CELLULAR TELEPHONE NETWORK SECURITY Ari Vesanen ari vesanenoulu































- Slides: 45

CELLULAR TELEPHONE NETWORK SECURITY Ari Vesanen, ari. vesanen@oulu. fi Department of Information Processing Sciences, University of Oulu

Contents 1. 2. 3. 4. 5. 6. Introduction to GSM network structure and properties GSM network security model GSM network security threats GPRS vs. GSM Security UMTS vs. GSM Security

Introduction to GSM • GSM world’s most widely used cellular phone system – About 1000 million users – First digital cellular phone standard – 1982 GSM (Groupe Special Mobile) –committee to create standard – 1989 ETSI (European Telecommunications Standards Institute) responsible for development – 1990 first specifications frozen

• GSM specifications developed secretly – No public evaluation according to scientific procedure – Kerckhoff’s principle violated: Algorithm strength should depend on secrecy of key and not on the secrecy of the algorithm itself – GSM specifications and encryption algorithms have leaked and been subject to criticism

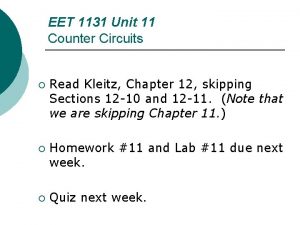
GSM Network Structure Mobile station MS SIM BTS Base Station subsystem BSS Network Switching Subsystem NSS PHONE BTS BSC Um Abis A HLR MSC Au. C PLMN, PSTN, . . . VLR EIR

• Mobile Station = phone + SIM – SIM = Subscriber Identity Module – User identity IMSI (International Mobile Subscriber Identity) on SIM – MSISDN (Mobile Subscriber International Integrated Services Digital Network) –number = Phone number on SIM – Phone identity IMEI (International Mobile Equipment Identity) in phone • Got from phone: type *#06#

• BSS components: Base Transceiver Station (BTS) and Base Station Controller (BSC) – BTS controls radio communication with phone, encrypts calls and does decryption – BSC can control several BTS’s, tasks • Initialization of radio channel • Frequency hopping • Handover (transferring user between cells) • Traffic between BSS and MSC

• NSS = MSC + SMSC + Registers (+ OSS) • Mobile Services Switching Centre (MSC) – Main component of NSS – Works as link to wired network – Services for registering and authenticating mobile user – Services related to mobility • Short Message Service Centre (SMSC) – Transmission of short messages – Needs routing information -> works in cooperation with HLR

• HLR (Home Location Register) – Information on subscribers registered in this GSM network – Current location of users (location network’s VLR address) – One network can contain only one HLR • VLR (Visitor Location Register) – Relevant information on all active users in GSM network • Au. C (Authentication Center) – User secret key information by IMSI • EIR (Equipment Identity Register) – Valid equipments by their IMEI code

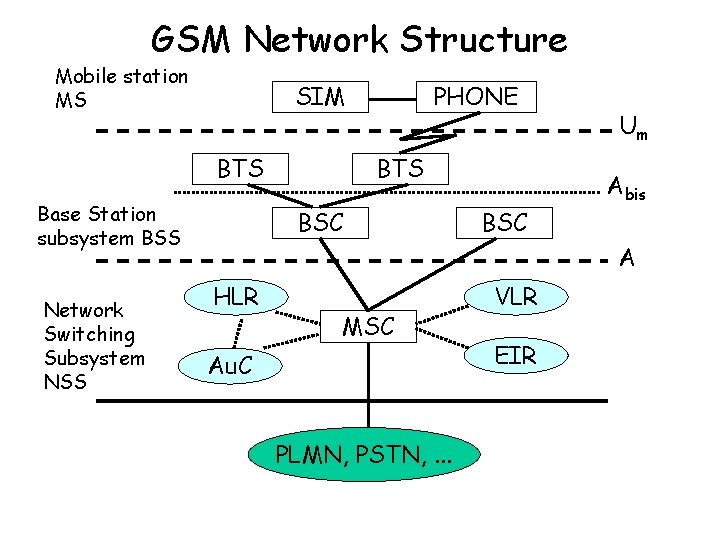
GSM Network Radio Interface • Band control: combined TDMA/FDMA – FDMA divides band into 200 k. Hz wide channels • GSM 900 – 124 channels • GSM 1800 – 374 channels • Channels grouped and distributed to operators – Carrier frequency into time frames according to TDMA model – TDMA frame = eight time intervals (slots) • Message in one slot = burst – Logical channel = one slot in one frame

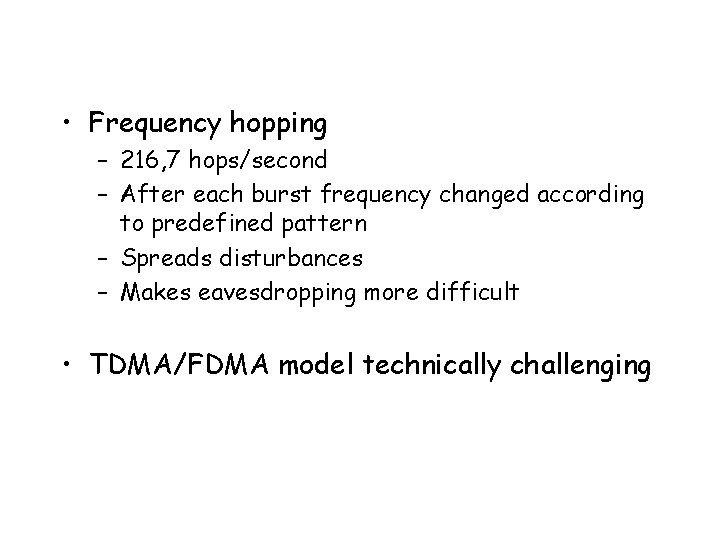
• Frequency hopping – 216, 7 hops/second – After each burst frequency changed according to predefined pattern – Spreads disturbances – Makes eavesdropping more difficult • TDMA/FDMA model technically challenging

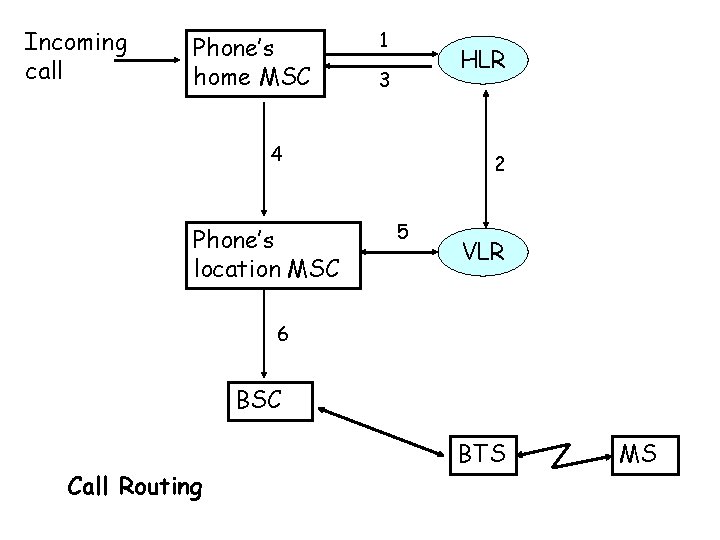
Establishing Call • Updating location – Uses MSC, HLR and VLR – When MS moves to new location area or to new operator area -> must register for update – Location update message to new MSC/VLR –pair that registers new information and sends it to subscribers HLR sends the previous VLR information that subscriber left its area

Incoming call Phone’s home MSC 1 HLR 3 4 Phone’s location MSC 2 5 VLR 6 BSC Call Routing BTS MS

GSM Network Security Model • Identification of subscriber – IMSI – 1. 2. 3. – IMSI consists of three components: Mobile Country Code (MCC) Mobile Network Code (MNC) Mobile Subscriber Identity Number (MSIN) TMSI temporary identifier, used instead of IMSI in communication • Changed when location changed • Makes IMSI capturing and subscriber communication monitoring more difficult

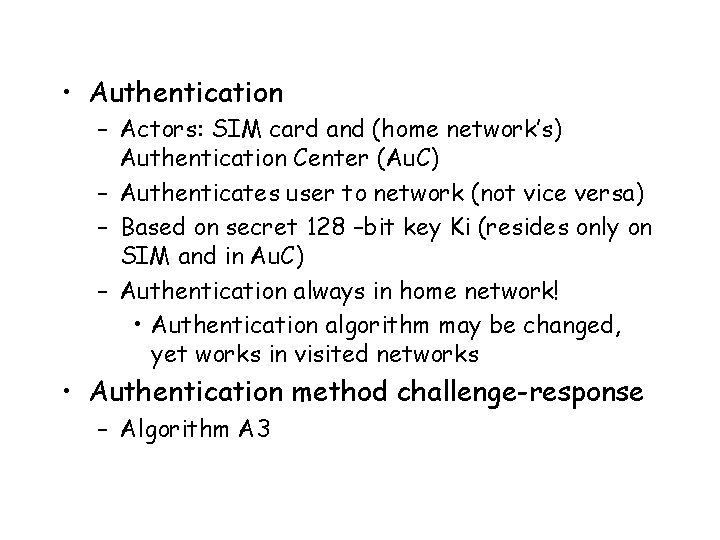
• Authentication – Actors: SIM card and (home network’s) Authentication Center (Au. C) – Authenticates user to network (not vice versa) – Based on secret 128 –bit key Ki (resides only on SIM and in Au. C) – Authentication always in home network! • Authentication algorithm may be changed, yet works in visited networks • Authentication method challenge-response – Algorithm A 3

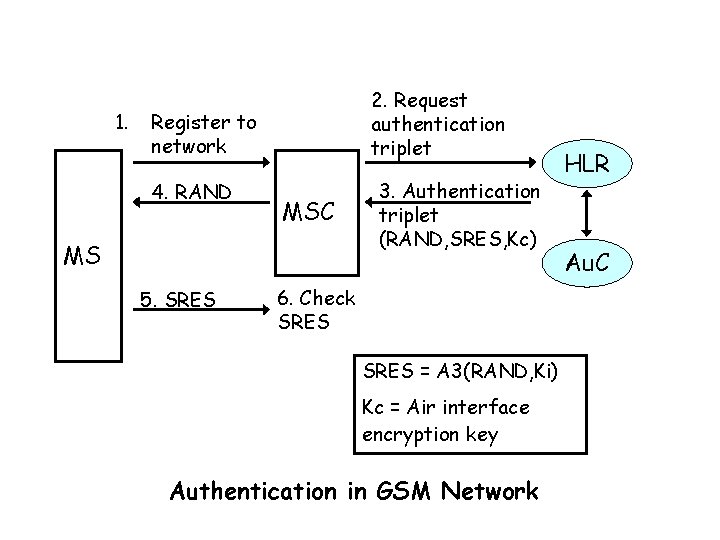
1. 2. Request authentication triplet Register to network 4. RAND MSC MS 5. SRES 3. Authentication triplet (RAND, SRES, Kc) 6. Check SRES = A 3(RAND, Ki) Kc = Air interface encryption key Authentication in GSM Network HLR Au. C

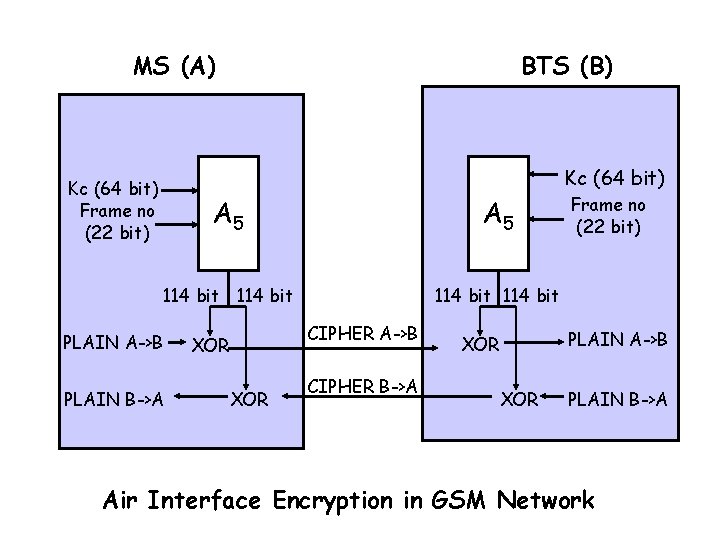
• Air interface encryption – Encryption algorithm A 5 must reside in phone, for all network operators common algorithm – Key generated using algorithm A 8 – on SIM, hence may be operator specific – Uses (64 –bit) session key Kc = A 8(RAND, Ki) and (22 –bit) TDMA frame number – A 5 stream cipher, re-synchronized for each frame – Kc rarely updated (in connection with authentication) – Only air interface encrypted in GSM network, no encryption in operator network • Relied on physical security

MS (A) BTS (B) Kc (64 bit) Frame no (22 bit) A 5 114 bit PLAIN A->B PLAIN B->A CIPHER A->B XOR CIPHER B->A Frame no (22 bit) PLAIN A->B XOR PLAIN B->A Air Interface Encryption in GSM Network

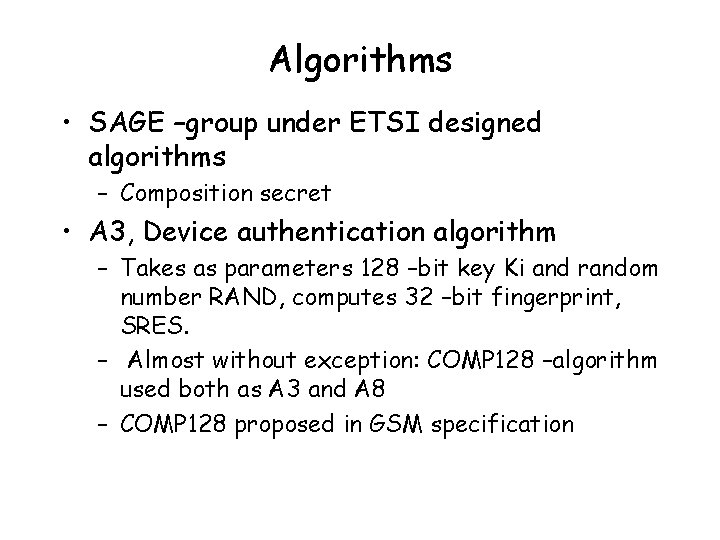
Algorithms • SAGE –group under ETSI designed algorithms – Composition secret • A 3, Device authentication algorithm – Takes as parameters 128 –bit key Ki and random number RAND, computes 32 –bit fingerprint, SRES. – Almost without exception: COMP 128 –algorithm used both as A 3 and A 8 – COMP 128 proposed in GSM specification

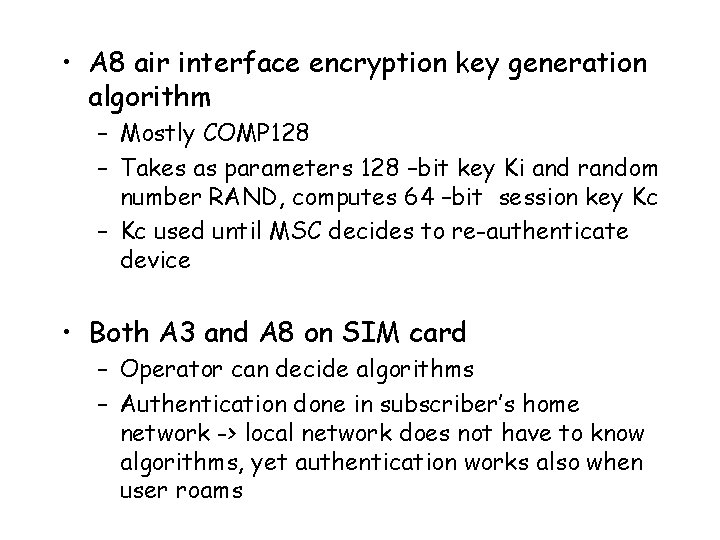
• A 8 air interface encryption key generation algorithm – Mostly COMP 128 – Takes as parameters 128 –bit key Ki and random number RAND, computes 64 –bit session key Kc – Kc used until MSC decides to re-authenticate device • Both A 3 and A 8 on SIM card – Operator can decide algorithms – Authentication done in subscriber’s home network -> local network does not have to know algorithms, yet authentication works also when user roams

• COMP 128 not public, found out using SIM cards and leaked specifications – http: //www. iol. ie/~kooltek/a 3 a 8. txt (Marc Briceno, Ian Goldberg and David Wagner) implementation – Published in April 1998 – Produces both SRES and Kc in one run • Upper 32 bits SRES • Lowest 54 bits + 10 zeros Kc -> effectively Kc is 54 –bit!

A 5 – Air Interface Encryption Algorithm • Stream cipher algorithm • ”Original” European algorithm A 5 leaked in general already in 1994, details in May 1999 (Briceno from GSM phone) • Initialized each sent frame – Key Kc used during call, but 22 -bit frame number changed

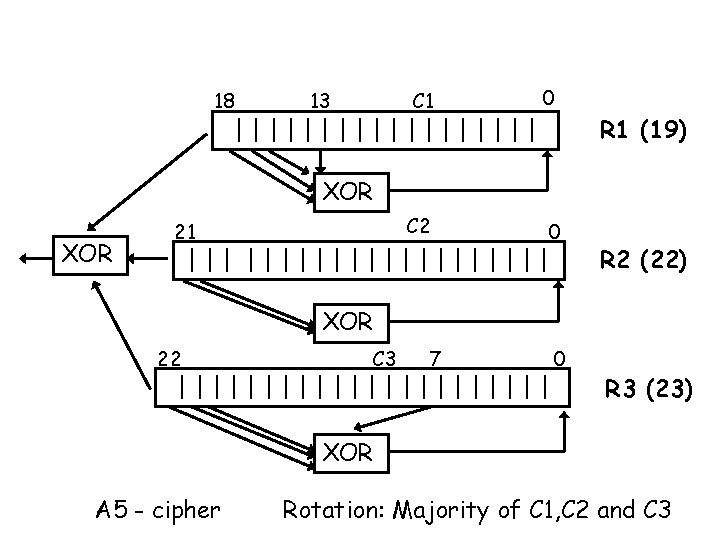
• European A 5 – Three feedback shift registers (LFSR = Linear Feedback Shift Register) of different lengths – Register lengths 19, 22 and 23 bits – Register values XORed and obtained bit XORed with plaintext bit – Registers initialized using session key Kc and frame number – After initialization 228 bits pseudo random bit stream formed: 114 first bits to encrypt frame from device to base station, rest 114 bits from base station to device – Cf. http: //cryptome. org/a 51 -bsw. htm

18 13 C 1 0 C 2 0 ||||||||| R 1 (19) XOR 21 ||||||||||| R 2 (22) XOR 22 C 3 7 ||||||||||| 0 R 3 (23) XOR A 5 - cipher Rotation: Majority of C 1, C 2 and C 3

• Algorithm in many forms, original A 5/1 – Stronger than other A 5/x ’s – A 5/0 = No encryption – A 5/2 decidedly weakened form (used e. g. in USA) • Published analyzed in August 1999 (very weak) – Other A 5/x ’s not become public (if any)

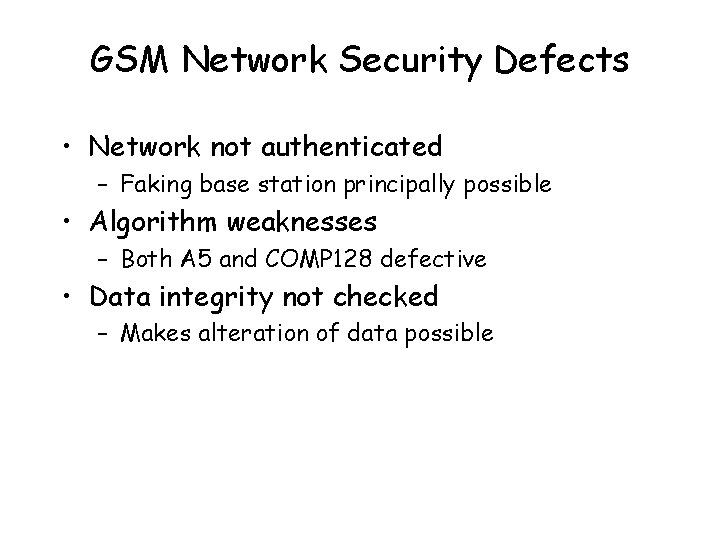
GSM Network Security Defects • Network not authenticated – Faking base station principally possible • Algorithm weaknesses – Both A 5 and COMP 128 defective • Data integrity not checked – Makes alteration of data possible

• Authentication data transmitted in clear both inside and between networks – Contains also air interface encryption key • Lack of visibility – User can not know whether encryption used or not – No confirmation to home network, whether serving network uses correctly authentication parameters when user roams

Threats • Attacks against A 5 –implementation (Mike Roe): http: //www. hackcanada. com/blackcrawl/cell/gs m/gsm_security. html – Breaking air interface encryption -> call eavesdropping – Many methods proposed for breaking A 5: – Almost practical attack by Golic: ” Cryptanalysis of Alleged A 5 Stream Cipher” cf. http: //downloads. securityfocus. com/library/a 5 hack. html • Birthday attack type time/memory optimization

– Attack applicable in real time: – Biryukov, Shamir and Wagner (cf. http: //cryptome. org/a 51 -bsw. htm): Real time break algorithm on PC against the strong algorithm A 5/1 – Basic assumption: Attacker knows or guesses part of bit stream produced by cipher – Basic idea: Great number of pre-computed states stored (possible, since feedback registers can only be in 264 different states) • Idea by Golic

– Key can be deduced from initial state of each frame – A 5/1 can be effectively implemented on PC (each register small enough to store their states in computer’s memory as three cyclic arrays) – A 5/1 can be run backwards effectively – However, backward computation not entirely deterministic: one state can be arrived at from several states

– Suitable 16 -bit number alpha in advance chosen and only frames that include alpha considered – The number of register states producing alpha is about 248 – States computed in advance and stored on disk -> attack demands large amount of space – Three different attacks (all require at least two 73 GB hard drives)

– Estimate: First type attack (”biased birthday attack” –two versions), needs about 2 minutes of call data • Alpha appears sufficiently many times (ca. 71) in data – Direct collision with disk data and cipher data • Encryption broken in one second – Third type attack (”random subgraph attack”): call data 2 seconds • Performing attack takes minutes – No crypto attack carried out in practice (presumably)

• SIM card cloning (by physical contact) – Subscriber’s secret key on SIM and security depends on this key -> if attacker obtains SIM security can be broken – An identical copy of SIM can be made • If card noticed missing, it can quickly be shut of services • If copy and original simultaneously used, network notices and invalidates both • In principal cloned card can be used such that subscriber is billed

– Revealing key Ki from SIM • Based on weakness of COMP 128 • Inventors: SDA (Smartcard Developer Association) and ISAAC (Internet Security, Applications, Authentication and Cryptography) – Cf. http: //www. isaac. cs. berkeley. edu/isaac/gsmfaq. html • Flaw in algorithm -> information on Ki obtained by giving suitable random number inputs RAND as an argument to A 8 – Input RAND slightly changed and observed when identical answer obtained – 217. 5 inputs enough to deduce Ki

• Test attack: SIM in card reader attached to PC; PC generated 150 000 challenges, using which SIM computed SRES –response and session key Kc -> based on information Ki computed. Took ca. 8 hours – April 1998 • Used attack technique standard -like – Cf. e. g. Serge Vaudenay ”FFT-Hash-II is not yet Collision-Free” http: //lasecwww. epfl. ch/pub/lasec/doc/liens-9217. A 4. ps

• SIM cloning over-the-air – ISAAC: According to experts possible in practice (faking base station) • Cf. http: //www. isaac. cs. berkeley. edu/isaac/ gsm. html – Type 1: Attacker builds fake base station, covering subscriber’s valid BTS -> Subscriber’s SIM may be bombed with self-generated authentication requests

• Estimate: Attack duration 8 – 13 hours, victim device has to be in operating area of fake base station (not necessarily continuously) • Subscriber can not detect attack – Enhanced version of COMP 128 exists (COMP 128 -2) • Some operators use • Not (known to be) broken – Type 2: Attack from legal network • Client outside home network (e. g. abroad) • Attacker inside location network

• Building fake (rogue) base station – Cost estimate 10 000 euros – Can capture IMSI – Gathered information might be used in networks with more loose authentication – Counter: Temporary identifier TMSI, changed when subscriber location updated • TMSI not entirely prevents IMSI capture since IMSI has to be sent once – Also other attacks (e. g. mentioned SIM – cloning)

• Cell change in GSM network 1. 2. 3. 4. Phone sends audibility reports to BTS adds own information and sends to BSC cell change request to MSC (if necessary) MSC resource allocation request to new BSC, that waits for MS to arrive 5. New BSC send acknowledgement to MSC that sends cell change command to old BSC, this forwards it to MS 6. MS breaks connection to old base station and continues with new one

How to hook up a phone to my fake base station? • Item 5: Cell change command from the network -> Attacker may simulate command force the phone to change – No authentication for base stations -> Device can not know communicating with a rogue base station

GPRS vs. GSM Security • GPRS transition phase to 3 G, supports packet switched traffic – Voice (circuit switched traffic) as in GSM – GPRS data uses multiple slots • Air interface encryption (differences with GSM) – New A 5 –algorithm GEA • Yet secret – GPRS traffic encryption extends further (base stations cannot cope with traffic using several slots)

• Authentication (differences with GSM) – Separate authentication for circuit switched and packet switched traffic • Packet switched backbone has own security features – Not considered here

UMTS vs. GSM Security • UMTS design applies open standardization • Specs: 3 GPP ( 3 rd Generation Partnership Project) – WWW –site http: //www. 3 gpp. org, contains specifications etc. – Cf. TTAE. 3 G-33. 102 ” 3 G Security; Security Architecture” – UMTS network constructed on (and parallel to) existing GSM networks -> Security model constructed on GSM security model

• Authentication method as in GSM – Based on a secret key K, residing only on USIM and in home network Au. C • Comparison: in GSM network authentication vectors triplets (RAND, SRES , Kc) in UMTS network quintets (RAND, XRES, CK, IK, AUTN) – IK integrity key for data integrity – AUTN authentication token for network authentication

• Improvements to GSM security – Encryption algorithms use longer keys – Network also authenticated – Signaling data authenticated and integrity checked • UMTS GSM –compatible – GSM users have GSM context – GSM users have practically GSM security in UMTS network
 A satellite used in a cellular telephone network
A satellite used in a cellular telephone network ñe'e jurugua ejemplos
ñe'e jurugua ejemplos Privatesecurity
Privatesecurity Osi security architecture model
Osi security architecture model Guide to network security
Guide to network security Wireless security in cryptography
Wireless security in cryptography Electronic mail security in network security
Electronic mail security in network security Security guide to network security fundamentals
Security guide to network security fundamentals Security guide to network security fundamentals
Security guide to network security fundamentals Public switched telephone network diagram
Public switched telephone network diagram Public switched telephone network diagram
Public switched telephone network diagram Pstn hierarchy
Pstn hierarchy Pstn hierarchy
Pstn hierarchy Introduction to network management
Introduction to network management Pstn adalah singkatan dari
Pstn adalah singkatan dari Cellular network range
Cellular network range Cellular core network
Cellular core network Visa international security model
Visa international security model Nstissc security model in information security
Nstissc security model in information security E commerce security meaning
E commerce security meaning Software security building security in
Software security building security in 5g americas
5g americas Wireless network security definition
Wireless network security definition Palo alto networks certified network security consultant
Palo alto networks certified network security consultant Network security protocols
Network security protocols Network security essentials 5th edition pdf
Network security essentials 5th edition pdf Intruders in cryptography and network security
Intruders in cryptography and network security Network security design
Network security design Module 3: information and network security
Module 3: information and network security Approaches to message authentication
Approaches to message authentication Playfair cipher
Playfair cipher Nsm network security monitoring open systems
Nsm network security monitoring open systems Gfi network security scanner
Gfi network security scanner Triple des meet in the middle attack
Triple des meet in the middle attack Cryptography and network security 6th edition
Cryptography and network security 6th edition Introduction to cryptography and network security
Introduction to cryptography and network security Number theory in cryptography and network security
Number theory in cryptography and network security Firewall in cryptography and network security
Firewall in cryptography and network security Authentication in cryptography and network security
Authentication in cryptography and network security Aes in network security
Aes in network security Modern network security
Modern network security Remote network security services
Remote network security services Network security topologies
Network security topologies Interesting topics in network security
Interesting topics in network security Kr
Kr Ic chip 74190
Ic chip 74190