity Thefts: n photograph, name, birthday, social security number necessary ingredients to build a new identity or create fake document. Tracking and Hotlisting: n static identifier allows for tracking the movements of RFID device. n Hotlisting: targeting specific individuals. n Unattended triggering.

Biometric Threat • Automation Human oversight • Opportunity for spoofing authentication system • Spillover • Compromised data in one system threaten integrity of unrelated ones • Special properties Passport photos • Image Quality • Higher quality than the image an attacker may produce • Forgery • Spoof face-recognition systems •

Cryptography in E-passports ICAO specification: specifies mandatory cryptographic feature for e-passports. Passive authentication: n Data on e-passport signed by issuing nation n Permitted signature algorithms: RSA, DSA and ECDSA n Only demonstrates that data is authentic n Does not prove that container for data is authentic (i. e. the passport)

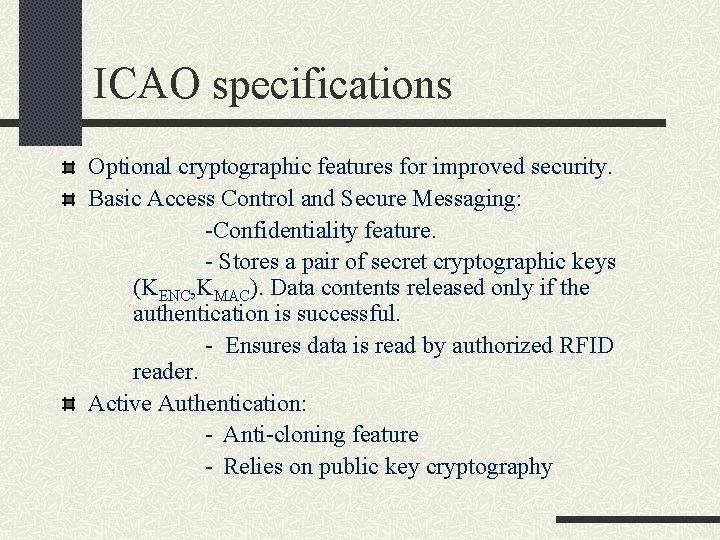
ICAO specifications Optional cryptographic features for improved security. Basic Access Control and Secure Messaging: -Confidentiality feature. - Stores a pair of secret cryptographic keys (KENC, KMAC). Data contents released only if the authentication is successful. - Ensures data is read by authorized RFID reader. Active Authentication: - Anti-cloning feature - Relies on public key cryptography

Basic Access Control When a reader attempts to scan the passport, it engages in challenge response protocol that proves the knowledge of the pair of keys and derives a session key. Data contents are released only if the authentication is successful. The keys derive from optically scannable data printed on the passport n The passport number n Date of birth n Date of expiration of the passport n Three check digits, one for each of the three preceding values.

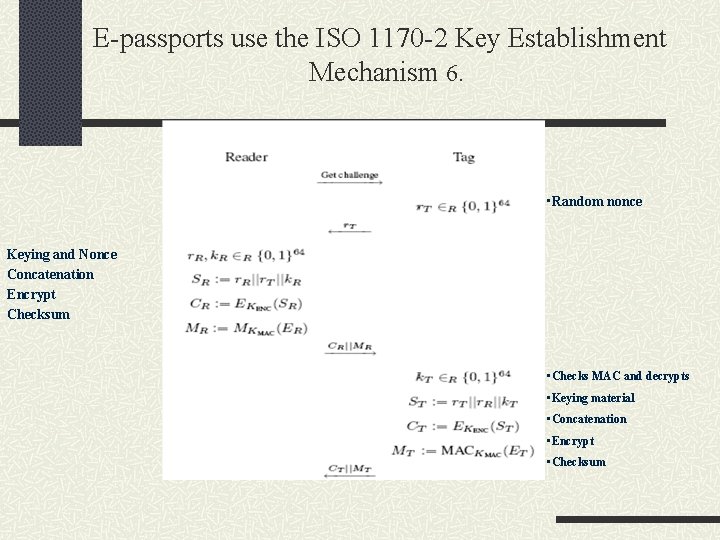
E-passports use the ISO 1170 -2 Key Establishment Mechanism 6. • Random nonce Keying and Nonce Concatenation Encrypt Checksum • Checks MAC and decrypts • Keying material • Concatenation • Encrypt • Checksum

Encryption and Decryption Two key 3 DES CBC mode with zero IV Cryptographic checksums are calculated using ISO/IEC 9797 -1 MAC algorithm 3 with Block cipher DES Zero IV (8 bytes) ISO 9797 -1 padding method 2

Shortcomings of Basic Access Control The entropy key is too small. Single key is used for lifetime of the e-passport. Despite of the shortcomings Basic Access Control is better than no encryption at all.

Active Authentication Anti cloning feature. Does not prevent unauthorized parties from reading epassport contents. Relies on public key cryptography. Works by having e-passport prove possession of a private key. Corresponding public key is stored as part of the signed data on the passport.

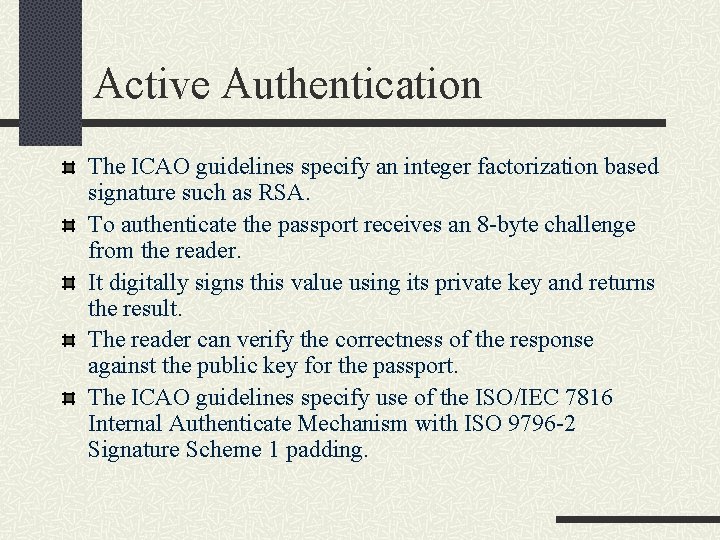
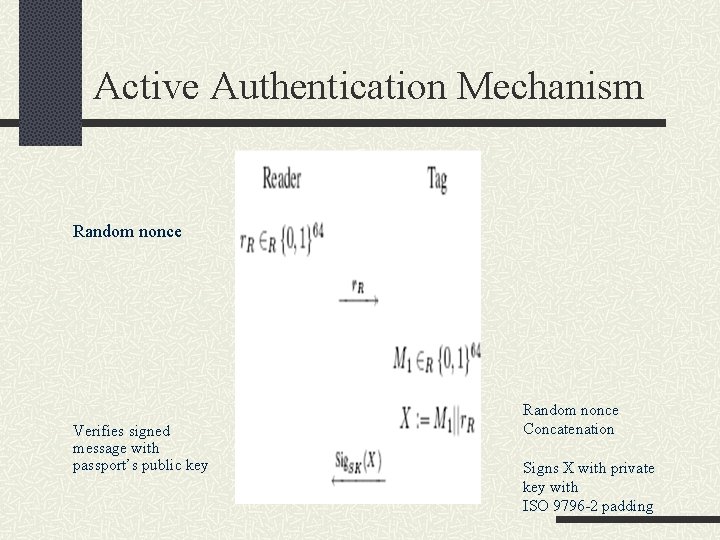
Active Authentication The ICAO guidelines specify an integer factorization based signature such as RSA. To authenticate the passport receives an 8 -byte challenge from the reader. It digitally signs this value using its private key and returns the result. The reader can verify the correctness of the response against the public key for the passport. The ICAO guidelines specify use of the ISO/IEC 7816 Internal Authenticate Mechanism with ISO 9796 -2 Signature Scheme 1 padding.

Active Authentication Mechanism Random nonce Verifies signed message with passport’s public key Random nonce Concatenation Signs X with private key with ISO 9796 -2 padding

Active Authentication Mechanism The public key must be tied to the specific e-passport and biometric data presented to avoid man-in-the-middle attack. Every reader capable of Active Authentication and compliant with the ICAO specification also has the hardware capability necessary for Basic Access Control to avoid the risk of clones e-passport. The private key used in Active Authentication must never leave a particular e-passport.

Active Authentication Issues The certificate required for verifying Active Authentication also contains enough information to derive a key for Basic Access Control as a result the certificate must be kept secret. When used with RSA or Rabin-Williams signatures responses with different moduli and hence from different e -passports can be distinguished. It enables tracking and hotlisting attacks even if Basic Access Control has been employed and session keys derived.

Related Work Pattinson § Points out the need for direct link between optically scanned card data and secret keys embedded in epassports § Outlines the privacy problems with passports readable by anyone Jacob § Discusses issues in e-passport deployment in the Netherlands § Highlights the importance of basic access control § Investigates the issues surrounding a national database of biometrics identifiers

Related Work Smart Card Research Group at IBM Zurich § Demonstrates a Javacard application running on a Philips chip that performs basic access control and active access control in under 2 seconds

Cryptographic measures in planned deployments Federal Register notice dated 18 February 2005 provides a number of details on U. S. e-passport plans. The Federal notice offers three reasons for the decision not to implement Basic Access Control: The data stored in the chip are identical to those printed in the passport. Encrypted data would slow entry processing time. Encryption would impose more difficult technical coordination requirements among nations implementing the e-passport system. E-passports will carry Faraday cages and readers will be shielded to prevent eavesdropping.

Flaw in Federal notice reasoning Reason 3 is flawed because : n Active Authentication required an optical scan of a passport to provide the claimed anti-cloning benefit. This is why The ICAO spec mandates readers supporting Active Authentication be able to optically scan e-passports. This optical scan capability is also sufficient for Basic Access Control. n All the data required to derive keys for Basic Access Control is present on the data page of the e-passport, no coordination among nations is required.

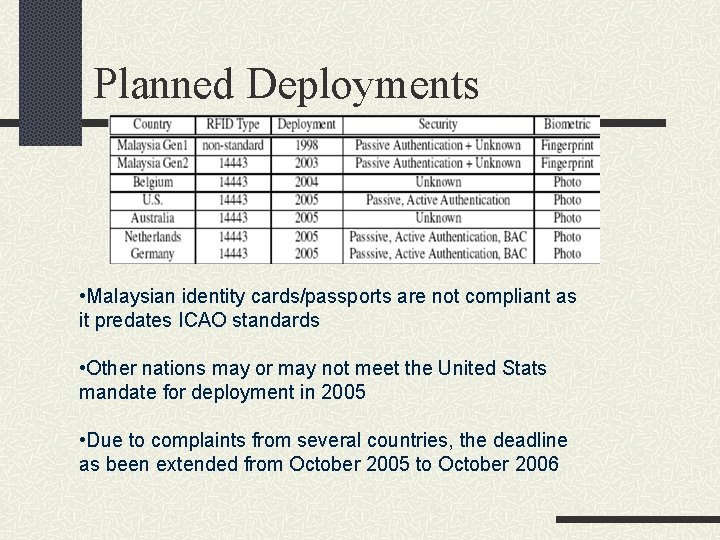
Planned Deployments • Malaysian identity cards/passports are not compliant as it predates ICAO standards • Other nations may or may not meet the United Stats mandate for deployment in 2005 • Due to complaints from several countries, the deadline as been extended from October 2005 to October 2006

Strengthening today’s E-passports Faraday Cages: n n n Simple measures to prevent unauthorized reading of epassports. Materials such as aluminum fiber are opaque to RF signals could be used to create a Faraday cage. Deprecated because does not prevent eavesdropping on legitimate conversations between readers and tags.

Strengthening today’s E-passports Larger secrets for basic access control: n n n Long term keys for Basic Access Control have 52 bits of entropy which is too low to resist a brute-force attack. A simple countermeasure would be to add a 128 -bit secret unique to each passport to the key derivation algorithm. The secret would be printed together with other passport information on the passport.

Strengthening today’s E-passports n Such secret could take the form of a larger passport ID number or a separate field on an epassport. n To aid mechanical reading the secret might be represented as a two dimensional bar code or written in an OCR font to the Machine Readable Zone of each passport.

Strengthening today’s E-passports Private Collision avoidance: n n n Collision avoidance protocol in ISO 14443 uses a UID as part of its collision avoidance protocol. Care must be taken that UID is different on each reading and that UIDs are unlinkable across sessions. Countermeasure is to pick a new random identifier on every tag read.

Strengthening today’s E-passports Beyond Optically readable keys: n n n Current ICAO approach neatly ties together physical presence and the ability to read biometric data. Next generation ID cards cannot count on this kind of tight coupling. Important to create a keying mechanism that limits a reader’s power to reuse secret keys and a matching authorization infrastructure for e-passport readers.

Future Issues in E-passports Visas and writeable e-passports: n Once the e-passports are accepted there would be a push for e-passports that support visas and other endorsements. n Because different RFID tags on the same passport can interfere with each other it may not be feasible to include a new RFID tag with each visa stamp. n Instead we would like to keep visa information on the same chip as the standard passport data. n These features require writing new data to an e-passport after issuance.

Future Issues in E-passports A simple first attempt at visas on e-passports: n An area specified as append-only memory for visas n Visa would be named by e-passport and signed by issuing government n Could possibly include “sanity checks” to ensure a visa is properly signed and names the correct e-passport before committing it to the visa memory area

Future Issues in E-passports Another thing to consider is that some travelers do not want border control to know where they’ve traveled n For example, most Arab countries will refuse entry to holders of passports which bear Israeli visas n The previous example is considered a legitimate reason, but someone entering the United States from Canada may be harboring terrorists n It may be hard in the future to determine the legitimate reasons from the illegitimate, but preventing illegitimate visa removals will become a goal of future visa-enabled e-passports

Future Issues in E-passports Function creep n n n Passports might some day come to serve as authenticators for consumer payments or mass transit passes Has the ability to undermine data protection features as it will spread bearer data more widely among divergent systems May lead to consumer convenience (i. e. removal of optical scanning and faraday-cage use)

Future Issues in E-passport Unless new privacy features are added, it is conceivable that an e-passport can reveal a great deal of private information n For example, an age check at a bar can also leak information about their passport number, place of birth, and possibly elements of their travel history n Web cookies are an instructive example of function creep n

Conclusion The secrecy requirements for biometric data imply that unauthorized reading of e-passport data is a security risk as well as a privacy risk At a minimum, a Faraday Cage and Basic Access Control should be used in ICAE deployments to prevent unauthorized remote reading of e-passports. Because the U. S. deployment uses Active Authentication, readers are required to include the capability to optically scan e-passports. This capability is sufficient for Basic Access Control and would therefore require no change or coordination with other nations to implement it. Today’s e-passports deployments are just the first wave of next-generation identification devices

References http: //travel. state. gov/passport/eppt_27 88. html http: //www. state. gov/r/pa/prs/ps/2006/7043 3. htm http: //en. wikipedia. org/wiki/RFID Epassport. ppt presented by Vivian Bates and Pano Elenis
 Sustantivo biforme
Sustantivo biforme Privacy awareness and hipaa privacy training cvs
Privacy awareness and hipaa privacy training cvs Three primary privacy issues are accuracy property and
Three primary privacy issues are accuracy property and Social issues in information technology
Social issues in information technology Big data privacy issues in public social media
Big data privacy issues in public social media Azure security privacy compliance and trust
Azure security privacy compliance and trust Chapter 9 privacy security and ethics
Chapter 9 privacy security and ethics Chapter 9 privacy security and ethics
Chapter 9 privacy security and ethics Chapter 9 privacy security and ethics
Chapter 9 privacy security and ethics Hipaa privacy and security awareness training
Hipaa privacy and security awareness training Is a destructive event a program is intended to deliver.
Is a destructive event a program is intended to deliver. Private securit
Private securit E commerce security and fraud issues and protections
E commerce security and fraud issues and protections Legal ethical and professional aspects of security
Legal ethical and professional aspects of security Legal and ethical issues in computer security
Legal and ethical issues in computer security Legal and ethical issues in computer security
Legal and ethical issues in computer security Legal and ethical issues in information security
Legal and ethical issues in information security Sip security issues
Sip security issues Risks of instant messaging in the workplace
Risks of instant messaging in the workplace Security issues in ajax
Security issues in ajax Software security issues
Software security issues Basis data relasional membuat pengamanan pada tingkatan:
Basis data relasional membuat pengamanan pada tingkatan: Wireless security in cryptography
Wireless security in cryptography E commerce security policy
E commerce security policy Ari allyn-feuer
Ari allyn-feuer Resektioartroplastia
Resektioartroplastia Ari koskelainen
Ari koskelainen Arı larvası modifikasyon
Arı larvası modifikasyon Ari kuusio
Ari kuusio Ereeri
Ereeri Stationary and mobile sources of air pollution
Stationary and mobile sources of air pollution Army ari
Army ari Prosessiosaaja
Prosessiosaaja Raha ja saatavatili
Raha ja saatavatili Borgarsjá
Borgarsjá Ari okkonen
Ari okkonen Ari kouvonen
Ari kouvonen Mehmet emre arı
Mehmet emre arı Ari edwald
Ari edwald Ari drager
Ari drager Kitinden
Kitinden Ari shilnikova
Ari shilnikova Andian ari anggraeni
Andian ari anggraeni Vuosiloma irtopäivät lauantai
Vuosiloma irtopäivät lauantai Ari jain
Ari jain Tres homens ari beto e ciro
Tres homens ari beto e ciro Ari anshori
Ari anshori Ari requicha
Ari requicha Ari mileage reporting
Ari mileage reporting Winifred jiau
Winifred jiau Ari rusila
Ari rusila Polvijärvi hammaslääkäri
Polvijärvi hammaslääkäri Partenogenez
Partenogenez Eko is titik-titik dan ari
Eko is titik-titik dan ari Oogenez spermatogenez farkları
Oogenez spermatogenez farkları Ari aranda
Ari aranda Kecap wawanohan dina bahasa indonesia nyaèta ...
Kecap wawanohan dina bahasa indonesia nyaèta ... Petsa ng itatag ang rebelyong boxer
Petsa ng itatag ang rebelyong boxer Ari miettinen
Ari miettinen Jalma anu ngawawancara, disebut
Jalma anu ngawawancara, disebut Ari maj wyciek
Ari maj wyciek




















































































