RFID Security and Privacy Author Ari Juels Presenter


























- Slides: 49

RFID Security and Privacy Author: Ari Juels Presenter: Yuliya Kopylova CSCE 790 slide 1

Roadmap u. Background u. RFID Risks u. Privacy: Simple Solutions u. Privacy: More Involved Solutions u. Authentication: Some Solutions u. Conclusion 1 2 3 4 5 2

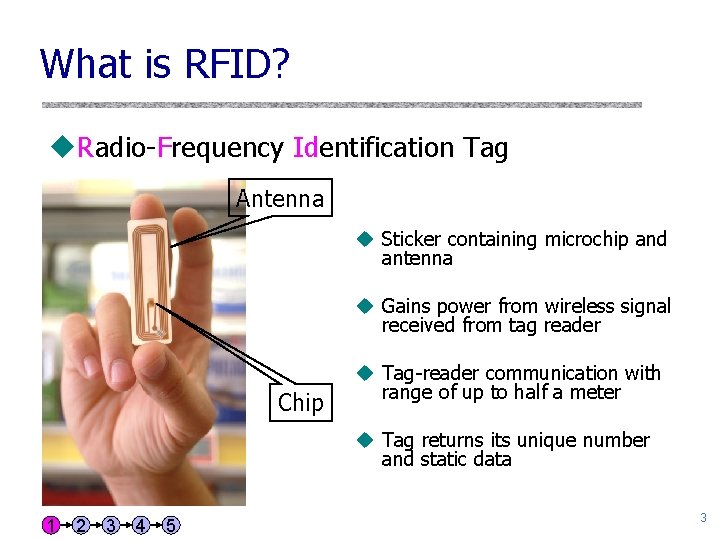
What is RFID? u. Radio-Frequency Identification Tag Antenna u Sticker containing microchip and antenna u Gains power from wireless signal received from tag reader Chip u Tag-reader communication with range of up to half a meter u Tag returns its unique number and static data 1 2 3 4 5 3

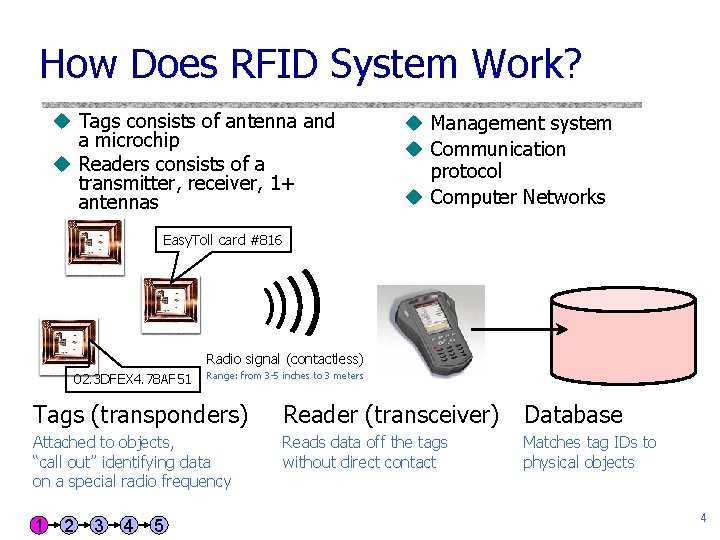
How Does RFID System Work? u Tags consists of antenna and a microchip u Readers consists of a transmitter, receiver, 1+ antennas u Management system u Communication protocol u Computer Networks Easy. Toll card #816 Radio signal (contactless) 02. 3 DFEX 4. 78 AF 51 Range: from 3 -5 inches to 3 meters Tags (transponders) Reader (transceiver) Database Attached to objects, “call out” identifying data on a special radio frequency Reads data off the tags without direct contact Matches tag IDs to physical objects 1 2 3 4 5 4

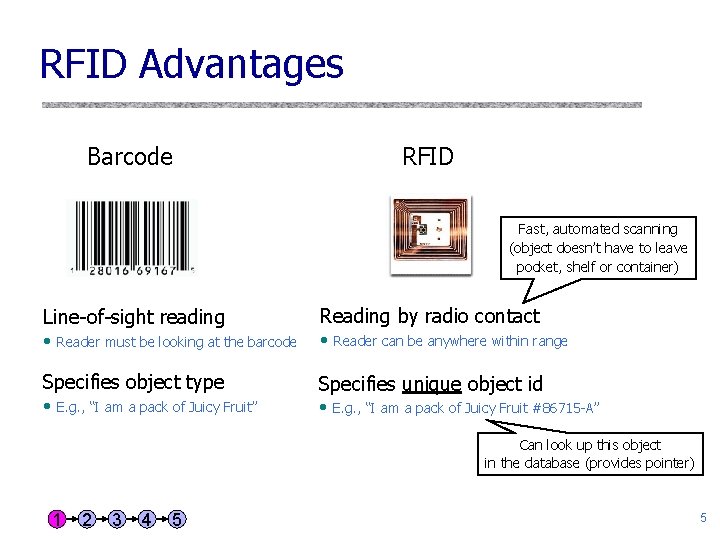
RFID Advantages Barcode RFID Fast, automated scanning (object doesn’t have to leave pocket, shelf or container) Line-of-sight reading • Reader must be looking at the barcode Specifies object type • E. g. , “I am a pack of Juicy Fruit” Reading by radio contact • Reader can be anywhere within range Specifies unique object id • E. g. , “I am a pack of Juicy Fruit #86715 -A” Can look up this object in the database (provides pointer) 1 2 3 4 5 5

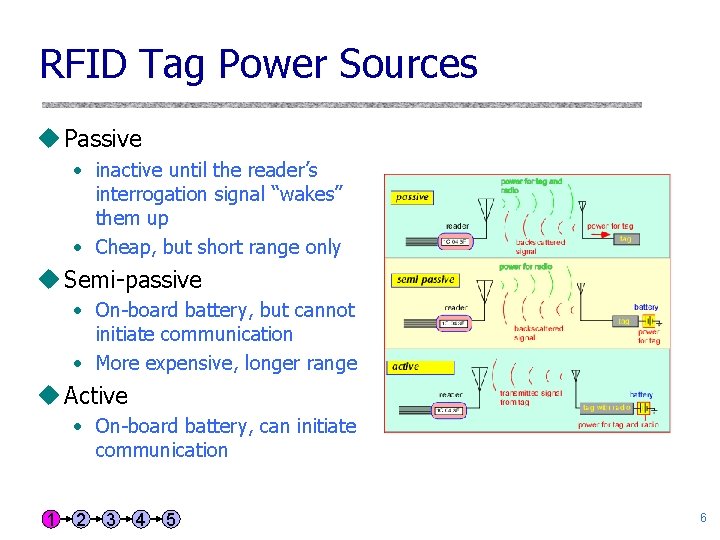
RFID Tag Power Sources u Passive • inactive until the reader’s interrogation signal “wakes” them up • Cheap, but short range only u Semi-passive • On-board battery, but cannot initiate communication • More expensive, longer range u Active • On-board battery, can initiate communication 1 2 3 4 5 6

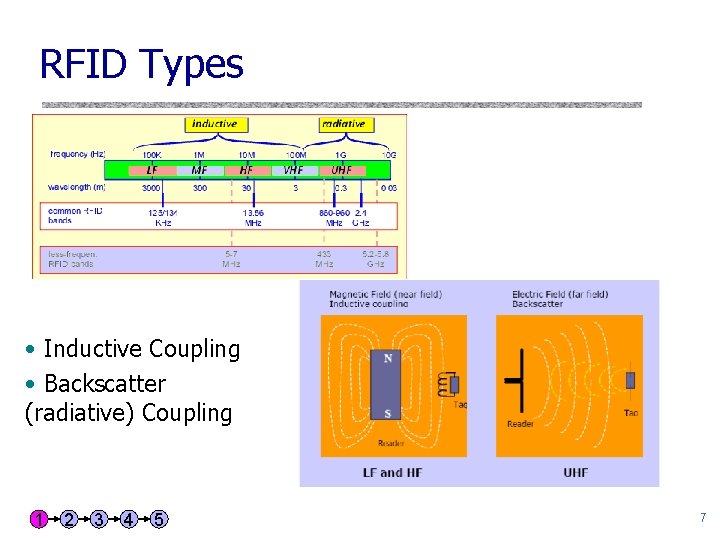
RFID Types • Inductive Coupling • Backscatter (radiative) Coupling 1 2 3 4 5 7

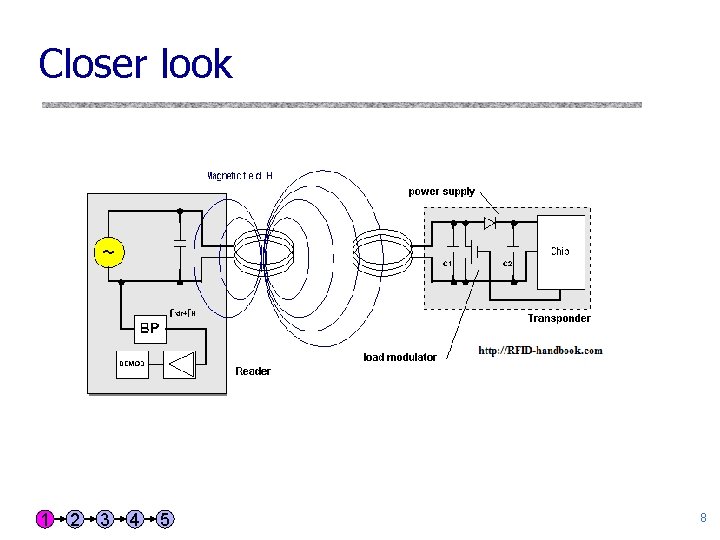
Closer look 1 2 3 4 5 8

RFID examples u Pervasive Devices • • • Low memory, few gates Low power, no clock, little state Low computational power u You may own a few. u Billions on the way. 1 2 3 4 5 9

Current Applications u Public Transport and Ticketing u Access Control u Logistics u Animal identification u Anti-theft system u Real time measurements in sports u Inventory Control in supermarkets u Electronic payments u Industry automation u Medical u Banknotes, casino chips 1 2 3 4 5 10

Futuristic Applications u “Smart” appliances • Refrigerators that automatically create shopping lists • Closets that tell you what clothes you have available, and search the Web for advice on current styles, etc. • Ovens that know how to cook pre-packaged food u “Smart” products • Clothing, appliances, CDs, etc. tagged for store returns u “Smart” paper • Airline tickets that indicate your location in the airport • Library books • Business cards u Recycling • Plastics that sort themselves 1 2 3 4 5 11

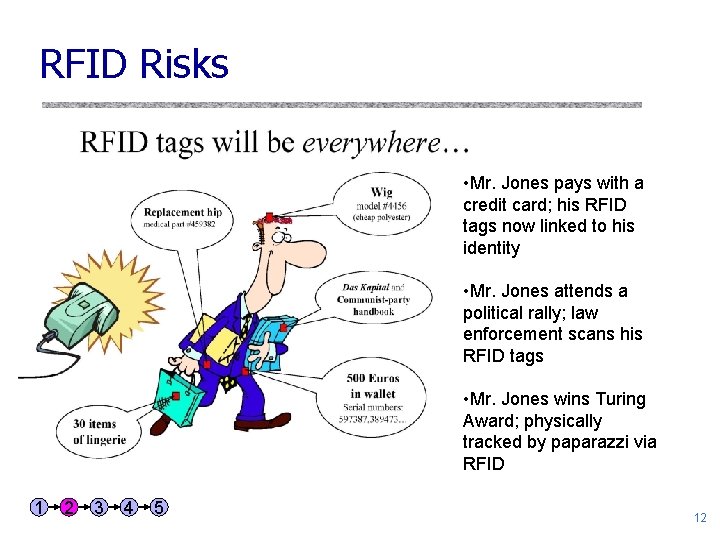
RFID Risks • Mr. Jones pays with a credit card; his RFID tags now linked to his identity • Mr. Jones attends a political rally; law enforcement scans his RFID tags • Mr. Jones wins Turing Award; physically tracked by paparazzi via RFID 1 2 3 4 5 12

Why RFID Risks Arise Three technical aspects of today’s RFID tags create potential problems: u They are promiscuous • they talk to any compatible reader. u They are remotely readable: • they can be read at a distance through materials like cardboard, cloth, and plastic. u They are stealthy • not only are the tags inconspicuous, you don't know when they are transmitting information or to whom. In short, the personal information 1 2 3 4 5 13

Risks: Privacy u Personal privacy • Clandestine inventory and tracking – Unsanctioned readers • Customer profiling – Tracking personal activities (e. g. , purchase habits, travel) • Big brother – Illicit or inappropriate use of personal data u Data cross contamination • Inventory tags plus personal info u Corporate espionage • Track your competitor’s inventory u Military espionage • Harvesting RFID communication to make inferences 1 2 3 4 5 14

Risks: Eavesdropping u Read ranges • nominal read range – max distance at which a normally operating reader can reliably scan tags • rogue scanning range – rogue reader can emit stronger signal and read tags from a larger distance than the nominal range • tag-to-reader eavesdropping range – read-range limitations result from the requirement that the reader powers the tag – however, one reader can power the tag, while another one can monitor its emission (eavesdrop) • reader-to-tag eavesdropping range – readers transmit at much higher power than tags – readers can be eavesdropped form much further – readers may reveal tag specific information 1 2 3 4 5 15

Risks: Counterfeits u Comes down to authentication u How can be accomplished • Replaying (RF “tape-recorder”) • Tag cloning • Back-engineering u A few examples from real life (easy to break) • Speed passes • Ignition keys • Physical coercion and attack – In 2005, a man in Malaysia had his fingertip cut off by thieves stealing his biometric-enabled Mercedes – What would happen if the Veri. Chip were used to access ATM machines and secure facilities? • Perhaps it is better then if tags can be cloned and are not used for authentication—only for identification 1 2 3 4 5 16

RFID capabilities u Little power • Receives power from reader • Range a few meters u Little memory • Static 64 -to-128 -bit identifier • Hundreds of bits soon u Little computational power • A few thousand gates • No cryptographic functions available • Static keys for read/write permission u In terms of computational power can be divided into – BASIC tags – SYMMETRIC KEY tags 1 2 3 4 5 17

Privacy protection approaches ustandard tags • • • jamming “kill” command “sleep” command Renaming Blocking ucrypto enabled tags • synchronization approach • hash chain based approach • tree-approach 1 2 3 4 5 18

Easiest solution u Keep it close to your body • Liquids are not penetrable by microwave frequencies u Faraday cage • Container made of foil or metal mesh, impenetrable by radio signals of certain frequencies • Shoplifters are already known to use foil-lined bags • Maybe works for a wallet, but huge hassle in general u Active jamming • Disables all RFID, including legitimate applications u All kinds of the above protections can be purchased now days • protective sleevers for passports, wallets, ids, etc. 1 2 3 4 5 19

Dead tags tell no tales u Idea: permanently disable tags with a special “kill” command • part of the EPC specification u Advantages: • Simple and effective u Disadvantages: • eliminates all post-purchase benefits of RFID for the consumer and for society • no return of items without receipt • no smart house-hold appliances • cannot be applied in some applications – library, e-passports, banknotes u Similar approaches: • put RFID tags into price tags or packaging which are removed and discarded 1 2 3 4 5 20

Don’t kill the tag, put it to sleep u Idea: instead of killing the tag put it in sleep mode • tag can be re-activated if needed u Advantages: • Simple • effective u Disadvantages: • difficult to manage in practice • tag re-activation must be password protected • how the consumers will manage hundreds of passwords for their tags? • passwords can be printed on tags, but then they need to be scanned optically or typed in by the consumer 1 2 3 4 5 21

Partial destruction u. Renaming • In simplest case renaming to gibberish • No intrinsic meaning • Still can be tracked – Backscatter from antennas – Hypothesize manufacturer type may be learnable – Do tags possess uniquely detectable RF fingerprints? (Device signatures a staple of electronic warfare) u. Relabelings • Retain only product ID for later use • Destroy unique ID at the time of purchase u. Splitting identifiers across two tags • Peel off one at time of purchase 1 2 3 4 5 22

Distance Measuring u. Signal-to-noise ratio of the reader signal in an RFID system provides a rough metric of the distance between a reader and a tag. u. With some additional, low-cost circuitry a tag might achieve rough measurement of the distance of an interrogating reader. u. Distance can serve as a metric for trust. • Release general information (“I am attached to a bottle of water”) when scanned at a distance • Release more specific information (ID), only at close range. 1 2 3 4 5 23

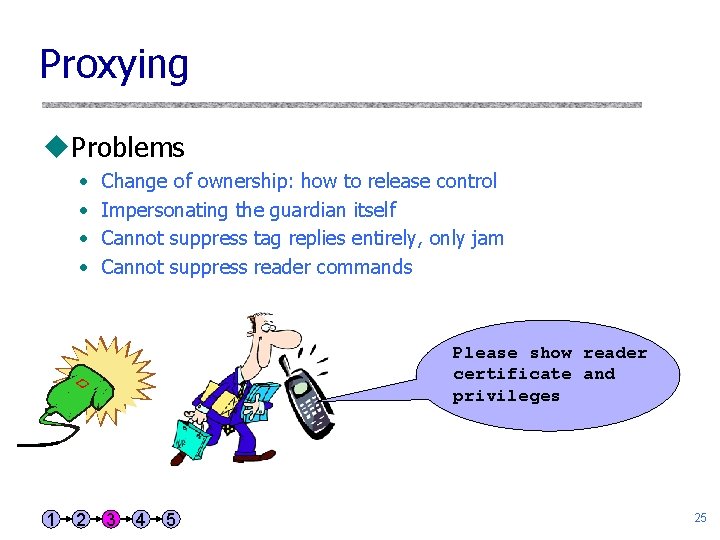
Proxying u. Proxying • Consumers carry their own privacy-enforcing devices (Higher-powered intermediaries like mobile phones) • Watch dog – Observer observing the observer: monitor if someone scans you – Selectively jams tag replies as needed • RFID guardian – Talk to the guardian first – Communication is released through a fortified intermediate 1 2 3 4 5 24

Proxying u. Problems • • Change of ownership: how to release control Impersonating the guardian itself Cannot suppress tag replies entirely, only jam Cannot suppress reader commands Please show reader certificate and privileges 1 2 3 4 5 25

Renaming u Idea: avoid using real Ids, change Identifiers across the reads • • get rid of fixed names (identifiers). Pseudonyms stored on tag (limited storage, i. e. 10 or so), tag cycles through pseudonyms use random pseudonyms and change them frequently u Requirements: • • only authorized readers should be able to determine the real identifier behind a pseudonym standard tags cannot perform computations -> next pseudonym to be used must be set by an authorized reader u A possible implementation • pseudonym = {R|ID}K • • • authorized readers can decrypt pseudonyms and determine real ID authorized readers can generate new pseudonyms for unauthorized readers, pseudonyms look like random bit strings • • tracking is still possible between two renaming operations if someone can eavesdrop during the renaming operation, then she may be able to link the new pseudonym to the old one no reader authentication -> rogue reader can overwrite pseudonyms in tags (tags will be erroneously identified by authorized readers) – R is a random number – K is a key shared by all authorized readers u Potential problems • 1 2 3 4 5 26

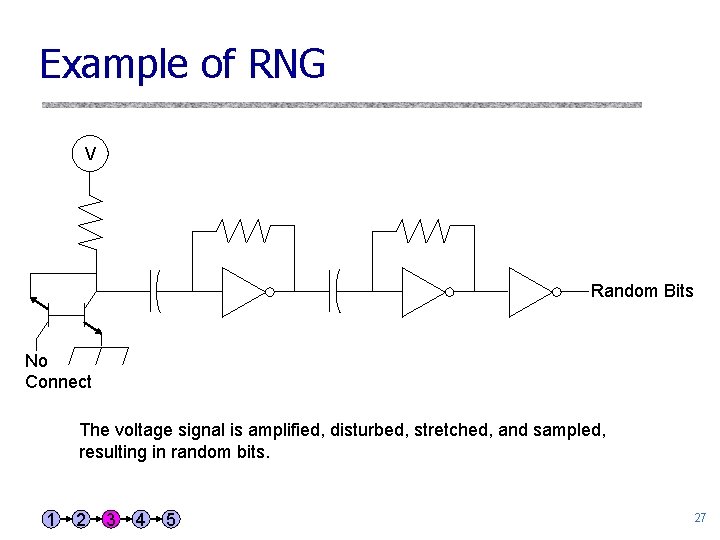
Example of RNG V Random Bits No Connect The voltage signal is amplified, disturbed, stretched, and sampled, resulting in random bits. 1 2 3 4 5 27

Renaming (re-encryption) u. A public key based implementation: • El Gamal scheme: – – 1 2 3 Inputs are ciphertexts Outputs are a re-encryption of the inputs. Anyone can encrypt without the public key E Those who know the secret key D can also decrypt messages encrypted with different keys are indistinguishable 4 5 28

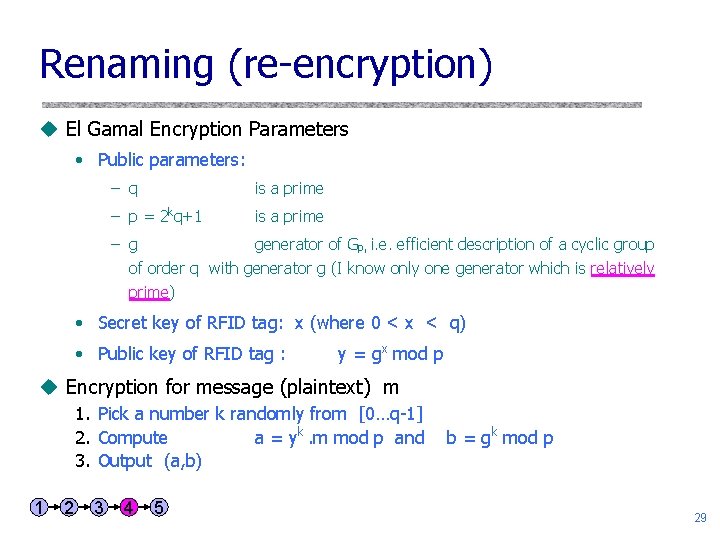
Renaming (re-encryption) u El Gamal Encryption Parameters • Public parameters: – q is a prime – p = 2 kq+1 is a prime – g generator of Gp, i. e. efficient description of a cyclic group of order q with generator g (I know only one generator which is relatively prime) • Secret key of RFID tag: x (where 0 < x < q) • Public key of RFID tag : y = gx mod p u Encryption for message (plaintext) m 1. Pick a number k randomly from [0…q-1] 2. Compute a = yk. m mod p and 3. Output (a, b) 1 2 3 4 5 b = gk mod p 29

Renaming (re-encryption) u Decryption • Compute m as a / bx (= yk. m/ (gk)x = gxk. m/ gkx = m) u One can re-encrypt a ciphertext (a, b) without decryption: Input: a ciphertext (a, b) and public key y 1. Pick a number a randomly from [0…q-1] 2. Compute a’ = ya. a mod p and b’ = ga. b mod p 3. Output (a’, b’) u Same decryption technique • Compute m = m) a’ / b’x (= yk. ya. m/ (gk. ga ) x = gx (k+a). m/ gx (k+a) u Properties: • • • 1 2 new tag pseudonyms can be computed by readers that know the public key real tag ID can be computed only by readers that know the private key Semantic security: Cannot distinguish between C = EPK, r [Alice] and C’ = EPK, r’ [Bob] – An attacker who intercepts C and C’ cannot tell if they come from the same chip, that is the attacker cannot identify or track Alice 3 4 5 30

Blocking u When the reader sends a signal, more than one RFID tag may respond: this is a collision • typical commercial application, such as scanning a bag of groceries, potentially hundreds of tags might be within range of the reader. u Reader must engage in a special singulation protocol to talk to each tag separately • Singulation is used by an RFID reader only when necessary to identify a specific tag (and its ID) from a number of tags in the field u Tree-walking is a common singulation method • • 1 2 3 4 5 Used by 915 Mhz tags, the most common type in the U. S. Slotted aloha is used for LF tags 31

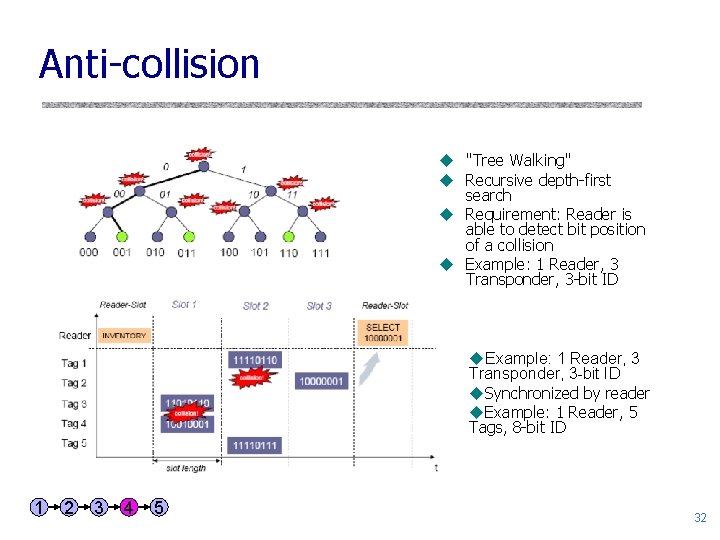
Anti-collision u "Tree Walking" u Recursive depth-first search u Requirement: Reader is able to detect bit position of a collision u Example: 1 Reader, 3 Transponder, 3 -bit ID u. Synchronized by reader u. Example: 1 Reader, 5 Tags, 8 -bit ID 1 2 3 4 5 32

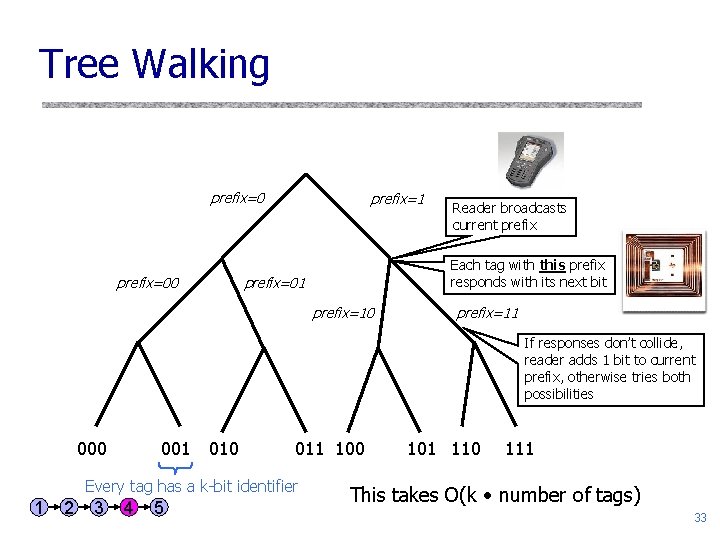
Tree Walking prefix=00 prefix=1 Reader broadcasts current prefix Each tag with this prefix responds with its next bit prefix=01 prefix=10 prefix=11 If responses don’t collide, reader adds 1 bit to current prefix, otherwise tries both possibilities 000 001 010 011 100 Every tag has a k-bit identifier 1 2 3 4 5 101 110 111 This takes O(k number of tags) 33

Tree-Walking u. Tree-walking” protocol for identifying tags recursively asks question: • “What is your next bit? ” • Something along the lines of: “Will all tags with 1 as their first digit raise their hand”. “Will all tags with 1 as their first digit, and 0 as their second. . ” u. Blocker tag always says both ‘ 0’ and ‘ 1’! • Makes it seem like all possible tags are present by making an RFID tag misbehave, and answers yes to every question. 1 2 3 4 5 34

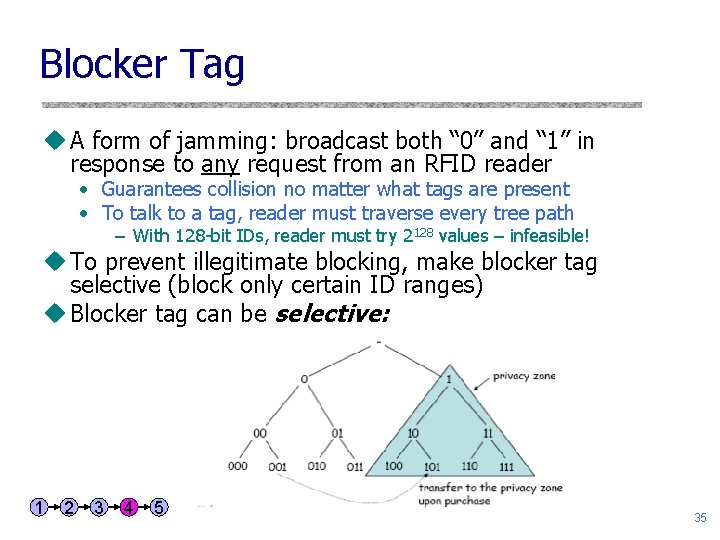
Blocker Tag u A form of jamming: broadcast both “ 0” and “ 1” in response to any request from an RFID reader • Guarantees collision no matter what tags are present • To talk to a tag, reader must traverse every tree path – With 128 -bit IDs, reader must try 2128 values – infeasible! u To prevent illegitimate blocking, make blocker tag selective (block only certain ID ranges) u Blocker tag can be selective: 1 2 3 4 5 35

Blocker Tag uprivacy zone • tree is divided into two zones • privacy zone: all IDs starting with 1 • upon purchase of a product, its tag is transferred into the privacy zone by setting the leading bit uthe blocker tag • when the prefix in the reader’s query starts with 1, it simulates a collision • when the blocker tag is not present, everything works normally u. Alternative: polite blocking (notify the reader) 36

Hash Locks u Locked tag transmit only meta. ID u Similar to the proximity approach u Unlocked tag can do all operations u Locking mechanism: • • Reader R selects a nonce and computes meta. ID = hash(key) R writes meta. ID to tag T T enters locked state R stores the pair (meta. ID, key). u Unlocking • • 1 2 Reader R queries tag T for its meta. ID R looks up (meta. ID, key) R sends key to T If (hash(key) == meta. ID), T unlocks itself 3 4 5 37

Hash locks u. Cheap to implement on tags: • A hash function and storage for meta. ID. u. Security based on hardness of hash. u. Hash output has nice random properties. u. Low key look-up overhead. u. Tags respond predictably; allows tracking. • Motivates randomization. u. Requires reader to know all keys 1 2 3 4 5 38

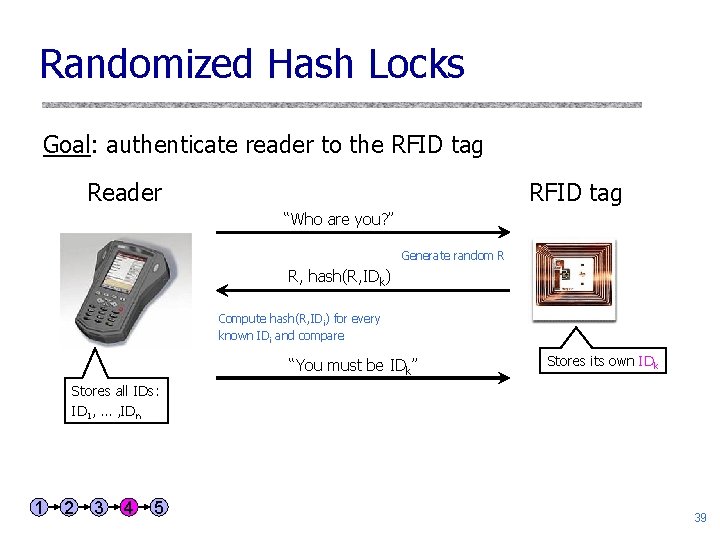
Randomized Hash Locks Goal: authenticate reader to the RFID tag Reader RFID tag “Who are you? ” Generate random R R, hash(R, IDk) Compute hash(R, IDi) for every known IDi and compare “You must be IDk” Stores its own IDk Stores all IDs: ID 1, … , IDn 1 2 3 4 5 39

Randomized Hash Locks u Tag must store hash implementation and pseudorandom number generator • Low-cost RNGs exist; can use physical randomness u Secure against tracking because tag response is different each time u Reader must perform brute-force ID search • Effectively, reader must stage a mini-dictionary attack to unlock the tag u Alternative: better searching • Tree approach • Synchronization approach 1 2 3 4 5 40

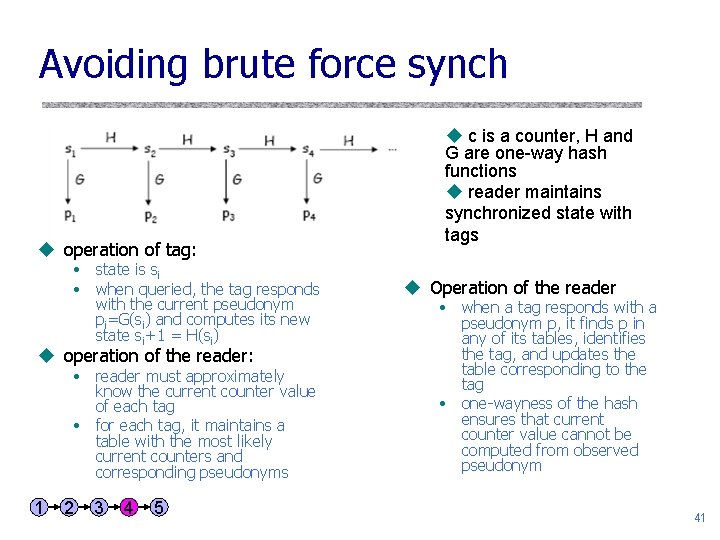
Avoiding brute force synch u operation of tag: • state is si • when queried, the tag responds with the current pseudonym pi=G(si) and computes its new state si+1 = H(si) u operation of the reader: • reader must approximately know the current counter value of each tag • for each tag, it maintains a table with the most likely current counters and corresponding pseudonyms 1 2 3 4 5 u c is a counter, H and G are one-way hash functions u reader maintains synchronized state with tags u Operation of the reader • when a tag responds with a pseudonym p, it finds p in any of its tables, identifies the tag, and updates the table corresponding to the tag • one-wayness of the hash ensures that current counter value cannot be computed from observed pseudonym 41

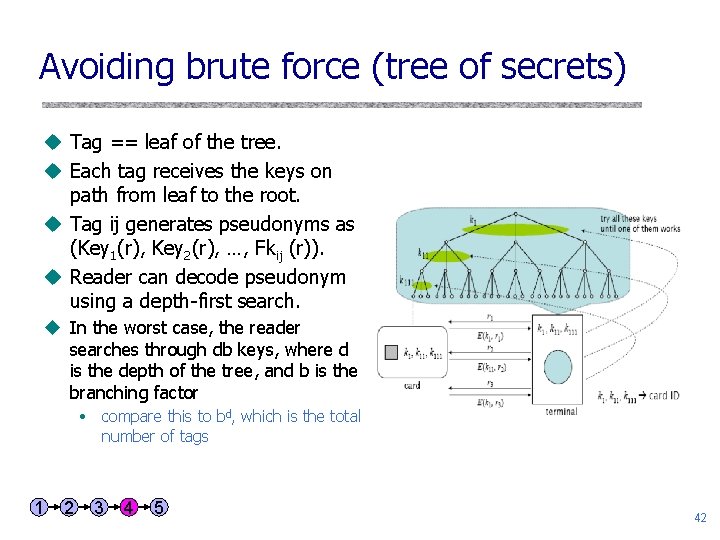
Avoiding brute force (tree of secrets) u Tag == leaf of the tree. u Each tag receives the keys on path from leaf to the root. u Tag ij generates pseudonyms as (Key 1(r), Key 2(r), …, Fkij (r)). u Reader can decode pseudonym using a depth-first search. u In the worst case, the reader searches through db keys, where d is the depth of the tree, and b is the branching factor • compare this to bd, which is the total number of tags 1 2 3 4 5 42

Authentication Workarounds u. No explicit counterfeiting measures whatsoever u. Possible solutions: • Repurpose the kill function for limited counterfeit • Yoking – cryptographic proof that two tags have been scanned simultaneously and evidence (although not proof) that the tags were scanned in physical proximity to one another. – Usable only in certain circumstances (pharmacy, aircraft safety) • Physical markers – Similar to explosive markers – Special dyes and packaging 1 2 3 4 5 43

HB Protocol u. Created by Nicholas Hopper and Manuel Blum as a tool for secure authentication and identification of unassisted humans to computers. u. Juels and Weis realized that this protocol was actually a natural protocol for the authentication of RFID tags to readers. u. The security of the HB Protocol is based on the underlining hardness of the Learning Parity with Noise (LPN) problem. 1 2 3 4 5 44

HB Protocol Definitions u The secret x is a k length binary string (tag ID). • The tag needs to prove to the reader that it knows one of the S's on the reader's list of acceptable secrets. • The tag only has one secret, but the reader generally has many. u A query q is also a k length binary string. • Produced by the reader. • One query is produced for each iteration of the protocol u Epsilon is a probability, ranging from 0 to Ѕ that the response calculated by the tag will be flipped • if the correct response was 1, the tag will send back 0, and vice versa. u Nu equals 1 with probability epsilon. u Delta is an error factor, 1 • ranges from 0 to Ѕ • defines how close the tag's actual flipping of responses must be to epsilon in order to be accepted. 2 3 4 5 45

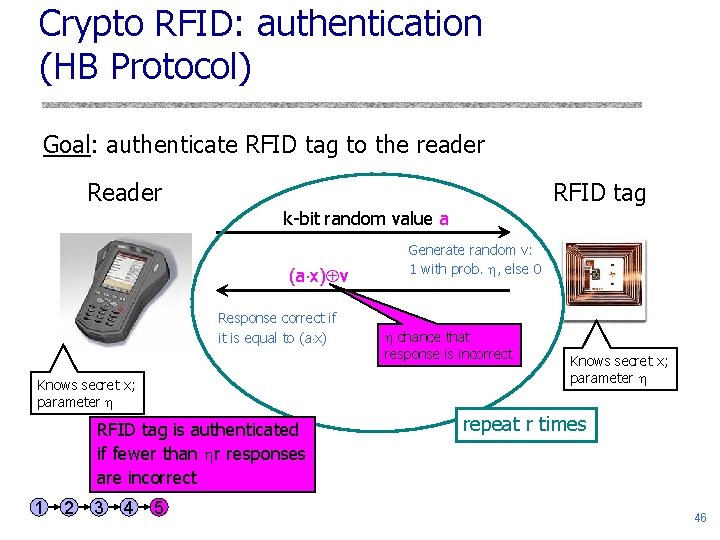
Crypto RFID: authentication (HB Protocol) Goal: authenticate RFID tag to the reader RFID tag k-bit random value a (a x) v Response correct if it is equal to (a x) Knows secret x; parameter RFID tag is authenticated if fewer than r responses are incorrect 1 2 3 4 5 Generate random v: 1 with prob. , else 0 chance that response is incorrect Knows secret x; parameter repeat r times 46

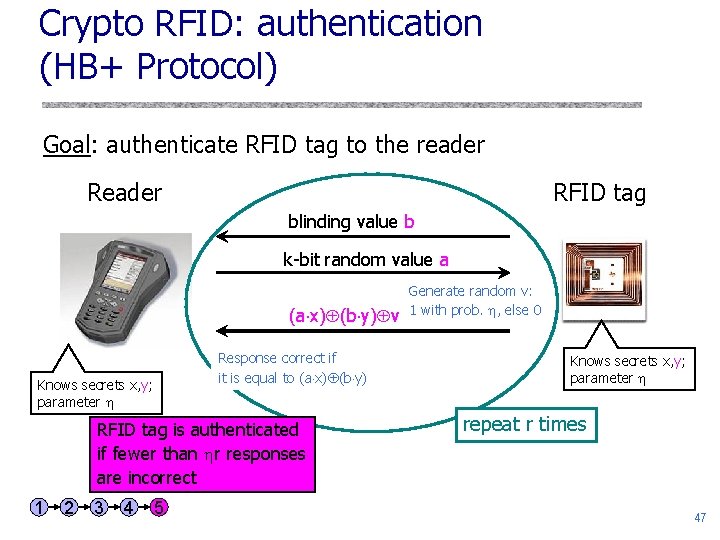
Crypto RFID: authentication (HB+ Protocol) Goal: authenticate RFID tag to the reader RFID tag blinding value b k-bit random value a (a x) (b y) v Response correct if it is equal to (a x) (b y) Knows secrets x, y; parameter RFID tag is authenticated if fewer than r responses are incorrect 1 2 3 4 5 Generate random v: 1 with prob. , else 0 Knows secrets x, y; parameter repeat r times 47

Wrapping it up u Some basic trends are apparent: • Pressure to build a smaller, cheaper tags without cryptography • • Urgent need for cheaper hardware for primitives “Security through obscurity” doesn’t work • • • How about encrypting ID? How about creating new static identifiers, i. e. , “meta-ID” How about a law-enforcement access key? – reverse-engineering a cheap RFID tag unlikely to be hard… u Simple static identifiers are the most naïve – Tag-specific keys require initial release of identity – Universal keys subject to interception u Special properties: • • • RFID tags are close and personal giving privacy a special dimension RFID tags change ownership frequently Key management will be a major problem – Think for a moment after this talk about distribution of kill passwords… – Are there good hardware approaches to key distribution, e. g. , proximity as measure of trust u Some privacy is clearly better than for naive approaches 48

Future Work Find New and Improve Existing Algorithms Authentication algorithms with human protocols Tag identification with delegation, ownership transfer Efficient cloning-resistant identification algorithms New and emerging problems 49